Note: Descriptions are shown in the official language in which they were submitted.
CA 02410039 2002-12-06
-1-
SYSTEM AND METHOD FOR TRIGGERING ACTIONS AT A HOST
COMPUTER BY TELEPHONE
BACKGROUND OF THE INVENTION
The present invention is directed toward the
field of remotely controlling the actions of a host
computer system using a telephone connection,
particularly in triggering a predetermined program,
sequence of events, or series of actions at the host
system. Such a sequence of events could be, for
example, a script of commands which cause the host
computer system to connect to the Internet for
subsequent access by a remotely located user.
Recently, there has been a proliferation of
~.5 computer systems that are connected to the Internet,
the global information network. Most of the
services available on the Internet are provided by
large organizations, such as Government, University,
and large corporations. These institutions have the
capital and resources to spend on high-powered
server computers with corresponding dedicated links
to the Internet. These dedicated links range in
bandwidth from 56KB for an ISDN (integrated Services
Digital Network) line to 1.5M8 for a full T1 line.
Such links are typically dedicated connections to an
Internet Service Provider ("ISP"), where the ISP
-i-
CA 02410039 2002-12-06
-2-
then provides a physical connection to the Internet.
For small companies and individual users desirous
of setting up a server to provide services, such as
a World-Wide-Web ("Web") server, or an FTP (File
S Transfer Protocol) server, the costs of leasing and
maintaining a dedicated connection to an ISP is
prohibitive. Without a dedicated connection to the
Internet, there is no means of providing on-demand
access to remote users who want to take advantage of
the services provided by the server. The present
invention overcomes this problem by providing a
system and method for controlling the actions of a
host computer system using a simple telephone call,
and in particular, for triggering a host computer
5 system to make a connection to a computer network,
such as the Internet, whereupon a remote user, or
multiple remote users, can then connect to the host
system over the network, thereby circumventing the
need for a costly dedicated connection to an ISP.
Previous systems for controlling a host
computer system over a telephone connection are
limited to two basic concepts: (1) remote power-up;
and (2) remote access. The remote power-up systems
include a circuit which detects a telephone call and
applies power to the host computer. According to
- 2 -
CA 02410039 2002-12-06
-3-
these prior art systems a telephone ring detector
and power switch are interposed between the power
outlet and the remote computer system to be
activated. When a telephone call is detected on the
phone line connected to the ring detector, the power
switch is activated and the host computer's power
supply is connected to the power outlet. One
disadvantage of these prior art systems is that they
are limited to simply powering up the computer.
These systems do not provide any mechanism, signal,
or intelligence which causes the host computer to
perform a sequence of predetermined actions based on
the detection of the phone call.
An additional disadvantage of these prior art
_5 systems is that there is no means to trigger a
program, or programs, at the host computer system
while the host system is activated, transparent to
other users of the system. Furthermore, the remote
power-up systems inherently disrupt any other users
of the host system, and are therefore useful only
for single-user computer systems, or Personal
Computers (PC's).
Previous remote access systems pernlit a
remotely located computer system to gain access to a
host system through an authorization device, and
- 3
CA 02410039 2002-12-06
-4-
thereafter to control the actions of the host
system. According to these types of systems, a user
at a remote location from the host computer system
gains access over a telephone connection between the
two computers. Each computer includes a modem for
communication over the phone line. In order to
selectively permit access to certain users, but deny
access to others, these remote access systems
require the use of special hardware on both ends of
the telephone connection, wherein the special
hardware is an access control device connected
between the respective computer and modem on each
end of the connection. The hardware devices perform
authorization handshaking using special codes, and
if the codes match, the hardware devices permit
access to the modem resources connected to the two
computers. After the hardware devices have
performed the authorization handshaking, the user of
the local system then accesses the host system and
controls its operations directly, as though he were
located at the host system.
These prior art remote access systems assume
that the control of the host system is to be carried
out by a local computer after access is authorized.
One disadvantage of these systems is that they do
- 4 -
CA 02410039 2002-12-06
-5-
not teach that a remote user can trigger a
predetermined sequence of events at a host system
using a ring signal on a phone line. For any
control to occur in these systems, the host computer
must actually answer the phone call and create a
logical connection between the host and local
systems.
An additional disadvantage of these systems is
that they are limited to access by one remote user
at a time per modem, since each remote user creates
a dedicated phone line connection to the modem
resource of the host system. The only way to
circumvent this shortcoming is for the host system
to provide a modem-pool of resources. Such a modem-
pool can support multiple remote users, but
increases the expense and complexity of the host
system. These systems do not teach that multiple
remote users can access the services of the host
system simultaneously through a single
communications link.
Another disadvantage of the previous remote
access systems is their inherent bandwidth
limitation. Because the remote access systems are
limited to communication using modems on either end
of the connection, the speed of communication will
- 5 -
CA 02410039 2002-12-06
-6-
be limited to the speed of state of the art analog
modems, which is currently 28.8Kbps. These systems
do not teach the ability to create an Internet
connection using TCP/IP (Transfer Control
Protocol/Internet Protocol), such that the remote
user could connect at a much higher bandwidth using,
for example, a 56KB or 128K8 ISDN connection, or
even a full Tl 1.5N!8 connection. The previous
remote access systems are limited to analog modem
communication.
Another prior art system combines the teachings
of the remote access systems and the remote power-up
systems by providing a remote power-up device that
is triggered by a phone call, and which "boots" a
computer system and causes an access control program
stored in the "boot drive" to be activated. Like
the other remote access systems, this system assumes
that the control of the host system is to be carried
out by a local computer. The host system is
controlled only after the access software permits
access to the local user by first answering the
telephone call and then establishing a logical
connection between the modem of the host system and
that of the local computer. This system does not
teach the triggering of a predetermined sequence of
- 6 -
CA 02410039 2002-12-06
events at a host system using a telephone ring
signal. In addition, this system requires two
computer systems, one at either end of the
connection, and also requires that the host computer
system be powered down before any type of control or
communication can take place. This system does not
teach multiple-user remote access through a single
communications device. Furthermore, this system is
limited to analog modem communication, as above, and
therefore cannot support high bandwidth
communications .
Therefore, there remains a need for a system
and method wherein a predetermined program, or
sequence of events, can be triggered for execution
at a host computer system using a telephone ring
signal.
There remains a further need for such a system
and method wherein the predetermined program is a
script of commands which cause the host computer
system to connect to the Internet.
There remains a further need for such a system
and method wherein after the host computer system
has made a connection to the Internet, a user at a
remote location, or multiple users at multiple
remote locations, can use local computer systems to
CA 02410039 2002-12-06
'8-
connect to the host system and thereby gain access
to the services of the host system.
There remains a further need for such a system
and method wherein the host computer system can be
triggered by a ring signal without effecting the
other operations of the host computer.
There remains a further need for such a system
and method wherein a plurality of predetermined
programs are stored at the host system, and,
following the ring signal, a trigger identification
code is transmitted over the phone line by the
remote user indicating which of the plurality of
predetermined programs is to be executed.
There remains a further need for such a system
and method wherein a user validation code is
transmitted on the phone line after the ring signal
by the remote user, and the host system
authenticates the user validation code prior to
executing the predetermined program.
There remains a further need for such a system
and method which enables higher bandwidth
connections to be created between remote users and
host systems via the Internet, independent of analog
modem technology.
_ g _
CA 02410039 2002-12-06
_g_
In addition, there remains a need for a method
of connecting a host computer system to the Internet
based on a request for services by a remote user,
such that the remote user can connect to the host
system using a local computer, where the connection
is caused by a third computer system that receives
the request for services from the remote user, and
which dials the phone number of a phone line
connected to the host system.
There remains a further need for such a method
where the third computer system is a server computer
at an ISP site that services the host system,
wherein the ISP server computer includes software
modules that automatically detect requests for
services by remote users, and which determine
whether the host system is already connected to the
network, and if not, which then generate a ring
signal on a telephone line connected to the host
system, thereby triggering the host system to
connect to the Internet for access by the remote
user.
There remains a further need for such a method
where the third computer system is a network server
that the remote user connects to, where the network
server contains a list of host systems that can be
_ g
CA 02410039 2002-12-06
- 1 ~ -
connected to the Internet by the server, and where
the remote user requests the services of a specific
host system, wherein the network server then
generates a ring signal on a telephone line
connected to the specified host system and verifies
that the host system has connected to the network.
SUN~lARY OF THE INVENTION
The present invention overcomes the problem of
having to lease and support a dedicated connection
to the Internet, and meets the needs noted above by
providing a system and method for controlling a host
computer system using a telephone ring signal. In
particular, the present invention provides a system
and method for remotely triggering a predetermined
program, or sequence of events, at a host computer
system using a ring signal, wherein the sequence of
events is, for example, a stored script of commands
that cause the host system to connect to a computer
network, such as the Internet. Using the present
invention, a small company or individual can achieve
the benefits of having their own Internet server
computer without having to shoulder the expense and
complexity of a dedicated link to an Internet
Service Provider.
- 10 -
CA 02410039 2002-12-06
-11-
According to the present invention, a system
and method is provided for triggering a
predetermined program stored at a host computer
system using a telephone ring signal, wherein the
host system includes a ring detection and triggering
circuit connected to a phone line for detecting a
ring signal on the line, and for generating a
trigger signal to the host system indicating that a
ring signal has been detected. The host system
receives the trigger signal and executes a
predetermined program stored at the host system.
The predetermined program could be, fox example, an
activation script of commands that create a
connection between the host system and the Internet.
According to another aspect of the present
invention, the host system includes a background
executing control signal monitoring process that
monitors an interface port of the host computer
system, such as a serial port, waiting for a trigger
signal indicating that a ring signal has been
detected on the phone line, and subsequently causes
the execution of at least one predeternnined program
stored at the host system.
- 11
CA 02410039 2002-12-06
-12-
According to another aspect of the present
invention, multiple predetermined programs are
stored at the host system, and in order to select
which program is to be executed, a trigger
identification code is transmitted after the ring
signal by the remote user, the code indicating which
of the multiple programs is to be executed.
According to another aspect of the present
invention, a user validation code is transmitted
after the ring signal by the remote user, and the
host system then validates the user code and if the
code is valid, the host system permits triggering of
the predeternlined program.
According to another aspect of the present
_5 invention, a method is disclosed for detecting the
network address of a host computer system at an
Internet Service Provider (ISP) site, for
determining whether the host computer system is
currently connected to the Internet, and if not so
connected, for dialing a phone number associated
with a phone line connected to the host system,
thereby triggering the host computer system to
execute a predetermined program which causes the
host computer system to connect to the Internet.
12 -
CA 02410039 2002-12-06
-13-
According to another aspect of the present
invention, a method is disclosed for a remote user
to select and trigger a host system to connect to
the Internet by connecting to a network server, such
as a Web Server, wherein the web Server includes a
list of host computer systems that can be triggered
for connection to the Internet by the network
server, and wherein the remote user selects the host
system to be triggered and the network server dials
a phone number associated with a phone line
connected to the host system, thereby triggering the
host computer system to execute a predetermined
program which causes the host system to connect to
the Internet.
An advantage of the present invention over the
prior art systems and methods is that it permits
various remote users to gain access to the services
of host computer systems without requiring that the
host computer system be connected to a computer
network, such as the Internet, using a costly
dedicated communication link.
Another advantage of the present invention is
that it enables a remote user to gain access to a
host computer system without having to pay for long
distance telephone charges associated with a direct
- 13 -
CA 02410039 2002-12-06
-14-
connection, since the remote user can trigger the
host system to connect to the Internet, and the
remote user can then use a local computer to access
the services of the host system. No long distance
telephone link is required, and since the Internet
is a global network, a remote user could be anywhere
in the world, and could gain access to the host
system without having to pay for a very expensive
long distance telephone call.
Another advantage of the present invention is
that it provides a method whereby Internet Service
Providers (ISPs) can activate a host computer system
automatically upon detection of a data packet which
is intended for the host computer. Using this
method, a remote user does not have to make a
telephone call to trigger the host system to connect
to the Internet, but instead sends data packets over
the network as if communicating to a host system
that has a dedicated link. These data packets are
then detected by the ISP server computer at which
the host computer has an account set up, and the
server computer determines whether the host system
is connected to the Internet. If the host system is
not connected, the ISP rings a phone line connected
to the host system, thereby triggering a connection
- 14 -
CA 02410039 2002-12-06
signal to a host computer system which causes the host
computer system to execute a predetermined program, the
circuit comprising:
a solid state data access arrangement including optical
isolation circuits connected to the phone line, and further
including a ring detector circuit that generates a signal on a
ring indicator signal line when the phone line is ringing;
a DTMF transceiver, including a digital databus and an
analog input/output port, wherein the analog input/output port
is connected to the solid state data access arrangement in
order to receive and transmit DTMF tones over the phone line;
and
a microcontroller connected to the digital databus and
further connected to the ring indicator signal line, wherein
the microcontroller includes a serial port connection to the
host system and wherein the microcontroller is programmed to
monitor the ring indicator signal line for a phone call and
generates a trigger signal to the host computer system over
the serial port, thereby triggering the execution of the
predetermined program.
A system for triggering a program stored at a host
computer system using a telephone ring signal, comprising:
means for detecting the telephone ring signal on a phone
line coupled to the host computer;
means for generating a trigger signal to the host
computer system indicating that a phone call has been
detected;
means for receiving the trigger signal at the host
computer system; and
means for executing the program stored at the host system
in response to receiving the trigger signal.
A system for connecting a host computer system to a
network based on a determination that the host computer is not
-15a-
CA 02410039 2002-12-06
presently connected to the network, the host computer system
including an activation program which when executed causes the
host computer system to connect to the network, the system
comprising:
means for detecting destination information contained in
data packets being transmitted over the network, wherein the
destination information corresponds to the host computer
system;
means for determining whether the host computer system is
presently connected to the network;
means for dialing a telephone line associated with the
host system when it is determined that the host computer
system is not presently connected to the network; and
said host computer system including means for detecting a
ring signal on the telephone line associated with the host
computer system and for triggering the activation program
stored at the host system, thereby causing the host system to
connect to the network.
