Note: Descriptions are shown in the official language in which they were submitted.
CA 02424782 2003-04-09
Persistent Authorization Context
z Based On External Authentication
3
4 RELATED PATENT APPLICATIONS
s The present patent application is related to U.S. Patent Application No.
6 09/886,146, titled "Methods And Systems For Controlling The Scope Of
Delegation Of Authentication Credentials", filed June 20, 2001, which is
hereby
s incorporated by reference.
9
TECHNICAL FIELD
to
This invention relates generally to computer access control, and more
11
particularly to methods and systems for providing a local system authorization
12
context for a user based on an external authentication of the user.
13
la BACKGROUND
15 Access control is paramount to computer security. To protect the integrity
16 of computer systems and the confidentiality of important data, various
access
I~ control schemes have been implemented to prevent unauthorized users and
18 malicious attackers from gaining access to computer resources.
1v To ensure the comprehensiveness of computer security, access control is
zo often implemented on various levels. For instance, on the level of one
computer, a
z1 user is typically required to go through a logon procedure in which the
computer
zz determines whether the user is authorized to use the computer. In addition,
on the
23 level of a computer network, a user is commonly required to go through a
user-
za authentication process for purposes of controlling the user's access to
various
z5 network services. Even after a network access control server has
authenticated the
Lts & HQyer. PLLC I 05100110.8 MSI-868USPATAPP
CA 02424782 2003-04-09
user, the user may still have to request a permit for a specific server in
order to
z access that service. Various schemes based on different protocols, such as
the
3 Kerberos 5 protocol, have been proposed and implemented for controlling
network
a access control by means of user authentication.
s Generally, the user logon for a computer and the user authentication for
6 network access control are two separate procedures. Nevertheless, to
minimize
the burden on a user in dealing with the different access control schemes, the
user
s logon and the user authentication for network access are sometimes performed
9 together. For example, in the case where the user authentication is
implemented
to under the Kerberos protocol, when the user logs on the computer, the
computer
~ 1 may also initiate a Kerberos authentication process. In the Kerberos
~2 authentication process, the computer contacts a Kerberos Key Distribution
Center
i3 (KDC) to first obtain a ticket-granting ticket (TGT) for the user. The
computer
~4 can then use the TGT to obtain, from the KDC, a session ticket for itself.
~s As networks have evolved, there has been a trend to have multiple tiers of
~6 server/service computers arranged to handle client computer requests. A
simple
m example is a client computer making a request to a World Wide Web website
via
1 s the Internet. Here, there may be a front-end web server that handles the
formatting
r9 and associated business rules of the request, and a back-end server that
manages a
zo database for the website. For additional security, the web site may be
configured
z, such that an authentication protocol forwards (or delegates) credentials,
such as,
zz e.g., the user's TGT, andl'or possibly other information from the front-end
server to
z3 a back-end server. This practice is becoming increasingly common in many
za websites, and/or other multiple-tiered networks.
Ltt do Hayu. PGLC 05100.1018 MS!-B68USPAT-APP
CA 02424782 2003-04-09
Delegation and other like techniques are useful when all of the
z servers/services and the client agree to use the same authentication
process. There
3 is not, however, just one authentication process in use today. Co-pending
U.S.
a Patent Application No. 09/886,146 presents improvements for controlling the
s delegation.
If the user is authenticated for a network/system, then there is usually one
or more additional authorization access control checks to prevent the user
from
s accessing resources that he/she is not authorized to access. Once a user has
been
9 authenticated and passed the applicable access control checks, the user is
said to
to be "authorized". In certain systems, for example, access control is based
on
1 ~ having access control lists (ACLs) for the various services and resources
(i.e.,
~z objects). An ACL usually includes access control entries (ACEs), in which
zero or
13 more security identifiers (SIDs) may be included. SIDs may be associated
with
~a one user or groups of users allowed to access the object. If there are no
SIDs in
,s the ACL, then no user will have access to the object. If there are SIDS in
the ACL,
16 then users that can produce at least one matching SID will be allowed to
access the
t~ object.
Thus, when an authenticated user logs on, an authentication context is
,9 created for the user, for example, by generating a token (e.g., an access
token) that
zo is associated with the user. The token typically includes SIDS that are
associated
z1 with the user. For example, the user's token may include a unique SID
assigned to
zz the user plus a group SID assigned to the user's business department. When
the
zs user attempts to access an object the object's ACL is compared to the
user's token.
za If the user's token includes at least one SID that matches a SID within the
object's
zs ACL, then the authenticated user is authorized to access the object in some
Lee & Haya, PGLC 03100:1018 MSI-868USPATAPP
CA 02424782 2003-04-09
manner. For example, the user may have read and write permissions for a file
2 generated by other members of his/her business department (i.e., another
group
member).
a Such authorization schemes tend to work very well for systems that are
s carefully controlled and managed. For example, an enterprise level computer
network within a corporation usually provides a cohesive environment wherein
the
users and ACLs can be carefully controlled by a centralized and/or distributed
authentication and access control system. On the other hand, for very large
nerivorks, e.g., the Internet, and/or otherwise significantly non-cohesive
networks,
io authentication and access control can be much more difficult, especially
when
i 1 there is a desire to serve as many of the users as possible, including
users that do
iz not have local access control accounts. As software programs and resources
13 migrate towards network-based services, the need to be able to authorize
user
is activity associated with such network services will further increase.
is Consequently, there is a need for improved authorization methods and
l6 systems. Preferably the methods and systems will allow users that are
authenticated by a trusted external resource to gain some controlled level of
access
,8 to certain objects without requiring the user to also have a unique user
account
associated with the object. Moreover, the methods and systems should not
2o significantly degrade the scalability of arrangements that are capable of
providing
2~ access to objects for very large numbers of users.
