Note: Descriptions are shown in the official language in which they were submitted.
CA 02412580 2002-11-22
1 METHOD AND APPARATUS FOR COMMUNICATING OVER A PUBLIC
2 COMPUTER NETWORK
3
4 BACKGROUND OF THE INVENTION
6
7 1. FIELD OF THE INVENTION
8 [0001] The present invention relates generally to communicating over a
public network, and
9 more particularly to processing credit card transactions over all public
computer network
11 2. DESCRIPTION OF THE PRIOR ART
12 [0002) There are three general categories of computer networks with respect
to their utilization:
13 private networks, public networks, and Virtual Private Networks (VPN's).
14
[0003] Private networks are usually encountered in business enterprises or
other organizations.
16 In these networks the network administrators may strictly control both
access to the network
17 resources and the content of traffic between the network members.
18
19 [0004] In private networks, the operating hardware, computer protocols and
the network
configuration may be strictly controlled and in most cases involve customized
hardware and/or
21 software. When the private network is constrained to one office, such
networks are usually
22 referred to as Local Area Networks (LANs). Wide Area Networks (WAN) utilize
leased
23 communication lines to create a private network over longer distances.
However, the leased lines
24 required are often expensive.
26 [0005] Public networks are generally classified as networks where a broad-
based participation of
27 users is allowed and encouraged. The Internet and the World Wide Web that
it supports is one
28 such system. However, such networks are inappropriate for corporate
communications since
29 there are no limits on who can access the network.
-1-
CA 02412580 2002-11-22
1 [0006) The Internet is a public network and is very difficult to impose
control over. Internet
2 users can "cloak" their identity by surfing the net through anonymous proxy
servers, easily
3 distribute viruses and other damaging micro programs, perform credit card
fraud, and damage
4 computer systems through hacking activities. The current state of the
Internet can therefore be
characterized as chaotic, uncontrolled and insecure.
6
7 [0007) Virtual Private Networks (VPN) are used by distributed enterprises
that desire the
8 convenience and security of a private network despite remote physical
locations of the enterprise
9 components, yet do not want to incur the extra expense of leased lines to
implement a WAN. A
VPN operates on top of an existing public network, yet provides the security
features normally
11 associated with a private network.
12
13 [0008) The following U.S. patents disclose methods for creation of VPNs
over a public network:
14 US Pat. No. 6,061,796 "Mufti access virtual private network" by James F.
Chen et al., US Pat.
No. 6,078,586 "ATM Virtual Private Networks" by Andrew J: Dugan et al., US
Pat. No.
16 6,105,132 "Computer network graded authentication system and method" by
Daniel Gene Fritch
17 et al., US Pat. No: 6,178,505 "secure delivery of information in a network"
by David S.
18 Schneider., US Pat. No. 6,205,488 "Internet protocol virtual private
network realization using
19 mufti-protocol label switching tunnels" by Liam M. Casey et al., US Pat.
No. 6,226,748
"Architecture for virtual private networks" by Henk J. Bots et al., US Pat.
No. 6,295,556
21 "Method and system for configuring computers to connect to networks using
network connection
22 objects" by Stephen R. Falcon et al., and US Pat. No. 6,055,575 "Virtual
private network system
23 and method" by Gaige B. Paulsen et al..
24
[0009) Most private computer networks and VPNs are also connected to the
Internet to provide
26 access to the Internet for their members.
27
28 [OOlOJ In computer networks, the security of the data and the communication
channel are a
29 concern to varying degrees.
-2-
CA 02412580 2002-11-22
r
1 [0011] The general principle that is applied by the prior art to
datalcornmunication security over
2 the Internet is shown in Figure A. A user 1 is attempting to communicate
with a user 2 over the
3 Internet. The User 1's computer system or network gateway, through the use
of appropriate
4 hardware or software combination, attempts to find answers to the following
questions:
1. Did I establish a connection with "User 2"?
6 2. Is the "User 2" really who it claims to be?
7 3. How do I prevent third parties from eavesdropping while the message goes
through the
8 Internet?
9
[0012] There is a wide body of prior art available describing unique methods
that generally try to
11 establish unique and innovative answers to one or more of the questions
listed above, for
12 example smart cards and their variants, and biometric technologies. Figure
B shows a more
13 general case of a user within a LAN interacting with another user within a
WAN through the
14 Internet.
16 [0013] In Figure B, the user 1 is protected from the Internet by the use of
a Firewall, which is
17 shown as Gateway 1. A firewall is a barrier between a LAN, a WAN or a
standalone client and
18 the Internet. Firewalls and gateways consist of software and hardware
components, which act as
19 an access filter. Many such filtering schemes exit: The filter checks
requests that arnve from the
Internet for a resource that is within the LAN or the WAN. The filter sends
the request to the
21 internal network if and only if the request is coming from an identifiable
source with the right to
22 access the information. If this check fails then the request is discarded.
23
24 [0014] The firewall filter attempts to answer the question of whether the
user 2 is who it claims
to be by the use of a process called authentication. This is generally
achieved through the use of
26 tokens. A token is a small piece of code that includes information about
the user, their machine,
27 the operating system identification, the Internet Protocol (IP) address and
domain names.
28
29 [0015] There are many different kinds of tokens, filters and other schemes
such as token-less
identification and biometrics etc. that serve to answer the same
authentication question. There is
-3-
CA 02412580 2002-11-22
t
1 a rich source of published material on this subject. Some of the more
popular references are:
2 Firewalls and Internet security by S. Bellovin and W. Cheswick, Addison
Wesley, Reading,
3 Mass., 1994, Building Internet Firewalls by E. D. Zicky et al., O'Riley &
Associates, 2000 and
4 Computer Forensics by W. G. Kruse II and J:G. Heiser, Addison-Wesley Pub.
Co. 2001.