A method of connecting a device to a network, comprising
the steps of:
detecting destination information in data being
transported over the network, the destination information
being associated with the device to be connected to the
network;
determining whether the device is presently connected to
the network; and
if the device is not connected to the network, then
transmitting an activation signal to the device, which causes
the device to execute an activation program that connects the
device to the network.
A method of remotely triggering a device to make a network
connection, comprising the steps of:
a remote user connecting to a network server that
-15b-
CA 02410039 2002-12-06
displays one or more devices that can be remotely triggered to
connect to the network;
selecting one of the devices;
determining whether the device is already connected to
the network; and
if the device is not connected to the network, then
transmitting an activation signal from the network server to
the device, which causes the device to execute an activation
program that creates a connection to the network.
A system for connecting a device to a network,
comprising:
a detector for detecting destination information being
transmitted over the network;
a processor for comparing the detected destination
information with destination information associated with the
device;
a connection determination program for determining
whether the device is presently connected to the network; and
a triggering module for transmitting an activation signal
to the device when the processor determines that the detected
destination information corresponds to the device, and the
device is not presently connected to the network.
As will be appreciated, the invention is capable of other
and different embodiments, and its several details are capable
of modifications in various respect, all without departing
from the invention. Accordingly, the drawings and description
are to be regarded as illustrative in nature and not
restrictive.
According to a further aspect of the present invention,
there is provided a system for connecting a plurality of
remote computers to a data network, wherein the plurality of
remote computers are disconnected from the data network,
comprising:
a database for storing information regarding the
plurality of remote computers, the information including, for
each of the plurality of remote computers, a routing address
associated with the data network, and a telecommunications
15c
CA 02410039 2002-12-06
address associated with a telecommunications network;
an access detector module coupled to the data network for
detecting routing addresses embedded in data packets being
transmitted over the data network;
a database decision module coupled to the database and
the access detector module for comparing the detected routing
addresses from the access detector module with the routing
addresses stored in the database to determine if the data
network is attempting to route data packets to one of the
l0 disconnected remote computers; and
a dialer module coupled to the database decision module
for transmitting an activation signal to at least one of the
disconnected remote computers using the stored
telecommunications address for the remote computer if the
database decision module determines that the data network is
attempting to route data packets to the at least one
disconnected remote computer;
wherein the activation signal causes the at least one
disconnected remote computer to execute an activation script
that causes the remote computer to create a connection to the
data network so that the data packets can be routed to the
remote computer.
According to yet a further aspect of the present
invention, there is provided a method of transmitting data
from a first computer system to a second computer system
through a data network, comprising the steps of:
transmitting data from the first computer system to the
data network, wherein the data is addressed using a network
address associated with the second computer system;
detecting the data transmitted from the first computer
system at a host system coupled to the data network, wherein
the second computer system is associated with the host system;
the host system determining whether the second computer
system is connected to the data network;
if the second computer system is not connected to the
data network, then transmitting an activation signal from the
host system to the second computer system, wherein the
15d
CA 02410039 2002-12-06
activation signal causes the second computer system to connect
to the data network; and
receiving the data from the first computer system at the
second computer system.
BRIEF DESCRIPTION OF THE DRAWINGS
15e
CA 02410039 2002-12-06
-16-
The above advantages will become apparent from
the following description when read in conjunction
with the accompanying drawings wherein:
FIG. 1A is a block diagram of a system
according to the present invention;
FIG. 1B is a circuit diagram of a ring
detection and triggering circuit according to the
present invention;
FIG. 2 is a data flow diagram of the
control signal monitor program;
FIG. 3A is a block diagram of an advanced
system according to the present invention;
FIG. 3B is a circuit diagram of an
advanced ring detection and triggering circuit
according to the present invention;
FIG. 4 is a block diagram of a system
located at an Internet Service Provider (ISP) site
that is used to detect and determine whether a host
system is connected to the Internet, and if not
connected, to dial the phone number associated with
the host system.
FIG. 4A is a flow chart of the steps
carried out by the system located at the ISP of Fig.
4 which is used to detect and determine whether a
- 16 - '
CA 02410039 2002-12-06
-17-
host system is connected to the Internet, and if not
connected, which dials the phone number associated
with the host system.
FIG. 5 is a flow chart of an alternative
method showing the selection, connection and
verification steps of a remote user contacting a
network server to trigger a specified host system to
connect to the Internet.
DETAILED DESCRIPTION OF THE DRAWINGS
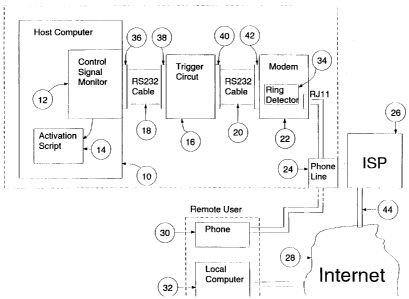
Referring now to the drawings, Figure 1A shows
a block diagram of a system according to the present
invention. Block 10 is a host computer system, such
~_5 as a personal computer, workstation, or mainframe
computer system, and which preferably is operating a
multi-tasking operating system, such as Unix,
Microsoft Windows 95, or Microsoft Windows NT. The
host computer system includes memory for storing a
variety of applications, including a control signal
monitor program 12, and at least one activation
script 14. The control signal monitor program 12 is
a background executing application that monitors a
serial port, or other interface port, of the host
system 36 for the presence of a trigger signal, and
in response to the trigger signal causes the
17 -
CA 02410039 2002-12-06
-18-
activation script 14 to be executed. The control
signal monitor program is discussed more fully below
in connection with Figure 2.
Connected to one serial port 36 of the host
computer 10 is a trigger circuit 16, discussed more
fully below in connection with Figure 1H. The
trigger circuit has two ports, one port 38 connected
to the serial port 36 of the host computer, and a
second port 40 connected to a serial port 42 of the
modem 22, also using a serial connection. The
serial connections in Figure 1A are preferably RS
232 connections, but could be any type of serial or
other interface connection. Trigger circuit 16 is
connected to the host computer system and the modem
using respective wiring harnesses 18 and 20, which
are preferably 25-wire connections, per the RS-232
standard. The modem 22 includes ring detector 34,
and is connected to an external phone line 24 via a
standard RJ11 phone jack.
In this embodiment of the present invention the
ring detection function 34 is carried out internally
within the modem 22. All standard modems have the
ability to detect a ring signal on a telephone line,
and generate a standard Ring Indicator (RI) signal
on pin 22 of the 25-pin modem interface, which is
- 18 -
CA 02410039 2002-12-06
-19-
preferably a standard RS-232 interface. The trigger
circuit 16, discussed in more detail below, passes
the majority of the modem signals on wiring harness
20 through to the serial port 36 of the host system
directly, so that the host system can communicate
over the phone line using the modem 22. The trigger
circuit 16 responds to the Ring Indicator (RI)
signal on pin 22 of the modem interface, and
generates a trigger signal to the host system 10
using one of the pins of the standard RS-232
interface, preferably pin 8.
External to the host system is an Internet
Service Provider (ISP) 26, which is preferably a
server computer with a modem pool, and which
provides dial-in and dedicated access to its
customers in order to make a connection to the
Internet 28. Also external to the host system is at
least one remote user, where the remote user has
access to a phone 30, and a local computer system
32.
The system according to Figure 1A operates as
follows. The remote user dials the phone number of
the phone line 24 associated with the host computer
system 10, causing a ring signal on the phone line
24. The ring detection circuit 34 of modem 22
- 19 -
CA 02410039 2002-12-06
-20-
detects the ring signal and passes this signal on to
the trigger circuit 16. The trigger circuit 16
detects the ring signal from the ring detector 34
and generates the trigger signal to the host
computer system 10 via the host computer system's
serial port 36. The control monitor program 12 then
detects the trigger signal on serial port 36 and
causes the activation program 14 to be executed.
The activation program 14 creates a connection
through the modem 22 and ISP 26 to the Internet 28.
The remote user can then make a connection to the
host system 10 over the Internet 28 using local
computer 32.
In this manner, a remote user can trigger a
host computer system to connect to the Internet
using a simple telephone ring signal, and
thereafter, the remote user can connect to the host
system over the Internet using a local computer,
thereby dispensing with the need to have a dedicated
link associated with the host system, and also
dispensing with the need to pay for a long distance
phone call. In addition, since the control monitor
program is a background executing application, the
actions of triggering the host system to make a
20 -
CA 02410039 2002-12-06
-21-
connection to the Internet can occur without
disrupting other users of the host system.
Referring now to Figure 1B, a circuit diagram
of the trigger circuit 16 is set forth. As
discussed previously, the trigger circuit 16 has two
ports, one port 38 connected to the host computer's
serial port 36, and the second port 40 connected to
the modem serial port 42. As set forth in Figure
1B, the majority of the signals associated with the
serial communications connection are simply passed
through the trigger circuit 16, from the modem port
42 to the host computer port 36.
According to the RS-232 serial communications
standard, pin 22 of the serial interface is the Ring
Indicator (RI) signal. The RI signal is an active-
high signal which is asserted when the ring
detection circuitry 34 of the modem 22 detects a
ring signal on the phone line 24.
Trigger circuit 16 monitors the RI signal 54 on
pin 22, and feeds the signal into a one-shot timer
58, which is preferably a type 555 timer. When the
RI signal 54 transitions from low to high on pin 22,
the one-shot timer 58 generates a pulse on its OUT
pin, wherein the duration of the pulse is determined
- 21 - '
CA 02410039 2002-12-06
-22-
by the external RC-network 60, and the resistor-
switch network 52.
The resistor-switch network 52 is used to
create pulses of varying duration, depending on the
particular requirements of the host system. Certain
host systems may require a longer trigger signal,
and therefore in order to avoid having a custom
trigger circuit for each type of host system, the
resistor-switch network 52 is provided in order to.
accommodate various host computers. Using the
resistor-switch network 52, the trigger pulse width
can be preferably varied between 10 and 70 seconds.
The pulse from the one-shot timer 58 is fed
into an optical relay 50, which is a normally
closed, single-throw double-pole device. The output
of the optical relay 50 is connected through jumper
J5 to pin 8 on the host computer port 36, which is
the trigger signal 56 to the host system. Using
jumpers J1-J6, an alternative connection using pin 5
as the trigger signal 56 can be made. When the one-
shot timer 58 is triggered by the transition on pin
22, the relay 50 is driven active, thereby opening
the relay and connecting the relay output to a high
voltage level. This level is maintained on the
22 -
CA 02410039 2002-12-06
-23-
output of the relay until the one-shot timer 58 OUT
signal returns to its inactive state. When this
occurs, the relay 50 returns to its normally closed
state, which then reconnects the trigger signal line
on pin 8 straight through from the modem port 42 to
the host computer port 36.
Referring now to Figure 2, a data flow diagram
of the control signal monitor program 12 is
provided. Exemplary source code for the control
signal monitor program 12 is set forth in this
application as Appendix A. The control monitor
program 12 begins in a non-running state 70. When
the monitor program 12 is executed it enters a state
74 where it is constantly monitoring one of the
serial ports 36 of the host computer system 10,
waiting for the trigger signal 56, which in the
present embodiment is pin 8 of the serial port 36.
In the case of a system where there is only a single
activation script 14, the control monitor detects
the trigger signal 56 on the serial port 36 and
causes the activation script 14 to be executed 76.
When the sequence of commands that comprise the
activation script 14 has been executed, the control
monitor 12 returns to state 74 where it is waiting
for another trigger signal.
- 23 -
CA 02410039 2002-12-06
-24-
In the case of a system where multiple
activation scripts 14 can be triggered for execution
(as set forth in Figure 3A), the control monitor
detects a trigger signal 56 at state 74, and then
checks for a trigger identification value on the
serial port 36 data lines. The trigger
identification value indicates which script is to be
executed, and is transmitted by the remote user when
making the phone call to trigger the host system.
The control monitor program 12 performs a "lookup"
into store 72 which indexes the activation scripts
14 by trigger identification value in order to
determine which script to execute.
The activation script 14 can be any sequence of
_5 commands which cause the host system 10 to perform
some specified series of actions, but in the
preferred embodiment is a sequence of commands which
cause the host system 10 to make a connection
through a communications device 22 to the Internet
28. Such command sequences are well known in the
art of data communications, in particular in causing
a host system to connect to a specific network, such
as the Internet.
Referring now to Figure 3A, an advanced system
according to the present invention is described.
- 24 -
CA 02410039 2002-12-06
-25-
The system of Figure 3A includes the same elements
as that in Figure 1, except that the ring detection
function is carried out by the advanced trigger
circuit 16A (discussed more fully below in
connection with Figure 3H), and a phone line
splitter 80 is added which connects the phone line
24 to both the modem 22 and the advanced trigger
circuit 16A using standard RJ11 phone jacks.
One advantage of this embodiment is that the
20 communication device 22 does not have to be external
to the host computer system 10, as shown, and the
advanced ring detection and triggering circuit 16A
can answer the phone call in order to process
additional information transmitted by the remote
user, such as a user validation code, or the trigger
identification values discussed above. The
preferred embodiment set forth in Figure 3A shows
the advanced triggering circuit 16A and an external
modem~22. An alternative embodiment (not shown)
would use an Internal modem within the host system
10, and there would therefore be no connection
between the trigger circuit 16A and the external
modem 22.
The operation of the advanced system in Figure
3A is identical to that of the system in Figure 1A,
- 25 -
CA 02410039 2002-12-06
-26-
except that in the advanced system the ring
detection and triggering circuit 16A performs
internal ring detection 34, and includes circuitry
that enables the circuit 16A to answer the phone
line 24 and process additional information
transmitted by the remote user, such as the user
validation signals or the trigger identification
value. In addition, the advanced ring detection and
triggering circuit 16A has the ability to transmit
DTMF (Dual Tone Multi-Frequency) tones back onto the
phone line 24 in order to signal the remote user
that the triggering operation has been carried out
by the host system 10.
Referring now to Figure 3B, the advanced ring
detection and triggering circuit 16A is described.
In the preferred embodiment this circuit is a three-
port device, two ports 38, 40 for establishing the
25-pin RS232 serial connection between the host
system port 36 and the external modem port 42, and a
third port for connecting to the phone line 24 using
a standard RJ11 phone jack. This three-port device
has two modes of operation, standard and advanced.
