Note: Descriptions are shown in the official language in which they were submitted.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-1-
METHOD AND SYSTEM OF SECURELY COLLECTING, STORING, AND
TRANSMITTING INFORMATION
BACKGROUND OF INVENTION
Technical Field
The present invention relates in general to a method and apparatus for
facilitating the completion of a transaction. The invention more particularly
relates to
electronic commerce transactions and systems to ensure the security of
confidential
information transmitted over potentially insecure communication media.
Background Art
In rapidly increasing numbers, consumers are opting to purchase products and
services online. To make purchases online, the vast majority of consumers pay
using
a conventional credit card. The increasing utilization of credit card
purchasing over
computer lines, and the incredible growth of online sales in recent years, has
highlighted the insecurity of such transactions. Systems currently in use to
authenticate and authorize information transmitted online are unable to detect
and
prevent credit card fraud and misuse.
Presently, all parties to online transactions may be at risk from the misuse
of
online sales systems and the data transmitted over electronic lines. Customers
face
potential fraudulent merchant transactions, overcharges, double billing,
impersonated
merchants, breaches of security on merchant computers, and the resulting
misuse of
information transmitted by the customer. Merchants risk losses from persons
purchasing goods with fraudulent or stolen credit cards, back charges,
impersonated
customers, computer hackers who steal customer data, employees who misuse
customer data, and other difficulties which threaten the integrity of their
data bases.
Credit card companies also risk losses from the fraud or misuse of data by
customers,
merchants and hackers.
Although the electronic sales market segment is rapidly expanding, growth has
been slowed by fear among consumers regarding the potential for misuse of
credit
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
_2_
card information transmitted online. Recent polls demonstrate that as many as
80%
of persons over 45 who utilize the Internet are reluctant to make purchases
online.
Although the use of the Internet to purchase goods and services has
highlighted
problems with the security of transactions, the risk of misuse of credit card
information is presented in more traditional methods of business transaction
as well.
For example, providing credit card information to a merchant by facsimile
transmission, telephone, or even in person does not prevent the merchant or
employees from misusing the credit card information, or from having the
information
misappropriated from that merchant's computer by hackers.
To allay customer concern over the security of Internet purchasing, system
have been developed to ensure the security of certain portions of the
transmission
process. However, these systems fail to ensure the security of the overall
transaction
and can not prevent misappropriation or misuse of credit card information.
Credit
card companies also take steps to protect customers from liability for stolen
or
misused credit card information. Even with such systems in place, consumers
are
inconvenienced by the need to scrutinize credit card statements and, where
apparent
misappropriation has occurred, the need to contact the credit card company,
cancel
credit cards, and delays inherent in obtaining new credit cards.
Credit card companies defray their losses from misappropriation of credit card
information by charging merchants increased fees for high-risk transactions
and
additional fees for charge backs. Merchants also experience losses by shipping
goods
or providing services for which they ultimately are not paid. Merchants
recapture
their losses by increasing the prices of goods sold. As a result, consumers
ultimately
pay for security breaches and the misappropriation of credit card information
through
higher interest rates on their credit cards, higher prices from merchants, and
taxes.
Information is misappropriated in several ways which current technology is
unable to prevent. Persons increasingly impersonate either a consumer or a
merchant
to obtain credit card information. Computer hackers gain unauthorized access
to
computers and the information stored on them. Although technology has been
developed to make unauthorized access more difficult, hackers have been able
to gain
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-3-
access to the computer servers of both credit card companies and merchants,
and
misappropriate credit card numbers and other sensitive information. Hackers
then sell
the misappropriated information to bulk emailing firms and/or use the numbers
to
extort payments from the merchants or credit card companies, which often pay
hackers to prevent the distribution of misappropriated information.
Computer programs have been developed to misappropriate information. For
example, software has been developed which seeks out unprotected servers and
downloads encrypted password files: The encryption is then defeated by
encryption
of an entire dictionary, and then cross-matching the encrypted passwords to
the
encrypted words from the dictionary. Software has also been developed which
will
impersonate a elected website, allowing a hacker to obtain information from
consumers who unwittingly access the impersonated website. Other software can
capture passwords, credit card numbers, or even screen images from a computer.
Yet
other programs exist which "listens" in on a particular computer data port,
forwarding
data traveling through that data port to another computer. Software also
exists which
can "reverse engineer" computer programs, bypassing unlock keys or making them
perform differently than intended.
By accessing a website's name server, a hacker can re-route a merchant's
website, so that consumers who believe they are transmitting credit card
numbers and
other information to a merchant's site are actually transmitting that
information to the
hacker. Hackers also gain access to merchant servers by emailing the webmaster
for a
particular merchant and depositing a program that captures the webmaster's
password
and returns it to the hacker, enabling access. Misappropriation of credit card
or
account information is an attractive crime because it is profitable and
perpetrators are
seldom prosecuted.
Conventional technology has focused on encryption of transmitted data and
authentication of the merchant. As seen above, such efforts fail to provide
adequate
security. Encryption of data can be defeated, or the data can be captured when
it is
not encrypted, such as at the time of transmission or after it is stored.
Hackers also
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-4-
have developed sophisticated methods of impersonating merchants, defeating
current
technology which focuses on merchant authentication.
As noted, misappropriation of credit card or other consumer information is not
limited to merchants utilizing the Internet for sales. Conventional business
transactions also carry a risk of misappropriation which is not prevented by
conventional technology. Most merchants use their computers to access the
Internet,
even if they do not make sales over the Internet. In so doing, such merchants
make
the data stored on their computer vulnerable to online hackers. Even merchants
who
do not use any computer face a risk of misappropriation of credit card or
other
information by employees.
In an attempt to alleviate some of these shortcomings, there have been a
number of U.S. patents addressing various aspects of the foregoing problems.
Reference may be made to the following U.S. patents: 5,974,367; 5,816,083;
5,974,367; 5,816,083; 4,297,569; 3,641,498; 5,886,421; 4,211,919; 4,947,163;
5,079,435; 5,033,084; 4,609,777; 4,295,039; 4,438,426; 5,206,905; 2,226,137;
RE029.259; 5,377,269; 4,609,777; 4,609,777; 4,819,267; 4,951,249; 4,959,861;
5,222,133; 5,604,343; 4,771,462; 4,408,203; 6,016,348; 6,025,785; 6,016,484;
5,590,038; 5,590,197; 5,671,279; 5,671,280; 5,677,955; 5,610,887; 5,715,314;
5,729,594; 5,742,845; 5,754,772; 5,793,966; 5,796,841; 6,025,379; 5,815,657;
5,812,668; 5,777,306; 5,367,698; 6,018,805; 6,029,150; 6,000,832; 5,777,306;
and
5,875,437.
For example, U.S. patent 6,029,150 discloses a method of payment wherein
consumers have an account with an agent. Consumers first interact with a
merchant,
who identifies the goods offered and the price desired. The consumer then
interacts
with the agent, and requests that the agent make a payment to the merchant.
However, the merchant could be impersonated and thus payments could be
made fraudulently to the wrong person. The 6,029,150 patent, therefore,
requires a
certifying authority to authenticate both the agent and the merchant. Such a
certification system is inherently awkward and undesirable. Moreover, the
customer's
private and fnancial information is stored on their local computer and subject
to
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-5-
hacker attacks. Also, the system software requires modification of all
existing web
browsers, and the setup requires the participation of a bank to open a special
account.
The patented system softwaxe can only be used with one computer. Thus there is
added unwanted complications and expense, and no protection of the transaction
data
from theft.
Accordingly, it would be highly desirable to have a system and method which
could facilitate transactions and ensure the security of data stored and
transmitted,
such as credit card information or checking account numbers.
SUMMARY OF THE INVENTION
The principal object of the present invention is to provide a new and improved
method and system of facilitating transactions in a secure manner.
Another object of the present invention is to provide a new and improved
method and system, which protects the participants from impersonation;
provides
secure communication over potentially insecure transmission media; enables
data to
be securely stored on potentially insecure computers; protects the software
and
encryption used from reverse engineering; and protects against raw data
capture.
Briefly, the above and further objects of the present invention are realized
by
providing a new and improved method and system for facilitating transactions.
A method and system facilitates transactions by enabling transactions between
and among customers, merchants, automated clearing houses, and credit card
processing centers. The inventive system authenticates parties, such as
customer,
merchant, and Gateway; and encrypts the transmitted information, as well as
provides
for secure storage of sensitive information.
BRIEF DESCRIPTION OF DRAWINGS
The above and other objects and advantages of the invention will be apparent
upon consideration of the following detailed description, taken in conjunction
with the
accompanying drawings, in which:
FIG. 1 is a block diagram of the system of the present invention;
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-6-
FIG. 2 - 4 are flow chart diagrams of the method of the present invention; and
FIG. 5 - 7 are detailed flow chart diagrams of the
GatewaylEncryption/Decryption Device communication of the method of FIGS. 2 -
4.
BEST MODE FOR CARRYING OUT THE INVENTION
The present invention will now be described in general terms to provide an
overview of the inventive method.
A. System Components
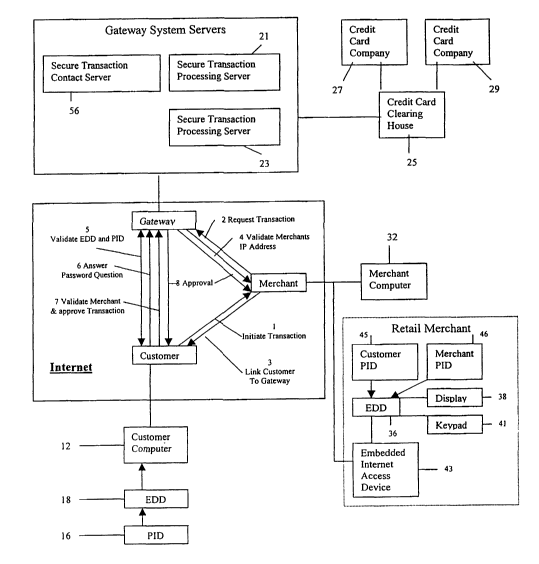
An embodiment of the present invention is described with reference to FIG. 1
wherein a tamper resistant electronic authentication and transaction system 10
is
shown and is constructed according to the present invention. The system
generally
indicated at I O works with a customer computer 12 associated with certain
information stoxed on Gateway servers 14 that store the information necessary
to
identify the customer and complete a transaction between the customer and
either an
online merchant 32, a conventional merchant 34, or another customer (not
shown)
over a potentially insecure medium. In preferred embodiments, the system 10
operates by using a customer's handheld personal identification device (PID)
16 such
as a key or card connected in communication with the customer computer 12; by
means of an incorporated intermediary Encryption/Decryption Device (EDD)
negotiate communication between the personal identification device and the
Gateway
servers 14.
