Note: Descriptions are shown in the official language in which they were submitted.
CA 02538190 1997-11-07
27631-11D
INTEGRATED INFORMATION COMMUNICATION SYSTEM
This is a divisional of Canadian patent application 2,220,559 filed
November 7, 1997.
BACKGROUND OF THE INVENTION
1. Field of the Invention
The present invention relates to an integrated information
communications system integrally connecting information communication
equipments or information communication systems such as and/or for
personal computer, LAN (Local Area Network), telephone (including
portable telephone), FAX (Facsimile), CATV (Cable Television),
Internet and the like, not only via dedicated lines, but also via
ISDN (Integrated Services Digital Network), FR (Franie Relay), ATM
(Asynchronous Transfer Mode), IPX (Integrated Packet Exchange),
satellite, wireless and public lines. Here, the integrated
information communication equipment performs communication provided
with an address (for the information or the communication) for
distinguishing the integrated information communication equipments
with other equipments. Particularly, the present invention relates
to an integrated information communication system which integrates
data transfer services based on connection-less networks (e.g., IP
(Internet Protocol) technology used RFC791 or RFC1883) and improves
the overall economics of the information communication system by
employing a unified address system, and ensuring security to realize
an interactive communication between connected terminals or systems.
2. Description of the Prior Art
In accordance with a development of computer and information
1
CA 02538190 1997-11-07
communication technology, computer communication networks have in
recent years come to be widely used in universities, research
institutes, government organizations and intra-corporation/inter-
corporation situations. LANs are used for intra-corporation
communication networks, and in the event that the geographic locale
is on a national basis, the form thereof becomes such as sown in
FIG.1. In the example described in FIG.1, each local LAN uses a
common protocol, with each being connected by dedicated lines. Here,
e.g., corporation X has LAN-Xl, LAN-X2 and LAN-X3 as LANs,
corporation Y has LAN-Y1, LAN-Y2 and LAN-Y3 as LANs, and both
corporations X and Y use communication address systems ADX and ADY
for respectively performing computer communications. Since it is
necessary to lay a separate dedicated line for each corporation with
such a LAN network, system architecture becomes costly, and in the
event that connection is to be made to a LAN network of another
corporation, interfacing must be matched such as the communication
' ,.
address system, making inter-connection very difficult and very
costly.
On the other hand, the Internet has recently become
widespread as a global-scale computer communication network. On the
Internet, networks are connected using a router of a provider, a
communication protocol called TCP (Transmission Control Protocol)/IP
(Internet Protocol) is employed, dedicated lines or FR networks are
used for connecting remote areas, and Ethernets which are 10 Mbps
LANs or FDDIs (Fiber Distributed Data Interface) which are 100 Mbps
2
CA 02538190 1997-11-07
LANs are used as communication paths within structures. FIG.2 shows
an example of an Internet connection, in which the routers in the
providers maintain mutual connection by exchanging routing-table
connection information. Each router is connected to a plurality of
networks, and judgment is made based on the routing-table regarding
to which router connected to which provider's network received data
should go next. Thus, on the Internet, the IP address attached to
each IP frame (IP datagram) is checked, the judgment is made to which
router the IP frame should be sent, and that the IP frame is sent
accordingly. Thus, the IP frames are trailsferred one after another
and delivered to a destination computer, by means of all routers
performing the above-described operation.
FIG.3 illustrates the information contents of the RFC791 of
the IP frame used by the Iriternet, divided into a control field and a
data field. FIG.4 illustrates the information contents of a similar
RFC1883, also divided into a control field and a data field. In
either figure, the parentheses () indicate the number of bits.
However, with the Internet, since the system is such that the
communication path is not administrated in an integrated manner, one
cannot tell whether the other party with which communication is being
made is the authorized party, and there are problems regarding
security in that information may be eavesdropped. Also, in reality,
IP addresses within many LANs are being separately decided by the LAN
users, so there is the necessity to replace the IP address of the LAN
user to the IP address for the Internet when connecting the LAN to
3
CA 02538190 1997-11-07
the Internet. Also, communication quality such as communication
speeds and communication error rates for the trunk lines making up
the Internet communication path differ from one line to another for
each LAN, and are practically non-uniform. For example, there are
problems such as an attempt to send a 10 Mbps TV signal for video-
conferencing not achieving the desired communication speed.
Therefore, the Internet cannot be in peace used for the communication
of the country and the research institute which especially require
the reliability or for the business of the company. Further, there
is no administrator for performing maintenance of the network such as
in the case of failure, of for integrating the overall network for
future planning for the network and so forth. Also, with LAN
networks and the Internet, the terminals are personal computers
(computers), and it has been difficult to user telephones, FAX, CATV
and so on in an integrated manner therein.
SUMMARY OF THE INVENTION
The present invention has been made in accordance with the
above-described situations, and it is an object of the present
invention to provide an integrated information communication system
capable of containing a plurality of VANs which perform
data/information transfer by using IP frame of which security and
reliability in commuilications has been ensured, by means of not using
dedicated lines or the Interilet so as to improve economic
considerations of the information communication system architecture,
and ensuring communication speeds, communication quality and
4
CA 02538190 1997-11-07
communication trouble countermeasures in a unified manner. Also, it
is another object of the present invention to provide an integrated
information communication system which uses a single information
transfer which is not dependent on the type of service, such as
sound, image (motion and still), text, etc., so as to inter-connect
services which have conventionally been provided separately, such as
total communication services, analog/digital telephone line services,
Internet provider services, FAX services, computer data exchange
services, CATV services and so forth. Further, it is another object
of the present invention to provide an integrated information
communication system which enables inter-corporation communication
with very little change to the computer communication address systems
which have been independently and separately created within each
separate corporation (including universities, research institutes,
government organizations, etc.).
The present invention relates to an integrated information
communication system, and the above objects of the present invention
are realized as follows: the present invention is configured by
providing an access control apparatus for connecting a plurality of
computer communication networks or information communication
equipments to each, and a relay device for networking the
aforementioned access control apparatus, the system having functions
for performing routing by transferring the information by a unified
address system, and is configures such that the aforementioned
plurality of computer communication networks or information
CA 02538190 1997-11-07
communication equipments can perform communications in an interactive
manner.