The mode in which the advanced ring detection
and triggering circuit 16A operates is selected
using the RJ11/RS232 Selector Switch 98, which is a
- 26 - '
CA 02410039 2002-12-06
-27-
standard DIP switch. The signal from the RJ11/RS232
selector switch 98 is input to the model selector
circuit 104, which routes the signal lines from
either the modem input port 40 or from the internal
microcontroller 100 onto the output port 38 which
connects to the serial port of the host computer 36.
In the standard mode of operation the circuit
operates in the same fashion as the circuit of
Figure 1B. The serial lines from the modem port 42
are routed through selector circuit 104 onto the
lines connected to host serial port 36. The
difference between the operation in the standard
mode and the operation of the circuit in Figure 1A
is that the ring detection is done in the advanced
ring detection and triggering circuit 16A by ring
detector 34 which generates an External Ring
Indicator signal 54 to microcontroller 100. The
microcontroller 100 senses this signal 54 and
generates a trigger signal that is routed through
selector circuit 104 onto pin 8 of the output port
38.
In the advanced mode of operation the signals
from the internal microcontroller 100 are routed
through the selector circuit 104 onto the output
port 38 for connection with the host system serial
- 27 -
CA 02410039 2002-12-06
-28-
port 36. This connection enables serial
communication between the host system 10 and the
microcontroller 100 of the advanced circuit 16A. In
this mode of operation the external modem 22 is not
used for making a connection to the Internet, but
rather an internal communication device within the
host system 10 is used to make the connection. This
internal communication device (not shown) could be
an analog modem, ISDN modem, or any other type of
communication device. In the advanced mode of
operation the advanced ring detection and triggering
circuit 16A is capable of answering the phone line
24 and of processing additional signals transmitted
by the remote user. In addition, the circuit 16A
can transmit DTMF signals back to the remote user
over the phone line 24.
These advanced features are carried out using
the following circuit components: (1) solid state
data access arrangement (DAA) 90; (2) signal
conditioning circuits 92; DTMF transmitter and
receiver 94; microcontroller 100; and TTL/RS232
level converter 102. The solid state DAA 90
includes ring detector 34, which detects a ring
signal on the phone line 24 and asserts the External
Ring Indicator signal 54 to the microcontroller 100.
- 28 -
CA 02410039 2002-12-06
-29-
The solid state DAA 90 also provides standard
interface and isolation circuitry required by the
FCC for communication over a telephone line.
Signal conditioning circuits 92 convert the
differential signals required for use by the DAA 90
into single ended signal levels compatible with the
dual tone multi-frequency (DTMF) transmitter and
receiver 94. The DTMF transceiver 94 receives
signals from the DAA 90 in DTMF format and converts
the signals into a digital format for transmission
to the microcontroller 100 over databus 96.
Likewise, the DTMF transceiver 94 receives a digital
signal from the microcontroller 100 over databus 96
and converts the digital signal into a DTMF signal
for transmission to the DAA circuit 90 which then
asserts the DTMF tones onto the phone line 24. In
this manner the microcontroller 100 can both send
and receive standard DTMF signals on the external
phone line 24.
Microcontroller 100 preferably includes a
central processing unit (CPU) core, temporary
storage, such as a random access memory (RAM), and
permanent storage, such as an Erasable Programmable
Read Only Memory (EPROM). The software that enables
the microcontroller to: (1) handle the signal on the
- 29 -
CA 02410039 2002-12-06
-30-
External Ring Indicator 54 line; (2) process the
incoming DTMF signals transmitted by the remote
user; and (3) determine what signals to transmit
back to the remote user; is either permanently
stored in the EPROM of the microcontroller, or is
downloaded from the host system 10. In the later
case, the EPROM only contains a small software
kernel which, on power up, instructs the
microcontroller 100 to download the software to
control the advanced operations discussed above from
the host system 10, via the serial connection 18.
The final circuit component depicted in Figure
3B is the TTL/RS232 converter 102. The TTL/RS232
level converter 102 takes the 0-5V TTL signals from
the microcontroller and converts them into the RS232
voltage levels that are part of the RS232 standard.
This circuit simply boosts the TTL serial port
voltage levels on the microcontroller to levels
which are compatible with the RS232 standard.
Alternatively, the serial connection could be an
RS422 or RS485 connection, in which case a TTL/RS422
or TTL/RS485 level converter would be required.
The advanced ring detection and triggering
circuit 16A operates as follows. When a phone call
is detected by ring detector 34 an active signal
- 30 -
CA 02410039 2002-12-06
-31-
level is asserted on the External Ring Indicator
line 54 to the microcontroller 100. The software
controlling the microcontroller causes the
microcontroller to wait for this signal 54 to become
active, and when detected the microcontroller 100
asserts an active level on the DCD (Data Carrier
Detect) line which is routed through the TTL/RS232
level converter 102 and the router 104 onto pin 8 of
the output port 38 to become the trigger signal 56.
The trigger signal 56 is detected by the control
monitor program 12 running on the host system 10,
and the control monitor then waits for additional
information to be transmitted over the serial port
36 from the advanced unit 16A.
After detection of the ring signal, the
advanced ring detection and triggering circuit 16A
then answers the phone line and looks for additional
DTMF tones being transmitted from the remote user.
These tones could represent either a user validation
sequence, or a trigger identification value. The
user validation signals are preferably a standard
Unix-type "login/password" sequence, where, for
example, the remote user transmits a mufti-digit
login number and a corresponding mufti-digit
password in the form of a series of DTMF tones.
31 - '
CA 02410039 2002-12-06
-32-
These tones are received by the DAA 90, passed
onto the DTMF transceiver 96 where they are
converted from DTMF format to a digital word and
transmitted to the microcontroller 100 over databus
96. The microcontroller 100 then preferably
transmits the login/password sequence to the control
monitor program via the serial communication port
38-36 for authorization. Host system 10 further
includes a datafile of valid login/password
sequences that is accessed by the control monitor
program 12 in order to determine whether the
transmitted sequence is valid. Alternatively, the
login/password sequence could be authorized by the
software stored in the advanced ring detection
circuit 16A directly. In this alternative case the
valid login/password sequences could be either
stored permanently in the EPROM of the advanced
circuit, or the microcontroller 100 could be
programmed to access the datafile of valid
login/passwords stored on the host system 10, using
the serial communications port 38. Assuming
that the user validation signals are received,
processed and then transmitted to the host system
for verification, the host system then transmits a
signal back to the advanced control unit 16A
- 32 -
CA 02410039 2002-12-06
-33-
indicating that the remote user has been verified.
The microcontroller 100 then examines the databus
96 to determine whether additional tones have been
transmitted that represent the trigger
identification value. As discussed above, the
trigger identification value permits the selection
of one of many scripts for execution by the host
system 10. This trigger identification value is
received by the microcontroller 100 and transmitted
onto the host system 10 where the control monitor
program reads the value from the serial port 36 and
uses it as the index into store 72 to determine
which activation script 14 to execute.
After the control monitor program 12 has
executed the selected script 14, a signal is sent to
the advanced control unit 16A indicating that a
script has been triggered. The microcontroller 100
receives this signal and then transmits a specific
tone or sequence of tones using the DTMF transceiver
96 and DAA circuit 90 back onto the phone line 24,
indicating to the remote user that the selected
script has been executed. In the preferred
embodiment, the script 14 creates a connection
between the host system 10 and the Internet 28,
using an internal communications device (not shown)
33
CA 02410039 2002-12-06
-34-
connected to the host system 10. The internal
communications device could be another analog modem,
or could be an ISDN digital communications device,
and is connected over a phone line to an ISP, so as
to create a connection to the Internet.
Using the advanced mode of operation, a remote
user can trigger one or more of a plurality of
scripts 14 stored at a host computer system 10, and
can receive audible feedback from the system that
the command has been executed. In addition, the
advanced mode provides for security and user
authentication through the verification of the user
login/password validation signals optionally
transmitted by the remote user.
Referring now to Figure 4, a system for
connecting a host computer system to a network based
on a determination that the host computer is not
presently connected to the network is set forth.
The system of Figure 4 includes a network
connection, or pipe 44, to the Internet over which a
multitude of data packets are being transmitted.
Each data packet contains routing information, such
as an IP address of a host system, or an EMAIL
address of a particular user, or some other unique
destination information that server computers
- 34 -
CA 02410039 2002-12-06
-35-
connected across the network use to direct and route
the packet to its destination.
The present invention uses this routing
information in order to determine whether the
destination computer, i.e. the host computer system,
is connected to the network, and if a determination
is made that the destination computer is not
currently connected, a phone call is made to the
host computer in order to trigger a connection to
the network for subsequent delivery of the data
packet. This triggering step assumes that the host
system 10 has a triggering circuit according to
Figures 1A or 3A, discussed above, that detects a
signal on the corresponding phone line 24 and
triggers a script of commands which cause the host
system to connect to the Internet.
The ISP host server system includes a number of
software and database components, a server computer,
and a pool of modems. The ISP server computer is
connected to the Internet via the network pipe 44,
which could be a dedicated connection, such as a T1
or T3 high bandwidth telephone connection.
The ISP server includes an Access Detector
Program 110, which is a software module that
constantly monitors the destination information of
- 35 -
CA 02410039 2002-12-06
-36-
data packets transmitted over the network pipe 44,
and extracts the destination address information
which corresponds to customers of the ISP. The
information extracted by the Access Detector Program
110 is routed to a Host Collection Module 112 which
is a software module that collects and stores the
destination information of detected packets that
correspond to customers of the ISP. This
information is then routed to a Raw Access Log 114
where it is stored and time stamped so that the ISP
server system knows when access to a customer's host
computer system 10 has been requested.
In addition to the Raw Access Log 114, the ISP
Host Server System includes an Organized Database
122, which stores a variety of information such as
which ISP customers have paid for the remote
triggering service, how many access requests for a
particular host have been logged into the Raw Access
Log, how many trigger signals have been generated,
the phone numbers of customer host systems 10,
billing information, etc.
The information stored in the Raw Access Log
114 and the Organized Database 122 is used by the
Database Decision Module 116 to determine whether to
trigger a specific host system 10 to connect to the
- 36 -
CA 02410039 2002-12-06
-37-
Internet by dialing a phone number associated with
the system. The Database Decision Module 116
examines the destination information stored in the
Raw Access Log 114 and compares it with the
information stored in the Organized Database 122.
If destination information is detected which
corresponds to a customer of the ISP referenced in
the Organized Database 122, the Database Decision
Module extracts the phone number of the host system
10 to be triggered from the Organized Database 122.
The ISP server computer then dials the phone number
associated with the customer's host computer system
10, using one of the modem's in the server modem
pool 120, thus creating a ring signal on the phone
line 24 connected to the host computer system 10.
As depicted in figures 1A, and 3A, this ring signal
is detected by the host computer system 10, and
causes an activation script 14 stored at the host
computer system to be executed, wherein the
activation script 14 creates a connection between
the host computer system 10 and the Internet 28.
Following the establishment of .this connection, data
packets designated for the customer's host computer
system 10, can thereafter be routed to the host
system.
- 37 -
CA 02410039 2002-12-06
-38-
Using the system described above, a customer of
an ISP can maintain a host computer system that
appears to have a dedicated link to the Internet
even though in reality it does not, thus saving the
customer the cost and complexity of maintaining a
dedicated link. Using this system and method, the
remote user, or users, do not need to know the phone
number of the host system, as this information is
retained at the ISP server.
Referring now to Figure 4A, a flow chart of the
steps carried out at the ISP Host Server System is
set forth. In step 132, a remote user 132 transmits
data packets with specific system destination
information embedded in the packets over the
Internet. These packets are routed by various other
computer systems (not shown) and ultimately are
directed to the ISP Host Server. If the destination
host computer system is presently connected to the
Internet, the user is simply connected to the host
system in step 148 (i.e. the packets are directly
routed to the host system).
However, if the host computer system is not
presently connected to the Internet, then at step
136, the ISP Host Server detects the destination
information corresponding to a request to access a
- 38 -
CA 02410039 2002-12-06
-39-
specific host system. Following the detection of
the destination information, the ISP Host Server
collects this information and routes it to the Raw
Access Log in step 140. Following the update to the
Raw Access Log, the Database Decision Module 116
then determines, in step 138, whether the
destination information corresponds to a host system
that is supported by the remote triggering service
of the ISP. If the requested host system is not
supported, then in step 134 the ISP Host Server
takes no additional action. To the remote user,
this will appear as though the host system is simply
not connected to the network. However, if the
requested host system is supported by the ISP, then
in step 142 a "ping" function is executed. The
"ping" function is used to determine whether a
particular system is presently connected to the
Internet. This function is well known in the art of
digital communications, particularly communications
between computers via a network such as the
Internet. If the "ping" command yields a positive
result, then the requested host system is presently
connected to the Internet, and the ISP Host Server
merely updates the Organized Database to reflect the
request for services 144 and the remote user is
- 39
CA 02410039 2002-12-06
-40-
connected to the host system 148. If the "ping"
command indicates that the requested host system is
not presently connected to the Internet, then the
ISP Host Server makes a telephone call 146 to the
requested host system using a modem 150.
If the requested host system includes a ring
detection and triggering circuit (as discussed above
in Figures 1A and 3A), the ring signal will be
detected and the host system will be triggered to
make a connection to the Internet. After the ISP
Host Server dials the phone number of the requested
host system, the "ping" function is executed again
to verify that the host system has properly been
triggered to connect to the network. If the "ping"
indicates that the host system has connected, the
Organized Database 122 is updated, and the remote
user data packets are then routed to the host system
148. If the "ping" indicates that the host did not
connect, then the ISP Host Server will repeat steps
142-146 until the host system makes a connection, or
until some maximum number of redials is attempted.
Referring now to Figure 5, an alternative
method of connecting a host computer system to the
Internet is disclosed where the remote user triggers
the host system to connect to the Internet by first
- 40 -
CA 02410039 2002-12-06
-41-
connecting to a third party intermediary server.
According to this method, if the remote user cannot
directly make a connection to the desired host
system 172, because the host system is not presently
connected to the Internet, the remote user can
connect to a third party server 162, which could be,
for example, a Web-server.
