Note: Descriptions are shown in the official language in which they were submitted.
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
COOPERATIVE USE OF IDENTIFICATION NUMBERS FOR CONSUMER
TRANSACTIONS
BACKGROUND OF THE INVENTION
FIELD OF THE INVENTION
This invention relates generally to systems for issuing consumer entitlements
in a retail store.
More specifically, the invention relates to systems for issuing promotions or
certificates of the
type that requires a unique personal identification number (PIN) to be
conveyed to a customer
receiving the item.
to
DISCUSSION OF THE BACKGROUND
PINs are printed or encoded on valuable certificates awarded to customers and
subject to
authorization for various products and services. Each certificate must be
resistant to fraud
and must be secure from duplication. Having random but valid unique numbers
requires the
15 creation and storage of the numbers in databases or on preprinted
certificates. The
administration of such databases or certificates become expensive and is
subject to fraud.
The art relating to PIN generation is discussed in detail in United States
Patent 5,892,827.
A marketing technique that has enjoyed increasing popularity is the awarding,
at the point-of
2o sale, of a free product or service as an incentive to purchase other
products or services.
Typical marketing programs offer 5 or I O minutes of long distance service as
incentives to
purchasing the sponsoring company's product, as potential prizes for
participating in a
marketing contest, or as premiums offered under a retailer's frequent shopper
loyalty program,
or simply as a product for purchase. With respect to marketing long distance
telephone
25 service, there are generally two methods employed. One method entails the
registration of the
consumer and the issuance of a telephone "credit card" for which an account is
established and
is later credited with certain dollar amounts of telephone service based on
the consumer's
actions or purchases. Another method is to issue telephone "debit cards" to
each consumer
meeting the requirements of the particular marketing program. These debit
cards are generally
3o pre-authorized in 5 or 10 minute denominations. The issuance of a debit
card does not
CA 02403234 2002-09-30
WO 01/75826 PCTNS00/06708
establish an account, but rather is authorized for the specified amount of
telephone service and
then becomes useless after the telephone time is exhausted. With both methods,
the consumer
is usually required to dial a toll-free number and provide a personal
identification number
(PIN) in order to activate the free service. This PIN must be randomly
generated prior to the
issuance of the telephone credit/debit card so that verification of valid
usage can be established
prior to granting the free service.
With each of the processes described above, there is a requirement that a
physical card
(similar to a consumer credit card) be issued to the consumer. The manufacture
and delivery
to of these cards represents a significant expense and therefore can be cost
prohibitive in many
circumstances. In addition, there are security concerns inherent in the
manufacture and
delivery of the cards since someone other than the intended user could easily
convert them for
their own use (especially in the case of the debit card since the PIN is
generally pre-printed on
the card itself). Another limitation of the current methods of marketing
telephone cards is the
15 fact that the account and/or a PIN must be generated prior to the issuance
of a card. This can
result in a time lag from the time the consumer complies with the offer and
the time at which
the telephone service is available (especially with respect to the credit card
method). This
limitation can also cause shortages or excess inventories of cards based on
consumer demand
(especially with respect to the debit card method).
Regardless of whether a certificate or award is presented to a consumer as an
incentive to
purchase selected products or simply in response to a request to purchase the
service that the
certificate provides, the difficulties described above have inhibited safe and
efficient
distribution of such certificates. The following paragraphs discuss the
problems that apply
specifically to the distribution of prepaid service certificates, such as
prepaid long-distance
calling cards.
Problems first arise at the manufacturing stage. Cards are typically
preprinted with the value in
dollars or the time in minutes, in preset amounts, even though the consumer
may prefer to
3o have a different value or time. Moreover, preprinted cards have the further
limitation that they
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
contain fixed important information, such as an "800" toll-free number for
accessing the
service. Access numbers may become overloaded and cause inconvenient delays
for the user
and new access numbers may have to be added to meet demand, but there is no
convenient
way to update this information on a pre-printed card. Similarly, each
preprinted card has a
PIN (personal identification number) that must be used to activate the card,
i.e., turn it on for
use. The preprinting of PINS on the card exposes the value of the card to
anonymous and
usually untraceable theft. Once the card is printed, its value can be stolen
without physically
taking the card itself. The theft can take place anywhere from the printing
source to the retail
outlet. It will be apparent that sending these "live" cards through a supply
and distribution
to process is fraught with security risks. The special handling adds to the
cost and difficulty of
marketing and selling remote value cards. Unsuspecting consumers may purchase
cards that
are either depleted or being used by others purchased illegally. The
merchandising and sales of
tamper resistant cards adds to the cost and effort for everyone. Live cards
with protected
PINS must be treated as a near-cash item through the distribution and
retailing process. As a
delivery of cards is made to a store, if it is not kept under lock and key or
in the cash drawer it
may be easily stolen, lost or misplaced. The cards themselves are very small
and easily
concealed by unscrupulous employees or shoppers. Therefore, suppliers and
retailers of these
cards are exposed to a very large financial risk in handling the cards. If the
value is taken
illegally from a card, it is not possible for the retailer to accept the
return or bill back the
supplier.