6 [0016] The visible Internet chaos stems from the difficulty in identifying
hosts that are on the
7 Internet at a given time.
8
9 [0017] The Internet Protocol (IP), the transport program (TCP) and User
Datagram Protocol
(UDP) are designed and used to transmit messages between different computer
networks. Each
11 Internet interface is identified by a 32-bit Internet address. When the
Internet protocol (IP) was
12 standardized in 1981, these addresses were identified as two part objects:
a network identifier
13 and a host number within that network. The Internet numbering authorities
designate the network
14 numbers, which are unique worldwide. The network manager assigns the host
numbers within
I S their network. In 1984 a third hierarchical level called a subnet was
added to the structure. A
16 subnet is a division of the addressing space reserved for a network.
17
18 [0018] Though the uniqueness of host numbers, within one network, combined
with worldwide
19 uniqueness of the network numbers creates an impression of an ability to
uniquely identify hosts
that are on the network, generally this is not the case since Internet
addresses do not designate
21 hosts. They are identifiers of network interfaces. A host with several
interfaces will have many
22 addresses. Furthermore, the network topology can dynamically change over
time. Customers
23 may change providers, company backbones may be reorganized, and providers
may merge or
24 split. If the topology changes with time and if the addresses must somehow
reflect the topology,
then addresses will have to change from time to time. Therefore IP addresses
do have lifetimes.
26 An address Whose lifetime has expired becomes invalid.
27
28 [0019] The IP is a highly effective protocol for providing connectivity
between various computer
29 networks, but it is extremely ineffective for determining who injected a
virus onto a network or
_4_
CA 02412580 2002-11-22
1 who was hacking into a network. The underlying reason for this is that the
Internet was built as a
2 network of computers, not people.
3
4 [0020] In credit card related transactions, the system functions on the
principle that the
cardholder is the gatekeeper and controls and polices the use of that
particular card and hence his
6 credit card number as shown in Figure 11. Though this particular transaction
system works
7 reasonably well in society where physical goods and credit are exchanged on
the spot it is not
8 very effective when it is applied to the financial transactions on the
Internet. Because the credit
9 card number is transmitted through a highly insecure environment and goods
and credit
information are not exchanged on a one-to-one basis, the overall transaction
is open to fraud and
11 abuse.
12
13 [0021] Another problem with the use of credit cards on the Internet stems
from the purchaser's
14 inability to verify the legitimacy of the seller. In a real market place,
generally the existence, size
and quality of the physical establishment serves as a relative assurance to
the purchaser of the
16 legitimacy of the seller. On the Internet the apparent size and quality of
a web site has no
17 correlation to the legitimacy of the seller.
18
19 [0022] It will therefore be appreciated that the physical marketplace based
credit card system is
not well suited for financial transactions on the Internet.
21
22 [0023] It is an object of the present invention to obviate or mitigate some
of the above
23 disadvantages.
24
SUMMARY OF THE INVENTION
26 [0024) In accordance with one aspect of the present invention, there is
provided a method of
27 processing a credit card transaction between a seller and a buyer using a
credit company
28 comprising the seller sending a sender identification and a product ID to
the buyer, the buyer
29 sending a buyer ID, the seller ID, the product ID and a price to the credit
company, the credit
-5-
CA 02412580 2002-11-22
1 company sending a bill to the buyer; the credit company sending payment to
the seller, and the
2 seller sending the product to the buyer.
3
4 [0025] The present invention attempts to eliminate the premise that the
prior art is built on,
S namely that the Internet is chaotic, uncontrolled and insecure, by devising
a method to bring law
6 and order to the Internet. A much simpler method of user accountability and
traceability is
7 provided as the prime source for Internet security. With the present method,
the Internet is
8 relatively orderly and secure and therefore the need for firewalls and other
methods is diminished
9 and could potentially be eliminated in proportion to the general security
provided by this method.
11 [0026] In accordance with another aspect of the present invention, there is
provided a method of
12 logging a user into a network comprising the steps of obtaining a user ID
by registering with the
13 network, requesting a permit from an archive on the network, the archive
verifying that the use is
14 registered with the network, and the archive sending the permit to the
user.
16 [0027] In accordance with yet another aspect of the present invention;
there is provided a method
17 of communicating between a first user and a second user on a network, each
user including a
18 respective user ID and a respective SNAP ID. The method comprises the steps
of the first user
19 sending an activity request to an archive on the network, the first user
sending the activity
request to the second user, the second user sending a verification request to
the archive, and the
21 archive verifying the first user and sending the verification to the second
user.
22
23 BRIEF DESCRIPTION OF THE DRAWINGS
24 [0028] These and other features of the preferred embodiments of the
invention will become more
apparent in the following detailed description in which reference is made to
the appended
26 drawings wherein:
27 [0029] Figure A is a schematic representation of a prior art method.
28 [0030] Figure B is a schematic representation of a prior art method.
29 [0031] Figure C is a schematic representation of a prior art method.
[0032] Figure D is a schematic representation of a prior art method.
-6-
CA 02412580 2002-11-22
1 [0033] Figure 1 is a schematic representation of a communication system.
2 [0034] Figures 2 is a schematic representation of a data structure used in
the communication
3 system of Figure 1.
4 [0035] Figure 3 is a schematic representation of a data structure used in
the communication
system of Figure 1.
6 [0036] Figure 4 is a schematic representation of a data structure used in
the communication
7 system of Figure 1.
8 [0037] Figure 5 is a schematic representation of a data structure used in
the communication
9 system of Figure 1.
[0038] Figure 6 is a schematic representation of a method performed by the
correspondents of
11 Figure 1.
12 [0039] Figures 7 is a schematic representation of a method performed by the
correspondents of
13 Figure 1.
14 [0040] Figure 8 is a schematic representation of a method performed by the
correspondents of
Figure 1.
16 [0041] Figure 9 is a schematic representation of a method performed by the
correspondents of
17 Figure 1.
18 [0042] Figure 10 is a schematic representation of a method performed by the
correspondents of
19 Figure 1.
[0043] Figure 11 is a schematic representation of a method performed by the
correspondents of
21 Figure 1.
22 [0044] Figure 12 is a schematic representation of a further method
performed by the
23 correspondents of Figure 1.