In FIG.1 which is given as an example of a conventional
arrangement, the range of dedicated lines used for intra-corporation
and inter-corporation communications is indicated by solid lines, and
this is replaced with the equivalent of a computer communication
network according to IP technology as a common communication network
indicated by broken lines.
The above-described objects of the present invention are
achieved by an ICS user frame having a unique ICS user address system
ADX being converted into an ICS network frame having an address
system ADS, based on the administration of a conversion table
provided within an access control apparatus, and by being arranged
such that in the case that transmission is made over at least one VAN
contained therein following rules of the aforementioned address
system ADS, and the destination other access control apparatus is
reached, conversion is made to the aforementioned ICS user address
system ADX based on the administration of the aforementioned
conversion table, and another external information communication
apparatus is reached. Also, the above-described objects of the
present invention are achieved by an ICS user frame having a unique
ICS user address system ADX being converted into an ICS network frame
corresponding with a reception ICS network address registered
beforehand to the conversion table in accordance with a user logic
communication line, rather than usiiig an ICS user address within the
6
CA 02538190 2007-07-31
27631-11D
aforementioned ICS user frame based on the administration of
a conversion table provided within the access control
apparatus, and by being arranged such that in the case that
transmission of the aforementioned ICS network frame is made
to another access control device via at least one VAN
following rules of the ICS address system ADS, the transfer
destination of the aforementioned ICS network frame being
either 1 or N, this is returned to the aforementioned
ICS network frame based on the administration of a
conversion table provided within the aforementioned access
control apparatus, and another external information
communication apparatus is reached.
In a broad aspect, the invention provides an IP
communication network, wherein said IP communication network
is connected to two or more terminals and includes plural
access control apparatus having a conversion table, a
sending side terminal forms an IP packet including a
telephone number of a destination terminal and sends said IP
packet to said IP communication network, said IP
communication network forms an IP address for communicating
with said destination terminal based on a record of said
conversion table and replies said IP address to said sending
side terminal, said record includes a set of a telephone
number of said destination terminal and an IP address for
communicating with said destination terminal, and a
communication between said sending side terminal and said
destination terminal is carried out based on an IP address
of said sending side terminal and said IP address of said
destination terminal.
In another aspect, the invention provides an
IP communication network, wherein a transfer network
includes plural access control apparatus having each
conversion table, first and second terminals outside said
7
CA 02538190 2007-07-31
27631-11D
transfer network are respectively connected to first and
second access control apparatus via first and second user
communication lines, said first terminal sends a first user
frame including a first telephone number of said second
terminal for requesting a connection to said second
terminal, and said first user frame is inputted to said
first access control apparatus via said first user
communication line from a first logical terminal assigned a
first ICS address, said first access control apparatus finds
a record including a second telephone number at said
conversion table, said first access control apparatus
obtains a second ICS address of a discrimination information
of a second logical terminal of said second access control
apparatus for connecting to said second user communication
line, said second ICS address is included in said record,
said first access control apparatus sends a first ICS frame
including said second ICS address and a receiving notice,
and said first ICS frame reaches at said second access
control apparatus through said transfer network, said second
access control apparatus sends a second user frame including
said receiving notice to said second terminal, said second
terminal sends a third user frame including a response
signal to said second access control apparatus, said second
access control apparatus sends a second ICS frame to said
first access control apparatus when it receives said third
user frame, and said first access control apparatus sends a
fourth user frame including said response signal to said
first terminal, a fifth user frame is inputted to said first
access control apparatus via said first user communication
line and said first logical terminal when said first
terminal sends said fifth user frame including a voice
digital signal, said fifth user frame is traiisferred in said
transfer network by being converted into a third ICS frame,
and said third ICS frame includes said second ICS address,
7a
CA 02538190 2007-07-31
27631-11D
and said third ICS frame is converted into a sixth user
frame when it reaches at said second access control
~apparatus, said sixth user frame reaches at said second
terminal via said second user communication line, and said
first terminal communicates with second said terminal via
said transfer network.
In another aspect, the invention provides an IP
communication network, wherein said IP communication network
is connected to terminals and a public telephone network and
includes plural access control apparatus having a conversion
table, telephones are connected to said public telephone
network, said IP communication network includes a function
to form an IP address for communicating with a destination
terminal based on a record of said conversion table, said
record includes a set of a telephone number of said
destination terminal and an IP address for communicating
with said destination terminal, and a telephone
communication is carried out between a terminal in said
terminals and a telephone in said telephones.
In another aspect, the invention provides an
IP communication network, wherein first and second terminals
outside a transfer network are respectively connected to
said transfer network via first and second user
communication lines, and said transfer network includes a
conversion table, said first terminal sends a first user
frame including a first telephone number of said second
terminal for requesting a connection to said second
terminal, and said first user frame is inputted to said
transfer network via said first user communication line from
a first logical terminal, said transfer network finds a
record including a second telephone number of said second
terminal at said conversion table, said transfer network
obtains discrimination information of a second logical
7b
CA 02538190 2007-07-31
27631-11D
terminal of said transfer network for connecting to said
second user communication line, said discrimination
information is included in said record, said transfer
network sends a second user frame including a receiving
notice by using said discrimination information via said
second logical terminal and said first discrimination
information, said second terminal sends a third user frame
including a response signal to said transfer network, and
said second terminal sends said third user frame to said
first terminal via said first logical terminal, said first
terminal send a user fourth frame including a voice digital
signal, and said fourth user frame is inputted to said
transfer network via said first communication line and said
first logical terminal, and said transfer network converts
said user fourth frame into an ICS user frame including said
discrimination information and sends, said ICS user frame is
converted into a fifth user frame and is sent from said
second logical terminal, said fifth user frame reaches at
said second terminal via said second user communication
line, and said first terminal communicates with said second
terminal 2 via said transfer network.