One solution is to distribute "dead" cards instead of "live" ones. A dead card
is one that has a
PIN that must be activated by the retailer before distribution to the
consumer. Activating
preset PI~'s is very expensive, time consuming and error prone. Distributing
dead cards with
PINs that require activation is, therefore, inconvenient and is still prone to
theft and misuse
because some card suppliers preprint and assign the PNs in a uniform,
predictable or
unprotected manner. Dishonest persons may dial the access number and enter
PINS until they
successfully access the service, or may look for a pattern in multiple PINs,
and then resell the
PIN and access numbers to different users. Another potential problem is that
some PIN
3o sequences are purposely short, for the convenience of the user. This
creates a dangerous
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
situation, since a computer dialer can more easily pick and decipher short
PINS that are not
encoded.
Another proposed solution to the security problem is to use scratch-off
coatings and
removable tape covers over the PINs. This has a limited effect because the
"live" and valuable
cards can still be stolen and used anonymously by dishonest persons, anywhere
through the
supply chain.
Systems have been proposed in which prepaid cards are sold without a PIN. The
PIN is
to activated or attached to the card after is a call is made to a central
computer that issues PINs.
In some systems of this type PINS may be downloaded in a batch, and then held
until a card is
purchased, at which time a PIN is attached to the preprinted portion of the
card. The principal
limitation of this method is that a call must be made to a central computer to
issue a PIN. This
slows the down the transaction and, in a retail environment, slows down the
cashier while the
15 computer is dialed and the PIN is issued. Further, a dishonest or
inattentive cashier could sell
or give away the value of the PINS.
Some prepaid telephone cards are sold or vended in enclosed plastic containers
placed in a
store display rack. The cashier selling such cards typically scans a bar code
on the display
2o itself, and a PIN is obtained by placing a call to the service provider.
This bar-coded activation
method fails to prevent fraud or misuse by others as the bar codes can be
duplicated and used
on more than one card. A thief could steal one or more cards and purchase one
to obtain the
valid batch code, thus activating the stolen cards as well.
25 It will be appreciated from the foregoing that prior art techniques for
distributing certificates
or cards redeemable for a valuable service all have practical difficulties
that render the
certificates or cards both inconvenient to the consumer and vulnerable to
fraud or theft. There
is a need for a new approach for distributing such certificates or cards in a
convenient manner
without compromising the security of the valuable services that are obtained
by use of the
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
cards. The present invention satisfies this need, as briefly described in the
following summary
of the invention.
While the invention will be described mainly in connection with the awarding
of free long
distance telephone service, it is to be understood that the principles of the
invention are also
applicable to providing any award, at the point-of sale, where the subsequent
verification of
the award can be accomplished without the need for a pre-established list of
valid
authorization codes.
to SUMMARY OF THE INVENTION
The invention provides a computer implemented system and method for assuring
security
and validity of pseudo randomly numbered authorization codes, typically
printed on
certificates or stored in machine readable memory on user's cards, including a
first
algorithmic means on a first computer for generating an authorization code in
response to a
request, and a second algorithmic means on a second computer for determining
if a code
provided by a user is an authorization code that would be generated by said
first
algorithmic means. The transmission of the second algorithmic means to the
second
computer obviates the requirement to transmit actual generated codes from the
computer
providing the authorization code to the computer determining if the code
presented by a
2o user is an authorized code.
The algorithm transmitted from the first computer, such as a retail store
computer that
functions to monitor transactions at point of sale (POS) terminals and kiosks
of a store, to
the second computer may either be the same algorithm used by the first
computer, or the
2s transmitted algorithm may be modified so that it functions by receiving a
user's code and
determining if the user's code is a code that could have been generated by the
algorithm
used in the first store. That is, the computer code defining the algorithm
transmitted to
the second computer may not have the ability to print or display codes,
thereby preventing
a user of the second computer from fraudulently obtaining and validating
authorization
3o codes. Instead the computer code defining the algorithm transmitted to the
second
5
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
computer may only have the ability to determine whether a code input to the
second
computer is valid in the sense that the code input into it is one that could
be generated by
the algorithm running on the first computer.
s Preferably, the authorization code contains a date indicating a date on
which it was
generated. Preferably, the product or service is a telecommunications services
credit. The
product or service may be a discount on another product or service. Typically,
but not
necessarily, product or service is a product or service that is not provided
by the retail
store at which the user receives the authorization code. The authorization
code may include
to digits associated with the store at which the authorization code was
generated. Preferably the
authorization code generation algorithm generates a code only once.
Briefly, and in general terms, the method of the invention comprises the steps
of detecting the
occurrence of an event that has been preselected to trigger the generation of
an authorization
15 code for distribution to a customer of a retail store; generating a
certificate or card storing in
human or machine readable form the authorization code, the authorization codes
generated in
a seemingly random sequence by a pseudo random code generating algorithm to
avoid
deciphering of the algorithm; receiving at a second computer from a user a
code; using an
algorithm to determine if the received code from the user is one that would be
generated by
2o the algorithm, and if so, determining to provide the associated product or
service associated
with the code to the user. If a determination is made to provide the
associated product or
service to the user, the product or service provider provides the product or
service to the user.