22
z3 SU1-~IMARY
2a Improved methods and systems are provided herein, which allow users that
zs ~~ are authenticated by a trusted external resource to gain controlled
levels of access
Lee & Nas-a. PLLC 03I001I0:8 MSI-86dUSPATAPP
CA 02424782 2003-04-09
1 to selected objects without requiring the user to also have a unique local
user
z account. The methods and systems can be implemented without significantly
3 degrading the scalability of computer system and/or network arrangements
that are
4 conf guyed to provide access to various resources for very large numbers of
users.
s The above stated needs and others may be satisfied, for example, by a
6 method for providing access control to at least one computing resource. The
method includes receiving a unique identifier that is associated with a user
seeking
s access to the computing resource(s). Preferably, the unique identifier has
been
9 generated by another computing resource that is deemed trustworthy andlor
serves
~o and often authenticates the user in some manner. The method includes
translating
~ ~ the received unique identifier into a security identifier (SID) that is
suitable for use
,z with the access control mechanism protecting the computing resource(s). The
~ 3 method further includes determining if the SID matches at least one other
SID that
~a was previously stored by the access control mechanism and is associated
with the
,s computing resource(s). In certain exemplary implementations, the unique
~s identifier includes a pair wise unique identifier (PUID), such as, e.g.,
that used by
1~ Passport services provided by Microsoft Corp., and the access control
mechanism
~s uses an access control List (ACL) to establish users or groups of users
allowed to
19 access the computing resources)
zo In accordance with certain other implementations of the present invention,
a
z~ method is provided for establishing access control permissions to at least
one
zz computing resource. Here, the method includes receiving at least one
electronic
z3 mail (e-mail) address for at least one user that is to be granted at least
limited
z4 access to the computing resource(s). For example, a user that is authorized
by the
zs access control mechanism may input an e-mail address of another user and
specify
Lie & Hay~a. PLLC S 051001!018 MSI-868USPAT.lPP
CA 02424782 2003-04-09
t the computer resources) to be accessed and/or privileges that this other
user will
2 have when accessing the computer resource(s). The method further includes
3 providing the e-mail address to a trustworthy service capable of returning a
unique
a identifier associated with the user based on the e-mail address. The method
s includes receiving the unique identifier and then setting at least one
access control
6 permission based on the unique identifier. This may include, e.g.,
translating the
7 unique identifier into a SID and associating the SID with at least one
access
s control list ACL for the computing resource(s).
In accordance with still other aspects of the present invention, a method for
~o translating a PUID into a corresponding SID is provided. The method
includes
i ~ receiving the PUID, subdividing it into at least one sub authority
identifier portion
n and at least one member identifier portion, and arranging the sub authority
13 identifier portion and the member identifier portion to form the SID.
is A system for controlling access to at least one computing resource is also
~s provided, in accordance with certain implementations of the present
invention.
16 The system includes logic and memory that are configurable to receive a
unique
m identifier associated with a user that is to be provided access to the
computing
18 resource(s), translate the unique identifier into a security identifier
(SID), and
i9 determine if the SID matches at least one other SID that is stored in the
memory
Zo and associated with the computing resource(s).
a~ Certain exemplary systems are provided for setting access control
2z permissions for the computing resource(s). One system includes a
communication
23 network connecting a first device and at least one other device. The first
device is
Za configured to accept an e-mail address for at least one user that is to be
granted at
Zs least limited access to the computing resource(s), provide the e-mail
address to the
Gee Q~ Haya, Pf GC OfJ00: J0=8 MSl-868USPA1',APP
CA 02424782 2003-04-09
other device over the network, receive from the other device over the network
a
z corresponding unique identifier associated with the e-mail address, and set
at least
3 one access control permission associated with the computing resources) based
on
4 the unique identifier. The other device is configured to receive the e-mail
address
s over the network, convert the e-mail address to the unique identifier, and
output
6 the unique identifier to the f rst device over the network.
s BRIEF DESCRIPTION OF THE DRAWINGS
A more complete understanding of the various methods and systems of the
~o present invention may be had by reference to the following detailed
description
~ 1 when taken in conjunction with the accompanying drawings wherein:
1z Fig. 1 is a block diagram generally illustrating an exemplary computer
~3 system suitable for use with certain implementations of the present
invention.
is Fig. 2 is a block diagram depicting a service-for-user-to-proxy (S4U2proxy)
is process that is performed within a client-server environment and suitable
for use
i6 with certain implementations of the present invention.
