Note: Descriptions are shown in the official language in which they were submitted.
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
A METHOD OF BILLING A PURCHASE MADE
OVER A COMPUTER NETWORK
The present application is a continuation-in-part application of U.S. Patent
Application Serial No. 09/362,238, filed July 28, 1999; which is a
continuation-in-
part application of U.S. Patent Application Serial No. 09/280,863, filed March
30,
1999, now abandoned; which is a continuation-in-part application of U.S.
Patent
Application Serial No. 09/245,713, filed February 8, 1999, now abandoned;
which is
a continuation-in-part of U.S. Patent Application Serial No. 09/039,335, filed
March
16, 1998, now abandoned; which is a continuation-in-part of U.S. Patent
Application
Serial No. 08/757,563, filed November 26, 1996, now U.S. Patent 5,960,069;
which is
a continuation-in-part of U.S. Patent Application Serial No. 08/658,378, filed
June 5,
1996, now U.S. Patent No. 5,802,156, each of which are incorporated by
reference
herein. The present application is also related to U.S. Patent Application
Serial No.
(Atty Docket 2416.84534) and filed ; which is a continuation-in-part
application of U.S. Patent Application Serial No. 09/362,239, filed July 28,
1999, and
now abandoned; which is a continuation-in-part application of U.S. Patent
Application Serial No. 09/280,862, filed March 30, 1999, and now abandoned;
which
is a continuation-in-part application of U.S. Patent Application Serial No.
09/245,713,
filed February 8, 1999, and now abandoned; and is related to U.S. Patent
Application
Serial No. (Atty Docket 2416.84536), filed ; which is a
continuation-in-part application of U.S. Patent Application Serial No.
09/356,572,
filed July 19, 1999, and now abandoned; which is a continuation-in-part
application of
U.S. Patent Application Serial No. 09/039,335, filed March 16, 1998 and now
abandoned, each of which is incorporated by reference herein. Additionally,
the
present application claims benefit of U.S. Provisional Patent Application
Serial No.
60/139,475, filed June 17, 1999, which is incorporated by reference herein.
1
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
I. BACKGROUND OF THE INVENTION
A. Technical Field
The present invention relates to an efficient payment authorization and
billing
arrangement for products and services purchased over a computer network, such
as
the Internet. More particularly, the present invention relates to a method for
providing payment authorization and a billing arrangement for a call or a
communication session to a service representative that is accessible over a
telecommunications network or a computer network, such as the Internet, and to
session limiting, blocking, fraud control associated with such a communication
session. The present invention also relates to a method for providing payment
authorization and a billing arrangement for effecting a sale of goods and/or
services
over a computer network, such as the Internet.
B. Description of the Related Arts
So-called psychic network services have been in operation for several years.
A service representative, or agent, at such a service counsels a caller who
has called
on an 800 or 900 telephone number regarding life, love and prosperity. For a
fee, the
caller can ask any question of the service representative and, generally, the
service
representative may counsel to the caller regarding the question.
Presently, a caller to the Yellow Pages Psychic Network service dials one of a
plurality of telephone numbers that are used by the network for determining
the
advertising source from which the caller became aware of the psychic network
service. Each respective telephone number connects a caller to the same
service
bureau where an automatic call distribution (ACD) system distributes calls
among
service representatives. The caller hears an announcement regarding costs and
charges, referred to as a preamble, and is then offered a menu of choices. The
caller is
given a choice to hear brief resumes of the service representatives that are
presently
available. When the caller decides on a specific psychic, the caller may press
the
button, for example, to reach that particular psychic. When the caller already
knows
the extension number of a psychic that the caller has used before, that
particular
2
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
telephone extension may be entered. The caller controls the call, but can
speak only
to one psychic during the call.
ACD telecommunications equipment is known for providing this and other
types of telecommunications services. Common-controlled ACD equipment is
available, for example, from Lucent Technologies, Inc. and other manufacturers
of
common-controlled switching equipment. Typically, a service bureau or related
organization offers services through a service bureau-owned ACD system. Such
an
ACD system directs a call from a caller requesting service to a next available
service
representative listed in a service representative availability queue. It is
always
assumed that one service representative responds to a call. Service
representatives,
typically equipped with displays and operator type headsets .for hands-free
operation,
usually consult databases for, for example, making travel reservations. To
this end,
service representatives have access to large computer databases of travel
reservation
and billing information.
Billing arrangements for such service bureau organizations are primitive and
may rely on a 900 service for the service provider to bill the caller for the
service
provided. For an 800 number call, the service provider pays for the call and
must
insure that payment for the service will be received, even more so than for
900-based
call. The service provider records credit card or other payment data manually
into a
memory of a billing system for properly billing the call. Such procedures have
led to
many callers questioning their bills in many instances. Additionally,
dishonest callers
have received free calls using fraudulent payment schemes, improper granting
of
credit and the like because of inefficiencies associated with conventional
billing
procedures.
One approach for overcoming these and other problems is provided by a
service offered by a company known as Mile High Psychics that uses credit
cards for
prepayment for blocks of service usage time. Credit authorization is obtained
well in
advance of when service is provided. For example, the customer may purchase a
block of 25 minutes of service in advance of a call and utilize a personal
identification
number or code (PIN) at the time of the call for accessing the service.
3
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
Another approach is presented by U.S. Patent No. 5,475,740 to Biggs, Jr., et
al. which discloses a system connected to a central distribution computer that
enables
a user to access and pay for amenities using a telephone for entering amenity
identification and billing information. A billing database is connected to the
central
distribution computer for validating entered billing information.
U.S. Patent No. 5,383,113 to Kight et al. and U.S. Patent No. 5,283,829 to
Anderson are both directed to a method for paying bills electronically.
According to
U.S. Patent No. 5,383,113 to Kight et al., a computerized payment system is
implemented by which a consumer may instruct a service provider by telephone,
computer terminal, or by using another telecommunications technique to pay
various
bills without the consumer being required to write a check for each bill. The
service
provider collects information from consumers, financial institutions and
merchants,
and arranges payment to the merchants according to each consumer's specific
instructions. Similarly, U.S. Patent No. 5,283,829 to Anderson discloses an
electronic
bill payment system and method that includes billing equipment for creating
approval
records and generating approval numbers for each pre-authorized subscriber.
The
system also includes an interactive payment approval apparatus into which
subscribers dial for approving payment and which determines, based upon
information collected, whether to initiate an electronic funds transfer. A
series of
security checks and comparisons are performed for guarding against accidental
and
malicious entry of approval numbers.
U.S. Patent No. 4,908,850 to Masson et al. discloses an information network
and method for providing a nationwide audio text network, including electronic
billing, that is useful for a wide variety of applications. The system allows
for
interactive communication with a computer that supplies the network
information to a
1-800 caller. The system is also capable of obtaining electronic credit card
authorization or charges, and controls routing an incoming call for
redirecting the call
to a live operator or to other equipment, or to outgoing lines to any desired
destination.
In another conventional system, credit cards are used for paying for service
representative calls. In this system, each time the caller calls, the caller's
credit card
4
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
account is accessed and a predetermined charge, such as 100 dollars, is
authorized and
set aside from the caller's credit card available line of credit. The caller
then speaks
with a service representative. The actual cost of the call is determined at
the end of
the call, and then transferred to the credit card company in the normal course
of
business. The charge is then compared to the amount that has been set aside
and the
difference between the amount that has been set aside and the actual cost of
the call is
returned to the caller's available line of credit. Unfortunately for the
caller, this
process usually takes approximately 3 or 4 days. As a result, the portion of
the caller's
available line of credit that has been set aside is unavailable for other
calls or
purchases for the approximately 3 to 4 days that it takes the credit card
company to
reconcile the authorized amount and the actual amount of the. call.
Additionally, there is a growing need for providing a billing arrangement for
effecting a sale of an item or a service occurring over a computer network.
For
example, U.S. Patent No. 5,724,424 to Gifford discloses a network sales system
that
allows a user to purchase goods or information over a computer network, such
as the
Internet. According to Gifford, the network sales system includes a plurality
of buyer
computers, a plurality of merchant computers and a payment computer that are
interconnected by the computer network. A user at a buyer computer purchases a
product and the buyer computer sends a purchase message to a merchant
computer.
The merchant computer constructs a payment order that it sends to the payment
computer. The payment computer authorizes the purchase and sends an
authorization
message to the merchant computer. When the merchant computer receives the
authorization message, product is sent to the buyer computer. Alternatively,
the buyer
computer can send a payment order directly to the payment computer, which, in
turn,
sends an authorization message back to the buyer computer that includes an
unforgeable certificate indicating that the order is valid. The buyer computer
then
constructs a purchase message that is sent to the merchant computer. When the
merchant computer receives the purchase request, the product is sent to the
buyer
computer based on the pre-authorized payment order.
U.S. Patent No. 5,715,314 to Payne et al. discloses a similar network-based
sales system that includes at least one buyer computer, at least one merchant
computer
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
and at least one payment computer that are interconnected by a computer
network,
such as the Internet. According to Payne et al., a merchant computer can
respond to
payment orders from a buyer computer without the merchant computer having to
communicate directly with the payment computer for ensuring that the user is
authorized to purchase the product and without the merchant computer having to
store
information in a database regarding which buyers are authorized to purchase
which
products. When the merchant computer receives an access message from the buyer
computer identifying a product to be purchased, the merchant computer need
only
check the access message for ensuring that the access message was created by
the
payment computer, thereby establishing that the buyer is authorized to
purchase the
product.
Despite these conventional billing arrangements for voice-based telephony
services over a circuit-switched telecommunications network and for products
and
services purchased over a computer network, such as the Internet, there is a
need for
an efficient payment authorization and billing arrangement for products,
services and
telephony-based services purchased over a computer network.
II. SUMMARY OF THE PRESENT INVENTION
The present invention provides an efficient payment authorization and a
billing arrangement for a communication session between a user and a service
representative that is accessible over a circuit-switched telecommunications
network
and a packet-switched telecommunications network, such as the Internet, and to
session limiting, blocking, fraud control associated with such a communication
session. The present invention also provides an efficient payment
authorization and
billing arrangement for products and services purchased over a computer
network,
such as the Internet, and to purchase limiting, blocking, fraud control
associated with
such a purchase.
The advantages of the present invention are provided by a method of billing a
communication session between a service representative and a user in which a
request
is received from a user for a communication session between the user and a
service
representative. Information associated with a credit account is requested
before the
6
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
user is connected to a service representative, and the information associated
with the
credit account is received in real time. According to the invention, the
information
associated with the credit account can be credit card information, debit card
information, checking account information, electronic funds transfer
information, a
telephone number, a cable television account, a utility service account, or an
Internet
service provider account. Credit account information is communicated to a
payment
authorization database, which can be located locally or remotely. When the
credit
account information relates to, for example, a credit card, the credit account
information includes the received information associated with the credit
account and a
predetermined amount that is to be set aside in the credit account.
Alternatively, the
credit account information includes the received information associated with
the
credit account and a predetermined amount that is to be charged to the credit
account.
Payment authorization information associated with the credit account is
received from
the payment authorization database before the user is connected to the service
representative, and the user is connected to the service representative when
the
payment authorization information is affirmative. A total charge for the
communication session is calculated when the communication session is
terminated
based on an actual time that the user is connected to the service
representative.