24 [0045] Figure 13 is schematic representation of another method performed by
the correspondents
of Figure 1.
26 [0046] Figure 14 is schematic representation of a yet further method
performed by the
27 correspondents of Figure 1.
28
_7.
CA 02412580 2002-11-22
1 DESCRIPTION OF THE PREFERRED EMBODIMENTS
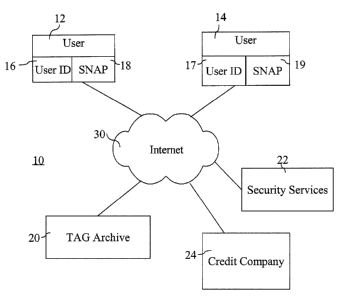
2 [0047] Referring to Figure l, a schematic representation of a network is
shown generally by the
3 numeral 10. A plurality of users, shown as a first user (User l ) 12 and a
second user (User 2) 14,
4 for the sake of example, each have a respective User ID 16, 17 and a Safe
Net Application
(SNAP) 18, 19. Each SNAP 18, I9 has an associated SNAP ID which is generated
uniquely from
6 parameters of the underlying computer system. The users are both connected
to the Internet 30
7 for communications. Also connected to the Internet 30 is a TAG Archive 20, a
Safe Net Security
8 Service 22, and a Safe Net Credit Company 24. The users 12, 14 communicate
with each other
9 over the Internet 30 by using the TAG Archive 20. The TAG Archive comprises
a plurality of
Safe Net servers. The Safe Net Security Service 22 monitors communications
through the
11 Internet 30 using the TAG Archive 20. The Safe Net Credit Company 24
provides payment
12 services to the users.
13
I4 [0048] In the following, it will be recognized that the network 10
facilitates accountability and
1 S traceability of transactions. These improvements nevertheless maintain the
richness and
16 diversity of the Internet. The User ID's 16, 17, a TAG data structure, and
the TAG archive 20
17 are used to provide accountability and traceability.
18
I9 [0049] Members of every society need a passport number to enjoy the
privileges of citizenship
associated with that society all over the world. They need a health insurance
card number to be
21 able to access the health care system. They need a driver's license number
to have access to the
22 privilege of private transportation. All modern societies are built on the
concept of licensing
23 individuals for a privilege of access to a service or a right, and in turn
demand accountability for
24 individual action. Every time the society grants a privilege to one of its
members it also provides
an ID number, which acts as the linkage between that privilege and the
accountability that
26 necessarily follows it.
27
28 [0050] Every user of the network 10 is fully registered and is given a user
ID 16, 17, also known
29 as a registration number or a personal user number, for use on the network
10. A unique
registration number will be necessary for individuals to roam on the network
10. This
_g_
CA 02412580 2002-11-22
1 registration number is keyed to an existing credit card system so that a
physical person can be
2 traced in relation to an ID number.
3
4 [0051] Therefore the goal of accountability is established through the use
ofpersonal user
numbers.
6
7 [0052] Every user of the network 10 is fully registered and has a user ID.
The host software for
8 the Safe Net also carries a unique number (product ID). Every single file
that is transmitted
9 across the network I O is given a unique file ID.
11 [0053] The host software creates a TAG for all files with all three ID
numbers, namely user ID,
12 f 1e ID, and product ID, as well as date and time. This TAG is not
destroyed even if the original
13 file is deleted.
14
[0054] Every time a file is received via the network 10, it is checked for the
presence of a TAG.
16 A file without a TAG will preferably not be processed or alternatively the
user will be positively
17 informed about the file's suspect status. Files without a TAG are also
forwarded to the Safe Net
18 security system for security reporting.
19
[0055] If the received file contains a valid TAG then its TAG is modified
immediately by adding
21 the various ID numbers of the receiving person and the computer. The TAGS
record an event
22 history of every file that is created and are thus provide traceability of
modifications to and
23 transmissions of files.
24
[0056] As soon as a user starts the Safe Net application 18, 19, it sends the
user's TAG to the
26 TAG archive 20. From this point on every activity of the user on the
network 10 is logged on the
27 Archive via modified TAGS. The Tag Archive 20 consists of a set of servers
located on the
28 Internet for the purpose of monitoring TAG activity of all of users of the
network 10.
29
_9_
CA 02412580 2002-11-22
1 [0057] The TAG system and the Archive TAG 20 jointly provide traceability of
the activities of
2 all users of the network 10.
3
4 [0058] Referring to Figures 2, 3, 4, and 5, exemplary TAGs for use with the
TAG Archive are
shown generally by the numerals 40, 40a, 40b, and 40c. Each TAG comprises a
USER ID 50,
6 SOa, SOb, SOc, a SNAP ID 51, Sla; Slb, 51c, and a Time Stamp 60, 60a, 60b,
60c. The
7 combination of a user ID, a SNAP ID, and a Time Stamp will be referred to as
a basic TAG. A
8 permit request TAG 40 is shown in Figure 2 and has the basic TAG structure.
As shown in
9 Figure 3, an activity TAG 40a includes the basic TAG and a Pass 52a, an
Activity Number 53a,
and a URL 54a. As shown in Figure 4, a check and verify TAG 40b includes the
basic TAG and
11 a Pass 52b, an Activity Number 53b, another USER ID 54b, another SNAP ID
SSb, and another
12 Pass 56b. As shown in Figure 5, an email TAG 40c includes the basic TAG and
a Pass 52c, an
13 Activity Number 53c, and an Email Address 54c.
14
1 S [0059] Referring to Figure 6, a method of logging on to the network 10 is
shown generally by
16 the numeral 100. The first user 12 wishes to log onto the network 10. It is
assumed that the first
17 user has already registered with the network 10, and thereby obtained its
User ID l 6. The SNAP
18 18 sends 102 a permit request TAG 40 to the TAG Archive 20. The Archive 20
verifies 104 that
19 the first user 12 is registered. If the first user 12 is registered, then
the Archive sends 106 a
permit to the first user 12. Then the first user 12 uses 108 the network 1 Q.