Fig. 3A is a block diagram depicting a service-for-user-to-self (S4U2self)
~s process that is performed within a client-server environment and suitable
for use
~9 with certain implementations of the present invention.
zo Fig. 3B is a block diagram depicting a service-for-user-to-self (S4U2selfj
z, process that is performed within a client-server environment and suitable
for use
zz with certain implementations of the present invention.
z3 Fig. 4 is an illustrative diagram depicting selected portions of an
exemplary
z4 message format suitable for use with certain implementations of the present
zs invention.
Lee & Hmu, PLLC 03100.10.8 MS!-868USPAT.APP
CA 02424782 2003-04-09
Fig. S is an illustrative block diagram depicting a system and process for
z providing local access control to users authenticated by a trusted resource,
in
3 accordance with certain exemplary implementations of the present invention.
Fig. 6 is an illustrative block diagram depicting an exemplary use of a
s system and process, e.g., as in Fig. 5, for allowing a user without a local
access
6 control account to access certain resources with an adequate level of
authorization
~ ~~ trust, in accordance with certain aspects of the present invention.
8i
9 (( DETAILED DESCRIPTION
~o i
~ 1 Overview
~z Some exemplary methods and systems are described herein that can be
i3 implemented in authenticating users/resources and/or providing an
authorization
~a context for users attempting to gain access to certain resources.
is The next section describes an exemplary computing environment. The
,6 sections after that briefly describe exemplary S4U2proxy and S4U2self
techniques
l, that are the subjects of co-pending U.S. Patent Application No. 09/886,146.
is Thereafter, techniques are described and shown in the accompanying
~9 drawings for providing a novel authorization scheme in accordance with
certain
zo aspects of the present invention. Improved methods and systems are
provided, for
zl example, which allow client services (e.g., users) that are authenticated
by a
zz trusted external service to gain controlled levels of access to selected
local server
z3 resources without requiring the client service to also have a local access
control
za capability. As will become apparent, the authorization schemes described
herein
zs can be employed in a variety of ways to improve the security of computing
Let & flm~a, PLLC 05100:10=8 MSf-868LS.PAT.APP
CA 02424782 2003-04-09
1 ~' resources and the ability of users to gain access to services provided by
the
z ~~ computing resources.
3
4 Exemplary Computing Environment
s Turning to the drawings, wherein like reference numerals refer to like
s elements, the invention is illustrated as being implemented in a suitable
computing
environment. Although not required, the invention will be described in the
general
s context of computer-executable instructions, such as program modules, being
9 executed by a personal computer. Generally, program modules include
routines,
,o programs, objects, components, data structures, etc. that perform
particular tasks
1 ~ or implement particular abstract data types. Moreover, those skilled in
the art will
,z appreciate that the invention may be practiced with other computer system
~3 configurations, including hand-held devices, mufti-processor systems,
is microprocessor based or programmable consumer electronics, network PCs,
is minicomputers, mainframe computers, and the like. The invention may also be
16 practiced in distributed computing environments where tasks are performed
by
o remote processing devices that are linked through a communications network.
In
la a distributed computing environment, program modules may be located in both
19 local and remote memory storage devices.
zo Fig.l illustrates an example of a suitable computing environment 120 on
z, which the subsequently described methods and systems may be implemented.
zz Exemplary computing environment 120 is only one example of a suitable
z3 computing environment and is not intended to suggest any limitation as to
the
za scope of use or functionality of the improved methods and systems described
zs herein. Neither should computing environment 120 be interpreted as having
any
Get & Nayes. PGLC 051001!0=8 MSI-868(lSPATAPP
CA 02424782 2003-04-09
dependency or requirement relating to any one or combination of components
2 illustrated in computing environment 120.
The improved methods and systems herein are operational with numerous
4 other general purpose or special purpose computing system environments or
s configurations. Examples of well known computing systems, environments,
6 and/or configurations that may be suitable include, but are not limited to,
personal
computers, server computers, thin clients, thick clients, hand-held or laptop
s devices, multiprocessor systems, microprocessor-based systems, set top
boxes,
9 programmable consumer electronics, network PCs, minicomputers, mainframe
~o computers, distributed computing environments that include any of the above
1, systems or devices, and the like.
As shown in Fig. 1, computing environment 120 includes a general-purpose
i3 computing device in the form of a computer 130. The components of computer
~a 130 may include one or more processors or processing units 132, a system
is memory 134, and a bus 136 that couples various system components including
~6 system memory 134 to processor 132.
l Bus 136 represents one or more of any of several types of bus structures,
~s including a memory bus or memory controller, a peripheral bus, an
accelerated
i9 graphics port, and a processor or local bus using any of a variety of bus
Zo architectures. By way of example, and not limitation, such architectures
include
z1 Industry Standard Architecture (ISA) bus, Micro Channel Architecture (MCA)
z2 bus, Enhanced ISA (EISA) bus, Video Electronics Standards Association
(VESA)
z3 local bus, and Peripheral Component Interconnects (PCI) bus also known as
Za Mezzanine bus.