In another aspect, the invention provides an
IP communication network, wherein a transfer network
includes plural access control apparatus, a first terminal
outside said transfer network is connected to a first line
converting unit in a first access control apparatus via a
first line, a second terminal being a first telephone number
is connected to a second line converting unit in a second
access control apparatus via a second line, and said first
and second lines are telephone lines or ISDN lines, said
first terminal sends a signal including said telephone
number for requesting a connection to said second terminal,
and said signal is inputted to said first access control
7c
CA 02538190 2007-07-31
27631-11D
apparatus via said first line from a first logical terminal
of said first line converting unit, said first access
control apparatus finds a record including first
discrimination information of said first logical terminal
and said telephone number at a conversion table, and said
first access control apparatus obtains a first address of
second discrimination information of a second logical
terminal for connecting said second terminal to said second
line and a second address assigned to said first logical
terminal, said first access control apparatus forms a first
IP packet for notice a receipt to said second terminal and
sends the first IP packet to said second access control
apparatus, a source address of said first IP packet is said
first address and a destination address of said first
IP packet is said second address, and said second access
control apparatus converts a receiving notice information
included in said first IP packet into said telephone line or
said ISDN line at said second line converting unit, said
second access control apparatus sends said receiving notice
information to said second terminal via said second logical
terminal, said second terminal sends a response signal to
said second access control apparatus, said response signal
reaches at said second line converting unit of said second
access control apparatus, said second access control
apparatus forms a second IP packet for noticing a reply and
sends the second IP packet to said first access control
apparatus terminal, said first line converting unit converts
said second IP packet into a signal of said telephone line
or said ISDN line and sends it to said first terminal via
said first logical terminal, and said first terminal
communicates with said second terminal via said first line,
said transfer network and said line.
7d
CA 02538190 2007-07-31
27631-11D
In another aspect, the invention provides an
IP communication network, wherein a transfer network
includes plural access control apparatus, a first terminal
outside said transfer network is connected to a first line
converting unit in a first access control apparatus via a
first line, a second terminal being a telephone number is
connected to a second line converting unit in a second
access control apparatus via a second line, and said first
and second lines are telephone lines or ISDN lines, said
first terminal sends a first signal including said telephone
number for requesting a connection to said second terminal,
and said signal is inputted to said access first control
apparatus via said first line from a first logical terminal
of said first line converting unit, said first access
control apparatus obtains a first address of a second
logical terminal for connecting to the second line connected
to said second terminal having the telephone number, said
first access control apparatus forms a first IP packet for
noticing a receipt to said second terminal and sends the
first IP packet to said second access control apparatus, and
a destination address of said first IP packet is said second
address, said second access control apparatus converts a
receiving notice information included in said first
IP packet into said telephone line or said ISDN line at said
second line converting unit, said second access control
apparatus sends said receiving notice information to said
second terminal via said second logical terminal, said
second terminal sends a response signal to said second
access control apparatus, said response signal reaches at
said second line converting unit of said second access
control apparatus, said second access control apparatus
forms a second IP packet for noticing a reply and sends the
second IP packet to said first access control apparatus
terminal, said first line converting unit converts said
7e
CA 02538190 2007-07-31
27631-11D
second IP packet into a second signal of said telephone line
or said ISDN line and sends said second signal to said first
terminal via said first logical terminal, and said first
terminal communicates with said second terminal via said
first line, said transfer network and said second line.
In another aspect, the invention provides an IP
communication network being connected to an international
telephone network, wherein said IP communication network is
connected to two or more terminals and includes plural
access control apparatus having a conversion table, a
telephone is connected to said international telephone
network, said IP communication network includes a function
to form an IP address for communicating with a destination
terminal based on a record of said conversion table, said
record includes a set of a telephone number of said
destination terminal and an IP address for communicating
with said destination terminal, and a telephone
communication is carried out between said terminal and said
telephone.
In another aspect, the invention provides a
communication method between terminals being connected to an
IP communication network, comprising the steps of: forming
an IP packet including a telephone number of a destination
terminal by a sending side terminal; sending said IP packet
to said IP communication network; forming an IP address of
said destination terminal based on said telephone number in
said IP communication network; replying said IP address to
said sending side terminal; and carrying out a communication
between said terminals based on said IP packet and said
IP address.
In another aspect, the invention provides a
communication method between terminals, wherein an ICS user
7f
CA 02538190 2007-07-31
27631-11D
frame including an IP address storage portion, a voice
input/output portion, a voice data sending/receiving portion
and a telephone number of a destination terminal is formed,
and said ICS user frame is sent to a user communication
line, an ICS user address in said ICS user frame is an
ICS user address of said terminal including in said
IP address storage portion and an ICS user address of an
inquiring server in an integrated information communication
system, comprising the steps of: receiving said ICS user
frame including in said ICS user address of said destination
terminal from said ICS user communication line; inputting a
voice from said voice input/output portion; converting from
said voice to digital voice at said voice data
sending/receiving portion; sending said digital voice to
said destination terminal by storing it in said ICS user
frame; carrying out a telephone communication by
sending/receiving said ICS user frame; and whereby said
ICS user address in said ICS user frame including said
digital voice includes a function to communicate by
connecting to a terminal to be communicated, based on said
ICS user address of said terminal and said ICS user address
of said destination terminal.
In another aspect, the invention provides a
communication method between terminals in an IP
communication network, comprising the steps of: forming an
IP packet including a telephone number of a destination
terminal of said terminals; sending said IP packet to an
access control apparatus having a conversion table provided
in said IP communication network; preparing a record stored
a set of a telephone number of said destination terminal and
an IP address for communicating with said destination
terminal; obtaining said IP address of said destination
terminal based on said record at said conversion table;
7g
CA 02538190 2007-07-31
27631-11D
replying said IP address to said terminal; and carrying out
a communication with said destination terminal by
sending/receiving said IP packet, and by using said IP
address and an own IP address of said terminal.
In another aspect, the invention provides a
terminal being connected to an IP communication network,
wherein a sending side terminal forms an IP packet including
a telephone number of a destination terminal and sends said
IP packet to said IP communication network, said
IP communication network forms an IP address of said
destination terminal based on said telephone number and
replies it to said sending side terminal, and a communication
with said destination terminal is carried out by using said
IP address and an own IP address of said sending side
terminal.
In another aspect, the invention provides a
terminal being connected to an IP communication network,
wherein an ICS user frame including an IP address storage
portion, a voice input/output portion, a voice data
sending/receiving portion and a telephone number of a
destination terminal is formed, and said ICS user frame is
sent to a user communication line, an ICS user address in
said ICS user frame is an ICS user address of said terminal
including in said IP address storage portion and an ICS user
address of an inquiring server in an integrated information
communication system, and said terminal receives an ICS user
frame stored at an ICS user address of said destination
terminal from said ICS user communication line, inputs a
voice from said voice input/output portion, converts from
said voice to digital voice in said voice data
sending/receiving portion, sends said digital voice to said
destination terminal by storing it at said ICS user frame
and carries out a telephone communication by
7h
CA 02538190 2007-07-31
27631-11D
sending/receiving said ICS user frame; and whereby said
ICS user address in said ICS user frame including said
digital voice includes a function to communicate by
connecting to a terminal to be communicated, based on said
ICS user address of said terminal and said ICS user address
of said destination terminal.