Preferably, the charge for the communication session is based on a per minute
rate.
Session charge information associated with the communication session is
transmitted
to the payment authorization database when the communication session is
terminated.
Accordingly, the session charge information includes information for charging
the
credit account an amount representing a charge for the communication session.
According to one aspect of the invention, when the credit account information
relates to, for example, a credit card, the credit account information
includes an
authorization of a predetermined amount, and the session charge information
includes
information for reversing the authorization of the predetermined amount and
for
reauthorizing the credit account the amount representing the charge for the
communication session. Alternatively, the session charge information is a
credit
representing an amount that is the predetermined amount minus the amount
representing the charge for the communication session.
7
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
The present invention also provides a method for controlling communication
session access to a service representation in which a request is received from
a user
for a communication session, such as a computer-network telephony call or a
multi-
media communication session, between the user and a service representative.
Information associated with the user is also received, and a database is
accessed. The
received information associated with the user is compared with information
stored in
the database, and the user is connected to the service representative when the
received
information associated with the user passes the comparison with the
information
stored in the database. The communication session can be blocked or limited
based
on different criteria, such as a frequency of communication sessions from the
user
during a predetermined period of time, an amount of money spent by the user
during a
predetermined period of time, a length of communication sessions during a
predetermined period of time, an identity of the user, a computer-network
address of
the user, credit account information of the user, personal information of the
user,
and/or a user billing address.
Another embodiment of the present invention provides a method of effecting a
sale over a computer network in which it is determined whether a user passes
fraud
control before effecting a sale over a computer network. Information
associated with
a method of payment, such as credit card information, debit card information,
checking account information, a telephone service account, a cable television
account,
a utility service account, or an Internet service provider account, is
requested from
the user after the user passes the fraud control. Information associated with
the
method of payment is received from the user in real time. Method-of payment
information is communicated to a payment authorization database, which can be
located locally or remotely. The method-of payment information includes the
received information associated with the method of payment. Payment
authorization
information associated with the method of payment is received from the payment
authorization database. A sale transaction is completed when the payment
authorization information is affirmative. Sale charge information associated
with the
sale effected over the computer network is transmitted to the payment
authorization
database when the sale transaction is complete. The sale charge information
includes
8
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
information for charging the method of payment an amount representing a charge
for
the sale.
According to one aspect of this embodiment of the present invention, whether
a user passes fraud control is based on computer-network address information
associated with the user that is received from the computer network and
computer-
network address information that is received from the user. The computer-
network
address information received from the computer network is compared to the
computer-network address information received from the user before the
information
associated with the method of payment is requested. According to another
aspect of
this embodiment of the present invention, whether a user passes fraud control
is
determined based on received information associated with the user. A database
is
accessed, and the received information associated with the user is compared
with
information stored in the database before information associated with the
method of
payment is requested from the user. The method also provides that information
associated with the user is compared with information stored in the database
before
determining whether to block, limit or complete the sale transaction. The
received
information can include an identity of the user, a frequency of sales to the
user during
a predetermined period of time, an amount of money spent by the user during a
predetermined period of time, a computer-network address for the user, credit
account
information associated with the user, a billing address, and/or personal
information of
the user.
BRIEF DESCRIPTION OF THE DRAWINGS
Figure 1 shows a schematic block diagram for an automatic call distribution
system that is programmed to operate according to the present invention;
Figure 2 shows a flowchart of the sequence of operations for logging a service
representative into a service representative availability queue according to
the present
invention;
Figure 3 shows a flowchart for processing a call received from a circuit-
switched telecommunications network or by way of computer-network telephony
over
9
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
a packet-switched computer network, such as the Internet, for a service
representative
according to the present invention;
Figure 4 shows a flow diagram for a real-time billing system for circuit-
switched and packet-switched calls in accordance with the principles of the
present
invention;
Figure S shows a schematic block diagram of a system for billing a
communication session conducted over a computer network, such as the Internet,
according to the present invention;
Figure 6 shows a flowchart for a communication for actuating and entering a
service representative into a service representative availability queue a
computer
network according to the present invention;
Figure 7 shows a flowchart for processing a service representative
communication session to a service bureau over a computer network according to
the
presentinvention;
Figure 8 shows a flow diagram for a real-time billing system for a billing
communication session occurring over a computer network according to the
present
invention;
Figure 9 shows a flow diagram for a real-time billing system for effecting a
sale over a computer network according to the present invention; and
Figures l0a-lOc show a flow diagram summarizing the real-time billing and
fraud control system of the present invention.
DETAILED DESCRIPTION
Figure 1 shows a schematic block diagram for an automatic call distribution
(ACD) system that is programmed to operate according to the present invention.
An
exemplary ACD system that is suitable for the present invention is disclosed
by U.S.
Patent No. 5,802,156 to Felger, which is incorporated by reference herein. An
ACD
system provides switched network access to a plurality of service
representatives or
agents. Such ACD systems may vary from manufacturer to manufacturer, but
according to the present invention, such an ACD system operates under common-
control of a controller 110. The ACD system of Figure 1 includes a switch 100
that is
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
connected to a plurality of service representatives, or agents, that operate
from service
representative positions 101-1 through 102-n. ACD 100 redirects calls (circuit-
switched voice and data) to any of service representative positions 101-1
through
102-n.
A service representative position, such as position 101-1, can include a
remote
dial-up terminal lOla that has a caller identification display lOlb.
Alternatively, a
service representative position can be a conventional service representative
position,
such as position 101-2, that includes such equipment (not shown) as an
operator
headset, a cathode ray tube display, a computer system and automatic number
identification/name display. Accordingly, such a service representative
position
operates as an extension line for the ACD system. As yet another alternative,
a
service representative position may include an intelligent telephone terminal,
a
personal computer or other intelligent terminal known in the art (not shown).
A service representative at a service representative position indicates
availability for providing service to callers by performing a log-in
procedure, such as
that shown by the flowchart of Figure 2, which will be further described
herein. A
caller requesting service is handled according to the flowchart of Figure 3,
which will
also be further described herein.
A plurality of service circuits and devices are connected to switch 100 that
provide various signaling, data input, data output, conferencing and other
services.
Such service circuits and devices include, but are not limited to, a dual tone
multi-
frequency (DTMF) receiver and decoder 120, an automatic number identification
(ANI), a dialed number identification (DNI) circuitry 125, an audio response
(message)' unit 135, a conference bridge circuit 130 and a
modulator/demodulator
circuitry (MODEM) 140. One or more of each type of these service circuits and
devices are typically provided, with the number depending on their respective
frequency of use.
Each service circuit or device is called into play by controller 110 in
accordance with call processing and control programs stored in a memory 115.
One
control program residing in memory 115 is a real time of day, day, month and
year
clock that is accurately maintained by, for example, periodic satellite update
and must
11
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/CTS00/30504
be preserved even in the event of a local power loss to the system. Another
program
is a translation program that may be needed for translating a called telephone
number
to an advertising source or for translating an extension number of a service
representative to a remote telephone number for remote dialing, when required.
DTMF receiver and decoder 120 is especially important for receiving
information, such as zip code, address, credit card number, bank account
number,
name input, command and signals for the system of the present invention for
caller
control and system control to the extent of at least providing service, call
blocking,
call limiting, fraud control and payment and billing features. Audio response
(message) unit 135 preferably includes an audible announcement capability for
querying a caller and a connection to DTMF receiver/decoder 120 for receiving
and
decoding input data entered via a telephone keypad in response to an
announcement
query. Alternatively, DTMF receiver/decoder 120 and other input circuits may
be
replaced by speech recognition and other automatic input devices. Modem 140
automatically forwards form-of payment data to a credit agency or bank under
control
of controller 110, and receives authorization in real time for a payment or a
charge to
an account. Modem 140 may comprise a network data mover (NDM) modem or a
remote job entry (RJE) modem. Once a call to a service representative is
terminated,
modem 140 communicates call charge information to a remotely-located billing
agency (not shown).
Callers call on lines 110-1 and 110-2, which are representative of
lines/trunks
connecting ACD 100 to a telephone switching center. A number of different
telephone numbers identified to the lines/trunks at a telephone central office
(not
shown) may be used for identifying the source of advertising or other source
by which
a caller learned of the existence of the call-in service. Typically, signaling
information is provided in advance of a call on the same or a different line.
The
signaling information includes the address of the calling party and may also
include
the called address. A dialed number identification/automatic number
identification
(ANI/DNI) unit 125 identifies the dialed number for determining, for example,
the
source by which a caller learned of the service. ANI/DNI unit 125 also
indicates the
calling telephone number for subsequent comparison with a telephone number
entered
12
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
through a telephone keypad by the caller in response to a request generated by
audio
response (message) unit 135 once the call has begun or for comparison with
negative
databases, as will be further described herein.
Briefly and according to one embodiment of the present invention, a toll, an
800 or 900 telephone number or an Internet address may be used for connecting
a new
caller to a single service representative in an available service
representative at, for
example, a psychic network service. A second telephone number or Internet
address
may be used for identifying a psychic twins service, such that two service
representatives are connected simultaneously to a caller through a dual
representative
service representative availability queue. A third number or Internet address
is used
for a three service representative call, and so on. In a preferred embodiment
of the
present invention, a caller is handled according to a call processing
algorithm shown
in Figure 3, which is described subsequently herein.
Conference bridge 130 may include automatic dialing equipment for dialing a
telephone number for a service representative. Alternatively, automatic
dialing
circuits (not shown) may be separately provided. Of course, in accordance with
the
present invention, a plurality of service representatives are simultaneously
connected
to a caller desiring such service and automatic dialing circuits may or may
not be
needed in a particular conference call, depending on whether the service
representative is directly connected to ACD 100 as an extension or must be
"dialed-
up." Ringing circuits (not shown) transmit ringing signals toward a service
representative, but according to the present invention, audible ringing is not
provided
the caller. The service representative is connected at the time the service
representative goes off hook.
The concepts of the present invention are fully applicable to all forms of
telephony, whether circuit-switched based telephony or computer-network
telephony,
such as packet-switched telephony. For example, a typical router connected to
a
computer network, such as the Internet, can handle packetized telephony data
in a
manner similar to how the ACD system shown in Figure 1 handles circuit-
switched
telephony. Just as an ACD system provides circuit-switched network access to a
plurality of service representatives or agents, a router provides packet-
switched
13
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/LTS00/30504
network access to a plurality of computer network addresses. The router
redirects
Internet-type telephony and communication session data packets to service
representative positions in a well-known manner. In that regard, an Internet
address
may be used for connecting a computer-network telephony caller to a single
service
representative in an available service representative at, for example, a
psychic
network service. A second Internet address may be used for identifying a
psychic
twins service, such that two service representatives are connected
simultaneously to a
caller through a dual representative service representative availability
queue. A third
Internet address is used for a three service representative call, and so on.
For a
computer-network based embodiment of the invention, a service representative
position is preferably an intelligent telephone terminal, a personal computer
or other
intelligent terminal known in the art.
Figure 2 shows a flowchart of the sequence of operations controlled by
controller 110 when actuating and entering a service representative into a
service
representative availability queue according to the present invention. The
overall
procedure of Figure 2 is performed whether the service representative is
accessing the
service bureau through a circuit-switched telecommunications network or by way
of
packet-switched telephony. At step 200, a service representative calls the
service
bureau and indicates the availability of a service representative for
providing service.