If and when the permit
21 expires and the first user 12 is still on the network 10, then step 102 is
repeated 110 to obtain a
22 fresh permit.
23
24 [0060) Referring to Figure 7, a method of downloading a file through the
network 10 is shown
generally by the numeral 200. The first user 12 wishes to download a file or
web page from the
26 second user 14. The first SNAP 18 makes 202 an activity TAG 40a. The first
SNAP sends 204
27 the activity TAG 40a to the TAG Archive 20. The first SNAP 18 then sends
206 the activity
28 TAG 40a to the second user 14. The TAG Archive 20 stores 208 the activity
TAG 40a. When the
29 web site receives 210 the activity TAG, it creates 212 a check and verify
TAG 40b. The web site
sends 214 the check and verify TAG 40b to the TAG Archive 20. The TAG Archive
20 verifies
- 10-
CA 02412580 2002-11-22
t
1 216 the first user, and sends 218 the verification to the second user 14.
The second user 14 then
2 sends 220 the file to the first user 12. The user then views 220 the
received file.
3
4 [0061 ) Referring to Figure 8, a method of modifying a file obtained from
the network 10 is
shown generally by the numeral 300. The first user obtains 302 a file through
the network 10.
6 The SNAP 18 then adds 304 a file number to the file. The file is then saved
306 to the user's
7 storage means, preferably a hard drive. When an application opens 308 or
modifies the file; the
8 SNAP 18 modifies 310 the file ID in a predetermined manner to indicate the
activity performed
9 on the file.
11 [0062) Referring to Figure 9, a method of emailing a file through the
network 10 is shown
12 generally by the numeral 400. The SNAP 18 generates 402 an email TAG. The
SNAP 18 then
13 sends 404 the email TAG to the TAG Archive 20. The SNAP 18 also sends 406
the email TAG
14 to the second user 14. The second user l4 creates 406 a check and verify
TAG and sends 410 the
check and verify TAG to the TAG Archive 20. The TAG Archive 20 verifies 412
that the first
16 user 12 is registered with the network 10 and sends 414 the verification to
the second user 14.
17 The second user then views 416 the email.
18
19 [0063) Referring to Figure 10; a method of processing a credit card payment
through the Safe
Net is shown generally by the numeral 500. The term "credit card" is used to
generically refer to
21 an electronic payment instrument settled through a financial institution
such as a credit card
22 company or a bank. Other payment instruments that provide credit or debit
accounts may also be
23 used. A seller sends 502 its seller ID and a product ID to a buyer. The
buyer sends its buyer ID,
24 seller ID, the product ID, and a price to the Safe Net Credit Company 24.
The Safe Net Credit
Company 24 sends 506 the bill to the buyer and sends 508 the payment to the
seller. Upon
26 receiving the payment, the seller sends S l O the goods to the buyer.
27
28 [0064) The following example will illustrate some of the characteristics of
the TAG system, the
29 Tag Archive 20 and the communication protocol involved.
-11-
CA 02412580 2002-11-22
1 [0065] In this example, the first user 12 and the second user 14 are both
registered members of
2 the network 10 and the first user 12 downloads a file from the second users
14's site, modifies
3 this file and e-mails it back to the second user 14.
4
[0066] The first user 12 logs onto the network 10 by initiating the Safe Net
Application (SNAP)
6 18 on a local computer, which performs the method of Figure 6.
7 1. SNAP 18 sends the following TAG 40 to the Archive 20
8
User ID 1 SNAP ID Time stamp
9
11 2. The Archive 20 verifies that the first user 12 is a registered user and
sends back a live
12 permit. This permit allows the user to operate on the network 10. It is
called live since
13 these permits are created with a definite expiry duration that might vary
from an order of
14 minutes to hours or days depending upon the characteristics of the user.
Upon expiry of
the permit, if the user is still on the network 10 and remains so, then the
SNAP 18
16 automatically asks for and receives another permit from the Archive.
17
18 3. Upon receipt of the permit from the Archive SNAP 18 makes a new TAG 40a
19
I User ID 1 ~ SNAP ID 1 ~ Pass for U 1 I Activity # ~ URL Time stamp f
21
22 This TAG is sent by SNAP 18, both to the Archive 20 and to the site that
the first user 12
23 wants to view. In this case the Activity number will correspond to "viewing
a web site."
24
4. TAG Archive 20 stores the activity under the database entry for the first
user 12.
26
27 5. The site of the second user 14 that is being visited by the first user
12 picks up the TAG
28 from the first user 12 and creates the followin TAG 406
29 UID 2 SNAP m 2 Pass for U2 Activity # UID 1 SNAP ID1
Pass for U 1 Time stamp _ 12 -
CA 02412580 2002-11-22
1 And sends this TAG 406 to the Archive 20. In this instance the Activity
Number
2 corresponds to "check and verify user".
3 6. The Archive checks this information against its database on the first
user 12 and verifies
4 its authenticity. It then sends verification to the SNAP 19 of the second
user 14.
7. The specific resource that was requested by the first user 12 is then
displayed on the first
6 user 12's computer screen.
7 8. If the first user 12 chooses to save this specific file on its hard drive
then a file number is
8 added by the SNAP 18 to that specific file that is being created. This
number can be
9 generated locally by the SNAP 18 by various means ranging from a high value
random
number to a time stamp based number. When combined with the USER ID and SNAP
ID
11 the joint number becomes unique for identification of this specific file.
12 9. If any application on the first user 12's computer opens and modifies
the file that was
13 downloaded then the file ID number is modified in a predetermined manner by
SNAP 18
14 to indicate this particular activity on the file: File ID numbers will
remain with all of the
files that are created or moved through the network 10.
16 10. The first user 12 now wants to send this file back to the second user
14 through the use of
17 e-mail. In this case SNAP 1 will generate the following TAG 40c:
18 User ID 1 SNAP IDl Pass for Ul Activity # e-mail address Time stamp
19
11. The process as shown on steps 3 - 7 for the first user 12 will be repeated
in a similar
21 manner by the second user 14 to ensure authenticity of both the second user
14 and its
22 activities on the network 10.