2s
Lee & Nayer, PLLC I O 051001/0=8 MSl-868US.PATAPP
CA 02424782 2003-04-09
Computer 130 typically includes a variety of computer readable media.
z Such media may be any available media that is accessible by computer 130,
and it
3 includes both volatile and non-volatile media, removable and non-removable
a media.
s In Fig. 1, system memory 134 includes computer readable media in the
6 form of volatile memory, such as random access memory (RAM) 140, and/or non-
? volatile memory, such as read only memory (ROM) 138. A basic input/output
s system (BIOS) 142, containing the basic routines that help to transfer
information
s between elements within computer 130, such as during start-up, is stored in
ROM
138. RAM 140 typically contains data and/or program modules that are
1 ~ immediately accessible to and/or presently being operated on by processor
132.
12 Computer 130 may further include other removable/non-removable,
i3 volatile/non-volatile computer storage media. For example, Fig. 1
illustrates a
is hard disk drive 144 for reading from and writing to a non-removable, non-
volatile
,s magnetic media (not shown and typically called a "hard drive"), a magnetic
disk
16 drive 146 for reading from and writing to a removable, non-volatile
magnetic disk
148 (e.g., a "floppy disk"), and an optical disk drive 150 for reading from or
is writing to a removable, non-volatile optical disk 152 such as a CD-
ROM/R/RW,
DVD-ROM/R/RW/+R/RAM or other optical media. Hard disk drive 144,
zo magnetic disk drive I46 and optical disk drive 150 are each connected to
bus 136
z i by one or more interfaces 154.
zz The drives and associated computer-readable media provide nonvolatile
z3 storage of computer readable instructions, data structures, program
modules, and
za other data for computer 130. Although the exemplary environment described
zs herein employs a hard disk, a removable magnetic disk 148 and a removable
Lee & Nayu, PLLC Ofl00=J0:8 MSJ-868USPATAPP
CA 02424782 2003-04-09
optical disk 152, it should be appreciated by those skilled in the art that
other types
z of computer readable media which can store data that is accessible by a
computer,
3 such as magnetic cassettes, flash memory cards, digital video disks, random
access
memories (RAMs), read only memories (ROM), and the like, may also be used in
s the exemplary operating environment.
s A number of program modules may be stored on the hard disk, magnetic
disk 148, optical disk 152, ROM 138, or RAM 140, including, e.g., an operating
s system 158, one or more application programs 160, other program modules 162,
and program data 164.
The improved methods and systems described herein may be implemented
within operating system 158, one or more application programs 160, other
~ z program modules 162, and/or program data 164.
i3 A user may provide commands and information into computer 130 through
~a input devices such as keyboard 166 and pointing device 168 (such as a
"mouse").
is Other input devices (not shown) may include a microphone, joystick, game
pad,
i6 satellite dish, serial port, scanner, camera, etc. These and other input
devices are
connected to the processing unit 132 through a user input interface 170 that
is
is coupled to bus 136, but may be connected by other interface and bus
structures,
such as a parallel port, game port, or a universal serial bus (USB).
zo A monitor 172 or other type of display device is also connected to bus 136
z, via an interface, such as a video adapter 174. In addition to monitor 172,
personal
zz computers typically include other peripheral output devices (not shown),
such as
z3 speakers and printers, which may be connected through output peripheral
interface
za 175.
zs
Ler Qc Nm~a, PLLC 03I00:!0:8 MSI-868USPATAPP
CA 02424782 2003-04-09
Computer 130 may operate in a networked environment using logical
z connections to one or more remote computers, such as a remote computer 182.
3 Remote computer 182 may include many or all of the elements and features
a ~ described herein relative to computer 130.
s Logical connections shown in Fig. 1 are a local area network (LAN) 177
6 and a general wide area network (WAN) I79. Such networking environments are
commonplace in offices, enterprise-wide computer networks, intranets, and the
s II Internet.
When used in a LAN networking environment, computer 130 is connected
~o to LAN 177 via network interface or adapter 186. When used in a WAN
1 ~ networking environment, the computer typically includes a modem 178 or
other
,z means for establishing communications over WAN 179. Modem 178, which may
~3 be internal or external, may be connected to system bus 136 via the user
input
,a interface 170 or other appropriate mechanism.
~s Depicted in Fig. 1, is a specific implementation of a WAN via the Internet.
a6 Here, computer 130 employs modem 178 to establish communications with at
" least one remote computer 182 via the Internet 180.
~s In a networked environment, program modules depicted relative to
i9 computer 130, or portions thereof, may be stored in a remote memory storage
zo device. Thus, e.g., as depicted in Fig. 1, remote application programs 189
may
z, reside on a memory device of remote computer 182. It will be appreciated
that the
zz network connections shown and described are exemplary and other means of
z3 establishing a communications link between the computers may be used.
za
Lee & Hayes. PLLC 13 OSIOOJI0:8 MS!-068USPAI:APP
CA 02424782 2003-04-09
Summary of Exemplary S4U2Proxy and S4U2Self Delegation Techniques
z This description will now briefly focus on certain techniques for
controlling
3 the scope of delegation of authentication credentials in a client-server
network
a environment. In this example, a Kerberos based system is described. These
s S4U2Proxy and S4U2Self techniques and the subsequently described
6 authorization techniques may or may not be implemented in the same systems
and
a may also be implemented in other certificate-based authentication systems.
s As mentioned above, having possession of a client's ticket granting ticket
9 (TGT) and associated authenticator allows the holder to request tickets on
behalf
~o of the client from the trusted third-party, e.g., a key distribution center
(KDC).
r ~ Such unconstrained delegation is currently supported in certain
implementations
~ z of Kerberos that have forwarded ticket delegation schemes.