In another aspect, the invention provides a
terminal being connected to an IP communication network,
wherein a terminal forms an IP packet including a telephone
number of a destination terminal and sends it to a server
connected with said IP communication network, said server
forms an IP address of said destination terminal based on a
telephone number and replies it to said terminal, and said
terminal carries out a communication with said destination
terminal by sending/receiving said IP packet and by using
said IP address of said destination terminal and an own
IP address of said terminal.
In another aspect, the invention provides a
telephone machine, wherein an ICS user frame including an
IP address storage portion, a voice input/output portion, a
voice data sending/receiving portion and a telephone number
of a destination telephone machine is formed, and said
ICS user frame is sent to a user communication line, an
ICS user address in said ICS user frame is an ICS user
address of said telephone machine including in said
IP address storage portion and an ICS user address of an
inquiring server in an integrated information communication
system, and said telephone machine receives said ICS user
frame stored at an ICS user address of said destination
telephone machine from said ICS user communication line,
inputs a voice from said voice input/output portion,
converts from said voice to digital voice in said voice data
sending/receiving portion, sends said digital voice to said
7i
CA 02538190 2007-07-31
27631-11D
destination telephone machine by storing it at said ICS user
frame and carries out a telephone communication by
sending/receiving said ICS user frame; and whereby said
ICS user address in said ICS user frame including said
digital voice includes a function to communicate by
connecting to a telephone machine to be communicated, based
on said ICS user address of said telephone machine and said
ICS user address of said destination telephone machine.
In another aspect, the invention provides a
telephone machine, wherein a terminal forms an IP packet
including a telephone number of a destination telephone
machine and sends it to an access control apparatus having a
conversion table provided in said IP communication network,
said access control apparatus forms an IP address of said
destination telephone machine based on a record in said
conversion table, said record includes a set of a telephone
number of said destination terminal and an IP address for
communicating with said destination terminal, said access
control apparatus replies said formed IP address to said
telephone machine, and said telephone machine carries out a
communication with said destination telephone machine by
sending/receiving said IP packet and by using said IP
address of said replied destination telephone and an own IP
address of said telephone.
BRIEF DESCRIPTION OF THE DRAWINGS
In the accompanying drawings:
FIG. 1 is a block diagram for describing
conventional LAN networks;
FIG. 2 is a diagram illustrating an example of a
form of the Internet;
7j
CA 02538190 2007-07-31
27631-11D
FIG. 3 is a diagram illustrating an IP frame
according to RFC791 stipulations;
FIG. 4 is a diagram illustrating an IP frame
according to RFC1883 stipulations;
FIG. 5 is a block diagram systematically
illustrating the basic principle of the present invention;
FIG. 6 is a block diagram to show an example of a
network wherein an ICS according to the present invention is
constructed of a plurality of VANs;
7k
CA 02538190 1997-11-07
FIG.7 is a block diagram to show an example of configuring
the access control apparatus;
FIG.8 is a block diagram to show an example of configuring
the relay apparatus;
FIG.9 is a block diagram to show an example of configuring
the inter-VAN gateway;
FIG.10 is a block diagram to show an example of configuring
the ICS network server;
FIG.11 is an array diagram illustrating an example of the ICS
user address used in the present invention;
FIG.12 is a wiring diagram illustrating the connection
relation between the ICS logic terminals and the user communication
lines;
FIG.13 is a diagram illustrating the relation between the ICS
user frame and the ICS network frame which are used in the present
invention;
FIG.14 is a portion of a constructional block diagram to show
a first embodiment (intra-corporation communication, inter-
corporation communication) according to the present invention;
FIG.15 is a portion of a constructional block diagram to show
a first embodiment (intra-corporation communication, inter-
corporation communication) according to the present invention;
FIG.16 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.17 is a diagram to show an example of the temporary
8
CA 02538190 1997-11-07
conversion table in the access control apparatus;
FIG.18 is a flowchart to show an example of operation of the
access control apparatus;
FIG.19 is a flowchart to show an example of operation of the
access control apparatus in inter-corporation communication;
FIG.20 is a constructional block diagram to show a second
embodiment (virtual dedicated line) according to the present
invention;
FIG.21 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.22 is a flowchart to show an example of operation of the
access control apparatus in virtual dedicated line connection;
FIG.23 is a constructional block diagram to show a third
embodiment (ICS network server) according to the present invention;.