23
24 [0067) Like all licensed activities in our. society, traffic on the network
10 will also be open to a
certain amount of abuse and lawlessness. But over time, organizations and
societies develop
26 ways and means to minimize such activities.
27
28 [0068) It is important to note that the existence of network 10 will not
detract from the Internet,
29 as we now know it. A user will be able to use the Internet and the network
10 simultaneously
through the same browser. The SNAP software 18, 19 will function as a plug-in
to all available
-13-
CA 02412580 2002-11-22
1 browsers. It may also function as a standalone program. The users of the
network 10 will be able
2 to send and receive data from other users who are not members of the network
10, but these files
3 are clearly identified for the user's benefit. It is expected that, over
time, financial transactions,
4 official company business, and all other correspondence that necessitates a
more secure
environment will move through the network 10. The Internet and the network l0
exist
6 concurrently.
7
8 [0069] The network 10 includes two internal organizations to provide greater
service to the users
9 12, 14:
1. Safety Net Security Service 22
11 This organization functions in a similar way to the police in our society.
It investigates all
12 Network Security related issues. Any security infringement on the Safe Net
that is traced
I 3 and documented by the Security Service is turned over to local authorities
along with the
14 evidence for the purpose of prosecution of the invaders. The Security
Service is bound by
the same set of rules that the police operate under.
16
17 2. Safe Net Credit Company 24
18 The purpose of this organization is to establish and maintain a secure and
reliable financial
19 transaction service within the network 10.
21 [0070] The Safe Net Credit Company 24 differs from existing systems in a
fundamental manner
22 and follows a different credit flow pathway. Figure 10 shows this
alternative transaction method.
23
24 [0071] When using the Safe Net Credit Company 24, the "credit card number"
of the purchaser
is never released to the seller thereby substantially eliminating the
possibility of fraud by the
26 seller. Furthermore each purchase is also correlated with a User ID and a
SNAP ID. The Archive
27 20 also tracks the interaction between the buyer and the seller prior to
the finalization of the
28 transaction.
29
-14-
CA 02412580 2002-11-22
1 [0072] With the Safe Net Credit Company 24, the credit card numbers and
other personal
2 information about the purchaser should never be transmitted on the Internet.
Furthermore the
3 merchants should not have credit card numbers of their customers since web
merchants go out of
4 business frequently and the fate of their databases containing this and
other information is always
questionable. It is also preferable that the broad protocol for the network 10
be able to prevent
6 both the merchant and the purchaser against various known attacks.
7
8 [0073] These goals are preferably accomplished without resorting to
complicated encryption
9 technologies, proprietary WANs, LANs and/or other token based or biometric
systems.
11 [0074] Potential clients of the Safe Net Credit Company 24 who have a
"goad" payment track
12 record for their credit cards (Visa, Master Card, phone companies etc can
be substituted or
13 combined) receive an invitation to activate secure Internet transaction
capabilities. This letter
14 contains their personalized PIN number (which can be changed to another
number or a phrase
later on).
16
17 [0075] The potential customers go to their bank's web site, or a special
web site, to log on using
18 this number and download a self extracting and installing application,
namely the SNAP 18,
19 19(Safe Net Application).
21 [0076] Each application that is downloaded by a purchaser will have a
unique embedded product
22 identifying number/Tag: Upon installation of this application on a client's
computer the
23 application modifies the product identification number using identifiers
from the hardware
24 components of that particular computer. This modified number will be
referred to as the SNAP
ID (Safe Net Application Identification) in the text below.
26
27 [0077] The registration process is completed when the client gets on the
Internet the next time.
28 At this point the application sends the new modif ed ID and the original ID
to the Safe Net
29 central server. The user also creates a pass phrase and user name. Neither
is stored on the PC, but
rather in the Safe Net central server.
-15-
CA 02412580 2002-11-22
1 [0078] Merchants install the Safe Net merchant software package on their
server. This package
2 includes a Kerberos key; which will be used to identify the merchant on the
Safe Net. Only the
3 merchant and the Safe Net central server know the merchant's Kerberos key.
4
S [0079] In the example below it is assumed that both the buyer and the seller
(Web store) are
6 registered members of the network 10. It is also assumed that throughout
this protocol the usual
7 Internet based technologies are utilized including the HTTP (HyperText
Transfer Protocol), SSL
8 (Secure Sockets Layer) etc.
(0080] Refernng to Figure 12, the connection between the merchant and the
Safenet server is an
11 SSL connection and as well the connection between the purchaser and the
Safenet server is also
12 an SSL connection. The SSL connection provides secure communication between
the respective
13 parties. Other types of secure connections could also be used. However, no
assumptions are
14 made for the connection between the purchaser and the merchant.
16 Example:
17 1. Purchaser visits a web store, does shopping; and brings a shopping cart
to check out. The
18 shopping cart holds a list of items and their respective prices. The price
is tallied, and the
19 site asks for a payment method. Purchaser selects his preferred payment
method
2. The "clicking" of button, which is used to end the shopping activity on the
merchant's
21 web page, initiates a "request to log on" signal from the merchant's server
to the Safe Net
22 Server. This process involves sending to the Safe Net server the SNAP ID of
the
23 Merchant's SNAP. Safe Net sends back to the seller a live permit (see the
end of this
24 document for the description of the live permit) encrypted using the
merchant's secret
key (Kerberos). Merchant's SNAP modifies the live permit in a predetermined
manner
26 and sends it back encrypted in the same manner immediately. The Safe Net
central server
27 cheeks to verify if the modification to the live permit was in the pre-
approved manner, as
28 set forth more fully below. If this test is successful then the merchant
becomes live on the
29 Safe Net for the duration of the permit. After becoming "live" on the Safe
Net, the
merchant's server sends to the Safe Net, over the SSL connection:
-16-
CA 02412580 2002-11-22
1 a. A unique transaction ID associated with this particular transaction
2 b. Shopping cart content and cost and customer's preferred payment method
3 c. A time stamp as in Figure 2
4 f. The merchant sends back to the purchaser
a. The transaction number
6 b. Shopping cart content
7 c. Time stamp
8 d. MIME type helper application.
