Note: Descriptions are shown in the official language in which they were submitted.
CA 02404922 2002-10-23
WO 97148216 PCT/US97/07607
-1-
0
REGISTRATION OF MOBILE PACKET DATA
TTRNlINALS AFTER DISASTER
BACKGROUND OF THE INVENTION
The present invention relates to a wireless packet data
communication system having a central system and mobile terminals, and in
particular, to recovering from a disaster at the central system.
In a communications system having a central system and addressable
mobile terminals, there is a forward or downstream channel and a reverse or
upstream channel.
On the downstream channel, the central system broadcasts
information accessible to, sometimes referred to as heard by, all of the
mobile
terminals. The downstream broadcast comprises system control messages
including
~ntr'°1 messages at predetermined time intervals and packets of message
data
respectively addressed to a single mobile terminal (or group of terminals
sharing a
common address). The downstream broadcast is essentially continuous. The
downstream channel may comprise several frequencies, and the central system
may
use one frequency for its transmission, or may hop among frequencies.
On the upstream channel, the mobile terminals respectively transmit
packets of message and system-related data to the central system using a
contention
protocol wherein if packets collide, retransmission is attempted after an
essentially
random time interval. The mobile terminals directly communicate only with the
central system, not with each other. The upstream channel may comprise several
frequencies, and a- mobile terminal may use one frequency for its
transmission, or
may hop among frequencies.
The communications system is designed so that the central system is
aware of each mobile terminal able to communicate therewith. When a new
mobile terminal enters the geographic area served by the central system, which
occurs from time to time, the mobile terminal must register with the central
system.
Registration commences when a mobile terminal sends, via the
upstream channel, its public identity number to the central system along with
a
west for a temporary identifier. The public identity number and the request
for
CA 02404922 2002-10-23
WO 97/48216 PGT/US97/0760'J
-2-
0
a temporary identifier are examples of system related data. The central system
responds by sending, via the downstream channel, a temporary identifier, which
is
a randomly chosen number in a predetermined range which has not previously
been
assigned to any other mobile terminals in communications range of the central
system, to the requesting mobile terminal. The temporary identifier is an
example
of a system control message which is sent as needed, that is, not at a regular
interval.
During registration, the central system adds to its routing table an
entry comprising the external address of the mobile terminal and the temporary
identifier assigned to the mobile terminal. The routing table may also include
an
upstream frequency for the mobile terminal. It will be appreciated that the
routing
table changes frequently due to the mobility of the terminals. Since the
routing
table is stored in one place, the central system is wlnerable to loss of the
routing
able. The central system uses the temporary identifier as the address for the
mobile terminal in subsequent downstream message data packets. The temporary
identifier is preferred to other pre-existing identifiers for security and
management
reasons.
The requesting mobile terminal and the central system then exchange
encryption information. After secure communications are established, the
mobile
terminal sends its secret identity number to the central system. The central
system
uses the secret identity number to access a stored profile for the mobile
terminal
containing various subscriber information,'including billing information.
The stored profile for the mobile terminal also contains an external
address for a subscriber associated with the mobile terminal. The public
identity
number of the mobile terminal may be its external address. From time to time,
external systems send message data packets having the external address of the
mobile terminal to the central system, which uses the external address and its
stored routing table to obtain the temporary identifier of the mobile
terminal. The
central system then transmits the message data packets on the downstream
channel
with the temporary identifier as destination address. The mobile terminal
captures
and processes data packets addressed to its temporary identifier.
CA 02404922 2002-10-23
PC'f/US97107607
WO 97148216
-3-
0
If a problem occurs at the central system, such as loss of its routing
table, which affects the essentially continuous transmission on the downstream
channel, some mobile terminals may interpret such problem as an error
condition
and attempt to register anew with the central system. As these mobile
terminals
attempt to register anew, the throughput of the upstream channel will be
reduced,
which may cause further problems at the central system. Yet more mobile
terminals will perceive an error condition. Eventually, essentially the entire
population of mobile terminals will be in contention for the upstream channel
while
tempting to register anew, so the throughput of the upstream channel will be
degraded to a very low value. Consequently, re-registration will take an
inordinately long time, and the message data packet throughput of the
communications system during such re-registration will become unacceptably
low.
Thus, there is a need for a way to register essentially the entire
popu~tion of terminals, that is, reconstruct the central system's routing
table of
temporary identifiers, after a disaster at the central system which has
obliterated its
routing table.
