Note: Descriptions are shown in the official language in which they were submitted.
CA 02479494 2004-10-04
DEMANDES OU BREVETS VOLUMINEUX
LA PRESENTE PARTIE DE CETTE DErLaNDE OU CE BREVETS
COMPREND PLUS D'UN TO1b1E.
CECI EST LE TOME l DE 4
NOTE: Pour les tomes additionels, veillez contacter le Bureau Canadien des
Brevets.
JUMBO APPLICATIONS / PATENTS
THIS SECTION OF THE APPLICATION / PATENT CONTAINS MORE
THAN ONE VOLUME.
THIS IS VOLUViE t OF ~
NOTE: For additional volumes please contact the Canadian Patent Office.
CA 02479494 2004-10-04
W0 98Ii0M PGT/U897/15W
SYSTEMS AND METSODB FOR SECURE TRANBACTION
h[ANAGEMENT AND ELECTRONIC RIGHTS PROTECTION
Field(e) of the Invention(s)
This invention generally relates to computer and/or
electronic security.
More particularly, this invention relates to systems and
techniques for secure transaction management. This invention
also relates to computer-based and other electronic appliance-
based technologies that help to ensure that information is
accessed and/or otherwise used only in authorized ways, and
maintains the integrity, availability, and/or confidentiality of
such information and processes related to such use.
The invention also relates to systems and methods for
protecting rights of various participants in electronic commerce
and other electronic or electronically-facilitated transactions.
The invention also relates to secure chains of handling and
control for both information content and information employed to
regulate the use of such content and consequences of such use. It
also relates to systems and techniques that manage, including
meter and/or limit and/or otherwise monitor use of electronically
stored and/or disseminated information. The invention
-1-
CA 02479494 2004-10-04
wo 98/09209 PCT/US97ns243
particularly relates to transactions, conduct and arrangements
that make use of, including consequences of use of, such systems
and/or techniques.
The invention also relates to distributed and other
operating systems, environments and architectures. It also
generally relates to secure architectures, including, for example,
tamper-resistant hardware-based processors, that can be used to
establish security at each node of a distributed system.
Background and Summary of the Invention(s)
Telecommunications, financial transactions, government
processes, business operations, entertainment, and personal
business productivity all now depend on electronic appliances.
Millions of these electronic appliances have been electronically
connected together. These interconnected electronic appliances
comprise what is increasingly called the "information highway."
Many businesses, academicians, and government leaders are
concerned about how to protect the rights of citizens and
organizations who use this information (also "electronic" or
"digital") highway.
-2-
CA 02479494 2004-10-04
"7O1"AV7 P(.TIUS97/1SL13
Electronic Content
Today, virtually anything that can be represented by
words, numbers, graphics, or system of commands and
instructions can be formatted into electronic digital information.
Television, cable, satellite transmissions, and on-line services
transmitted over telephone lines, compete to distribute digital
information and entertainment to homes and businesses. The
owners and marketers of this content include software
developers, motion picture and recording companies, publishers
of books, magazines, and newspapers, and information database
providers. The popularization of on-line services has also
enabled the individual personal computer user to participate as a
content provider. It is estimated that the worldwide market for
electronic information in 1992 was approximately $40 billion and
is expected to grow to $200 billion by 1997, according to
Microsoft Corporation. The present invention can materially
enhance the revenue of content providers, lower the distribution
costs and the costs for content, better support advertising and
usage information gathering, and better satisfy the needs of
electronic information users. These improvements can lead to a
significant increase in the amount and variety of electronic
= information and the methods by which such information is
distributed.
-3-
CA 02479494 2004-10-04
WO 9fJ09Z09 PCT/[TS97/1SZ43
The inability of conventional products to be shaped to the
needs of electronic information providers and users is sharply in
contrast to the present invention. Despite the attention devoted
by a cross-section of America's largest telecommunications,
computer, entertainment and information provider companies to
some of the problems addressed by the present invention, only
the present invention provides commercially secure, effective
solutions for configurable, general purpose electronic commerce
transaction/distribution control systems.
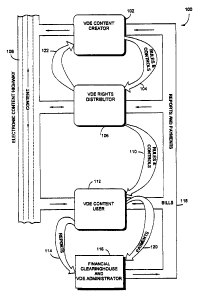
Controlling Electronic Content
The present invention provides a new kind of "virtual
distribution environment" (called "VDE" in this document) that
secures, administers, and audits electronic information use.
VDE also features fundamentally important capabilities for
managing content that travels "across" the "information
highway." These capabilities comprise a rights protection
solution that serves all electronic community members. These
members include content creators and distributors, financial
service providers, end-users, and others. VDE is the first general
purpose, configurable, transaction control/rights protection
solution for users of computers, other electronic appliances,
networks, and the information highway.
-4-
CA 02479494 2004-10-04
wo Mo9zo9 rcr/UsmnsW
A fundamental problem for electronic content providers is
extending their ability to control the use of proprietary
information. Content providers often need to limit use to
authorized activities and amounts. Participants in a business
model involving, for example, provision of movies and
advertising on optical discs may include actors, directors, script
and other writers, musicians, studios, publishers, distributors,
retailers, advertisers, credit card services, and content end-users.
These participants need the ability to embody their range of
agreements and requirements, including use limitations, into an
"extended" agreement comprising an overall electronic business
model. This extended agreement is represented by electronic
content control information that can automatically enforce
agreed upon rights and obligations. Under VDE, such an
extended agreement may comprise an electronic contract
involving all business model participants. Such an agreement
may alternatively, or in addition, be made up of electronic
agreements between subsets of the business model participants.
Through the use of VDE, electronic commerce can function in the
same way as traditional commerce-that is commercial
relationships regarding products and services can be shaped
through the negotiation of one or more agreements between a
variety of parties.
-5-
CA 02479494 2004-10-04
wo 98I09Z09 PGT/0897/15243
Commercial content providers are concerned with ensuring
proper compensation for the use of their electronic information.
Electronic digital information, for example a CD recording, can
today be copied relatively easily and inexpensively. Similarly,
unauthorized copying and use of software programs deprives
rightful owners of billions of dollars in annual revenue according
to the International Intellectual Property Alliance. Content
providers and distributors have devised a number of limited
function rights protection mechanisms to protect their rights.
Authorization passwords and protocols, license servers,
"lock/unlock" distribution methods, and non-electronic
contractual limitations imposed on users of shrink-wrapped
software are a few of the more prevalent content protection
schemes. In a commercial context, these efforts are inefficient
and limited solutions.
Providers of "electronic currency" have also created
protections for their type of content. These systems are not
sufficiently adaptable, efficient, nor flexible enough to support
the generalized use of electronic currency. Furthermore, they do
not provide sophisticated auditing and control configuration
capabilities. This means that current electronic currency tools
lack the sophistication needed for many real-world financial
business models. VDE provides means for anonymous currency
-6-
CA 02479494 2004-10-04
w0 98/09Z09 rcr/US97/iS213
and for "conditionally" anonymous currency, wherein currency
related activities remain anonymous except under special
circumstances.
VDE Control Capabilities
VDE allows the owners and distributors of electronic
digital information to reliably bill for, and securely control, audit,
and budget the use of, electronic information. It can reliably
detect and monitor the use of commercial information products.
VDE uses a wide variety of different electronic information
delivery means: including, for example, digital networks, digital
broadcast, and physical storage media such as optical and
magnetic disks. VDE can be used by major network providers,
hardware manufacturers, owners of electronic information,
providers of such information, and clearinghouses that gather
usage information regarding, and bill for the use of, electronic
information.
VDE provides comprehensive and configurable transaction
management, metering and monitoring technology. It can
change how electronic information products are protected,
marketed, packaged, and distributed. When used, VDE should
result in higher revenues for information providers and greater
-7-
CA 02479494 2004-10-04
WO 9&409209 PCT/US97/15243
user satisfaction and value. Use of VDE will normally result in
lower usage costs, decreased transaction costs, more efficient
access to electronic information, re-usability of rights protection
and other transaction management implementations, greatly
improved flexibility in the use of secured information, and
greater standardization of tools and processes for electronic
transaction management. VDE can be used to create an
adaptable environment that fulfills the needs of electronic
information owners, distributors, and users; financial
clearinghouses; and usage information analyzers and resellers.
Raghts and Control Information
In general, the present invention can be used to protect the
rights of parties who have:
(a) proprietary or confidentiality interests in electronic
information. It can, for example, help ensure that
information is used only in authorized ways;
(b) financial interests resulting from the use of
electronically distributed information. It can help
ensure that content providers will be paid for use of
distributed information; and
-8-
CA 02479494 2004-10-04
wo 98r09209 pCT/Ug97/ISqg
(c) interests in electronic credit and electronic currency
storage, communication, and/or use including
electronic cash, banking, and purchasing.
Protecting the rights of electronic community members
involves a broad range of technologies. VDE combines these
technologies in a way that creates a "distributed" electronic
rights protection "environment." This environment secures and
protects transactions and other processes important for rights
protection. VDE, for example, provides the ability to prevent, or
impede, interference with and/or observation of, important rights
related transactions and processes. VDE, in its preferred
embodiment, uses special purpose tamper resistant Secure
Processing Units (SPUs) to help provide a high level of security
for VDE processes and informatioii storage and communication.
The rights protection problems solved by the present
invention are electronic versions of basic societal issues. These
issues include protecting property rights, protecting privacy
rights, properly compensating people and organizations for their
work and risk, protecting money and credit, and generally
protecting the security of information. VDE employs a system
that uses a common set of processes to manage rights issues in
an efficient, trusted, and cost-effective way.
-9-
CA 02479494 2004-10-04
wo 98/09209 PcrnUS97/15243
VDE can be used to protect the rights of parties who create
electronic content such as, for example: records, games, movies,
newspapers, electronic books and reference materials, personal
electronic mail, and confidential records and communications.
The invention can also be used to protect the rights of parties
who provide electronic products, such as publishers and
distributors; the rights of parties who provide electronic credit
and currency to pay for use of products, for example, credit
clearinghouses and banks; the rights to privacy of parties who
use electronic content (such as consumers, business people,
governments); and the privacy rights of parties described by
electronic information, such as privacy rights related to
information contained in a medical record, tax record, or
personnel record.
In general, the present invention can protect the rights of
parties who have:
(a) commercial interests in electronically distributed
information -- the present invention can help
ensure, for example, that parties, will be paid for use
of distributed information in a manner consistent
with their agreement;
CA 02479494 2004-10-04
Wo 9&109209 PCT/US97/1SW
(b) proprietary and/or confidentiality interests in
electronic information - the present invention can,
for example, help ensure that data is used only in
authorized ways;
(c) interests in electronic credit and electronic currency
storage, communication, and/or use -- this can
include electronic cash, banking, and purchasing;
and
(d) interests in electronic information derived, at least
in part, from use of other electronic information.
VDE Functional Properties
VDE is a cost-effective and efficient rights protection
solution that provides a unified, consistent system for securing
and managing transaction processing. VDE can:
(a) audit and analyze the use of content,
(b) ensure that content is used only in authorized ways,
= and
-11-
CA 02479494 2004-10-04
wo 98/09109 rcr/US97/isza3
(c) allow information regarding content usage to be
used only in ways approved by content users.
In addition, VDE:
(a) is very configurable, modifiable, and re-usable;
(b) supports a wide range of useful capabilities that
may be combined in different ways to accommodate
most potential applications;
(c) operates on a wide variety of electronic appliances
ranging from hand-held inexpensive devices to large
mainframe computers;
(d) is able to ensure the various rights of a number of
different parties, and a number of different rights
protection schemes, simultaneously;
(e) is able to preserve the rights of parties through a
series of transactions that may occur at different
times and different locations;
-12
CA 02479494 2004-10-04
wo 98A9zo9 PcrNS9'1/1s?A.;
(f) is able to flexibly accommodate different ways of
securely delivering information and reporting usage;
and
(g) provides for electronic analogues to "real" money
and credit, including anonymous electronic cash, to
pay for products and services and to support
personal (including home) banking and other
financial activities.
VDE economically and efficiently fulfills the rights
protection needs of electronic community members. Users of
VDE will not require additional rights protection systems for
different information highway products and rights
problems-nor will they be required to install and learn a new
system for each new information highway application.
VDE provides a unified solution that allows all content
creators, providers, and users to employ the same electronic
rights protection solution. Under authorized circumstances, the
participants can freely exchange content and associated content
control sets. This means that a user of VDE may, if allowed, use
the same electronic system to work with different kinds of
content having different sets of content control information. The
13
CA 02479494 2004-10-04
wo 9&4)9m rcr/vs97/Iss43
content and control information supplied by one group can be
used by people who normally use content and control information
supplied by a different group. VDE can allow content to be
exchanged "universally" and users of an implementation of the
present invention can interact electronically without fear of
incompatibilities in content control, violation of rights, or the
need to get, install, or learn a new content control system.
The VDE securely administers transactions that specify
protection of rights. It can protect electronic rights including, for
example:
(a) the property rights of authors of electronic content,
(b) the commercial rights of distributors of content,
(c) the rights of any parties who facilitated the
distribution of content,
(d) the privacy rights of users of content,
(e) the privacy rights of parties portrayed by stored
and/or distributed content, and
-14-
CA 02479494 2004-10-04
wo 98/o9209 rcT/US97/15?A3
(f) any other rights regarding enforcement of electronic
agreements.
VDE can enable a very broad variety of electronically enforced
commercial and societal agreements. These agreements can
include electronically implemented contracts, licenses, laws,
regulations, and tax collection.
Contrast With Traditional Solntions
Traditional content control mechanisms often require
users to purchase more electronic information than the user
needs or desires. For example, infrequent users of shrink-
wrapped software are required to purchase a program at the
same price as frequent users, even though they may receive
much less value from their less frequent use. Traditional
systems do not scale cost according to the extent or character of
usage and traditional systems can not attract potential
customers who find that a fixed price is too high. Systems using
traditional mechanisms are also not normally particularly
secure. For example, shrink-wrapping does not prevent the
constant illegal pirating of software once removed from either its
physical or electronic package.
-15-
CA 02479494 2004-10-04
wo 98/o9so9 rcrIvs97/1s2a3
Traditional electronic information rights protection
systems are often inflexible and inefficient and may cause a
content provider to choose costly distribution channels that
increase a product's price. In general these mechanisms restrict
product pricing, configuration, and marketing flexibility. These
compromises are the result of techniques for controlling
information which cannot accommodate both different content
models and content models which reflect the many, varied
requirements, such as content delivery strategies, of the model
participants. This can limit a provider's ability to deliver
sufficient overall value to justify a given product's cost in the
eyes of many potential users. VDE allows content providers and
distributors to create applications and distribution networks that
reflect content providers' and users' preferred business models.
It offers users a uniquely cost effective and feature rich system
that supports the ways providers want to distribute information
and the ways users want to use such information. VDE
supports content control models that ensure rights and allow
content delivery strategies to be shaped for maximum
commercial results.
Chain of Handling and Control
VDE can protect a collection of rights belonging to various
parties having in rights in, or to, electronic information. This
-16-
CA 02479494 2004-10-04
Wo Mro9209 rc"rnrs97n5213
information may be at one location or dispersed across (and/or
moving between) multiple locations. The information may pass
through a "chain" of distributors and a "chain" of users. Usage
information may also be reported through one or more "chains" of
parties. In general, VDE enables parties that (a) have rights in
electronic information, and/or (b) act as direct or indirect agents
for parties who have rights in electronic information, to ensure
that the moving, accessing, modifying, or otherwise using of
information can be securely controlled by rules regarding how,
when, where, and by whom such activities can be performed.
VDE Applications and Software
VDE is a secure svstem for regulating electronic conduct
and commerce. Regulation is ensured by control information put
in place by one or more parties. These parties may include
content providers, electronic hardware manufacturers, financial
service providers, or electronic "infrastructure" companies such
as cable or telecommunications companies. The control
information implements "Rights Applications." Rights
applications "run on" the "base software" of the preferred
embodiment. This base software serves as a secure, flexible,
general purpose foundation that can accommodate many
different rights applications, that is, many different business
models and their respective participant requirements.
-17-
CA 02479494 2004-10-04
w0 980"M rcrrL"J97/15M
A rights application under VDE is made up of special
purpose pieces, each of which can correspond to one or more
basic electronic processes needed for a rights protection
environment. These processes can be combined together like
building blocks to create electronic agreements that can protect
the rights, and may enforce fiilfiilment of the obligations, of
electronic information users and providers. One or more
providers of electronic information can easily combine selected
building blocks to create a rights application that is unique to a
specific content distribution model. A group of these pieces can
represent the capabilities needed to fulfill the agreement(s)
between users and providers. These pieces accommodate many
requirements of electronic commerce including:
= the distribution of permissions to use electronic
information;
= the persistence of the control information and sets of
control information managing these permissions;
= configurable control set information that can be
selected by users for use with such information;
-18-
CA 02479494 2004-10-04
WO 98AOlr2o9 rcrnJS97nsM
= data security and usage auditing of electronic
information; and
' = a secure system for currency, compensation and
debit management.
For electronic commerce, a rights application, under the
preferred embodiment of the present invention, can provide
electronic enforcement of the business agreements between all
participants. Since different groups of components can be put
together for different applications, the present invention can
provide electronic control information for a wide variety of
different products and markets. This means the present
invention can provide a "unified," efficient, secure, and
cost-effective system for electronic commerce and data security.
This allows VDE to serve as a single standard for electronic
rights protection, data security, and electronic currency and
banking.
In a VDE, the separation between a rights application and
its foundation permits the efficient selection of sets of control
information that are appropriate for each of many different types
of applications and uses. These control sets can reflect both
rights of electronic community members, as well as obligations
19
CA 02479494 2004-10-04
WO 98/09209 PCT/tJS97/15243
(such as providing a history of one's use of a product or paying
taxes on one's electronic purchases). VDE flexibility allows its
users to electronically implement and enforce common social and
commercial ethics and practices. By providing a unified control
system, the present invention supports a vast range of possible
transaction related interests and concerns of individuals,
coaimunities, businesses, and governments. Due to its open
design, VDE allows (normally under securely controlled
circumstances) applications using technology independently
created by users to be "added" to the system and used in
conjunction with the foundation of the invention. In sum, VDE
provides a system that can fairly reflect and enforce agreements
among parties. It is a broad ranging and systematic solution
that answers the pressing need for a secure, cost-effective, and
fair electronic environment.
VDE Implementation
The preferred embodiment of the present invention
includes various tools that enable system designers to directly
insert VDE capabilities into their products. These tools include
an Application Programmer's Interface ("API") and a Rights
Permissioning and Management Language ("RPML"). The
RPML provides comprehensive and detailed control over the use
of the invention's features. VDE also includes certain user
-20-
CA 02479494 2004-10-04
wo 9M9209 Pcr/US97nS?A3
interface subsystems for satisfying the needs of content
providers, distributors, and users.
Information distributed using VDE may take many forms.
It may, for example, be "distributed" for use on an individual's
own computer, that is the present invention can be used to
provide security for locally stored data. Alternatively, VDE may
be used with information that is dispersed by authors and/or
publishers to one or more recipients. This information may take
many forms including: movies, audio recordings, games,
electronic catalog shopping, multimedia, training materials,
E-mail and personal documents, object oriented libraries,
software programming resources, and reference/record keeping
information resources (such as business, medical, legal,
scientific, governmental, and consumer databases).
Electronic rights protection provided by the present
invention will also provide an important foundation for trusted
and efficient home and commercial banking, electronic credit
processes, electronic purchasing, true or conditionally
anonymous electronic cash, and EDI (Electronic Data
Interchange). VDE provides important enhancements for
improving data security in organizations by providing "smart"
-21-
CA 02479494 2004-10-04
WO 9e109Z09 PCT/U897/15243
transaction management features that can be far more effective
than key and password based "go/no go" technology.
VDE normally employs an integration of cryptographic
and other security technologies (e.g. encryption, digital
signatures, etc.), with other technologies including: component,
distributed, and event driven operating system technology, and
related communications, object container, database, smart agent,
smart card, and semiconductor design technologies.
1. Overview
A. VDE Solves Important Problems and Fills
Critical Needs
The world is moving towards an integration of electronic
information appliances. This interconnection of appliances
provides a foundation for much greater electronic interaction and
the evolution of electronic commerce. A variety of capabilities
are required to implement an electronic commerce environment.
VDE is the first system that provides many of these capabilities
and therefore solves fundamental problems related to electronic
dissemination of information.
22
CA 02479494 2004-10-04
wo nlom rcrrtis"nsm
El=atronic Content
VDE allows electronic arrangements to be created
involving two or more parties. These agreements can themselves
comprise a collection of agreements between participants in a
commercial value chain and/or a data security chain model for
handling, auditing, reporting, and payment. It can provide
effident, reusable, modifiable, and consistent means for secure
electronic content: distribution, usage control, usage payment,
usage auditing, and usage reporting. Content may, for example,
include:
= financial information such as electronic currency
and credit;
= commercially distributed electronic information such
as reference databases, movies, games, and
advertising; and
= electronic properties produced by persons and
organizations, such as documents, e-mail, and
proprietary database information.
-23-
CA 02479494 2004-10-04
Wo M09209 Pt,'T/U899/15m
VDE enables an electronic commerce marketplace that supports
differing, competitive business partnerships, agreements, and
evolving overall business models.
The features of VDE allow it to function as the first
trusted electronic information control environment that can
conform to, and support, the bulk of conventional electronic
commerce and data security requirements. In particular, VDE
enables the participants in a business value chain model to
create an electronic version of traditional business agreement
terms and conditions and further enables these participants to
shape and evolve their electronic commerce models as they
believe appropriate to their business requirements.
VDE offers an architecture that avoids reflecting specific
distribution biases, administrative and control perspectives, and
content types. Instead, VDE provides a broad-spectrum,
fundamentally configurable and portable, electronic transaction
control, distributing, usage, auditing, reporting, and payment
operating environment. VDE is not limited to being an
application or application specific toolset that covers only a
limited subset of electronic interaction activities and
participants. Rather, VDE supports systems by which such
applications can be created, modified, and/or reused. As a result,
-24-
CA 02479494 2004-10-04
Wo 9&09Z09 PCT/[r8{97/15243
the present invention answers pressing, unsolved needs by
offering a system that supports a standardized control
environment which facilitates interoperability of electronic
appliances, interoperability of content containers, and efficient
creation of electronic commerce applications and models through
the use of a programmable, secure electronic transactions
management foundation and reusable and extensible executable
components. VDE can support a single electronic "world" within
which most forms of electronic transaction activities can be
managed.
To answer the developing needs of rights owners and
content providers and to provide a system that can accommodate
the requirements and agreements of all parties that may be
involved in electronic business models (creators, distributors,
administrators, users, credit providers, etc. ), VDE supplies an
efficient, largely transparent, low cost and sufficiently secure
system (supporting both hardware/ software and software only
models). VDE provides the widely varying secure control and
administration capabilities required for:
1. Different types of electronic content,
2. Differing electronic content delivery schemes,
-25-
CA 02479494 2004-10-04
WO M9?09 PCT/US99/1S2A3
3. Differing electronic content usage schemes,
4. Different content usage platforms, and
5. Differing content marketing and model strategies.
VDE may be combined with, or integrated into, many
separate computers and/or other electronic appliances. These
appliances typically include a secure subsystem that can enable
control of content use such as displaying, encrypting, decrypting,
printing, copying, saving, extracting, embedding, distributing,
auditing usage, etc. The secure subsystem in the preferred
embodiment comprises one or more "protected processing
environments", one or more secure databases, and secure
"component assemblies" and other items and processes that need
to be kept secured. VDE can, for example, securely control
electronic currency, payments, and/or credit management
(including electronic credit and/or currency receipt,
disbursement, encumbering, and/or allocation) using such a
"secure subsystem." ,
VDE provides a secure, distributed electronic transaction
management system for controlling the distribution and/or other
usage of electronically provided and/or stored information. VDE
-26-
CA 02479494 2004-10-04
WO 9eA)9209 PCT/[JS97/iS2/3
controls auditing and reporting of electronic content and/or
appliance usage. Users of VDE may include content creators
who apply content usage, usage reporting, and/or usage payment
related control information to electronic content andlor
appliances for users such as end-user organizations, individuals,
and content and/or appliance distributors. VDE also securely
supports the payment of money owed (including money owed for
content and/or appliance usage) by one or more parties to one or
more other parties, in the form of electronic credit and/or
currency.
Electronic appliances under control of VDE represent VDE
'nodes' that securelv process and control; distributed electronic
information andlor appliance usage, control information
formulation, and related transactions. VDE can securely
manage the integration of control information provided by two or
more parties. As a result, VDE can construct an electronic
agreement between VDE participants that represent a
"negotiation" between, the control requirements of, two or more
parties and enacts terms and conditions of a resulting
agreement. VDE ensures the rights of each party to an
electronic agreement regarding a wide range of electronic
activities related to electronic information andJor appliance
usage.
-27-
CA 02479494 2004-10-04
wo M9z+u9 rcrRrs77n5243
Through use of VDE's control system, traditional content
providers and users can create electronic relationships that
reflect traditional, non-electronic relationships. They can shape
and modify commercial relationships to accommodate the
evolving needs of, and agreements among, themselves. VDE
does not require electronic content providers and users to modify
their business practices and personal preferences to conform to a
metering and control application program that supports li.mited,
largely fixed functionality. Furthermore, VDE permits
participants to develop business models not feasible with non-
electronic commerce, for example, involving detailed reporting of
content usage information, large numbers of distinct
transactions at hitherto infeasibly low price pomts, "pass-along"
control information that is enforced without involvement or
advance knowledge of the participants, etc.