Each customer has private information that he or she wishes to use to transact
with another party. This information is distributed on a plurality of servers
such as
servers 21 and 23 of the Gateway system servers 14. Where the private
information
involves financial information needed to negotiate authorization of payment
and
payment to an merchant, the Gateway servers 14 assemble the private
information and
transmit it to a processing center or credit card clearing house 25 for
authorization and
payment. In this regard, the clearing house 25 communicates with one of a
possible
number of different credit card companies, such a companies 27 and 29,
depending
upon the credit card of the customer.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
_7_.
After the customer signs up for the system's service, the customer is given
the
personal identification device 16 and encryption decryption device 18. The
encryption decryption device 18 is connected to a free port on the customer's
computer 12. Although the customer is given an encryption decryption device 18
and
a personal identification device 16, his or her personal identification
devices may be
used with any encryption decryption device.
The encryption decryption device 18 is used to negotiate digital signals
between the Gateway servers 14 and the personal identification device 16. The
encryption decryption device 18 stores a serial number specific to that
encryption
decryption device and an additional changing code which is specific to that
encryption
decryption device. The personal identification device 16 contains a serial
number and
an additional changing code, each of which are specific to that customer. The
serial
number and additional code are used to authenticate the user of the personal
identification device. Additionally, the customer preferably answers random
password question or ultimate challenge question password that are based upon
information predefined by the customer, but a personal identification number,
fixed
password or other identifying information may also be used.
Where a transaction involves a customer a~.id an online merchant computer 32,
the customer's web browser stored in the computer 12 and optional software,
the
personal identification device 16 and the encryption decryption device 18 are
used to
communicate with the Gateway server. No modification of the web browser is
needed. The online merchant only needs nominal additional software that is
added to
the online merchant's "shopping cart" to communicate with the Gateway server
and
provide the Gateway server with the merchant identity, the transaction
information,
and the method in which to contact the customer. Where a transaction involves
a
customer and a conventional merchant such as a retail merchant 34, an
encryption
decryption device 36 with a digital display 38, a keypad 41, a printer (not
shown) and
an Internet enabled communication device 43 is used to negotiate the
transaction in
preferred embodiments. In this case, the customer connects his or her personal
identification device 45 to the encryption decryption device 36, and the
encryption
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
_$_
decryption device connects with the Gateway servers 14 via an Internet service
provider 47 directly and display communications from the Gateway on its
display.
The customer then responds to the Gateway server 14, which requests via the
keypad
41 on the encryption decryption device 36. When the Gateway server
authenticates
the user and completes the transaction, the Gateway server sends the result to
the
conventional merchant via the encryption decryption device 18. The
conventional
merchant's system would only require a nominal amount of software to provide
the
transaction information and receive the transaction results.
In other embodiments of the system, software is built into the conventional
merchant's computer (not shown) to perform the transaction. In addition, the
encryption decryption device 36 may be connected to the serial port or other
port of
the conventional merchant's computer (not shown), and use as communication
device
built into its computer to communicate with the Gateway server 14. The
conventional
merchant's computer screen (not shown) and keyboard (not shown) are used to
permit
communication between the Gateway servers and the customer. The result of the
transaction is then reported directly to the conventional merchant's computer.
In either embodiment, a conventional merchant's personal identification
device may be connected to the same encryption decryption device or a
different
encryption decryption device.
With reference to FIG. l, the inventive method will now be described in
general terms. When a customer orders goods or services from an online
merchant,
the customer contacts the merchant's website via the Internet and selects
goods or
services. The merchant then sends a data packet containing the transaction
information to the Gateway system servers via the Internet or other form of
communication. This transaction information includes the merchant
identification
information, the transaction amount and the customer IP number to the Gateway
system servers 14.
Merchant connects the customer to the Gateway server via hyperlink.
Thereafter, the Gateway system servers 14 sends a request validation signal
from a
secured transaction contact server 56 of the Gateway system servers 14. In
this
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-9-
regard, the device 18 of the customer computer 12 and the secured transaction
contact
server 56 negotiate an encryption for this transaction and the device 18 acts
as a
conduit which enables the server to read and write to the personal
identification device
16. The customer's personal identification device such as a key or card,
contains the
identification and a transaction code which is created anew each time it is
used. In
this regard, a variable transaction code and identification number are sent to
the
transaction contact server for authentication puzposes.
The transaction information is stored partially in different ones of the
secured
transaction processing servers, such as the servers 21 and 22. In a
transaction
involving payment of goods or services, the Gateway system servers compile the
complete transaction information including the customer specified payment
information in volatile memory (not shown) and that is transmitted in its
complete
form to the credit card clearing house 25 or check clearing house, which in
turn
communicates with the selected one of the credit card companies, such as the
company 27, a bank or other financial institution. In other embodiments, the
compiled transaction information and financial information is sent directly to
the
credit card company, bank or other financial institution. As a result, the
financial
transaction is then either accepted or rejected. Assuming that it is accepted,
a
transaction validation signal is then sent from the Gateway system servers 14
to the
merchant computer 32 and to the customer computer to indicate that the
financial
institution is validated.
B. The inventive Method
1. Identifying the Customer and System Gateway
In preferred embodiments of the invention, the customer logs on to the
Gateway website servers and enters his or her name and address and possibly
his or
her email address. The customer is then sent an Encryption/Decryption Device
and a
Personal Information Device if he or she does not already have one. In the 10
preferred embodiment, the encryption decryption device and the personal
information
device are separate hardware devices. However, as will become apparent to
those
skilled in the art, it is equally possible to combine the two into one device.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-10-
On a different day, the customer is mailed an activation code. At this point,
the customer does not know if the system Gateway server has been impersonated,
and
the Gateway does not know yet if the customer has been impersonated.
The customer receives the encryption decryption device and personal
identification device, logs onto the website server specified in the package
and
downloads software which enables communication with a serial port or other
port on
the customer's computer. The software also detects software on the customer's
computer which may be enabled to capture keystrokes and/or information on the
screen. Reverse engineering the software would yield nothing of value, nor
will it
enable unauthorized access to the encryption decryption device or personal
identification device. The customer installs the software.
2. Authenticating the Customer and System Gateway
The customer receives the activation code and activation LTRL in the mail.
The customer logs onto the system Gateway activation website servers and
enters his
or her activation code. Software on the Gateway website displays the customer
information screen, communicates with the encryption decryption device and
verifies
the encryption decryption device serial number. The Gateway website software
initiates an encryption scheme to be used for this transaction. The ability to
encrypt
and decrypt is programmed (hard wired) into the encryption decryption device
chip
(not shown) along with its serial number. If the Gateway website server is
impersonated, the encryption decryption device and Gateway website server
would
not be able to communicate. When the encryption decryption device and the
system
Gateway server have successfully established the encrypted link, a changing
transaction code is written to the encryption decryption device and stored in
its
internal, secure non-volatile memory (not shown).
The encryption decryption device now verifies the personal identification
device with the Gateway server and initializes its transaction code. In
preferred
embodiments, light emitting diodes (not shown) on the encryption decryption
device
tell the customer whether he or she is connected to a valid Gateway server or
other
website server. A red LED acts as a pilot and lights when communication and
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-11-
encryption are being established. The red LED extinguishes and a green LED
illuminates steadily to indicate a successful connection. If the Gateway
server or
website server is being impersonated, the red LED flashes. Other LED codes can
be
used to communicate other events or status.
At this stage in the process, the mailing address has now been verified by the
activation code. The encryption decryption device has been verified by the
Gateway
server. The personal identification device has been verified by the encryption
decryption device and the Gateway server. The Gateway server has been verified
by
the encryption decryption device and the customer.
Using the activated encryption decryption device and personal identification
device, the customer logs into his or hex account and enters the following
information:
additional personal information that the customer may want disseminated to
others, a
series of questions and answers that are used later to generate random
password
question questions to be used in place of a Personal Identification Number
(PIN); a
series of questions and answers used later in the event of a subsequent random
password question failure (ultimate challenge question password); additional
email
addresses; partial card (credit and or debit) numbers; partial bank account
numbers;
and other private information.
The customer is then provided, by email, a telephone number and one-time
password to use with the call. The customer calls the number provided, enters
the one
time password and the balance of the card and bank account numbers on the
telephone
keypad.
The Gateway server requests an AVS check from all the credit and debit card
companies to verify the customer's name, address, and credit card accounts. If
the
AVS check passes, the Gateway charges the customer's bank account for the
service,
thereby verifying the checking account name, number and bank. If the bank
account
charges correctly, the customer is considered valid.
3. Making a Purchase
The present invention provides an improved method of making a purchase
whether that purchase in made online or in a conventional store.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-12-
a. Making an online purchase
In preferred embodiments of the invention, after a customer has selected the
goods or services he or she desires online at a merchant's website, the
merchant
contacts the Gateway server and transmits the merchant identification
information, the
purchase amount and the customer's IP address. The merchant then connects the
customer to the Gateway server of the system 10 via a hyperlink used to
connect with
the Gateway server, and optionally includes his or her information passed as a
command line parameter that transmits the same data packet.
The Gateway server communicates with the customer's encryption decryption
device and establishes an encryption system to be used for this transaction.
If the
encryption system cannot be negotiated, the customer clicks back to the
merchant's
website and clicks on a "Bad Connection" link which tells the merchant the
Gateway
server did not authenticate. If the encryption system does authenticate, the
personal
identification device is verified and used to authenticate this customer.
The customer is asked a random question from his or her stored question and
answer pool as opposed to a fixed password or personal identification number,
(e.g.
What is the 3rd letter of the answer to: What is my mother's maiden name?) The
customer is then asked to authenticate the merchant. At this point, the
transaction
may be cancelled by the merchant based upon a percentage which is the number
of
disputed transactions divided by the total number of transactions for this
customer.
The merchant's account on the Gateway server may pre-define an authorized
percentage that may be used to determine whether to transact with this
customer. In
the preferred embodiment, the merchant has a "percentage" value displayed to
the
customer along with the transaction information, representing the number of
disputed
transactions divided by the total number of transactions for this merchant. If
the
customer decides not to authorize the transaction, the transaction is
discontinued and
the merchant notified of the event by the Gateway server. If the customer
authorizes
the transaction, the customer then selects a payment method (checking account,
credit
card, debit card, etc.). If the payment method selected fails, the customer is
asked to
select an alternate means of payment. The merchant is then authenticated via
the
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-13-
merchant's IP address and also a secure socket layer authentication from a
certifying
authority if possessed by the merchant, and then notified of the transaction
result. The
merchant is also sent information about the customer that is either
predetermined by
the customer or selected by the customer after payment authorization is
successful.
b. Alternative embodiment - making a conventional purchase
As an alternative embodiments of the invention, a transaction can be
completed in a conventional store or restaurant according to the inventive
method.