The third party server is configured to present
the remote user with a list of host computer systems
that may be remotely triggered to connect to the
Internet. The remote user connects to the third
party server at step 162, and selects the system he
desires to communicate with at step 164. Stored at
the third party server are the corresponding phone
numbers and network addresses of the host systems
that can be remotely triggered. After the remote
user selects a host system 164, the third party
server executes a "ping" command to determine
whether the selected host system is presently
connected to the network. If the system is
connected, the third party system immediately
reports to the remote user at step 170 that the
selected system is available. The remote user can
then communicate directly with the host system. If
the "ping" command indicates that the selected host
- 41 -
CA 02410039 2002-12-06
-42-
system is not presently connected to the Internet,
then at step 168 the third party server then calls
the phone number associated with the selected host
system. Assuming that the host system is equipped
with the ring detection and triggering circuitry and
software of the present invention, the phone call
will cause the host system to execute a script that
will create a connection to the Internet. If the
host system is using the advanced ring detection
circuit of the present invention (Figure 3A), the
third party system could also be supplied with the
user validation signals and the trigger
identification value to transmit in order to cause
the proper connection to be established.
After the third party server dials the phone
number of the selected host system it loops back to
step 166 and executes the "ping" command in order to
verify that the proper connection has been made. If
the "ping" command is negative, the host system is
dialed again. The looping between dialing and
"ping"-ing continues until the host system makes a
connection, or until some maximum number of redials
is exceeded. After the "ping" command yields a
positive result, the third party system reports to
the remote user at step 170 that the selected host
- 42 -
CA 02410039 2002-12-06
-43-
system is now connected to the Internet. The remote
user can then directly communicate with the host
system 172.
The invention has been described with reference
to the preferred embodiments. Obviously,
modifications and alterations will occur to others
upon a reading and understanding of this
specification. It is intended to include all such
modifications and alterations insofar as they come
within the scope of the appended claims or the
equivalents thereof.
- 43 -
CA 02410039 2002-12-06
APPENDIX A: Page 1
//
// Software Developed by: Softell
//
// Purpose: Act as the "Signal Monitor Process" for Windows 3.1.1
//
// Module: monitor.h
//
// Description:
// This program opens a comm port and waits for CTS to change state.
// When it sees a change, it waits for another change back. When this happens,
// it compares the time agianst the time set in the jumpers, and then executes
the
// program specified on the command line.
//
#define WIN31 // this is a Windows 3.1 application
#define USECOMM // yes, we need the COMM API
#define STRICT // be bold!
#i
nclude < windows.h >
#include < commdlg.h >
#inciude < string.h >
#include "version.h"
#include "resource.h"
// constant definitions
#define GWW_NPTTYINFO 0
#define ABOUTDLG USEBITMAP 0
#define ATOM TTYINFO 0x100
// terminal size
#define MAXROWS 25
#define MAXCOLS 80
#define MAXBLOCK 80
#define MAXLEN TEMPSTR 81
#define RXQUEUE 4096
#define TXOUEUE 4096
CA 02410039 2002-12-06
APPENDIX A: Page 2
// cursor states
#define CS_HIDE 0x00
#define CS SHOW 0x01
// Flow control flags
#define FC_DTRDSR 0x01
#define FC RTSCTS 0x02
#define FC XONXOFF 0x04
// ascii definitions
#define 8EL 0x07
ASCII
#define _ 0x08
ASCII BS
#define _ OxOA
ASCII LF
#define CR OxOD
ASCII
#define _ 0x11
ASCII XON
#define _ 0x13
ASCII XOFF
// data structures
typedef struci tagTTYlNFO
int idComDev ;
BYTE bPort, abScreen[ MAXROWS * MAXCOLS ] ;
BOOL (Connected, fXonXoff, fLocaiEcho, fNewLine, fAutoWrap,
fUseCNReceive, fDispIayErrors;
BYTE bByteSize, bFIowCtrl, bParity, bStopBits ;
WORD wBaudRate, wCursorState ;
HFONT hTTYFont ;
LOGFONT IfTTYFont ;
DWORD rgbFGColor ;
int xSize, ySize, xScroll, yScroll, xOffset, yOffset,
nColumn, nRow, xChar, yChar ;
char CommandLine[128];
}TTYINFO, NEAR *NPTTYINFO ;
// macros ( for easier readability )
#define GETHINST( hWnd ) ((HINSTANCE) GetWindowWord( hWnd,
GWW HINSTANCE ))
#define COMDEV( x ) (x -> idComDev)
CA 02410039 2002-12-06
APPENDIX A: Page 3
#define PORT( x ) (x -> bPort)
#define SCREEN( x ) (x -> abScreen)
#define CONNECTED( x ) (x -> fConnected)
#define XONXOFF( x ) (x - > fXonXoff)
#define LOCALECHO( x ) (x -> fLocaiEcho)
#define NEWUNE( x ) (x -> fNewVne)
#define AUTOWRAP( x ) (x -> fAutoWrap)
#define BYTESIZE( x ) (x -> bByteSize)
#define FLOWCTRL( x ) (x -> bFlowCtrl)
#define PARITY( x ) (x -> bParity)
#define STOPBITS( x ) (x -> bStopBits)
#define BAUDRATE( x ) (x -> wBaudRate)
#define COMMANDLINE( x ) (x-> CommandLine)
#define CURSORSTATE( x ) (x -> wCursorState)
#define HTTYFONT( x ) (x - > hTTYFont)
#define LFTTYFONT( x ) (x -> IfTT'YFont)
#define FGCOLOR( x ) (x -> rgbFGColor)
#define XSIZE( x ) (x -> xSize)
#define YSIZE( x ) (x -> ySize)
#define XSCROLL( x ) (x -> xScroll)
#define YSCROLL( x ) (x -> yScroll)
#define XOFFSET( x ) (x - > xOffset)
#define YOFFSET( x ) (x -> yOffset)
#define COLUMN( x ) (x -> nColumn)
define ROW( x ) (x -> nRow)
#define XCHAR( x ) (x -> xChar)
#define YCHAR( x ) (x -> yChar )
#define USECNRECEIVE( x ) (x -> fUseCNReceive)
#define DISPLAYERRORS( x ) (x -> fDispIayErrors)
#define SET PROP( x, y, z ) SetProp( x, MAKEINTATOM( y ), z )
#define GET PROP( x, y ) GetProp( x, MAKEINTATOM( y ) )
#define REMOVE_PROP( x, y ) RemoveProp( x, MAKEINTATOM( y
// global stuff
char gszTTYClass[] _ "TTYWndClass"
char gszAppName[] _ "TTY" ;
HANDLE ghAccel ;
WORD gawBaudTable[] _ {0, 1 };
WORD gawParityTable[] _ {0, 1 };
WORD gawStopBitsTable[] _ {0, 1 };
CA 02410039 2002-12-06
APPENDIX A: Page 4
// function prototypes (private)
BOOL NEAR InitApplication( HANDLE ) ;
HWND NEAR Initlnstance( HANDLE, int ) ;
LRESULT NEAR CreateTTYinfo( HWND ) ;
BOOL NEAR DestroyTTYlnfo( HWND ) ;
BOOL NEAR ResetTTYScreen( HWND, NPTTYINFO ) ;
BOOL NEAR KiIITTYFocus( HWND ) ;
BOOL NEAR PaintTTY( HWND ) ;
BOOL NEAR SetTTYFocus( HWND ) ;
BOOL NEAR ScroIITTYHorz( HWND, WORD, WORD ) ;
BOOL NEAR ScroIITTYVert( HWND, WORD, WORD ) ;
BOOL NEAR SizeTTY( HWND, WORD, WORD ) ;
BOOL NEAR ProcessTTYCharacter( HWND, BYTE ) ;
BOOL NEAR WriteTTYBlock( HWND, LPSTR, int ) ;
int NEAR ReadCommBlock( HWND, LPSTR, int ) ;
BOOL NEAR WriteCommByte( HWND, BYTE ) ;
BOOL NEAR MoveTTYCursor( HWND ) ;
BOOL NEAR OpenConnection( HWND ) ;
BOOL NEAR SetupConnection( HWND ) ;
BOOL NEAR CIoseConnection( HWND ) ;
BOOL NEAR ProcessCOMMNotification( HWND, WORD, LONG ) ;
VOID NEAR GoModaIDialogBoxParam( HINSTANCE, LPCSTR, HWND, DLGPROC,
LPARAM ) ;
VOID NEhR FiIIComboBox( HINSTANCE, HWND, int, WORD NEAR *, WORD, WORD )
BOOL NEAR SelectTTYFont( HWND )
BOOL NEAR SettingsDlglnit( HWND )
BOOL NEAR SettingsDIgTerm( HWND
// function prototypes (public)
LRESULT FAR PASCAL export TTYWndProc( HWND, UINT, WPARAM, LPARAM
BOOL FAR PASCAL ,export AboutDIgProc( HWND, UINT, WPARAM, LPARAM ) ;
BOOL FAR PASCAL -export SettingsDIgProc( HWND, UINT, WPARAM, LPARAM )
//_______________~___________________________________________~_____________
// End of File: riy.h
//__________________________________________________________________________
//__________________________________________________._____________,__________
// '
Software Developed by: Softell
//
CA 02410039 2002-12-06
APPENDIX A: Page 5
// Purpose: Act as the "Signal Monitor Process" for Windows 3.1.1
//
// Module: resource.h
//
// Description:
// This program opens a comm port and waits for CTS to change state.
// When it sees a change, it waits for another change back. When this happens,
// it compares the time agianst the time set in the jumpers, and then executes
the
// program specified on the command line.
//
//{{NO DEPENDENCIES}}
J/ App Studio generated include file.
// Used by MONITOR.RC
//
#define IDD OK 1
#define IDDrCANCEL 2
#define ABOUTDLGBOX 100
#define SETTINGSDLG80X 101
#define T'TYACCEL 200
#define IDM_CONNECT 0x100
#define IDM_DISCONNECT 0x101
#define IDM_EXIT 0x102
#define IDM SETTINGS 0x103
#define IDMrABOUT 0x104
#define TTYMENU 300
#define TTYICON 400
#define 500
TTYBITMAP
#define ABOUTICON 0x210
IDD
#define TITLELINE 0x211
IDD
#define VERSION 0x212
IDD
#define _BYLINE 0x213
IDD
#define WINDOWSMODE 0x214
IDD
#define FREEMEM 0x215
IDD
#define _RESOURCES 0x216
IDD
#define _PORTCB 0x220
IDD
#define BAUDCB 0x221
IDD
#define DATABITSCB 0x222
IDD
#define PARITYCB 0x223
IDD
#define _ 0x224
IDD STOPBITSCB
#define _DTRDSR 0x225
IDD
#define RTSCTS 0x226
IDD_
#define _XONXOFF 0x227
IDD
#define AUTOWRAP 0x228
IDD
#define NEWLINE 0x228
IDD
CA 02410039 2002-12-06
APPENDIX A: Page 6
#define LOCALECHO Ox22A
IDD
#define FONT Ox22B
IDD
r
_ USECNRECEIVE Ox22C
#define
IDD
#define DISPLAYERRORS Ox22D
IDD
r
_ BYLINE 0x300
#define
(DS
#define MODE STANDARD 0x301
IDS
#define ENHANCED 0x302
IDS MODE
_ _ 0x303
#define MODE WLO
IDS
#define UNDEF 0x304
IDS MODE
#define _ 0x310
IDS COMPREFIX
#define BAUD110 0x320
IDS
#define BAUD300 0x321
IDS
#define BAUD600 0x322
IDS
#define BAUD1200 0x323
IDS
#define BAUD2400 0x324
IDS
#define BAUD4800 0x325
IDS
#define BAUD9600 0x326
IDS
_ BAUD14400 0x327
#define
IDS
_ BAUD19200 0x328
#define
IDS
#define BAUD38400 0x329
IDS
#define BAUD56000 Ox32A
IOS
#define BAUD128000 Ox32B
IDS~
#define BAUD256000 0x32C
IDS
#define PARITYNONE 0x330
IDS~
#define PARITYEVEN 0x331
IDS~
#define PARITYODD 0x332
IDS
_ PARITYMARK 0x333
#define
IDS
#define PARITYSPACE 0x334
IDS
#define ONESTOPBIT 0x340
iDS
_ ONE5STOPBITS 0x341
#define
IDS
_ TWOSTOPBITS 0x342
#define
IDS
#define COMMANDLINEEDIT 1000
IDC
#define STATIC -1
IDC
j/ Next default values for new objects
#ifdef APSTUDIO_INVOKED
#ifndef APSTUDIO READONLY SYMBOLS
#define APS NEXT RESOURCE VALUE 105
#define _APS_NEXT_COMMAND_VALUE 101
#define _APS_NEXT CONTROL VALUE 1001
#define _APS_NEXT_SYMED VALUE 101
#endif
IDD
#define _RESOURCES 0x216
IDD
#define _PORTCB 0x220
IDD
CA 02410039 2002-12-06
APPENDIX A: Page 7
#endif
//
Software Developed by: Softell
//
// Purpose: Act as the "Signal Monitor Process" for Windows 3.1.1
//
// Module: version.h
//
// Description:
// This program opens a comm port and waits for CTS to change state.
// When 'rt sees a change, it waits for another change back. When this
happens,
// it compares the time agianst the time set in the jumpers, and then executes
the
// program specified on the command fine.
//
#define VER MAJOR 1
#define VER_MINOR 0
#define VER BUILD 0
//__~_~_____~__~__________________________________________~
//
Software Developed by: Softell
//
// Purpose: Act as the "Signal Monitor Process" for Windows 3.1.1
//
// Module: monitor.c
//
// Description:
// This program opens a comm port and waits for CTS to change state.
// When it sees a change, it waits for another change back. When this happens,
// it compares the time agianst the time set in the jumpers, and then executes
the
// program specified on the command line.
//
#include "monitor.h"
#include < stdio.h >
#include < time.h >
short call started = 0;
short wait time[4) _ {5,10,20,40};
short wait time index = 0;
int Read_Fife(HWND hWnd);
time_t event_time;
FILE *f in;
CA 02410039 2002-12-06
APPENDIX A: Page 8
//
// int PASCAL WinMain( HANDLE hlnstance, HANDLE hPrevlnstance,
// LPSTR fpszCmdLine, int nCmdShow )
//
// Description:
// This is the main window loopl
//
// Parameters:
// As documented for all WinMainQ functions.