The present invention allows content providers and users
to formulate their transaction environment to accommodate:
(1) desired content models, content control models, and
content usage information pathways,
(2) a complete range of electronic media and
distribution means,
-28-
CA 02479494 2004-10-04
wo 9t/09209 rcr/trs97/25M
(3) a broad range of pricing, payment, and auditing
strategies,
(4) very flegible privacy and/or reporting models,
(5) practical and effective security architectures, and
(6) other administrative procedures that together with
steps (1) through (5) can enable most "real world"
electronic commerce and data security models,
including models unique to the electronic world.
VDE's transaction management capabilities can enforce:
(1) privacy rights of users related to information
regarding their usage of electronic information
and/or appliances,
(2) societal policy such as laws that protect rights of
content users or require the collection of taxes
derived from electronic transaction revenue, and
-29-
CA 02479494 2004-10-04
wo 981Mo4 rCrr0397n3sa3
(3) the proprietary and/or other rights of parties related
to ownership of, distribution of, and/or other
commercial rights related to, electronic information.
VDE can support "real" commerce in an electronic form,
that is the progressive creation of commercial relationships that
form, over time, a network of interrelated agreements
representing a value chain business model. This is achieved in
part by enabling content control information to develop through
the interaction of (negotiation between) securely created and
independently submitted sets of content and/or appliance control
information. Different sets of content andi'or appliance control
information can be submitted by different parties in an electronic
business value chain enabled by the present invention. These
parties create control information sets through the use of their
respective VDE installations. Independently, securely
deliverable, component based control information allows efficient
interaction among control information sets supplied by different
parties.
VDE permits multiple, separate electronic arrangements
to be formed between subsets of parties in a VDE supported
electronic value chain model. These multiple'agreements
together comprise a VDE value chain "extended" agreement.
-30-
CA 02479494 2004-10-04
WO 98/09209 rcT/U897/15SA3
VDE allows such constituent electronic agreements, and
therefore overall VDE extended agreements, to evolve and
reshape over time as additional VDE participants become
involved in VDE content and/or appliance control information
handling. VDE electronic agreements may also be extended as
new control information is submitted by existing participants.
With VDE, electronic commerce participants are free to structure
and restructure their electronic commerce business activities and
relationships. As a result, the present invention allows a
competitive electronic commerce marketplace to develop since
the use of VDE enables different, widely varying business models
using the same or shared content.
A significant facet of the present invention's ability to
broadly support electronic commerce is its ability to securely
manage independently delivered VDE component objects
containing control information (normallv in the form of VDE
objects containing one or more methods, data, or load module
VDE components). This independently delivered control
information can be integrated with senior and other pre-existing
content control information to securely form derived control
information using the negotiation mechanisms of the present
invention. All requirements specified by this derived control
information must be satisfied before VDE controIled content can
31
CA 02479494 2004-10-04
wo 9dUO2o9 rcrIos97nSW
be accessed or otherwise used. This means that, for example, all
load modules and any mediating data which are lfsted by the
derived control information as required must be available and
securely perform their required function. In combination with
other aspects of the present invention, securely, independently
delivered control components allow electronic commerce
participants to freely stipulate their business requirements and
trade offs. As a result, much as with traditional, non-electronic
commerce, the present invention allows electronic commerce
(through a progressive stipulation of various control
requirements by VDE participants) to evolve into forms of
business that are the most efficient, competitive and useful.
VDE provides capabilities that rationalize the support of
electronic commerce and electronic transaction management.
This rationalization stems from the reusability of control
structures and user interfaces for a wide variety cf transaction
management related activities. As a result, content usage
control, data security, information auditing, and electronic
financial activities, can be supported with tools that are
reusable, convenient, consistent, and familiar. In addition, a
rational approach-a transaction/distribution control
standard-allows all participants in VDE the same foundation
set of hardware control and security, authoring, administration,
-32-
-- - ------- ------ -
CA 02479494 2004-10-04
wo 994om rcrnrJS97nsM
and management tools to support widely varying types of
information, business market model, and/or personal objectives.
Employing VDE as a general purpose electronic
transaction/distribution control system allows users to maintain
a single transaction management control arrangement on each of
their computers, networks, communication nodes, and/or other
electronic appliances. Such a general purpose system can serve
the needs of many electronic transaction management
applications without requiring distinct, different installations for
different purposes. As a result, users of VDE can avoid the
confusion -and expense and other inefficiencies of different,
limited purpose transaction control applications for each
different content and/or business model. For example, VDE
allows content creators to use the same VDE foundation control
arrangement for both content authoring and for licensing content
from other content creators for inclusion into their products or
for other use. Clearinghouses, distributors, content creators, and
other VDE users can all interact, both with the applications
running on their VDE instaliations, and with each other, in an
entirely consistent manner, using and reusing (largely
transparently) the same distributed tools, mechanisms, and
consistent user interfaces, regardless of the type of VDE activity.
-33-
CA 02479494 2004-10-04
wo MIM pcrrnS971LsM
VDE prevents many forms of unauthorized use of
electronic information, by controlling and auditing (and other
administration of use) electronically stored and/or disseminated
information. This includes, for example, commercially
distributed content, electronic currency, electronic credit,
business transactions (such as EDI), confidential
communications, and the like. VDE can further be used to
enable commercially provided electronic content to be made
available to users in user defined portions, rather than
constraining the user to use portions of content that were
"predetermined" by a content creator and/or other provider for
billing purposes.
VDE, for example, can employ:
(1) Secure metering means for budgeting and/or
auditing electronic content and/or appliance usage;
(2) Secure flexible means for enabling compensation
and/or billing rates for content and/or appliance
usage, including electronic credit and/or currency
mechanisms for payment means;
-34-
CA 02479494 2004-10-04
w0 999ow PCTIUS97ILCO
(3) Secure distributed database means for storing
control and usage related information (and
employing validated compartmentalization and
tagging schemes);
(4) Secure electronic appliance control means;
(5) A distributed, secure, "virtual black box" comprised
of nodes located at every user (including VDE
content container creators, other content providers,
client users, and recipients of secure VDE content
usage information) site. The nodes of said virtual
black box normally include a secure subsystem
having at least one secure hardware element (a
semiconductor element or other hardware module
for securely executing VDE control processes), said
secure subsystems being distributed at nodes along
a pathway of information storage, distribution,
payment, usage, and/or auditing. In some
embodiments, the functions of said hardware
element, for certain or all nodes, may be performed
by software, for example, in host processing
environments of electronic appliances;
-35-
CA 02479494 2004-10-04
WO niom rCT/U897/1S?A3
(6) Encryption and decryption means;
(7) Secure communications means employing
authentication, digital signaturing, ar.d encrypted
transmissions. The secure subsystems at said user
nodes utilize a protocol that establishes and
authenticates each node's and/or participant's
identity, and establishes one or more secure
host-to-host encryption keys for communications
between the secure subsystems; and
(8) Secure control means that can allow each VDE
installation to perform VDE content authoring
(placing content into VDE containers with
associated control information), content distribution,
and content usage; as well as clearinghouse and
other admiwistrative and analysis activities
employing content usage information.
VDE may be used to migrate most non-electronic,
traditional information delivery models (including
entertainment, reference materials, catalog shopping, etc.) into
an adequately secure digital distribution and usage management
-36.
CA 02479494 2004-10-04
WO 98109209 rcTrvs97/15243
and payment context. The distribution sad financial pathways
maaaged by a VDE arrangement may include:
= content creator(s),
= distributor(s),
= redi,stributor(s),
= client administrator(s),
= client user(s),
= financial and/or other clearinghouse(s),
= and/or government agencies.
These distribution and financial pathways may also include:
= advertisers,
= market survey organizations, and/or
= other parties interested in the user usage of
information securely delivered and/or stored using
VDE.
Normally, participants in a VDE arrangement will employ the
same secure VDE foundation. Alternate embodiments support
VDE arrangements employing differing VDE foundations. Such
alternate embodiments may employ procedures to ensure certain
interoperability requirements are met.
-37-
CA 02479494 2004-10-04
wo MMM PCTNS97/15W
Secure VDE hardware (also known as SPUs for Secure
Processing Units), or VDE installations that use software to
substitute for, or complement, said hardware (provided by Host
Processing Environments (HPEs)), operate in conjunction with
secure communications, systems integration software, and
distributed software control information and support structures,
to achieve the electronic contract/rights protection environment
of the present invention. Together, these VDE components
comprise a secure, virtual, distributed content and/or appliance
control, auditing (and other administration), reporting, and
payment environment. In some embodiments and where
commercially acceptable. certain VDE participants, such as
clearinghouses that normally maintain sufficiently physically
secure non-VDE processing environments, may be allowed to
employ HPEs rather VDE hardware elements and interoperate,
for example, with VDE end-users and content providers. VDE
components together comprise a configurable, consistent, secure
and "trusted" architecture for distributed, asynchronous control
of electronic content and/or appliance usage. VDE supports a
"universe wide" environment for electronic content delivery,
broad dissemination, usage reporting, and usage related
payment activities.
-38-
CA 02479494 2004-10-04
WO 98I09?A9 PCT/US97/15243
VDE provides generalized configurability. This results, in
part, from decomposition of generalized requirements for
supporting electronic commerce and data security into a broad
range of constituent "atomic" and higher level components (such
as load modules, data elements, and methods) that may be
variously aggregated together to form control methods for
electronic commerce applications, commercial electronic
agreements, and data security arrangements. VDE provides a
secure operating environment employing VDE foundation
elements along with secure independently deliverable VDE
components that enable electronic commerce models and
relationships to develop. VDE specifically supports the unfolding
of distribution models in which content providers, over time, can
expressly agree to, or allow, subsequent content providers and/or
users to participate in shaping the control information for, and
consequences of, use of electronic content and/or appliances. A
very broad range of the functional attributes important for
supporting simple to very complex electronic commerce and data
security activities are supported by capabilities of the present
invention. As a result, VDE supports most types of electronic
information and/or appliance: usage control (including
distribution), security, usage auditing, reporting, other
= administration, and payment arrangements.
-39-
CA 02479494 2004-10-04
wo 9fmm ''CT~/ISW
VDE, in its preferred embodiment, employs object software
technology and uses object technology to form "containers" for
delivery of information that is (at least in part) encrypted or
otherwise secured. These containers may contain electronic
content products or other electronic information and some or all
of their associated permissicns (control) information. Theae
container objects may be distributed alflng pathways involving
content providers and/or content users. They may be securely
moved among nodes of a Virtual Distribution Environment
(VDE) arrangement, which nodes operate VDE foundation
software and execute control methods to enact electronic
information usage control and/or administration models. The
containers delivered through use of the preferred embodiment of
the present invention may be employed both for distributing
VDE control instractions (information) and/or to encapsulate and
electronicaIly distribute content that has been at least partiaily
secured.
Content providers who employ the present invention may
include, for example, software application and game publishers,
database publishers, cable, television, and radio broadcasters,
electronic shopping vendors, and distributors of information in
electronic document, book, periodical, e-mail and/or other forms.
Corporations, government agencies, and/or individual
-40.
CA 02479494 2004-10-04
wo 9i/09Z09 PCT/US99n5?A3
"end-users" who act as storers of, and/or distributors of,
electronic information, may also be VDE content providers (in a
restricted model, a user provides content only to himself and
employs VDE to secure his own confidential information against
unauthorized use by other parties). Electronic information may
include proprietary and/or confidential information for personal
or internal organization use, as well as information, such as
software applications, documents, entertainment materials,
and/or reference information, which may be provided to other
parties. Distribution may be by, for example, physical media
delivery, broadcast and/or telecommunication means, and in the
form of "static" files and/or streams of data. VDE may also be
used, for example. for multi-site "real-time" interaction such as
teleconferencing, interactive games, or on-line bulletin boards,
where restrictions on, and/or auditing of, the use of all or
portions of communicated information is enforced.
VDE provides important mechanisms for both enforcing
commercial agreements and enabling the protection of privacy
rights. VDE can securely deliver information from one party to
another concerning the use of commercially distributed electronic
content. Even if parties are separated by several "steps" in a
chain (pathway) of handling for such content usage information,
such information is protected by VDE through encryption and/or
-41-
CA 02479494 2004-10-04
WO 98409209 PCT1US97/15243
other secure processing. Because of that protection, the accuracy
of such information is guaranteed by VDE, and the information
can be trusted by all parties to whom it is delivered.
Furthermore, VDE guarantees that all parties can trust that
such information cannot be received by anyone other than the
intended, authorized, party(ies) because it is encrypted such that
only an authorized party, or her agents, can decrypt it. Such
information may also be derived through a secure VDE process
at a previous pathway-of-handling location to produce secure
VDE reporting information that is then communicated securely
to its intended recipient's VDE secure subsystem. Because VDE
can deliver such information securely, parties to an electronic
agreement need not trust the accuracy of commercial usage
and/or other information delivered through means other than
those under control of VDE.
VDE participants in a commercial value chain can be
"commercially" confident (that is, sufficiently confident for
commercial purposes) that the direct (constituent) and/or
"extended" electronic agreements they entered into through the
use of VDE can be enforced reliably. These agreements may
have both "dynamic" transaction management related aspects,
such as content usage control information enforced through
budgeting, metering, and/or reporting of electronic information
-42-
CA 02479494 2004-10-04
wo W09209 rcr/US97/1S243
and/or appliance use, and/or they may include "static" electronic
assertions, such as an end-user using the system to assert his or
her agreement to pay for services, not to pass to unauthorized
parties electronic information derived from usage of content or
systems, and/or agreeing to observe copyright laws. Not only can
electronically reported transaction related information be trusted
under the present invention, but payment may be automated by
the passing of payment tokens through a pathway of payment
(which may or may not be the same as a pathway for reporting).
Such payment can be contained within a VDE container created
automatically by aVllE installation in response to control
information (located, in the preferred embodiment, in one or
more permissions records) stipulating the "withdrawal" of credit
or electronic currency (such as tokens) from an electronic account
(for example, an account securely maintained by a user's VDE
installation secure subsystem) based upon usage of VDE
controlled electronic content and/or appliances (such as
governments, financial credit providers, and users).
VDE allows the needs of electronic commerce participants
to be served and it can bind such participants together in a
universe wide, trusted commercial network that can be secure
enough to support very large amounts of commerce. VDE's
security and metering secure subsystem core will be present at
-43-
CA 02479494 2004-10-04
wo 98Ii09109 PCT/US97nSW
all physical locations where VDE related content is (a) assigned
usage related control information (rules and mediating data),
and/or (b) used. This core can perform security and auditiag
functions (including metering) that operate within a"virtual
black box," a collection of distributed, very secure VDE related
hardware instances that are interconnected by secured
information exchange (for example, telecommunication)
processes and distributed database means. VDE further
includes highly configurable transaction operating system
technology, one or more associated libraries of load modules
along with affiliated data, VDE related administration, data
preparation, and analysis applications, as well as system
software designed to enable VDE integration into host
environments and applications. VDE's usage control
information, for example, provide for property content and/or
appliance related: usage authorization, usage auditing (which
may include audit reduction), usage billing, usage payment,
privacy filtering, reporting, and security related communication
and encryption techniques.
VDE extensively employs methods in the form of software
objects to augment configurability, portability, and security of
the VDE environment. It also employs a software object
architecture for VDE content containers that carries protected
-44-
CA 02479494 2004-10-04
WO 98109209 PCT/US97/15243
content and may also carry both freely available information (e.g,
snmmary, table of contents) and secured content control
information which ensures the performance of control
information. Content control information governs content usage
according to criteria set by holders of rights to an object's
contents and/or according to parties who otherwise have rights
associated with distributing such content (such as governments,
financial credit providers, and users).
In part, security is enhanced by object methods employed
by the present invention because the encryption schemes used to
protect an object can efficiently be further used to protect the
associated content control information (software control
information and relevant data) from modification. Said object
techniques also enhance portability between various computer
and/or other appliance environments because electronic
information in the form of content can be inserted along with (for
example, in the same object container as) content control
information (for said content) to produce a "published" object.
As a result, various portions of said control information may be
specifically adapted for different environments, such as for
diverse computer platforms and operating systems, and said
various porticns may all be carried by a VDE container.
-45-
CA 02479494 2004-10-04
w0 9e/09?,09 PCT/US97/15Z43
An objective of VDE is supporting a
transaction/distribution control standard. Development of such a
standard has many obstacles, given the security requirements
and related hardware and communications issues, widely
differing environments, information types, types of information
usage, business and/or data security goals, varieties of
participants, and properties of delivered information. A
significant feature of VDE accommodates the many, var-ying
distribution and other transaction variables by, in part,
decomposing electronic commerce and data security functions
into generalized capability modules executable within a secure
hardware SPU and/or corresponding software subsystem and
further allowing extensive flexibility in assembling, modifving,
and/or replacing, such modules (e.g. load modules and/or
methods) in applications run on a VDE installation foundation.
This configurability and reconfigurability allows electronic
commerce and data security participants to reflect their
priorities and requirements through a process of iteratively
shaping an evolving extended electronic agreement (electronic
control model). This shaping can occur as content control
information passes from one VDE participant to another and to
the extent allowed by "in place" content control information.
This process allows users of VDE to recast existing control
-46-
CA 02479494 2004-10-04
wo 98p9209 rcrMs97/15243
information and/or add new control information as necessary
(including the elimination of no longer required elements).
VDE supports trusted (sufficiently secure) electronic
information distribution and usage control models for both
commercial electronic content distribution and data security
applications. It can be configured to meet the diverse
requirements of a network of interrelated participants that may
include content creators, content distributors, client
administrators, end users, and/or clearinghouses and/or other
content usage information users. These parties may constitute a
network of participants involved in simple to complex electronic
content dissemination, usage control, usage reporting, and/or
usage payment. Disseminated content may include both
originally provided and VDE generated information (such as
content usage information) and content control information may
persist through both chains (one or more pathways) of content
and content control information handling, as well as the direct
usage of content. The configurability provided by the present
invention is particularly critical for supporting electronic
commerce, that is enabling businesses to create relationships
and evolve strategies that offer competitive value. Electronic
commerce tools that are not inherently configurable and
interoperable will ultimately fail to produce products (and
-47-
CA 02479494 2004-10-04
WO 9M209 PCT/US97/15243
services) that meet both basic requirements and evolving needs
of most commerce applications.
VDE's fundamental configurability will allow a broad
range of competitive electronic commerce business models to
flourish. It allows business models to be shaped to maximize
revenues sources, end-user product value, and operating
efficiencies. VDE can be employed to support multiple, differing
models, take advantage of new revenue opportunities, and
deliver product configurations most desired by users. Electronic
commerce technologies that do not, as the present invention
does:
= support a broad range of possible, complementary
revenue activities,
= offer a flexible array of content usage features most
desired by customers, and
= exploit opportunities for operating efficiencies,
will result in products that are often intrinsically more costly
and less appealing and therefore less competitive in the
marketplace.
Some of the key factors contributing to the configurability
intrinsic to the present invention include:
-48-
CA 02479494 2004-10-04
W0 98A9109 PCT/U897/15243
(a) integration into the fundamental control
environment of a broad range of electronic
appliances through portable API and programming
language tools that efficiently support merging of
control and auditing capabilities in nearly any
electronic appliance environment while maintaining
overall system security;
(b) modular data structures;
(c) generic content model;
(d) general modularity and independence of foundation
architectural components;
(e) modular security structures;
(f) variable length and multiple branching chains of
control; and
(g) independent, modular control structures in the form
of executable load modules that can be maintained
in one or more libraries, and assembled into control
methods and models, and where such model control
- 49
CA 02479494 2004-10-04
wo 9W9Z09 rcr/US'97/1s2a3
schemes can "evolve" as control information passes
through the VDE installations of participants of a
pathway of VDE content control information
handling.
Because of the breadth of issues resolved by the present
invention, it can provide the emerging "electronic highway" with
a single transaction/distribution control system that can, for a
very broad range of commercial and data security models, ensure
against unauthorized use of confidential and/or proprietary
information and commercial electronic transactions. VDE's
electronic transaction management mechanisms can enforce the
electronic rights and agreements of all parties participating in
widely varying business and data security models, and this can
be efficiently achieved through a single VDE implementation
within each VDE participant's electronic appliance. VDE
supports widely varying business and/or data security models
that can involve a broad range of participants at various "levels"
of VDE content and/or content control information pathways of
handling. Different content control and/or auditing models and
agreements may be available on the same VDE installation.
These models and agreements may control content in
relationship to, for example, VDE installations and/or users in
general; certain specific users, installations, classes and/or other
-50.
CA 02479494 2004-10-04
wo 9&409209 rcrn3W711SZ13
groupings of installations and/or users; as well as to electronic
content generally on a given installation, to specific properties,
property portions, classes and/or other groupings of content.
Distribution using VDE may package both the electronic
content and control information into the same VDE container,
and/or may involve the delivery to an end-user site of different
pieces of the same VDE managed property from plural separate
remote locations and/or in plural separate VDE content
containers andlor employing plural different delivery means.
Content control information may be partially or fully delivered
separately from its associated content to a user VDE instaUation
in one or more VDE administrative objects. Portions of said
control information may be delivered from one or more sources.
Control information may also be available for use by access from
a user's VDE installation secure sub-system to one or more
remote VDE secure sub-systems and/or VDE compatible,
certified secure remote locations. VDE control processes such as
metering, budgeting, decrypting and/or fingerprinting, may as
relates to a certain user content usage activity, be performed in a
user's local VDE installation secure subsystem, or said processes
may be divided amongst plural secure subsystems which may be
located in the same user VDE installations and/or in a network
server and in the user installation. For example, a local VDE
51.
CA 02479494 2004-10-04
wo 9dJ09209 PCT/US97n5243
instaIlation may perform decryption and save any, or all of,
usage metering information related to content and/or electronic
appliance usage at such user installation could be performed at
the server employing secure (e.g., encrypted) communications
between said secure subsystems. Said server location may also
be used for near real time, frequent, or more periodic secure
receipt of content usage information from said user installation,
with, for example, metered information being maintained only
temporarily at a local user installation.
Delivery means for VDE managed content may include
electronic data storage means such as optical disks for delivering
one portion of said information and broadcasting and/or
telecommunicating means for other portions of said information.
Electronic data storage means may indude magnetic media,
optical media, combined magneto-optical systems, flash RAM
memory, bubble memory, and/or other memory storage means
such as huge capacity optical storage systems employing
holographic, frequency, and/or polarity data storage techniques.
Data storage means may also employ layered disc techniques,
such as the use of generally transparent andlor translucent
materials that pass light through layers of data carrying discs
which themselves are physically packaged together as one
- 52 -
CA 02479494 2004-10-04
wo 9sro9i09 PCr/US97nS243
thicker disc. Data carrying locations on such discs mav be, at
least in part, opaque.
VDE supports a general purpose foundation for secure
transaction management, including usage control, auditing,
reporting, and/or payment. This general purpose foundation is
called "VDE Functions" ("VDEFs"). VDE also supports a
collection of "atomic" application elements (e.g., load modules)
that can be selectively aggregated together to form various
VDEF capabilities called control methods and which serve as
VDEF applications and operating system functions. When a host
operating environment of an electronic appliance includes VDEF
capabilities, it is called a "Rights Operating System" (ROS).
VDEF load modules, associated data, and methods form a body of
.15 information that for the purposes of the present invention are
called "control information." VDEF control information may be
specifically associated with one. or more pieces of electronic
content and/or it may be employed as a general component of the
operating system capabilities of a VDE installation.
VDEF transaction control elements reflect and enact
content specific and/or more generalized administrative (for
example, general operating system) control information. VDEF
capabilities which can generaUy take the form of applications
-53-
CA 02479494 2004-10-04
WO 98/09209 rcTiusrmnas
(application models) that have more or less configurability which
can be shaped by VDE participants, through the use, for
example, of VDE templates, to employ specific capabilities, along,
for example, with capability parameter data to reflect the
elements of one or more express electronic agreements between
VDE participants in regards to the use of electronic content such
as commercially distributed products. These control capabilities
manage the use of, and/or auditing of use of, electronic content,
as well as reporting information based upon content use, and any
payment for said use. VDEF capabilities may "evolve" to reflect
the requirements of one or more successive parties who receive
or otherwise contribute to a given set of control information.
Frequently, for a VDE application for a given content model
(such as distribution of entertainment on CD-ROM, content
delivery from an Internet repository, or electronic catalog
shopping and advertising, or some combination of the above)
participants would be able to securely select from amongst
available, alternative control methods and apply related
parameter data, wherein such selection of control method and/or
submission of data would constitute their "contribution" of
control information. Altematively, or in addition, certain control
methods that have been expressly certified as securely
interoperable and compatible with said application may be
independently submitted by a participant as part of such a
- 54
CA 02479494 2004-10-04
WO 98A9209 PCT/pS97/1S243
contribution. In the most general exa.mple, a generally certified
load module (certified for a given VDE arrangement and/or
content class) may be used with many or any VDE application
that operates in nodes of said arrangement. These parties, to the
extent they are allowed, can independently and securely add,
delete, and/or otherwise modify the specification of load modules
and methods, as well as add, delete or otherwise modify related
information.
Normally the party who creates a VDE content container
defines the general nature of the VDEF capabilities that will
and/or may apply to certain electronic information. A VDE
content container is an object that contains both content ( for
example, commercially distributed electronic information
products such as computer software programs, movies, electronic
publications or reference materials, etc.) and certain control
information related to the use of the object's content. A creating
party may make a VDE container available to other parties.