After a customer has selected the goods or services he or she desires at a
conventional
merchant's store, the customer inserts his or hex personal identification
device in the
store's point of sale device (POS), which is an encryption decryption device
combined
with embedded Internet access.
Optimally, the merchant or particular employee also has a personal
identification device, which must be present and must also validate. The
encryption
decryption device connects with the Gateway server. The encryption decryption
device is validated and then both the customer's personal identif cation
device and the
merchant's personal identification device are validated.
The customer is asked his or her random password question. If successful, he
or she is prompted to validate the merchant and the amount. The transaction is
then
processed and the outcome returned. If the charge is denied, the customer may
select
an alternate means of payment. The Merchant is then notified of the outcome of
the
transaction.
C. The System Protocol
The tamper resistant electronic identification and transaction system operates
according to the following protocol (described in FIG. 1).
1. Between Customer and Gateway Server
In preferred embodiments of the system, the customer communicates with the
Gateway server via the Gateway website using a personal identification device
and an
encryption decryption device. The Gateway server first authenticates the
encryption
decryption device by recognizing the encryption decryption device's serial
number
and transaction code. The encryption decryption device then authenticates the
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-14-
Gateway server by the encryption scheme used by the Gateway. If the Gateway
server authenticates, the encryption decryption device and the Gateway server
calculate a new transaction code and a new encryption scheme. Preferably, LEDs
on
the encryption decryption device indicate to the customer whether he is
connected to a
valid website. A red LED acts as a pilot and lights when communication and
encryption are being established. The red LED is extinguished and a green LED
comes on steadily to indicate a successful connection. If the Gateway or the
merchant's website are being impersonated, the red LED will flash. Other LED
codes
can be used. For example, a flashing red LED could be used to indicate that
the
Gateway is being impersonated, a flashing green LED could be used to indicate
that
the merchant is being impersonated, both flashing could indicate a defective
personal
identification device, and the absence of any lit LED could be used to
indicate a
defective encryption decryption device.
The encryption decryption device then transmits the personal identification
devices serial number and transaction code to the Gateway and the Gateway uses
the
serial number and transaction code to identify and authenticate the customer.
The
customer is then asked to answer a random password question created using
questions
and answers previously provided by the customer. In some situations, an
ultimate
challenge question is needed, consisting of special questions and answers that
are only
used under certain circumstances such as reactivation of a personal
identification
device.
2. Between Customer and Merchant
In preferred embodiments of the system, the customer selects goods and
services at the online merchant's website using the customer's standard web
browser.
The online merchant communicates with the customer using a web server
connected
to a network such as the Internet. Authentication of the online merchant and
authentication of the customer are performed between the online merchant and
the
Gateway and between the customer and the Gateway. In preferred embodiments of
the system, authentication of the conventional merchant and authentication of
the
customer are performed between the conventional merchant and the Gateway and
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-15-
between the customer and the Gateway. No particular protocol is required
between
the conventional merchant and customer.
3. Between Online Merchant and Gateway Servers
In preferred embodiments of the system, the online merchant communicates
with the Gateway via a web server connected to the Internet. The online
merchant is
. authenticated by the Gateway via the online merchant's IP and optionally a
secure
socket layer authentication from a certified authority. The online merchant's
IP
address is validated on the nameservers. The Gateway is authenticated to the
online
merchant by the customer's encryption decryption device when involved in a
I O transaction with a customer. Otherwise, the online merchant uses a
personal
identification device and encryption decryption device to communicate with the
Gateway and the Gateway is authenticated by the online merchant's encryption
decryption device in the same manner as the protocol between a customer and a
Gateway.
4. Between Conventional Merchant and Gateway Servers
In preferred embodiments of the system, when the conventional merchant is
involved in a transaction with a customer, the Gateway is authenticated by the
conventional merchant's encryption decryption device in the same manner as the
protocol between a customer and a Gateway, and the customer authenticates the
conventional merchant.
If not involved in a transaction with a customer, the conventional merchant
uses a personal identification device and encryption decryption device to
communicate with the Gateway. The Gateway is authenticated by the conventional
merchant's encryption decryption device in the same manner as the protocol
between
a customer and a Gateway. The conventional merchant is authenticated by the
conventional merchant's personal identification device serial number and
transaction
code.
5. Between Customer and Customer
In preferred embodiments of the system, each customer is using a personal
identification device and an encryption decryption device. Each customer's
personal
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-16-
identification device and encryption decryption device are authenticated by
the
Gateway and the Gateway is authenticated in the same manner as the protocol
between a customer and a Gateway. Optionally, customer to customer
transactions
may be performed using a single encryption decryption device with two or more
personal identification devices connectors.
D. Detailed Description of System Components
1. The Gateway
In preferred embodiments of the system, the Gateway server 14 maintains a
number of servers and databases that store each online merchant's information,
each
conventional merchant's information, each customer's information, personal
identification device serial numbers, personal identification device
transaction codes,
encryption decryption device serial numbers, encryption decryption device
transaction
codes, and all transaction information.
Each online merchant, conventional merchant and customer is assigned one or
more accounts that is preferably accessed using a personal identif cation
device, an
encryption decryption device and preferably a random password question, but a
fixed
password or personal identification number stored on the Gateway servers may
also
be used.
The online merchant and conventional merchant information includes
merchant name, billing address, bank information, merchant account
information,
email address, telephone and fax numbers, contact names, private information,
password information and other necessary information. The private information
may
include the online merchant's bank account information, which is stored on
different
Gateway servers in the same manner as customer's private information is
stores, as
discussed below.
The customer information stored on Gateway servers includes personal
information, private information, random password question information,
ultimate
question information, and other password or personal identification number
information. The personal information includes the customer's name, phone
number,
email address, billing address, and other customer provided information. The
random
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-17-
password question information includes questions and answers provided by
customer
either at sign up or at any other time when the customer accesses his account.
The
random password question information is used as part of identifying the
customer.
The ultimate challenge question questions are questions and answers provided
by the
customer at sign up and can be changed at any time by the customer by
accessing his
personal Gateway account. The ultimate challenge question questions are used
in
situations where the personal identification device is not validating properly
or the
customer has missed a random password question.
The private information includes the customer's credit card numbers, debit
card numbers, bank account information, other payment or financial
information,
medical information or records, and other private information. The customer's
private
information is stored on two or more servers and encrypted using a unique non-
sequential encryption code, to prevent tampering. The customer provides
portions of
each item of private information online, over the phone, by mail, and/or by
fax.
Preferably, different modes are used to transmit separate portions of each
item of
information to ensure security. Private information received online is
encrypted and
stored on one or more servers, and private information received over the phone
using
the telephone keypad or other method is encrypted and stored on a separate
server or
servers.
Personal identification device serial numbers, encrypted personal
identification
device codes, encryption decryption device serial numbers, and encrypted
encryption
decryption device codes are also stored on the Gateway servers. Software on
the
Gateway servers uses the personal identification device serial numbers and
encrypted
personal identification device transactions codes to validate the personal
identification
device and identify and authenticate the customer. Software on the Gateway
servers
uses the encryption decryption device serial number and encrypted encryption
decryption device transaction code to validate the encryption decryption
device and
identify the model of the encryption decryption device to the Gateway. Being
able to
distinguish the model of encryption decryption device allows the Gateway to
upgrade
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-18-
to new encryption decryption devices without losing the ability to communicate
to
older models of encryption decryption devices.
The information stored is encrypted under a private encryption system which
differs for each customer, encryption decryption device, personal
identification
device, and merchant. This is done so that if any one part of the information
is
breached, the rest of the information is still protected. The software used on
the
Gateway can also be distributed on more than one location and chained so that
more
than one program is required to complete a transaction. Reverse engineering
one
program will not provide the information necessary to unencrypt or locate
stored data.
One or more software programs on the Gateway servers 14 are responsible for
performing certain unique tasks. One or more software programs maintain
communications between the Gateway servers and an merchant and maintain
communications between the Gateway and the customer computer. One or more
software programs authenticate the identity of the customer, the online
merchant or
the conventional merchant. One or more software programs receive merchant
identity
numbers, transaction information, customer IP address, and other necessary
information from the merchant, contacting the customer's IP address, and
displaying
the transaction information and merchant identity to the customer for
approval.
Where a transaction involves payment for goods or servers, one or more
software
programs assemble the customer's private information in volatile memory and
transmit it to the credit card processing company, credit card company,
Automated
Clearing House, bank or other financial institution for verification and
authorization
of payment. One or more software programs report the results of the credit
card
processing company or automated clearing house back to the customer and the
merchant. One or more software programs receive personal information selected
by
the customer to be given to the merchant and transmit the personal information
and
the transaction results to the merchant. Optionally, if a credit card company
or other
financial institution wished to completely remove the credit or debit card
number or
bank account number from the Internet transaction and use a numbering system
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-19-
devised by the Gateway software, then the Gateway servers would use the number
devised in place of the credit card or debit card numbers or bank account
numbers.
2. An Online Merchant
In preferred embodiments of the system, the online merchant is a merchant
who possesses or shares a network server which is connectable to a network
such as
the Internet, possesses a website, and offers goods or services to other
businesses or
consumers.
The online merchant website also possesses software, such as a "shopping
cart," to transact with the customer and allow the customer to select the
merchant's
I O goods or services.
The online merchant's software contains additional code to permit the online
merchant's website to transact with the Gateway. The software transmits the
online
merchant's merchant identity, the transaction information, and the IP address
of the
customer to the Gateway. After the customer completes the transaction with the
Gateway, the software then receives and stores a transmission from the Gateway
containing the result of the transaction.
The online merchant also possesses one or more personal identification
devices and encryption decryption devices to permit the online merchant's
employees
to access the online merchant's account on the Gateway website.
3. A Conventional Merchant
In preferred embodiments of the system, the conventional merchant is a
conventional retail merchant that offers goods or services to other businesses
or
consumers usually with a physical store. The conventional merchant has the
communication device 43 and conventional accounting software.
If the encryption decryption device does not possess add-ons (e.g., display,
keypad, printer, communication device), the encryption decryption device is
connected to a port of the conventional merchant's computer and uses a
communication device built into the conventional merchant's computer (not
shown) to
communicate with the Gateway.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-20-
The conventional merchant's computer screen and keyboard are used to permit
communication between the Gateway and the customer. Additional software is
built
into the conventional merchant's accounting software to transmit the merchant
26
identity and transaction information and record the transaction results. The
conventional merchant also possesses one or more encryption decryption devices
to
permit the conventional merchant's employees to access the conventional
merchant's
account on the Gateway website.