BRIEF DESCRIPTION OF THE DRAWINGS
25 A more complete appreciation of the invention and many of the attendant
advantages thereof
will be readily obtained as the same becomes better understood by reference to
the following
detailed description when considered in connection with the accompanying
drawings, wherein:
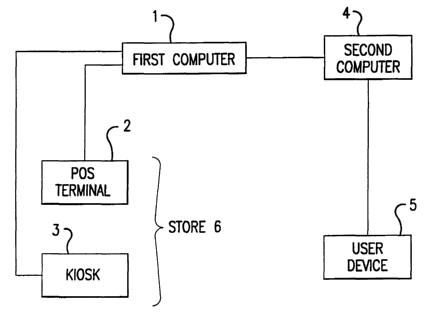
Figure I is a schematic of an embodiment of a novel computer system of the
invention;
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
Figure 2 is a flow chart of the process of a consumer receiving an
authorization code for the
system of Figure 1; and
Figure 3 is a flowchart of the process of validating the authorization code
for the system of
Figure I.
DESCRIPTION OF THE PREFERRED EMBODIMENTS
In the drawings, like reference numerals designate identical or corresponding
parts
throughout the several views, and Figure 1 shows a first computer 1 connected
to a POS
l0 terminal 2 and a kiosk 3 of a store 6. The POS terminal 2 includes means to
enter transaction
data and provide price information for transacting a sale with a customer. POS
terminals are
well known in the art. The POS terminal 2 may include a machine means to
identify products
codes and a user identification, such as a bar code scanner (for scanning
product identification
bar codes on product items and user identification bar codes on user
identification cards), a
magnetic stripe reader for scanning magnetic media containing a user's
identification number
(such as a bank or credit card), a MICR coder reader for reading MICR codes on
checks to
obtain check authorization and to obtain a user identification. The POS
terminal also includes
a means to write an authorization code in either human readable form or
machine readable
form.
The store 6 may also include a kiosk 3. For the purposes of this invention, a
kiosk is a
terminal of a computer system including a means for the customer to enter a
payment (such as
cash or a credit card) or a unique identification associated with the customer
and a means for
writing an authorization code in either human readable form or machine
readable form.
2~
The POS terminal 2 and the kiosk 3 of the store 6 are each connected via a
communication
line with the first computer 1. The communication line may pass through
network
connections or other intermediaries. For example, there may be a store
controller computer
interposed in the communication line between the first computer 1 and the POS
terminal 2 and
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
kiosk 3. However, it is to be understood that the first computer may be a
store controller
computer.
The first computer 1 is connected via a communication line to a second
computer 4. There
may be intermediary devices interposed along the communication line connecting
the first
computer 1 and the second computer 4 so long as the first computer 1 can
communicate with
the second computer 4.
The second computer 4 is in communication with a user device 5. The user
device 5 may be a
to wire line telephone, a wire less telephone, or another computer. The user
device 5 may be any
device that enables a user to transmit data si;nals conveying an authorization
code to the
second computer 4.
In figure 2, in step 10, the consumer takes action which results in a request
signal transmitted
from the POS terminal 2 or the kiosk 3 to the first computer 1 prompting
generation of an
authorization code. The action by the consumer may be the purchase of an item
at the POS
terminal or the kiosk entitling the user to an authorization code for a
product, service, or
discount on a product or service, it may be an explicit request by the
consumer to purchase an
authorization code entitling the user to receive the product or the service,
it may be based
2o upon the customer's prior shopping history as recorded in a database
associated with the first
computer 1, or it may instead be based a promotional campaign in which each
consumer at
either the POS terminal 2 or the kiosk 3 are provided an authorization code.
In step 11, the
first computer 1 generates an authorization code. In step 12, the first
computer 1 transmits
the generated code to the POS terminal or kiosk. In step 13, the POS terminal
or kiosk
records the authorization code in a recordable medium. In the preferred
embodiment the
medium is paper and the code is in human readable digits, such as letters and
numbers, and the
printed paper includes a telephone number to call to obtain the authorized
product or service.
In figure 3, in step 14, the second computer system 4 receives the code
entered into the user
3o device 5. In step 21, the second computer system 4 executes an algorithm
that determines if
s
CA 02403234 2002-09-30
WO 01/75826 PCT/US00/06708
the code it received is one that could have been generated by the
authorization code
algorithm.
In the preferred embodiment, the product or service associated with the
authorization code is
prepaid telecommunication time. In the preferred embodiment, if the second
computer
system 4 determines that the code it received from the user device S is one
that could have
been generated by the authorization code algorithm, it dueries the user device
5 for a
telephone number to which to credit prepaid telecommunications time, receives
a telephone
number from the user device 5, and credits the account for that telephone
number.
to Optionally, the second computer system 4 may also provide a dial around
telephone number
to the user device 5 and instruct the consumer to dial the dial around number
as a
precondition for using the credit obtained from the authorization code.
Preferably, the second
computer system stores authorization numbers received from a user device and
does not
reauthorize any of those numbers.