Control information delivered by, and/or otherwise available for
use with, VDE content containers comprise (for commercial
content distribution purposes) VDEF control capabilities (and
any associated parameter data) for electronic content. These
capabilities may constitute one or more "proposed" electronic
agreements (and/or agreement functions available for selection
- 55
CA 02479494 2004-10-04
wo nlom Mr/LW7nRA3
and/or use with parameter data) that manage the use and/or the
consequences of use of such content and which can enact the
terms and conditions of agreements involving multiple parties
and their various rights and obligations.
A VDE electronic agreement may be explicit, through a
user interface acceptance by one or more parties, for example by
a "junior" party who has received control information from a
"senior" party, or it may be a process amongst equal parties who
individually assert their agreement. Agreement may also result
from an automated electronic process during which terms and
conditions are "evaluated" by certain VDE participant control
information that assesses whether certain other electronic terms
and conditions attached to content and/or submitted by another
party are acceptable (do not violate acceptable control
information criteria). Such an evaluation process may be quite
simple, for example a comparison to ensure compatibility
between a portion of, or all senior, control terms and conditions
in a table of terms and conditions and the submitted control
information of a subsequent participant in a pathway of content
control information handling, or it may be a more elaborate
process that evaluates the potential outcome of, and/or
implements a negotiation process between, two or more sets of
control information submitted by two or more parties. VDE also
-56-
CA 02479494 2004-10-04
Wo 98009?A9 PCT/US97n5243
accommodates a semi-automated process during which one or
more VDE participants directly, through user interface means,
resolve "disagreements" between control information sets by
accepting and/or proposing certain control information that may
be acceptable to control information representing one or more
other parties interests and/or responds to certain user interface
queries for selection of certain alternative choices and/or for
certain parameter information, the responses being adopted if
acceptable to applicable senior control information.
When another party (other than the first applier of rules),
perhaps through a negotiation process, accepts, and/or adds to
andlor otherwise modifies, "in place" content control information,
a VDE agreement between two or more parties related to the use
of such electronic content may be created (so long as any
modifications are consistent with senior control information).
Acceptance of terms and conditions related to certain electronic
content may be direct and express, or it may be implicit as a
result of use of content (depending, for example, on legal
requirements, previous exposure to such terms and conditions,
and requirements of in place control information).
VDEF capabilities may be employed, and a VDE
agreement may be entered into, by a plurality of parties without
-57-
CA 02479494 2004-10-04
wo W09zo9 rCr/Q897115243
the VDEF capabilities being directly associated with the
controlling of certain, specific electronic information. For
example, certain one or more VDEF capabilities may be present
at a VDE installation, and certain VDE agreements may have
been entered into during the registration process for a content
distribution application, to be used by such installation for
securely controlling VDE content usage, auditing, reporting
and/or payment. Similarly, a specific VDE participant may enter
into a VDE user agreement with a VDE content or electronic
appliance provider when the user and/or her appliance register
with such provider as a VDE installation andlor user. In such
events, VDEF in place control information available to the user
VDE installation may require that certain VDEF methods are
employed, for example in a certain sequence. in order to be able
to use all and/or certain classes, of electronic content and/or VDE
applications.
VDE ensures that certain prerequisites necessary for a
given transaction to occur are met. This includes the secure
execution of any required load modules and the availability of
any required, associated data. For example, required load
modules and data (e.g. in the form of a method) might specify
that sufFicient credit from an authorized source must be
confirmed as available. It might further require certain one or
-58-
CA 02479494 2004-10-04
WO MOM
more load modules execute as processes at an appropriate time
to ensure that such credit will be used in order to pay for user
use of the content. A certain content provider might, for
example, require metering the number of copies made for
distribution to employees of a given software program (a portion
of the program might be maintained in encrypted form and
require the presence of a VDE installation to run). This would
require the execution of a metering method for copying of the
property each time a copy was made for another employee. This
same provider might also charge fees based on the total number
of different properties licensed from them by the user and a
metering history of their licensing of properties might be
required to maintain this information.
VDE provides organization, community, and/or universe
wide secure environments whose integrity is assured by
processes securely controlled in VDE participant user
installations (nodes). VDE installations, in the preferred
embodiment, may include both software and tamper resistant
hardware semiconductor elements. Such a semiconductor
arrangement comprises, at least in part, special purpose circuitry
that has been designed to protect against tampering with, or
unauthorized observation of, the information and functions used
in performing the VDE's control functions. The special purpose
-59-
CA 02479494 2004-10-04
WO 9M9209 PCT/US97/15243
secure circuitry provided bv the present invention includes at
least one of: a dedicated semiconductor arrangement known as a
Secure Processing Unit (SPU) and/or a standard microprocessor,
microcontroller, andlor other processing logic that accommodates
the requirements of the present invention and functions as an
SPU. VDE's secure hardware may be found incorporated into,
for example, a fax/modem chip or chip pack, I/0 controller, video
display controller, and/or other available digital processing
arrangernents. It is anticipated that portions of the present
invention's VDE secure hardware capabilities may ultimatelv be
standard design elements of central processing units (CPUs) for
computers and various other electronic devices.
Designing VDE capabilities into one or more standard
microprocessor, microcontroller and/or other digital processing
components may materially reduce VDE related hardware costs
by employing the same hardware resources for both the
transaction management uses contemplated by the present
invention and for other, host electronic appliance functions. This
means that a VDE SPU can employ (share) circuitry elements of
a "standard" CPU. For example, if a "standard" processor can
operate in protected mode and can execute VDE related
instructions as a protected activity, then such an embodiment
may provide sufficient hardware security for a variety of
-60-
CA 02479494 2004-10-04
wo 98189209 PCT/US97/15243
applications and the expense of a special purpose processor
might be avoided. Under one preferred embodiment of the
present invention, certain memory (e.g., RAM, ROM, NVRAM) is
maintained during VDE related instruction processing in a
protected mode (for example, as supported by protected mode
microprocessors). This memory is located in the same package as
the processing logic (e.g. processor). Desirably, the packaging
and memorv of such a processor would be designed using
security techniques that enhance its resistance to tampering.
The degree of overall security of the VDE system is
primarily dependent on the degree of tamper resistance and
concealment of VDE control process execution and related data
storage activities. Employing special purpose semiconductor
packaging techniques can significantlv contribute to the degree
of security. Concealment and tamper-resistance in
semiconductor memory (e.g., RAN1, ROM, NVRAM) can be
achieved, in part, by employing such memory within an SPU
package, by encrypting data before it is sent to external memory
(such as an external RAM package) and decrypting encrypted
data within the CPU/RAM package before it is executed. This
process is used for important VDE related data when such data
is stored on unprotected media, for example, standard host
storage, such as random access memory, mass storage, etc. In
-61-
CA 02479494 2004-10-04
wo 9949zo9 rczivs97n52a3
that event, a VDE SPU would encrypt data that results from a
secure VDE execution before such data was stored in exteraal
memory.
Summary of Some Ianpostant Featatree Provided by VDE in
Accordance With the Present Invention
VDE employs a variety of capabilities that serve as a
foundation for a general purpose, sufficiently secure distributed
electronic commerce solution. VDE enables an electronic
commerce marketplace that supports divergent, competitive
business partnerships, agreements, and evolving overall
business models. For example, VDE includes features that:
"sufficiently" impede unauthorized and/or
uncompensated use of electronic information andlor
appliances through the use of secure
communication, storage, and transaction
management technologies. VDE supports a model
wide, distributed security implementation which
creates a single secure "virtual" transaction
processing and information storage environment.
VDE enables distributed VDE installations to
securely store and communicate information and
remotely control the execution processes and the
-62-
CA 02479494 2004-10-04
WO W"209 rcr/US97nss4'3
character of use of electronic information at other
VDE installations and in a wide variety of ways;
= support low-cost, efficient, and effective security
architectures for transaction control, auditing,
reporting, and related communications and
information storage. VDE may employ tagging
related security techniques, the time-ageing of
encryption keys, the compartmentalization of both
stored control information (including differentially
tagging such stored information to ensure against
substitution and tampering) and distributed content
(to, for many content applications, employ one or
more content encryption keys that are unique to the
specific VDE installation and/or user), private key
techniques such as triple DES to encrypt content,
public key techniques such as RSA to protect
communications and to provide the benefits of
digital signature and authentication to securely bind
together the nodes of a VDE arrangement, secure
processing of important transaction management
executable code, and a combining of a small amount
of highly secure, hardware protected storage space
with a much larger "exposed" mass media storage
-63-
CA 02479494 2004-10-04
wo M9209 rciYOS97113W
space storing secured (normally encrypted and
tagged) control and audit information. VDE
employs special purpose hardware distributed
throughout some or all locations of a VDE
implementation: a) said hardware controlling
impormnt elements of: content preparation (such as
causing such content to be placed in a VDE content
container and associating content control
information with said content), content and/or
electronic appliance usage auditing, content usage
analysis, as well as content usage control; and b)
said hardware having been designed to securely
handle processing load module control activities,
wherein said control processing activities may
involve a sequence of required control factors;
0 support dynamic user selection of information
subsets of a VDE electronic information product
(VDE controlled content). This contrasts with the
constraints of having to use a few high level
individual, pre-defined content provider information
increments such as being required to select a whole
information product or product section in order to
acquire or otherwise use a portion of such product or
-64-
CA 02479494 2004-10-04
WO 98J0209 PGT/UM1S243
section. VDE supports metering and usage control
over a variety of increments (including "atomic"
increments, and combinations of different increment
, types) that are selected ad hoc by a user and
represent a collection of pre-identified one or more
increments (such as one or more blocks of a
preidentified nature, e.g., bytes, images, logically
related blocks) that form a generally arbitrary, but
logical to a user, content "deliverable." VDE control
inforrnation (including budgeting, pricing and
metering) can be configured so that it can
specifically apply, as appropriate, to ad hoc selection
of different, unanticipated variable user selected
aggregations of information increments and pricing
levels can be, at least in part, based on quantities
and/or nature of mixed increment selections (for
example, a certain quantitv of certain text could
mean associated images might be discounted by
15%; a greater quantity of text in the "mixed"
increment selection might mean the images are
discounted 20%). Such user selected aggregated
information increments can reflect the actual
requirements of a user for information and is more
flexible than being limited to a single, or a few, high
- 65
CA 02479494 2004-10-04
w0 9M092 9 Pcrnrs97/0M
level, (e.g. product, document, database record)
predetermined increments. Such high level
increments may include quantities of information
not desired by the user and as a result be more
costly than the subset of information needed by the
user if such a subset was available. In sum, the
present invention allows information contained in
electronic information products to be supplied
according to user specification. Tailoring to user
specification allows the present invention to provide
the greatest value to users, which in turn will
generate the greatest amount of electronic commerce
activity. The user, for example, would be able to
define an aggregation of content derived from
various portions of an available content product, but
which, as a deliverable for use by the user, is an
entirely unique aggregated increment. The user
may, for example, select certain numbers of bytes of
information from various portions of an information
product, such as a reference work, and copy them to
disc in unencrypted form and be billed based on
total number of bytes plus a surcharge on the
number of "articles" that provided the bytes. A
content provider might reasonably charge less for
-66-
CA 02479494 2004-10-04
WO 984)9209 PCTN07/1sZ43
such a user defined information increment since the
user does not require all of the content firom aIl of
the articles that contained desired information. This
process of defining a user desired iaformation
increment may involve artificial intelligence
database search tools that contribute to the location
of the most relevant portions of information from an
information product and cause the automatic display
to the user of information describing search criteria
hits for user selection or the automatic extraction
and delivery of such portions to the user. VDE
further supports a wide variety of predefined
increment types including:
= bytes,
= images,
= content over time for audio or video, or any
other increment that can be identified by content
provider data mapping efforts, such as:
= sentences,
= paragraphs,
= articles,
= database records, and
= byte offsets representing increments of
logically related information.
-67-
CA 02479494 2004-10-04
wo 98/ro71o9 PCTlUS97/15243
VDE supports as many simultaneous predefined increment types
as may be practical for a given type of content and business
model.
= securely store at a user's site potentially highly
detailed information reflective of a user's usage of a
variety of different content segment types and
employing both inexpensive "exposed" host mass
storage for maintaining detailed information in the
form of encrypted data and maintaining summary
information for security testing in highly secure
special purpose VDE installation nonvolatile
memory (if available).
= support trusted chain of handling capabilities for
pathways of distributed electronic information
and/or for content usage related information. Such
chains may extend, for example, from a content
creator, to a distributor, a redistributor, a client
user, and then may provide a pathway for securely
reporting the same and/or differing usage
information to one or more auditors, such as to one
or more independent clearinghouses and then back
to the content providers, including content creators.
-68-
CA 02479494 2004-10-04
wo NAMM rcrrtrs"nsm
The same and/or different pathways employed for
certain content handling, and related content control
information and reporting information handling,
may also be employed as one or more pathways for
electronic payment handling (payment is
characterized in the present invention as
administrative content) for electronic content and/or
appliance usage. These pathways are used for
conveyance of all or portions of content, and/or
content related control information. Content
creators and other providers can specify the
pathways that, partially or fully, must be used to
disseminate commercially distributed property
content, content control information, payment
administrative content, andi'or associated usage
reporting information. Control information specified
by content providers may also specify which specific
parties must or may (including, for example, a group
of eligible parties from which a selection may be
made) handle conveyed information. It may also
specify what transmission means (for example
telecommunication carriers or media types) and
= transmission hubs must or may be used.
-69-
CA 02479494 2004-10-04
wo MOM rcrtis"iism
= support fleaible auditing mecbanisms, such as
employing 'bitmap meters," that achieve a high
degree of efficiency of operation and throughput and
allow, in a practical manner, the retention and
ready recall of information related to previous usage
activities and related patterns. This flexibility is
adaptable to a wide variety of billing and security
control strategies such as:
0 upgrade pricing (e.g. suite purchases),
~ pricing discounts (including quantity
discounts),
= billing related time duration variables such as
discounting new purchases based on the
timing of past purchases, and
8 security budgets based on quantity of
different, logicaIly related units of electronic
information used over an interval of time.
Use of bitmap meters (including "regular" and
"wide" bitmap meters) to record usage and/or
purchase of information, in conjunction with other
elements of the preferred embodiment of the present
invention, uniquely supports efficient maintenance
of usage history for: (a) rental, (b) flat fee licensing
-70-
CA 02479494 2004-10-04
WO 98009209 PGT/US97/151A3
or purchase, (c) licensing or purchase discounts
based upon historical usage variables, and (d)
reporting to users in a manner enabling users to
determine whether a certain item was acquired, or
acquired within a certain time period (without
requiring the use of conventional database
mechanisms, which are highly inefficient for these
applications). Bitmap meter methods record
activities associated with electronic appliances,
propenies, objects, or portions thereof,.and/or
administrative activities that are independent of
specific properties, objects, etc., performed by a user
and/or electronic appliance such that a content
and/or appliance provider andlor controller of an
administrative activity can determine whether a
certain activity has occurred at some point, or
during a certain period, in the past (for example,
certain use of a commercial electronic content
product and/or appliance). Such determinations can
then be used as part of pricing and/or control
strategies of a content and/or appliance provider,
and/or controller of an administrative activity. For
example, the content provider may choose to charge
only once for access to a portion of a property,
-71-
CA 02479494 2004-10-04
wo 9MZ09 PGT/US97n5243
regardless of the number of times that portion of the
property is accessed by a user.
= support "launchable" content, that is content that
can be provided by a content provider to an
end-user, who can then copy or ,pass along the
content to other end-user parties without requiring
the direct participation of a content provider to
register and/or otherwise initialize the content for
use. This content goes "out of (the traditional
distribution) channel" in the form of a "traveling
object." Traveling objects are containers that
securely carry at least some permissions information
and/or methods that are required for their use (such
methods need not be carried by traveling objects if
the required methods will be available at, or directly
available to, a destination VDE installation).
Certain travelling objects may be used at some or all
VDE installations of a given VDE arrangement since
they can make available the content control
information aecessary for content use without
requiring the involvement of a commercial VDE
value chain participant or data security
administrator (e.g. a control officer or network
-72-
CA 02479494 2004-10-04
w0 90109zo9 rcrrtrMnSM
administrator). As long as traveling object control
information requirements are available at the user
VDE installation secure subsystem (such as the
presence of a su$$cient quantity of financial credit
from an authorized credit provider), at least some
travelling object content may be used by a receiving
party without the need to establish a connection
with a remote VDE authority (until, for example,
budgets are exhausted or a time content usage
reporting interval has occurred). Traveling objects
can travel "out-of-channel," allowing, for example, a
user to give a copy of a traveling object whose
content is a software program, a movie or a game, to
a neighbor, the neighbor being able to use the
traveling object if appropriate credit (e.g. an
electronic clearinghouse account from a
clearinghouse such as VISA or AT&T) is available.
Similarly, electronic information that is generally
available on an Internet, or a similar network,
repository might be provided in the form of a
traveling object that can be downloaded and
subsequently copied by the initial downloader and
then passed along to other parties who may pass the
object on to additional parties.
-?3.
CA 02479494 2004-10-04
WO 98J09209 PCTlUS97nS243
= provide very flexible and extensible user
identification according to individuals, i.nstallations,
by groups such as classes, and by function and
hierarchical identification employing a hierarchy of
levels of client identification (for example, client
organization ID, client department ID, client
network ID, client project ID, and client employee
ID, or any appropriate subset of the above).
= provide a general purpose, secure, coinponent based
content control and distribution system that
functions as a foundation transaction operating
system environment that employs executable code
pieces crafted for transaction control and auditing.
These code pieces can be reused to optimize
efficiency in creation and operation of trusted,
distributed transaction management arrangements.
VDE supports providing such executable code in the
form of "atomic" load modules and associated data.
Many such load modules are inherently
configurable, aggregatable, portable, and extensible
and singularly, or in combination (along with
associated data), run as control methods under the
VDE transaction operating environment. VDE can
-74-
CA 02479494 2004-10-04
wo 98A9Z09 rcr/OS97113M
satisfy the requirements of widely differing
electronic commerce and data security applications
by, in part, employing this general purpose
' transaction management foundation to securely
process VDE transaction related control methods.
Control methods are created primarily through the
use of one or more of said executable, reusable load
module code pieces (normally in the form of
executable object components) and associated data.
The component nature of control methods allows the
present invention to efficiently operate as a highly
configurable content control system. Under the
present invention, content control models can be
iteratively and asynchronously shaped, and
otherwise updated to accommodate the needs of
VDE participants to the extent that such shaping
and otherwise updating conforms to constraints
applied by a VDE application, if any (e.g., whether
new component assemblies are accepted and, if so,
what certification requirements exist for such
component assemblies or whether any or certain
participants may shape any or certain control
information by selection amongst optional control
information (permissions record) control methods.
-75-
CA 02479494 2004-10-04
WO 98109209 YCP/US97115243
This iterative (or concurrent) multiple participant
process occurs as a result of the submission and use
of secure, control information components
(executable code such as load modules and/or
methods, and/or associated data). These
components may be contributed independently by
secure communication between each control
information influencing VDE participant's VDE
installation and may require certification for use
with a given application, where such certification
was provided by a certification service manager for
the VDE arrangement who ensures secure
interoperability andlor reliability (e.g., bug control
resulting from interaction) between appliances and
.15 submitted control methods. The transaction
management control functions of a VDE electronic
appliance transaction operating environment
interact with non-secure transaction management
operating system functions to properly direct
transaction processes and data related to electronic
information security, usage control, auditing, and
usage reporting. VDE provides the capability to
manages resources related to secure VDE content
-76.
CA 02479494 2004-10-04
wo 9&109z09 Pcr/[J397nS243
and/or appliance control information execution and
data storage.
= facilitate creation of application and/or system
functionality under VDE and to facilitate integration
into electronic appliance environments of load
modules and methods created under the present
invention. To achieve this, VDE employs an
Application Programmer's Interface (API) and/or a
transaction operating system (such as a ROS)
programming language with incorporated functions,
both of which support the use of capabilities and can
be used to efficiently and tightly integrate VDE
functionality into commercial and user applications.
= support user interaction through: (a) "Pop-Up"
applications which, for example, provide messages to
users and enable users to take specific actions such
as approving a transaction, (b) stand-alone VDE
applications that provide administrative
environments for user activities such as: end-user
preference specifications for limiting the price per
transaction, unit of time, and/or session, for
-77-
CA 02479494 2004-10-04
wo 9810s09 rCr1US97/1520
accessing history information concerning previous
transactions, for reviewing financial information
such as budgets, expenditures (e.g. detailed and/or
summary) and usage analysis information, and (c)
VDE aware applications which, as a result of the use
of a VDE API and/or a transaction management (for
example, ROS based) programming language
embeds VDE "awareness" into commercial or
internal software (application programs, games, etc.)
so that VDE user control information and services
are seamlessly integrated into such software and
can be directly accessed by a user since the
underlying functionality has been integrated into
the commercial software's native design. For
example, in a VDE aware word processor
application, a user may be able to "print" a
document into a VDE content container object,
applying specific control information by selecting
from amongst a series of different menu templates
for different purposes (for example, a confidential
memo template for internal organization purposes
may restrict the ability to "keep," that is to make an
electronic copy of the memo).
-78-
CA 02479494 2004-10-04
WO MAD9?A9 PCrlU89T/iS243
= employ "templates ' to ease the process of configuring
capabilities of the present invention as they relate to
specific industries or businesses. Templates are
applications or application add-ons under the
present invention. Templates support the efficient
specification and/or manipulation of criteria related
to specific content types, distribution approaches,
pricing mechanisms, user interactions with content
and/or administrative activities, and/or the like.
Given the very large range of capabilities and
configurations supported by the present invention,
reducing the range of configuration opportunities to
a manageable subset particularly appropriate for a
given business model allows the full configurable
.15 power of the present invention to be easily employed
by "typical" users who would be otherwise burdened
with complex programming and/or configuration
design responsibilities template applications can
also help ensure that VDE related processes are
secure and optimally bug free by reducing the risks
associated with the contribution of independently
developed load modules, including unpredictable
' aspects of code interaction between independent
modules and applications, as well as security risks
-79-
CA 02479494 2004-10-04
Wo 98009209 rcz/US9711sZ43
associated with possible presence of viruses in such
modules. VDE, through the use of templates,
reduces typical user configuration responsibilities to
an appropriately focused set of activities including
selection of method types (e.g. functionality) through
menu choices such as multiple choice, icon selection,
and/or prompting for method parameter data (such
as identification information, prices, budget limits,
dates, periods of time, access rights to specific
content, etc.) that supply appropriate and/or
necessary data for control information purposes. By.
limiting the typical (non-program*ning) user to a
limited subset of configuration activities whose
general configuration environment (template) has
been preset to reflect general requirements
corresponding to that user, or a content or other
business model can very substantially :imit
difficulties associated with content containerization
(including placing initial control information on
content), distribution, client administration,
electronic agreement implementation, end-user
interaction, and clearinghouse activities, including
associated interoperability problems (such as
conflicts resulting from security, operating system,
-80-
CA 02479494 2004-10-04
wo eseosa- PCT/US"IISW
and/or certification incompatibilities). Use of
appropriate VDE templates can assure users that
their activities related to content VDE
containerization, contribution of other control
information, communicatione, encryption techniques
and/or keys, etc. will be in compliance with
specifications for their distributed VDE
arrangement. VDE templates constitute preset
configurations that can normally be reconfigurable
to allow for new and/or modified templates that
reflect adaptation into new industries as they evolve
or to reflect the evolution or other change of an
existing industry. For example, the template
concept may be used to provide individual, overall
frameworks for organizations and individuals that
create, modify, market, distribute, consume, and/or
otherwise use movies, audio recordings and live
performances, magazines, telephony based retail
sales, catalogs, computer software, information data
bases, multimedia, commercial communications,
advertisements, market surveys, infomercials,
games, CAD/CAM services for numerically
= controIled machines, and the like. As the context
surrounding these templates changes or evolves,
-81-
CA 02479494 2004-10-04
WO "109?A9 PC'T/0$97/1S243
template applications provided under the present
invention may be modified to meet these changes for
broad use, or for more focused activities. A given
VDE participant may have a plurality of templates
available for different tasks. A party that places
content in its initial VDE container may have a
variety of different, configurable templates
depending on the type of content and/or business
model related to the content. An end-user may have
different configurable templates that can be applied
to different document types (e-mail, secure internal
documents, database records, etc.) and/or subsets of
users (applying differing general sets of control
i.nformation to different bodies of users, for example,
-15 selecting a list of users who may, under certain
preset criteria, use a certain document). Of course,
templates may, under certain circumstances have
fixed control information and not provide for user
selections or parameter data entry.
= support plural, different control models regulating
the use and/or auditing of either the same specific
copy of electronic information content and/or
differently regulating different copies (occurrences)
-82-
CA 02479494 2004-10-04
w0 9&I"W rcrrtrMnsM
of the same electronic information content.
Differing models for biUing, auditing, and security
can be applied to the same piece of electronic
information content and such differing sets of
control information may employ, for control
purposes, the same, or differing, granularities of
electronic information control increments. This
includes supporting variable control information for
budgeting and auditing usage as applied to a variety
of predefined increments of electronic- information,
including emploving a variety of different budgets
and/or metering increments for a given electronic
information deliverable for: billing units of measure,
credit limit, security budget limit and security
content metering increments, and/or market
surveying and customer profiling content metering
increments. For example, a CD-ROM disk with a
database of scientific articles might be in part billed
according to a formula based on the number of bytes
decrypted, number of articles containing said bytes
decrypted, while a security budget might limit the
= use of said database to no more than 5% of the
database per month for users on the wide area
network it is installed on.