SLfMMARY OF THE INVENTION
In accordance with the present disclosure, registration attempts by a
terminal using a contention protocol to communicate with a central system are
controlled by transmitting a registration index from the central system to the
~~~ at specified temporal periods, and modifying the value of the registration
index when the terminal should attempt to register with the central system.
Use of
the registration index prevents unnecessary registration attempts by the
terminal.
A mode flag is transmitted from the central system to the terminal at
predetermined temporal intervals, and the value of the mode flag is modified
when
~e central system is recovering from a disaster so that the terminal refrains
from
immediately attempting to register with the central system during disaster
recovery.
During disaster recovery, the terminal is able to associate itself with
one of a plurality of sub-intervals. The central system transmits a sub-
interval
designator to the terminal at regular temporal periods during disaster
recovery.
CA 02404922 2002-10-23
WO 97/48216 PCT/US97~7607
-4-
0
The central system modifies the value of the sub-interval designator after a
predetermined number of the regular temporal periods. The flow of registration
attempts by a community of terminals is smoothed fmm a situation wherein
essentially the entire community of terminals is contending to register after
a '
disaster to a situation wherein subsets of the community try to register in
respective
sub-intervals after the disaster.
It is not intended that the invention be summarized here in its
entirety. Rather, further features, aspects and advantages of the invention
are set
forth in or are apparent from the following description and drawings.
BRIEF DESCRIPTION OF THE DRAWINGS
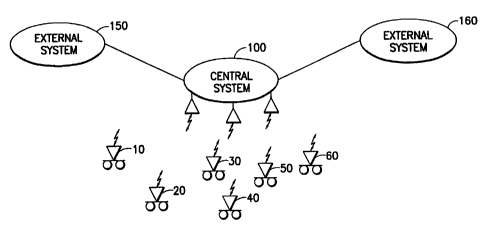
Fig. 1 is a diagram of the environment in which the present
invention is applied;
Fig. 2 is a diagram of the communication channels between the
central system and mobile terminals;
Fig. 3 is a flowchart of actions at the central system;
Fig. 4 is a flowchart of actions at a mobile terminal;
Figs. 5A and 5B are timing charts illustrating traffc on the
downstream channel; and
Figs. 6A and 6B are timing charts illustrating traffic on the upstream
channel.
DfiTAII..ED DESCRIPTION
Fig. 1 illustrates an environment having mobile terminals 10-60 in
wireless communication with central system 100, which is accessible to
external
systems 150, 160 via conventional communications techniques. The central
system
includes a general purpose processor, memory, storage and other conventional
data
processing facilities. Each mobile tenninal includes a processor, memory and
storage, not shown or further described as the particular components are not
critical to the present invention.
IS As shown in Fig. 2, central system 100 sends information to mobile
CA 02404922 2002-10-23
WO 97/48216 PCT/US97/07607
-5-
0
terminals 30-50 via downstream channel 5, while the mobile terminals 30-50
send
information to centrat system 100 via upstream channel 6. Mobile terminals 10,
20
and 60 communicate with c~tral system 100 in similar manner, and are not shown
to simplify the drawing in Fig. 2.
According to the present technique, a mobile terminal has a definite
way to determine wh~her it should register with the central system after what
may
be a disaster. For instances where registration is appropriate, the mobile
terminal
has a procedure by which it can determine when it should register.
The system control messages broadcast at regular intervals by the
central system 100 on the downstream channel are augmented to include a
registration index and a mode flag.
The registration index indicates a period of validity for temporary
identifiers, that is, a sort of batch number. When the cxntral system routing
table
is unusable, also referred to as lost, the registration index .is incremented.
Typically, the registration index is a few bits long to ensure that even if a
sequence
of system failures are clustered, the registration process is fully performed
after the
last system failure. In contrast, if the registration index is only one bit
long, then
it has the same value after a cluster of two failures in which the routing
table is
lost, and a mobile terminal is not aware that its temporary identifier is
invalid. All
valid temporary identifiers have the same registration index.
The mode flag indicates whether registration for a community of
mobile terminals sharing a central system, also referred to as central system
disaster recovery, is in progress.
Fig. 3 is a flowchart depicting actions at central system 100. Fig. 4
is a flowchart depicting actions at, for example, mobile terminal 10. Figs.
5A,
58, 6A, 6B are charts depicting traffic on the downstream and upstr~m channels
~r a ~~c example of the present disaster recovery registration scheme.