Of course, when the service representative is directly connected to switch
100, such as
by a private dedicated line, the calling service representative may need only
to merely
pick up the phone or log on, respectively. Whether or not the calling service
representative is connected via a dedicated line, the extension or telephone
number is
automatically recognized by controller 110, for example, through automatic
number
identification circuit 125. In a packetized telephony-based embodiment, the
Internet
address or log-on data of the service representative may be compared against a
database for determining service representative identity.
An audio response unit 13 S is connected to the service representative at step
210. Typically, the time of day and date is recorded in memory 115 via
controller 110
recording the time and date that the service representative has offered to
begin
servicing callers. The service representative receives a programmed
announcement at
14
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
step 210 querying the service representative to identify certain choices and
preferences for recording in memory 115. For example, a pair of psychic twins
may
prefer to offer services together to a caller. That is, a service
representative A may
request to only be connected in a psychic dual-conferencing call with a
specific
psychic twin service representative B. Other preferences may be predetermined
or
entered for the first time, such as the service representative's name,
address, billing
rate, Zodiac birth sign and/or other information, preferably automatically via
a
telephone keypad or via speech recognition. In another embodiment involving
computer service assistance, a service representative may specify expertise in
hardware matters and another service representative may specify expertise in
software
matters.
In an alternative embodiment or in a packetized telephony-based embodiment,
the service representative is equipped with a cathode ray terminal, a printer
or other
display and a full keyboard permitting a written query and response and so the
"announcement" of step 210 may be a written or a displayed announcement. In a
preferred embodiment, however, an exemplary announcement or instructional
display
provided by either embodiment may include: "Press 1 if you wish to serve one
call at
a time by yourself. Press 2 if you wish to confer with a second conferee on
each
incoming call. Press 3 if you wish to confer with two other conferees on each
incoming call requesting service. ... ." and so on. When the service
representative
has a computer mouse, the mouse may be used to input selection criteria.
Flow continues to step 220 where a preference selection is made. Steps 210
and 220 are repeated until log-in is complete. Once the responses to the
queries of
step 210 are registered by DTMF or other data receiver 120 and reported to
controller
110, ARU 135 may provide a validity check for the entered data and provide
audible
feedback for selections. Then, ARU 135 may further request, "Do you have a
preference for the second conferee? If so, enter by pressing keys of the
keypad the
first several letters of the preferred conferee's last name." Of course, a
psychic twin
would enter their own last name and their twin could be immediately identified
via a
memory look-up in memory 115. Audible or visual confirmation/feedback that the
choice has been accepted may be provided, in additional to error algorithms
can be
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/LJS00/30504
provided, as necessary. for correcting an erroneous choice made by a service
representative.
In the log-in process of Figure 2, the various announcements and responses of
steps 210 and 220 can be varied depending on the desired service to be
performed.
Moreover, the result may vary. In one scenario, there may be an availability
queue of
available service representatives willing to confer with a caller individually
or with
other conferees. In other words, the service representative may be willing to
accept
any request for services. In other embodiments, there may be availability
queues
formed in memory 115 for individual service representative calls, dual or
twins calls,
triplets or three service representative calls and so on. Or there may be a
combination
of such queues depending on the embodiment. Consequently, in its simplest
embodiment the present invention involves the service representative logging
in to a
dual service representative availability queue so that upon receiving a call
to a special
dual service representative telephone number, the next two service
representatives
that are available in the dual service representative availability queue are
automatically and connected practically simultaneously to the caller.
The result of the log-in process is shown as step 230, that is, the service
representative is entered into memory 115 in one or more service
representative
availability queues as a memory table. Of course, when a service
representative takes
a call and is connected with a caller (and maybe one or more other service
representative conferees), the appropriate availability table in memory 115
records a
"busy" status for the service representative, as signaled by controller 110.
Moreover,
the service representative has recorded the preferred type of call that the
service
representative is willing to accept (for example, individually, with another
service
representative conferee, and the like) and certain other preferences, such as
their own
Zodiac sign, the day, month, year of birth, gender or other information that
is useful
for arranging a call. Some or all of this information may be preserved in
memory 115
depending on the service offered. Over time, information such as the number,
type,
caller identities, caller preferences and the like of calls handled by each
respective
service representative may be recorded in memory 115 and associated with the
service
16
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
representative for assisting in providing better caller service, and for
providing salary
or other compensation to the service representatives.
Figure 3 shows a flowchart for processing a call received from a circuit-
switched telecommunications network or from a packet-switched computer
network,
such as the Internet, for a service representative according to the present
invention. A
caller may define certain parameters for the ACD (Internet router) system of
Figure 1
to follow when connecting the caller to at least one service representative.
At step
305, a caller to the psychic network service calls an 800 or a 900 telephone
number
for the service bureau on line 110-1 or series of trunks 110-1 and 110-2, or
accesses
the service bureau using an Internet address. A second line or Internet
address or a
series of trunks or Internet addresses may be separately provided for a twins
service.
In such an instance, the caller may be immediately passed to step 320 and the
input
data registered including, but not limited to, the calling telephone number,
address
and billing information of the caller, or Internet address of the caller.
According to the present invention, call limiting, call blocking and fraud
control checking is performed automatically at this stage. For example, call
limiting
criteria may be established for protecting callers against excess usage and
billing,
such as two calls per day, 40 call minutes per day, 50 call minutes per week,
85 call
minutes per month, and/or an amount of money spent by a caller during a
predetermined period of time. A caller is queried in a database for
determining how
frequently and, for each respective call, how long the caller was connected
for
determining whether any individual or combination of the call limiting
criteria have
been exceeded. When any call limiting criteria has been exceeded, the caller
may
receive a message thanking the caller for their previous calls, and possibly
blocking or
limiting the duration of the present call.
Regarding call blocking based on input data and certain negative databases,
the calling telephone number (or Internet address), the first several digits
of the
address or apartment number and/or the zip code of the caller that have been
entered
by way of a telephone keypad may be matched against the calling telephone
number
(obtained via ANI), the originating Internet address (obtained via packetized
data)
and/or credit card data so that a security breach is pre-identified. The
comparison of
17
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/LTS00/30504
the user-entered first several digits of a street address or apartment number
and/or zip
code against credit card data downloaded or prestored from a credit agency or
a bank
is referred to herein as an address verification system (AVS). The caller may
be
asked to explain any discrepancy and/or the call is blocked. The calling
telephone
numbers (obtained via ANI and by caller entry) or Internet addresses (obtained
via
packetized data and by caller entry) can be checked against each other and
against
telephone number/Internet address negative databases that identify pay phones,
prisons, schools, selected commercial establishments, and other institutions
or
locations of telephones or Internet access devices from which calls may be
blocked at
switch (router) 100.
A voiceprint of the caller's voice may be recorded via message unit 135 and
converted to digital form for comparison against a voiceprint database for
insuring the
validity of the identity of the caller. The caller's name may be spelled into
the system
via a telephone or intelligent terminal keypad, and compared against a card-
holder or
account name as a security check. When the caller is making a packet-switched
call,
a voiceprint, a fingerprint image and/or a portrait image can be used for
insuring the
validity of the identity of the caller. At least, via AVS, the address of the
caller,
entered by telephone keypad, can be matched against the address of the card
holder or
on an account that is pre-stored and downloaded from a credit agency or a
bank. In an
alternative embodiment, a non-service representative may assist, supplement or
replace an automated system regarding call limiting, call blocking, fraud
control,
collecting form of payment information and obtaining payment authorization.
At step 325, the caller is identified to be served by at least one service
representative and at step 330 immediately connected to an identified service
representative listed in the availability queue of service. Once it has been
determined
that call blocking, call limiting and fraud control criteria have not been
exceeded, a
caller is immediately connected and served by at least one service
representative listed
in the service representative availability queue.
In a further preferred embodiment of the present invention, steps 310 and 315
performed repeatedly in a manner that is similar to the way the service
representative
logs in, as per Figure 2, until the caller logs in. For example, at step 310,
an
18
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
announcement is played welcoming the caller to the service bureau, such as to
a
psychic network service. When the service representative queue is relatively
full, the
announcement can indicate that the caller's call is important and connection
to a
service representative be momentarily delayed. Based on controller calculated
average call durations and other queuing theory calculations, controller 110
may even
indicate an expected waiting time for the caller and, in the meanwhile, will
begin to
record certain service and service representative preference information.
While the caller is waiting for a service representative, the caller may be
provided with their horoscope or other information of interest to the caller
until a
service representative is available to conduct a session with the caller. For
example, a
caller may enter the month, day and year of birth, their gender and service
preference
(such as one or more service representative conferees). This information may
be used
for providing a personalized horoscope or other information that may be of
interest to
the caller while the caller is waiting for a service representative.
As steps 310 and 315 are repeated, controller 100 variously calls into play
ARU 135, ANI 125 and DTMF receiver/decoder 120, as necessary. Controller 100
may query a database for determining billing arrangements, among other things,
such
as whether the caller has used the service before, how the caller has paid in
the past,
what preferences and data was accumulated at that time, and bring such data
that is
useful for this call to active memory.
Once the call has been accepted and the caller has logged in, the caller's
input
data is registered into active memory 115 at step 320. The registered data may
include, among other things, the caller's name, address, zip code, telephone
number,
credit card type and number, bank name and account number and billing data,
service
preference, and data that may be used for matching the caller with service
representative data. For example, the caller's sign of the Zodiac, determined
from an
entered birth date, or separately entered, may be matched with similar psychic
service
representative information before the call is initiated.
Identification of service representatives at step 325 then may be as simple as
selecting the next available service representative from an availability queue
and
associating the selected service representative with a caller. In a dual
service
19
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
representative call (twin service), the next two available service
representatives are
selected from the availability queue for a call, and so on. Service
representative
selection can be more complicated when, for example, a pair of psychic twins
is
required to be identified and selected. Other criteria for selecting a service
representative can include gender, sign of the Zodiac and other preference
data. In all
such criteria selection and matching of preferences, step 325 is crucial for
obtaining
the best service for a particular caller. A trade-off is that there may not be
as many
available service representatives having desired criteria, so that a delay in
arranging a
call may be lengthened or impossible to accomplish at a particular time.
Announcement 310 may be adaptively used for describing for the caller the real
choices that the caller is able to make at a particular time under control of
controller
110. The caller may be offered additional choices within the same network, or
through prior arrangement with another psychic counseling network service, the
caller
may be transferred to an available psychic representative associated with
another
psychic network service for receiving service.
Once the service representative goes off hook, the caller is billed for the
call.
Consequently, at step 335, all caller and service representative data is
logged in along
with time of day and date for calculating call duration in minutes and for
billing, and
service representative compensation data logging. More specifically, a caller
is billed
for the duration of time beginning when the first service representative goes
off hook
or begins an Internet telephony session until the last service representative
goes on-
hook or terminates the Internet telephony session. Individual time logs are
maintained for the caller (call duration) and each service representative
(service
duration). For example, when the first service representative hangs up, the
system
will update the database with the first service representative's connect time,
time of
day and the date. When the second or final service representative hangs up,
the caller
is billed for the total call time and the second service representative's
connect time,
time of day and date are logged accordingly.