-83-
CA 02479494 2004-10-04
w0 9anno9 rcrrvs97nsaa3
= provide mechanisms to persistently maintain
trusted content usage and reporting control
information through both a sufficiently secure chain
of handling of content and content control
information and through various forms of usage of
such content wherein said persistence of control may
survive such use. Persistence of control includes the
ability to extract information from a VDE container
object by creating a new container whose contents
are at least in part secured and that contains both
the extracted content and at least a portion of the
control information which control information of the
original container and/or are at least in part
produced by control information of the original
container for this purpose and/or VDE installation
control information stipulates should persist and/or
control usage of content in the newly formed
container. Such control information can continue to
manage usage of container content if the container
is "embedded" into another VDE managed object,
such as an object which contains plural embedded
VDE containers, each of which contains content
derived (extracted) from a different source.
-84-
CA 02479494 2004-10-04
wo 9MM9 rcrnrs9711sU3
= enables users, other value chain participants (such
as clearinghouses and government agencies), and/or
user organizations, to specify preferences or
requirements related to their use of electronic
content and/or appliances. Content users, such as
end-user customers using commercially distributed
content (games, information resources, software
programs, etc.), can deSne, if allowed by senior
control information, budgets, and/or other control
information, to manage their own anternal use of
content. Uses include, for example, a user setting a
limit on the price for electronic documents that the
user is willing to pay without prior express user
authorization, and the user establishing the
character of metering information he or she is
willing to allow to be collected (privacy protection).
This includes providing the means for content users
to protect the privacy of information derived from
their use of a VDE instaIIation and content and/or
appliance usage auditing. In particular, VDE can
prevent information related to a participant's usage
of electronic content from being provided to other
parties without the participant's tacit or explicit
agreement.
-85-
CA 02479494 2004-10-04
wo "fi9209 rcr/U997nS2I3
= provide mechanisms that allow control information
to "evolve" and be modified according, at least in
part, to independently, securely delivered further
control information. Said control information may
include executable code (e.g., load modules) that has
been certified as acceptable (e.g., reliable and
trusted) for use with a specific VDE application,
class of applications, and/or a VDE distributed
arrangement. This modification (evolution) of
control information can occur upon content control
information (load modules and anv associated data)
circulating to one or more VDE participants in a
pathway of handling of control information, or it
may occur upon control information being received
from a VDE participant. Handlers in a pathway of
handling of content control information, to the
extent each is authorized, can establish, modify,
and/or contribute to, permission, auditing, payment,
and reporting control information related to
controlling, analyzing, paying for, and/or reporting
usage of, electronic content and/or appliances (for
example, as related to usage of VDE controlled
property content). Independently delivered (from an
independent source which is independent except in
- 86 -
CA 02479494 2004-10-04
wo 9sM9so9 rcrnr897/15243
regards to certification), at least in part secure,
control information can be employed to securely
modify content control information when content
control information has flowed from one party to
another party in a sequence of VDE content control
information handling. This modification employs,
for example, one or more VDE component
assemblies being securely processed in a VDE secure
subsystem. In an alternate embodiment, control
information mav be modified by a senior party
through use of their VDE installation secure
sub-system after receiving submitted, at least in
part secured, control information from a "junior"
party, normally in the form of a tiDE administrative
object. Control information passing along VDE
pathways can represent a mixed control set, in that
it may include: control information that persisted
through a sequence of control information handlers,
other control information that was allowed to be
modified, and further control informatiori
representing new control information and/or
= mediating data. Such a control set represents an
' evolution of control information for disseminated
content. In this example the overall content control
-87-
CA 02479494 2004-10-04
wo 9RIa2S9 rCrrO897n5Z43
set for a VDE content container is "evolving" as it
securely (e.g. communicated in encrypted form and
using authentication and digital signaturing
techniques) passes, at least in part, to a new
participant's VDE installation where the proposed
control information is securely received and
handled. The received control information may be
integrated (through use of the receiving parties'
VDE installation secure sub-system) with in-place
control information through a negotiation process
involving both control information sets. For
example, the modification, within the secure
sub-system of a content provider's VDE installation,
of content control information for a certain VDE
content container may have occurred as a result of
the incorporation of required control information
provided by a financial credit provider. Said credit
provider may have employed their VDE installation
to prepare and securely communicate (directly or
indirectly) said required control information to said
content provider. Incorporating said required
control information enables a content provider to
allow the credit provider's credit to be employed by a
content end-user to compensate for the end-user's
-88-
CA 02479494 2004-10-04
wo 9&V9Z09 PCT/US97nS243
use of VDE controlled content and/or appliances, so
long as said end-user has a credit account with said
financial credit provider and said credit account has
sufficient credit available. Similarly, control
information requiring the payment of taxes andlor
the provision. of revenue information resulting from
electronic commerce activities may be securely
received by a content provider. This control
information may be received, for example, from a
government agency. Content providers might be
required by law to incorporate such control
information into the control information for
commercially distributed content and/or services
related to appliance usage. Proposed control
information is used to an extent allowed by senior
control information and as determined by any
negotiation trade-offs that satisfy priorities
stipulated by each set (the received set and the
proposed set). VDE also accommodates different
control schemes specifically applying to different
participants (e.g., individual participants and/or
- participant classes (types)) in a network of VDE
content handling participants.
-89-
CA 02479494 2004-10-04
WO 9f109?a19 YGT/Os97/f.3s43
= support muitiple simultaneous control models for
the same content property and/or property portion.
This allows, for example, for concurrent business
activities which are dependent on electronic
commercial product content distribution, such as
acquiring detailed market survey information and/or
supporting advertising, both of which can increase
revenue and result in lower content costs to users
and greater value to content providers. Such control
information and/or overall control models may be
applied, as determined or allowed by control
information, in differing manners to different
participants in a pathwav of content, reporting,
payment, andlor related control information
handling. VDE supports applying different content
control information to the same and/or different
content and/or appliance usage related activities,
and/or to different parties in a content and/or
appliance usage model, such that different parties
(or classes of VDE users, for example) are subject to
differing control information managing their use of
electronic information content. For example,
differing control models based on the category of a
user as a distributor of a VDE controlled content
-90-
CA 02479494 2004-10-04
wo MOzo9 rcrnrMrlisW
object or an end-user of such content may result in
different budgets being applied. Alternatively, for
example, a one distributor may have the right to
distribute a different array of properties than
another distributor (from a common content
collection provided, for example, on optical disc). An
individual, and/or a class or other grouping of
end-users, may have different costs (for example, a
student, senior citizen, and/or poor citizen user of
content who may be provided with the same or
differing discounts) than a "typical" content user.
= support provider revenue information resulting from
customer use of content and/or appliances, andlor
provider and/or end-user payment of taxes, through
the transfer of credit and/or electronic currency from
said end-user and/or provider to a government
agency, might occur "automatically" as a result of
such received control information causing the
generation of a VDE content container whose
content includes customer content usage information
reflecting secure, trusted revenue summary
information and/or detailed user transaction listings
(level of detail might depend, for example on type or
-91-
CA 02479494 2004-10-04
wo 9MO09 rcrn)s7n5?A3
size of transaction-information regarding a baak
interest pa-vment to a customer or a transfer of a
large (e.g. over $10,000) might be, by law,
automatically reported to the government). Such
summary and/or detailed information related to
taxable events and/or currency, and/or creditor
currency transfer, may be passed along a pathway of
reporting and/or payment to the government in a
VDE container. Such a container mav also be used
for other VDE related content usage reporting
information.
= support the flowing of content control information
through different "branches" of content control
information handling so as to accommodate, under
the present invention's preferred embodiment,
diverse controlled distributions of VDE controlled
content. This allows different parties to employ the
same initial electronic content with differing
(perhaps competitive) control strategies. In this
instance, a party who first placed control
information on content can make certain control
assumptions and these assumptions would evolve
into more specific and/or extensive control
-92-
CA 02479494 2004-10-04
wo 981O9ZOS rcrrtT897nxt43
assumptions. These control assumptions can evolve
during the branching sequence upon content model
participants submitting control information changes,
for example, for use in "negotiating" with "in place"
content control information. This can result in new
or modified content control information and/or it
might involve the selection of certain one or more
already "in-place" content usage control methods
over in-place alternative methods, as well as the
submission of relevant control information
parameter data. This form of evolution of different
control information sets applied to different copies of
the same electronic property content and/or
appliance results from VDE control information
flowing "down" through different branches in an
overall pathway of handling and control and being
modified differently as it diverges down these
different pathway branches. This ability of the
present invention to support multiple pathway
branches for the flow of both VDE content control
information and VDE managed content enables an
electronic commerce marketplace which supports
diverging, competitive business partnerships,
agreements, and evolving overall business models
-93-
CA 02479494 2004-10-04
wo M09209 rcrlU897nss13
which can employ the sams content properties
combined, for example, in differing coIIections of
content representing differing at least in part
competitive products.
= enable a user to securely extract, through the use of
the secure subsystem at the user's VDE installation,
at least a portion of the content included within a
VDE content container to produce a new, secure
object (content container), such that the extracted
information is maintained in a continually secure
manner through the extraction process. Formation
of the new VDE container containing such extracted
content shall result in control information consistent
.15 with, or specified by, the source VDE content
container, and/or local VDE installation secure
subsystem as appropriate, content control
information. Relevant control information, such as
security and administrative information, derived, at
least in part, from the parent (source) object's
control information, will normally be automatically
inserted into a new VDE content container object
containing extracted VDE content. This process
typically occurs under the control framework of a
-94-
CA 02479494 2004-10-04
WO lWO9209 PCT/US99/15243
parent object and/or VDE installation control
information executing at the user's VDE installation
secure subsystem (with, for example, at least a
portion of this inserted control information being
stored securelv in encrypted form in one or more
permissions records). In an alternative embodiment,
the de.rived content control information applied to
extracted content may be in part or whole derived
from, or employ, content control information stored
remotely from the V'DE installation that performed
the secure extraction such as at a remote server
location. As with the content control information for
most VDE managed content, features of the present
invention allows the content's control information to:
(a) "evolve," for example, the extractor of content
may add new control methods and/or modi.fy
control parameter data, such as VDE
application compliant methods, to the extent
allowed by the content's in-place control
information. Such new control information
might specify, for example, who may use at
least a portion of the new object, and/or how
said at least a portion of said extracted
-95-
CA 02479494 2004-10-04
WO 98/0m rcr/US97n5aa3
content may be used (e.g. when at least a
portion may be used, or what portion or
quantity of portions may be used);
(b) allow a user to combine additional content
with at least a portion of said extracted
content, such as material authored by the
extractor and/or content (for example, images,
video, audio, and/or text) extracted from one
or more other VDE container objects for
placement directly into the new container;
(c) allow a user to securely edit at least a portion
of said content while maintaining said content
in a secure form within said VDE content
container;
(d) append extracted content to a pre-existing
VDE content container object and attach
associated control information - in these
cases, user added information may be secured,
e.g., encrypted, in part or as a whole, and may
be subject to usage andlor auditing control
-96-
CA 02479494 2004-10-04
wo 98A9as9 pcT/Us97115Z43
information that differs from the those applied
to previously in place object content;
= (e) preserve VDE control over one or more
portions of extracted content after various
forms of usage of said portions, for example,
maintain content in securely stored form
while allowing "temporary" on screen display
of content or allowing a software program to
be maintained in secure form but transiently
decrypt any encrypted executing portion of
said program (all, or only a portion, of said
program may be encrypted to secure the
program).
Generally, the extraction features of the present
invention allow users to aggregate and/or
disseminate and/or otherwise use protected
electronic content information extracted from
content container sources while maintaining secure
VDE capabilities thus preserving the rights of
= providers in said content information after various
content usage processes.
-97-
CA 02479494 2004-10-04
wo 9dJ09209 PCTI[J397/0?A3
= support the aggregation of portions of VDE
controlled content, such portions being subject to
differing VDE content container control information,
wherein various of said portions may have been
provided by independent, different content providers
from one or more different locations remote to the
user performing the aggregation. Such aggregation,
in the preferred embodiment of the present
invention, may involve preserving at least a portion
of the control information (e.g., executable code such
as load modules) for each of various of said portions
by, for example, embedding some or all of such
portions individually as VDE content container
objects within an overall VDE content container
and/or embedding some or all of such portions
directly into a VDE content container. In the latter
case, content control information of said content
container may apply differing control information
sets to various of such portions based upon said
portions original control information requirements
before aggregation. Each of such embedded VDE
content containers may have its own control
information in the form of one or more permissions
records. Alternatively, a negotiation between
-98-
CA 02479494 2004-10-04
wo 98lom PG1'nrS97/0243
control information associated with various
aggregated portions of electronic content, may
produce a control information set that would govern
some or all of the aggregated content portions. The
VDE content control information produced by the
negotiation may be uniform (such as having the
same load modules and/or component assemblies,
and/or it may apply differing such content control
information to two or more portions that constitute
an aggregation of VDE controlled content such as
differing metering, budgeting, billing and/or
payment models. For example, content usage
payment may be automatically made, either through
a clearinghouse, or directlv, to different content
providers for different potions.
= enable flexible metering of, or other collection of
information related to, use of electronic content
and/or electronic appliances. A feature of the
present invention enables such flexibility of
metering control mechanisms to accommodate a
- simultarteous, broad array of: (a) different
' parameters related to electronic information content
use; (b) different increment units (bytes, documents,
-99-
CA 02479494 2004-10-04
wo W091A9 rMrtrS97113243
properties, paragraphs, images, etc.) and/or other
organizations of such electronic content; andlor (c)
different categories of user and/or VDE installation
types, such as client organizations, departments,
projects, networks, andlor individual users, etc.
This feature of the present invention can be
employed for content security, usage analysis (for
example, market surveying), and/or compensation
based upon the use and/or exposure to VDE
managed content. Such metering is a flexible basis
for ensuring payment for content royalties,
licensing, purchasing, and/or advertising. A feature
of the present invention provides for payment means
supporting flexible electronic currency and credit
mechanisms, including the ability to securely
maintain audit trails reflecting information related
to use of such currency or credit. VDE supports
multiple differing hierarchies of client organization
control information wherein an organization client
administrator distributes control information
specifying the usage rights of departments, users,
and/or projects. Likewise, a department (division)
network manager can function as a distributor
-100-
CA 02479494 2004-10-04
wo 9&VM rcrNSmnszas
(budgets, access rights, etc.) for department
networks, projects, and/or users, etc.
= provide scalable, integratable, standardized control
means for use on electronic appliances ranging from
inexpensive consumer (for example, television
set-top appliances) and professional devices (and
hand-held PDAs) to servers, mainframes,
communication switches, etc. The scalable
transaction rnanagement!auditing technology of the
present invention will result in more efficient and
reliable interoperability amongst devices functioning
in electronic commerce and/or data security
environments. As standardized physical containers
have become essential to the shipping of physical
goods around the world, allowing these physical
containers to universally "fit" unloading equipment,
efficiently use truck and train space, and
accommodate known arrays of objects (for example,
boxes) in an efficient manner, so VDE electronic
content containers may, as provided by the present
= invention, be able to efficiently move electronic
information content (such as commercially published
properties, electronic currency and credit, and
-101-
CA 02479494 2004-10-04
WO 98J09Z09 PC17US9711s?.43
content audit information), and associated content
control information, around the world.
Interoperability is fundamental to effiicient
electronic commerce. The design of the VDE
foundation, VDE load modules, and VDE containers,
are important features that enable the VDE node
operating environment to be compatible with a very
broad range of electronic appliances. The ability, for
example, for control methods based on load modules
to execute in very "small" and inexpensive secure
sub-system environments, such as environments
with very little read/write memory, while also being
able to execute in large memory sub-systems that
may be used in more expensive electronic
appliances, supports consistency across many
machines. This consistent VDE operating
environment, including its control structures and
container architecture, enables the use of
standardized VDE content containers across a broad
range of device types and host operating
environments. Since VDE capabilities can be
seamlessly integrated as extensions, additions,
and/or modifications to fundamental capabilities of
electronic appliances and host operating systems,
-102-
CA 02479494 2004-10-04
WO M09Z09 K,'1'/U$97/LSZ43
VDE containers, content control information, and
the VDE foundation will be able to work with many
device types and these device types will be able to
. consistently and efficiently interpret and enforce
' 5 VDE control information. Through this integration
users can also benefit from a transparent interaction
with many of the capabilities of VDE. VDE
integration with software operating on a host
electronic appliance supports a variety of
capabilities that wouid be unavailable or less secure
without such integration. Through integration with
one or more device applications and/or device
operating environments, many capabilities of the
present invention can be presented as inherent
capabilities of a given electronic appliance,
operating system, or appliance application. For
example, features of the present invention include:
(a) VDE system software to in part extend and/or
modify host operating systems such that they
possesses VDE capabilities, such as enabling secure
= transaction processing and electronic information
storage; (b) one or more application programs that in
. part represent tools associated with VDE operation;
and/or (c) code to be integrated into application
-103-
CA 02479494 2004-10-04
wo 98/09ZOS rcrruM7115s43
programs, wherein such code incorporates references
into VDE system software to integrate VDE
capabilities and makes such applications VDE
aware (for example, word processors, database
retrieval applications, spreadsheets, multimedia
presentation authoring tools, film editing software,
music editing software such as MIDI applications
and the like, robotics control systems such as those
associated with CAD/CAM environments and NCM
software and the like, electronic mail systems,
teleconferencing software, and other data authoring,
creating, handling, and/or usage applications
including combinations of the above). These one or
more features (which may also be implemented in
firmware or hardware) may be employed in
conjunction with a VDE node secure hardware
processing capability, such as a microcontroller(s),
microprocessor(s), other CPU(s) or other digital
processing logic.
= employ audit reconciliation and usage pattern
evaluation processes that assess, through certain,
normally network based, transaction processing
reconciliation and threshold checking activities,
- 104 -
CA 02479494 2004-10-04
wo M9209 rcr/rtrW7115s43
whether certain violations of security of a VDE
arrangement have occurred. These processes are
performed remote to VDE controlled content
end-user VDE locations by assessing, for example,
purchases, and/or requests, for electronic properties
by a given VDE installation. Applications for such
reconciliation activities include assessing whether
the quantity of remotely delivered VDE controlled
content corresponds to the amount of financial credit
and/or electronic currency employed for the use of
such content. A trusted organization can acquire
information from content providers concerning the
cost for content provided to a given VDE installation
and/or user and compare this cost for content with
the credit andlor electronic currency disbursements
for that installation and/or user. Inconsistencies in
the amount of content delivered versus the amount
of disbursement can prove, and/or indicate,
depending on the circumstances, whether the local
VDE instaIlation has been, at least to some degree,
, compromised (for example, certain important system
security functions, such as breaking encryption for
at least some portion of the secure subsystem and/or
VDE controlled content by uncovering one or more
- 105 -
CA 02479494 2004-10-04
WO 90Ji99?A9 PCTIUS9711S3A3
keys). Determining whether irregular patterns (e.g.
unusually high demand) of content usage, or
requests for delivery of certain kinds of VDE
controlled information during a certain time period
by one or more VDE installations andlor users
(including, for example, groups of related users
whose aggregate pattern of usage is suspicious) may
also be useful in deternnining whether security at
such one or more installations, and/or by such one or
more users, has been compromised, particularly
when used in combination with an assessment of
electronic credit andlor currency provided to one or
more VDE users and/or installations, by some or all
of their credit andlor currency suppliers, compared
with the disbursements made by such users and/or
installations.
~ support security techniques that materially increase
the time required to "break" a system's integrity.
This includes using a collection of techniques that
minimizes the damage resulting from comprising
some aspect of the security features of the present
inventions.
-106-
CA 02479494 2004-10-04
wo WI9ZO9 rcrrtJS97nS1,43
+ provide a family of authoring, administrative,
reporting, payment, and billing tool user
= applications that comprise components of the
present invention's trusted/secure, universe wide,
distributed transaction control and administration
system. These components support VDE related:
object creation (including placing control
information on content), secure object distribution
and management (including distribution control
information, financial related, and other usage
analysis), client internal VDE activities
administration and control, security management,
user interfaces, payment disbursement, and
clearinghouse related functions. These components
are designed to support highly secure, uniform,
consistent, and standardized: electronic commerce
and/or data security pathwav(sJ of handling,
reporting, and/or payment; content control and
administration; and human factors (e.g. user
interfaces).
+ support the operation of a plurality of
= clearinghouses, including, for example, both
financial and user clearinghouse activities, such as
-107-
CA 02479494 2004-10-04
wo M09209 pCTNg~/LSM
those performed by a client administrator in a large
organization to assist in the organization's use of a
VDE arrangement, including usage information
analysis, and control of VDE activities by
individuals and groups of employees such as
specifying budgets and the character of usage rights
available under VDE for certain groups of and/or
individual, client personnel, subject to control
information series to control information submitted
by the client admuiistrator. At a clearinghouse, one
or more VDE installations may operate together
with a trusted distributed database environment
(which may include concurrent database processing
meansi. A financial clearinghouse normally receives
at its location securely delivered content usage
information, and user requests (such as requests for
further credit, electronic currency, and/or higher
credit limit). Reporting of usage information and
user requests can be used for supporting electronic
currency, billing, payment and credit related
activities, and/or for user profile analysis and/or
broader market survey analysis and marketing
(consolidated) list generation or other information
derived, at least in part, from said usage
- 108 -
CA 02479494 2004-10-04
wo W09209 PCTJU897nSZA3
information. this information can be provided to
content providers or other parties, through secure,
' authenticated encrypted communication to the VDE
installation secure subsystems. Clearinghouse
processing means would normally be connected to
specialized I/O means, which may include high
speed telecommunication switching means that may
be used for secure communications between a
clearinghouse and other VDE pathway participants.
= securely support electronic currency and credit
usage control, storage, and communication at, and
between, VDE installations. VDE further supports
automated passing of electronic currency and/or
credit information, including payment tokens (such
as in the form of electronic currency or credit) or
other payment information, through a pathway of
payment, which said pathway may or may not be the
same as a pathway for content usage information
reporting. Such payment may be placed into a VDE
container created automatically by a VDE
= installation in response to control information
stipulating the "withdrawal" of credit or electronic
currency from an electronic credit or currency
- 109
CA 02479494 2004-10-04
wo 98A09209 rcrnrS97nss43
account based upon an amount owed resulting from
usage of VDE controlled electronic content and/or
appliances. Payment credit or currency may then be
automaticaIIy communicated in protected (at least in
part encrypted) form through telecommunication of
a VDE container to an appropriate party such as a
clearinghouse, provider of original property content
or appliance, or an agent for such provider (other
than a ciearinghouse). Payment information may be
packaged in said VDE content container with, or
without, related content usage information, such as
metering information. An aspect of the present
invention further enables certain information
regarding currency use to be specified as
unavailable to certain, some, or all VDE parties
("conditionally" to fully anonymous currency) and/or
further can regulate certain content information,
such as currency and/or credit use related
information (and/or other electronic information
usage data) to be available only under certain strict
circumstances, such as a court order (which may
itself require authorization through the use of a
court controlled VDE installation that may be
required to securely access "conditionaIly"
- 110 -
CA 02479494 2004-10-04
wo 98/MSe9 rcr/[T07115M
anonymous information). Currency and credit
information, under the preferred embodiment of the
present invention, is treated as administrative
content;
= support fingerprinting (also known as
watermarking) for embedding in content such that
when content protected under the present invention
is released in clear form from a VDE object
(displayed, printed, communicated, extracted, and/or
saved), information representing the identification
of the user and/or VDE installation responsible for
transforming the content into clear form is
embedded into the released content. Fingerprinting
is useful in providing an ability to identify who
extracted information in clear form a VDE
container, or who made a copy of a VDE object or a
portion of its contents. Since the identity of the user
and/or other identifying information may be
embedded in an obscure or generally concealed
manner, in VDE container content and/or control
information, potential copyright violators may be
deterred from unauthorized extraction or copying.
Fingerprinting normally is embedded into
- 13.1-
CA 02479494 2004-10-04
WO MU9Z09 PCT/US97/2St43
unencrypted electronic content or control
information, though it can be embedded into
encrypted content and later placed in unencrypted
content in a secure VDE installation sub-system as
the encrypted content carrying the fingerprinting
information is decrypted. Electronic information,
such as the content of a VDE container, may be
fingerprinted as it leaves a network (such as
Internet) location bound for a receiving party. Such
repository information may be maintained in
unencrypted form prior to communication and be
encrypted as it leaves the repository. Fingerprinting
would preferably take place as the content leaves
the repository, but before the encryption step.
Encrypted repository content can be decrypted, for
example in a secure VDE sub-system, fingerprint
information can be inserted, and then the content
can be re-encrypted for transmission. Embedding
identification information of the intended recipient
user and/or VDE insta.llation into content as it
leaves, for example, an Internet repository, would
provide important information that would identify
or assist in identifying any party that managed to
compromise the security of a VDE installation or the
-112-
CA 02479494 2004-10-04
wo'98JOlno9 rcr/US97115Z43
delivered content. If a party produces an authorized
clear form copy of VDE controlled content, including
= making unauthorized copies of an authorized clear
= form copy, fingerprint information would point back
to that individual and/or his or her VDE
installation. Such hidden information will act as a
strong disincentive that should dissuade a
substantial portion of potential content "pirates"
from stealing other parties electronic information.
Fingerprint information identifying a receiving
party and/or VDE installation can be embedded into
a VDE object before, or during, decryption,
replication, or communication of VDE content
objects to receivers. Fingerprinting electronic
content before it is encrypted for transfer to a
customer or other user provides information that
can be very useful for identifying who received
certain content which may have then been
distributed or made available in unencrypted form.