At step 310, central system 100 is assumed to be in normal
operation, in accordance with the functions of a mobile data intermediate
system
(MDIS) described in Cellular Digital Paclret Data System Specification,
Release
1.0, July 19, 1993, and Release 1.1, January 19, 1995, available from CDPD
CA 02404922 2002-10-23
-6-
Industry Input Coordinator, 650 Town Center Drive, Suite 820, Costa Mesa, CA
92626.
Central system 100 broadcasts, that is, transmits on downstream
channel 5, system control messages at regular intervals. Fig. 5A shows
regularly
broadcast system control messages 551-555; system control message 555 is seen
to
include registration index 510A, illustrated as being of length two bits and
having a
value of "01 ", and mode flag S I 5A, illustrated as being of length one bit
and having
a value of "0" corresponding to being onset. At step 320 of Fig. 3, central
system
100 broadcasts the registration index and the mode flag, such as registration
index
5I OA and mode flag 515A.
At step 330, central system 100 determines whether its routing table
is properly available; if so, central system 100 returns to normal operation
310.
Let is be assumed that mobile terminal 10 generally operates in
accordance with the functions of a mobile end system as described in Cellular
Digital Packet Data System Specification.
Mobile terminal 10 enters the communications area of central system
100, and, at step 405 of Fig. 4, registers with central system 100. As shown
in
Fig. 6A, registration commences with mobile terminal 10 sending a registration
request 61 OA, including its public identity number, herein "717171 ", to
central
system 100 via upstream channel 6. Central system 100 replies to the
registration
request 610A by sending registration response 530A, including atemporary
identifier, herein "5568", to mobile terminal 10 via downstream channel 5. At
step
410 of Fig. 4, mobile terminal 10 stores the temporary identifier "5568" and
the
registration index at the time of receipt of the temporary identifier. From
Fig. 5A,
the registration index in broadcast message 552 is seen to have a value of "O1
". Box
600A in Fig. 6A indicates a portion of the storage of the mobile terminal 10.
After registration is complete, at step 415 of Fig. 4, mobile terminal
10 enters normal operation. For example, if external system 150 wishes to send
a
message to mobile terminal 10 during normal operation (central system 100 in
step
310 of Fig. 3 and mobile terminal 10 in step 4I 5 of Fig. 4), central system
I00
CA 02404922 2002-10-23
wo 9~nsm 6 pcrnrs9~ro~ao~
0
receives the message from external system 150, and places the message into one
or
more message data packets, shown as message data packet 540A in Fig. 5A.
Meanwhile, mobile terminal 10 listens to the packets broadcast on downstream
channel 6, recognizes its temporary identifier "5568" in message data packet
540A,
captures the message data packet 540A, and processes it.
At step 420 of Fig. 4, mobile terminal 10 captures the broadcast
registration index and mode flag in each of broadcast system control messages
553-
555. Since, at step 425, mobile terminal 10 determines that the broadcast
registration index value "0l " matches the stored registration index value "O1
",
mobile terminal 10 returns to normal operation 415.
Bven if traffic on downstream channel 5 was interrupted during this
time, mobile terminal 10 does not attempt to register again because the
broadcast
and stored registration indices match. Use of the registration index is seen
to
prevent unnecessary regisdation.
Let it be assumed that a disaster has occurred at central system 100,
so~that at step 330 of Fig. 3, the routing table is found to be unusable.
Central
system 100 now proceeds to a disaster recovery procedure according to the
present
disaster recovery technique. During disaster recovery, the central system
suspends
normal message data packs transmission, and uses the downstream channel to
transmit a sub-interval designator and to register mobile terminals. The sub-
interval designator controls the number of mobile terminals allowed to attempt
ro~~on at any time.
Let it be assumed that the community of mobile terminals is
unknown, and that each mobile terminal has a stored but no longer valid
temporary
identifier. It will be appreciated that using only the least significant bit
(LSB) of
the invalid temporary. identifier divides the mobile terminal community into
two
g~ups, the (LSB = 0) group and the (I,SB = 1) group. Similarly, using the n
least significant bits of the invalid temporary identifier divides the mobile
terminal
community into 2° groups of essentially equal size, whether the
temporary
identifiers were assigned randomly or sequentially.
Instead of using its temporary identifier, each mobile terminal use a
CA 02404922 2002-10-23
wo mm2is rcr~rs9zro~6o~
_g_
0
random number, or a different pre-stored number which is statistically evenly
distributed over the community of mobile terminals. Instead of using the least
significant bits of its invalid temporary identifier, each mobile terminal
could use
the most significant bits; however, if temporary identifiers are assigned '
sequentially, the most significant bits will not have an even statistical
distribution
and so will not ensure that each group is of essentially equal size.