4. A Customer
A customer can be an individual, a business, or other entity.
a. An individual as customer - a personal account
In preferred embodiments of the system, where the customer is an individual,
the
customer signs up for a personal account with the Gateway, provides personal,
private, random password question, and ultimate challenge question password
information, and receives a unique personal identification device and
encryption
decryption device. The customer uses the personal identification device and
encryption decryption device to update the customer's account or accounts and
transact with online merchant's, conventional merchant's or other customers or
entities. The personal identification device works with any encryption
decryption
device.
More then one customer may be allowed to a personal account. This is
achieved by assigning more than one serial number and transaction code on a
personal
identification device to the personal account. The individual who establishes
the
account can authorize access, control what is accessed and deny access to the
information on the personal account.
b. A business as customer - a business account
Where the customer is a business, the person authorized to sign checks and to
charge items to that business's credit accounts (the signatory) must sign up
for a
business account with the Gateway system 10, provide the business's general
information, the business's private information, random password question
information, ultimate challenge question password question, and certain
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-21-
documentation from the business authorizing the opening of a Gateway account
and
use of the private information.
The general information includes the businesses name, address, telephone and
faa numbers, email, etc. The random password question and ultimate challenge
question password could include any questions and answers the signatory
desires,
including the same questions and answers the signatory uses on a personal
Gateway
account. No one other than the signatory will ever have access to view or
update the
random password question or ultimate challenge question password question
information. If the signatory desires to allow additional employees to view
the
transaction history, a section in the business account permits the signatory
to list the
names of additional employees to whom he desires to allow access and create
one or
more questions and answers to be used during employee activation.
A single personal identification device can possess more than one personal
identification device serial number and personal identification device
transaction
code, which can be assigned to more than one personal and/or business customer
account. In addition, each account can have different levels and areas of
access
depending upon the assigned personal identification device serial number. As
such,
the signatory can select how each employee may access the business account,
including which items of private information may be used, any limits on the
total
dollar amount that may be charged or debited, what items of the general
information
may be updated by the employee and whether or not the transaction information
may
be viewed by that person.
A personal identification device and encryption decryption device may be
mailed to the signatory for each employee listed by the signatory. The
employee is
authenticated and initializes access to the business account in one of two
ways. If the
employee already has a personal account, the employee may insert his personal
identification device into any encryption decryption device, access his
personal
account and request to add another account. The employee is then asked to
input an
activation code that is given by the Gateway to the signatory when he added
the
employee. When the activation code is entered, the Gateway matches the name on
the
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-22-
personal account with the name of the employee authorized by the signatory on
the
business account. If the name on the personal account does not match an
employee
name on the business account, the activation code is cancelled and the
transaction is
declined. If the name matches the name on the business account, the holder of
the
personal identification device is asked a question created by the signatory.
If the
holder of the personal identification device answers correctly, an additional
new
personal identification device serial number and additional new personal
identification
device transaction code is written to the personal identification device and
assigned to
the business account.
If the employee authorized by the signatory does not already have a personal
account, the signatory must gain access to the business account using the
signatory's
personal identification device and an encryption decryption device with two
personal
identification device connections (not shown), then go to the "activate an
employee"
screen. When at the "activate an employee" screen, an inactive personal
identification
device must be connected to the encryption decryption device simultaneously
with
signatory's personal identification device. The signatory is then asked to
enter the
name of the employee to activate and press a submit button. The name of the
employee being activated must match a name of an employee already authorized
to
gain access by the signatory. If the name matches, a new personal
identification
device serial number and personal identification device transaction code is
written to
the inactive personal identification device and the signatory is given an
activation
code. The signatory must then deliver the personal identification device to
the
employee. The signatory must authenticate the employee when the signatory
delivers
the personal identification device to the employee.
To complete activation of the employee, the employee must logon to the
Gateway using the personal identification device delivered to the employee by
the
signatory, input the activation code and answer the question created by the
signatory.
If either the activation code or answering the signatory's question fails, the
activation
code and activation process is cancelled and the serial number and transaction
code of
the employee's personal identification device is cancelled. If the activation
code
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-23-
passes and the employee answers the signatory's question properly, the
employee is
then asked to provide random password question and ultimate challenge question
password information and general information about the employee. Once the
random
password question information, ultimate challenge question password question
information and general information are completed, the employee is then
permitted to
create a personal account by adding personal and private information following
the
procedures of creating a personal account. If the employee decides to do so,
an
additional new personal identification device serial number and personal
identification
device transaction code are written to the personal identification device and
assigned
to a personal account.
Activation of the new personal identification device serial number and
personal identification device transaction code follows the same procedures of
creating a personal account, requiring mailing of an activation code to the
personal
billing address of the employee. The employee is then allowed access to his
personal
account and access to the business account in the manner authorized by the
signatory.
No one other than the employee, not even the signatory, will ever have access
to view
or update the random password question information and ultimate challenge
question
password question information provided.
The signatory may deny use of the business' private information by an
employee at any time simply by modifying the access permitted by the employee
in
the Gateway business account. The signatory may add or remove employees at any
time by accessing the business account.
If the signatory on the account is ever terminated, the new signatory is give
a
new and unique personal identification device serial number and personal
identification device transaction code. The new personal identification device
serial
number and personal identification device transaction code are assigned to the
account
as the new signatory, and the personal identification device serial number and
personal identification device transaction code used by the former signatory
are
cancelled. The personal identification device serial number and personal
identification device transaction code used by the former signatory may be
cancelled
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-24-
at any time, even prior to activation of the new signatory's personal
identification
device serial number and personal identification device transaction code. When
the
personal identification device serial number and personal identification
device
transaction code used by the former signatory is cancelled prior to the new
signatory's
personal identification device serial number and personal identification
device
transaction code being activated, the employees authorized access by the
former
signatory continue to be allowed access until the new signatory denies access
or the
business faxes authenticated legal documentation denying access to one or more
of all
of the employees previously allowed access.
New employees can only be allowed access by a new signatory.
The business must fax the Gateway's written request, preferably notarized,
authorizing the activation, modification or cancellation of a business
account. This
faxed authorization must be accompanied by a lawful document of the business
that
identifies the authority of the parties authorizing the activation,
modification or
cancellation.
5. A Customer
In preferred embodiments of the system, the personal identification device in
its simplest form, is an electronic device with memory which can be both read
from
and written to and requires no electricity to maintain the data. Its
embodiments
include a key, card, or other handheld configurations.
The personal identification device, such as the device 16, minimally has one
or
more serial numbers, and one or more encrypted transaction codes, but may
store
other information as needed or desired. In this embodiment, the personal
identification device 16 is a passive device, requiring an encryption
decryption device
to read from it and write to it.
The encryption decryption device contains a micro controller (not shown),
non-volatile memory (not shown) and possibly an Internet enabled device (not
shown)
such as a modem, Digital Subscriber Line, muter, cellular device or other
communication device. A unique serial number and initializing code are "hard
coded"
into the micro controller. Once written, they cannot be changed. It also has
non-
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-25-
volatile memory, which is preferably a physical part of the micro controller
and not a
separate device used to store information.
The encryption decryption device such as the device 18 communicates with
the Gateway, authenticates the Gateway and encrypts/decrypts the transaction
according to a private key system known only to it and the Gateway software.
The
private encryption key is changed with each access of the encryption
decryption
device using a non-sequential key-hopping system known only to the encryption
decryption device and the Gateway. The encryption decryption device reads from
and
writes to the personal identification device according to instructions from
the
Gateway.
In other embodiments, the encryption decryption device and personal
identification device are combined, requiring only a connection to a computer
or other
Internet enabled device to perform these functions.
The encryption decryption device may also include a digital display, a keypad,
a printer, a modem, DSL modem or router, cable modem, cellular device,
satellite or
other communication device. Where the encryption decryption device includes a
keypad, a digital display, and preferably a communication device, the
encryption
decryption device may also act as an access control device when attached to a
security
system.
The encryption decryption device can connect to a serial or other port on a
computer or other Internet enabled device. The encryption decryption device
has light
emitting diodes (LEDs) to indicate Gateway authentication success or failure,
and
personal identification device authentication success or failure. Additional
LEDs be
used to inform the customer that the encryption decryption device is receiving
power
andlor is being prompted by the Gateway server for personal identification
device
insertion.
An encryption decryption device can also be configured to accept multiple
personal identification devices and can require two or more validated personal
identification devices to enable a transaction. For example, an employee
personal
identification device might be required in an conventional merchant store
before a
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-26-
customer personal identification device can be used. Alternatively, a
signatory
personal identification device may be required to activate an employee's
personal
identification device.
In an alternative embodiment, information, or portions of information, could
be accessible to two different personal identification devices. For example,
when a
doctor needs to access a customer's medical records in an emergency and the
customer is unable to approve the transaction, an encryption decryption device
with
two personal identification device connectors would allow both to be active at
the
same time. In this embodiment, the doctor is permitted a one-time limited
access to a
protected area of the customer's personal account containing the customer's
medical
record but not his financial information. Both the customer's Gateway account
and
the doctor's Gateway account would reflect the doctor's access in the
transaction
history. A mufti-personal identification device encryption decryption device
would
allow transactions using only one personal identification device as well.
6. Version Control
The encryption decryption device devices possess an encryption decryption
device serial number. Software on the Gateway servers 14 use these serial
numbers to
determine which model encryption decryption device is being used. The software
can
then determine how to communicate with the model encryption decryption device
being used to complete the transaction. Certain features or capabilities might
only be
available to certain devices.
7. Cross Platform Note
Although, the preferred embodiment uses software on the customer computer,
it is not required. Communication between the Gateway and the encryption
decryption device is accomplished via HTTP and Java. Both the HTTP protocol
and
Java applications are executable on most, if not all currently available
customer
computers able to browse the Internet. This embodiment may not perform
properly in
some applications. An encryption decryption device may be incorporated into
these
applications, or connected to an rs232 port it will encrypt the data and
secure the
transmission.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-27-
E. Setup and Initialization
1. Personal Account setup/Initialization
In preferred embodiments of the system, explained in FIGS. 2 - 4, the customer
first inputs a portion of their personal information online in the personal
Gateway
account setup. The portion of personal information submitted includes the
name,
address, telephone and fax numbers, email addresses, etc. An activation code
is then
provided to the customer. If the customer does not already have a personal
identification device, and encryption decryption device, those devices are
separately
mailed.
The customer then accesses the Gateway signup website with his encryption
decryption device installed. The encryption decryption device serial number is
validated against the Gateway encryption decryption device database. The
encryption
decryption device such as the device 18 and the Gateway servers 14 negotiate
an
encryption system to be used solely for this transaction using a private key
encryption
system known only to the encryption decryption device and the Gateway server
software. If the negotiation fails, a LED on the encryption decryption device
flashes
to indicate the failure. A failed negotiation can indicate a defective
encryption
decryption device, a bad connection to the Gateway server, an impersonated
Gateway,
an impersonated encryption decryption device, or other fault. If the
negotiation is
successful, the private key stored in the encryption decryption device's non-
volatile
memory is updated with a non-sequential private key to be used with the next
transaction.