9 The MIME type helper application received by the purchaser's SNAP terminates
the
communication between the purchaser and the merchant.
11 4. In response to the incoming MIME type helper application, the
purchaser's SNAP pops
12 up a window containing the following fields:
13 a. Purchaser Login ID Field: purchaser needs to input his/her ID into this
text field.
14 b. Purchaser Password Field: purchaser needs to input his/her password to
this text
field.
16 c. Reset Button: clicking this button will clear the contents in the ID and
password
17 field.
18 d. Login Button: clicking this button will communicate to Safe Net server
with
19 specified ID and password.
e. Real Time Transaction Monitor: any transaction process message will be
21 displayed in this window. The second line in this window displays the
purchaser
22 phrase. This phrase is stored in purchaser application environment setup
file and
23 was chosen during the registration process of the purchaser to Safe Net to
24 ascertain that the observed pop up window is originating from the
purchaser's
computer and not due to some malicious applet ran by an outsider.
26 f. Order Window: The shopping cart contents will be listed in the window.
27 g. Transaction Confirmation Button: if login successful, this button will
be
28 highlighted. Clicking this button will result in confirming the current
transaction.
29 h. Cancel Button: Clicking this button will cancel the current transaction
and
terminate the program.
-17-
CA 02412580 2002-11-22
n
1 [0081) When the purchaser fills out the "purchaser log in ID" and the
"password" fields and
2 clicks on the login button, the Purchaser SNAP sands to the Safe Net server
the information that
3 is filled in the aforementioned fields and the embedded SNAP ID: If the
purchaser presses the
4 "confirm" button before the transaction times out then the purchaser's SNAP
sends to the Safe
Net server:
6 a. The unique transaction ID that was received from the merchant
7 b. The contents of the shopping cart including price and payment method.
8 [0082) For the purposes of this example we are combining: the actions of the
"log-in" button with
9 the "confirm" button.
11 [0083) The Safe Net Server identifies the matching transaction numbers and
compares the
12 transaction records
13 a. Reconciles the two identical shopping cart contents prices and payment
methods.
14 b. Verifies that two time stamps and two live permits overlap
1 S c. If all entries reconcile then
16 [0084] Safe Net identifies the card number of the purchaser from its
database (offline and
17 secure)
18 [0085) Safe Net identifies the gateway of the merchant
19 5. Safe Net connects to the acquiring bank through the merchant's payment
gateway
requests transaction clearance.
21 6. Payment gateway sends the authorization request to the Issuing bank
22 7. Issuing bank approves the transaction and issues an authorization
number.
23 8. The merchants payment gateway returns this authorization number the Safe
Net server.
24 9. Safe Net sends back to the Merchant
a. Transaction verification number and the credit card authorization number
26 b. Purchaser's Shopping cart content and value
27 c, Purchaser's shipping address (obtained from the Safe Net database)
28 (0086) The Purchaser receives an e-mail and/or notification indicating
29 a. Transaction verification number
b. Shopping cart content and value.
_ 1g _
CA 02412580 2002-11-22
1
2 [0087] As a result of this protocol the credit card numbers, expiration
dates are not exchanged
3 over an unsecured channel such as the Internet. The purchaser receives the
goods at the same
4 address that he receives his credit card invoice. The above example assumed
purchases via credit
cards. The Safe Net protocol also allows the purchaser to register its
selected bank accounts with
6 Safe Net and debit this account through Safe Net. Debit cards can also be
used with this system.
7
8 Discussion on live permits
9
[0088] The purpose of live permits is to prevent playback fraud. The
communication between
11 the purchaser and the Safe Net server or the merchant and the safe net
server can possibly be
12 recorded and then be played back to the Safe Net Server even though these
lines are both secured
13 with SSL.
14
1 S [0089] The validity of live permits that are sent from the Safe net to the
client can be anywhere
16 from few seconds to minutes depending on the application.
17
18 (0090) The Safe Net Application has an embedded mathematical formula and a
random number
19 file. The Safe Net server also has the same information.
2U
21 [0091] The client's SNAP modifies the permit using the embedded
mathematical formula and
22 the set of the random numbers as input parameters to the formula. Upon
receipt of a modified
23 random number by the client's computer the Safe Net server cheeks to see if
the modification is
24 valid. For a client to log on to the Safe Net server this particular set of
procedures have to be
25 performed correctly.
2G
27 [0092] If the permit happens to have a lifetime of l0 seconds then afterthe
completion of this
28 duration the client's SNAP automatically asks for another permit fromthe
server and repeats the
29 above process.
3U
-19-
CA 02412580 2002-11-22
1 [0093] With this approach, someone capturing the on line communication
between the client and
2 the Safe Net server has to reverse engineer the precise character of the
mathematical formula and
3 the complete set of predetermined random numbers that are used in
conjunction with this
4 formula. Only then it is possible to impersonate a client on the net.
6 [0094) It will be recognized that the Safe Net protocol mitigates some known
fraud attacks as
7 follows.
8
9 Fraud originating from SNAP ID related issues.
[0095] The connection between the physical user, hislher and the SNAP ID will
be established
11 during the actual online registration process through the use of a PIN
number that is created by
12 the card issuing bank and physically mailed to the user. SNAP IDs will be
stored on the users'
13 SNAP application embedded into the machine code.
14
[0096] If same SNAP software could be installed on two different machines then
this situation
16 would lead to replication of the same mathematical formula and the random
number array on two
17 different physical computer systems. As a result the incoming live permits
will be modified by
18 the SNAPs in the same manner by two different machines. This would not be a
problem as long
19 as the resultant SNAP IDs are unique.