FIG.24 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.25 is a diagram to show an example of the table in the
ICS network database;
FIG.26 is a flowchart to show an example of operation within
the access control apparatus in virtual ICS network server
connection;
FIG.27 is a constructional block diagram to show a fourth
embodiment (ICS address administration server) according to the
present invention;
FIG.28 is a diagram to show an example of the conversion
9
CA 02538190 1997-11-07
table in the access control apparatus;
FIG.29 is a diagram to show an example of the correspondence
table in the ICS address administration server;
FIG.30 is a flowchart to show an example of operation of the
ICS address administration server;
FIG.31 is a constructional block drawing illustrating a fifth
embodiment (ICS name server) according to the present invention;
FIG.32 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.33 is a diagram to show an example of the ICS name
conversion table in the ICS name server;
FIG.34 is a flowchart to show an example of operation of the
ICS name server;
FIG.35 is a portion of a constructional block drawing
illustrating a eighth embodiment (accounting server) according to the
present invention;
FIG.36 is a portion of a constructional block diagram to show
an eighth embodiment (accounting server) according to the present
invention;
FIG.37 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.38 is a diagram to show an example of the fixed charging
definition table in the accounting server;
FIG.39 is a diagram to show an example of the accounting
information database in the accounting server;
CA 02538190 1997-11-07
FIG.40 is a flowchart to show an example of operation of the
charging process;
FIG.41 is a portion of a constructional block diagram to show
a ninth embodiment (ICS frame database server) according to the
present invention;
FIG.42 is a portion of a constructional block diagram to show
a ninth embodiment (ICS frame database server) according to the
present invention;
FIG.43 is a diagram to show an exainple of the stored
information administration table and the Box in the ICS frame
database server;
FIG.44 is a diagram to show an example of the stored
information administration table and the Box in the ICS frame
database server;
FIG.45 is a diagram illustrating an example of an ICS user
frame used by the ICS frame database server;
FIG.46 is a flowchart to show an example of operation of the
communication example 1 of the ICS frame database server;
FIG.47 is a flowchart to show an example of operation of the
communication example 2 of the ICS frame database server;
FIG.48 is a flowchart to show an example of operation of the
communication example 3 of the ICS frame database server;
FIG.49 is a portion of a constructional block diagram to show
a tenth embodiment (transfer by X.25, FR, ATM, satellite
communication, and containment of telephone line, ISDN line, CATV
11
CA 02538190 1997-11-07
line, satellite line, IPX frame) according to the present invention;
FIG.50 is a portion of a constructional block diagram to show
a tenth embodiment according to the present invention;
FIG.51 is a portion of a constructional block diagram to show
a tenth embodiment according to the present invention;
FIG.52 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.53 is a diagram illustrating the manner of frame
conversion of the ICS network frame and the X.25 format;
FIG.54 is a diagram illustrating the manner of frame
conversion of the ICS network frame and the FR format;
FIG.55 is a diagram illustrating the manner of frame
conversion of the ICS network frame and the ATM format;
FIG.56 is a portion of a constructional block diagram to show
an eleventh embodiment (transfer by X.25, FR, ATM, satellite
communication, and containment of telephone line, ISDN line, CATV
line, satellite line, IPX frame) according to the preseilt invention;
FIG.57 is a portion of a constructional block diagram to show
an eleventh embodiment according to the present invention;
FIG.58 is a portion of a constructional block diagram to show
a twelfth embodiment (containment of the access control apparatus
within the X.25 network and FR network) according to the present
invention;
FIG.59 is a portion of a constructional block diagram to show
a twelfth embodiment according to the present invention;
12
CA 02538190 1997-11-07
FIG.60 is a portion of a constructional block diagram to show
a thirteenth embodiment (the access control apparatus connected with
the relay network) according to the present invention;
FIG.61 is a portion of a constructional block diagram to show
a fourteenth embodiment (provision of access control apparatuses
outside of the ICS) according to the present iilvention;
FIG.62 is a portion of a construction block diagram to show a
fifteenth embodiment according to the present invention;
FIG.63 is a portion of a constriiction block diagram to show a
fifteenth embodiment according to the present invention;
FIG.64 is a portion of a construction block diagram to show a
fifteenth embodiment according to the present invention;
FIG.65 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.66 is a diagram illustrating an example of the table to
define the relation between the communication speed and the speed
class;
FIG.67 is a flowchart to show an example of operation of the
fifteenth embodiment;
FIG.68 is a flowchart to show an example of operation of the
fifteenth embodiment;
FIG.69 is a diagram to show the ICS user frame after the
electronic signature assignment;
FIG.70 is a diagram to show the ICS user frame before the
electronic signature assignment;
13
CA 02538190 1997-11-07
FIG.71 is a construction block diagram to show a sixteenth
embodiment according to the present invention;
FIG.72 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.73 is a flowchart to show an example of operation of the
sixteenth embodiment;
FIG.74 is a diagram to explain the electronic signature at
sending and receiving times;
FIG.75 is a construction block diagram to show a seventeenth
embodiment according to the present invention;
FIG.76 is a construction block diagram to show a eighteenth
embodiment according to the present invention;
FIG.77 is a diagram to show an example of the conversion
table in the access control apparatus;
FIG.78 is a diagram to show an example of the conversion
table original in the ICS conversion table server;
FIG.79 is a diagram to show an example of the correspondence
table in the ICS address administration server;
FIG.80 is a diagram to show an example of the ICS name
convertion table in the ICS name server;
FIG.81 is a construction block diagram to show a nineteenth
embodiment according to the present invention;
FIG.82 is a diagram to show an example of the intensive
conversion table in the intensive access control apparatus;
FIG.83 is a diagram to show an example of the simple
14
CA 02538190 1997-11-07
conversion table in the sin-ple access control apparatus; and
FIG.84 is a flowchart to show an operation of the nineteenth
embodiment.
DESCRIPTION OF THE PREFERRED EMBODIMENTS
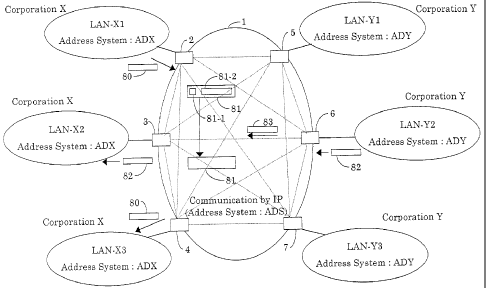
FIG.5 systematically illustrates the basic principle of the
present invention, wherein an integrated information communication
system (hereafter referred to as "ICS") 1 according to the present
invention has self-appointed address providing rules as a computer
information/communication address. i.e., the system has a unique
address system ADS, and lias access control apparatuses (2 through 7
in the present example) which serve as access points for connecting a
plurality of computer communication networks or information
communication equipment, e.g., a great number of LANs (in the present
example, corporation )C s LAN-X1, LAN-X2 and LAN-X3, and corporation
Y's LAN-Yl, LAN-Y2 and LAN-Y3). Here, the corporation X's LAN-X1,
LAN-X2 and LAN-X3 have the same address system ADX, and the
corporation Y's LAN-Y1, LAN-Y2 and LAN-Y3 have the same address
system ADY. The access control apparatuses 2, 3 and 4 have
conversion tables for admiriistrating mutual conversion between the
address system ADS and the address system ADX. The access control
apparatuses 5, 6 and 7 liave conversion tables for administrating
mutual conversion between the address system ADS and the address
system ADY. The computer communication data (ICS frame) within the
ICS 1 uses addresses according to the address system ADS of the ICS
1, and performs the communication according to IP frame which is used
CA 02538190 1997-11-07
on the Internet.