This information would be useful in tracking who
may have "broken" the security of a VDE
. instaIlation and was iUegally making certain
= electronic content available to others.
Fingerprinting may provide additional, available
-113-
CA 02479494 2004-10-04
WO n/09Z09 PCT/QS97/1SS43
information such as time and/or date of the release
(for example extraction) of said content information.
Locations for inserting fingerprints may be specified
by VDE installation and/or content container control
information. This information may specify that
certain areas and/or precise locations within
properties should be used for fingerprinting, such as
one or more certain fields of information or
information types. Fingerprinting information may
be incorporated into a property by modifying in a
normally undetectable way color frequency and/or
the brightness of certain image pixels, by slightly
modifying certain audio signals as to frequency, by
modifying font character formation, etc.
Fingerprint information, itself, should be encrypted
so as to make it particularly difficult for tampered
fingerprints to be interpreted as valid. Variations in
fingerprint locations for different copies of the same
property; "false" fingerprint information; and
multiple copies of fingerprint information within a
specific property or other content which copies
employ different fingerprinting techniques such as
information distribution patterns, frequency and/or
brightness manipulation, and encryption related
- 114 -
CA 02479494 2004-10-04
wo 98/ozv9 rcrrtS"nsM
techniques, are features of the present invention for
increasing the difficulty of an unauthorized
individual identifying fingerprint locations and
erasing and/or modifying fingerprint information.
~ provide smart object agents that can carry requests,
data, and/or methods, including budgets,
authorizations, credit or currency, and content. For
example, smart objects may travel to and/or from
remote information resource locations and fulfill
requests for electronic information content. Smart
objects can, for example, be transmitted to a remote
location to perform a specified database search on
behalf of a user or otherwise "intelligently" search
.15 remote one or more repositories of information for
user desired information. After identifying desired
information at one or more remote locations, by for
example, performing one or more database searches,
a smart object may return via communication to the
user in the form of a secure "return object"
containing retrieved information. A user may be
charged for the remote retrieving of information, the
' returning of information to the user's VDE
installation, and/or the use of such information. In
-115-
CA 02479494 2004-10-04
wo 9fA9ZO9 rcrRTS97nsW
the latter case, a user may be charged only for the
information in the return object that the user
actually uses. Smart objects may have the means to
request use of one or more services and/or resources.
Services include locating other services and/or
resources such as information resources, language or
format translation, processing, credit (or additional
credit) authorization, etc. Resources include
reference databases, networks, high powered or
specialized computing resources (the smart object
may carry information to another computer to be
efficiently processed and then return the
information to the sending VDE installation),
remote object repositories, etc. Smart objects can
make efficient use of remote resources (e.g.
centralized databases, super computers, etc.) while
providing a secure means for charging users based
on information and/or resources actually used.
= support both "translations" of VDE electronic
agreements elements into modern language printed
agreement elements (such as English language
agreements) and translations of electronic rights
protection/transaction management modern
-116-
CA 02479494 2004-10-04
wo 900os rcrrtMIIBW
language agreement elements to electronic VDE
agreement elements. This feature requires
maintaining a library of textual language that
corresponds to VDE load modules and/or methods
and/or component assemblies. As VDE methods are
proposed andlor employed for VDE agreements, a
listing of textual terms and conditions can be
produced by a VDE user application which, in a
preferred embodiment, provides phrases, sentences
and/or paragraphs that have been stored and
correspond to said methods and/or assemblies. This
feature preferably employs artificial intelligence
capabilities to analyze and automatically determine,
and/or assist one or more users to determine, the
proper order and relationship between the library
elements corresponding to the chosen methods
andlor assemblies so as to compose some or all
portions of a legal or descriptive document. One or
more users, and/or preferably an attorney (if the
document a legal, binding agreement), would review
the generated document material upon completion
and employ such additional textual information
= and/or editing as necessary to describe non
electronic transaction elements of the agreement
- 117 -
CA 02479494 2004-10-04
wossMos PMmS"M%43
and make any other improvements that may be
necessary. These features further support
employing modern language tools that allow one or
more users to make selections from choices and
provide answers to questions and to produce a VDE
electronic agreement from such a process. This
process can be interactive and the VDE agreement
formulation process may employ artificial
intelligence expert system technology that learns
from responses and, where appropriate and based at
least in part on said responses, provides further
choices and/or questions which "evolves" the desired
VDE electronic agreement.
= support the use of multiple VDE secure subsystems
in a single VDE installation. Various security
and/or performance advantages may be realized by
employing a distributed VDE design within a single
VDE installation. For example, designing a
hardware based VDE secure subsystem into an
electronic appliance VDE display device, and
designing said subsystem's integration with said
display device so that it is as close as possible to the
point of display, will increase the security for video
-118-
CA 02479494 2004-10-04
wo 981842o9 rcTnrS97/15W
materials by making it materially more difficult to
"steal" decrypted video information as it moves from
outside to inside the. video system. Ideally, for
example, a VDE secure hardware module would be
in the same physical package as the actual display
monitor, such as within the packaging of a video
monitor or other display device, and such device
would be designed, to the extent commercially
practical, to be as tamper resistant as reasonable.
As another example, embedding a VDE hardware
module into an I/0 peripheral may have certain
advantages from the standpoint of overall system
throughput. If multiple VDE instances are
employed within the same VDE installation, these
instances will ideally share resources to the extent
practical, such as VDE instances storing certain
control information and content and/or appliance
usage information on the same mass storage device
and in the same VDE management database.
= requiring reporting and payment compliance by
. employing exhaustion of budgets and time ageing of
- keys. For example, a VDE commercial arrangement
and associated content control information may
-119-
CA 02479494 2004-10-04
wo MIzo9 rCT/US97nsW
involve a content provider's content and the use of
clearinghouse credit for payment for end-user usage
of said content. Control information regarding said
arrangement may be delivered to a user's (of said
content) VDE installation and/or said financial
clearinghouse's VDE installation. Said control
information might require said clearinghouse to
prepare and telecommunicate to said content
provider both content usage based information in a
certain form. and content usage payment in the form
of electronic credit (such credit might be "owned" by
the provider after receipt and used in lieu of the
availability or adequacy of electronic currency)
and/or electronic currency. This delivery of
information and payment mav employ trusted VDE
installation secure subsvstems to securely, and in
some embodiments, automatically, provide in the
manner specified by said control information, said
usage information and payment content. Features
of the present invention help ensure that a
requirement that a clearinghouse report such usage
information and payment content will be observed.
For example, if one participant to a VDE electronic
agreement fails to observe such information
- 120 -
CA 02479494 2004-10-04
Wo 96Al309 PCiYUS97115M
reporting and/or paying obligation, another
participant can stop the delinquent party from
successfuUy participating in VDE activities related
= to such agreement. For example, if required usage
information and payment was not reported as
specified by content control information, the
"injured" party can fail to provide, through failing to
securely communicate from his VDE installation
secure subsystem, one or more pieces of secure
information necessary for the continuance of one or
more critical processes. For example, failure to
report information and/or payment from a
clearinghouse to a content provider (as well as any
security failures or other disturbing irregularities)
can result in the content provider not providing key
and/or budget refresh information to the
clearinghouse, which information can be necessary
to authorize use of the clearinghouse's credit for
usage of the provider's content and which the
clearinghouse would communicate to end-user's
during a content usage reporting communication
= between the clearinghouse and end-user. As
another example, a distributor that failed to make
payments and/or report usage information to a
-121-
CA 02479494 2004-10-04
NM ygpgZpg pCT/U9971i3?A3
content provider might find that their budget for
creating permissions records to distribute the
content provider's content to users, and/or a secnrity
budget limiting one or more other aspect of their use
~ of the provider's content, are not being refreshed by
the content provider, once exhausted or timed-out
(for example, at a predetermined date). In these and
other cases, the offended party might decide not to
refresh time ageing keys that had "aged out." Such
a use of time aged keys has a similar impact as
failing to refresh budgets or time-aged
authorizations.
= support smart card implementations of the present
invention in the form of portable electronic
appliances, including cards that can be employed as
secure credit, banking, and/or money cards. A
feature of the present invention is the use of
portable VDEs as transaction cards at retail and
other establishments, wherein such cards can "dock"
with an establishment terminal that has a VDE
secure sub-system and/or an online connection to a
VDE secure and/or otherwise secure and compatible
subsystem, such as a "trusted" financial
-122-
CA 02479494 2004-10-04
wo WOM PCT/US97/15Z4.3
clearinghouse (e.g., VTSA,lriastercard). The VDE
card and the terminal (and/or online connection) can
securely exchange information related to a
transaction, with credit and/or electronic currency
being transferred to a merchant and/or
clearinghouse and transaction information flowing
back to the card. Such a card can be used for
transaction activities of all sorts. A docking station,
such as a PCMCIA connector on an electronic
appliance, such as a personal computer, can receive
a consumer's VDE card at home. Such a
station/card combination can be used for on-line
transactions in the same manner as a VDE
installation that is permanentl}= installed in such an
electronic appliance. The card can be used as an
"electronic wallet" and contain electronic currency as
well as credit provided by a clearinghouse. The card
can act as a convergence point for financial activities
of a consumer regarding many, if not all, merchant,
banking, and on-line financial transactions,
including supporting home banking activities. A
= consumer can receive his paycheck and/or
investment earnings and/or "authentic" VDE content
container secured detailed information on such
- 123 -
CA 02479494 2004-10-04
wo MA09m9 rCC/[rs97/162a3
receipts, through on-line connections. A user can
send digital currency to another party with a VDE
arrangement, including giving away such currency.
A VDE card can retain details of transactions in a
highly secure and database organized fashion so
that financially related information is both
consolidated and very easily retrieved and/or
analyzed. Because of the VDE security, including
use of effective encryption, authentication, digital
signaturing, and secure database structures, the
records contained within a VDE card arrangernent
may be accepted as valid transaction records for
government and/or corporate recordkeeping
requirements. In some embodiments of the present
invention a VDE card may employ docking station
and/or electronic appliance storage means and/or
share other VDE arrangement means local to said
appliance and/or available across a network, to
augment the information storage capacity of the
VDE card, by for example, storing dated, and/or
archived, backup information. Taxes relating to
some or all of an individual's financial activities may
be automatically computed based on "authentic"
information securely stored and available to said
-124-
CA 02479494 2004-10-04
WO 9W9ZO9 rC-rnJ897115M
VDE card. Said information may be stored in said
card, in said docking station, in an associated
electronic appliance, and/or other device operatively
attached thereto, and/or remotely, such as at a
remote server site. A card's data, e.g. transaction
history, can be backed up to an individual's personal
computer or other electronic appliance and such an
appliance may have an integrated VDE installation
of its own. A current traasaction, recent
transactions (for redundancy), or all or other
selected card data may be backed up to a remote
backup repository, such a VDE compatible
repository at a financial clearinghouse, during each
or periodic docking for a financial transaction and/or
information communication such as a user/merchant
transaction. Backing up at least the current
transaction during a connection with another party's
VDE installation (for example a VDE installation
that is also on a financial or general purpose
electronic network), by posting transaction
= information to a remote clearinghouse and/or bank,
can ensure that sufficient backup is conducted to
enable complete reconstruction of VDE card internal
information in the event of a card failure or loss.
- 125 -
CA 02479494 2004-10-04
wo Mno9 rcT/Us"nsvo
= support certification processes that ensure
authorized interoperability between various VDE
installations so as to prevent VDE arrangements
and/or instaUations that unacceptably deviate in
specification protocols from other VDE
arrangements and/or installations from
interoperating in a manner that may introduce
security (integrity and/or confidentiality of VDE
secured information), process control, and/or
software compatibility problems. Certification
validates the identity of VDE installations and/or
their components, as well as VDE users.
Certification data can also serve as information that
contributes to determining the decommissioning or
other change related to VDE sites.
= support the separation of fundamental transaction
control processes through the use of event
(triggered) based method control mechanisms.
These event methods trigger one or more other VDE
methods (which are available to a secure VDE
sub-system) and are used to carry out VDE managed
transaction related processing. These triggered
methods include independently (separably) and
- 126 -
-.-._....~...-
CA 02479494 2004-10-04
WO 9"9209 PCT/U897/16243
securely processable component billing management
methods, budgeting management methods, metering
= management methods, and related auditing
management processes. As a result of this feature of
the present invention, independent triggering of
metering, auditing, billing, and budgeting methods,
the present invention is able to efficiently,
concurrently support multiple financial currencies
(e.g. dollars, marks, yen) and content related
budgets, and/or billing increments as well as very
flexible content distribution models.
= support, complete, modular separation of the control
structures related to (1) content event triggering, (2)
auditing, (3) budgeting tincluding specifying no right
of use or unlimited right of use), (4) billing, and (5)
user identity (VDE installation, client name,
department, network, and/or user, etc.). The
independence of these VDE control structures
provides a flexible system which allows plural
relationships between two or more of these
structures, for example, the ability to associate a
financial budget with different event trigger
structures (that are put in place to enable
-127-
CA 02479494 2004-10-04
wo 9&"M rcrAM7115M
controlling content based on its logical portions).
Without such separation between these basic VDE
capabilities, it would be more diff cult to efficiently
maintain separate metering, budgeting,
identification, and/or biIling activities which involve
the same, differing (including overlapping), or
entirely different, portions of content for metering,
billing, budgeting, and user identification, for
example, paying fees associated with usage of
content, performing home banking, managing
advertising services, etc. VDE modular separation
of these basic capabilities supports the programming
of plural, "arbitrary" relationships between one or
differing content portions (andior portion units) and
budgeting, auditing, and/or billing control
information. For example, under VDE, a budget
limit of $200 dollars or 300 German Marks a month
may be enforced for decryption of a certain database
and 2 U.S. Dollars or 3 German Marks may be
charged for each record of said database decrypted
(depending on user selected currency). Such usage
can be metered while an additional audit for user
profile purposes can be prepared recording the
identity of each filed displayed. Additionally,
-128-
CA 02479494 2004-10-04
wo 98N9209 rcr/U897nS?A3
further metering can be conducted regarding the
number of said database bytes that have been
decrypted, and a related security budget may
prevent the decrypting of more than 5% of the total
bytes of said database per year. The user may also,
under VDE (if allowed by senior control
information), collect audit information reflecting
usage of database fields by different individuals and
client organization departments and ensure that
differing rights of access and differing budgets
limiting database usage can be applied to these
client individuals and groups. Enabling content
providers and users to practically employ such
diverse sets of user identification, metering,
budgeting, and billing control information results, in
part, from the use of such independent control
capabilities. As a result, VDE can support great
configurability in creation of plural control models
applied to the same electronic property and the
same and/or plural control models applied to
differing or entirely different content models (for
example, home banking versus electronic shopping).
-129-
CA 02479494 2004-10-04
WO nA9201 PCT/US9"1/1S243
Mothode, Other Control Iaformation, and VDE Objecte
VDE control information (e.g., methods) that collectively
control use of VDE managed properties (database, document,
individual commercial product), are either shipped with the
content itself (for example, in a content container) andJor one or
more portions of such control information is shipped to
distributors and/or other users in separably deliverable
"administrative objects." A subset of the methods for a property
may in part be delivered with each property while one or more
other subsets of methods can be delivered separately to a user or
otherwise made available for use (such as being available
remotely by telecommunication means). Required methods
(methods listed as required for property and/or appliance use)
must be available as specified if VDE controlled content (such as
intellectual property distributed within a VDE content container)
is to be used. Methods that control content may apply to a
plurality of VDE container objects, such as a class or other
grouping of such objects. Methods may also be required by
certain users or classes of users andlor VDE installations and/or
classes of installations for such parties to use one or more
specific, or classes of, objects.
A feature of VDE provided by the present invention is that
certain one or more methods can be specified as required in order
-130-
CA 02479494 2004-10-04
wo 98109Z09 rcrnIJS971161A3
for a VDE installation ancUor user to be able to use certain
andlor all content. For example, a distributor of a certain type of
content might be allowed by "senior" participants (by content
creators, for example) to require a method which prohibits
end-users from electronically saving decrypted content, a
provider of credit for VDE transactions might require an audit
method that records the time of an electronic purchase, and/or a
user might require a method that summarizes usage information
for reporting to a clearinghouse (e.g. biliing information) in a
way that does not convey confidential, personal information
regarding detailed usage behavior.
A further feature of VDE provided bv the present
invention is that creators, distributors, and users of content can
select from among a set of predefined methods (if available) to
control container content usage and distribution functions and/or
they may have the right to provide new customized methods to
control at least certain usage functions (such "new" methods may
be required to be certified for trustedness and interoperability to
the VDE installation and/or for of a group of VDE applications).
As a result, VDE provides a very high degree of configurability
with respect to how the distribution and other usage of each
property or object (or one or more portions of objects or properties
as desired and/or applicable) wiA be controlled. Each VDE
- 131-
CA 02479494 2004-10-04
WO l81D92A9 PLTtUS97J1S243
participant in a VDE pathway of content control information
may set methods for some or all of the content in a VDE
container, so long as such control information does not conflict
with senior control information already in place with respect to:
(1) certain or all VDE managed content,
(2) certain one or more VDE users andlor groupings of
users,
(3) certain one or more VDE nodes and/or groupings of
nodes, and/or
(4) certain one or more VDE applications andJor
arrangements.
For example, a content creator's VDE control information
for certain content can take precedence over other submitted
VDE participant control information and, for example, if allowed
by senior control information, a content distributor's control
information may itself take precedence over a client
administrator's control information, which may take precedence
over an end-user's control information. A path of distribution
participant's ability to set such electronic content control
-132-
CA 02479494 2004-10-04
wO 961i09Zn9 rCTrt1s99n5W
information can be limited to certain control information (for
ezample, method mediating data such as pricing and/or sales
' dates) or it may be limited only to the extent that one or more of
the participant's proposed control information conflicts with
control information set by senior control information submitted
previously by participants in a chain of handling of the property,
or managed in said participant's VDE secure subsystem.
VDE control information may, in part or in full, (a)
represent control information directly put in place by VDE
content control information pathway participants, and/or (b)
comprise control information put in place by such a participant
on behalf of a party who does not directly handle electronic
content (or electronic appliance) permissions records information
(for example control information inserted by a participant on
behalf of a financial clearinghouse or government agency). Such
control information methods (and/or load modules and/or
mediating data and/or component assemblies) may also be put in
place by either an electronic automated, or a semi-automated
and human assisted, control information (control set) negotiating
process that assesses whether the use of one or more pieces of
submitted control information wiill be integrated into and/or
replace existing control information (and/or chooses between
alternative control information based upon interaction with
-133-
CA 02479494 2004-10-04
Wo l94olsa9 rct'nJS97115M
in-place control information) and how such control information
may be used.
Control information may be provided by a party who does
not directly participate in the handling of electronic content
(and/or appliance) and/or control information for such content
(and/or appliance). Such control information may be provided in
secure form using VDE instaIlation secure sub-system managed
communications (including, for example, authenticating the
deliverer of at least in part encrypted control information)
between such not directly participating one or more parties' VI?E
installation secure subsystems, and a pathway of VDE content
control information participant's VDE installation secure
subsystem. This control information may relate to, for example,
the right to access credit supplied by a financial services
provider, the enforcement of regulations or laws enacted by a
government agency, or the requirements of a customer of VDE
managed content usage information (reflecting usage of content
by one or more parties other than such customer) relating to the
creation, handling and/or manner of reporting of usage
information received by such customer. Such control information
may, for example, enforce societal requirements such as laws
related to electronic commerce.
-134-
CA 02479494 2004-10-04
wo 9949M rcri[WnsW
VDE content control information may apply differently to
different pathway of content and/or control information haadling
participants. Furthermore, permissions records rights may be
added, altered, and/or removed by a VDE participant if they are
allowed to take such action. Rights of VDE participants may be
defined in relation to specific parties andlor categories of parties
and/or other groups of parties in a chain of handling of content
and/or content control information (e.g., permissions records).
Modifications to control information that may be made by a
given, eligible party or parties, may be limited in the number of
modifications, and/or degree of modification, they may make.
At least one secure subsystem in electronic appliances of
creators, distributors, auditors, clearinghouses, client
administrators, and end-users (understanding that two or more
of the above classifications may describe a single user) provides a
"sufficiently" secure (for the intended applications) environment
for:
1. Decrypting properties and control information;
= 2. Storing control and metering related information;
3. Managing communications;
-135-
CA 02479494 2004-10-04
wo MIso9 rcr/vM7nsW
4. Processing core control programs, along with
associated data, that constitute control information
for electronic content and/or appliance rights
protection, including the enforcing of preferences
and requirements of VDE participants.
Normally, most usage, audit, reporting, payment, and
distribution control methods are themselves at least in part
encrypted and are executed by the secure subsystem of a VDE
installation. Thus, for example, billing and metering records can
be securely generated and updated, and encryption and
decryption keys are securely utilized, within a secure subsystem.
Since VDE also employs secure (e.g. encrypted and
authenticated) communications when passing information
between the participant location (nodes) secure subsystems of a
VDE arrangement, important components of a VDE electronic
agreement can be reliably enforced with sufficient security
(sufficiently trusted) for the intended commercial purposes. A
VDE electronic agreement for a value chain can be composed, at
least in part, of one or more subagreements between one or more
subsets of the value chain participants. These subagreements
are comprised of one or more electronic contract "compliance"
elements (methods including associated parameter data) that
ensure the protection of the rights of VDE participants.
-136-
CA 02479494 2004-10-04
WO 9fAS9209 P'Cr/US97/1s?A3
The degree of trustedness of a VDE arrangement will be
primarily based on whether hardware SPUs are employed at
participant location secure subsystems and the effectiveness of
the SPU hardware security architecture, software security
techniques when an SPU is emulated in software, and the
encryption algorithm(s) and keys that are employed for securing
content, control information, communications, and access to VDE
node (VDE install ation) secure subsystems. Physical facility and
user ideritity authentication security procedures may be used
instead ofhardware SPUs at certain nodes, such as at an
established financial ciearinghouse, where such procedures may
provide sufficient security for trusted interoperability with a
VDE arrangement employing hardware SPUs at user nodes.
The updatizig of property management files at each
location of a VDE arrangement, to accommodate new or modified
control information, is performed in the VDE secure subsystem
and under the control of secure management file updating
programs executed by the protected subsystem. Since all secure
communications are at least in part encrypted and the
processing inside the secure subsystem is concealed from outside
observation and interference, the present invention ensures that
content control information can be enforced. As a result, the
creator and/or distributor and/or client adaainistrator and/or
-137-
CA 02479494 2004-10-04
wo 9I072@9 rcrrtJS97n6243
other contributor of secure control iaformation for each property
(for example, an end-user restricting the kind of audit
information he or she will allow to be reported and/or a financial
clearinghouse establishing certain criteria for use of its credit for
payment for use of distributed content) can be confident that
their contributed and accepted control information will be
enforced (within the security limitations of a given VDE security
implementation design). This control information can determine,
for example:
(1) How and/or to whom electronic content can be
provided, for example, how an electronic property
can be distributed;
(2) How one or more objects and/or properties, or
portions of an object or property, can be directly
used, such as decrypted, displayed, printed, etc;
(3) How payment for usage of such content and/or
content portions may or must be handled; and
(4) How audit information about usage information
related to at least a portion of a property should be
collected, reported, and/or used.
- 138 -
CA 02479494 2004-10-04
wo 9&4)9ZO9 rCrAYS97nS243
Seniority of contributed control 'information, including
resolution of conflicts between content control information
submitted by multiple parties, is normally established by:
(1) the sequence in which control information is put in
place by various parties (in place control information
normally takes precedence over subsequently
submitted control information),
(2) the specifics of VDE content and/or appliance control
inforination. For example, in-place control
information can stipulate which subsequent one or
more piece of control from one or more parties or
class of parties will take precedence over control
information submitted by one or more yet different
parties and/or classes of parties, and/or
(3) negotiation between control information sets from
plural parties, which negotiation establishes what
control information shall constitute the resulting
control information set for a given piece of VDE
managed content and/or VDE installation.
- 139 -
CA 02479494 2004-10-04
w0 9MM PCT/US!P7nSW
Electronic Agreemeats and Righte Protection
An important feature of VDE is that it can be used to
assure the administration of, and adequacy of security and rights
protection for, electronic agreements implemented through the
use of the present invention. Such agreements may involve one
or more of
(I) creators, publishers, and other distributors, of
electronic information,
10.
(2) fuiancial service (e.g. credit) providers,
(3) users of (other than financial service providers)
information arising from content usage such as
content specific demographic information and user
specific descriptive information. Such users may
include market analysts, marketing list compilers
for direct and directed marketing, and government
agencies,
(4) end users of content,
(5) infrastructure service and device providers such as
telecommunication companies and hardware
- 140 -
CA 02479494 2004-10-04
wo M09M PcrnrS97/15?A3
maaufacturers (semiconductor and electronic
appliance and/or other computer system
manufacturers) who receive compensation based
upon the use of their services and/or devices, and
(6) certain parties described by electronic information.
VDE supports commercially secure "extended" value chain
electronic agreements. VDE can be configured to support the
various underlying agreements between parties that comprise
this extended agreement. These agreements can define
important electronic commerce considerations including:
(1) security,
(2) content use control, including electronic distribution,
(3) privacy (regarding, for example, information
concerning parties described by medical, credit, tax,
personal, and/or of other forms of confidential
information),
(4) management of financial processes, and
- 141-
CA 02479494 2004-10-04
Wo MO9so9 PG1'![JM113243
(5) pathways of handling for electronic content, content
andlor appliance control information, electronic
content andlor appliance usage information and
payment and/or credit.