//
//
int PASCAL WinMain( HINSTANCE hlnstance, HINSTANCE hPrevlnstance,
LPSTR IpszCmdLine, int nCmdShow )
HWND hTTYWnd ;
MSG msg ;
'rf (IhPrevlnstance)
if (llnitAppiication( htnstance )~
return ( FALSE ) ;
if (NULL = _ (hT'fYWnd = Initlnstance( hlnstance, nCmdShow )))
return ( FALSE ) ;
while (GetMessage( &msg, NULL, 0, 0 ))
if (lTransIateAccelerator( hTTYWnd, ghAccel, 8~msg ))
TransIateMessage( 8~msg ) ;
DispatchMessage( 8~msg ) ;
}
}
return ( (int) msg.wParam ) ;
} j/ end of WinMainQ
// BOOL NEAR InitApplication( HANDLE hlnstance )
//
// Description:
// First time initialization stuff. This registers information
// such as window classes.
//
CA 02410039 2002-12-06
APPENDIX A: Page 9
// Parameters:
// HANDLE hlnstance
// Handle to this instance of the application.
//
//
BOOL NEAR InitAppiication( HANDLE hlnstance )
WNDCLASS wndclass ;
// register tty window class
wndciass.style = NULL ;
wndciass.lpfnWndProc = TTYWndProc ;
wndciass.cbCIsExtra = 0 ;
wndcfass.cbWndExtra = sizeof( WORD ) ;
wndclass.hlnstance = hlnstance ;
wndclass.hicon = Loadfcon( hlnstance, MAKEINTRESOURCE( TTYICON ) );
wndciass.hCursor = LoadCursor( NULL, 1DC ARROW ) ;
wndclass.hbrBackground = (HBRUSH) (COLOR WINDOW + 1) ;
wndclass.lpszMenuName = MAKEINTRESOURCE( TTYMENU ) ;
wndciass.ipszCiassName = gszTTYClass ;
return( RegisterClass( ~wndclass ) ) ;
f // end of ~nitApplication ~
//-_ ~ ~ ~ _~
// HWND NEAR lnitlnstance( HANDLE hlnstance, int nCmdShow )
!/
// Description:
// initializes instance specific information.
//
// Parameters:
// HANDLE hlnstance
// Handle to instance
//
// int nCmdShow
// How do we show the window?
//
/I__----- -M_~_~_~_________ _
HWND NEAR Initlnstance( HANDLE hlnstance, int nCmdShow )
CA 02410039 2002-12-06
APPENDIX A: Page 10
HWND hTTYWnd ;
// load accelerators
ghAccel = LoadAccelerators( hlnstance, MAKEINTRESOURCE( TTYACCEL ) ) ;
// create the TTY window
hTTYWnd = CreateWindow( gszTTYClass, gszAppName,
WS OVERLAPPEDWINDOW,
CW_USEDEFAULT, CW USEDEFAULT,
CW USEDEFAULT, CW USEDEFAULT,
NULL, NULL, hlnstance, NULL ) ;
if (NULL = = hTTYWnd)
return ( NULL ) ;
ShowWindow( hTTYWnd, nCmdShow ) ;
UpdateWindow( hTTYWnd ) ;
return ( hTlYWnd ) ;
}// end of Initlnstance0
~__w_ ___
// LRESULT FAR PASCAL _export TTYWndProc( HWND hWnd, UINT uMsg,
// WPARAM wParam, LPARAM IParam )
//
// Description:
// This is the TTY Window Proc. This handles ALL messages
// to the tty window.
//
// Parameters:
// As documented for Window procedures.
//
// ____ __________________________________
LRESULT FAR PASCAL _export TTYWndProc( HWND hWnd, UINT uMsg,
WPARAM wParam, LPARAM IParam )
switch (uMsg)
case WM CREATE:
{ CreateT'TYlnfo( hWnd )
Read_File(hWnd);
CA 02410039 2002-12-06
APPENDIX A: Page i 1
/ j SetupConnection( hWnd );
if (lOpenConnection( hWnd ))
MessageBox( hWnd, "Connection failed.", gszAppName,
MB ICONEXCLAMATION ) ;
break;
case WM COMMAND:
switch ((WORD) wParam)
Case IDM CONNECT:
CIoseConneciion(hWnd); '
if (IOpenConnection( hWnd ))
MessageBox( hWnd, "Connection failed.", gszAppName,
MB ICONEXCLAMATION ) ;
break ;
case IDM SETTINGS:
NPTTYINFO npTTYlnfo ;
if (NULL = = (npTTYlnfo =
(NPTTYINFO) GetWindowWord( hWnd,
GWW~NPTTY1NF0 )))
return ( FALSE ) ;
GoModaIDialogBoxParam( GETHINST( hWnd ),
MAKEINTRESOURCE( SETT'INGSDLGBOX ), hWnd,
SettingsDIgProc,
(LPARAM) (LPSTR) npTTYlnfo ) ;
// if fConnected, set new COM parameters
if (CONNECTED( npTTYlnfo ))
if (ISetupConnection( hWnd ))
MessageBox( hWnd, "Settings failed!", gszAppName,
MB ICONEXCLAMATION ) ;
break ;
CA 02410039 2002-12-06
APPENO1X A: Page 12
case IDM ABOUT:
GoModaIDialogBoxParam ( GETHINST( hWnd ),
MAKEINTRESOURCE( ABOUTDLGBOX ),
hWnd,
AboutDigProc, NULL ) ;
break;
case IDM EXIT:
PostMessage( hWnd, WM'CLOSE, NULL, OL ) ;
break ;
break ;
case WM COMMNOT1FY:
#ifdef DEBUG
f in =fopen("debug.bct","a"~;
tlme(~event_time);
iprintf(f in, "%Id\r\n",event time);
fclose(f in);
#endif
ProcessCOMMNotification( hWnd, (WORD) wParam, (LONG) IParam );
break ;
case WM_PAINT:
PaintTTY( hWnd ) ;
break ;
case WM S1ZE:
SizeTTY( hWnd, HIWORD( IParam ), LOWORD( IParam ) ) ;
break ;
case WM HSCROLL:
Scrol~l'TYHorz( hWnd, (WORD) wParam, LOWORD( IParam ) ) ;
break ;
case WM VSCROLL:
Scroi(TTYVert( hWnd, (1IVORD) wParam, LOWORD( IParam ) ) ;
break ;
case WM_CHAR:
ProcessTTYCharacter( hWnd, LOBYTE( wParam ) ) ;
break ;
CA 02410039 2002-12-06
APPENDIX A: Page 13
case WM SETFOCUS:
SetTTYFocus( hWnd ) ;
break ;
Case WM KILLFOCUS:
IGI~T'YFocus( hWnd ) ;
break ;
case WM_DESTROY:
DestroyTTYlnfo( hWnd ) ;
PostQuitMessage( 0 ) ;
break ;
case WM CLOSE:
if (IDOK 1= MessageBox( hWnd, "OK to close window?", "'TTY Sample",
MB~ICONOUESTION ~ MB OKCANCEL ))
break ;
// fall through
default:
return( DefWindowProc( hWnd, uMsg, wParam, lParam ) ) ;
return OL ;
// end of TTYWndProcQ
//_____ _~_~___~____~_______________________~_____._______
// LRESULT NEAR CreateTTYlnfo( HWND hWnd )
//
/ j Description:
// Creates the tty information structure and sets
/ j menu option availability. Returns -1 if unsuccessful.
//
// Parameters:
// HWND hWnd
// Handle to main window.
//
//~_~_ _~__________________._._~________w__________
LRESULT NFa4R CreateTTYlnfo( HWND hWnd )
HMENU hMenu ;
NPTTYINFO npTTYlnfo ;
CA 02410039 2002-12-06
APPENDIX A: Page 14
if (NULL = _ (npTTYlnfo =
(NPTTYINFO) LocalAlloc( LPTR, sizeof( TTYINFO ) )))
return ( (LRESULT) -1 ) ;
// initialize TTY info structure
COMDE~I( np'T?Yinfo ) = 0 ;
CONNECTED( npTTYlnfo ) = FALSE ;
CURSORSTATE( npTTYlnfo ) = CS_HIDE ;
LOCALECHO( npTTYlnfo ) = FALSE ;
AUTOWRAP( npTTYlnfo ) = TRUE ;
PORT( npTTYlnfo ) = 1 ;
BAUDRATE( npTTYlnfo ) = CBR 9600 ;
BYTESIZE( npTTYlnfo ) = 8 ;
FLOWCTRL( npTTYlnfo ) = FC RTSCTS ;
PARITY( npTTYlnfo ) = NOPARITY ;
STOPBITS( npTTYlnfo ) = ONESTOP81T ;
XONXOFF( npTTYlnfo ) = FALSE ;
XSIZE( npTTYlnfo ) = 0 ;
YSIZE( npTTYlnfo ) = 0 ;
XSCROLL( npTTYlnfo ) = 0 ;
YSCROLL( npTTYlnfo ) = 0 ;
XOFFSET( npTTYfnfo ) = 0 ;
YOFFSET( npTTYlnfo ) = 0 ;
COLUMN( npTTYlnfo ) = 0 ;
ROW( npTTYlnfo ) = 0 ;
HTTYFONT( npTTYlnfo ) = NULL ; .
FGCOLOR( npTTYlnfo ) = RGB( 0, 0, 0 ) ;
USECNRECEIVE( npTTYlnfo ) = TRUE ;
DISPLAYERRORS( npTTYlnfo ) = TRUE ;
// clear screen space
fmemset( SCREEN( npTTYlnfo ), ' ', MAXROWS * MAXCOLS ) ;
// setup default font information
LFTTYFONT( npTTYlnfo ).IfHeight = 12 ;
LFTTYFONT( npTTYlnfo ).IfWidth = 0 ;
LFt"1YFONT( npTTYlnfo ).IfEscapement = 0 ;
LFTTYFONT( npTTYlnfo ).IfOrientation = 0
LFTTYFONT( npTTYlnfo ).IfWeight = 0 ; '
LFTTYFONT( npTTYlnfo ).lfltalic = 0 ;
LFTTYFONT( npTTYlnfo ).ffUnderline = 0 ;
CA 02410039 2002-12-06
APPENDIX A: Page 15
LF1TYFONT( npTTYlnfo ).lfStrike0ut0 ;
=
LFTTYFONT( npTTYlnfo ).IfCharSetOEM CHARSET ;
=
LFTTYFONT( npTTYlnfo ).IfOutPrecisionOUT_DEFAULT PRECIS ;
=
LF1TYFONT( npTTYlnfo ).IfClipPrecisionCUP DEFAULT PRECIS ;
=
LFTTYFONT( npTTYlnfo ).IfQualityDEFAULT
= OUAL(TY ;
LFTTYFONT( npTTYlnfo ).IfPitchAndFamiiy_
= FIXED PITCH ~ FF
MODERN ;
LFT~YFONT( npTTYlnfo ).IfFaceName[OJ_
= NULL ;
// set TTYlnfo handle before any further message processing.
SetWindowWord( hWnd, GWW_NPTTYINFO, (WPARAM) npTTYlnfo ) ;
// reset the character information, etc.
ResetTTYScreen( hWnd, npTTYfnfo ) ;
hMenu = GetMenu( hWnd ) ;
EnableMenultem( hMenu, IDM_DISCONNECT,
MF GRAYED ~ MF DISABLED ~ MF BYCOMMAND ) ;
EnabIeMenuitem( hMenu, IDM CONNECT, MF_ENABLED ~ MF_BYCOMMAND ) ;
return ( (LRESULT) TRUE ) ;
}// end of CreateTTYlnfoQ
/ /_____~______________________________________________________
// BOOL NEAR DestroyTTYlnfo( HWND hWnd )
//
// Description:
// Destroys block associated with TTY window handle.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
//-.____________ _~________________~___~_~_______________
BOOL NEAR DestroyTTYlnfo( HWND hWnd
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 16
// force connection closed (if not already closed)
if (CONNECTED( npTTYlnfo ))
CIoseConnection( hWnd ) ;
DeleteObject( HTTYFONT( npTTYlnfo ) ) ;
LocaIFree( npTTYlnfo ) ;
return ( TRUE ) ;
}// end of DestroyTTYlnfo~
//_________ ______~______~ ~_ __________
// BOOL NEAR ResetTTYScreen( HWND hWnd, NPTTYINFO npTT'Ylnfo )
//
// Description:
// Resets the TTY character information and causes the
// screen to resize to update the scroll information.
//
// Parameters:
// NPTTYINFO npTTYlnfo
// pointer to TTY info structure
//
_~_______~_~____~~____~________
BOOL NEAR ResetTT'YScreen( HWND hWnd, NPTTYINFO npTTYlnfo )
HDC hDC ;
TEXTMETRIC tm ;
RECT rcWindow ;
if (NULL = = npTTYlnfo)
return ( FALSE ) ;
if (NULL ! = HTTYFONT( npTTYlnfo ))
DeleteObject( HTTYFONT( npTTYlnfo ) ) ;
HTTYFONT( npTTYlnfo ) = CreateFonttndireci( &LFTTYFONT( npTTYlnfo ) ) ;
hDC = GetDC( hWnd ) ;
SelectObject( hDC, HTTYFONT( npTTYlnfo ) ) ;
GetTextMetrics( hDC, &tm ) ;
ReleaseDC( hWnd, hDC ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 17
XCHAR( npTTYlnfo ) = tm.tmAveCharWidth ;
YCHAR( npTTYlnfo ) = tm.tmHeight + tm.tmE~cternatLeading ;
// a slimy hack to force the scroll position, region to
// be recalculated based on the new character sizes
GetWindowRect( hWnd, B~rcWindow ) ;
SendMessage( hWnd, WM SIZE, SIZENORMAL,
(LPARAM) MAKELONG( rcWindow.right - rcWindow.left,
rcWindow.bottom - rcWindow.top ) ) ;
return ( TRUE ) ;
}// end of ResetTTYScreen~
//_____~~__ ______________________________~.________________
// BOOL NEAR ProcessCOMMNoiification( HWND hWnd, WORD wParam, LONG
IParam )
//
// Description:
// Processes the WM COMMNOTIFY message from the COMM.DRV.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// WORD wParam
// specifes the device (nCid)
//
// LONG IParam
// LOWORD contains event trigger
// HIWORD is NULL
//
//______________________________________________________________________
BOOL NEAR ProcessCOMMNotification( HWND hWnd, WORD wParam, LONG IParam
)
NPTTYINFO npTTYlnfo ;
UINT e_comm, ret;
time t elapsed time, start time, end time;
CA 02410039 2002-12-06
APPENDIX A: Page 18
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
// verify that 'rt is a COMM event specified by our mask
if (CN EVENT & LOWORD( IParam ) 1= CN EVENT)
return ( FALSE ) ;
wait_time index = BAUDRATE(npTTYlnfo)*2 + BYTESIZE(npTTYlnfo);
if (call started = = 0)
time(&start time);
call started = 1;
} _
else
time(8end time);
elapsed time = end time - start time;
if(( elapsed time > wait time[watt time index]*.75 )
88~( elapsed time < wait time[wait time index]*1.25 ))
// run application
ret = WinExec(npTTYlnfo- > CommandLine, SW SHOW);
// reset the event word so we are notified
// when the next event occurs
a comm = GetCommEventMask( COMDEV( npTTYlnfo ), EV CTS ) ;
return ( TRUE ) ;
}// end of ProcessCOMMNotification~
//__________~ ____________________________
// BOOL NEAR ProcessTTYCharacter( HWND hWnd, BYTE bout )
//
// Description:
// This simply writes a character to the port and echos it
// to the TTY screen rf fLocalEcho is set. Some minor
// keyboard mapping could be performed here.