The customer is then prompted to connect his personal identification device to
the encryption decryption device and the Gateway verifies the serial number
and
encrypted transaction code stored on the personal identification device. If
the serial
number/transaction code information pair fail, the personal identification
device's
serial number is disabled and the customer is required to obtain an new
personal
identification device because the most likely reasons for the failure are
defective
hardware or tampering. In neither circumstance can the system allow reuse of
the
personal identification device. Alternately, the Customer may be instructed to
login to
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-28-
a Technical Support site, which could attempt a complete erasure and re-
initialization
of the personal identification device.
If the personal identification device validates, a new encryption transaction
code is written to the personal identification device's non-volatile memory to
be used
for the next,transaction. The transaction code is encrypted using a non-
sequential
private key encryption system known only to the Gateway software.
The customer now uses the one-time account activation code to login to the
customer's account and activate the personal identification device. If the
personal
identification device does not activate, a new activation code is mailed or
delivered to
the customer and assigned to the customer's account. If the personal
identification
device is activated, the customer is asked to provide password information.
There are
four types of possible passwords: a random password question, an ultimate
challenge
question password question, a fixed password, and a personal identification
number.
Where a random password question is used, the customer completes a random
password question form. The random password question form consists of field
areas
where the customer can input multiple or more questions, and corresponding
answers.
These question/answer pairs will be used later to validate customer access by
asking
for a part of the answer to the provided question. As an example, a customer
might be
prompted with 'What is the 3'a letter of the answer to: "What is my mother's
maiden
name?"'
Where an ultimate challenge question password question is used, the customer
completes an ultimate challenge question password question form. The ultimate
challenge question password question form consists of field areas where the
customer
can input three or more questions and corresponding answers.
Input of the customer's random password question and ultimate challenge
question password question can occur online at the Gateway website, by mail,
by fax,
or over the telephone. If the random password questions andlor ultimate
challenge
question passwords are input online, one or more web browser windows may be
opened and the questions and corresponding answers may be input in different
windows, stored on different servers, and assembled later when necessary.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-29-
The customer is then asked to input the customer's private information. In
this
step, the customer provides the credit card information, debit card
information, bank
account information, medical information, and any other information he would
like
transmitted securely.
The customer may provide the private information online at the Gateway
website, by mail, by fax, by telephone, and by other means of communicating
information. Preferably, portions of the credit card, debit card, and bank
account
information are entered using more than one method. When online, the customer
enters the name of each credit card, debit card, and bank account, the
corresponding
financial institutions, credit card types and or bank account types, then the
first twelve
or so digits of a credit card or debit card number, and the routing number and
first
seven or so digits of the bank account number.
After completing the online input of the first portion of private information,
the customer is given a one-time password and a telephone number, or a mail in
address or facsimile number. The customer must contact the Gateway by
telephone
using the telephone number provided by the Gateway. The customer is then asked
to
use the keypad on the telephone to enter the one-time password provided online
to the
customer by the Gateway. Once the Gateway verifies the password, the Gateway
may
request the customer to state or keyboard his name to confirm that it is the
correct
customer associated with that one-time password. If the one-time password
lookup or
customer confirmation fails, the customer must contact the Gateway through the
Gateway website to receive a new one-time password. Once the customer has
properly
entered a one-time password and the Gateway has confirmed that the customer
matches the assigned one-time password, the customer uses the keypad on the
telephone to enter the last eight digits or so of every credit card or debit
card, and the
last seven digits or so of every bank account number.
In order to better authenticate that the customer signing up for the account
is
the rightful owner or holder of the private information, the one-time account
activation password and or the personal identification device and encryption
decryption device are mailed to the billing address of one or more of the
items of
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-30-
private information. If the shipping address requested by the customer fails
to match
any of the potential billing address associated with any of the items of
private
information, the customer is asked to contact one of their financial
institutions and
change their billing address to where they want the one-time account
activation
password or personal identification device and encryption decryption device
shipped,
or they must change the shipping address of the one-time account activation
password
and/or personal identification device and encryption decryption device to
match one
or more of billing addresses of the items of private information.
Additional persons can be authorized to access certain information in an
account. For example, a parent may wish to allow a child to use the private
information of the parent's personal account. In the manner described below
for
business accounts, a parent could select which items of private information
may be
used and set a limit on the dollar amount the child may spend and or a time
period in
which it may be spent.
Any of the information being provided during signup can also be
accomplished by mail, fax, or other means of communication.
2. Business Account Setup
Setup of a customer desiring a business account occurs as follows.
In preferred embodiments of the system of the system, where the customer is
setting up a business account, only a person to whom the business's credit
card, debit
card or bank accounts are issued (a signatory) may sign up for a business
account with
the Gateway.
The first stage of the customer setup of a business account involves four
steps:
providing the business's general information, providing a signatory's random
password question information, providing a signatory's ultimate challenge
question,
and providing the business' private information.
In the first step of setup, the signatory provides the business's general
information, including the business's name, address, telephone and fax
numbers,
email, etc. The first step also includes the business sending a communication
by fax,
mail or other means of sending a communication, a legal, authenticated
document of
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-31-
the business authorizing the setup of the business account and authorizing the
signatory to use the private information provided by the signatory. This
authentication process can also be required to modify or cancel the business
account,
or change the signatory on the account.
An activation code is then mailed or delivered to the signatory. An encryption
decryption device and a personal identification device are presented in a
delivery
separate from an activation code. Unlike an encryption decryption device
shipped
during setup of a personal account, an encryption decryption device shipped to
a
signatory preferably is configured to permit the simultaneous connection of
two
personal identification devices.
After receiving the new personal identification device and encryption
decryption device, the signatory must access the Gateway signup website with
his
encryption decryption device installed. The encryption decryption device
serial
number is validated against the Gateway encryption decryption device database.
The
encryption decryption device and the Gateway negotiate an encryption system to
be
used for this transaction only using a private key encryption system known
only to the
encryption decryption device and the Gateway software.
If the negotiation fails, a LED on the encryption decryption device flashes to
indicate the failure. A failed negotiation can indicate a defective encryption
decryption device, a bad connection to the Gateway server, an impersonated
Gateway,
an impersonated encryption decryption device or other fault.
If the negotiation is successful, the transaction code stored in the
encryption
decryption device's non-volatile memory is updated with a non-sequential
transactional code to be used with the next transaction.
The signatory is prompted to connect his personal identification device to the
encryption decryption device and the Gateway verifies the serial number and
encrypted transaction code stored on the personal identification device. If
the serial
number / transaction code information pair fail, the personal identification
device's
serial number is disabled and the signatory is required to obtain an new
personal
identification device because the most likely reasons for the failure are
defective
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-32-
hardware or tampering. In neither circumstance can the system allow reuse of
the
personal identification device. Alternately, the Signatory may be instructed
to login to
a Technical Support site, which could attempt a complete erasure and re-
initialization
of the personal identification device.
If the personal identification device validates, a new encrypted transaction
code is written to the personal identification device's non-volatile memory to
be used
next time. The transaction code is encrypted using a non-sequential private
key
encryption system known only to the Gateway software.
The signatory then uses the one-time account activation password to login to
the business account at the Gateway website and activate the personal
identification
device. In addition to providing the one-time account activation password, the
signatory must enter his name and business name. Optionally, the signatory may
create a question and answer during the first step of the setup that is asked
now to
authenticate the signatory. If the one-time password, the signatory's name or
business
name do not match, the personal identification device does not activate, and a
new
activation code is mailed or delivered to the signatory and assigned to the
business
account. If the personal identification device validates, the signatory is
asked to
provide his random password question information. The random password question
could include any questions and answers he desires, including the same
questions and
answers he uses on a personal Gateway account.
Next, the signatory provides his ultimate challenge question information. The
ultimate challenge question questions also includes any questions and answers
the
signatory desires, including the same questions and answers the signatory uses
on his
personal Gateway account. No one other than the signatory a personal
identification
device is issued will ever be able access to view or update his random
password
question or ultimate challenge question password information.
The signatory next inputs the business's private information. In this area of
the account, the signatory enters the credit card information, debit card
information,
bank account information, and any other private information the business would
like
transmitted or stored securely.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-33-
During this step, where credit card, debit card, and bank account information
is
entered, the signatory enters the financial institution, the credit card type
or bank
account type, the first twelve or so digits of a credit card or debit card
number, and the
routing number and first seven or so digits of the bank account number.
The signatory must then contact the Gateway by telephone, mail or facsimile.
The signatory is asked to use the keypad on the telephone to enter one-time
password
provided to the signatory by the Gateway at the end of the second stage. Once
the
Gateway verifies the password, the Gateway requests the signatory to state
their name
to confirm that it is the correct signatory associated with that one-time
password. If
the~one-time password lookup or signatory confirmation fails, the signatory
must
contact the gateway through the Gateway website to receive a new one-time
password. Once the signatory has properly entered a one-time password and the
Gateway has confirmed that he signatory matches the assigned one-time
password, the
signatory uses the keypad on the telephone to enter the last eight digits or
so of every
credit card or debit card, and the last seven or so digits of every bank
account number.
At some point, either during the online set up process above, or after the
setup
and activation of the account, the signatory may permit additional employees
to use
the private information and or view the transaction history. If the signatory
desires to
allow additional employees use of the private information or desires to allow
additional employees to view the transaction history, a section in the
business account
permits the signatory to list the names of additional employees to whom he
desires to
allow access. Preferably, the signatory can also select how each employee may
access
the business account, including which items of private information may be
used, any
limits on the total dollar amount that may be charged or debited, what items
of the
general information may be updated by the employee and whether or not the
transaction may be viewed.
Unless the signatory indicates that the signatory already possesses additional
inactivated personal identification devices and encryption decryption devices
for the
additional employees, a personal identification device and encryption
decryption
device are mailed to the business billing address for each employee listed by
the
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-34-
signatory. The employee is authenticated and initializes access to the
business
account in one of two ways. If the employee already has a personal account,
the
employee may insert his personal identification device into any encryption
decryption
device, access his personal account and request to add another account. The
employee
is then asked to input an activation code that is given by the Gateway to the
signatory
when he added the employee. When the activation code is entered, the Gateway
matches the name on the personal account with the name of the employee
authorized
by the signatory on the business account. If the name on the personal account
does
not match an employee name on the business account, the activation code is
cancelled
and the transaction is declined. If the name matches the name on the business
account, the holder of the personal identification device is asked a question
created by
the signatory. If the holder of the personal identification device answers
correctly, an
additional new personal identification device serial number and additional new
personal identification device transaction code is written to the personal
identification
device and assigned to the business account.