VDE agreements may define the electronic commerce
relationship of two or more parties of a value chain, but such
agreements may, at times, not directly obligate or otherwise
directly involve other VDE value chain participants. For
example, an electronic agreement between a content creator and
a distributor may establish both the price to the distributor for a
creator's content (such as for a property distributed in a VDE
container object) and the number of copies of this object that this
distributor may distribute to end-users over a given period of
time. In a second agreement, a value chain end-user may be
involved in a three party agreement in which the end-user
agrees to certain requirements for using the distributed product
such as accepting distributor charges for content use and
agreeing to observe the copyright rights of the creator. A third
agreement might exist between the distributor and a financial
clearinghouse that allows the distributor to employ the
cleari.nghouse's credit for payment for the product if the end-user
has a separate (fourth) agreement directly with the
clearinghouse extending credit to the end-user. A fifth, evolving
-142-
CA 02479494 2004-10-04
wo M9ZO9 rcrrtrs97nSZ13
agreement may develop between all value chain participants as
content control information passes along its chain of handling.
This evolving agreement can establish the rights of alI parties to
content usage information, including, for example, the nature of
information to be received by each party and the pathway of
handling of content usage information and related procedures. A
sixth agreement in this example, may involve all parties to the
agreement and establishes certain general assumptions, such as
security techniques and degree of trustedness (for example,
commercial integrity of the system may require each VDE
installation secure subsystem to electronically warrant that their
VDE node meets certain interoperability requirements). In the
above example, these six agreements could comprise agreements
of an extended agreement for this commercial value chain
instance.
VDE agreements support evolving ("livine) electronic
agreement arrangements that can be modified by current and/or
new participants through very simple to sophisticated
"negotiations" between newly proposed content control
information interacting with control information already in place
and/or by negotiation between concurrently proposed content
= control information submitted by a plurality of parties. A given
model may be asynchronously and progressively modified over
- 143 -
CA 02479494 2004-10-04
WO 98109109 PCr/0991/1S?43
time in accordance with existing senior rules and such
modification may be applied to all, to classes of, and/or to specific
content, and/or to classes and/or specific users andlor user nodes.
A given piece of content may be subject to different control
information at different times or places of handling, depending
on the evolution of its content control information (and/or on
differing, applicable VDE installation content control
information). The evolution of control information can occur
during the passing along of one or more VDE control information
containing objects, that is control information may be modified at
one or more points along a chain of control information handling,
so long as such modification is allowed. As a result, VDE
managed content may have different control information applied
at both different "locations" in a chain of content handling and at
similar locations in differing chains of the handling of such
content. Such different application of control i.nformatio:l may
also result from content control information specifying that a
certain party or group of parties shall be subject to content
control information that differs from another party or group of
parties. For example, content control information for a given
piece of content may be stipulated as senior information and
therefore not changeable, nzight be put in place by a content
creator and might stipulate that national distributors of a given
piece of their content may be permitted to make 100,000 copies
-144-
CA 02479494 2004-10-04
wo 98migm pcrtis97/isU3
per calendar quarter, so long as such copies are provided to boni
fide end-users, but may pass only a single copy of such content to
a local retailers and the control information limits such a retailer
to making no more than 1,000 copies per month for retail sales to
end-users. In addition, for example, an end-user of such content
might be limited by the same content control iaformation to
m.aldng three copies of such content, one for each of three
different computers he or she uses (one desktop computer at
work, one for a desktop computer at home, and one for a portable
computer).
Electronic agreements supported by the preferred
embodiment of the present invention can vary from very simple
to very elaborate. They can support widely diverse information
management models that provide for electronic information
security, usage administration, and communication and may
support:
(a) secure electronic distribution of information, for
example commercial literary properties,
(b) secure electronic information usage monitoring and
reporting,
- 145 -
CA 02479494 2004-10-04
WO 98In92os rcr/US97nS?A3
(c) secure financial transaction capabilities related to
both electronic information andlor appliance usage
and other electronic credit andlor currency usage
and administration capabilities,
(d) privacy protection for usage information a user does
not wish to release, and
(e) "living" electronic information content dissemination
models that flexibly accommodate:
(1) a breadth of participants,
(2) one or more pathways (chains) for: the
handling of content, content and/or appliance
control information, reporting of content
and/or appliance usage related information,
and/or payment,
(3) supporting an evolution of terms and
conditions incorporated into content control
information, including use of electronic
negotiation capabilities,
-146 -
CA 02479494 2004-10-04
WO 98109Z09 PCT/pel7/iS243
(4) support the combination of multiple pieces of
content to form new content aggregations, and
= (5) multiple concurrent models.
Secuse Processing Units
An important part of VDE provided by the present
invention is the core secure transaction control arrangement,
herein called an SPU (or SPUs), that typically must be present in
each user's computer, other electronic appliance, or network.
SPUs provide a trusted environment for generating decryption
keys, encrypting and decrypting information, managing the
secure communication of keys and other information between
electronic appliances (i.e. between VDE installations and/or
between plural VDE instances within a single VDE installation),
securely accumulating and managing audit trail, reporting, and
budget information in secure and/or non-secure non-volatile
memory, maintaining a secure database of control information
management instructions, and providing a secure environment
for performing certain other control and administrative
functions.
= A hardware SPU (rather than a software emulation)
within a VDE node is necessary if a highly trusted environment
-147-
CA 02479494 2004-10-04
wo 9809! 9 Pcrilrs97/15?43
for performing certa.in VDE activities is required. Such a trusted
environment may be created through the use of certain control
software, one or more tamper resistant hardware modules such
as a semiconductor or semiconductor chipset (including, for
example, a tamper resistant hardware electronic appliance
peripheral device), for use within, andlor operatively connected
to, an electronic appliance. With the present invention, the
trustedness of a hardware SPU can be enhanced by enclosing
some or all of its hardware elements within tamper resistant
packaging and/or by employing other tamper resisting
techniques (e.g. microfusing and/or thin wire detection
techniques). A trusted environment of the present invention
implemented, in part, through the use of tamper resistant
semiconductor design, contains control logic, such as a
microprocessor, that securely executes VDE processes.
A VDE node's hardware SPU is a core component of a VDE
secure subsystem and may employ some or all of an electronic
appliance's primary control logic, such as a microcontroller,
microcomputer or other CPU arrangement. This primary control
logic may be otherwise employed for non VDE purposes such as
the control of some or all of an electronic appliance's non-VDE
functions. When operating in a hardware SPU mode, said
primary control logic must be sufficiently secure so as to protect
- 148 -
CA 02479494 2004-10-04
wogoinm PCT/US97ASM
and conceal important VDE processes. For example, a hardware
SPU may employ a host electronic appliance microcomputer
operating in protected mode while performing VDE related
. activities, thus allowing portions of VDE processes to execute
with a certain degree of security. This alternate embodiment is
in contrast to the preferred embodiment wherein a trusted
environment is created using a combination of one or more
tamper resistant semiconductors that are not part of said
primary control logic. In either embodiment, certain control
information (software and parameter data) must be securely
maintained within the SPU, and further control information can
be stored externally and securely (e.g. in encrypted and tagged
form) and loaded into said hardware SPU when needed. In
many cases, and in particular with microcomputers, the
preferred embodirnent approach of employing special purpose
secure hardware for executing said VDE processes, rather than
using said primary control logic, may be more secure and
efficient. The level of security and tamper resistance required
for trusted SPU hardware processes depends on the commercial
requirements of particular markets or market niches, and may
vary widely.
-149-
CA 02480118 2006-08-22
In accordance with a first aspect of the invention,
there is provided a method for installing a software
program on a computer system, the method including the
steps of:
(a) receiving installation programming including a
first portion and a second portion, the second portion of
the installation programming being encrypted or otherwise
protected;
(b) receiving operational programming, the
operational programming being encrypted or otherwise
protected;
(c) executing programming contained in the first
portion of the installation programming, the programming
contained in the first portion of the installation
programming being operable to initiate communication with
a remote site, the remote site providing information for
enabling execution of the programming contained in the
second portion of the installation programming; and
(d) executing programming contained in the second
portion of the installation programming, wherein
execution of the programming contained in the second
portion of the installation programming is operable to
install the operational programming on the computer
system.
149a
CA 02479494 2004-10-04
Wo 9BFD9Z09 Pc-r/Iis97/02a3
BB.IEP' DBSCBIPTION OF TSB DRAWINQB
These aad other featvres and advantages provided by the
present invention(s) may be better and more completely
understood by referring to the following detailed description of
presently preferred example embodiments in connection with the
drawings, of which:
FIGURE 1 iUustrates an example of a "Virtual
Distribution Environment" provided in accordance with a
preferred ezample/embodiment of this invention;
FIGURE lA is a more detailed illustration of an example
of the "Information Utility" shown in FIGURE 1; '
FIGURE 2 illustrates an example of a chain of handling
and control;
FIGURE 2A illustrates one example of how rules and
control information may persist from one participant to another
in the Figure 2 chain of handling and control;
FIGURE 3 shows one example of different control
information that may be provided;
-150-
CA 02479494 2004-10-04
wo MOM rcrnT07ns243
FIGURE 4 illustrates exampies of some different types of
rules andlor control informatioa;
FIGURES 5A and 58 show an example of an "object";
FIGURE 6 shows an example of a Secure Processing Unit
("SPtJ");
FIGURE 7 shows an example of an electronic appliance;
FIGURE 8 is a more detailed block diagram of an example
of the electronic appliance shown in FIGURE 7;
FIGURE 9 is a detailed view of an example of the Secure
Processing Unit (SPU) shown in FIGURES 6 and 8;
Figure 9A shows an example combined secure processing
unit and control processing unit;
Figure 9B shows an example secure processing unit
integrated with a standard CPU;
-151-
CA 02479494 2004-10-04
WO 98109?A9 PC!'/US97/1S?d3
FIGLTRE 10 shows an example of a"Rights Operating
System" ("ROS") architecture provided by the Virtual
Distribution Environment;
FIGURES 11A-11C show examples of functional
relationship(s) between applications and the Rights Operating
System;
FIGURES 11D-11J show examples of "components" and
"component assemblies";
FIGURE 12 is a more detailed diagram of an example of
the Rights Operating System shown in FIGURE 10;
FIGURE 12A shows an example of how "objects" can be
created;
FIGURE 13 is a detailed block diagram of an example the
software architecture for a "protected processing environment"
shown in FIGURE 12;
FIGURES 14A-14C are examples of SPU memory maps
provided by the protected processing environment shown in
FIGURE 13;
- 152 -
CA 02479494 2004-10-04
wo 9M92o9 rcrnr897l1S'i43
FIGtJR,E 15 i]lustrates an example of how the chaaael
services manager and load module execution manager of
FIGURE 13 can support a channel;
FIGURE 15A is an example of a channel header and
channel detail records shown in. FIGURE 15;
FIGURE 15B is a flowchart of an example of program
control steps that may be performed by the FIGURE 13 protected
processing environment to create a channel;
FIGLTRE 16 is a block diagram of an example of a secure
data base structure;
FIGURE 17 is an illustration of an example of a logical
object structure;
FIGLTRE 18 shows an example of a stationary object
structure;
FIGURE 19 shows an example of a traveling object
' structure;
-153-
CA 02479494 2004-10-04
wo 991"no9 PcrrUS971151A3
FIGURE 20 shows an example of a content object
structure;
FIGURE 21 shows an example of an administrative object
structure;
FIGURE 22 shows an example of a method core structure;
FIGURE 23 shows an example of a load module structure;
FIGURE 24 shows an example of a User Data Element
(UDE) and/or Method Data Element (MDE) structure;
FIGURES 25A-25C show examples of "map meters";
FIGURE 26 shows an example of a permissions record
(PERC) structure;
FIGURES 26A and 26B together show a more detailed
example of a permissions record structure;
FIGURE 27 shows an example of a shipping table
structure;
- 154 -
CA 02479494 2004-10-04
wo 99+09ZO9 rcTrtJ89711SW
FIGURE 28 shows an example of a receiving table
structure;
= FIGURE 29 shows an example of an admiaistrative event
log structure;
FIGURE 30 shows an example inter-relationship between
and use of the object registration table, subject table and user
rights table shown in the FIGURE 16 secure database;
FIGURE 31 is a more detailed example of an object
registration table shown in FIGURE 16;
FIGUR.E 32 is a more detailed example of subject table
shown in FIGURE 16;
FIGURE 33 is a more detailed example of a user rights
table shown in FIGURE 16;
FIGURE 34 shows a specific example of how a site record
table and group record table may track portions of the secure
= database shown in FIGURE 16;
- 155 -
CA 02479494 2004-10-04
Wo 9&49zo9 rcNUO7115M
FIGITB.E 34A is an example of a FIGURE 34 site rec:ord
table stracture;
FIGURE 34B is an example of a FIGURE 34 group record
table structure;
FIGURE 35 shows an example of a process for updating
the secure database;
FIGURE 36 shows an example of how new elements may
be inserted into the FIGLTRE 16 secure data base;
FIGURE 37 shows an example of how an element of the
secure database may be accessed;
FIGURE 38 is a flowchart example of how to protect a
secure database element;
FIGITRE 39 is a flowchart example of how to back up a
secure database;
FIGURE 40 is a flowchart example of how to recover a
secure database from a backup;
-156-
CA 02479494 2004-10-04
Wo 9 /e9209 Pcr/U997119243
FIGURES 41A-41T') are a set of examples showing how a
"chsin of handling and control" may be enabled using "reciprocal
methods";
FIGURES 42A-42D show an exanlple of a"reciprocal"
BUDGET method;
FIGURES 43A-43D show an example of a"reciprocaP'
REGISTER method;
FIGIJRES 44A-44C show an example of a "reciprocal"
AUDIT method;
FIGLTRES 45-48 show examples of several methods being
used together to control release of content or other information;
FIGURES 49, 49A-49F show an example OPEN method;
FIGURES 50, 50A-50F show an example of a READ
method;
' FIGURES 51, 51A-51F show an example of a WRITE
method;
- 157 -
CA 02479494 2004-10-04
WO "/04?A9 Pcr/US9TnSW
FIGURE 52 shows an example of a CLOSE method;
FIGU'RES 53A-53B show an example of an EVENT
method;
FIGITRE 53C shows an example of a BILLING method;
FIGURE 54 shows an example of an ACCESS method;
FIGURES 55A-55B show examples of DECRYPT and
ENCRYPT methods:
FIGURE 56 shows an example of a CONTENT method;
FIGURES 57A and 57B show examples of EXTRACT and
EMBED methods;
FIGURE 58A shows an example of an OBSCURE method;
FIGURES 58B, 58C show examples of a FINGERPRINT
method;
FIGtTRE 59 shows an example of a DESTROY method;
-158-
CA 02479494 2004-10-04
wo "109so9 rcTnS97n3M
FIGURE 60 shows an example of a PANIC method;
FIGURE 61 shows an example of a METER method;
FIGURE 62 shows an example of a key "convolution"
process;
FIGURE 63 shows an example of how different keys may
be generated using a key convolution process to determine a
"true" key;
FIGURES 64 and 65 show an example of how protected
processing environment keys may be initialized;
FIGURES 66 and 67 show example processes for
decrypting information contained within stationary and
traveling objects, respectively;
Figures 67A and 67B show example techniques for
cracking a software-based protected processing environment;
FIGURE 68 shows an example of how a protected
processing environment may be initialized;
- 159 -
CA 02479494 2004-10-04
WO 98/09m9 PCPN9971LS243
FIGURE 69 shows an example of how firmware may be
downloaded into a protected processing environment;
Figure 69A shows an example technique for distributing
protected processing environment software;
Figure 69B-69C show an example i.nstallation routine for
installing a software-based protected processing environment;
Figure 69D shows example techniques for embedding
cryptographic keys at random locations within structure-based
protected processing environment operational materials;
Figure 69E shows example locations for PPE operational
materials random modifications and/or digital fingerprints;
Figure 69F shows an example customized static storage
layout for PPE operational materials;
Figure 69G shows example electronic appliance signature
locations;
Figure 69H shows example sequence dependent and
independent processes;
-160
CA 02479494 2004-10-04
wo9999o9 rcrlusrnsw
Figures 691 and 69J show example static code and data
storage organizations;
. Figures 69K-69L together show ezample steps for
providing dynamic protection mechanisms;
Figure 69M shows an example initialization time check
routine;
Figure 69N shows an example time check routine;
Figure 690 shows example time check data structures;
FIGUR.E 70 shows an example of multiple VDE electronic
appliances connected together with a network or other
communications means;
Figure 70A shows how content may be prepared for
printing and encrypted inside a PPE, then decrypted inside a
printer;
Figure 70B shows how characters may be selected from
slightly different fonts in order to place an electronic fingerprint
or watermark into printed output;
- 161 -
CA 02479494 2004-10-04
wo 98p:rZQ9 rcr/UWJ15W
Figure 70C shows how characters in a font may be
permuted to render a printed page unusable without the
corresponding scrambled font;
FIGURE 71 shows an example of a portable VDE
electronic appliance;
FIGURES 72A-72D show examples of "pop-up* displays
that may be generated by the user notification and exception
interface;
FIGIJR.E 73 shows an example of a "smart object";
FIGURE 74 shows an example of a process using "smart
objects";
FIGURES 75A-75D show examples of data structures used
for electronic negotiation;
FIGURES 75E-75F show example structures relating to an
electronic agreement;
FIGURES 76A-76B show examples of electronic
negotiation processes;
-162-
CA 02479494 2004-10-04
wo 9on9ZA9 rcr/[1897115Z43
FIGURE 77 shows a further example of a chain of
bandling and control;
FIGURE 78 shows an example of a VDE "repository";
FIGUR,ES 79-83 show an example illustrating a chain of
handling and control to evolve and transform VDE managed
content and control information;
FIGLTRE 84 shows a further example of a chain of
handiing and control involving several categories of VDE
participants;
FIGURE 85 shows a further example of a chain of
distribution and handling within an organization;
Figures 86 and 86A show a further example of a chain of
handling and control; and
Figure 87 shows an example of a virtual silicon container
model.
MORE DETA= DESCRIPTION
-163-
CA 02479494 2004-10-04
wo ~ rcrnS9711su3
Figures 1-7 and the discussion below provides an overview
of some aspects of features provided by this invention. Following
this overview is a more technical "detail descriptson" of example
embodiments in accordance with the invention.
Overviep
Figure 1 shows a"Virtual Distribution Environmene
("VDE") 100 that may be provided in accordance with this
invention. In Figure 1, an infarma 'on utility v 200 connects to
communications means 202 such as telephone or cable TV lines
for example. Telephone or cable TV lines 202 may be part of an
"electronichiehwav" that carries electronic information from
place to place. Lines 202 connect information utility 200 to other
people such as for example a consumer 208, an office 210, a video
production studio 204, and a publishing house 214. Each of the
people connected to information utility 200 may be called a "VDE
participant" because they can participate in transactions
occurring within the virtual distribution environment 100.
Almost any sort of transaction you can think of can be
supported by virtual distribution environment 100. A few of
many examples of transactions that can be supported by virtual
distribution environment 100 include:
- 164 -
CA 02479494 2004-10-04
wo e&99M rcrIUMnsM
= home banking and electronic payments;
= electronic legal contracts;
= = distribution of "content" such as electronic printed matter,
video, audio, images and computer programs; and
= 5 = secure communication of private information such as
medical records and financial information.
Virtual distribution environment 100 is "virtual" because
it does not require many of the physical "things" that used to be
necessary to protect rights, ensure reliable and predictable
distribution, and ensure proper compensation to content creators
and distributors. For example, in the past, information was
distributed on records or disks that were difficult to copy. In the
past, private or secret content was distributed in sealed
envelopes or locked briefcases delivered by courier. To ensure
appropriate compensation, consumers received goods and
services only after they handed cash over to a seller. Although
information utility 200 may deliver information by transferring
physical "things" such as electronic storage media, the virtual
distribution envirornment 100 facilitates a completely electronic
"chain of handling and control."
VDE Flezibility Supports Transactions
-165-
CA 02479494 2004-10-04
vm9&09Z09 PCTlUS97115M
Information utility 200 flexibly supports many different
kinds of information transactions. Different VDE participants
may define and/or participate in different parts of a transaction
Information utility 200 may assist with delivering information
about a transaction, or it may be one of the transaction
participants.
For example, the video production studio 204 in the upper
right-hand corner of Figure 1 may create videoJtelevision
programs. Video production studio 204 may send these
programs over lines 202, or may use other paths such as satelllite
link 205 and CD ROM delivery service 216. Video production
studio 204 can send the programs directly to consumers 206, 208,
210, or it can send the programs to information utility 200 which
may store and later send them to the consumers, for example.
Consumers 206, 208, 210 are each capable of receiving and
using the programs created by video production studio
204---assuming, that is, that the video production studio or
information utility 200 has arranged for these consumers to have
appropriate "rules and controls" (control information) that give
the consumers rights to use the programs.
Even if a consumer has a copy of a video program, she
cannot watch or copy the program unless she has "rules and
-166-
CA 02479494 2004-10-04
wo M9209 rcrrtJ07n5M
controls" that authorize use of the program. She can use the
program only as permitted by the "rules and controls."
For example, video production studio 204 might release a
half-hour exercise video in the hope that as many viewers as
possible will view it. The video production studio 204 wishes to
receive $2.00 per viewing. Video production studio 204 may,
through information utility 200, make the exercise video
available in "protected" form to all consumers 206, 208, 210.
Video production studio 204 may also provide "rules and
controls" for the video. These "rules and controls" may specify
for example:
(1) any consumer who has good credit of at least $2.00
based on a credit account with independent financial
provider 212 (such as Mastercard or VISA) may v.,atch the
video,
(2) virtual distribution environment 100 will "meter" each
time a consumer watches the video, and report usage to
video production studio 204 from time to time, and
(3) financial provider 212 may electronicaIly collect
payment ($2.00) from the credit account of each consumer
-167-
CA 02479494 2004-10-04
wo 98N92e9 rcTrUS97nsu3
who watches the video, and transfer these payments to the
video production studio 204.
Information utility 200 allows even a smaII video
production studio to market videos to consumers and receive
compensation for its efforts. Moreover, the videos can, with
appropriate payment to the video production studio, be made
available to other video publishers who may add value andlor act
as repackagers or redistributors.
Figure 1 also shows a publishing house 214. Publishing
house 214 may act as a distributor for an author 206. The
publishing house 214 may distribute riQhts to use "content" (such
as computer software, electronic newspapers, the video produced
'16 by publishing house 214, audio, or any other data) to consumers
such as office 210. The use rights may be defined by "rules and
controls" distributed by publishing house 216. Publishing house
216 may distribute these "rules and controls" with the content,
but this is not necessary. Because the content can be used only
by consumers that have the appropriate "rules and controls,"
content and its associated "rules and controls" may be
distributed at different times, in different ways, by different
VDE participants. The ability of VDE to securely distribute and
-168
CA 02479494 2004-10-04
WO 9iB169109 P~.'r/U997/1SZ43
enforce "rnles and controls" separately from the content they
apply to provides great advantages.
Use rights distributed by publishing house 214 may, for
example, permit office 210 to make and distribute copies of the
content to its employees. Office 210 may act as a redistributor by
extending a "chain of handli,ng and control" to its employees.
The office 210 may add or modify "rules and controls" (consistent
with the "rules and controls" it receives from publishing house
214) to provide office-internal control information and
mechanisms. For example, office 210 may set a maximum usage
budget for each individual user and/or group within the office, or
it may permit only specified employees and/or groups to access
certain information.
Figure 1 also shows an information delivery service 216
delivering electronic storage media such as "CD ROM" disks to
consumers 206. Even though the electronic storage media
themselves are not delivered electronically by information utility
200 over iines 202, they are still part of the virtual distribution
environment 100. The electronic storage media may be used to
distribute content, "rules and controls," or other information.
-169-
CA 02479494 2004-10-04
W0 98Al-?A9 rcr/IW7ns7r43
Ezample of What's Inside Information Utitity 200
"Information utility" 200 in Figure 1 can be a collection of
partilcipants that may act as distributors, financial
clearinghouses, and administrators. Figure 1A shows an
example of what may be inside one example of information
utility 200. Information utility participants 200a-200g could
each be an independent organization/business. There can be any
number of each of participants 200a-200g. In this example,
electronic "switch" 200a connects internal parts of information
utility 200 to each other and to outside participants, and may
also connect outside participants to one another.
Information utility 200 may include a "transaction
processor" 200b that processes transactions (to transfer
electronic funds, for example) based on requests from
participants and/or report receiver 200e. It may also include a
"usage analyst" 200c that analyzes reported usage information.
A "report creator" 200d may create reports based on usage for
example, and may provide these reports to outside participants
andlor to participants within information utility 200. A "report
receiver" 200e may receive reports such as usage reports from
content users. A"permissioning agent" 200f may distribute
"rules and controls" granting usage or distribution permissions
based on a profile of a consumer's credit worthiness, for example.
-170-
CA 02479494 2004-10-04
wo 981409M rMos97n00
An administrator 200h may provide information that keeps the
virtual distribution environment 100 operating properly. A
content and message storage 200g may store information for use
by participants within or outside of information utility 200.
Ezample of Distributing Content' Using A Chain of 8aadliag
aad Control'
As explained above, virtual distribution environment 100
can be used to manage almost any sort of transaction. One type
of important transaction that virtual distribution environment
100 may be used to manage is the distribution or communication
of "content" or other important information. Figure 2 more
abstractly shows a "model" of how the Figure 1 rirtual
distribution environment 100 may be used to proN-ide a "chain of
handling and control" for distributing content. Each of the
blocks in Figure 2 may correspond to one or more of the VDE
participants shown in Figure 1.