CA 02410039 2002-12-06
APPENDIX A: Page 19
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// BYTE bout
// byte from keyboard
//
//
BOOL NEAR ProcessTTYCharacter( HWND hWnd, BYTE bout )
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
if (ICONNECTED( npTTYlnfo ))
return ( FALSE ) ;
WriteCommByte( hWnd, bout ) ;
'rf (LOCALECHO( npTTYlnfo ))
WriteTTY8lock( hWnd, ~bOut, 1 ) ;
return ( TRUE ) ;
}// end of ProcessTTYCharacter~
//____ __~ ___~___
// BOOL NEAR OpenConnection( HWND hWnd )
//
// Description:
// Opens communication port specified in the TTYINFO struct.
// It also sets the CommState and notifies the window via
// the fConnected flag in the TTYINFO struct.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
//___~_ _~ __~~______~________~~ ,
BOOL NEAR OpenConnection( HWND hWnd )
CA 02410039 2002-12-06
APPENDIX A: Page 20
char szPort[ 10 ], szTemp[ ~ o ] ;
BOOL fRetVal ;
HCURSOR hOIdCursor, hWaitCursor ;
HMENU hMenu ;
NPTTYINFO npTTYlnfo ;
UINT ret;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
// show the hourglass cursor
hWaitCursor = LoadCursor( NULL, IDC WAIT ) ;
hOIdCursor = SetCursor( hWaitCursor ) ;
// load the COM prefix string and append port number
LoadString( GETHINST( hWnd ), IDS COMPREFIX, szTemp, sizeof( szTemp ) ) ;
wsprintf( szPort, "9'°s%d", (LPSTR) szTemp, PORT( npTTYlnfo ) ) ;
// open COMM device
if ((COMDEV( npTTYlnfo ) = OpenComm( szPort, RXQUEUE, TXQUEUE )) < 0)
return ( FALSE ) ;
fRetVal = SetupConnection( hWnd ) ;
if (fRetVal)
CONNECTED( npTTYlnfo ) = TRUE ;
// set up notifications from COMM.DRV
// In this case we really are only using the notifications
// for the received characters - it could be expanded to
// cover the changes in CD or other status lines.
SetCommEventMask( COMDEV( npTTYlnfo ), EV CTS ) ;
// Enable notifications for events only.
// NB: This method does not use the specific
// in/out queue triggers.
CA 02410039 2002-12-06
APPENDIX A: Page 21
EnabieCommNotification( COMDEV( npTTYlnfo ), hWnd, -1, -1 ) ;
// assert DTR
EscapeCommFunction( COMDEV( npTTYlnfo ), SETDTR ) ;
SetTTYFocus( hWnd ) ;
hMenu = GetMenu( hWnd ) ;
EnabIeMenultem( hMenu, IDM_DISCONNECT,
MF ENABLED ~ MF BYCOMMAND ) ;
EnabIeMenuitem( hMenu, IDM_CONNECT,
MF GRAYED ~ MF_DISABLED ~ MF_BYCOMMAND ) ;
}
else
CONNECTED( npTTYlnfo ) -- FALSE ;
CIoseComm( COMDEV( npTTYlnfo ) ) ;
}
// restore cursor
SetCursor( hOldCursor ) ;
return ( fRetVal ) ;
}// end of OpenConnectionQ
//
// BOOL NEAR SetupConnection( HWND hWnd )
//
// Description:
// This routines sets up the DCB based on settings in the
// TTY info structure and performs a SetCommStateQ.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// __~_____ _~~_
BOOL NEAR SetupConnection( HWND hWnd )
BOOL fRetVal ;
CA 02410039 2002-12-06
APPENDIX A: Page 22
BYTE bSet ;
DCB dcb ;
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
GetCommState( COMDEV( npTTYlnfo ), 8~dcb ) ;
dcb.BaudRate = CBR_9600 ;
dcb.ByteSize = 8;
dcb.Parity = NOPARITY;
dcb.StopBits = ONESTOPBIT ;
// setup hardware flow control
//bSet = (BYTE) ((FLOWCTRL( npTTYlnfo ) ~ FC_DTRDSR) ! = 0) ;
dcb.fOubcDsrFlow = dcb.fDtrflow = 0 ;
dcb.DsrTimeout = 0;
//bSet. _ (BYTE) ((FLOWCTRL( npTTYlnfo ) 8 FC_RTSCTS) ! = 0) ;
dcb.fOutxC~sFlow = dcb.fRtsflow = 0 ;
dcb.CtsTimeout = 0 ;
// setup software flow control
//bSet = (BYTE) ((FLOWCTRL( npTTYlnfo ) & FC XONXOFF) ! = 0) ;
dcb.flnX
= dcb.fOutX
= 0 ;
dcb.XonChar= ASCII_XON
;
dcb.XoffChar= ASCII
XOFF
dcb.XonLim_
= 100 ;
dcb.XoffLim100 ;
=
// other various settings
dcb.fBinary = TRUE ;
dcb.fPariry = TRUE ;
dcb.fRtsDisable = FALSE ;
dcb.fDtrDisable = FALSE ;
fRetVal = ! (SetCommState( &dcb ) < 0) ;
CA 02410039 2002-12-06
APPENDIX A: Page 23
return ( fRetVal ) ;
} // end of SetupConnection Q
//-_~ _ ~~ ~___
// BOOL NEAR CIoseConnection( HWND hWnd )
//
// Description:
// Closes the connection to the port. Resets the connect flag
// in the TTYINFO struct.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
//________________________________________________________________________
BOOL NEAR CIoseConnection( HWND hWnd )
HMENU hMenu ;
NPTTYINFO npTTYinfo ;
'rf (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
// Disable event notification. Using a NULL hWnd tells
// the COMM.DRV to disable future notifications.
EnabIeCommNotification( COMDEV( npTTYlnfo ), NULL, -1, -1 ) ;
// kill the focus
KiIITT'YFocus( hWnd ) ;
// drop DTR
EscapeCommFunction( COMDEV( npTTYlnfo ), CLRDTR ) ;
// close comm connection
CIoseComm( COMDEV( npTTYlnfo ) ) ;
CONNECTED( npTTYlnfo ) = FALSE ;
CA 02410039 2002-12-06
APPENDIX A: Page 24
// change the selectable items in the menu
hMenu = GetMenu( hWnd ) ;
EnabIeMenultem( hMenu, IDM_DISCONNECT,
MF GRAYED ~ MF DISABLED ~ MF BYCOMMAND ) ;
EnabIeMenultem( hMenu, IDM_CONNECT,
MF_ENABLED ~ MF-BYCOMMAND ) ;
return ( TRUE ) ;
}// end of CIoseConnectionQ
//-__~ ____ ~_~_~
// int NEAR ReadCommBlock( HWND hWnd, LPSTR IpszBlock, int nMaxLength )
//
// Description:
// Reads a block from the COM port and stuffs it into
// the provided block.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// LPSTR IpszBlock
// block used for storage
//
// int nMaxLength
// max length of block to read
//
//__________w~___~_________________~_________~____________
int NEAR ReadCommBlock( HWND hWnd, LPSTR IpszBlock, int nMaxLength )
char szError[ 10 ] ;
int nLength, nError ;
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
nLength = ReadComm( COMDEV( npTTYlnfo ), IpszBlock, nMaxLength ) ;
if (nLength < 0)
CA 02410039 2002-12-06
APPENDIX A: Page 25
nLength * _ -1 ;
white (nError = GetCommError( COMDEV( npTTYlnfo ), NULL ))
if (DISPLAYERRORS( npTTYlnfo ))
wsprintf( szError, " < CE-%d > ", nError ) ;
WriteTTYBlock( hWnd, szError, Istrlen( szError ) ) ;
}
}
}
return ( nLength ) ;
}// end of ReadCommBIockQ
//-______________~~w_____~___~~_________________________
// BOOL NEAR WriteCommByte( HWND hWnd, BYTE bByte )
//
// Description:
// Writes a byte to the COM port specified in the associated
// TTY info structure.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// BYTE b8yte
// byte to write to port
//
//___________~ ____________________________________~_________
BOOL NEAR WriteCommByte( HWND hWnd, BYTE bByte )
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
WriteComm( COMDEV( npTTYlnfo ), (LPSTR) ~bByte, 1 ) ;
return ( TRUE ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 26
}// end of WriteCommByteQ
//
// BOOL NEAR WriteTTYBlock( HWND hWnd, LPSTR IpBlock, int nLength )
//
// Description:
// Writes block to TTY screen. Nothing fancy - just
// straight TTY.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// LPSTR IpBlock
// far pointer to block of data
//
// int nLength
// length of block
//
// ~_________~_________~_~___~___
BOOL NEAR WriteTTYBlock( HWND hWnd, LPSTR IpBlock, int nLength )
int i ;
NPTTYINFO npTTYlnfo ;
RECT rest ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
for (i = 0 ; i < nLength; i + + )
switch (IpBlock[ i J)
case ASCII_BEL:
// Bell
MessageBeep( 0 ) ;
break ;
case ASCII BS:
// Backspace
if (COLUMN( npTTYlnfo ) > 0)
COLUMN( npTTYlnfo ) -- ;
CA 02410039 2002-12-06
APPENDIX A: Page 27
MoveTTYCursor( hWnd ) ;
break ;
case ASCII CR:
// Carriage return
COLUMN( npTTYlnfo ) = 0 ;
MoveTTYCursor( hWnd ) ;
if (INEWLINE( npTTYlnfo ))
break;
// fall through
case ASCII LF:
// Line feed
if (ROW( npTTYlnfo ) + + _ = MAXROWS - 1 )
_fmemmove( (LPSTR) (SCREEN( npTTYlnfo )),
(LPSTR) (SCREEN( npTTYlnfo ) + MAXCOLS),
(MAXROWS - 1 ) * MAXCOLS ) ;
_fmemset( (LPSTR) (SCREEN( npTTYlnfo ) + (MAXROWS - 1)
MAXCOLS),
' ', MAXCOLS ) ;
InvalidateRect( hWnd, NULL, FALSE ) ;
ROW( npTTYlnfo )-- ;
MoveTTYCursor( hWnd ) ;
break ;
default:
*(SCREEN( npTTYlnfo ) + ROW( npTTYlnfo ) * MAXCOLS +
COLUMN( npTTYlnfo )) = IpBlock[ i ] ;
rect.left = (COLUMN( npTTYlnfo ) * XCHAR( npTTYlnfo )) -
XOFFSET( npTTYlnfo ) ;
rect.right = rect.left + XCHAR( npTTYlnfo ) ;
rect.top = (ROW( npTTYlnfo ) * YCHAR( npTTYlnfo )) -
YOFFSET( npTTYlnfo ) ;
rect.bottom = rect.top + YCHAR( npTTYlnfo ) ;
InvalidateRect( hWnd, erect, FALSE ) ;
// Line wrap
if (COLUMN( npTTYlnfo ) < MAXCOLS - 1)
COLUMN( npTTYlnfo )++ ;
else if (AUTOWRAP( npTTYlnfo ))
WriteTTYBlock( hWnd, "\r\n", 2 ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 28
break;
}
return ( TRUE ) ;
}// end of WriteTTYBIockQ
//--~_ _____
// VOID NEAR GoModaIDialogBoxParam( HINSTANCE hlnstance,
// LPCSTR IpszTemplate, HWND hWnd,
// DLGPROC IpDIgProc, LPARAM IParam )
//
// Description:
// It is a simple utility function that simply performs the
// MPI and invokes the dialog box with a DWORD paramter.
//
// Parameters:
// similar to that of DialogBoxParamQ with the exception
// that the IpDIgProc is not a procedure instance
//
//_~- ____ ___________~,___
VOID NEAR GoModaIDiaiog8oxParam( HINSTANCE hlnstance, LPCSTR IpszTemplate,
HWND hWnd, DLGPROC IpDIgProc, LPARAM IParam )
DLGPROC IpProclnstance ;
IpProcinstance = (DLGPROC) MakeProcinstance( (FARPROC) IpDIgProc,
hlnstance ) ;
DialogBoxParam( hlnstance, IpszTemplate, hWnd, IpProclnstance, IParam ) ;
FreeProclnstance( (FARPROC) IpProclnstance ) ;
}// end of GoModaIDialogBoxParamQ
//-_______w_ ____~_____________ ~_ _________
// BOOL FAR PASCAL _export AboutDIgProc( HWND hDlg, UINT uMsg,
// WPARAM wParam, LPARAM IParam )
//
// Description:
// Simulates the Windows System Dialog Box.
//
// Parameters:
// Same as standard dialog procedures.