With this in mind, U.S. Patent Application No. 09/886,146 describes
~a methods and systems to constrain or otherwise better control the delegation
is process. The delegation process can be controlled through a service-for-
user-to-
~6 proxy (S4U2proxy) technique that allows a server or service, such as, e.g.,
a front-
1 ~ end server/service, to request service tickets on behalf of a client for
use with other
1g servers/services. The S4U2proxy protocol advantageously provides for
~9 constrained delegation in a controllable manner that does not require the
client to
zo forward a TGT to the front-end server. Another technique is a service-for-
user-to-
z~ self (S4U2self) protocol that allows a server to request a service ticket
to itself, but
z2 with the client°s identity being provided in the resulting service
ticket. This
z3 allows, for example, a client that has been authenticated by other
authentication
za protocols to receive a service ticket that can be used with the S4U2proxy
protocol
is to provide constrained delegation. There are two exemplary forms to the
S4U2self
Lee & Hays, PLLC 05!00110=8 MSl-868US.PATAPP
CA 02424782 2003-04-09
technique, namely a "no evidence" form and an "evidence" form. In the no
z evidence form, the server is trusted to authenticate the client, for
example, using
3 another security/authentication mechanism that is private to the server. In
the
a evidence form, the KDC (or a trusted-third-party) makes the authentication
based
s on information (evidence) provided about the client obtained when the client
6 authenticated to the server.
A client may therefore access servers/services within a Kerberos
s environment regardless as to whether the client has been authenticated by
Kerberos or some other authentication protocol. Consequently, back-end and/or
io other servers/services can be operated in an essentially Kerberos only
~ I environment.
~z Reference is now made to the block diagram in Fig. 2, which depicts an
~3 S4U2proxy protocol/process within a client-server environment 200. As
shown, a
is client 202 is operatively coupled to a trusted third-party 204 having an
is authentication service 206, e.g., a KDC, a certificate granting authority,
a domain
is controller, and/or the like. Authentication service 206 is configured to
access
l~ information maintained in a database 208. Client 202 and trusted third-
party 204
is are further operatively coupled to a server, namely server A 210. Note, as
used
19 herein, the terms server and service are used intermixable to represent the
same or
zo similar functionality.
z~ In this example, server A 210 is a front-end server to a plurality of other
zz servers. Thus, as depicted, server A 210 is operatively coupled to server B
212
z3 and server C 214. As illustrated, server B 212 may be a replicated service.
Also,
za server C 214 is further operatively coupled to a server D 216.
zs
Lei & Hoyu, PLLC 1 S 05100=10:d MSl-868USPATAPP
CA 02424782 2003-04-09
In response to a user logging on at client 202, an authentication request
z (AS REQ) message 220 is sent to authentication service 206, which responds
with
3 an authentication reply (AS REP) message 222. Within AS REP message 222, is
a a TGT associated with the user/client. The same or similar procedure (not
illustrated) is followed to authenticate server A 210.
When client 202 wants to access server A 210, client 202 sends a ticket
granting service request (TGS_REQ) message 224 to authentication service 206,
s which returns a ticket granting service reply (TGS_REP) message 226. TGS REP
9 message 226 includes a service ticket associated with client 202 and server
A 210.
~o Subsequently, to initiate a communication session, client 202 forwards the
service
i i ticket to server A 210, in an application protocol request (AP~REQ)
message 228.
~2 Such processes/procedures are well known, and as such are not disclosed
herein in
~3 greater detail.
,a In certain systems, to support delegation the client would need to provide
,s server A 210 with the client's TGT to allow server A 210 to request
additional
~6 service tickets on behalf of client 202. This is not necessary with the
S4U2proxy
1 ~ protocol. Instead, when server A 210 needs to access another server on
behalf of
,8 client 202, for example, server C 214, then server A 210 and authentication
service
~9 206 operate according to the S4U2proxy protocol.
zo Server A 210 sends a TGS_REQ message 230 to authentication service 206.
zi TGS REQ message 230 includes the TGT for server A 210 and the service
ticket
zz received from client 202, and identifies the desired or targeted
server/service to
z3 which client 202 is seeking access, e.g., server C 214. In Kerberos, for
example,
za there is a defined extensible data field, which is typically referred to as
the
zs "additional tickets" field. This additional tickets field can be used in
the
Lee & Nmea, PLLC 1 OJIOO:I0J8MS1-868G5PATAPP
CA 02424782 2003-04-09
S4U2proxy protocol to carry the service ticket received from client 202, and a
z KDC options field can include a flag or other indicator that instructs the
receiving
3 KDC to look in the additional tickets field for a ticket to be used to
supply a client
a identity. Those skilled in the art will recognize that these or other fields
and/or
s data structures can be used to carry the necessary information to
authentication
6 service 206.