If the employee authorized by the signatory does not already have a personal
account, the signatory must gain access to the business account using the
signatory's
personal identification device and an encryption decryption device with two
personal
identification device connectors, then go to the "activate an employee"
screen. When
at the "activate an employee" screen, an inactive personal identification
device must
be connected to the encryption decryption device simultaneously with the
signatory's
personal identification device. The signatory is then asked to enter the name
of the
employee to activate and hit a submit button. The name of the employee being
activated must match a name of an employee already authorized to gain access
by the
signatory. If the name matches, a new personal identification device serial
number
and personal identification device transaction code is written to the inactive
personal
identification device and the signatory is given an activation code. The
signatory
must then deliver the personal identification device to the employee. The
signatory
must authenticate the employee when the signatory delivers the personal
identification
device to the employee. To complete activation of the employee, the employee
must
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-35-
logon to the Gateway using the personal identification device delivered to the
employee by the signatory, input the activation code and answer the question
created
by the signatory. If either the activation code or answering the signatory's
question
fails, the activation code and activation process is cancelled. If the
activation code
passes and the employee answers the signatory's question properly, the
employee is
then asked to provide random password question and ultimate challenge question
password information and general information about the employee.
Once the random password question information, ultimate challenge question
password and general information are completed, the employee is then permitted
to
create a personal account by adding personal and private information following
the
procedures of creating a personal account. If the employee decides to do so,
an
additional new personal identification device serial number and personal
identification
device transaction code are written to the personal identification device and
assigned
to the personal account. Activation of the additional new personal
identification
device serial number and personal identification device transaction code
follows the
same procedures of creating a personal account, requiring delivery of an
activation
code to the personal billing address of the employee. The employee is then
allowed
access to his personal account and access to the business account (in the
manner
authorized by the signatory). No one other than that employee, not even the
signatory, will ever have access to view or update the random password
question and
ultimate challenge question password information.
The signatory may deny or limit the use of the private information by an
employee at any time simply by modifying the access permitted by the employee
in
the Gateway business account. The signatory may also input a list of
authorized
shipping addresses. The signatory may add or remove employees or change what
each
employee may access at any time by accessing the business account.
If the signatory on the account is ever terminated, the new signatory must be
issued a new personal identification device with a new serial number and
transaction
code. The new signatory must also input random password question and ultimate
challenge question password information. The personal identification device
serial
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-36-
number and personal identification device transaction code assigned to the old
signatory is cancelled.
Any of the information being provided during signup can also be
accomplished by mail, fax or other means of communication.
3. Merchant Setup
In preferred embodiments of the system, the merchant account setup occurs in
three stages.
The first stage is similar to that of setting up a customer business account.
An
authorized signatory of the merchant must provide the same general
information,
'10 private information, random password question information, and ultimate
password
information as the signatory of a customer business account. The credit or
debit card
information and checking account information of the merchant are optional, but
the
signatory must provide merchant banking information so that the Gateway can
process transactions with customers and provide payment to the merchant.
The merchant signatory first provides the merchant's general information,
including the merchant's name, address, telephone and fax numbers, email, etc.
The
merchant must send a communication by fax, mail or other means of sending a
communication a legal, authenticated document authorizing the setup of the
merchant
account and authorizing the merchant signatory to use the private information
provided by the merchant signatory. This authentication process can also be
required
to modify or cancel the business account, or change the merchant signatory on
the
account.
The merchant signatory is then mailed or delivered an activation code and an
encryption decryption device and personal identification device in separate
deliveries.
Unlike an encryption decryption device shipped during signup of a personal
account,
an encryption decryption device shipped to an merchant signatory preferably
has two
personal identification device connectors for the connection of two personal
identification devices.
After receiving the new personal identification device and encryption
decryption device, the merchant signatory must access the Gateway signup
website
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-37-
with his encryption decryption device installed. The encryption decryption
device
serial number is validated against the Gateway encryption decryption device
database.
The encryption decryption device and the Gateway negotiate an encryption
system to
be used for this transaction only using a private key encryption system known
only to
the encryption decryption device and the Gateway software.
If the negotiation fails, a LED on the encryption decryption device flashes to
indicate the failure. A failed negotiation can indicate a defective encryption
decryption device, a bad connection to the Gateway server, an impersonated
Gateway,
an impersonated encryption decryption device or other fault. If the
negotiation is
successful, the transaction code stored in the encryption decryption device's
non-
volatile memory is updated with a non-sequential transaction code to be used
with the
next transaction.
The merchant signatory is prompted to connect his personal identification
device to the encryption decryption device and the Gateway verifies the serial
number
and encrypted transaction code stored on the personal identification device.
If the
serial number / transaction code information pair fail, the personal
identification
device's serial number is disabled and the merchant signatory is required to
obtain an
new personal identification device because the most likely reasons for the
failure are
defective hardware or tampering. In neither circumstance can the system allow
reuse
of the personal identification device. Alternately, the merchant signatory may
be
instructed to login to a Technical Support site, which could attempt a
complete erasure
and re-initialization of the personal identification device.
If the personal identification device validates, a new encrypted transaction
code is written to the personal identification device's non-volatile memory to
be used
next time. The transaction code is encrypted using a non-sequential private
key
encryption system known only to the Gateway software.
The merchant signatory now uses the one-time account activation password to
login to the merchant account at the Gateway's website and activate the
personal
identification device. In addition to providing the one-time account
activation
password, the merchant signatory must enter his name and business name.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-3 8-
Optionally, the merchant signatory may create a question and answer during the
first
step of the setup that is asked now to authenticate the merchant signatory. If
the one-
time password, the merchant signatory's name or business name do not match,
the
personal identification device does not activate, and a new activation code is
mailed or
delivered to the merchant signatory and assigned to the merchant account. If
the
personal identification device validates, the merchant signatory is asked to
provide his
random password question information. The random password question could
include
any questions and answers he desires, including the same questions and answers
he
uses on a personal Gateway account.
Next, the merchant signatory provides his ultimate challenge question
information. The ultimate challenge question questions also includes any
questions
and answers the merchant signatory desires, including the same questions and
answers
the merchant signatory uses on his personal Gateway account. No one other than
the
merchant signatory a personal identification device is issued to will ever be
allowed
access to view or update his random password question or ultimate challenge
question
password information.
The merchant signatory then inputs the merchant's private information. In this
area of the account, the merchant signatory has the option of entering the
credit card
information, debit card information, bank account information (checking or
savings),
and any other private information the merchant would like transmitted or
stored
securely. More importantly, the merchant signatory inputs the merchant bank
account
information.
During this step, where credit card, debit card, and bank account information
(checking, savings, or merchant banking) is entered, the merchant signatory
enters the
financial institution, the credit card type or bank account type, the first
twelve or so
digits of a credit card or debit card number, and the routing number and first
seven or
so digits of the bank account number.
The merchant signatory must then contact the Gateway by telephone, mail or
facsimile. The merchant signatory is asked to se the keypad on the telephone
to enter
a one-time password provided to the merchant signatory by the Gateway at the
end of
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-39-
the second stage. Once the Gateway verifies the password, the Gateway requests
the
merchant signatory to state their name to confirm that it is correct merchant
signatory
associated with that one-time password. If the one-time password lookup or
merchant
signatory confirmation fails, the merchant signatory must contact the Gateway
through the Gateway website to receive a new one-time password. Once the
merchant
signatory has properly entered a one-time password and the Gateway has
confirmed
that the merchant signatory matches the assigned one-time password, the
merchant
signatory uses the keypad on the telephone to enter the last eight digits or
so of every
credit card or debit card, and the last seven or so digits of every bank
account number.
At some point, either during the online set up process above, or after the
setup
and activation of the account, the merchant signatory may permit additional
employees to use the private information and or view the transaction history.
If the
merchant signatory desires to allow additional employees use of the private
information or desires to allow additional employees to view the transaction
history, a
section in the merchant account permits the merchant signatory to list the
names of
additional employees to whom he desires to allow access. Preferably, the
merchant
signatory can also select how each employee may access the merchant account,
including which items of private information may be used, any limits on the
total
dollar amount that may be charged or debited, what items of the general
information
may be updated by the employee and whether or not the transaction information
may
be viewed.
Setup of the additional employees for a merchant account is done the same
manner as the setup of additional employees of a customer business account.
The second stage of the setup involves providing an authorization for the
Gateway to process credit card, debit card and bank account transactions for
the
merchant. The merchant must agree to the terms of the merchant agreement
provided
by the Gateway on the Gateway website and provide it to the Gateway. In
addition to
the merchant agreement, the merchant must provide a copy of a legal document
authenticating the merchant such as a business license, federal tax
identification
number, or similar document.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-40-
The third stage involves integrating the Gateway software into the online
merchant's shopping cart, or implementing the Gateway software with the
conventional merchant's accounting software if needed. This software is meant
to
permit communications between the Gateway, online merchant, conventional
merchant and/or customer. Where the Gateway software is to be implemented with
an
online merchant's shopping cart, the Gateway software contains code that must
be
inserted in the Merchant's shopping cart program. The Gateway software is used
to
authenticate the online merchant and transmit and receive communications
between
the online merchant and the Gateway. The online merchant may download the
transaction history from the Gateway website in a comma delimited or other
file
format so that the data may be imported into the online merchant's accounting
software. The merchant software is not necessary if the merchant chooses to
have the
Gateway handle his customer purchases for him. In this scenario, the merchant
has
pre-defined product service pages stored on the Gateway. The merchant simply
hyperlinks the customer to that page to enable the Gateway to process the
transaction
in this behalf.
Where the conventional merchant's accounting 'software requires additional
Gateway software to permit communications between the conventional merchant,
Gateway and customer, and automatically receive data into the accounting
software,
the conventional merchant must install the appropriate Gateway software
depending
upon the name and version of the conventional merchant's accounting software.
Additional Gateway software is not required where the conventional merchant
uses a
standalone encryption decryption device to process transactions. A standalone
encryption decryption device can possess a keypad, digital display, printer,
communication device, and other options. The conventional merchant also has
the
option of downloading the transaction history from the Gateway website in a
comma
delimited or other file format so that the data may be imported into the
conventional
merchant's accounting software.
The fourth stage involves the merchant contacting the merchant's bank and
setting up merchant services with the Gateway or contacting the merchant's
bank and
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-41-
switching Gateway services. Most of this stage is performed between the online
merchant, conventional merchant and the bank and between the bank and the
Gateway.