Let the registration interval be divided into 2° sub-intervals.
During
the first sub-interval, only the mobile terminals in the first group of the
2° groups
of mobile terminals are permitted to attempt registration. During the second
sub-
interval, the mobile terminals in the second group and the as-yet unregistered
mobile terminals in the first group are permitted to attempt registration.
During
the third sub-interval, the mobile terminals in the third group and the as-yet
unregistered mobile terminals in the second and first groups are permitted to
a~ypt registration. This procedure continues, so that during the last sub-
interval,
all of the as-yet unregistered mobile terminals are permitted to attempt
registration.
It will be appreciated that n and the temporal length of the sub-
interval are matters of design choice. For example, as n increases, the number
of
mobile terminals trying to register in a sub-interval decreases, so the
efficiency of
the upstream channel increases. It is important to appreciate that the number
of
mobile terminals trying to register during a sub-interval decreases with time,
as a
portion thereof become successfully registered. The sub-interval designator
2$ functions as a blind address, in that it selects an individually unknown
but
statistically manageable number of mobile terminals. Use of the sub-interval
designator controls the registration flow of mobile terminals.
More specifically, the length of a sub-interval is chosen depending
on the contention protocol and the expected number of mobile terminals being
~rv~. gxamples of contention protocols are slotted ALOHA, carrier sense
multiple access with collision detection (CSMA/CD), digital sense multiple
access
with collision detection (DSMA/CD). Important characteristics of the
contention
protocol include number of retries after a failed transmission, wait time
before
retrying, and so on.
CA 02404922 2002-10-23
WO 97/48216 PCT/US97l0760?
-9-
0
At step 340, central system 100 increments the registration index,
for example, from "0l" to "10" (base 2 addition) and sets the sub-interval to
"-1".
At step 350, central system I00 increments the sub-interval to "0" and sets a
sub-
interval timer to zero. At step 360, central system I00 transmits the new
registration index "10", transmits the mode flag in a set condition, such as
having a
value of " 1 ", and transmits the sub-interval "0" .
For purposes of this example, assume that only the least significant
digit (base 10) of the temporary identifier is used, so that there are ten sub-
intervals. In other words, one-tenth of the mobile terminals wiD be permitted
to
register during each sub-interval, plus as yet unregistered mobile terminals,
if any,
from previous sub-intervals. At step 370, central system 100 receives and
responds to registration requests from mobile terminals having a stored
invalid
temporary identifier with a least significant digit of "0". At regular
intervals,
~~ sy~m 100 checks whether the sub-interval has been in progress for long
enough, as shown at step 380. If the sub-interval has not reached its
pr~etermined temporal duration, then steps 360-380 are rated.
If, at step 380, central system 100 determines that the sub-interval
duration has elapsed, then at step 390, central system 100 determines whether
al/
sub-intervals, herein, all ten sub-intervals, have run. If not, central system
100
returns to step 350, inctEments the sub-interval, resets the sub-interval
timer and
repeats steps 360-380 as generally ascribed above.
After central system 100 increments the registration index at step
340 and broadcasts the incremented registration index " IO" at step 360,
mobile
terminal 10 will find that the broadcast registration index "10" does not
match its
stored regist:ation index "0l " at step 425 of Fig. 4. Consequently, mobile
terminal 10 knows that its temporary identifier "5568" is invalid.
At step 430, mobile terminal 10 checks whether the most recently
broadcast mode flag is set. It will be recalled that at step 360, the mode
flag was
broadcast by central system 100 as being set. Because the broadcast mode flag
is
set, mobile terminal 10 knows that a disaster recovery is in progress. Use of
the
mode flag allows suspension of the normal registration procedure for the
CA 02404922 2002-10-23
WO 97/48116 PCT/US97/07607
- 10-
0
community of mobile terminals served by the central system.
At step 435 of Fig. 4, mobile terminal 10 captures the broadcast
interval. At the first execution of step 360 of Fig. 3, the interval has a
value of
"0" . At step 440 of Fig. 4, mile terminal 10 compares the broadcast interval
"0" to the least significant digit of its invalid temporary identifier "8" .
Since the
former value "0" is less than the latter value "8", mobile terminal 10
effectively
knows that it is not yet permitted to try. to obtain a valid temporary
identifier.