In processing TGS REQ 230, authentication service 206 determines if
s client 202 has authorized delegation, for example, based on the value of a
9 "forwardable flag" established by client 202. Thus, delegation per client is
~o enforced by the presence of the forwardable flag in the client's service
ticket. If
" client 202 does not want to participate in delegation, then the ticket is
not flagged
,z as forwardable. Authentication service 206 will honor this flag as a client
initiated
,3 restriction. Authentication service 206 may access additional information
in
~a database 208 that defines selected services that server A 210 is allowed to
delegate
,s to (or not delegate to) with respect to client 202.
16 If authentication service 206 determines that server A 210 is allowed to
m delegate to the targeted server/service, then a TGS REP message 232 is sent
to
,g server A 210. TGS REP message 232 includes a service ticket for the
targeted
i9 server/service. This service ticket appears as if client 202 requested it
directly
zo from authentication service 206, for example, using the client's TGT.
However,
z~ this was not done. Instead, authentication service 206 accessed the
zz similar/necessary client information in database 208 after being satisfied
that the
z3 authenticated client is essentially involved in the request based on the
service
za ticket that authenticated server A 210 received from client 202 and
included in
Cee & Haya, PLLC 17 05100110=8.HS1-868USPATAPP
CA 02424782 2003-04-09
TGS REQ message 230. However, since the client information is carried in the
z client's ticket, the server only needs to copy the data from the ticket.
In certain implementations TGS REP message 232 identifies the targeted
a server/service and client 202, and further includes implementation-specific
s identity/user/client account data, e.g., in the form of a privilege
attribute certificate
6 (PAC), a security identifier, a Unix ID, Passport ID, a certificate, etc. A
PAC, for
7 example, may be generated by authentication service 206, or simply copied
from
s the client's service ticket that was included in TGS REQ message 230. The
use of
9 a Passport ID will be further described in the exemplary authorization
context
,o generating schemes presented below.
PAC or other user/client account data may also be configured to include
,z information relating to the scope of delegation. Thus, for example, Fig. 4
is an
i3 illustrative diagram depicting selected portions of a Kerberos message 400
having
~a a header 402 and a PAC 404. Here, PAC 404 includes delegation information
406.
,s As illustrated, delegation information 406 includes compound identity
information
,6 408 and access restriction information 410.
m Compound identity information 408 may, for example, include recorded
,8 information about the delegation process, such as, e.g., an indication
regarding the
,9 fact that server A 210 requested the service ticket on behalf of
user/client 202.
zo Here, a plurality of such recorded information may be provided that can be
used to
z, string together or otherwise identify the history over multiple delegation
zz processes. Such information may be useful for auditing purposes andl'or
access
z3 control purposes.
za Access restriction information 410 may be used, for example, in
zs conjunction with an access control mechanism to selectively allow access to
Lee & Hayes, PLLC 1 Of100=1018MS1-868U,~PAP.APP
CA 02424782 2003-04-09
certain servers/services provided that client 202 has either directly or
indirectly
z through server A 210 sought to access the serer/service, but not if the
server/service is being indirectly sought through server B 212. This feature
adds
a additional control over the delegation of authentication credentials.
s In the above examples client 202 was authenticated by authentication
service 206. However, it is recognized that other clients may not be so
authenticated. An example of such a situation is depicted in Fig. 3A. Here, a
client 302 has been authenticated using a different authentication protocol
mechanism 303. For example, authentication protocol mechanism 303 may
,o include Passport, secure sockets layer (SSL), NTLM, Digest, or other like
authenticating protocols/procedures. Here, in this example, it is assumed that
,z client 302 chooses to access a targeted service, which just so happens to
be
,3 provided by server C Z14. This choice can be satisfied using the above-
described
,a S4U2proxy protocol, but only after server A 210 has completed/followed an
,s S4U2self protocol/procedure.
,6 One basic premise with the S4U2self protocol is that the server, e.g.,
server
17 A 210, is able to request a service ticket to itself for any user/client
that is
is accessing the server and which the server has authenticated. The exemplary
,9 S4U2self protocol described herein is configured to support clients that
have
zo authenticating "evidence" and clients that do not have such authenticating
21 evidence.
zz In the absence of authentication evidence that can be evaluated by
zs authentication service 206, server A 210 will need to come to "trust"
client 302.
za Thus, for example, if client 302 has an authentication certificate or like
mechanism
zs
Lee & Hays, PLLC 05100.10.8 MSI-868USPAT.APP
CA 02424782 2003-04-09
304 that server A 210 is able to validate, then the client 302 may be
determined to
z be "trusted". Hence, server A 210 is essentially authenticating client 302.
Next, server A 210 sends a TGS REQ message 306 to authentication
a service 206 requesting a service ticket to itself for client 302. In
response,
s authentication service 206 generates a TGS REP message 308 that includes the
6 requested service ticket. The received service ticket is then used in a
subsequent
7 S4U2proxy protocol/procedure to request a service ticket to server C 214 for
client
s 302. In certain Kerberos implementations, for example, this requires that a
9 forwardable flag in the TGS_REP message 308 be set to allow forwarding of
the
,o service ticket. The trusted third-party may also build a PAC for client
302, which
11 can then be included in the resulting service ticket
,z If evidence of the authentication does exist for a client 302', then server
A
13 210 can include such evidence in a TGS_REQ message 312 as additional pre-
ia authentication data. This is illustratively depicted in environment 300' in
Fig. 3B.