Once the conferees (including the caller) have completed a call, step 340 is
entered. On-hook conditions and the time-of day are registered by controller
110 so
that the duration of the call can be calculated. Each of the service
representatives are
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/tTS00/30504
returned to their respective availability queues until they choose to log off
by
following a log-off process that is complimentary to the log-in process of
Figure 2, or
become unavailable by accepting a service call. Once a service representative
logs in,
controller 110 anticipates that the next call to the service bureau is a log-
off call and
will provide an appropriate sequence of announcements and obtain responses for
logging off. The time of day may be recorded to determine how long the service
representative has been on the job.
When the counseling service is provided for a fee, it is anticipated according
to the principles of the present invention that callers may be offered a
variety of ways
to pay for the services offered. Some methods of payment, such as debit cards,
bank
checks or drafts, smartcards, electronic wallets (e-wallets), and major credit
cards, are
more creditworthy than other methods of payment. Other forms of payment
contemplated by the present invention include billing to a telephone number, a
cable
television account number, a utility service account, or an Internet service
provider
(ISP) account number. A caller enters a preferred form of payment in response
to a
request via ARU unit 135. A caller may receive preauthorization using these
credit
arrangements in real time, even prior to the counseling service and,
consequently,
may realize a discount according to the present invention, which can induce
the caller
to use a method of payment that is preferred by the service vendor. Payment
method
and billing arrangements are typically agreed upon after the call limiting,
call
blocking and fraud control features previously described, and may be agreed
upon in
advance of the call or prior to conclusion of the call. Preferably, such
arrangements
are agreed upon automatically by using message unit 135 and data input 120, as
described above, when modem 140 is used for obtaining the payment
authorization
from a bank or credit agency.
Figure 4 shows a flow diagram for a real-time billing system for circuit-
switched and packet-switched calls in accordance with the principles of the
present
invention. At block 401, the initial fraud control are activated, which can
include
verifying whether the caller is calling from a location that matches the
originating
telephone number of the call, limiting the number and duration of calls made
during a
21
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
certain time period and/or limiting the amount of money a caller spends on
service
representative calls in a predetermined time period.
When a call is received from a circuit-switched telecommunications network,
the system prompts the caller at block 401 to enter the caller's telephone
number to
verify that the caller is calling from a location that matches the telephone
number
from a displayed ANI. When the entered telephone number does not match the
number forwarded by the ANI, the caller may be disconnected or the caller may
be
given another chance to reenter the correct telephone number. When the call is
received from a packet-switched network, the initial fraud control of block
401
verifies that the caller is calling from an Internet address that matches the
Internet
address contained in the packetized telephony data received with the call. The
caller
is similarly prompted to enter the caller's Internet address or a unique
identification
associated with the caller and/or terminal equipment. When the entered
Internet
address (unique identification) and the Internet address (unique
identification)
forwarded in the packetized telephony data do not match, the caller may be
disconnected or the caller may be given another chance to reenter the correct
Internet
address or unique identification.
When the originating telephone number or Internet address (unique
identification) entered by the caller is verified to match the ANI or Internet
address
(unique identification) forwarded with the call, the initial fraud control of
block 401
verifies that the caller's telephone number or Internet address (unique
identification)
is not stored in a negative database of known bad telephone numbers and/or
Internet
addresses (unique identifications). The negative database can be located
locally in
memory 115 or located remotely and accessed via a modem or over the Internet.
Telephone numbers and/or Internet addresses (unique identifications) stored in
the
negative database result from insufficient payment of a telephone bill or a
credit card
charge, or a caller's refusal of payment relating to a disputed charge from a
previous
service representative call. The present invention, however, is not limited by
the
above-mentioned negative database satisfying the criteria mentioned above
(storing
telephone numbers and/or Internet addresses (unique identifications) having
disputed
charges or insufficient payments with respect to a service representative
call). The
22
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
negative database used at this stage of the initial fraud control of the
present invention
may be a shared database that stores telephone numbers and/or Internet
addresses
(unique identifications) of callers who have credit problems with other types
of
telephone and/or Internet-based ordering/payment systems.
The present system also checks to ensure that calls are not made from
locations in which the telephone number and/or an originating Internet address
(unique identification) cannot be forwarded to, for example, a Caller ID or
other
device that displays and/or records the telephone number or Internet address
(unique
identification) of the incoming call. In particular, certain parts of the
United States
cannot read ANIs and calls originating from telephone numbers located in these
areas
are detected by the initial fraud control of block 401. The present invention
is also
capable of detecting calls from particular institutions and communication
devices,
such as cellular telephones, numbers associated with a PBX system,
governmental
facilities, pay telephones, prisons, hospitals, schools, selected commercial
establishments, etc.
The above-described initial fraud controls are illustrative examples. Other
fraud controls will be apparent to those skilled in the art, thus the
invention is not
limited to the fraud controls described above. In general, the system can be
designed
to prevent any unwanted telephone numbers from entering the system.
When the originating telephone number or Internet address (unique
identification) entered by the caller is verified to match the ANI or Internet
address
(unique identification) forwarded with the call and the originating telephone
number
or Internet address (unique identification) is not contained in the negative
database,
the initial fraud control of block 401 checks that the caller has not exceed a
permissible number or duration of calls the caller has made during a
predetermined
period of time, or an amount of money the caller has spent during a
predetermined
period of time by querying a database. For example, a caller may be limited to
only
two calls per day or two calls per week, and the to duration of calls may be
limited so
that a caller is allowed to speak with service representatives for a maximum
of, for
example, 100 minutes per month. The amount of money that a caller can spend
can
be limited to, for example, an expenditure of $100 per month. The database
23
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
containing this type of information can be part of or separate from the
negative
database, and can be a shared database.
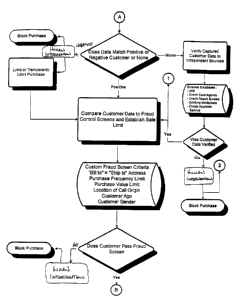
Calls that fail the initial fraud control of block 401 are forwarded to block
410
where the call is processed to determine what the next course of action will
be.
According to the invention, calls can be blocked, temporarily blocked or
limited.
Blocked calls are permanently prohibited from connection with a service
representative. A message may be played for a blocked call that advises the
caller to
stop calling because the calling number or Internet address has been blocked.
Examples of potentially blocked calls include calls from telephone numbers
located in
a negative database or calls from localities where an ANI cannot be forwarded.
Similarly, Internet telephony calls originating from Internet addresses
(unique
identification) that are not properly forwarded with packetized telephony data
can be
blocked calls.
A limited call prohibits a caller who has exceeded an allotted number of
calls,
an allotted duration (in minutes, hour or days) of calls or an allotted
expenditure
amount during a certain period of time from being connected to a service
representative. The limitations placed on a given caller may be removed once
the
caller has satisfied criteria for removing the limitation. A temporarily
blocked calls
can include a call in which a telephone number requested by a service
representative
does not match an ANI number displayed or received packetized telephony data.
The
caller may be able to reenter the correct telephone number or Internet address
(unique
identification), or may be allowed to call again for correctly entering the
caller's
telephone number or Internet address (unique identification). Therefore, the
caller is
temporarily blocked from being connected to a service representative. When any
of
the call limiting, call blocking, or temporarily call blocking features is
activated, the
call is disconnected.
When the call successfully passes the initial fraud control of block 401, the
call then advances to block 402 where the form of payment that will be used to
pay
for the call to a service representative is solicited. The caller is prompted
by, for
example, a computer-activated voice or by an operator (a non-service
representative),
to indicate the form of payment information the caller wishes to use. The form
of
24
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
payment can be cash, debit cards, check or electronic draft, electronic funds
transfer,
credit, major credit card, electronic wallet and the like. For this particular
embodiment of the invention, the preferred form of payment involves credit
cards,
debit cards and the like.
Alternatively, in situations when the caller has previously called into the
service, the form of payment information can be automatically accessed from a
form-
of payment/credit database in a well-known manner based on the ANI and/or
other
information that has been provided by the caller. Preferably, the form-of
payment/credit database is stored locally, but can also be remotely located.
The
previously-used form of payment information stored in the form-of
payment/credit
database is presented to the caller in a well-known manner as .a possible
selection by
the caller for payment of the current call.
The operator or computer-activated voice may offer the caller a discount when
the form of payment selected by the caller is convenient for the billing
system. A
further discount may be given when the caller is a frequent caller who has not
exceeded the caller's allowance for prescribed calls or expenditure amount. Of
course, any other form of preferential treatment may also be initiated. In the
exemplary embodiment described in Figure 4, the caller provides the form of
payment
information to the operator or inputs this information via a telephone keypad
or
keyboard. The caller can be requested to enter or supply information such as
credit
card or debit card numbers, the card expiration date, address including zip
code,
billing address, date of birth, driver's license number, etc. When the form of
payment
is not successfully communicated to the operator or successfully entered by
the caller
via the telephone keypad or keyboard, the call is disconnected. Alternatively,
the
caller may be temporarily blocked and/or given another chance for entering the
correct information. The caller may also be completely blocked from calling
the
system again.
When the information is successfully communicated or entered, flow
continues to block 404 where additional fraud control is implemented. Such
additional fraud control may, for example, include comparing information given
by
the caller against information stored in a database of information related to
each
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
respective caller, and/ or verifying that the caller's credit card or debit
card number
has not been in a negative database for delinquent payment. The information
stored
in this database can be part of or separate from the negative database of call
originating telephone numbers and/or Internet addresses (unique
identifications), and
can be a shared database.
The information entered or communicated by the caller is also used for
determining whether the caller has not exceed a permissible number or duration
of
calls the caller has made during a predetermined period of time, or an amount
of
money the caller has spent during a predetermined period of time by querying a
database. The queried database may be the same database used in step 401 for
determining whether the caller has exceeded any of the same criteria.
When a call fails the additional fraud control of block 404, the call is
forwarded to block 410 where the call can be selectively blocked, temporarily
blocked, or limited. A blocked call includes a call in which a credit card or
debit card
has expired or is invalid. A limited call includes a call in which a credit
card or a
debit card exceeds the monthly/weekly allocations of calls or exceeds the time
allowance for a certain period of time. A temporarily blocked call includes a
call in
which the zip code or other information supplied by the caller does not match
the
appropriate information stored in a database. Moreover, the system can be
designed
so that calls classified as blocked calls can also be classified as
temporarily blocked
calls when the system allows a caller to supply information, such as the
correct
expiration date of a charge card. When the caller is allowed to make payment
to a
lending institution in order to validate the credit or debit card, a call can
be classified
as temporarily blocked.
According to one embodiment of the present invention, when the call passes
the additional fraud control, the credit card account information or the debit
card
account information is forwarded at block 405 to a remote site for
authorization.
Remote sites used for authorization may, for example, include a credit bureau,
a
banking institution, a third-party biller, or the like. The remote site checks
to ensure
that the credit card or debit card is valid. When the card is valid, a
predetermined
amount of money is charged against the credit or debit card account at block
406.
26
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
According to another embodiment of the present invention, when the call passes
the
additional fraud control, the credit card account information or the debit
card account
information is forwarded to a local database to ensure that the credit card or
debit card
is valid. When the card is valid, a predetermined amount of money is charged
against
the credit or debit card account at block 406.