The fifth stage of the online merchant account activation involves changing
the online merchant's name server address to that of the Gateway. Once the
name
server addresses are switched to the Gateway, the account is activated and the
Gateway can begin taking orders on behalf of the online merchant.
F. Operation of the System
1. Customer Transaction with Online Merchant
In preferred embodiments of the system with reference to FIGS. 5 - 7, prior to
a transaction occurring, the customer must select the items or services the
customer
desires and press a checkout link on the online merchant's website. Two
different
checkout buttons can exist on the online merchant's website, a checkout button
for
those who possess a personal identification device and a checkout button for
those
who do not possess a personal identification device and wish to transact using
traditional methods that can also be handled by the Gateway using traditional
methods.
When a customer with a personal identification device presses the personal
identification device checkout button, the Gateway software implemented with
the
online merchant's shopping cart packets the transaction amount, the identity
of the
goods or services selected by the customer, the merchant identity and the
customer's
IP address. The packet of information is then transmitted to the Gateway. The
Gateway then authenticates the merchant by analyzing the merchant's IP address
and
nameserver address. If the merchant has no software installed, the
authentication
process still applies.
The customer is connected to the Gateway servers via a hyperlink to the
Gateway website. A customer can be an individual, business or other entity.
Once
contact with the customer is established, the Gateway servers attempt to
identify and
authenticate the customer.
The Gateway server contacts the encryption decryption device being used by
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-42-
the customer and requests the encryption decryption device serial number. That
number is verified in the encryption decryption device database and a request
for the
encryption decryption device to send its transaction code is sent using the
current
encryption scheme. If the encryption scheme is correct, the encryption
decryption
device calculates the next transaction code and encrypts it using the next
scheme and
sends it along with the current transaction code using the current encryption
scheme.
The Gateway calculates the next scheme and unencrypts the next transaction
code
using that scheme. If the next transaction code is incorrect, the transaction
is
terminated and the encryption decryption device flagged as invalid in the
encryption
decryption device database.
Preferably, LEDS on the encryption decryption device tell the customer
whether he is connected to a valid Gateway server. A red LED acts as a pilot
and
lights when communication and encryption are being established. The red LED is
extinguished and a green LED lights steadily to indicate a successful
connection. If
the website is being impersonated, the red LED will flash.
The personal identification device is inserted in an encryption decryption
device upon the request of the Gateway servers. The encryption decryption
device
then reads the personal identification device serial number and personal
identification
device encrypted transaction code, encrypts the personal identification device
serial
number and personal identification encrypted transaction code, then transmits
the
encrypted personal identification device serial number and personal identif
cation
device encrypted transaction code to the Gateway server. The Gateway receives
the
encrypted personal identification device serial number and personal
identification
device encrypted transaction code and unencrypts them. The Gateway first
locates the
personal identification device serial number in the personal identification
device
database then authenticates the transaction code stored in the personal
identification
device. If no matching personal identification device serial number is found,
or the
transaction code does not validate, the transaction is cancelled and the
customer and
online merchant are notified. If the personal identification device
transaction code
validates, the Gateway servers calculates the next non-sequential transaction
code,
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-43-
encrypts it and writes it to the personal identification device. The
transaction code is
read back and verified before continuing with the transaction.
If the personal identification device encryption code does not validate, the
previous personal identification device encryption code is compared to the
current
personal identification device encryption code. If they match, the transaction
continues but the Gateway servers' personal identification device serial
number
database is flagged with a duplicate personal identification device encryption
code
marker if the database was not already flagged. If the database was already
flagged,
the personal identification device is marked as invalid in the database and
the
I O customer is notified of the deactivation. The customer is then offered an
opportunity
to activate a new personal identification device by answering an ultimate
challenge
question, described below from a group of ultimate challenge question
questions he
entered when he signed up. If he fails the ultimate challenge question, or all
the
questions have already been asked, the customer's account is flagged and will
allow
no further transactions, the online merchant is notified, and an activation
code and
URL address is then delivered to the billing address of the customer of the
personal
identification device. To reactivate the account, the customer must access the
Gateway
website at the URL, insert the customer's personal identification device into
the
encryption decryption device, provide the activation code, and answer an
ultimate
challenge question. Provided the activation code is correct and the ultimate
challenge
question is answered correctly, a new serial number and transaction code are
written
to the customer's personal identification device.
If the personal identification device encryption code validates, the customer
is
then asked to answer one or more random password questions created using
questions
and answers previously provided by the customer. If the customer fails to
answer the
random question correctly, the customer is asked one or more additional random
password question questions. If the customer fails to answer the second set of
random
password questions correctly, the serial number and transaction code
associated with
that personal identification device are flagged and will allow no further
transactions
and the online merchant is notified. An activation code is then delivered to
the billing
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-44-
address of the customer of the personal identification device. To reactivate
the
account, the customer must access the Gateway website, insert the customer's
personal identification device into the encryption decryption device, provide
the
activation code, and answer an ultimate challenge question. Provided the
activation
code is correct and the ultimate challenge question is answered correctly, a
new serial
number and transaction code are written to the customer's personal
identification
device.
If the customer answers the random password questions correctly, the Gateway
then uses the information provided by the online merchant and requests that
the
customer verify the transaction information and online merchant. If the online
merchant is authenticated by the customer, the transaction may be cancelled by
the
online merchant based upon a percentage which relates to the number of
disputed
transaction divided by the number of transaction for this customer. The online
merchant selects which percentages are acceptable in the online merchant's
Gateway
merchant account. If the customer does not accept the transaction information
or
cancels the transaction, the customer is sent back to the online merchant's
website. If
the customer approves the transaction information, and desires to complete the
transaction, the customer is asked which account the customer would like to
use if
there is more than one account, and which type of payment the customer would
like to
use if there is more than one payment type. The Gateway then assembles the
customer's payment type and online merchant's merchant bank information on its
servers in secure volatile memory along with the transaction amount, and sends
it to
the appropriate company or financial institution for payment authorization or
processing. If the payment is authorized or processed, the customer and the
merchant
are notified via each party's respective IP address. If the payment is
declined or not
authorized, the customer is asked if he wishes to select a different payment
type or to
cancel the transaction. If the transaction is cancelled, the online merchant
is notified
using the online merchant's IP address. If a new payment type is selected, the
Gateway again attempts to obtain authorization or payment. If no payment type
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-45-
works, the transaction is cancelled by the Gateway and both the customer and
the
online merchant are notified via each party's respective IP address.
2. Customer Transaction with Conventional Merchant
In preferred embodiments of the system, prior to a transaction occurring, the
customer must select the items or services the customer desires and request to
pay for
the selected goods or services. The employee then enters the transaction
information
into the conventional merchant's point of sale system (accounting software)
and the
method of payment of the customer. If the transaction involves cash, the
customer
gives the cash to the employee and the sale is complete. If the transaction
involves
I O debit or credit, the accounting software requests whether the customer
wishes to use a
personal identification device, a smart caxd, or a magstripe card.
If the customer wishes to use a smart card or a magstripe card, the smart card
or magstripe card are passed through the smart card or magstripe reader on the
encryption decryption device. The encryption decryption device then connects
to the
Gateway server through a communication device. Once connected to the Gateway's
server, the server attempts to authenticate the encryption decryption device.
The Gateway server contacts the encryption decryption device and uses a
predefined encryption scheme to requests the encryption decryption device
serial
number and transaction code of the encryption decryption device. If the
encryption
scheme is correct, the encryption decryption device calculates the next
transaction
code and encrypts it using the next scheme and sends it along with the current
transaction code using the current encryption scheme. The Gateway calculates
the
next scheme and unencrypts the next transaction code using that scheme. If the
next
transaction code is incorrect, the transaction is terminated and the
encryption
decryption device flagged as invalid in the encryption decryption device
database.
Preferably, LEDs on the encryption decryption device tell the conventional
merchant
whether the conventional merchant is connected to a valid Gateway server. A
red LED
acts as a pilot and lights when communication and encryption are being
established.
The red LED is extinguished and a green LED lights to indicate a successful
connection. If the website is being impersonated, the red LED will flash.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-46-
The encryption decryption device then transmits the information from the
smart card or magstripe card to the Gateway server along with the transaction
information and merchant identity. The Gateway server then causes the amount
of the
transaction to appear on a digital display built into the encryption
decryption device
and the customer is asked to verify the transaction amount using the keypad on
the
encryption decryption device. If the customer fails to acknowledge the amount,
the
transaction is cancelled. If the customer acknowledges the amount, the Gateway
processes the transaction using the transaction information and the debit or
credit
account information from the smart card or magstripe card.
If the customer wishes to use a personal identif canon device, the accounting
software causes the encryption decryption device to connect to the Gateway
server
through a communication device internal or external to the encryption
decryption
device or internal or external to the hardware device possessing the
accounting
software. Once connected to the'Gateway's server, the server attempts to
authenticate
the encryption decryption device.
The Gateway server contacts the encryption decryption device and uses a
predefined encryption scheme to requests the encryption decryption device
serial
number and transaction code of the encryption decryption device. If the
encryption
scheme is correct, the encryption decryption device calculates the next
transaction
code and encrypts it using the next scheme and sends it along with the current
transaction code using the current encryption scheme. The Gateway calculates
the
next scheme and unencrypts the next transaction code using that scheme. If the
next
transaction code is incorrect, the transaction is terminated and the
encryption
decryption device flagged as invalid in the encryption decryption device
database.
Preferably, LEDs on the encryption decryption device tell the Customer
whether he is connected to a valid Gateway server. A red LED acts as a pilot
and
lights when communication and encryption are being established. The red LED is
extinguished and a green LED lights to a successful connection. If the website
is
being impersonated, the red LED will flash.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-47-
The encryption decryption device then reads the personal identification device
serial number and personal identification device encrypted transaction code,
encrypts
the personal identification device serial number and personal identification
device
encrypted code, then transmits the encrypted personal identification device
serial
number and personal identification device encrypted transaction code along
with the
transaction information and merchant ID to the Gateway server. The Gateway
receives
the encrypted personal identification device serial number and personal
identification
device encrypted code and unencrypts them. The Gateway first locates the
personal
identification device serial number in the personal identification device
database then
authenticates the transaction code stored in the personal identification
device. If no
matching personal identification device serial number is found, or the
transaction code
does not validate, the transaction is cancelled and the customer and online
merchant
are notified. If the personal identification device transaction code
validates, the
Gateway server calculates the next non-sequential transaction code, encrypts
it and
writes it to the personal identification device. The transaction code is read
back and
verified before continuing with the transaction.