Now, description will be made regarding the operation in the
case of communication within a single corporation. The computer
communication data (ICS frame) 80 transmitted from the LAN-X1 of a
corporation X is provided with addressing following the address
system ADX, but is subjected to address conversion following the
address system ADS under administration of the conversion table of
the access control apparatus within ICS 1, and becomes ICS frame 81.
This is then sent within the ICS 1 under the rules of the address
system ADS, and upon reaching the destination access control
apparatus 4, is restored to the computer communication data 80 of the
address system ADX under the administration of the conversion table
thereof, and is sent to the LAN-X3 within the same corporation X.
Here, the ICS frame being sent and received within the ICS 1 is
referred to as an "ICS network frame", and the ICS frame being sent
and received outside of the ICS 1 is referred to as an "ICS user
frame". The form of the ICS user frame is stipulated by a form
defined by RFC791 or RFC1883 as a rule used in the Internet, but
dealing with ICS frames wliich do not follow -tlie above rule will be
described later in conjunction with description of another
embodiment.
The ICS network frame 81 is comprised of a network control
field 81-1 and a network data field 81-2, with the network control
field 81-1 storing the addresses (address system ADS) of the access
control apparatuses 2 and 4 therein. The ICS user frame is either
1 G
CA 02538190 1997-11-07
used as the network data field 81-2 with no change to the data value
thereof, or is subjected to data format conversion under the
stipulations determined within the ICS 1 and is used as network data
field 81-2. An example of the data format conversion stipulations
might be conversion to ciphertext or data compression, and the access
control apparatus 2 may be provided with ciphering means, deciphering
means for returning the ciphertext to the original plain-text (ICS
user frame), data compression means, and data decompression means for
returning the compressed data to the original data. In the access
coiitrol apparatus 2, the ICS user frame 80 is used as the ICS network
frame 81-2, and the operation of adding the network control field 81-
1 to the ICS network frame 81-2 is referred to as "ICS encapsula-
tion". Also, in the access control apparatus 4, the operation of
removing the network control field 81-1 from the ICS network frame 81
is referred to as "ICS reverse encapsulation".
Now, description will be made regarding the operation in the
case of communication between different corporations. The computer
communicati.on data (ICS user frame) 82 transmitted from the LAN-Y2 of
a corporation Y is provided with addressing following the address
system ADY, but is subjected to address conversion following the
address system ADS tuider administra-tion of the conversion table of
the access control apparatus 6 wi-t:hin ICS 1, and becoines ICS frame
83. This is then sent within the ICS 1 in accordance with the rules
of the address system ADS, and upon reaching the destination access
control apparatus 3, is converted to the computer communicatioii data
17
CA 02538190 1997-11-07
82 of the address system ADX under the administration of the
conversion table thereof, and is sent to the LAN-X2 within the
corporation X. While address lengths of 32 bits and 128 bits are
used in the present invention, the present invention is by no means
restricted to these. Even if the length of the address is changed to
such other than 32-bit or 128-bit, this does not change the principle
of address conversion which is the principle idea of the present
invention.
Thus, according to the present invention, both intra-
corporation and inter-corporation computer communications are enabled
by unified address administration by the ICS 1. Generally used user
terminals for computer communications are incorporated within the LAN
within the structure of the user, and incorporated within the VAN
(Value Added Network) via access lines, and user data frames are sent
which have differing data formats and differing address system for
each type of service. For example, an IP address is used for
Internet services, a telephone number/ISDN number (E.164 address) for
telephone services, and an X.121 address is used for X.25 packet
services. Conversely, according to the ICS 1 of the present
invention, address conversion (referred to as "ICS address
conversion") is performed with the conversion table of the access
control apparatus based on the inpiitted ICS user frame, thus
realizing sending of information frames of data of varied structures
unified under a single data format and address system, i.e.,
converted to ICS frames.
18
CA 02538190 1997-11-07
FIG.6 schematically illustrates an example wherein the ICS 1
of the present invention is comprised of a plurality of VANs (VAN-1,
VAN-2, VAN-3), with each VAN being administered by a VAN operator.
An ICS 1 user applies to the VAN operator for a user communication
line, and the VAN operator decides an ICS address, an ICS network
address and the like for the user and registers these informations
with a circuit type in a conversion table 12 within the access
control apparatus 10 such as shown in FIG.7. The ICS 1 has as access
points serving as external connection elements with the LANs (or
terminals thereof) of the corporations X and Y the access control
apparatuses 10-1, 10-2, 10-3, 10-4 and 10-5, and further has relay
apparatuses 20-1, 20-2, 20-3 and 20-4, and also ICS network servers
40-1, 40-2, 40-3, 40-4 and 40-5, as well as ICS address administra-
tion servers 50-1 and 50-2. A relay apparatus 20 such as shown in
FIG.8 is provided to the communication path within each of the VANs,
and an inter-VAN gateway 30 such as illustrated in FIG.9 is provided
as a connection element of the VAN-2 and the VAN-3. The LANs 1-1, 1-
2, 1-3 and 1-4 shown in FIG.6 are respectively connected to the
access control apparatuses 10-1, 10-5, 10-4 and 10-2, via the user
communication lines 36-1, 36-2, 36-3 and 36-4.
The access control apparatus 10 (10-1, 10-2, 10-3, 10-4 and
10-5) are devices containing the user commtinication lines from the
user (corporations X and Y) to the ICS 1, and as shown in FIG.7, is
comprised of a processing device 11 comprised of a CPU and so on, a
conversion table 12 serving as a database for performing address
19
CA 02538190 1997-11-07
conversion and the like, a line portion 13 of an input/output
iriterface, and a temporary conversion table 14. Also, the relay
apparatus 20 has a transferring function of an ICS network frame and
a routing function of path designating, and as shown in FIG.8 has a
processing device 21 comprised of a CPU and so on and a relay table
22, the relay table 22 being used for determining the communication
destination when the ICS network frame is transferred within the ICS
1. The inter-VAN gateway 30 has a processing device 31 comprised of
a CPU and so on and a relay table 32 for determining where to send
the ICS network frames between the VANs, as shown in FIG.9.