The predetermined amount of money charged against the credit account can be
performed in several ways. For example, a portion of the caller's available
line of
credit for the account equal to the predetermined amount can be authorized or
set
aside for the purpose of making the call. Alternatively, the account may be
debited by
the predetermined amount. In any event, the predetermined amount of money
charged to the account is preferably greater than the probable charge for the
telephone call for insuring that the charges incurred during the call will be
paid.
When the predetermined charge to the account is approved or denied, the remote
site
sends an approval or denial notification back to the system at block 406. When
the
remote site authorizes the call, the call is forwarded to a service
representative, such
as a psychic counselor. When the call is not authorized, the call is either
blocked or
temporarily blocked until information regarding the credit bureau or the
banking
institution is settled by the caller.
At block 407, the call is redirected to a service representative and, at this
point, the billing processes begin, as shown in block 408. The call is billed
from the
time the call is redirected to one or more service representatives and to the
time when
the last service representative hangs up. The caller is billed in real time
for only the
actual minutes that the caller is connected to a service representative.
When the call is terminated, the system calculates the total billable amount
for
the call. The system then sends the billable amount to the remote site at
block 410.
The system can also send the credit card or debit card account information or
some
other identifying information along with the billable amount to the remote
site. The
remote site then reverses the previous charge of the predetermined amount to
the
account and a new charge for the actual billable amount of the call is charged
to the
account at block 408.
27
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
This reverse authorization routine can be performed in several ways and the
invention is not limited to the following examples. First, the initial
authorization to
set aside the predetermined amount of available credit is reversed, thereby
returning
the amount that was set aside to the available credit line. A second
authorization is
then performed wherein a portion of the available credit line that is equal to
the actual
cost of the call is set aside. In another embodiment of the invention, the
account may
receive a credit in the amount of the predetermined amount to negate the
initial charge
of the predetermined amount. A new charge in the amount of the actual cost of
the
call is then made to the credit card account. Alternatively, the account may
just
receive a credit in the amount of the difference of the predetermined amount
initially
set aside minus the actual billable amount of the call. Furthermore, when the
caller is
not connected to a service representative and the billing has not begun before
the call
is terminated, the caller is not charged for the call and the initial charge
is completely
reversed. When the credit account information relates to a checking account or
an
electronic funds transfer, the reverse authorization feature of the present
invention is,
of course, not used.
The present invention is adaptable for providing video conferencing services
to callers equipped with video cameras. Moreover, the service representatives
may
not necessarily need to depend on central controller 110 for database
maintenance
services regarding caller and service representative data. Such data may be
maintained and updated within personal computers at the service
representative's
premises. Other modifications and enhancements to the present invention may be
adaptively made for providing other services than that described, such as
medical
counseling, suicide hot-line and other services.
The present invention also provides for a call-out feature in which selected
callers are called by the system in a well-known manner. Once the call has
been
connected to the caller, message unit 135 plays an announcement for the call
recipient
offering services and/or goods that can be accepted. If the offer of services
and/or
goods is accepted by the call recipient, message unit 135 provides audio
prompts
querying the call recipient for a form of payment. Accordingly, a previously-
used
form of payment can be accessed from a form-of payment/credit database for
28
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
providing a possible selection by the call recipient. The fraud control
features of the
present invention can optionally be used in conjunction with the querying for
the form
of payment Accessing the form-of payment database When the form of payment is
selected, the fraud controls relating to the form of payment provided by the
present
invention are then initiated before the services and/or goods are delivered.
Figure 5 shows a schematic block diagram of a system 500 for billing a
communication session conducted over a packetized digital data computer
network
501, such as the Internet, according to the present invention. In Figure 5, a
plurality
of Internet Service Providers (ISPs) 502 are connected to the Internet 501 for
providing access to the Internet 501 and to resources connected to the
Internet 501.
Each of a plurality of user terminals 503 are connected to the Internet 501
through an
ISP 502. Typically, a user terminal 503 uses an automatic dialing modem to
create a
circuit-switched data link to an ISP 502. Alternatively, a user terminal 503
can access
an ISP 502 through a cable link or a high-speed digital link. The ISP, in
turn, creates
a packet-switched data link to a desired address over the Internet 502 in a
well-known
manner. A plurality of servers, which may comprise routers, are also connected
to the
Internet 501 for providing access to web pages and other data in a well-known
manner. Only three such servers 504, 505 and 506 are shown in Figure 5 for
clarity.
Server 504 is connected to a computer system 507 that is used for providing a
service representative-based service, for example, a psychic counseling
network
service. Other computer systems (not shown) can also be connected to server
504.
Preferably, though, computer system 507 is the only computer system connected
to
the Internet 501 through a server 504 so that users requesting service receive
an
optimum level of performance. A plurality of service representative terminals
508
can be connected locally to computer system 507 so that service
representatives can
interface with users for counseling communication sessions from a centrally-
located
place. Additionally or in the alternative, a service representative can be
located
remotely from computer system 507 through a link over the Internet 501. For
example, user terminals 503a and 503b can be operated by service
representatives that
are associated with the representative-based service provided through computer
system 507 in a manner that appears to be transparent to users requesting
service.
29
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/CTS00/30504
Figure 6 shows a flowchart for actuating and entering a service representative
into a service representative availability queue using a communication session
over a
computer network according to the present invention. Such a communication
session
can be a data-only session or a multimedia session that includes any
combination of
audio, video and data. At step 600, a service representative contacts the
service
bureau at computer system 507 over the Internet 501 for indicating an
availability for
providing service. At step 610, the service representative receives a log-on
page
requesting, for example, the service representative to identify certain
choices and
preferences for recording in memory of system 507 that are similar to the
choices
presented in connection with the logging in sequence of Figure 2. Preferences
may be
predetermined or entered for the first time, such as the name and address of
the
service representative, billing rate, Zodiac birth sign and/or other
information.
Typically, at this time, a time of day and date is recorded in the memory of
system
507 logging the time and date the service representative has offered to begin
servicing
users. When the service representative is directly connected to computer
system 507,
the service representative need only to initiate a log-on procedure, as
opposed to
logging into an ISP and initiating a communication session with system 507.
Flow continues to step 620 where the service representative enters a
preference selection and sends the preference selection information to system
507.
Steps 610 and 620 are repeated until log-in is complete. Once the responses to
the
queries of step 610 are registered, system 507 may provide a validity check
for the
entered data, and provide an audible and/or visual feedback for selections.
System
507 may then send additional log-in query pages, such as whether the service
representative desires to work with one or more conferees. Feedback
connrmation
that the choices have been accepted by system 507 may be provided in addition
to
error algorithms provided for correcting erroneous choices made by a service
representative, as necessary.
In the log-in process of Figure 6, the various query pages and responses of
steps 610 and 620 can be varied depending on the desired service that is to be
performed. Moreover, the result may vary. In one scenario, there may be an
availability queue of available service representatives willing to confer with
a user
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
individually, with other conferees or in a chatroom-type of setting. In other
words,
the service representative may be willing to accept any request for services.
In other
embodiments, there may be availability queues formed in the memory of system
507
for individual service representative communication session, dual or twins
communication sessions, triplets or three service representative communication
sessions, and so on. There may be a combination of such queues depending on
the
embodiment. Consequently, in its simplest embodiment, the present invention
involves the service representative logging in to a dual service
representative
availability queue such that on receiving a request for a communication
session at a
special dual service representative website or web page, the next two service
representatives that are presently available in the dual. service
representative
availability queue are automatically connected to the user.
The result of the log-in process is shown as step 630, that is, the service
representative is entered into the memory of system 507 in one or more service
representative availability queues as a memory table. Of course, when a
service
representative accepts a communication session and is connected with a user,
and
perhaps one or more other service representative conferees, the appropriate
availability table in the memory of system 507 records a "busy" status for the
service
representative. Moreover, the service representative has signaled and recorded
their
preferences for the type of communication session that the service
representative is
willing to accept (for example, individually, with one or more service
representative
conferees or in a chatroom-type environment) and certain other preferences,
for
example, their own Zodiac sign, the day, month, year of birth, gender or other
information that is useful for arranging a communication session. Some or all
of this
information depending on the service offered may be preserved in the memory of
system 507. Over time, information such as the number, type, user identities,
user
preferences and the like of communication sessions accepted by each respective
service representative may be recorded and associated with the service
representative
for assisting in providing better user service, and for providing salary or
other
compensation to the service representatives.
31
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
Figure 7 shows a flowchart for processing a service representative
communication session, whether a data-only session or a multimedia session,
according to the present invention. Such a communication session can be a data-
only
session or a multimedia session that includes any combination of audio, video
and
data. At step 705, a potential user of the service bureau provided at computer
system
507 accesses a log-in page at the service bureau web address. A second web
address
or series of web pages may be separately provided for accessing a twins
service. In
such an instance, the user may be immediately passed to step 720 and the input
data
registered including, but not limited to, the Internet address of the user,
the physical
address and billing information of the user.
According to the present invention, communication session limiting, session
blocking and fraud control checking is performed automatically at step 710.
For
example, arbitrary communication session limiting criteria may be established,
such
as two sessions per day, 40 session minutes per day, 50 session minutes per
week, 85
session minutes per month and/or an amount of money spent by a user during a
predetermined period of time for communication session services for protecting
user
against excess usage and billing. A user is queried in a database for
determining how
frequently and, for each session, how long the user has been connected for
determining whether any individual or combination of session limiting criteria
have
been exceeded. When any session limiting criteria has been exceeded, the user
may
receive a message thanking the user for past sessions, but possibly blocking
or
limiting the duration of the present session.
Regarding session blocking based on input data and certain negative
databases, the Internet address initiating the session, the first several
digits of the
address or apartment number and/or the zip code of the user that have been
entered by
the user may be matched against the Internet address (obtained via packetized
data
when the session is initiated) and/or credit card data so that a security
breach is pre-
identified. The comparison of the user-entered first several digits of a
street address
or apartment number, and/or zip code against credit card data downloaded or
prestored from a credit agency or a bank is an address verification system
(AVS).
The user may be queried to explain any discrepancy and/or the session is
blocked.
32
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
The Internet address (or other unique address) from where the session is
initiated
(obtained via packetized data) can be checked against the Internet address (or
unique
address) entered by the user and against Internet address and telephone
negative
databases identifying pay phones, prisons, schools, selected commercial
establishments, and other institutions or locations of terminals and/or
telephones from
where communication sessions may be blocked.
If the session is a multimedia session involving voice communications, a
voiceprint of the user's voice may be recorded by system 507 for comparison
against a
voiceprint database for insuring the validity of the identity of the user. The
user's
name may be input and compared against a card-holder or account name as a
security
check. Additionally, a fingerprint image and/or a portrait .image can be used
for
insuring the validity of the identity of the caller. At least, via AVS, the
address of the
user, entered through a keyboard, can be matched against the address of the
cardholder or on an account that is pre-stored and downloaded from a credit
agency or
a bank 511. In an alternative embodiment, a non-service representative may
assist,
supplement or replace an automated system in regard to session limiting,
session
blocking, fraud control, collecting form of payment information and obtaining
payment authorization.