If the personal identification device encryption code does not validate, the
previous personal identification device encryption code is compared to the
current
personal identification device encryption code. If they match, the transaction
continues but the Gateway servers' personal identification device serial
number
database is flagged with a duplicate personal identification device encryption
code
marker if the database was not already flagged. If the database was already
flagged,
the personal identification device is marked as invalid in the database and
the
customer is notified of the deactivation. The customer is then offered an
opportunity
to activate a new personal identification device by answering an ultimate
challenge
question from a group of ultimate challenge question questions he entered when
he
signed up. The ultimate challenge question appears on the display on the
encryption
decryption device and the customer must use the keypad on the encryption
decryption
device to respond. If he fails the ultimate challenge question, or all the
questions have
already been asked, the customer's account is flagged and will allow no
further
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-48-
transactions, the merchant is notified, and an activation code is then
delivered to the
billing address of the customer of the personal identification device. To
reactivate the
account, the customer must access the Gateway website, insert the customer's
personal identification device into the encryption decryption device, provide
the
activation code, and answer an ultimate challenge question. Provided the
activation
code is correct and the ultimate challenge question is answered correctly, a
new serial
number and transaction code are written to the customer's personal
identification
device.
If the personal identification device encryption code validates, the customer
is
then asked to answer one or more random password questions created using
questions
and answers previously provided by the customer. The one or more random
password
questions appear on the display on the encryption decryption device and the
customer
must use the keypad on the encryption decryption device to respond. If the
customer
fails to answer the random question correctly, the customer is asked one more
additional random password question questions. If the customer fails to answer
the
second random password question correctly, the serial number and transaction
code
associated with that personal identification device are flagged and will allow
no
further transactions and the conventional merchant is notified. An activation
code is
then delivered to the billing address of the customer of the personal
identification
device. To reactivate the account, the customer must access the Gateway
website,
insert the customer's personal identification device into the encryption
decryption
device, provide the activation code, and answer an ultimate challenge
question.
Provided the activation code is correct and the ultimate challenge question is
answered correctly, a new serial number and transaction code are written to
the
customer's personal identification device.
If the customer answers the random password questions correctly, the
Gateway then uses the information provided by the conventional merchant and
request
that the customer verify the transaction information and the conventional
merchant
using the keypad on the encryption decryption device. If the customer does not
accept
the transaction information or cancels the transaction, the conventional
merchant is
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-49-
notified via the encryption decryption device and the conventional merchants
hardware device possessing the accounting software. If the customer approves
the
transaction information, and desires to complete the transaction, the customer
is asked
via the digital display on the encryption decryption device which account the
customer would like to use if there is more than one account, and which type
of
payment the customer would like to use if there is more than one payment type.
The
customer responds using the keypad on the encryption decryption device and the
encryption decryption device forwards the response to the Gateway. The Gateway
then assembles the customer's payment type and conventional merchant's
merchant
bank information on its servers in secure volatile memory along with the
transaction
amount, and sends it to the appropriate company or financial institution for
payment
authorization or processing. If the payment is authorized or processed, the
customer
and the merchant axe notified via the conventional merchant's accounting
software. If
the payment is declined or not authorized, the customer is asked if he wishes
to select
a different payment type or to cancel the transaction. If the transaction is
cancelled,
the conventional merchant's accounting software is notified via the encryption
decryption device. If a new payment type is selected, the Gateway again
attempts to
obtain authorization or payment. If no payment type works, the transaction is
cancelled by the Gateway and conventional merchant's accounting software is
notified via the encryption decryption device.
3. Customer Transaction with Customer
If one Gateway customer wishes to transact with another Gateway customer,
one customer can login to his account and specify an amount to transfer from
his
checking account to the other customer's checking account. Each customer is
assigned
a customer ID number during the initial setup of each customer account. The
receiving customer's ID number is specified to identify the transfer
recipient.
If the transaction involves transfer of goods, the paying customer can elect
to
put money from his checking account into an escrow account where the money
will be
dispersed when goods arrive at a bonded warehouse.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-50-
Another option is to place funds in the holding account until the customer
paying authorizes the release upon completion of a specified event such as
receipt of
shipment.
In either situation, the Gateway servers assemble the bank account information
from each customer's account in volatile memory along with the transaction
amount
and transmits the information to the pertinent company or financial
institution for
authorization or processing. Both parties are then notified of the result via
their
accounts and e-mail.
The Customer Account
When a customer signs up with the system 10, an account is established on a
server of FIG. 1. This account maintains the following information. The
customer
may login and review or modify his or her information whenever he or she
chooses.
In order to review or modify the customer account, an encryption decryption
device and personal identification device are required for authentication (see
the
authentication sheet for details). The following is an example of one form of
a
customer account information:
~ Name
0 Company
~ Department
0 Address
~ City
0 State
~ Zip
0 Country
~ Daytime Telephone
CI Evening Telephone
~ Email address 1
~ Email address2
0 Email address3
D Fax number
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-51-
The checkboxes specify which information to make available to merchants Cards:
Visal Visa Name on the card 4711 2013
Visa2 Visa Name on the card 4690 1390
MC 1 MasterCard Name on the card 1103 1111
Discoverl Discover Name on the card 3333.1212
Amexl American Express Name on the card 4567 .100
The Card names (underlined) above are user-defined names)
0 Allow repetitive Billing
If Allow Repetitive Billing is checked:
Repetitive or delayed billing is authorized with the following companies:
Check to require per incident authorization.
CI ABC Company
19.95
per month
for 12 months
~ DEF Company
29.95
1 time after 04-10-2000
25.00 Max Shipping
2.90 Max Tax
~ GHI Copany
$2500.00
1 times) after
upon notice o- f shipment
Transaction History
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-52-
The customer is able to review his or her history in order of newest-to-
oldest.
The initial display is shown in summary form with hyperlinks to view details
about
each transaction.
An option to download a statement is available. The download format is
compatible with conventional accounting packages.
The Merchant Account
When a merchant signs up with the system 10, an account is established on a
server FIG. 1. This account maintains the following information. The merchant
may
login and review or modify his or her information whenever he or she chooses.
In order to review or modify the merchant account, an encryption decryption
device and personal identification device are required for authentication. The
following is an example of one form of a merchant account information:
~ Contact Name
~ Company
~ Department
~ Address
~ City
~L State
~ Zip .
~ Country
~~ Daytime Telephone
0 Evening Telephone
~ Email address 1
~ Email address2
0 Email address3
~ Fax number
The checkboxes specify which information to make available to Customers
Transaction History
The Merchant is able to review his or her history in order of newest-to-
oldest.
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-53-
The initial display is shown in summary form with hyperlinks to view details
about
each transaction.
An option to download a statement is available. The download format is
compatible with popular accounting packages.
Authentication Process
The information packet is received from the merchant once direct contact has
been made with the customer, this server finds and connects to the attached
encryption
decryption device (Encryption/Decryption Device).
The encryption decryption device's serial number is verified and then its
transaction code is read and verified. The serial number is a burned-in code-
protected
read-only number embedded in the microcontroller (not shown) of the
encryption/decryption device of FIG. 1. The transaction code is an encrypted
non-
sequential variable value identifying the previous transaction residing in non-
volatile
memory. If the serial number does not exist in the encryption decryption
device
database, the transaction is denied. The previous transaction identified by
the
transaction code is queried to see if this encryption decryption device serial
number is
the same as the one identified last time. If not, the customer to whom the
encryption
decryption device was issued is notified via email and mail to return it for a
replacement unit. The customer and merchant are notified of the failed
transaction. If
the serial number and transaction code are both verified, a new key is
calculated and
negotiated between the Gateway and the encryption decryption device. This key
will
be used to encrypt all the information used throughout this transaction.
The encryption decryption device reads the personal identification device
(Personal Information Device) information and sends it to this server. The
sewer
verifies the personal identification device serial number and transaction code
and
refuses the transaction if the serial number is not valid. If the transaction
code does
not validate, its previous transaction code is compared to its current value.
If they
match, the transaction continues but the personal identification device serial
number
database is flagged with a duplicate transaction code marker if the database
was not
already flagged. If the database was already flagged, the personal
identification
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-54-
device is marked as invalid in the database and the customer is notified of
the
deactivation.
The customer is ten offered an opportunity to activate a new personal
identification device by answering a reactivation question from a group of
personal
questions he or she entered when he or she signed up. If he or she fails the
question,
or all the questions have already been asked, he or she is notified that he or
she must
repeat the signup process. If he or she answers correctly,.a new serial number
and
transaction code are written to the personal identification device.
The customer is then asked a random password question randomly derived
from his or her personal information provided at signup. The random password
questions are not taken from the set of questions used for reactivation. If he
or she
fails the random password question twice, his or her personal identification
device is
deactivated and he or she must reactivate it as described above.
The Merchant Packet contains (example only):
The Merchant's ID
Customer's IP address or Repetitive Billing code
Transaction Description
Transaction Amount
Shipping & Handling
Sales Tax
Tax rate
Transaction type: P or N (Preferred or Normal)
The window on the customer's screen presents with (example only)
Merchant business name
Merchant address
Merchant telephone number
Merchant email address
Transaction description
Transaction amount
Shipping amount
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-55-
Sales tax amount ,
Tax rate
C~ Repetitive Billing
~ - times) ~ after (date)
0 Weekly
~ BI weekly
~ Monthly
0 Yearly
Max tax
Max shipping
~ Authorized only upon notice of shipment
0 Per incident authorization required
Comments:
Card to use:
0 Visal
0 Visa2
~ MC 1
0 Discoverl
0 American Express 1
~ Yes, I authorize this
D No, this isn't what I agreed to
~ I have never heard of this merchant
Repetitive Billing
If a merchant wishes to initiate a periodic billing to the customer, the
merchant
CA 02418096 2003-O1-31
WO 02/01462 PCT/USO1/20216
-5 6-
contacts the transaction server (FIG. 1) and sends a merchant packet with the
IP
address changed to the proper periodic billing code. If the customer has
specified to
allow repetitive billing, the transaction is processed and a confirming email
sent to the
customer.
If the customer has elected not to allow repetitive billing, he or she is
emailed
a Request to Authorize. The customer must contact the server and authorize the
transaction before it can be processed. The merchant receives the results of
the
customer and card company response if applicable.
Other Applications
The random password question portion of the system 10 can be replaced with
other forms of identification techniques. For example, a bionetic (sometimes
called
biometric) identification system such as a fingerprint, retina scan or other
biological
identifying device, may also be used.
Non financial information exchange
A customer may pre-enter personal information and instruct the Gateway to
make certain portions automatically available to participating websites he or
she is
browsing which ask for user input. Instead of filling out a particular form,
the
customer could simply click on a button or link and the Gateway provides the
' information to the website. The customer account on the Gateway could also
include
the storage of specific logins and passwords for various websites the customer
frequents. A link to the Gateway on the website provides the customer's IP
address to
the Gateway which validates the customer and automatically logs the customer
into
the website.