As shown in FIG.10, the ICS network server 40 is comprised of
a processing device 41 and an ICS network database 42, the usage of
the ICS network database 42 being various. Examples of the usage
include: user-specific data (such as the name or address of the user)
corresponding with the ICS user address, data not corresponding with
the ICS user address, such as data indicating the state of
communication trouble within the VAN, or data not directly related to
the VAN, such as an electronic library which mairitains and discloses
digital documents, public keys for a public encryption system using
encryption technology employed in verifying the authenticity of the
transmitter and receiver, and maintaining data such as public key
proof data or secret keys for a secret encryption system. The
processing device 41 refers to the ICS network database 42, and
obtains corresponding data and transmits the data to the access
control apparatus 10. Further, not only does the ICS network
2 0
CA 02538190 1997-11-07
database 42 operate in stand-alone manner, but also is capable of
communicating with other ICS network servers and obtaining data
therefrom, by means of transmitting and receiving the ICS network
frames based on IP communication technology. Within the ICS, the ICS
network server is the only component provided with a single ICS
network address.
According to the present invention, the address used to
identify computers, terminals and the like used within the ICS
network frame is referred to as an "ICS network address", and the
address used to identify computers, terminals and the like used
within the ICS user frame is referred to as an "ICS user address".
The ICS network address is used only within the ICS, one or both of
the two types being used; 32-bit length and/or 128-bit length.
Similarly, the ICS user address also uses one or both of the two
types; 32-bit length and/or 128-bit length. The ICS logic terminal
within the access control apparatus 10, the relay apparatus 20, the
inter-VAN gateway 30 and the ICS network server are arranged so as to
be provided each with an ICS network address so as to be uniquely
identified. Also, the ICS user address is formed of a VAN upper code
and a VAN internal code. With the length of the VAN upper code being
represented as Cl bits and the length of the VAN internal code being
represented as C2 bits, the ICS user address is used such that the
total of Cl + C2 equals either 32 bits or 128 bits.
In the present invention, no particular method for deciding
the VAN upper code and the VAN internal code is stipulated, but in
21
CA 02538190 1997-11-07
the case of Cl + C2 = 32 bits, the following example can be given for
a method for deciding such:
VAN upper code = district administration code (4 bits) II
country code (4 bits) II VAN code (8 bits)
VAN internal code = VAN district code (4 bits) II VAN access
point code (8 bits) II user logic code (4 bits)
FIG.11 makes description thereof using an example of an ICS
user address. Here, the symbol "a II b" indicates linkage of data "a"
and "b", i.e., data obtained by means of arrayed data "a" and "b" in
this order. The ICS network address can be provided with locality in
the same manner as with the user network address. i.e.,
ICS network address = district administration code II country
code II VAN code II VAN district code II user logic
communications line code
Thus, the relay apparatus can efficiently find the transfer
destination by means of deciding the transferring destination with
consideration to the district. The address can be determined in the
same way in the case of Cl + C2 = 128 bits, as well. Incidentally,
with the present invention, the ICS frame can be constructed as
described later, as long as Cl + C2 = 32 bits or Cl + C2 = 128 bits
22
CA 02538190 1997-11-07
is kept, regardless of how the field sections for the VAN upper code
and the VAN internal code are made, or the lengtll of each of the
sections. Also, when deciding the VAN upper code and the VAN
internal code, part of these codes may be made to be unique to the
user. That is, the user can make a user-specific address system.
The address values of a 32 bit expression value are from address 0 to
address (232-1), the present invention is carried out by providing
an address decided uniquely to the user within the range of address
x 224 to address (10 x 224+224-1), or address (172 x 224+ 16 x 216)
to address (172 x 224+ 32 x 2'-6-1) or address (192 x 224+ 168 x 216)
to address (192 x 224+ 169 x 216-1).
A physical communication line can be separated into a
plurality of communication lines and used, this being realized in
conventional art as a multiplex communication method by frame relay
(FR), for example. According to the present invention, the user's
communication line is separated into a user physical communication
line and one or more user logic communication lines. FIG.12
illustrates an example of this aspect, wherein a user physical
communication line 60 is separated into two user logic communication
lines 61 -1 and 61-2. Also, separated computer communication
apparatuses 62-1, 62-2, 62-3 and 62-4 are each connected to
respective user logic communication lines, and the ICS user addresses
"4123, 0025, 0026, 4124" are assigned to each of the computer
communication apparatuses 62-1 throtigh 62-4. The user physical
communication line 60 is connected to the access control apparatus
23
CA 02538190 1997-11-07
63, and the point of contact between the two is called "ICS logic
terminal". The ICS logic terminal is provided with an only ICS
network address within the ICS. In the example showil in FIG.12, the
user logic communication lines 61-1 and 61-2 are connected to the
access control apparatus 63, and ICS network addresses "8710" and
"8711" are assigned to the ICS logic terminals 64-1 and 64-2 of the
contact points, respectively.
As described above, the ICS network server 40 is also
provided with an only ICS network address, so that the ICS network
address can determine that the ICS logic terminal or the ICS network
server is the only one within the ICS. The ICS network server is
capable of exchanging information with other ICS network servers by
means of transmitting and receiving the ICS network frames provided
with each other's ICS network addresses, using IP communication
technology. This function is referred to as a "ICS network server
communication function". The access control apparatus is also
provided with an only ICS network address within the ICS, and is
capable of exchanging information with other ICS servers by means of
a communication function of the ICS network server. The ICS network
server conununication function can be realized by TCP or UDP (User
Datagram Protocol) of a conventional technology.
There are two types of the ICS frames in the present
invention, as described above, the ICS network frame which is
transmitted and received within the ICS, and the ICS user frame
which is transmitted and received outside of the ICS. Each ICS
24
CA 02538190 1997-11-07
network frame is comprised of a control field and a network data
field (ICS user frame), and, as shown in FIG.13, the network control
field is comprised of a besic field and an expansion field, and the
network data field is comprised of a user control field and user data
field, so as to allow usage by ICS encapsulation or ICS reverse
encapsulation. That is, when the ICS user frame eilters the ICS from
the access control apparatus, the ICS user frame becomes a data field
of the ICS network frame, and the control field (network control
field) of the ICS network frame is added thereto (ICS encapsulation).
The expansion field in the network control field is used for the
cipher or the like. In a case that the cipher is useless, the
expansion field is not used.