In the Figure 2 example, a VDE content creator 102
creates "conten ." The content creator 102 may also specify
"rules and controls" for distributing the content. These
' distribution-related "rules and controls" can specify who has
permission to distribute the rights to use content, and how many
users are allowed to use the content.
-171-
CA 02479494 2004-10-04
WO 98A9m9 rcr/US97/2s243
Arrow 104 shows the content creator 102 sending the
"rules and controls" associated with the content to a VDE LWIU
distributor 106 ("distributor") over an electronic highwav 108 (or
by some other path such as an optical disk sent by a delivery
service such as U. S. mail). The content can be distributed over
the same or different path used to send the "rules and controls."
The distributor 106 generates her own "rules and controls " that
relate to uaM of the content. The usage-related "rules and
controls" may, for example, specify what a user can and can't do
with the content and how much it costs to use the content. These
usage-related "rules and controls" must be consistent with the
"rules and controls" specified by content creator 102.
Arrow 110 shows the distributor 106 distributing rights to
use the content by sending the content's "rules and controls" to a
content user 112 such as a consumer. The content user 112 uses
the content in accordance with the usage-related "rules and
controls."
In this Figure 2 example, information relating to content
use is, as shown by arrow 114, reported to afmaUcW
cleari.ngbeuse 116. Based on this "reporting," the financial
clearinghouse 116 may generate a bj,ij, and send it to the content
user 112 over a"rgnorts and pa ents" network 118. Arrow 120
-172-
CA 02479494 2004-10-04
wo 9i61a9]09 rcrnrS97115243
shows the content user 112 providing F,ay,M= for content
usage to the financial clearinghouse 116. Based on the reports
and payments it receives, the financial clearinghouse 116 may
provide reports and/or payments to the distributor 106. The
distributor 106 may, as ahown by arTow 122, provide reports
and/or payments to the content creator 102. The clearinghouse
116 may provide reports and payments directly to the creator
102. Reporting and/or payments may be done differently. For
example, clearinghouse 116 may directly or through an agent,
provide reports and/or payments to each of VDE content creators
102, and rights distributor 106, as well as reports to content user
112.
The distributor 106 and the content creator 102 may be
the same person, or thev may be different people. For example, a
musical performing group may act as both content creator 102
and distributor 106 by creating and distributing its own musical
recordings. As another example, a publishing house may act as a
distributor 106 to distribute rights to use works created by an
author content creator 102. Content creators 102 may use a
distributor 106 to efficiently manage the financial end of content
= distribution.
- 173 -
CA 02479494 2004-10-04
Wo 98A092A9 rcTlU$97/13243
The "financiai clearinghouse" 116 shown in Figure 2 may
also be a'VDE administratar." Financial clearinghouse 116 in its
VDE administrator role sends "administrative" information to
the VDE participants. This administrative information helps to
keep the virtual distribution environment 100 operating
properly. The "VDE administrator" and financial clearinghouse
roles may be performed by different people or companies, and
there can be more than one of each.
More about Rules and Controls'
The virtual distribution environment 100 prevents use of
protected information except as permitted by the "rules and
controls" (control information). For example. the "rules and
controls" shown in Figure 2 may grant specific individuals or
classes of content users 112 "permission" to use certain content.
They may specifv what kinds of content usage are permitted, and
what kinds are not. They may specify how content usage is to be
paid for and how much it costs. As another example, "rules and
controls" may require content usage information to be reported
back to the distributor 106 and/or content creator 102.
Every VDE participant in "chain of handling and control"
is normally subject to "rules and controls." "Rules and controls"
define the respective rights and obligations of each of the various
-174-
CA 02479494 2004-10-04
WO 98A9209 PCTlUS97/iS?A3
VDE participants. "Rules and controls" provide information and
mecbanisms that may establish interdependencies and
relationships between the participants. "Rules and controls" are
, flexible, and permit "virtual distribution environment" 100 to
- 5 support most "traditional" business transactions. For example:
= "Rules and controls" may specify which financial
clearinghouse(s) 116 may process payments,
= "Rules and controls" may specify which participant(s)
receive what kind of usage report, and
= "Rules and controls" may specify that certain information
is revealed to certain participants, and that other
information is kept secret from them.
"Rules and controls" may self limit if and how they may be
changed. Often, "rules and controls" specified by one VDE
participant cannot be changed by another VDE participant. For
example, a content user 112 generally can't change "rules and
controls" specified by a distributor 106 that require the user to
pay for content usage at a certain rate. "Rules and controls" may
"persist" as they pass through a "chain of handling and control,"
and may be "inherited" as they are passed down from one VDE
participant to the next.
- 175 -
CA 02479494 2004-10-04
WU M091A9 PGT/IT897/15143
Depending upon their needs, VDE participants can specify
that their "rules and controls" can be changed under conditions
specified by the same or other "rules and controls." For example, '
"rules and controls" specified by the content creator 102 may
permit the distributor 106 to "mark up" the usage price just as
retail stores "mark up" the wholesale price of goods. Figure 2A
shows an example in which certa.in "rules and controls" persist
unchanged from content creator 102 to content user 112; other
"rules and controls" are modified or deleted by distributor 106;
and still other "rules and controls" are added by the distributor.
"Rules and controls" can be used to protect the content
user's privacy by limiting the information that is reported to
other VDE participants. As one example, "rules and controls"
can cause content usage information to be reported anonymously
without revealing content user identity, or it can reveal only
certain information to certain participants (for example,
information derived from usage) with appropriate permission, if
required. This ability to securely control what information is
revealed and what VDE participant(s) it is revealed to allows the
privacy rights of all VDE participants to be protected.
- 176 -
CA 02479494 2004-10-04
wo M0M YcT/US97nSZ43
Rules and Contents' Can Be Separately Deliv~ued
As mentioned above, virtual distribution environment 100
"associates" content with corresponding "rules and controls," and
. prevents the content from being used or accessed unless a set of
' 5 corresponding "rules and controls" is available. The distributor
106 doesn't need to deliver content to control the content's
distribution. The preferred embodiment can securely protect
content by protecting corresponding, usage enabling "rules and
controls" against unauthorized distribution and use.
In some examples. "rules and controls" may travel with the
content they apply to. Virtual distribution environment 100 also
allows "rules and controls" to be delivered separately from
content. Since no one can use or access protected content
without "permission" from corresponding "rules and controls,"
the distributor 106 can control use of content that has already
been (or will in the future be) delivered. "Rules and controls"
may be delivered over a path different from the one used for
content delivery. "Rules and controls" may also be delivered at
some other time. The content creator 102 might deliver content
to content user 112 over the electronic highway 108, or could
make the content available to anyone on the highway. Content
may be used at the time it is delivered, or it may be stored for
later use or reuse.
-177-
CA 02479494 2004-10-04
WO "1'09Z09 PC.TlIJW7/1SZ43
The virtual distribution environment 100 also allows
payment and reporting means to be delivered separately. For
eYample, the content user 112 may have a virtual "credit card"
that extends aredit (up to a certain limit) to pay for usage of any
content. A"credit transaction" can take place at the user's site
without requiring any "online" connection or further
authorization. This invention can be used to help securely
protect the virtual "credit card" against unauthorized use.
Rules and Contents' Define Processes
Figure 3 shows an example of an overall process based on
"rules and controls." It includes an "events" process 402, a meter
process 404, a billing process 406, and a budget process 408. Not
all of the processes shown in Figure 3 will be used for every set of
"ruies and controls."
The "events process" 402 detects things that happen
("events") and determines which of those "events" need action by
the other "processes." The "events" may include, for example, a
request to use content or generate a usage permission. Some
events may need additional processing, and others may not.
Whether an "event" needs more processing depends on the "rules
and controls" corresponding to the content. For example, a user
who lacks permission will not have her request satisfied ("No
-178-
CA 02479494 2004-10-04
w0 9SA9M pCrNmnsw
Go"). As another example, each user request to turn to a new
page of an electronic book may be satisfied ("Go"), but it may not
be necessary to meter, bill or budget those requests. A user who
has purchased a copy of a novel may be permitted to open and
read the novel as many times as she wants to without any
further metering, billi.ng or budgeting. In this simple example,
the "event process" 402 may request metering, billing and/or
budgeting processes the first time the user asks to open the
protected novel (so the purchase price can be charged to the
user), and treat all later requests to open the same novel as
"insignificant events." Other content (for example, searching an
electronic telephone directory) may require the user to pay a fee
for each access.
"Meter" process 404 keeps track of events, and may report
usage to distributor 106 and/or other appropriate VDE
participant(s). Figure 4 shows that process 404 can be based on
a number of different factors such as:
(a) type of usage to charge for,
(b) what kind of unit to base charges on,
(c) how much to charge per unit,
-179-
CA 02479494 2004-10-04
wo 9949?A9 rcr/ns97nS213
(d) when to report, and
(e) how to pay.
These factors may be specified by the "rules and controls" that
control the meter process.
Billing process 406 determines how much to charge for
events. It records and reports payment information.
Budget process 4081imits how much content usage is
permitted. For example, budget process 408 may limit the
number of times content may be accessed or copied, or it may
limit the number of pages or other amount of content that can be
used based on, for example, the number of dollars available in a
credit account. Budget process 408 records and reports financial
and other transaction information associated with such limits.
Content may be supplied to the user once these processes
have been successfully performed.
Containers and Objects'
Figure 5A shows how the virtual distribution environment
100, in a preferred embodiment, may package information
elements (content) into a"~~tainer" 302 so the information can't
be accessed except as provided by its "rules and controls."
-180-
CA 02479494 2004-10-04
wo 9919za9 rcrILM"nsus
Normally, the container 302 is glectronic rather than physicel.
Electronic container 302 in one example comprises "digital"
information having a well defined structure. Container 302 and
its contents can be caIIed an "object 300."
The Figure 5A example shows items "with.i.nA and enclosed
by container 302. However, container 302 may "contain" items
without those items actually being stored within the container.
For example, the container 302 may reference items that are
available elsewhere such as in other containers at remote sites.
Container 302 may reference items available at different times
or only during liinited times. Some items may be too large to
store Arithin container 302. Items may, for example, be delivered
to the user in the form of a "live feed" of video at a certain time.
Even then, the container 302 "contains" the live feed (by
reference) in this example.
Container 302 may contain informatign cantent 304 in
electronic (such as "digital") form. Information content 304 could
be the text of a novel, a picture, sound such as a musical
performance or a reading, a movie or other video, computer
= software, or just about any other kind of electronic information
you can think of. Other types of "objects" 300 (such as
-181-
CA 02479494 2004-10-04
w0 lSf09m9 rCr/UM7115Z43
"administrative objects") may contain "administrative" or other
information instead of or in addition to information content 304.
In the Figure 5A example, container 302 may also contain
"rules and controls" in the form of:
(a) a "pr-znisgions record" 808;
(b) "budgg " 308; and
(c) "other methods" 1000.
Figure 5B gives some additional detail about permissions
record 808, budgets 308 and other methods 1000. The
"permissions record" 808 specifies the rights associated with the
object 300 such as. for example, who can open the container 302,
who can use the object's contents, who can distribute the object,
and what other control mechanisms must be active. For
example, permissions record 808 mav specifv a user's rights to
use, distribute andlor administer the container 302 and its
content. Permissions record 808 may also specify requirements
to be applied by the budgets 308 and "other methods" 1000.
Permissions record 808 may also contain security related
information such as scrambling and descrambling "keys."
"Budgets" 308 shown in Figure 5B are a special type of
"method" 1000 that may specify, among other things, limitations
- 182 -
CA 02479494 2004-10-04
wo s9os'o9 PcrnJS9711043
on usage of information content 304, and how usage will be paid
for. Budgets 308 can specify, for example, how much of the total
information content 304 can be used and/or copied. The methods
310 may prevent use of more than the amount specified by a
specific budget.
"Other methods" 1000 define basic operations used by
"rules and controls." Such "methods" 1000 may include, for
example, how usage is to be "metered," if and how content 304
and other information is to be scrambled and descrambled, and
other processes associated with handling and controlli.ng
information content 304. For example, methods 1000 may record
the identity of anyone who opens the electronic container 302,
and can also control how information content is to be charged
based on "metering." Methods 1000 may apply to one or several
different information contents 304 and associated cont~iners
302, as well as to all or specific portions of information content
304.
Secnre Processiag Unit (SPU)
The "VDE participants" may each have an "electronic
= appliance." The appliance may be or contain a computer. The
appliances may communicate over the electronic highway 108.
Figure 6 shows asecure,n-rocessingunit ("SPU") 500 portion of
-183-
CA 02479494 2004-10-04
w0 99U9Z09 PCr/(J39TnS243
the "electronic appliance" used in this example by each VDE
participant. SPU 500 processes information in aWMM&
ptocessing envi m n- 503, and stores important information
securely. SPU 500 may be emulated by software operating in a
host electronic appliance.
SPU 500 is enclosed within and protected by a"Uun=
resistant securiV barrier" 502. Security barrier 502 separates
the secure environment 503 from the rest of the world. It
prevents information and processes within the secure
environment 503 from being observed, interfered with and
leaving except under appropriate secure conditions. Barrier 502
also controls external access to secure resources, processes and
information within SPU 500. In one example, tamper resistant
security barrier 502 is formed by security features such as
"encryption," and hardware that detects tampering and/or
destroys sensitive information within secure environment 503
when tampering is detected.
SPU 500 in this example is an integrated circuit ("IC")
"chip" 504 including "hardware" 506 and "firmware" 508. SPU
500 connects to the rest of the electronic appliance through an
"appliance link" 510. SPU "firmware" 508 in this example is
"software" such as a "computer program(s)" "embedded" within
-184-
CA 02479494 2004-10-04
wo 9lA9se9 rccrt1897115M
chip 504. Firmware 508 makes the hardware 506 work.
Hardware 506 preferably contains a processor to perform
' instructions specified by firmware 508. "Hardware" 506 also
contains long-term and short-term memories to store information
securely so it can't be tampered with. SPU 500 may also have a
protected clocklcalendar used for timing events. The SPU
hardware 506 in this example may include special purpose
electronic circuits that are specially designed to perform certain
processes (such as "encryption" and "decryption") rapidly and
efficiently.
The particular context in which SPU 500 is being used will
determine how much processing capabilities SPU 500 should
have. SPU hardware 506, in this example, provides at least
enough processing capabilities to support the secure parts of
processes shown in Figure 3. In some contexts, the functions of
SPU 500 may be increased so the SPU can perform all the
electronic appliance processing, and can be incorporated into a
general purpose processor. In other contexts, SPU 500 may work
alongside a general purpose processor, and therefore only needs
to have enough processing capabilities to handle secure
processes.
- 185 -
CA 02479494 2004-10-04
wo ninms rcTIUS97115M
VDE Elsctroaic Appliaacs and Righl:s Operatiag 8yatA,m"
Figure 7 shows an example of an electronic appliance 600
including SPU 500. Electronic appliance 600 may be practicaIly
any kind of electrical or electronic device, such as:
= a computer
= a T.V. "set top" control box
= a pager
= a telephone
= a sound system
= a video reproduction system
= a video game player
= a "smart" credit card
Electronic appliance 600 in this example mav include a keyboard
or keypad 612, a voice recognizer 613, and a display 614. A
human user can input commands through kevboard 612 and/or
voice recognizer 613, and may view information on display 614.
Appliance 600 may communicate with the outside world through
any of the connections/devices normally used within an electronic
appliance. The connections/devices shown along the bottom of
the drawing are examples:
a"modem" 618 or other telecommunications link;
a CD ROM disk 620 or other storage medium or device;
-186-
CA 02479494 2004-10-04
WO 9&99Z09 PC'T/US97/15M
a printer 622;
broadcast reception 624;
= a document scanner 626; and
a "cable" 628 connecting the appliance with a "network."
Virtual distribution environment 100 provides a"riZbU
one ratinQgygem" 602 that manages appliance 600 and SPU 500
by controlling their hardware resources. The operating system
602 may also support at least one "application" 608. Generally,
"application" 608 is hardware and/or software specific to the
context of appliance 600. For example, if appliance 600 is a
personal computer, then "application" 608 could be a program
loaded by the user, for instance, a word processor, a
communications system or a sound recorder. If appliance 600 is
a television controller box, then application 608 might be
hardware or software that allows a user to order videos on
demand and perform other functions such as fast forward and
rewind. In this example, operating system 602 provides a
standardized, well defined, generalized "interface" that could
support and work with many different "applications" 608.
Operating system 602 in this example provides "riLrhts and
auditing operating system functions" 604 and "other o ra 'n
system functions" 606. The "rights and auditing operating
- 187 -
CA 02479494 2004-10-04
woWon" pcr/US97n5M
system functions" 604 securely handle tasks that relate to virtual
distribution environment 100. SPU 500 provides or supports
many of the security fanctions of the "rights and auditiag
operating system functions" 402. The "other operating system
functions" 606 handle general appliance functions. Overall
operating system 602 may be designed from the beginning to
include the "rights and auditing operating system functions" 604
plus the "other operating system functions" 606, or the "rights
and auditing operating system functions" may be an add-on to a
preexisting operating system providing the "other operating
system functions."
"Rights operating system" 602 in this example can work
with many different types of appliances 600. For example, it can
work with large mainframe computers, "minicomputers" and
"microcomputers" such as personal computers and portable
computing devices. It can also work in control boxes on the top of
television sets, small portable "pagers," desktop radios, stereo
sound systems, telephones, telephone switches, or any other
electronic appliance. This ability to work on big appliances as
well as little appliances is called "scalable." A "scalable"
operating system 602 means that there can be a standardized
interface across many different appliances performing a wide
variety of tasks.
-188 -
CA 02479494 2004-10-04
Wo lSMo9so9 PCl'ros97n3243
The "rights operating system functions" 604 are "ser-yices-
hased" in this example. For example, "rights operating system
functions" 604 handle summary requests from application 608
rather than requiring the application to always make more
detailed "subrequests" or otherwise get involved with the
underlying complexities involved in satisfying a summary
request. For eYample, application 608 may simply ask to read
specified information; "rights operating system functions" 604
can then decide whether the desired informatian is VDE-
protected content and, if it is, perform processes needed to make
the information available. This feature is called "transparency."
"Transparency" makes tasks easy for the application 608.
"Rights operating system functions" 604 can support applications
608 that "know" nothing about virtual distribution environment
100. Applications 608 that are "aware" of virtual distribution
environment 100 may be able to make more detailed use of
virtual distribution environment 100.
In this example, "rights operating system functions" 604
are "event driven". Rather than repeatedly examining the state
of electronic appliance 600 to determine whether a condition has
= arisen, the "rights operating system functions" 604 may respond
directly to "events" or "happenings" within appliance 600.
- 189 -
CA 02479494 2004-10-04
wo noom rcrrtms97119u3
In this example, some of the services performed by "rights
operating system functions" 604 may be extended based on
additional "components" delivered to operating system 602.
"Rights operating system fvnctions" 604 can collect together and
use "components" sent by different participants at different
times. The "components" help to make the operating system 602
"scalable." Some components can change how services work on
little appliances versus how they work on big appliances (e.g.,
multi-user). Other components are designed to work with
specific applications or classes of applications (e.g., some types of
meters and some types of budgets).
Electronic Appliance 600
An electronic appliance 600 provided by the preferred
embodiment may, for example, be anv electronic apparatus that
contains one or more microprocessors andior microcontrollers
and/or other devices which perform logical andlor mathematical
calculations. This may include computers; computer terminals;
device controllers for use with computers; peripheral devices for
use with computers; digital display devices; televisions; video
and audio/video projection systems; channel selectors and/or
decoders for use with broadcast and/or cable transmissions;
remote control devices; video and/or audio recorders; media
players including compact disc players, videodisc players and
- is0 -
CA 02479494 2004-10-04
wo 98/09M rcrruS"nssu3
tape players; audio and/or video amplifiers; virtual reality
nuachiaes; electronic game players; multimedia players; radios;
telephones; videophones; facsimile macbines; robots; numerically
controlled machines including machine tools and the like; and
= 5 other devices contain.ing one or more microcomputers and/or
microcontrollers and/or other CPUs, including those not yet in
existence.
Figure 8 shows an example of an electronic appliance 600.
This example of electronic appliance 600 includes a system bus
653. In this example, one or more conventional general purpose
central processing units ("CPUs") 654 are connected to bus 653.
Bus 653 connects CPU(s) 654 to RAM 656, ROM 658, and I/0
controller 660. One or more SPUs 500 may also be connected to
system bus 653. System bus 653 may permit SPU(s) 500 to
communicate with CPU(s) 654, and also mav allow bcth the
CPU(s) and the SPU(s) to corrimunicate (e.g., over shared
address and data lines) with RAM 656, ROM 658 and I/0
controller 660. A power supply 659 may provide power to SPU
500, CPU 654 and the other system components shoam.
' In the example shown, I10 controller 660 is connected to
= secondary storage device 652, a keyboard/display 612,614, a
communications controller 666, and a backup storage device 668.
- 191 -
CA 02479494 2004-10-04
wo 9t1G9299 rcrros971154W
Backup storage device 668 may, for example, store iaformation
on mass media such as a tape 670, a floppy disk, a removable
memory card, etc. Communications controller 666 may allow
electronic appliance 600 to communicate with other electronic
appliances via network 672 or other telecommunications links.
Different electronic appliances 600 may interoperate even if they
use different CPUs and different instances of ROS 602, so long
as they typically use compatible communication protocols and/or
security niethods. In this example, I/0 controller 660 permits
CPU 654 and SPU 500 to read firom and write to secondary
storage 662, keyboard/displav 612, 614, communications
controller 666, and backup storage device 668.
Secondary storage 662 may comprise the same one or
more non-secure secondary storage devices (such as a magnetic
disk and a CD-ROM drive as one example) that electronic
appliance 600 uses for general secondary storage functions. In
some implementations, part or all of secondary storage 652 may
comprise a secondary storage device(s) that is physically enclosed
within a secure enclosure. However, since it may not be practical
or cost-effective to physically secure secondary storage 652 in
many implementations, secondary storage 652 may be used to
store information in a secure manner by encrypting information
before storing it in secondary storage 652. If information is
-192-
CA 02479494 2004-10-04
wo sB/oM rcrnJS07115?A3
encrypted before it is stored, physical access to secondary storage
652 or its contents does not readily reveal or compromise the
= information.
Secondary storage 652 in this example stores code and
data used by CPU 654 and/or SPU 500 to control the overall
operation of electronic appliance 600. For ezample, Figure 8
shows that "Rights Operating System" ("ROS") 602 (including a
portion 604 of ROS that provides VDE functions and a portion
606 that provides other OS functions) shown in Figure 7 may be
stored on secondary storage 632. Secondary storage 652 may
also store one or more VDE objects 300. Figure 8 also shows that
the secure files 610 shown in Figure 7 may be stored on
secondary storage 652 in the form of a "secure database" or
management file system 610. This secure database 610 may
store and organize information used by ROS 602 to perform VDE
functions 604. Thus, the code that is executed to perform VDE
and other OS functions 604, 606, and secure files 610 (as well as
VDE objects 300) associated with those functions may be stored
in secondary storage 652. Secondary storage 652 may also store
"other information" 673 such as, for example, information used
= by other operating system functions 606 for task management,
non-VDE files, etc. Portions of the elements indicated in
secondary storage 652 may al-so be stored in ROM 658, so long as
-193-
CA 02479494 2004-10-04
wo 98A)9209 pCT/UW7y5=
those elements do not require changes (except when ROM 658 is
replaced). Portions of ROS 602 in particular may desirably be
included in ROM 658 (e.g., "bootstrap" routines, POST routines,
etc. for use in establishing an operating environment for
electronic appliance 600 when power is applied).
Figure 8 shows that secondary storage 652 may also be
used to store code ("application programs") providing user
application(s) 608 show-n in Figure 7. Figure 8 shows that there
may be two general types of application programs 608: "VDE
aware" applications 608a, and Non-VDE aware applications
608b. VDE aware applications 608a may have been at least in
part designed specifically with VDE 100 in mind to access and
take detailed advantage of VDE functions 604. Because of the
.15 "transparency" features of ROS 602, nonA'DE aware
applications 608b (e.g., applications not specifically designed for
VDE 100) can also access and take advantage of VDE functions
604.
SECURE PROCESSING UNIT 500
Each VDE node or other electronic appliance 600 in the
preferred embodiment may include one or more SPUs 500. SPUs
500 may be used to perform all secure processing for VDE 100.
For example, SPU 500 is used for decrypting (or otherwise
- 194 -
CA 02479494 2004-10-04
WO 98P99Z09 PCTN897/1SM
unsecuring) VDE protected objects 300. It is also used for
managing encrypted andlor otherwise secured communication
(such as by employing authentication and/or error-correction
validation of information). SPU 500 may also perform secure
data management processes including governing usage of,
auditing of, and where appropriate, payment for VDE objects 300
(through the use of prepayments, credits, real-time electronic
debits from bank accounts andlor VDE node currency token
deposit accounts). SPU 500 may perform other transactions
related to such VDE objects 300.
SPU Physical Packaging and Security Barrier 502
As shown Figure 6, in the preferred embodiment, an SPU
500 may be implemented as a single integrated circuit "chip" 505
to provide a secure processing environment in which confidential
and/or commercially valuable information can be safely
processed, encrypted andlor decrypted. IC chip 505 may, for
example, comprise a small semiconductor "die" about the size of a
thumbnail. This semiconductor die may include semiconductor
and metal conductive pathways. These pathways define the
circuitry, and thus the functionality, of SPU 500. Some of these
pathways are electrically connected to the external "pins" 504 of
the chip 505.