21 [0097] There are two distinct aspects to this problem:
22 a) Capturing the uninstalled executable prior to its installation
23 If the uninstalled executable is captured and installed on two different
computers then two
24 different SNAP IDs will result upon completion of the registration process.
This case will not
be a cause for concern since both unique SNAP IDs will be connected to the
known user
26 during online registration.
27
28 [0098] If the captured executable is installed on two physically identical
computers then this
29 might result in creation of two Identical SNAP ID s. Including time codes
into the SNAP ID can
circumvent this difficulty.
-20-
CA 02412580 2002-11-22
1 b) Removing the hard disk from a computer which has the SNAP already
installed
2
3 [0099] The SNAP application will verify its environment upon power up. This
can be
4 accomplished by re-performing the operation that led to the unique SNAP ID
starting from the
original, embedded product ID. If the new SNAP ID does not match the old one,
then the
6 operation of the SNAP can be interrupted.
7
8 [0100] Communication playback type attacks:
9 a) Recording the communication between the merchant and Safe Net Server.
This connection is an SSL line. Even if this line is breached then the only
information that is
11 exchanged between the merchant and the Safe Net server is the unique
transaction ID for that
12 session between the merchant and the purchaser and the shopping cart
content. No financial
13 or other benefit can be derived from this information. Furthermore the live
permit issued by
14 the Safe Net server during the playback session will be different than the
one that was
previously recorded and hence live permit activity will fail for such a
transaction.
16 b) Recording the communication between the purchaser and Safe Net Server.
17 This is also an SSL line. It also has the live permit facility built in.
18 c) Recording both simultaneously
19 It will be recognized that such recording is relatively difficult to do.
Even if it were
accomplished, then it has the same live permit protection
21
22 [0101 ] Stealing of the pass phrase and user name
23 If both the pass phrase and the user name is stolen from the user then this
information cannot be
24 used by a third party on a PC with a SNAP since the SNAP ID of that PC will
not match the user
pass phrase and name. The only way to have all three coincident is if the
user's PC, pass phrase
26 and user name are all stolen at the same time. Even the theft of all three
will not necessarily lead
27 to fraud due to the shipping address'issues set forth below:
28
29
-21 -
CA 02412580 2002-11-22
a
1
2 [0102] Malicious applet attack on the purchaser's computer
3 The pop up window on the purchaser's computer can be simulated through a
malicious applet.
4 Such an applet can create a window that looks exactly like the original one
and if the user fills in
the user name and pass phrase then it can transmit this information to a third
party.
6
7 [0103] To disable such an attack, the SNAP's Pop up window uses a phrase
chosen by the user
8 during the registration process that is stored on that computer's hard
drive. The user can easily
9 verify the existence of this phrase to ensure himself that the pop up window
is created by a
resident application and not an applet from a hacker.
11
12 [0104) It will be recognized that the next level of attack might include
applets that search the
13 known hard drive location for the special "user phrase" and subsequently
display this phrase. In
14 a further embodiment designed to protect against such an attack, all such
information is stored on
the user's hard drive encrypted. However, it is recognized that the addition
of encryption of the
16 user phrase may render the complete system more difficult to use:
17
18 [0105] Fake web stores
19 It will be recognized that the possibility of committing credit card fraud
through the use of fake
web stores is mitigated. An illegitimate merchant will not have a connection
to the Safe Net
21 server. Thus the merchant to Safe Net connection will be missing from the
verification stage with
22 the Safe Net server.
23
24 [0106] Friendly fraud
If a user purchases an item from a web store via Safe Net legitimately, and if
the transaction is
26 allowed by the system then the user will not be able to claim that he/she
never purchased the
27 item due to non-repudiation capability of Safe net. The non-repudiation
capability results from
28 including the user ID, password and SNAP ID in the verification stage with
the Safe Net central
29 server.
-22-
CA 02412580 2002-11-22
1 [0107] Use of stolen cards on the web
2 Most use of stolen cards on the web is not possible with Safe Net: Users
will not be able to "add"
3 credit cards to their Safe Net profiles without first receiving the
invitation letter from their
4 issuing bank, which includes a specific credit card number.
6 [0108] Shipping address issues
7 The default shipping address of the goods that are purchased is the billing
address for the credit
8 card of the user. Users are able to redirect the purchased goods but for
this they will have to
9 answer several challenges successfully. These special challenge questions
and their answers are
established during the initial registration.
11
12 [0109] In another embodiment, the Safe Net Credit System operates in a
truncated, subset form.
13 In this instance the triangle between the purchasers, the safe net server
and the merchant can be
14 broken and the connectivity between the Safe Net system and the merchant
can be dropped out
of the requirements. In this truncated version only the connectivity between
the purchaser and
16 the Safe Net server is maintained. In figure 13; the Safe Net server is
shown to have a specific
17 relationship with an issuer. Having similar relationships with more then
one issuer is also
18 completely possible
19
[0110] Refernng to Figure 13, the Safe Net's partner issuer (or issuers)
either provides
21 (issues) new credit cards to applicants or registers the existing cards for
Internet/Safe Net usage.
22 If the applicant (purchasers in our previous example) does not have an
existing card then the
23 applicant goes through an online credit card application process. Upon
approval, the applicant is
24 informed through via mail or another secure system, which will include a
PIN and is invited to
visit a web site to upload the Safe Net application (SNAP). The installation
of the General Form
26 of the SNAP application creates a special button on the web browser (this
button will be called
27 "P4M" button meaning "Pay for Me")
28
29 [0111] Once the system is in place the following is the messaging protocol
between the parties
involved:
-23-
CA 02412580 2002-11-22
1
2 1. Purchaser visits a web store; does shopping, brings shopping cart to
check out. The
3 purchaser at this point clicks on the P4M button on his browser.
4 2. The "clicking" of the P4M button, initiates a "request to log on" signal
and the purchaser
logs on as described above. Purchaser's SNAP application forwards the
merchant's
6 shopping cart page to the Safe Net server along with a unique transaction
number.