~s Here, evidence information 310 is provided by client 302' to server A 210.
i6 Evidence information 310 may include, for example, a challenge/response
dialog,
1~ or other, information generated by another "trusted" entity. Upon receipt
of
,s evidence information 310 and subsequent validation, authentication service
206
~9 will grant the requested service ticket to server A 210 itself. It is
noted, that in
zo certain implementations, with the use of evidence it may be possible for
the server
z, to obtain a restricted TGT for the client.
zz ~ In certain Kerberos implementations, the forwardable flag in the TGS REP
z3 message 314 will be set to allow forwarding of the service ticket. If a PAC
was
za provided in TGS REQ message 312, then it can be used in the service ticket;
is otherwise, a PAC may be generated by authentication service 206 (here, a
KDC)
Lee & Hayer, PLLC 05100110.8 MS!-B68USPA7.APP
CA 02424782 2003-04-09
1 based on evidence information 310. For example, in S4U2self, the identity of
the
z client is included in the pre-authentication data. This identity can be used
in the
3 construction of the PAC for that client and added to the issued service
ticket to the
a server (for the client).
6 Exemplary Authorization Context Generating Techniques
The description will now focus on exemplary methods and systems in
a accordance with certain implementations of the present invention. These
methods
9 and systems may be implemented with or without the use of the S4U2proxy
and/or
~o S4U2self protocols. These methods and systems may be implemented with or
" without the use of Kerberos. These methods and systems may be implemented
12 with or without the use of Passport services (provided by Microsoft Corp.
of
3 Redmond, WA). Those skilled in the art will recognize that the techniques
may be
la implemented using a variety of other protocols and/or services.
Nevertheless in
I s these examples, it will be assumed that these protocols and services are
available
16 to support the authorization context generating techniques, if needed.
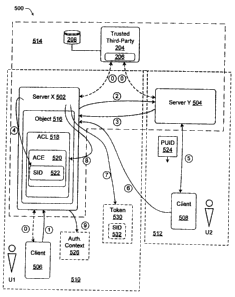
n Reference is now made to Fig. S, which is an illustrative block diagram
s depicting certain features/functions/processes relating to a client-server
network
19 arrangement S00 that is capable of providing an authorization context for
users
zo that would not otherwise have authorization to access certain resources.
2i As shown, a server X SOZ is operatively coupled to a server Y 504, a first
Zz client 506 associated with user #1 (UI), and a second client S08 associated
with
23 user #2 (U2). In this example, there are several trust relationships
between these
Za devices, as represented by dashed line boxes S I0, S I 2 and S 14. Thus,
client S06
Zs and server X S02 are configured to form trust relationship S10 when U1
Iogons to
Lee & Hayu, PLLC OfI00:I0:8 MSI-868USPATAPP
CA 02424782 2003-04-09
client 506 and server X 502, for example, to access a resource provided by
server
z X 502, such as, object 516. This logon procedure may include authentication
and
access control. Similarly, client 504 and server Y 508 are configured to form
trust
a relationship 512 when U2 logons to client 504 and server Y502. Further, in
this
s example, server X 502 and server Y 504 are able to form trust relationship
514 via
trusted third party 204. Notice, however, that at this point there is no trust
relationship between client 508 and server X 502.
s A process will now be described using Fig. 5 and later Fig. 6 to illustrate
s certain aspects of the present invention that allow client 508 to have an
~o authorization context with server X 502 that allows U2 to gain access to
object
11 516. Arrows next to sequential numerical identifiers within a small circle
,z illustratively represent the process acts. Some of the acts may occur in a
different
n order in other implementations.
Act #0 is the creation of trust relationships 510, 512, and 514 as described
,s above. Such trust relationships may be selectively created as needed for
certain
is operations.
» In this example, it is assumed that U1 desires to allow U2 to access object
la 516. While U1 is authorized through trust relationship 510 to access object
516,
,9 U2 is not authorized to access object 516 at this time. Moreover, there is
a further
zo desire to avoid adding U2 as another authorized user to the access control
system
z, of server X 502. This situation can arise, for example, when U1 desires to
allow
zz U2 to access U 1's online planning calendar that is hosted or otherwise
provided
23 through U1's employer. Here, the employer does not want to add a new
za authorized user account to its system.
zs
Gee & Haya, PLGC 2 05100.10:8 MSl-868USPAT.APP
CA 02424782 2003-04-09
Reference is made to Fig. 6, which is a block diagram 600 showing certain
z representative features associated with a graphical user interface (GUI)
provided
3 to U1 through client 506. In this example, a web page 602 or like screen is
a displayed for U1 after logging on to server X 502. Within web page 602
object
s 516 presents a calendar GUI 604 that displays information about U 1. U 1 is
able to
6 open up an entry form 606 that includes an identifier entry field 608 and
(optionally) one or more selectable permission settings 610. This is where U 1
will
s initiate the process that will eventually allow U2 to gain access to object
516.