Mobile terminal 10 repeats steps 435 and 440.
As shown in Fig. 5A, central system 100 eventually executes step
360 resulting in broadcast of system control message 561 including
registration
index 5 l OB with a value of " 10" (base 2), mode flag 515B with a value of "
1 "
(base 2), that is, the mode flag is set, sub-interval flag 520B with a value
of " 1 "
(base 2) and sub-interval designator 525B with a value of "5" (base 10).
For convenience, the sub-interval flag is transmitted in a system
control message. When the sub-interval is upset, or has a value of "0" as
shown in
field 520A of system control message 55 I , it indicates that a sub-interval
designator is not transmitted. In contrast, when the sub-interval flag is set,
or has
a value of "1 " as shown in field 520B of system control message 561, it
indicates
that a sub-interval designator is also transmitted, such as sub-interval
designator
525B.
The sub-interval flag is described as having a length of one bit,
w~ch is consistent with the sub-interval designator having a predetermined
length.
Alternatively, if the length in bits of the sub-interval is determined
dynamically,
the sub-interval length in bits must also be broadcast. That is, the
granularity of a
sub-interval can be predetermined or determined dynamically as a function of,
for
example, the number of mobile terminals in the routing table before the
routing
ale was lost. Dynamic determination of the length of a sub-interval increases
the
efficiency and complexity of the recovery mechanism.
By the aforementioned process, central system 100 also generates
and broadcasts system control messages 562-573, shown in Figs. 5A-5B. Upon
subsequent executions of steps 435-440, mobile terminal 10 captures system
control
CA 02404922 2002-10-23
WO 97!48216 PCTIUS97J07607
-11-
0
messages 562-567, and determines that it should not attempt registration yet.
Eventually, at an execution of step 435, mobile terminal 10 captures
broadcast system control message 568, shown in Fig. 6B, having an interval
value
of "8" . At step 440, mobile terminal 10 finds that the broadcast sub-interval
"8" is
equal to the least .significant digit of its invalid temporary identifier "8",
so mobile
terminal 10 proceeds to step 450 and registers. During the registration of
step 450,
mobile terminal 10 sends registration request 6108, shown in Fig. 6B, to
central
system 100 via upstream channel 6. Central system 100 flies to the
registration
~lu~ 610B by sending registration response 5308, shown in Fig. 5B; including
temporary identifier "2394" to mobile terminal 10 via downstream channel 5.
At step 455 of Fig. 4, mobile terminal 10 stores the new temporary
identifier "2394" and the registration index "10" at the time of receipt of
the
temporary identifier. Box 6008 in Fig. 6B indicates a portion of the storage
of the
I S mobile terminal 10 after step 455 of Fig. 4. .
At step 460, mobile terminal 10 captures the broadcast mode flag in
system control message 570 of Fig. 58. At step 465, mobile terminal 10
determines that the mode flag is set, meaning that a disaster recovery is
still in
progress and so mobile terminal 10 should not attempt to send packets of
message
data. Mobile terminal 10 repeats steps 4fi0-465 for system control messages
571-
573.
At some time after broadcasting system control message 573 of Fig.
5B~ ~~ system 100 executes step 390 of Fig. 4, and determines that all sub-
intervals have elapsed, i.e., that the post-disaster registration process has
ended.
At this point, central system 100 has a valid routing table for the mobile
terminals
in communication therewith. So, central system 100 returns to normal operation
at
step 310. Upon the next execution of step 320, central system 1 ~ broadcasts
system control message 574 of Fig. 5B. If a message for mobile terminal IO
arrives from external system 160, central system 100 places the message into
message data packet 5408, seen to have the new temporary identifier "2394" for
mobile terminal 10, and transmits the message data packet 5408 on downstream
channel 5. Upon the following execution of step 320, central system 100
CA 02404922 2002-10-23
WO 97148216 _ Cl'/t1S97f07607
- 12-
0
broadcasts system control message 575.
Immediately after system control message 573 is broadcast, at the
execution of steps 460-465, mobile terminal 10 determines that the mode flag
is no
longer set, and returos to normal operation at step 415. During normal
operation,
mobile terminal 10 captures and processes message data packet 540B in a
conventional manner.
As a further example illustrating operation of the inventive
technique, let it be assumed that after capturing and processing system
control
m~~~ 555 in Fig. 5A, mobiIe~ terminal 10 went into a power standby mode, or
for some other reason stopped monitoring downstream channel 5 for a while.