7 3. The Safe Net server generates a credit card number and tags this number
to the
8 purchaser's original card number. The Safe Net server fills the merchant's
shopping cart
9 page using this number and with the shipping information from its database
and submits
the shopping cart page back to the merchant.
11
12 [0112] The remainder of the process proceeds as shown in figure 11.
13
14 [0l 13] The reduced version of the Safe Net Credit System potentially
brings the following
benefits;
16 1. Credit card information of the purchaser is not used directly;
17 2. Merchants do not have to modify their servers;
18 3. In-store credit cards can be registered for use on the Internet as long
as the issuer of those
19 cards can approve transactions;
4. If the purchaser registers specific bank accounts with the Safe Net server
then these
21 accounts can be selected by the purchaser for direct debit. This
transaction goes through
22 ACH system;
23 5. Debit cards can be used in the same manner:
24
[0l 14] In both the reduced and the full versions of the Safe Net system the
purchaser's PC can be
26 replaced by:
27 1. the purchaser's cell phone or a PDA (Personal Digital Assistant) -
wireless Safe Net; or
28 2. a combination of a public Internet kiosk and his cell phone - Public
kiosk with a wireless
29 device; or
-24-
CA 02412580 2002-11-22
1 3. a public Internet and a personal ID card with a magnetic stripe - Public
kiosk without a
2 wireless device.
3
4 [0115] In another embodiment of a cell phone replacement for a purchaser's
PC the system
works mostly as a proximity-purchasing device, as shown in Figure 14.
Merchants and their
6 goods are assigned unique numbers and these are displayed by the merchant. A
Safe Net client
7 who happens to be in the proximity of the merchant's location and sees an
item that he would
8 like to purchase dials the numerical coordinates of the item on his cell
phone to complete the
9 purchase.
11 [0116] In this example his cell phone communicates with Safe Net's IVR, the
voice recognition
12 unit. IVR converts the data elements originating from the cell phone and
populate an XML
13 file,which can be recognized by the merchant's web site. The rest of the
transaction between the
14 parties will follow the communication lines indicated in Figures 12 or 13.
16 [0117) In a further embodiment, a wireless phone interface is added to the
Safe Net application
17 18, 19 that uses the architecture defined above. The wireless device will
act through an IVR
18 system that behaves the same way as an Internet browser.
19
21 Sample wireless Session with wireless Safe Net
22
23 [0118] Client is in the proximity of a film theatre and would like to see
Star Wars. The client notices the
24 SafeNet logo and SafeNet location and items available for purchase as
follows:
26 Famous Players
27 SafeNet - 1138
28 Theater 1 - 2 Adults - 0 Kids = 120
29 ...
-25-
CA 02412580 2002-11-22
1 The client dials: 1800 SAFENET
2 SafeNet responds: "Welcome to Safi:Net, please enter the merchant number"
3 The client enters: 1138#
4 SafcNet responds: "You are at Famous 1'Luyers, please enter the. item yorr
wish to pLrrchase."
The client responds: 120#
6 SafeNet Steps 1,2,3,4,5
7 SafeNet responds: "Four VIS.I~ card urill be ehar~ed ###, press 1 to
confirm."
8 The client responds: 1
9 SafeNet Steps 6-12
SateNet responds: "thank you your tickets are now available; your transactiotl
code is ###"
11
12
13 Functions of the IVR
14 [0119] The IVR will require two functions (or definitions for implementing
two functions)
16 ~ data elements to Merchant or SafeNet
17 E- data elements returned from Merchant or SafeNet
18
19 Message sequencing in the wireless Safe Net
[0120] Transaction initiated from NR and responded to by Merchant.
21 ID ~ Entered by the customer orbuilt into the wireless device
22 ShoppingCart ~ item to be purchased
23 SuccessOrFailure E- if not OK then the reason the transaction failed
24 ie out of stock, bad item, etc
26 Seller SNAPID E-
27 Purchaser SNAPID
28 ShoppingCart ~ echoed back
29 TimeStamp ~
Permit E-
31 TransactionNumber ~
32
-26-
CA 02412580 2002-11-22
1 Confirm Purchase
2 [0121] Transaction initiated from NR and responded to by Safe Net
3 PurchaserSNAPID
4 SellerSNAPm
ShoppingCart -~
6 TimeStamp ~
7 Permit ~
8 TransactionNumber
9 SuccessOrFailure ~ if not OK then the reason the transaction failed
e.g. out of stock, bad item, etc
11 ShoppingCart
12 TransVerification E-
13
14 (0122] In another embodiment, the Safe Net infrastructure is accessed
through public Internet
terminals (i.e. Internet kiosks). Access to Safe Net through public kiosks can
be done in one of
16 two ways:
17 1. Customer is carrying a wireless device;
18 2. Customer accesses the system using a card with a magnetic stripe.
19
[0123] In both instances the customer surfs the net via a public terminal and
decides on a
21 purchase. When he is at the shopping cart page he dials a phone number that
is displayed on the
22 terminal. Once the phone connection between the terminal and the cell phone
is established then
23 the phone sends the encrypted SNAP ID associated with that wireless device
to the public kiosk.
24 The terminal simply forwards this message to the Safe Net server. Later on
the user also enters
his PIN number and pass phrase on his cell phone. All customer specific or
security related data
26 originates from the wireless device and is not entered into the public
terminal. The remainder of
27 the communication between the parties involved follows the same pathway as
shown in figures
28 12 or 13.
29
[0124] The second alternative assumes that the customer does not have a
wireless device and/or
31 his wireless device does not operate in that particular geographic
location. In this case the system
-27-
CA 02412580 2002-11-22
r
1 functions much like the ATMs where the customer is asked to swipe a card,
which contains his
2 SNAP ID and is followed by physical typing of his pass phrase and PIN.
3
4 [0125] Although the invention has been described with reference to certain
specific
embodiments, various modifications thereof will be apparent to those skilled
in the art without
6 departing from the spirit and scope of the invention as outlined in the
claims appended hereto.
8
-28-