At step 725, the user is identified to be served by at least one service
representative and at step 730 immediately connected to an identified service
representative listed in the availability queue of service for the type of
service
requested by the user, such as an individual service representative
consultation, a
consultation with a plurality of service representatives, a chatroom
environment, etc.
Once session blocking, session limiting and fraud control criteria have not
been
exceeded, a user is immediately connected and served by at least one service
representative listed in the service representative availability queue.
In a further embodiment of the present invention, steps 710 and 715 are
repeatedly performed until the user logs in a manner that is similar to the
way the
service representative logs in using a communication session, as per Figure 6.
For
example, at step 710, a welcome announcement to the psychic network service is
sent
to the user. When the service representative queue is relatively full, the
33
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
announcement may indicate that the user session is important and connection to
a
service representative be momentarily delayed. Based on a calculated average
session
durations and other queuing theory calculations, system 507 may send a message
indicating an expected waiting time for the user and, in the meanwhile, will
begin to
record certain other service and service representative preference
information. For
example, as with the telephony-based embodiment of the present invention of
Figures
1-4, a user may enter the month, day and year of birth, their gender and
service
preference (such as one or more service representative conferees, or a
chatroom
environment).
As steps 710 and 715 are repeated, system 507 may query a database for
determining billing arrangements, among other things, such as whether the user
has
used the service before, how the user has paid in the past, what preferences
and data
was accumulated at that time, and bring such data that is useful for the
session to
active memory.
Once the communication session has been accepted and the user has logged in,
of course, the user's input data is registered into the memory of system 507
at step
720. The registered data may include, among other things, the user's name,
address,
zip code, telephone number, credit card type and number, bank name and account
number and billing data, service preference, and data that may be used for
matching
the user with service representative data. For example, the user's sign of the
Zodiac,
determined from an entered birth date or entered separately may be matched
with
similar psychic service representative information before the session is
initiated.
When the service representative queue is relatively full and/or when a user
must wait to connect to a particular service representative, system 507 can
send pages
of information to the user that have been customized for the user or may be of
interest
to the user. For example, while a user is waiting, horoscope information or an
astrological chart (personalized for the user based on data input by the user)
can be
sent to the user for the user's information and entertainment. Another example
is to
send marketing information, such as a information regarding products and/or
services
available from the service bureau, to the user so that the user is entertained
while
waiting for a service representative.
34
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
Identification of service representatives step 725 then may be as simple as
selecting the next available service representative in an availability queue
and
associating the selected service representative with a user. In a dual service
representative session (twin service), the next two available service
representatives
are selected from the availability queue for a session, and so on. Service
representative selection can be more complicated when a pair of psychic twins
is
required to be identified and selected. Other criteria can include gender,
sign of the
Zodiac and other preference data. In all such criteria selection and matching
of
preferences, step 725 is crucial for obtaining the best service for a
particular user. A
trade-off is that there may not be as many available service representatives
having
desired criteria, so that a delay in arranging a session may be lengthened or
impossible to accomplish at a given time. The announcement message of step 710
may be adaptively used for describing for the user the real choices the user
is able to
make at a particular time. The user may be offered additional choices within
the same
network, or through prior arrangement with another psychic counseling network
service, the user may be transferred to an available psychic representative
associated
with another psychic network service for receiving service. Further, system
507 can,
as previously mentioned, send pages of information to the user that have been
personalized for the user or may be of interest to the user, such as
horoscope,
astrological and/or information regarding other products and services that are
available. When the selected service representatives) is (are) available,
system 507
connects the user to the service representative(s).
Once all of the selected service representatives are connected to the session,
the user is billed for the session. Consequently, at step 735, all user and
service
representative data is transmitted to system 507 and logged in along with time
of day
and date for calculating session duration in minutes and for billing, and
service
representative compensation data logging. Specifically, a user is billed for
the
duration of time beginning when the first service representative goes is
connected to
the session until the last service representative terminates the session.
Individual time
logs are maintained for the user (session duration) and each service
representative
(service duration). For example, when each service representative disconnects
or
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/L1S00/30504
terminates from the session, the respective service representative's terminals
transmit
the service representative's connect time, disconnect time, time of day and
date to
system 507. In the situation when a user connects to a chatroom environment,
the
user is billed for the duration of time when the user first connects to the
chatroom
until the time the user disconnects from the chatroom.
Once the conferees (including the users) have completed a session, step 740 is
entered and a total time for the communication session is determined for
billing the
user accordingly. Each of the service representatives are returned to their
respective
availability queues until they choose to log off by following a log-off
process that is
complimentary to the log-in process of Figure 6, or become unavailable by
accepting
a service session. Once a service representative logs in, system 507
anticipates that
the next communication session to the service bureau from the service
representative
is a log-off session and will provide an appropriate sequence of announcements
and
obtain responses for logging off. The time of day may be recorded for
determining
how long the service representative has been on the job.
When the counseling service is provided for a fee, it is anticipated according
to the present invention that users will be offered a variety of ways to pay
for the
services offered. Some methods of payment, such as debit cards, bank checks or
drafts, smartcards, electronic wallets, and major credit cards are more
creditworthy
than other methods of payment. Other forms of payment contemplated by the
present
invention include billing to a telephone number, a cable television account
number, a
utility service account, or an Internet service provider (ISP) account number.
A user
enters a preferred form of payment in response to a query from system 507. A
user
may receive preauthorization using these credit arrangements in real time,
even prior
to the counseling service and, consequently, may realize a discount according
to the
present invention that can induce the user to use a method of payment that is
preferred
by the service vendor. Payment method and billing arrangements are typically
agreed
upon after the session limiting, session blocking and fraud control features
previously
described, and may be agreed upon in advance of the session or prior to
conclusion of
the session.
36
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
Figure 8 shows a flow diagram for a real-time billing system for billing a
communication session occurring over a computer network according to the
present
invention. Such a communication session can be a data-only session or a
multimedia
session that includes any combination of audio, video and data. At block 801,
the
initial fraud control are activated, which can include verifying whether the
user is
requesting a communication session from a location that matches the
originating
Internet address and/or a unique identification requesting the session,
limiting the
number and duration of sessions made during a certain time period and/or
limiting the
amount of money a user spends on service representative communication sessions
in a
predetermined time period.
When a request for a session is received from a user, the system prompts the
user at block 801 to enter the user's Internet address or a unique
identification to
verify that the user is requesting a session from a location that matches the
user's
Internet address or unique identification associated with the user and/or
terminal
equipment received with the request for a session. When the entered Internet
address
or unique identification, and the Internet address or unique identification
forwarded in
the packetized data do not match, the user may be disconnected or the user may
be
given another chance to reenter the correct Internet address or unique
identification.
When the originating Internet address or unique identification entered by the
user is verified to match the Internet address or unique identification
forwarded with
the request, the initial fraud control of block 801 verifies that the user's
Internet
address or unique identification is not stored in a negative database of known
bad
Internet addresses and/or unique identifications. The negative database can be
located
in the memory of system 507, and/or remotely located at 509 and accessed over
the
Internet 501 through server 505. Internet addresses and/or unique
identifications
stored in the negative database result from insufficient payment of a credit
card
charge, or a user's refusal of payment relating to a disputed charge from a
previous
service representative communication session. The present invention, however,
is not
limited by the above-mentioned negative database satisfying the criteria
mentioned
above (storing Internet addresses and/or unique identifications having
disputed
charges or insufficient payments with respect to a service representative
session). The
37
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
negative database used at this stage of the initial fraud control of the
present invention
may be a shared database that stores Internet addresses and/or unique
identifications
of users who have credit problems with other types of Internet-based
ordering/payment systems.
System 507 also checks to ensure that sessions are not initiated from
locations
in which an Internet address or a unique identification cannot be forwarded.
System
507 is also capable of detecting a communication session initiated from
particular
institutions and communication devices, such as cellular telephones, numbers
associated with a PBX system, governmental facilities, pay telephones,
prisons,
hospitals, schools, selected commercial establishments, etc.
The above-described initial fraud controls are illustrative examples. Other
fraud controls will be apparent to those skilled in the art, thus the
invention is not
limited to the fraud controls described above. In general, the system can be
designed
to prevent any unwanted Internet addresses and/or unique identifications from
entering the system.
When the originating Internet address or unique identification entered by the
user is verified to match the Internet address or unique identification
forwarded with
the session request, and the originating Internet address or unique
identification is not
contained in the negative database, the initial fraud control of block 801
checks that
the user has not exceed a permissible number or duration of sessions the user
has
made during a predetermined period of time, or an amount of money the user has
spent during a predetermined period of time by querying a database. For
example, a
user may be limited to only two sessions per day or two sessions per week, and
the
duration of 'sessions may be limited so that a user is allowed to communicate
with
service representatives for a maximum of, for example, 100 minutes per month.
The
amount of money that a user can spend can be limited to, for example, an
expenditure
of $100 per month. The query can be based on identification information
associated
with the user, such as the Internet address of the user, a unique
identification of the
user, a driver's license and/or social security number of the user, the user's
mother's
maiden name, a password and/or a digital certificate associated with the user.
The
38
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
database containing this type of information can be part of or separate from
the
negative database, and can be a shared database.
Sessions that fail the initial fraud control of block 801 are forwarded to
block
810 where the session is processed to determine what the next course of action
will
be. According to the invention, sessions can be blocked, temporarily blocked
or
limited. Blocked sessions are permanently prohibited from connection with a
service
representative. A message may be sent to a user for a blocked session that
advises the
user to stop requesting a session because the originating Internet address or
unique
identification has been blocked. Examples of potentially blocked sessions
include
sessions originating from Internet addresses and/or unique identifications
that are not
properly forwarded with packetized data.
A limited session prohibits a user who has exceeded an allotted number of
sessions, an allotted duration (in minutes, hour or days) of sessions or an
allotted
expenditure amount during a certain period of time from being connected to a
service
representative. The limitations placed on a given user may be removed once the
user
has satisfied criteria for removing the limitation. A temporarily blocked
session can
include a session in which an Internet address or a unique identification does
not
match the received packetized data when the session is requested. The user may
be
able to reenter the correct Internet address or unique identification, or may
be allowed
to request another session for correctly entering the user's Internet address,
unique
identification of other user identification information. Therefore, the user
is
temporarily blocked from being connected to a service representative. When any
of
the session limiting, session blocking, or temporary session blocking features
is
activated, the request is terminated.
When the session successfully passes the initial fraud control of block 801,
the
session then advances to block 802 where the form of payment that will be used
to
pay for the session to a service representative is solicited. At step 802, the
user is
prompted by, for example, a page that queries the user for the form of payment
information the user wishes to use. The form of payment can be cash, debit
cards,
electronic draft or check, electronic funds transfer, credit, major credit
card, electronic
39
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
wallet and the like. This embodiment of the invention, however, involves
credit
cards, debit cards and the like.
Alternatively, in situations when the user has previously accessed the
service,
the form of payment information can be automatically accessed from a form-of
payment/credit database in a well-known manner based on the user
identification
and/or other information that has been provided by the user or through other
well-
known techniques, such as a cookie. Preferably, the form-of payment/credit
database
is stored locally, but can also be remotely located. The previously-used form
of
payment information stored in the form of payment/credit database is presented
to the
user in a well-known manner as a possible selection by the user for payment of
the
current session.