-195-
CA 02479494 2004-10-04
w0 990M rcr/Us77/IsW
As shown in Figures 6 and 9, SPU 500 may be surrounded
by a tamper-resistant hardware security barrier 502. Part of this
security barrier 502 is formed by a plastic or other package in
which an SPU "die" is encased. Because the processing occurring
within, and information stored by, SPU 500 are not easily
accessible to the outside worid, they are relatively secure from
unauthorized access and tampering. All signals cross barrier
502 through a secure, controIled path provided by BIU 530 that
restricts the outside world's access to the internal components
within SPU 500. This secure, controlled path resists attempts
from the outside world to access secret information and resources
within SPU 500.
It is possible to remove the plastic package of an IC chip
and gain access to the "die." It is also possible to analyze and
"reverse engineer" the "die" itself (e.g., using various types of
logic analyzers and microprobes to collect and analyze signals on
the die while the circuitry is operating, using acid etching or
other techniques to remove semiconductor layers to expose other
layers, viewing and photographing the die using an electron
microscope, etc.) Although no system or circuit is absolutely
impervious to such attacks, SPU barrier 502 may include
additional hardware protections that make successful attacks
exceedingly costly and time consuming. For example, ion
-196-
CA 02479494 2004-10-04
wo MOM rcrNS97115M
implantation and/or other fabrication techniques may be used to
make it very difficult to visually discern SPU die conductive
pathways, and SPU internal circuitry may be fabricated in such
a way that it "self-destructs" when exposed to air and/or light.
SPU 500 may store secret information in internal memory that
loses its contents when power is lost. Circuitry may be
incorporated withi,n SPU 500 that detects microprobing or other
tampering, and self-destructs (or destroys other parts of the
SPU) when tampering is detected. These and other hardware-
based physical security techniques contribute to tamper-
resistant hardware security barrier 502.
To increase the security of security barrier 502 even
further, it is possible to encase or include SPU 500 in one or
more further physical enclosures such as, for example: epoxy or
other "potting compound"; further module enclosures including
additional self-destruct, self-disabling or other features activated
when tampering is detected; further modules providing
additional security protections such as requiring password or
other authentication to operate; and the like. In addition,
further layers of metal may be added to the die to complicate
acid etching, micro probing, and the like; circuitry designed to
"zeroize" memory may be included as an aspect of self-destruct
processes; the plastic package itself may be designed to resist
-197-
CA 02479494 2004-10-04
WO 98109209 PCT/U997/15243
chemical as well as physical "attacks"; and memories internal to
SPU 500 may have specialized addressing and refresh circuitty
that "shuffles" the location of bits to complicate efforts to
electricaIIy detsrraine the value of memory locations. Z'hese and
other techniques may contribute to the secnrity of barrier 502.
In some electmnic appliances 600, SPU 500 may be
integrated together with the device microcontroller or equivalent
or with a device I/O or communications microcontroller into a
common chip (or chip set) 505. For example, in one preferred
embodiment, SPU 500 may be integrated together with one or
more other CPU(s) (e.g., a CPU 654 of an electronic appliaace) in
a single component or package. The other CPU(s) 654 may be
any centrally controlling logic arrangement, such as for example,
a microprocessor, other microcontroller, and/or array or other
parallel processor. This integrated configuration may result in
lower overall cost, smaller overall size, and potentially faster
interaction between an SPU 500 and a CPU 654. Integration
may also provide wider distribution if an integrated SPU/CPU
component is a standard feature of a widely distributed
microprocessor li.ne. Merging an SPU 500 into a main CPU 654
of an electronic appliance 600 (or into another appliance or
appliance peripheral microcomputer or other microcontroller)
may substantially reduce the overhead cost of implementing
-198-
CA 02479494 2004-10-04
w0 9UM PM/Un7nSW
VDE 100. Integration considerations may include cost of
implementation, cost of manufacture, desired degree of security,
and value of compactness.
SPU 500 may also be integrated with devices other than
CPUs. For example, for video and multimedia applications, some
performance and/or security advantages (depending on overall
design) could result from integrating an SPU 500 into a video
controller chip or chipset. SPU 500 can also be integrated
directly into a network communications chip or chipset or the
like. Certain performance advantages in high speed
communications applications may also result from integrating an
SPU 500 with a modem chip or chipset. This may facilitate
incorporation of an SPU 500 into communication appliances such
as stand-alone fax machines. SPU 500 may also be integrated
into other peripheral devices, such as CD-ROM devices, set-top
cable devices, game devices, and a wide variety of other
electronic appliances that use, allow access to, perform
transactions related to, or consume, distributed information.
SPU 500 Internal Architecture
Figure 9 is a detailed diagram of the internal structure
within an example of SPU 500. SPU 500 in this example
includes a single microprocessor 520 and a limited amount of
-199-
CA 02479494 2004-10-04
wo 98"zo4 rcMrtrMMSM
memory configured as ROM 532 and RAM 534. In more detail,
this example of SPU 500 includes microprocessor 520, an
encrypt/decrypt engine 522, a DMA controller 526, a real-time
clock 528, a bus interface unit ('BIU") 530, a read only memory
(ROM) 532, a random access memory (RAM) 534, and a memory
management unit ("MMU") 540. DMA controller 526 and MMU
540 are optional, but the performance of SPU 500 may suffer if
they are not present. SPU 500 may also include an optional
pattern matching engine 524; an optional random number
generator 542, an optional arithmetic accelerator circuit 544, and
optional compression/decompression circuit 546. A shared
address/data bus arrangement 536 may transfer information
between these various components under control of
microprocessor 520 andfor DMA controller 526. Additional or
alternate dedicated paths 538 may connect microprocessor 520 to
the other components (e.g., encrypt/decrypt engine 522 via line
538a, real-time clock 528 via line 538b, bus interface unit 530 via
line 538c, DMA controller via line 538d, and memory
management unit (MMU) 540 via line 538e).
The following section discusses each of these SPU
components in more detail.
-200-
CA 02479494 2004-10-04
wo WOM rcrIUM71LI443
Mioroprocessor 520
Microprocessor 520 is the "brain" of SPU 500. In this
example, it executes a sequence of steps specified by code stored
. (at least temporarily) within ROM 532 and/or RAM 534.
Microprocessor 520 in the preferred embodiment comprises a
dedicated central processing arrangement (e.g., a RISC and/or
CISC processor unit, a microcontroller, and/or other centraI
processing means or, less desirably in most applications, process
specific dedicated control logic) for executing instructions stored
in the ROM 532 and/or other memory. Microprocessor 520 may
be separate elements of a circuitry layout, or may be separate
packages within a secure SPU 500.
In the preferred embodiment, microprocessor 520 normally
handles the most security sensitive aspects of the operation of
electronic appliance 600. For example, microprocessor 520 may
manage VDE decrypting, encrypting, certain content and/or
appliance usage control information, keeping track of usage of
VDE secured content, and other VDE usage control related
functions.
Stored in each SPU 500 and/or electronic appliance
secondary memory 652 may be, for example, an instance of ROS
602 software, application programs 608, objects 300 containing
-201-
CA 02479494 2004-10-04
wo eAMm9 rcrrtW7n5W
VDE controlled property content and related information, and
management database 610 that stores both information
associated with objects and VDE control information. ROS 602
includes software intended for execution by SPU microprocessor
520 for, in part, controlling usage of VDE related objects 300 by
electronic appliance 600. As will be explained, these SPU
programs include "load modules" for performing basic control
functions. These various programs and associated data are
executed and manipulated primarily by microprocessor 520.
Rea114me Clock (RTC) 528
In the preferred embodiment, SPU 500 includes a real
time clock circuit ("RTC") 528 that serves as a reliable, tamper
resistant time base for the SPU. RTC 528 keeps track of time of
day and date (e.g., month, day and vear) in the preferred
embodiment, and thus may comprise a combination calendar and
clock. A reliable time base is important for implementing time
based usage metering methods, "time aged decryption keys," and
other time based SPU functions.
The RTC 528 must receive power in order to operate.
Optimally, the RTC 528 power source could comprise a small
battery located within SPU 500 or other secure enclosure.
However, the RTC 528 may employ a power source such as an
- 202 -
CA 02479494 2004-10-04
w0 9WOos rcrnrs97n5M
externally located battery that is external to the SPU 500. Such
an externally located battery may provide relatively
uninterrupted power to RTC 528, and may also maintain as
non-volatile at least a portion of the otherwise volatile RAM 534
within SPU 500.
In one implementation, electronic appliance power supply
659 is also used to power SPU 500. Using any external power
supply as the only power source for RTC 528 may significantly
reduce the usefulness of time based security techniques uniess,
at minimum, SPU 500 recognizes any interruption (or any
material interruption) of the supply of extaernal power, records
such interruption, and responds as may be appropriate such as
disabling the ability of the SPU 500 to perform certain or all
VDE processes. Recognizing a power interruption may, for
example, be accomplished by employing a circuit which is
activated by power failure. The power failure sensing circuit
may power another circuit that includes associated logic for
recording one or more power fail events. Capacitor discharge
circuitry may provide the necessary temporary power to operate
this logic. In addition or alternatively, SPU 500 may from time
to time compare an output of RTC 528 to a clock output of a host
electronic appliance 600, if available. In the event a discrepancy
is detected, SPU 500 may respond as appropriate, including
- 203 -
CA 02479494 2004-10-04
WO 96IOZA9 PGTlUS97/1'.S2A.3
recording the discrepancy and/or disabling at least some portion
of processes performed by SPU 500 under at least some
circumrstances.
If a power failure andlor RTC 528 discrepancy and/or other
event indicates the possibility of tampering, SPU 500 may
automatically destroy, or render inaccessible without privileged
intervention, one or more portions of sensitive information it
stores, such as execution related information andJor encryption
key related information. To provide further SPU operation, such
destroyed information would have to be replaced by a VDE
clearinghouse, administrator and/or distributor, as may be
appropriate. This may be achieved by remotely downloading
update and/or replacement data and/or code. In the event of a
disabling andlor destruction of processes and/or information as
described above, the electronic appliance 600 may require a
secure VDE communication with an administrator,
clearinghouse, and/or distributor as appropriate in order to
reinitialize the RTC 528. Some or all secure SPU 500 processes
may not operate until then.
It may be desirable to provide a mechanism for setting
and/or synchronizing RTC 528. In the preferred embodiment,
when communication occurs between VDE electronic appliance
- 204 -
CA 02479494 2004-10-04
wo s0ro9m Pcrnrs97115M
600 and another VDE appliance, an output of RTC 528 may be
compared to a controlled RTC 528 output time under control of
the party authorized to be "senior" and controlling. In the event
of a discrepancy, appropriate action may be taken, including
resetting the RTC 528 of the "junior" controlled participant in
the communication.
SPU Enarypt/Decrypt Eagiae 522
In the preferred embodiment, SPU encrypt(deciypt engine
522 provides special purpose hardware (e.g., a hardware state
machine) for rapidly and efficiently encrypting andlor decrypting
data. In some implementations, the encrypt/decrypt functions
may be performed instead by microprocessor 520 under software
control, but providing special purpose encrypt/decrypt hardware
engine 522 will, in general, provide increased performance.
Microprocessor 520 may, if desired, comprise a combination of
processor circuitry and dedicated encryption/decryption logic
that may be integrated together in the same circuitry layout so
as to, for example, optinnally share one or more circuit elements.
Generally, it is preferable that a computationally effrcient
but highly secure "bulk" encryptionldecryption technique should
be used to protect most of the data and objects handled by SPU
500. It is preferable that an extremely secure
- 205 -
CA 02479494 2004-10-04
WO 9s1e930! PCT/U897/1STA3
encryption/decryption technique be used as an aspect of
authenticating the identity of electronic appliances 600 that are
establishing a communication channel and securing any
transferred permission, method, and administrative information.
In the preferred embodiment, the encrypt/decrypt engine 522
includes both a symmetric key encryption/decryption circuit (e.g.
DES, Skipjack/Clipper, IDEA, RC-2, RC-4, etc.) and an
antisymmetric (asymmetric) or Public Key ('PK")
encryption/decryption circuit. The public/private kev
encryption/decryption circuit is used principally as an aspect of
secure communications between an SPU 500 and VDE
administrators, or other electronic appliances 600, that is
between VDE secure subsystems. A svmmetric
encryption/decryption circuit may be used for bulk" encrypting
.15 and decrvpting most data stored in secondan= storage 662 of
electronic appliance 600 in which SPU 500 resides. The
symmetric key encryption/decryption circuit may also be used for
encrypting and decrypting content stored within VDE objects
300.
DES or public/private key methods may be used for all
encryption functions. In alternate embodiments, encryption and
decryption methods other than the DES and public/private key
methods could be used for the various encryption related
- 206 -
CA 02479494 2004-10-04
wo 994"M rcrrttwnsw
fnnctioas. For instance, other types of symmetric
encryption/decryption techniques in which the same key is used
for encryption and decryption could be used in place of DES
encryption and decryption. The preferred embodiment can
support a plurality of decryption/encryption techniques using
multiple dedicated circuits within encrypt/decrypt engine 522
and/or the processing arrangement within SPU 500.
Pattern Matching Engine 524
Optional pattern matching engine 524 may provide special
purpose hardware for performing pattern matching functions.
One of the functions SPU 500 may perform is to
validate/authenticate VDE objects 300 and other items.
Validation/authentication often involves comparing long data
strings to determine whether they compare in a predetermined
way. In addition, certain forms of usage (such as logical and/or
physical (contiguous) relatedness of accessed elements) may
require searching potentially long strings of data for certain bit
patterns or other significant pattern related metrics. Although
pattern matching can be performed by SPU microprocessor 520
under software control, providing special purpose hardware
pattern matching engine 524 may speed up the pattern matching
process.
- 207 -
CA 02479494 2004-10-04
Wo 9BA9Z 9 rcrn)S971132d3
Compression/Decompresaion Engine 546
An optional compression/decompression engine 546 may be
provided within an SPU 500 to, for example, compress andlor
decompress content stored in, or released from, VDE objects 300.
Compression/decompression engine 546 may implement one or
more compression algorithms using hardware circuitry to
improve the performance of compression/decompression
operations that would otherwise be performed by software
operating on microprocessor 520, or outside SPU 500.
Decompression is important in the release of data such as video
and audio that is usually compressed before distribution and
whose decompression speed is important. In some cases,
information that is useful for usage monitoring purposes (such as
record separators or other delimiters) is "hidden" under a
compression layer that must be removed before this information
can be detected and used inside SPU 500.
Random Number Generator 642
Optional random number generator 542 may provide
specialized hardware circuitry for generating random values
(e.g., from inherently unpredictable physical processes such as
quantum noise). Such random values are particularly useful for
constructing encryption keys or unique identifiers, and for
initializing the generation of pseudo-random sequences.
-208-
CA 02479494 2004-10-04
wo 9SIM rerms"nsw
Random number generator 542 may produce values of any
convenient length, including as small as a single bit per use. A
random number of arbitrary size may be constructed by
, concatenating values produced by random number generator
542. A cryptographically strong pseudo-random sequence may
be generated from a random key and seed generated with
random number generator 542 and repeated encryption either
with the encrypt/decrypt engine 522 or cryptographic algorithms
in SPU 500. Such sequences may be used, for example, in
private headers to frustrate efforts to determine an encryption
key through cryptoanalysis.
Arithmetic Accelerator 544
An optional arithmetic accelerator 544 may be proNided
within an SPU 500 in the form of hardware circuitry that can
rapidly perform mathematical calculations such as
multiplication and exponentiation involving large numbers.
These calculations can, for example, be requested by
microprocessor 520 or encrypt/decrypt engine 522, to assist in the
computations required for certain asyinmetric
encryption/decryption operations. Such arithmetic accelerators
are well-known to those skilled in the art. In some
implementations, a separate arithmetic accelerator 544 may be
- 209 -
CA 02479494 2004-10-04
wo 98109209 PcT/U841/1SZ43
omitted and any necessary calculations may be performed by
microprocessor 520 under software control.
DDi[A Controller 526
DMA controller 526 controls information transfers over
address/data bus 536 without requiring microprocessor 520 to
process each individual data transfer. Typically, microprocessor
520 may write to DMA controller 526 target and destination
addresses and the number of bytes to transfer, and DMA
controller 526 may then automatically transfer a block of data
between components of SPU 500 (e.g., from ROM 532 to RAM
534, between encrvpt/decrypt engine 522 and RAM 534, between
bus interface unit 530 and RkM 534, etc, ). DNLA controller 526
may have multiple channels to handle multiple transfers
simultaneously. In some implementations. a separate DMA
controller 526 may be omitted, and anr necessary data
movements may be performed by microprocessor 520 under
software control.
Bus Interface Unit (BIU) 530
Bus interface unit (BIU) 530 communicates information
between SPU 500 and the outside world across the security
barrier 502. BIU 530 shown in Figure 9 plus appropriate driver
software may comprise the "appliance link" 510 shown in Figure
- 210 -
CA 02479494 2004-10-04
wo 9a)"M rCrIETWnsw
6. Bus interface unit 530 may be modelled after a USART or PCI
bus interface in the preferred embodiment. In this example, BI[7
= 530 connects SPU 500 to electronic appliance system bus 653
shown in Figure 8. BIU 530 is designed to prevent unauthorized
access to internal components within SPU 500 and their
contents. It does this by only allowing signals associated with an
SPU 500 to be processed by control programs running on
microprocessor 520 and not supporting direct access to the
internal elements of an SPU 500.
Memory Management Unit 540
Memory Management Unit (MMU) 540, if present,
provides hardware support for memory management and virtual
memory management functions. It may also provide heightened
security by enforcing hardware compartmentalization of the
secure execution space (e.g., to prevent a less trusted task from
modifying a more trusted task). More details are provided below
in connection with a discussion of the architecture of a Secure
Processing Environment ("SPE") 503 supported by SPU 500.
MMU 540 may also provide hardware-level support
functions related to memory management such as, for example,
address mapping.
-211-
CA 02479494 2004-10-04
wo 9M09209 rcTRTS97ILqw
SPU Mamory Architsctusa
In the preferred embodiment, SPU 500 uses three general
kinds of memory:
(1) internal ROM 532;
(2) internal RAM 534; and
(3) external memory (typicaIly RAM and/or disk supplied
by a host electronic appliance).
The internal ROM 532 and RAM 534 within SPU 500
provide a secure operating environment and execution space.
Because of cost limitations, chip fabrication size, complexity and
other limitations, it may not be possible to provide sufficient
memory within SPU 500 to store all information that an SPU
needs to process in a secure manner. Due to the practical limits
on the amount of ROM 532 and RAM 534 that may be included
within SPU 500, SPU 500 may store information in memory
external to it, and move this information into and out of its
secure internal memory space on an as needed basis. In these
cases, secure processing steps performed by an SPU typically
must be segmented into small, securely packaged elements that
may be "paged in" and "paged out" of the limited available
internal memory space. Memory externai to an SPU 500 may
not be secure. Since the external memory may not be secure,
SPU 500 may encrypt and cryptographically seal code and other
- 212 -
CA 02479494 2004-10-04
WO 99S/09Z09 PCTNSMS2/3
information before storing it in external memory. Similarly,
SPU 500 must typicaIly decrypt code and other information
= obtained from external memory in encrypted form before
processing (e.g., executing) based on it. In the preferred
embodiment, there are two general approaches used to address
potential memory limitations in a SPU 500. In the first case, the
small, securely packaged elements represent information
contained in secure database 610. In the second case, such
elements may represent protected (e.g., encrypted) virtual
memory pages. Although virtual memory pages may correspond
to information elements stored in secure database 610, this is not
required in this example of a SPU memory architecture.
The following is a more detailed discussion of each of these
three SPU memory resources.
SPU Internal ROM
SPU 500 read only memory (ROM) 532 or comparable
purpose device provides secure internal non-volatile storage for
certain programs and other information. For example, ROM 532
may store "kernel" programs such as SPU control fimware 508
and, if desired, encryption key information and certain
fundamental "load modules." The "kerael" programs, load
module information, and encryption key information enable the
- 213 -
CA 02479494 2004-10-04
wo "IOM PcrRrs97nSZ13
control of certain basic functions of the SPU 500. Those
components that are at least in part dependent on device
configuration (e.g., POST, memory allocation, and a dispatcher)
may be loaded in ROM 532 along with additional load modules
that have been determined to be required for specific
installations or applications.
In the preferred embodiment, ROM 532 may comprise a
combination of a masked ROM 532a and an EEPROM and/or
equivalent "flash" memory 532b. EEPROM or flash memory
532b is used to store items that need to be updated and/or
initialized, such as for example, certain encryption keys. An
additional benefit of providing EEPROM andlor flash memory
532b is the ability to optimize any load modules and library
functions persistently stored within SPU 500 based on typical
usage at a specific site. Although these items could also be
stored in NVRAM 534b, EEPROM and/or flash memory 532b
may be more cost effective.
Masked ROM 532a may cost less than flash and/or
EEPROM 532b, and can be used to store permanent portions of
SPU software/firmware. Such permanent portions may include,
for example, code that interfaces to hardware elements such as
the RTC 528, encryption/decryption engine 522, interrupt
-214-
CA 02479494 2004-10-04
Wo 019309 PCT/U997l15Z43
handlers, key generators, etc. Some of the operating system,
library calls, libraries, and many of the core services provided by
SPU 500 may also be in masked ROM 532a. In addition, some of
the more coaamonly used executables are also good candidates for
inclusion in masked ROM 532a. Items that need to be updated
or that need to disappear when power is removed from SPU 500
should not be stored in masked ROM 532a.
Under some circumstances, RAM 534a and/or NVRAM
534b (NVRAM 534b may, for example, be constantly powered
conventional RAM) may perform at least part of the role of ROM
532.
SPU Internal RAM
SPU 500 general purpose RAM 534 provides, among other
things, secure execution space for secure processes. In the
preferred embodiment, RAM 534 is comprised of different types
of RAM such as a combination of high-speed RAM 534a and an
NVRAM ("non-volatile RAM") 534b. RAM 534a may be volatile,
while NVRAM 534b is preferably battery backed or otherwise
arranged so as to be non-volatile (i.e., it does not lose its contents
when power is turned ofI).
-215-
CA 02479494 2004-10-04
wo Mon" rcrrtuwmsw
High-speed RAM 534a stores active code to be executed
and associated data structures.
NVRAM 534b preferably contains certain keys and
summary values that are preloaded as part of an initialization
process in which SPU 500 communicates with a VDE
administrator, and may also store changeable or changing
information associated with the operation of SPU 500. For
security reasons, certain highly sensitive information (e.g.,
certain load modules and certain encryption key related
information such as internally generated private keys) needs to
be loaded into or generated internally by SPU 500 from time to
time but, once loaded or generated internally, should never leave
the SPU. In this preferred embodiment, the SPU 500
non-volatile random access memory (NVRAM) 534b may be used
for securely storing such highly sensitive information. NVRAM
534b is also used by SPU 500 to store data that may change
frequently but which preferably should not be lost in a power
down or power fail mode.
NVRAM 534b is preferably a P~ash memory array, but may
in addition or alternatively be electrically erasable
programmable read only memory (EEPROM), static RAM
(SR.AM), bubble memory, three dimensional holographic or other
-216-
CA 02479494 2004-10-04
WO 98p9269 PcrnJS97/1S?A3
electro-optical memory, or the like, or any other writable (e.g.,
randomly accessible) non-volatile memory of sufficient speed and
cost-effectiveness.
SPU External Memory
The SPU 500 can store certain information on memory
devices external to the SPU. If available, electronic appliance
600 memory can also be used to support any device external
portions of SPU 500 software. Certain advantages may be
gained by allowing the SPU 500 to use exteraal memory. As one
example, memory internal to SPU 500 may be reduced in size by
using non-volatile read/write memory in the host electronic
appliance 600 such as a non-volatile portion of RAM 656 and/or
ROM 658.
Such external memory may be used to store SPU
programs, data and/or other information. For example, a VDE
control program may be, at least in part, loaded into the memory
and communicated to and decrypted within SPU 500 prior to
execution. Such control programs may be re-encrypted and
communicated back to external memory where they may be
' stored for later execution by SPU 500. "Kernel" programs and/or
some or all of the non-kernel "load modules" may be stored by
SPU 500 in memory external to it. Since a secure database 610
-217-
CA 02479494 2004-10-04
wo 9M9ZO9 rcr/US97ML13
may be relatively large, SPU 500 can store some or all of secure
database 610 in external memory and call portions into the SPU
500 as needed.
As mentioned above, memory external to SPU 500 may not
be secure. Therefore, when security is required, SPU 500 must
encrypt secure information before writing it to external memory,
and decrypt secure information read from external memory
before using it. Inasmuch as the encryption laver relies on
secure processes and information (e.g., encryption algorithms
and keys) present within SPU 500, the encryption layer
effectively "extends" the SPU security barrier 502 to protect
information the SPU 500 stores in memory externai to it.
SPU 500 can use a wide variety of different types of
external memorv. For example, external memorv mav comprise
electronic appliance secondary storage 652 such as a disk;
external EEPROM or flash memory 658; and/or external RAM
656. External RAM 656 may comprise an external nonvolatile
(e.g. constantly powered) RAM andlor cache RAM.
Using external RAM local to SPU 500 can significantly
improve access times to information stored externally to an SPU.
For example, external RAM may be used:
-218-
CA 02479494 2004-10-04
WO 9 IOl309 P~.'T