Assume further that the mobile terminal 10 then woke up, or resumed listening
to
downstream channel 5, and, at an execution of step 420, capnrred broadcast
system
control message 575. Upon the next execution of step 425, mobile terminal 10
determines that the broadcast registration index "10" captured from message
575
does not match its stored registration index "0l" (shown in box 600A of Fig.
6A).
At' step 430, mobile terminal 10 determines that the mode flag in message 575
was
not set, so mobile terminal 10 effectively knows that a disaster recovery is
not in
progress. Mobile terminal 10 then proceeds to step 405 to obtain a new
temporary
identifier.
An advantage of the above-described scheme isv that a mobile
terminal can determine whether its temporary ident~er is valid, and so will
refrain
from needless registration even if there is ~ problem.
Another advantage of the above-described scheme is that only a
subset of mobile terminals attempts to register at any time after a disaster,
thereby
avoiding crippling congestion on the upstream channel.
A further advantage of the above-described scheme is that the
~~ion of the disaster recovery registration period is substantially known in
advance.
Yet another advantage of the above-described scheme is that co-
ordination between individual mobile terminals is not required.
Still another advantage of the above-described scheme is that the
CA 02404922 2002-10-23
WO 97I48Z16 PCT/US97/07607
-13-
0
actual registration process for a specific mobile terminal after a disaster is
the same
as during normal operation, which avoids an increase in the complexity of the
mobile terminal and central system.
New mobile terminals which enter the area served by the central
system while a disaster n~overy is in progress are allowed to immediately join
in
the registration process, that is, consider themselves to be as yet
unregistered
mobile terminals from a previous sub-interval. The result is that a new mobile
terminal quickly obtains a registration number, then enters a power standby
mode
until disaster recovery is complete, which saves battery power in the mobile
terminal. Typically, when a communications system provides for a standby power
mode for its mobile terminals, there is a regularly broadcast system control
message which "wakes up" mobile terminals having pending messages.
In a modification, new mobile terminals must wait until the disaster
every is complete before registering. A drawback of this scheme is that when
disaster recovery is complete, which may be indicated by a broadcast from the
ce~ltral system which is globally addressed to all mobile terminals, the group
of
new mobile terminals all attempt registration at approximately the same time,
which may congest the communication channel.
Alternatively, a new mobile terminal selects a random number or
other prestored number, and uses the selected number in Geu of an invalid
temporary identifier. This promotes statistical spreading of new mobile
terminals,
but does not have the power saving advantage of maximizing time in standby
mode.
In another embodiment, the profiles associated with certain mobile
terminals are designated for priority services. After a disaster, as soon as
such
mobile terminals are registered, the central system will transmit message data
packets between external systems and such mobile terminals, while the non-
priority
mobile terminals are continuing with post disaster registration. This is
useful for
essential services such as ambulances, emergency crews and so on.
In a modification, for priority mobile terminals, the central system
assigns temporary identifiers having their n least significant bits equal to a
CA 02404922 2002-10-23
wo ~nam6 rcrrUS9~ro~so~
14-
0
predetermined value, and this predetermined value is the first group permitted
to
register during the first sub-interval after a disaster. This embodimern
ensures that
priority mobile terminals have the shortest service intem~ption. For example,
the
central system reserves temporary identifiers ending in "00" for priority
mobile
terminals. During a normal registration, the central system does not assign
temporary identifiers ending in "00"; after accessing the profile of a newly
registered mobile terminal and determining it has priority status, the central
system
sends a revised temporary identifier ending in "00" to the priority mobile
terminal.
The above described embodiments are concen~ed with a
configuration having one central system serving a community of mobile
terminals.
It will be readily appreciated that the central system may correspond to one
radio
cell in a cellular system, and that the above-described disaster recovery
registration
scheme facilitates orderly registration of subsets of the mobile terminals in
a cell
1$ without any knowledge of which mobile terminals are in the cell. Since the
identities of the mobile terminals in a cell at any time are unpredictable, it
is
important that the disaster recovery registration protocol function without
such
identities, and without reliance on control messages addressed to identified
mobile
20 terminals.
Although illustrative embodiments of the present invention, and
various modifications thereof, have been described in detail herein with
reference
to the accompanying drawings, it is to be understood that the.invention is not
25 ~i~ to these precise embodiments and the described modifications, and that
various changes and further modifications may be effected therein by one
skilled in
the art without departing from the scope or spirit of the invention as defined
in the
appended claims.
35