//
CA 02410039 2002-12-06
APPENDIX A: Page 29
//
BOOL FAR PASCAL _export AboutDIgProc( HWND hDlg, UINT uMsg,
WPARAM wParam, LPARAM IParam )
switch (uMsg)
case WM INITDIALOG:
int idModeString ;
char szBuffer[ MAXLEN TEMPSTR ], szTemp[ MAXLEN TEMPSTR ] ;
DWORD dwFreeMemory, dwWinFlags ;
WORD wFreeResources, wRevision, wVersion ;
#ifdef ABOUTDLG USEBITMAP
// 'rf we are using the bitmap, hide the icon
ShowWndow( GetDlgltem( hDlg, IDD ABOUTICON ), SW_HIDE ) ;
#endif
// sets up the version number for Windows
wVersion = LOWORD( GetVersion~ ) ;
switch (HIBYTE( wVersion ))
Case 10:
wRevision = 1 ;
break ;
default:
wRevision = 0 ;
break;
wVersion & = OxFF ;
GetDIgItemText( hDlg, IDD TITLELINE, szTemp, sizeof( szTemp ) ) ;
wsprintf( szBuffer, szTemp, wVersion, wRevision ) ;
SetDIgItemText( hDlg, IDD TITLELINE, szBuffer ) ;
// sets up version number for TTY
GetDIgItemText( hDlg, IDD VERSION, szTemp, sizeof( szTemp ) ) ;
wsprintf( szBuffer, szTemp, VER MAJOR, VER MINOR ) ;
SetDIgItemText( hDlg, IDD VERSION, (LPSTR) szBuffer ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 30
// get by-line
LoadString( GETHINST( hDlg ), IDS BYLINE, szBuffer,
sizeof( szBuffer ) ) ;
SetDIgItemText( hDlg, IDD_BYUNE, szBuffer ) ;
// set windows mode information
dwWinFlags = GetWinFIagsQ ;
if (dwWinFlags & WF ENHANCED)
idModeString = IDS_MODE ENHANCED ;
else if (dwWinFlags & WF STANDARD)
idModeString = IDS MODE STANDARD ;
else if (dwWinFlags & WF WLO)
idModeString = IDS_MODE WLO ;
else
idModeString = IDS_MODE_UNDEF ;
LoadString( GETHINST( hDlg ), idModeString, szBuffer,
sizeof( szBuffer ) ) ;
SetDIgItemText( hDlg, IDD WINDOWSMODE, szBuffer ) ;
// get free memory information
dwFreeMemory = GetFreeSpace( 0 ) / 1024L ;
GetDIgItemText( hDlg, IDD_FREEMEM, szTemp, sizeof( szTemp ) ) ;
wsprintf( szBuffer, szTemp, dwFreeMemory ) ;
SetDIgItemText( hDlg, IDD_FREEMEM, (LPSTR) szBuffer ) ;
// get free resources information
wFreeResources = GetFreeSystemResources( 0 ) ;
GetDIgItemText( hDlg, IDD_RESOURCES, szTemp, sizeof( szTemp ) ) ;
wsprintf( szBuffer, szTemp, wFreeResources ) ;
SetDIgItemText( hDlg, IDD_RESOURCES, (LPSTR) szBuffer ) ;
return ( TRUE ) ;
#ifdef ABOUTDLG USEBITMAP
// used to paint the bitmap
case WM PAINT:
HBITMAP hBitMap ;
CA 02410039 2002-12-06
APPENDIX A: Page 31
HDC hDC, hMemDC ;
PAINTSTRUCT ps ;
// load bitmap and display it
hDC = BeginPaint( hDlg, &ps ) ;
if (NULL 1= (hMemDC = CreateCompatibIeDC( hDC )))
hBitMap = LoadBitmap( GETHINST( hDlg ),
MAKEINTRESOURCE( TTYBITMAP ) ) ;
hBitMap = SelectObject( hMemDC, hBitMap ) ;
BitBlt( hDC, 10, 10, 64, 64, hMemDC, 0, 0, SRCCOPY ) ;
DeleteObject( SelectObject( hMemDC, hBitMap ) ) ;
DeleteDC( hMemDC ) ;
}
EndPaint( hDlg, 8~ps ) ;
}
break ;
#endif
case WM_COMMAND:
if ((WORD) wParam = = IDD OK)
EndDialog( hDtg, TRUE ) ;
return ( TRUE ) ;
}
break;
}
return ( FALSE ) ;
}// end of AboutDIgProcQ
//____~____ ~_____~_____________________~_____________
// BOOL NEAR SettingsDlglnit( HWND hDlg )
//
/ j Description:
// Puts current settings into dialog box (via CheckRadioButtonQ.etc.)
//
// Parameters:
// HWND hDlg
// handle to dialog box
//
//-_________ ~______w_____________________~____________
CA 02410039 2002-12-06
APPENDIX A: Page 32
BOOL NEAR SettingsDlglnit( HWND hDlg )
char szBuffer( MAXLEN TEMPSTR ], szTemp[ MAXLEN TEMPSTR ] ;
NPTTYINFO npTTYlnfo ;
WORD wCount, wMaxCOM, wPosition ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GET_PROP( hDlg, ATOM TTYINFO )))
return ( FALSE ) ;
wMaxCOM = LOWORD( EscapeCommFunction( NULL, GETMAXCOM ) ) + 1 ;
// load the COM prefix from resources
LoadString( GETHINST( hDlg ), IDS COMPREFIX, szTemp, sizeof( szTemp ) ) ;
// fill port combo box and make initial selection
for (wCount = 0; wCount < wMaxCOM; wCount+ +)
wsprintf( szBuffer, "%s%d", (LPSTR) szTemp, wCount + 1 ) ;
SendDIgItemMessage( hDlg, IDD PORTCB, CB ADDSTRING, NULL,
(LPARAM) (LPSTR) szBuffer ) ;
SendDIgItemMessage( hDlg, IOD PORTCB, CB_SETCURSEL,
(V1IPARAM) PORT(npTTYlnfo)-1 , NULL ) ;
for (wCount = 0; wCount < 2; wCount++)
wsprintf( sz8uffer, "%d", wCount ) ;
wPosition = LOWORD( SendDIgItemMessage( hDlg, IDD_BAUDCB,
CB ADDSTRING, NULL,
(LPARAM) (LPSTR) szBuffer ) ) ;
SendDIgItemMessage( hDlg, IDD BAUDCB, CB_SETCURSEL,
(WPARAM)BAUDRATE(npTTYlnfo), NULL ) ;
// fill data bits combo box and make initial selection
for (wCount = 0; wCount < 2; wCount++)
wsprintf( szBuffer, "%d", wCount ) ;
wPosition = LOWORD( SendDIgItemMessage( hDlg, IDD_DATABITSCB,
CA 02410039 2002-12-06
APPENDIX A: Page 33
CB ADDSTRING, NULL,
(LPARAM) (LPSTR) szBuffer ) ) ;
}
SendDIgItemMessage( hDlg, IDD DATABITSCB, CB SETCURSEL,
(V11PARAM)BYTESIZE(npTTYlnfo), NULL ) ;
// fill data bits combo box and make initial selection
for (wCount = 0; wCount < 2; wCount+ +)
wsprintf( szBuffer, "9'°d", wCount ) ;
wPosition = LOWORD( SendDIgItemMessage( hDlg, IDD PARITYCB,
CB_ADDSTRING, NULL,
(LPARAM) (LPSTR) szBuffer ) ) ;
}
SendDIgItemMessage( hDlg, IDD PARITYCB, CB_SETCURSEL,
(WPARAM)PARITY(npTTYlnfo), NULL ) ;
// fill data bits combo box and make initial selection
for (wCount = 0; wCount < 2; wCount+ +)
wsprintf( szBuffer, "%d", wCount ) ;
wPosition = LOWORD( SendDIgltemMessage( hDlg, IDD STOPBITSCB,
CB ADDSTRING, NULL,
(LPARAM) (LPSTR) szBuffer ) ) ;
}
SendDIgItemMessage( hDlg, IDD STOPBITSCB, CB_SETCURSEL,
STOPBITS(npTTYlnfo), NULL ) ;
SendDIgItemMessage( hDlg, IDC COMMANDL1NEEDIT, WM SETTEXT,
NULL, (LPARAM)(LPSTR) COMMANDLINE( npTTYlnfo) ) ;
return ( TRUE ) ;
}// end of SettingsDIgInitO
//___________~____________________________ _________~___~
// BOOL NEAR SelectTTYFont( HWND hDlg )
//
// Description:
// Selects the current font for the TTY screen.
// Uses the Common Dialog ChooseFontQ API.
//
CA 02410039 2002-12-06
APPENDIX A: Page 34
// Parameters:
// HWND hDlg
// handle to settings dialog
//
//-
BOOL NEAR SelectTTYFont( HWND hDig )
f
CHOOSEFONT cfITYFont ;
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GET_PROP( hDlg, ATOM TTYINFO )))
return ( FALSE ) ;
cfTfYFont.IStruciSize= sizeof( CHOOSEFONT ) ;
cfTTYFont.hwndOwner= hDlg ;
cfTTYFont.hDC = NULL ;
cfTTYFont.rgbColors= FGCOLOR( npTTYlnfo ) ;
cfTTYFont.IpLogFont= &LFTTYFONT( npTTYlnfo ) ;
cfTTYFont.Flags = CF_SCREENFONTS ~ CF FIXEDPITCHONLY
CF EFFECTS ~ CF INITTOLOGFONTSTRUCT ;
cfTT'YFont.lCustData_
= NULL ;
cfT'tYFont.IpfiHook= NULL ;
ctTTYFont.IpTempIateName
= NULL ;
cfTTYFont.hlnstance= GETHINST( hDlg ) ;
if (ChooseFont( B~cfTTYFont ))
FGCOLOR( npTTYlnfo ) = cfTIYFont.rgbColors ;
ResetTTYScreen( GetParent( hDlg ), npTTYlnfo ) ;
return ( TRUE ) ;
}// end of SelectTTYFontQ
//-_____~____ _________________________________________.____________.
// BOOL NEAR SettingsDIgTerm( HWND hDlg )
//
// Description:
// Puts dialog contents into TTY info structure.
//
// Parameters:
// HWND hDlg
CA 02410039 2002-12-06
APPENDIX A: Page 35
// handle to settings dialog
//
//
BOOL NEAR SettingsDIgTerm( HWND hDlg )
f
NPTTYINFO npTTYlnfo ;
WORD wSelection ;
WORD cbText;
unsigned char szBuf[128J;
FILE *f out;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GET_PROP( hDlg, ATOM TTYINFO )))
return ( FALSE ) ;
if((f out = fopen("COMM.CFG","w")) _ = NULL)
return ( FALSE ) ;
// get port selection
PORT( npTTYlnfo ) _
LOBYTE( LOWORD( SendDIgItemMessage( hDlg, IDD_PORTCB,
CB_GETCURSEL,
NULL, NULL ) ) + 1 ) ;
fprintf(f out, "%d\r\n",PORT( npTTYlnfo ));
// get baud rate selection
wSelection =
LOWORD( SendDIgltemMessage( hDlg, IDD BAUDCB, CB GETCURSEL,
NULL, NULL ) ) ;
fprintf(f out, "%d\r\n", wSelection );
BAUDRATE( npTTYlnfo ) _
LOWORD( SendDIgltemMessage( hDlg, IDD BAUDCB, CB GETCURSEL,
(VIIPARAM) wSelection, NULL ) ) ;
// get data bits selection
BYTES1ZE( npTTYlnfo ) -
LOBYTE( LOWORD( SendDlgltemMessage( hDlg, !DD DATABITSCB,
CB_GETCURSEI,
NULL, NULL ))) ;
fprintf(f out, "~°d\r\n", wSelection);
CA 02410039 2002-12-06
APPENDIX A: Page 36
// get parity selection
wSelection =
LOWORD( SendDIgItemMessage( hDlg, IDD_PARITYCB, CB GETCURSEL,
NULL, NULL ) ) ;
PARITY( npTTYlnfo ) _
LOBYTE( LOWORD( SendDIgItemMessage( hDlg, IDD_PARITYCB,
CB GETITEMDATA,
(V1IPARAM) wSelection,
NULL)));
fprintf(f out, "%d\r\n", wSelection );
// get stop bits selection
wSelection =
LOWORD( SendDIgItemMessage( hDlg, IDD STOPBITSCB, CB GETCURSEL,
NULL, NULL ) ) ;
STOPBITS( npTTYlnfo ) _
LOBYTE( LOWORD( SendDIgItemMessage( hDlg, IDD STOPBITSCB,
CB GETITEMDATA,
(WPARAM) wSelection, NULL ) ) ) ;
fprintf(f out, "%d\r\n", wSelection );
// 11
*(V110RD *) szBuf = sizeof(szBuf) - 1; /* sets the buffer size */
cbText = (WORD) SendDIgItemMessage(hDlg, IDC_COMMANDLINEEDIT,
EM_GETLINE,
0, /* line number */
(DWORD) (LPSTR) szBuf); /* buffer address */
szBuf[cbText] _ '\0'; /* terminating null character */
strcpy(npTTYlnfo->CommandLine , szBuf);
(puts( szBuf, f out);
fclose(f_out);
//D
// get flow control settings
return ( TRUE ) ;
}// end of SettingsDIgTermQ
//-______~___~~____w~~______~____________________________
// BOOL FAR PASCAL export SettingsDIgProc( HWND hDlg, UINT uMsg,
CA 02410039 2002-12-06
APPENDIX A: Page 37
// WPARAM wParam, LPARAM IParam )
//
// Description:
// This handles all of the user preference settings for
// the TTY.