System 507 may offer the user a discount when the form of payment selected
by the user is convenient for the billing system. A further discount may be
given
when the user is a frequent user who has not exceeded the user's allowance for
prescribed sessions. Any other form of preferable treatment may also be
initiated. In
the exemplary embodiment described in Figure 8, the user provides the form of
payment information and sends the information to system 507 in a well-known
manner. The user can also be requested to enter or supply information, such as
a
checking account number, credit card or debit card numbers, the card
expiration date,
address including zip code, billing address, date of birth, driver's license
number,
social security number, a password, a digital certificate, mother's maiden
name, etc.
When the form of payment is not successfully communicated to system 507 by the
user, the session is disconnected. Alternatively, the user may be temporarily
blocked
and/or given another chance for entering the correct information. The user may
also
be completely blocked from accessing system 507 again.
When the information is successfully communicated or entered, flow
continues to block 804 where additional fraud control is implemented. Such
additional fraud control may, for example, include comparing information given
by
the user against information stored in a database of information related to
each
respective user, and/or verifying that the user's credit card or debit card
number has
not been in a negative database for delinquent payment. The information stored
in
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
this database can be part of or separate from the negative database of call
originating
Internet addresses and/or unique identifications, and can be a shared
database.
The information entered or communicated by the user is also used for
determining whether the user has not exceeded a permissible number or duration
of
sessions the user has initiated during a predetermined period of time, or an
amount of
money the user has spent during a predetermined period of time by querying a
database. The queried database may be the same database used in step 801 for
determining whether the user has exceeded any of the same criteria.
When a session fails the additional fraud control of block 804, the session is
forwarded to block 810 where the session can be selectively blocked,
temporarily
blocked, or limited. A blocked session includes a session in which a credit
card or
debit card has expired or is invalid, and/or an address associated with the
user, such as
a billing address and/or zip code, is different from an address in the
database
associated with the user. A limited session includes a session in which a
credit card
or a debit card exceeds the monthly/weekly allocations of session or exceeds
the time
allowance for a certain period of time. A temporarily blocked session includes
a
session in which the zip code or other information supplied by the user does
not
match the appropriate information stored in a database. Moreover, the system
can be
designed so that sessions classified as blocked sessions can also be
classified as
temporarily blocked sessions when the system allows a user to supply
information,
such as the correct expiration date of a charge card. When the user is allowed
to make
payment to a lending institution in order to validate the credit or debit
card, a call can
be classified as temporarily blocked.
According to one embodiment of the invention, when the session passes the
additional fraud control, the credit card account information or the debit
card account
information is forwarded at block 805 to a remotely located site 511 for
authorization.
Site 511 can be accessed over the Internet through server 506. Alternatively,
site 511
can be accessed via a modem link 512. Remote sites used for authorization may,
for
example, include a credit bureau, a banking institution, a third party biller
such as a
telephone service provider, a cable television service provider, a utility
service
provider, or an Internet service provider, or the like. Remote site 511 checks
to
41
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
ensure that the credit card, debit card or account number is valid. In the
situation of a
credit card, when the credit card is valid, a predetermined amount of money is
charged against the credit or debit card account at block 806. According to
another
embodiment of the present invention, when the session passes the additional
fraud
control, the credit card account information or the debit card account
information is
forwarded to a local database to ensure that the credit card or debit card is
valid.
When the card is valid, a predetermined amount of money is charged against the
credit or debit card account at block 806.
The predetermined amount of money charged against the credit account can be
performed in several ways. For example, a portion of the user's available line
of
credit for the account equal to the predetermined amount can be authorized or
set
aside for the purpose of completing the session. Alternatively, the account
may be
debited by the predetermined amount. In any event, the predetermined amount of
money charged to the account is preferably greater than the probable charge
for the
telephone call for insuring that the charges incurred during the call will be
paid.
When the predetermined charge to the account is approved or denied, remote
site 511
sends an approval or denial notification back to system 507 at block 806. When
remote site S 11 authorizes the session, the session is forwarded to a service
representative, such as a psychic counselor. When the session is not
authorized, the
session is either blocked or temporarily blocked until information regarding,
for
example, the credit bureau, banking institution, telephone service account,
cable
television account, a utility service account, or Internet service provider
account is
settled by the user.
At block 807, the session is redirected to a service representative and at
this
point, the billing processes begin, as shown in block 808. The session is
billed from
the time the session is redirected and connected to a service representative
or the first
of a plurality of service representatives and to when the last service
representative
terminates or ends the session. The user is billed in real time for only the
actual
minutes that the user communicates with a service representative. When the
user is
connected to a chatroom environment, the user is billed from the time that the
user is
connected to the chatroom until the time the user disconnects from the
chatroom.
42
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
When the session is terminated, system 507 calculates the total billable
amount for the session. System 507 then sends the billable amount to remote
site 511
at block 810. System 507 can also send the credit card or debit card account
information or some other identifying information along with the billable
amount to
remote site 511. Remote site 511 then reverses the previous charge of the
predetermined amount to the account and a new charge for the actual billable
amount
of the session is charged to the account at block 808. Alternatively, the
billable
amount is sent to a payment authorization database, which can be locally or
remotely
located.
As with the voice-based embodiment of the present invention, the reverse
authorization routine for the computer network-based embodiment of the present
invention can be performed in several ways and the invention is not limited to
the
following examples. First, the initial authorization to set aside the
predetermined
amount of available credit is reversed, thereby returning the amount that was
set aside
to the available credit line. A second authorization is then performed wherein
a
portion of the available credit line that is equal to the actual cost of the
session is set
aside. In another embodiment of the invention, the account may receive a
credit in
the amount of the predetermined amount to negate the initial charge of the
predetermined amount. A new charge in the amount of the actual cost of the
session
is then made to the credit card account. Alternatively, the account may just
receive a
credit in the amount of the difference of the predetermined amount initially
set aside
minus the actual billable amount of the session. Furthermore, when a user is
not
connected to a service representative and the billing has not begun before the
session
is terminated, the user is not charged for the session and the initial charge
is
completely reversed. When the credit account information relates to a checking
account or an electronic funds transfer, the reverse authorization feature of
the present
invention is, of course, not used.
As indicated, the present invention is adaptable for providing multimedia-
based conferencing services between users and service representatives that are
appropriately equipped. Moreover, the service representatives may not
necessarily
need to depend on system 507 for database maintenance services regarding user
and
43
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
service representative data. Such data may be maintained and updated within
personal computers at the service representative's premises.
The present invention also provides for a feature in which selected users are
contacted by the system in a well-known manner, such as by e-mail, offering
services
and/or goods that can be accepted. Alternatively, a selected user can be
contacted by
way of a multimedia technique in which particular services and/or goods are
offered
for purchase. If the offer of services and/or goods is accepted by the user,
the system
provides audio prompts querying the user for a form of payment. Accordingly, a
previously-used form of payment can be accessed from a form-of payment/credit
database and provided as a possible selection by the user. The fraud control
features
of the present invention can optionally be used in conjunction with the
querying for
the form of payment.
The fraud control of the present invention can also be used for other forms of
e-commerce over a computer network, such as the Internet. Goods and/or other
services can be made available for sale to potential customers who access a
website
using a browser or by way of computer-network telephony techniques. When a
user
accesses a website using a browser, the ISP through which the user is
connecting to
the website forwards the Internet address of the user to the accessed website.
That is,
identification information uniquely-identifying the user is available to the
accessed
website. Alternatively, a mechanism referred to as a cookie can be used for
transmitting information between the accessed website and the user that is
used for
uniquely identifying the user.
A user can browse through different pages at the website and select items for
purchase by, for example, placing the items into a virtual shopping cart. Once
a user
decides to buy the selected items, the user clicks on a purchase button. In
response,
system 507 enters the fraud control process shown in Figure 9 and queries the
user for
the information necessary for avoiding fraud. Figure 9 shows a flow diagram
for a
real-time billing system for effecting a sale over a computer network
according to the
present invention. According to the invention, the entire flow diagram or
selected
aspects of the embodiment shown by Figure 9 can be used.
44
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
For an e-commerce embodiment of the present invention, the initial fraud
control activated at block 901 can include verifying whether the user is
purchasing a
good and/or service from a location that matches the originating Internet
address
and/or has a unique identification, and/or limiting a sale amount that can be
purchased
during a certain time period. When a purchase request is received from a user,
the
system prompts the user at block 901 to enter the user's Internet address or a
unique
identification to verify that the user is making a purchase from a location
that matches
the user's Internet address or unique identification associated with the user
and/or
terminal equipment received with the purchase request. When the entered
Internet
address or unique identification, and the Internet address or unique
identification
forwarded in the packetized data do not match, the user may .be disconnected
or the
user may be given another chance to reenter the correct Internet address or
unique
identification. Alternatively, a cookie can be used in a well-known manner for
gathering specific information that can be used for uniquely identifying a
user. In
such a situation, the user is then prompted at block 901 to enter information
that can
be compared to information gathered by use of a cookie.
When the originating Internet address or unique identification entered by the
user is verified to match the Internet address or unique identification
forwarded with
the request, the initial fraud control of block 901 also verifies that the
user's Internet
address or unique identification is not stored in a negative database of known
bad
Internet addresses and/or unique identifications. The negative database can be
located
in the memory of system 507, and/or remotely located at 509 and accessed over
the
Internet 501 through server 505. Internet addresses and/or unique
identifications
stored in the negative database result from insufficient payment of a credit
card
charge, or a user's refusal of payment relating to a disputed charge from a
previous
purchase of a product and/or service. The present invention, however, is not
limited
by the above-mentioned negative database satisfying the criteria mentioned
above
(storing Internet addresses and/or unique identifications having disputed
charges or
insufficient payments with respect to the purchase of a product and/or
service). The
negative database used at this stage of the initial fraud control of the
present invention
may be a shared database that stores Internet addresses and/or unique
identifications
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
of users who have credit problems with other types of Internet-based
ordering/payment systems.
System 507 also checks to ensure that purchase requests are not initiated from
locations in which an Internet address or a unique identification cannot be or
is not
forwarded. System 507 is also capable of detecting a communication session
initiated
from particular institutions and communication devices, such as cellular
telephones,
numbers associated with a PBX system, governmental facilities, pay telephones,
prisons, hospitals, schools, selected commercial establishments, etc.
The above-described initial fraud controls are illustrative examples. Other
fraud controls will be apparent to those skilled in the art, thus the
invention is not
limited to the fraud controls described above. In general, the system can be
designed
to prevent any unwanted Internet addresses andlor unique identifications from
making
purchases.
When the originating Internet address or unique identification entered by the
user is verified to match the Internet address or unique identification
forwarded with
the purchase request, and the originating Internet address or unique
identification is
not contained in the negative database, the initial fraud control of block 901
checks
that the user has not exceed a permissible amount of money the user has spent
during
a predetermined period of time by querying a database. The amount of money
that a
user can spend can be limited to, for example, an expenditure of $100 per
month. The
query can be based on identification information associated with the user,
such as the
Internet address of the user, a unique identification of the user, a driver's
license
and/or social security number of the user, the user's mother's maiden name, a
password and/or a digital certificate associated with the user. The database
containing
this type of information can be part of or separate from the negative
database, and can
be a shared database.