U1 enters an identifier for U2. In this example, the identifier includes the
~o unique World Wide Web electronic mail address for U2, namely,
~ 1 user2@hotmail.com. The identifier entered here is for a registered user of
the
iz hotmail.com services provided by Microsoft Core. As a registered user of
1~ hotmail.com, U2 is presumed to also have a corresponding Passport account
with
Microsoft Corp. U1 may also define one or more permission settings 610 for U2
i s with regard to the access granted to obj ect 516 (here, e.g., an online
planning
i6 calendar application). Currently, U1 has set permissions for U2 to have
read
n permission. Returning now to Fig. 5, this user identification process is
represented
,8 by act #1 between client 506 and server X 502.
i9 Server X 502 recognizes that U1 has provided a hotmail.com identifier for
zo U2, and in act #2, communicates with server Y 504, which in this case is
presumed
z~ to be a well-known Passport server. Here, server X 502 provides the
identifier
zz user2@hotmail.com to server Y 504 and requests that server Y 504 provide a
z3 corresponding universally unique Passport user identity (PUID) (also often
z4 referred to as a Pair wise Unique ID). In act #3, server Y 504 returns the
PUID
zs
Lee & Hayes, PLLC 23 05100:10=8 ~HSI-868USPAT.APP
CA 02424782 2003-04-09
1 (524) for U2. If trust relationship 514 is a Kerberos based relationship,
then the
z PUID can be returned, for example, in a PAC as previously mentioned.
Server X 502 now has the PUID for U2. In act #4, server X 502 translates
a the PUID into a corresponding SID 522 suitable for use with the native
s authentication system of server X 502. As illustrated, object 516 is
associated
6 with an ACL 518, having at least one ACE 520 that includes SID 522.
The 64-bit PUID is actually composed of a 16-bit Passport domain
a authority identifier and a 48-bit member identifier. To form a SID it is
desirable to
9 maintain the domain authority as a separate value. To do this, the
MemberIDHigh
to is separated into two parts and the parts are formed as separate sub
authorities, for
,1 example, as shown below:
tz S-1-10-21- (HIWORD (Member)DHigh)) - (LOWORD (MemberIDHigh)~-MemberIDLow-0
,3 In this example, "S-1-10-21" is a new identifier authority defined by
ntseapi.h. In
~a this exemplary implementation, ntseapi.h is a header file used to build the
~s Microsoft~ Windows~ operating system that contains the definition for this
SID
,6 value used to construct the PUID-SID. Note that this header would not
usually be
a not directly exposed to developers. However, the declarations in ntseapi.h
are
is published publicly in the Platform SDK in winnt.h.
Thus, an exemplary SID that is created from the PUID or other like
zo identifier returned from a "trusted" source, essentially identifies the
well-known
z~ sub authority and the member user in a unique combination and in a format
zz compatible with the native authorization system.
z3 In act #5, U2 logons (is authenticated) to server Y 504 and in doing so
za receives PUID 524. In act#6, U2 connects to server X 502 using a default
(e.g.,
zs unknown or anonymous) user account and provides information (e.g., in the
PAC)
Lct & Hayes, PLLC 24 031001 /0.8 MS1.868USPAT.APP
CA 02424782 2003-04-09
i including PUID 524 in a request or other like message. In act #7, server X
504
2 recognizes that a PUID has been provided by this default user (U2) and in
3 response builds a corresponding SID 532 that is then placed in a token 530
4 associated with the default user (U2) who is seeking access to object 516.
In
s certain implementations, a SID is built by passing the PUID to an
application
6 programming interface (API) called LsaLogonUser. This API returns the SID.
z In act #8, server X 502 determines if this default user (U2) has appropriate
8 access permissions) to access object 516 by comparing one or more SID(s) in
the
9 default user's token 530 with those in ACL 518. Here, SID 532 from token 530
~o would match SID 522 in ACE 520. Consequently, in act # 9, an authentication
a context 526 is created for U2, which allows U2 to access object 516 in
accordance
1z with the applicable permission settings. Hence, for example, U2 could view
(read)
3 the planning calendar of U 1 and determine if U 1 and U2 might be able to
have
a4 lunch together next week. U2 did not logon to server X 502; indeed U2
cannot
~s logon to server X 502 since U2 does not have an account, as does U1.
i6 Authentication of U2 in this case is essentially based on trust
relationships 510,
i~ S 12 and 514, and the initial authentication of U2 using client 508 and
server Y
is 504. Access control of U2 to server X 502 is granted based essentially on
the
9 trusted authorization of U1 (through client 506 and server X 502 in Act #0)
and
zo trust relationship with server Y 504 in providing PUID 524 in act #3.
2i One of the benefits to using the PUID is that the resulting SID will be
22 globally unique and persistent based on the controlled assignment of PLTIDs
by
z3 Passport.
24
25 Summary
Lee & Haym, PLLC 05100-!0:8 MSl-868LSPAT.APP
CA 02424782 2003-04-09
I Although some preferred implementations of the various methods and
2 systems of the present invention have been illustrated in the accompanying
3 Drawings and described in the foregoing Detailed Description, it will be
4 understood that the invention is not limited to the exemplary embodiments
s disclosed, but is capable of numerous rearrangements, modifications and
6 substitutions without departing from the spirit of the invention as set
forth and
defined by the following claims.
s
9
t0
11
l2
l3
14
16
17
18
19
Z1
22
23
24
Lu & Hayu, PLLC 26 05!001!0:8 MSJ-868US.PAT.APP