//
// Parameters:
// same as all dialog procedures
//
// ~~ ___
BOOL FAR PASCAL export SettingsDIgProc( HWND hDlg, UINT uMsg,
WPARAM wParam, LPARAM IParam )
switch (uMsg)
case WM tNITDIALOG:
NP1TYINFO npTTYlnfo ;
// get & save pointer to TTY info structure
npTTYlnfo = (NPITYINFO) LOWORD( IParam ) ;
SET_PROP( hDlg, ATOM TTYINFO, (HANDLE) npTTYlnfo ) ;
return ( SettingsDlglnit( hDlg ) ) ;
case WM_COMMAND:
switch ((WORD) wParam)
case IDD FONT:
return ( SelectTTYFont( hDlg ) ) ;
case IDD OK:
// Copy stuff into structure
SettingsDIgTerm( hDlg ) ;
EndDialog( hDlg, TRUE ) ;
return ( TRUE ) ;
case IDD CANCEL:
// Just end
EndDialog( hDlg, TRUE ) ;
return ( TRUE ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 38
break;
case WM_DESTROY:
REMOVE_PROP( hDlg, ATOM TTYINFO ) ;
break ;
}
return ( FALSE ) ;
}// end of SettingsDIgProc~
// ____ __~__~~_ _~
// BOOL NEAR PaintTTY( HWND hWnd )
//
// Description:
// Paints the rectangle determined by the paint struct of
// the DC.
//
// Parameters:
// HWND hWnd
// handle to TTY window (as always)
//
//___________ _______________~~_____________~_________
BOOL NEAR PaintTTY( HWND hWnd )
int nRow, nCol, nEndRow, nEndCol, nCount, nHorzPos, nVertPos ;
HDC hDC ;
HFONT hOIdFont ;
NPTTYINFO npTTYlnfo ;
PAINTSTRUCT ps ;
RECT rest ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
hDC = BeginPaint( hWnd, &ps ) ;
hOIdFont = SelectObject( hDC, HTTYFONT( npTTYlnfo ) ) ;
SetTextColor( hDC, FGCOLOR( npTTYlnfo ) ) ;
SetBkColor( hDC, GetSysColor( COLOR WINDOW ) ) ;
rest = ps.rcPaint ;
nRow =
min( MAXROWS - 1,
max( 0, (rect.top + YOFFSET( npTTYlnfo )) / YCHAR( npTTYlnfo ) ) ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 39
nEndRow =
min( MAXROWS - 1,
((rect.bottom + YOFFSET( npTTYlnfo ) - 1 ) / YCHAR( npTTYlnfo ) ) ) ;
nCol =
min( MAXCOLS - 1,
max( 0, (rect.left + XOFFSET( npTTYlnfo )) / XCHAR( npTTYlnfo ) ) ) ;
nEndCol =
min( MAXCOLS - 1,
((rect.right + XOFFSET( npTTYlnfo ) - 1 ) / XCHAR( npTTYlnfo ) ) ) ;
nCount = nEndCol - nCol + 1 ;
for (; nRow < = nEndRow; nRow+ +)
nVertPos = (nRow * YCHAR( npTTYlnfo )) - YOFFSET( npTTYlnfo ) ;
nHorzPos = (nCol * XCHAR( npTTYlnfo )) - XOFFSET( npTTYlnfo ) ;
rect.top = nVertPos ;
rect.bottom = nVertPos + YCHAR( npTTYlnfo ) ;
rect.left = nHorzPos ;
rect.right = nHorzPos + XCHAR( npTTYlnfo ) * nCount ;
SetBkMode( hDC, OPAQUE ) ;
ExtTextOut( hDC, nHorzPos, nVertPos, ETO_OPAOUE ~ ETO_CLIPPED, 8~rect,
(LPSTR)( SCREEN( npTTYlnfo ) + nRow * MAXCOLS + nCol ),
nCount, NULL ) ;
}
SelectObject( hDC, hOIdFont ) ;
EndPaint( hWnd, fps ) ;
MoveTTYCursor( hWnd ) ;
return ( TRUE ) ;
}// end of PaintTTY~
//________~____ _ _____________________________~______
// BOOL NEAR SizeTTY( HWND hWnd, WORD wVertSize, WORD wHorzSize )
//
// Description:
// Sizes TTY and sets up scrolling regions.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// WORD wVertSize
// new vertical size
//
// WORD wHorzSize
CA 02410039 2002-12-06
APPENDIX A: Page 40
// new horizontal size
//
//
BOOL NEAR SizeTTY( HWND hWnd, WORD wVertSize, WORD wHorzSize )
int nScroIlAmt ;
NPTTYINFO npTTYlr>fo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GV11W_NPTTYINFO )))
return ( FALSE ) ;
YSIZE( npTTYlnfo ) _ (int) wVertSize ;
YSCROLL( npTTYlnfo ) = max( 0, (MAXROWS * YCHAR( npTTYlnfo )) -
YSIZE( npTTYlnfo ) ) ;
nScrolIAmt = min( YSCROLL( npTTYlnfo ), YOFFSET( npTTYlnfo ) ) -
YOFFSET( npTTYlnfo ) ;
ScroIIWindow( hWnd, 0, -nScroIlAmt, NULL, NULL ) ;
YOFFSET( npTTYlnfo ) = YOFFSET( npTTYlnfo ) + nScroIlAmt ;
SetScrolIPos( hWnd, SB_VERT, YOFFSET( npTTYlnfo ), FALSE ) ;
SetScroIIRange( hWnd, SB VERT, 0, YSCROLL( npTTYlnfo ), TRUE ) ;
XSIZE( npTTYlnfo ) _ (int) wHorzSize ;
XSCROLL( npTTYlnfo ) = max( 0, (MAXCOLS * XCHAR( npTTYlnfo )) -
XSIZE( npTTYlnfo ) ) ;
nScroIlAmt = min( XSCROLL( npTTYlnfo ), XOFFSET( npTTYlnfo )) -
XOFFSET( npTTYlnfo ) ;
ScroIIWindow( hWnd, 0, -nScrolIAmt, NULL, NULL ) ;
XOFFSET( npTTYlnfo ) = XOFFSET( npTTYlnfo ) + nScroIlAmt ;
SetScroIIPos( hWnd, SB HORZ, XOFFSET( npTTYlnfo ), FALSE ) ;
SetScroIIRange( hWnd, SB HORZ, 0, XSCROLL( npTTYlnfo ), TRUE ) ;
InvalidateRect( hWnd, NULL, TRUE ) ;
return ( TRUE ) ;
}// end of SizeTTY~
//___.______ _____________________~________~~_______
// BOOL NEAR ScroIITTYVert( HWND hWnd, WORD wScroIICmd, WORD wScroIIPos
//
CA 02410039 2002-12-06
APPENDIX A: Page 41
// Description:
// Scrolls TTY window vertically.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// WORD wScroIICmd
// type of scrolling we're doing
//
// WORD wScroIIPos
// scroll position
//
//____~___ ___~_____________
BOOL NEAR ScroIfTTYVert( HWND hWnd, WORD wScroIICmd, WORD wScroIIPos )
int nScroIlAmt ;
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
switch (wScroIICmd)
case SB TOP:
nScroIlAmt = -YOFFSET( npTTYlnfo ) ;
break ;
case SB BOTTOM:
nScroIlAmt = YSCROLL( npTTYlnfo ) - YOFFSET( npTTYlnfo ) ;
break ;
case SB PAGEUP:
nScroIlAmt = -YSIZE( npTTYlnfo ) ;
break ;
case SB_PAGEDOWN:
nScroIlAmt = YSIZE( npTTYlnfo ) ;
break ;
case SB_LINEUP:
nScroIlAmt = -YCHAR( npTTYlnfo ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 42
break ;
case SB LINEDOWN:
nScrotIAmt = YCHAR( npTTYlnfo ) ;
break ;
case SB THUMBPOSITION:
nScroIlAmt = wScroIIPos - YOFFSET( npTTYlnfo ) ;
break ;
default:
return ( FALSE ) ;
if ((YOFFSET( npTTYlnfo ) + nScroIlAmt) > YSCROLL( npTTYlnfo ))
nScroIlAmt = YSCROLL( npTTYlnfo ) - YOFFSET( npTTYlnfo ) ;
if ((YOFFSET( npTTYlnfo ) + nScroIlAmt) < 0)
nScroliAmt = -YOFFSET( npTTYlnfo ) ;
ScroIIWindow( hWnd, 0, -nScroIlAmt, NULL, NULL ) ;
YOFFSET( npTTYlnfo ) = YOFFSET( npTTYlnfo ) + nScroIlAmt ;
SetScroIIPos( hWnd, SB VERT, YOFFSET( npTTYlnfo ), TRUE ) ;
return ( TRUE ) ;
}// end of ScroIITTYVertQ
//__ _____________________~______ ________
// BOOL NEAR ScroIITTYHorz( HWND hWnd, WORD wScroiICmd, WORD wScroIIPos
//
// Description:
// Scrolls TTY window horizontally.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
// WORD wScroIICmd
// type of scrolling we're doing
//
// WORD wScrollPos
// scroll position
//
//___ _ _________________~_~_~_________
CA 02410039 2002-12-06
APPENDIX A: Page 43
BOOL NEAR ScrotI~YHorz( HWND hWnd, WORD wScroIICmd, WORD wScrotIPos )
int nScroIlAmt ;
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
switch (wScrolICmd)
case SB_TOP:
nScrollAmt = -XOFFSET( npTTYlnfo ) ;
break ;
case SB BOTTOM:
nScroIlAmt = XSCROLL( npTTYlnfo ) - XOFFSET( npTTYlnfo ) ;
break ;
case SB PAGEUP:
nScroIlAmt = -XSIZE( npTTYlnfo ) ;
break ;
case SB_PAGEDOWN:
nScroIlAmt = XSIZE( npTTYlnfo ) ;
break ;
case SB LINEUP:
nScroIlAmt = -XCHAR( npTTYlnfo ) ;
break ;
case SB_L1NEDOWN:
nScroIlAmt = XCHAR( npTTYlnfo ) ;
break ;
case SB_THUMBPOSITION:
nScroIlAmt = wScroIIPos - XOFFSET( npTTYlnfo ) ;
break ;
default:
return ( FALSE ) ;
'rf ((XOFFSET( npTTYlnfo ) + nScrollAmt) > XSCROLL( npTTYlnfo ))
nScroIlAmt = XSCROLL( npTTYlnfo ) - XOFFSET( npTTYlnfo ) ;
CA 02410039 2002-12-06
APPENDIX A: Page 44
if ((XOFFSET( npTlYlnfo ) + nScroIlAmt) < 0)
nScroIlAmt = -XOFFSET( npTTYlnfo ) ;
ScroIIWindow( hWnd, -nScrotIAmt, 0, NULL, NULL ) ;
XOFFSET( npT?Ylnfo ) = XOFFSET( npTTYlnfo ) + nScrotlAmt ;
SetScroIIPos( hWnd; SB_HORZ, XOFFSET( npTTYlnfo ), TRUE ) ;
return ( TRUE ) ;
}// end of ScroIITTYHorzQ
//---_
// BOOL NEAR SetTTYFocus( HWND hWnd )
//
// Description:
// Sets the focus to the TTY window also creates caret.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
//_____~ _~ ~_____~
BOOL NEAR SetTT'YFocus( HWND hWnd )
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
'rf (CONNECTED( npTTYlnfo ) 8~8~ (CURSORSTATE( npTTYlnfo ) ! = CS SHOW))
CreateCaret( hWnd, NULL, XCHAR( npTTYlnfo ), YCHAR( npTTYlnfo ) ) ;
ShowCaret( hWnd ) ;
CURSORSTATE( npTTYlnfo ) = CS SHOW ;
}
MoveTTYCursor( hWnd ) ;
return ( TRUE ) ;
}// end of SetTTYFocusQ
//____~_ __w___~_~___~_~_ _ ,
// BOOL NEAR Kil(TTYFocus( HWND hWnd )
//
CA 02410039 2002-12-06
APPENDIX A: Page 45
// Description:
// Kills TTY focus and destroys the caret.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
//
BOOL NEAR Kill'('TYFocus( HWND hWnd )
NPTTYINFO npTTYlnfo ;
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
if (CONNECTED( npTTYlnfo ) 8~~ (CURSORSTATE( npTTYlnfo ) ! = CS_HIDE))
HideCaret( hWnd ) ;
DestroyCaretQ ;
CURSORSTATE( npTTYlnfo ) _ CS_HIDE ;
}
return ( TRUE ) ;
}// end of KiIfTTYFocusQ
__ ____________________~ _
// BOOL NEAR MoveTTYCursor( HWND hWnd )
//
// Description:
// Moves caret to current position.
//
// Parameters:
// HWND hWnd
// handle to TTY window
//
//______________~___~_~___~__________________~~~________
BOOL NEAR MoveTTYCursor( HWND hWnd )
NPTTYINFO npTTYlnfo ;
CA 02410039 2002-12-06
APPENDIX A: Page 4G
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetwndowWord( hWnd,
GWW NPTTYINFO )))
return ( FALSE ) ;
'rf (CONNECTED( npTTYlnfo ) ~8~ (CURSORSTATE( npTTYlnfo ) & CS SHOW))
SetCaretPos( (COLUMN( npTTYtnfo ) * XCHAR( npTTYlnfo )) -
XOFFSET( npTTYlnfo ), '
(ROW( npTTYlnfo ) * YCHAR( npTTYlnfo )) - '
YOFFSET( npTTYlnfo ) ) ;
return ( TRUE ) ;
}// end of MoveTTYCursor~
int Read Fle(HWND hWnd)
FILE *f in;
NPTTYINFO npTTYlnfo
int wSelection;
char buff[128];
if (NULL = _ (npTTYlnfo = (NPTTYINFO) GetWindowWord( hWnd,
GWW_NPTTYINFO )))
return ( FALSE ) ;
if(NULL = _ (f in = fopen("comm.cfg","r")))
return (FALSE);
fscanf(f_in, "%d", (int *)BwSelection);
PORT( npTTYlnfo ) = wSelection;
fscanf(f in, "%d", (int *)BwSelection);
BAUDRATE( npTTYlnfo ) = wSeiection;
fscanf(f in, "~°d", (int *)&wSelection);
BYTESIZE( npTTYlnfo ) = wSelection;
fscanf(f in, "9'°d", (int *)&wSelection);
PARITY( npTTYlnfo ) = wSelection;
fscanf(f in, "%d", (int *)BwSelection);
STOPBITS( npTTYlnfo ) = wSelection;
fscanf(f in, "%s" , buff );
strcpy(npTTYlnfo->CommandLine, buff);
fclose(f in);
return (TRUE);
CA 02410039 2002-12-06
APPENDIX A: Page 47
//
// End of Fle: monrtor.c
//