Purchase requests that fail the initial fraud control of block 901 are
forwarded
to block 910 where the purchase request is processed to determine what the
next
course of action will be. According to the invention, purchases can be
blocked,
temporarily blocked or limited. Blocked purchases are permanently prohibited
from
completing a sale transaction. A message may be sent to a user for a blocked
46
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
purchase request that advises the user to stop requesting a purchase because
the
originating Internet address or unique identification has been blocked.
Examples of
potentially blocked purchases include sessions originating from Internet
addresses
and/or unique identifications that are not properly forwarded with packetized
data.
A limited purchase prohibits a user who has exceeded an allotted expenditure
amount during a certain period of time from making a purchase. The limitations
placed on a given user may be removed once the user has satisfied criteria for
removing the limitation. A temporarily blocked purchase request can include a
purchase request in which an Internet address or a unique identification does
not
match the received packetized data when the purchase is requested. The user
may be
able to reenter the correct Internet address or unique identification, or may
be allowed
to request another purchase for correctly entering the user's Internet
address, unique
identification of other user identification information. Therefore, the user
is
temporarily blocked from being connected from making a purchase. When any of
the
purchase request limiting, purchase request blocking, or temporary purchase
request
blocking features is activated, the request is terminated.
When the purchase request successfully passes the initial fraud control of
block 901, the purchase request then advances to block 902 where the form of
payment that will be used to pay for the purchase is solicited. At step 902,
the user is
prompted by, for example, a page that queries the user for the form of payment
information the user wishes to use. The form of payment can be cash, debit
cards,
electronic draft or check, electronic funds transfer, credit, major credit
card, smart
card, electronic wallet, and the like, or applying the charge to a telephone
bill, a cable
television account, a utility service account, an Internet service provider
account, and
the like.
System 507 may offer the user a discount when the form of payment selected
by the user is convenient for the billing system. A further discount may be
given
when the user is a frequent user who has not exceeded the user's allowance for
prescribed purchases. Any other form of preferable treatment may also be
initiated.
In the exemplary embodiment described in Figure 9, the user provides the form
of
payment information and sends the information to system 507 in a well-known
47
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
manner. The user can also be requested to enter or supply information, such as
a
checking account number, a credit card or debit card numbers, a card
expiration date,
a telephone number, a cable television account number, a utility service
account
number, an Internet service provider account number, an address including zip
code,
billing address, date of birth, driver's license number, social security
number, a
password, a digital certificate, mother's maiden name, etc. When the form of
payment is not successfully communicated to system 507 by the user, the
purchase
request is disconnected. Alternatively, the user may be temporarily blocked
and/or
given another chance for entering the correct information. The user may also
be
completely blocked from accessing system 507 again.
When the information is successfully communicated or entered, flow
continues to block 904 where additional fraud controls are implemented. Such
additional fraud controls may, for example, include comparing information
given by
the user against information stored in a database of information related to
each
respective user, verifying that the user's credit card or debit card number
has not been
in a negative database for delinquent payment. The information stored in this
database can be part of or separate from the negative database of
communication
session originating Internet addresses and/or unique identifications, and can
be a
shared database.
The information entered or communicated by the user is also used for
determining whether the user has not exceeded a permissible amount of money
the
user has spent during a predetermined period of time by querying a database.
The
queried database may be the same database used in step 901 for determining
whether
the user has 'exceeded any of the same criteria.
When a purchase request fails the additional fraud control of block 904, the
purchase request is forwarded to block 910 where the purchase can be
selectively
blocked, temporarily blocked, or limited. A blocked purchase request includes
a
purchase request in which a credit card or debit card has expired or is
invalid, and/or
an address associated with the user, such as a billing address and/or zip
code, is
different from an address in the database associated with the user. A limited
purchase
request includes a purchase request in which a credit card or a debit card
exceeds the
48
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
monthly/weekly allocations of session or exceeds the time allowance for a
certain
period of time. A temporarily blocked purchase request includes a purchase
request
in which the zip code or other information supplied by the user does not match
the
appropriate information stored in a database. Moreover, the system can be
designed
so that purchase requests classified as blocked can also be classified as
temporarily
blocked when the system allows a user to supply information, such as the
correct
expiration date of a charge card. When the user is allowed to make payment to
a
lending institution in order to validate the credit or debit card, a
communication
session can be classified as temporarily blocked.
According to one embodiment of the invention, when the purchase request
passes the additional fraud control, the credit card account information or
the debit
card account information is forwarded at block 905 to a remotely located site
511 for
authorization. Site 511 can be accessed over the Internet through server 506.
Alternatively, site 511 can be accessed via a modem link 512. Remote sites
used for
authorization may, for example, include a credit bureau, a banking
institution, a third
party biller such as a telephone service provider, a cable television service
provider, a
utility service provider, an Internet service provider, or the like. Remote
site 511
checks to ensure that the credit card, debit card or account number is valid.
According
to another embodiment of the present invention, when the purchase request
passes the
additional fraud control, the credit card account information or the debit
card account
information is forwarded to a local database to ensure that the credit card or
debit card
is valid.
When the predetermined charge to the account is approved or denied, remote
site 511 sends an approval or denial notification back to system 507 at block
906.
When remote site 511 authorizes the purchase request, the purchase request is
entered
into system 507 at block 907. When the purchase request is not authorized, the
purchase request is either blocked or temporarily blocked until information
regarding
the credit bureau, banking institution, telephone service account, cable
television
account, a utility service account, or Internet service provider account is
settled by the
user.
49
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
When the purchase request is entered into system 507, system 507 calculates
the total billable amount for the session. System 507 then sends the billable
amount
to remote site 511 at block 908. System 507 can also send the credit card,
debit card,
telephone service account, cable television account, utility service account,
or Internet
service provider account information or some other identifying information
along
with the billable amount to remote site 511. Remote site 511 then charges the
billable
amount to the account and a new charge for the actual billable amount for the
purchase is charged to the account at block 908. Alternatively, the billable
amount is
sent to a payment authorization database, which can be locally or remotely
located.
Figures l0a-lOc show a flow diagram summarizing the real-time billing and
fraud control system of the present invention. At step 1001, a customer is
connected
to a service provider or a merchant providing telephone or communication
session
services, and/or goods and services for purchase by way of e-commerce. At step
1002, the customer is queried for personal information and a method of payment
that
will be used by the customer. In situations when the customer has previously
purchased services and/or goods, form of payment information can be
automatically
accessed from a form-of payment/credit database based on the ANI and/or other
information that has been provided by the customer, and presented to the
customer for
possible selection by the customer. At step 1003, the personal information of
the
customer and the method of payment information that is to be used by the
customer
are actively and/or passively captured. The personal information of the
customer that
is captured can include, the customer's telephone number, address, DL number,
social
security number, mother's maiden name, a PIN, a password, a digital
certificate, a
credit card number, a debit card number, banking information, a voiceprint, a
fingerprint, a portrait image and/or a computer network address.
At step 1004, the captured customer data is compared to information contained
in one or more customer databases, such as any of an external shared negative
customer database 1005, an internal negative customer database 1006, an
external
shared positive customer database 1007 and an internal positive customer
database
1008. At step 1009, it is determined whether the captured customer data
matches
information contained in a positive customer database or a negative customer
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
database, or whether the captured customer data does not match information
contained in any of the databases accessed. If, at step 1009, the captured
customer
data matches information contained in a positive customer database, flow
continues to
step 1010
If, at step 1009, the captured customer data matches information contained in
a
negative customer database, flow continues to step 1011 where a service
representative can intervene for making a final determination regarding
blocking or
limiting purchases of the goods and/or services available for purchase. When
the
service representative decides to block a purchase based on the available
information,
flow continues to step 1012. When the service representative, based on the
available
information, decides to limit or temporarily limit a purchase, . flow
continues to step
1013, and then to step 1010. Alternatively, flow can proceed to block
purchases (step
1012) or limit purchases (step 1013) based on information available at
decision step
1009.
If, at step 1009, the captured customer information does not match information
contained in any of the databases that were accessed, flow continues to step
1014
where the captured information is verified at step 1015 with independent
sources by
queries to at least one external database, such as an ANI database, a credit
card
agency database, a credit report bureau database, a banking institution, and a
check
approval service. Flow continues to step 1016, where it is determined whether
the
captured customer information was verified. If not, flow continues to step
1017
where a service representative can intervene for making a final determination
regarding blocking purchases of the goods and/or services available for
purchase.
When the service representative decides to block a purchase based on the
available
information, flow continues to step 1018 and to step 1019 where the captured
information is shared with negative customer databases, such as databases 1005
and
1006. When the service representative decides to permit a purchase based on
the
available information, flow continues to step 1010 where the customer
information is
compared to fraud control screening criteria and to establish a sale limit,
and to step
1020 where the captured information is shared with positive customer
databases, such
51
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
as databases 1007 and 1008. Alternatively, flow can proceed to block purchases
(step
1018) based on information available at decision step 1016.
At step 1010, the customer information is compared to fraud control screening
criteria and a sale limit is established. Flow continues to step 1021 where
customer
fraud screening criteria is accessed, such as a bill-to address, a ship-to
address, a
purchase-frequency limit, a purchase-value limit, a call origin location, the
customer
age, and customer gender. At step 1022, it is determined whether the customer
passed
the fraud control screening. If not, flow continues to step 1023 where a
service
representative can intervene for making a final determination regarding
blocking
purchases of the goods and/or services available for purchase. When the
service
representative decides to block a purchase based on the available information,
flow
continues to step 1024. Alternatively, flow can proceed to block purchases
(step
1024) based on information available at decision step 1022.
If, at step 1022, the customer passes the fraud control screening, flow
continues to step 1025 where a customer purchase value limit is established.
Flow
continues to step 1026 where the established purchase value limit is
communicated to
appropriate internal and external databases, such as databases 1005-1008. Flow
continues to step 1027 where it is determined whether the customer purchase
value
has been authorized. If not, flow continues to step 1028 where a service
representative can intervene for making a final determination regarding
blocking
purchases of the merchants goods and/or services. When the service
representative
decides to block a purchase based on the available information, flow continues
to step
1029. Alternatively, flow can proceed to block purchases (step 1029) based on
information available at decision step 1027.
If the customer purchase value was authorized at step 1027, flow continues to
step 1030 where the customer selects goods and/or services having a value that
is less
than or equal to the established limit for the customer. Flow continues to
step 1031
where the customer is billed by way of the customer-selected method of
payment,
such as an invoice, an electronic funds transfer or e-draft, a credit or debit
card
transaction, an Internet Service Provider, a telephone, a cable or other
utility account,
or an e-wallet. The purchase value is transmitted to appropriate internal and
external
52
Substitute Sheet (Rule 26)
CA 02390494 2002-05-03
WO 01/33520 PCT/US00/30504
authorization and credit limit amount databases at step 1032 and the process
is exited
at step 1033.
Other modifications and enhancements to the present invention may be
adaptively made for providing other services over a computer network, such as
the
Internet, than that described, such as computer service advice, medical
counseling,
suicide hot-line and other services.
Any patents or publications referenced above should be deemed to be
incorporated by reference as to their entire subject matter should one believe
it
relevant to obtain details from such sources for explanations of related
arrangements
and how they may be employed to advantage in the present invention. The
present
invention should only be deemed to be limited in scope by the claims which
follow.
53
Substitute Sheet (Rule 26)