Inside the network control field of the ICS frame is placed
an area for storing the transmitter's address and intended receiver's
address. There are two types of the ICS frames, those with a 32-bit
address length and-those with a 128-bit address length, and a frame
format with 32-bit address length being employed according to the
RFC791 stipulations shown in FIG.3, for example. In the event that
32 bits is insufficient for the ICS network address, for example, in
the event that a 64-bit address is to be used, following the RFC791
stipulations, the lacking 32 bits (64 bits - 32 bits) are written
into an option field or the expansion field in the network control
field of the ICS network frame control field, thus making the network
address usable at 64 bits. Now, supplemeiltal description will be
made regarding the aforementioned user-specific address. In the
CA 02538190 1997-11-07
event that a great number of users have a private address (a type of
ICS user address) in the section between an address (10 x 224) and an
address (10 x 224 + 224 - 1) for example, in the case that the length
of the ICS user address is 32 bits, the 32 bits is insufficient for
the ICS network address, since the ICS network address is assigned
corresponding to the ICS user address, and 64 bits is required, for
example. In this case, as described above, the lacking 32 bits are
written into the option field of the ICS network frame control field,
thus making the network address usable at 64 bits. The fact that
communication between the same user (called "intra-corporation
communications") is possible using a private address will be
described in the first embodiment. Also, in the event that the
address length is 128 bits, the present embodiment is carried out
under the frame format according to the RFC1883 stipulations such as
shown in FIG.4, for example. The originating address area within the
network control field and the address stored in the destination
address area are made to be ICS network addresses, eacli respectively
being the transmitting ICS ne-twork address and the receiving ICS
network address. Further, the originating address area within the
user control field and the address stored in the destination address
area are made to be ICS user addresses, each respectively being the
sending ICS user address and the receiving ICS user address.
Incidentally, there is no need to following the RFC791 or
RFC1883 stipulations for the ICS frame format in carrying out the
present invention; the present invention can be carried out as long
26
CA 02538190 1997-11-07
as the frame format is such that uses addresses of 32 bits or 128
bits in length. Generally, the ICS receives the ICS user frame
stipulated by RFC791 or RFC1883, but other frame formats can be
handles within the ICS network by converting to ICS user frame with a
conversion means (or changing portion).
Embodiment-1 (Basic ICS, intra-corporation communication and inter-
corporation communication):
A first embodiment of the present invention will be described
with reference to FIGs.14 and 15, regarding a basic communication
wherein the transfer destination within the ICS is determined from
the receiver ICS user address, based on administration by a
conversion table. In the figures, 170-1, 170-2, 170-3 and 170-4
respectively denote gateways provided within the LANs 100-1, 100-2,
100-3 and 100-4, and the ICS frames can pass through these gateways
170-1 through 170-4. FIG.16 shows an example of a conversion table
113-1 in the access control apparatus 111-1 and FIG.17 does the same
of a temporary conversion table 114-2 in the access control
apparatus 110-4.
First, description will be made regarding communication
between a terminal which is connected to a LAN 100-1 of the
corporation X which has a unique address system ADX, and a terminal
which is coniiected to a LAN 100-2 of the same corporation X. That
is, this is a communication between a terminal which has an ICS user
address "0012" on the LAN 100-1 and a terminal which has an ICS user
27
CA 02538190 1997-11-07
address "0034" on the LAN 100-2. This communication is a typical
communication made between terminals which have set addresses based
on a unique address system within a single corporation (ADX in this
example), the communication being made via the ICS 100 in an
interactive manner. This type of communication is referred to as
intra-corporation communication service (or intra-corporation
communication). Next, description will be made regarding a
communication between a terminal which is connected to a LAN 100-1 of
the corporation X which has a unique address system ADX and a
terminal which is connected to a LAN 100-3 of the corporation Y which
has a unique address system ADY. That is, this is a communication
between a terminal which has an ICS user address "0012" on the LAN
100-1 and a terminal which has an ICS user address "1156" on the LAN
100-3. This communication is a typical communication made between
terminals which have different address systems within different
corporations, the communication being made using an ICS address
system which can be shared between the two. This type of
communication is referred to as inter-corporatioii connnunication
service (or inter-corporation communication).
<<Common preparation>>
In describing the present embodiinent, the address format and
so fortll is determined as described below, but the specific numeric
values and formats are all but an example, and the present invention
is by no means limited to these. The ICS network address is
represented by a 4-digit number, and the sender ICS user address and
2 8
CA 02538190 1997-11-07
the receiver ICS user address are both represented by a 4-digit
number. Of the sender ICS user address and the receiver ICS user
address, addresses of which the upper two digits are not "00" are
used as an inter-corporation communication address, and this inter-
corporation communication address is an only value within the ICS
100. Of the sender ICS user address and the receiver ICS user
address, addresses of which the upper two digits are "00" are used as
an intra-corporation communication address, and this intra-
corporation communication address may be duplicate of other intra-
corporation communication address within the ICS 100. Also, the
conversion table 113-1 in FIG.16 provided to the access control
apparatus 110-1 contains the following: transmitting ICS network
addresses, receiving ICS network addresses, sender ICS network
addresses, receiver ICS network addresses, request identification
(ID), speed segments and so forth. The request identification
registered to the conversion table 113-1 is such that, e.g., "1"
represents the intra-corporation communication service, "2"
represents the inter-corporation communication service, and "3"
represents a virtual dedicated line connection (which will be
descrived hereinafter). The speed segment is the line speed that the
communicatioii from the ICS network address requires, including
throughput (e.g., the number of ICS frames sent within a
predetermined time).
<<Preparation for intra-corporation communication>>
The users of the LAN 100-1 and the LAN 100-2 specify the
29
CA 02538190 1997-11-07
terminals and apply to the VAN operator in order that the intra-
corporation communication of the terminals connected to the LANs can
perform the communication via the VAN-1 and VAN-3. The VAN operator
responds to the application and sets the aforementioned ICS network
address, ICS user address, requested identification, etc. to the
conversion tables of the access control apparatuses 110-1 and 110-5
connected to the LAN 100-1 and LAN 100-2, and further writes and
holds them in the ICS address administration server 150-1.
The items to be set for the VAN-1 are as follows. The ICS
network address is decided by the ICS logic terminal of the access
control apparatus 110-1 to which the LAN 100-1 is connected, with the
ICS network address of the ICS logic terminal in this case being set
as "7711". The intra-corporation communication address of the
terminal connected to the LAN 100-1 from which the application was
made is set as "0012", and this is used as the sender ICS user
address. The intra-corporation communication address used by the
terminal of the above address is set as "2212", and this is used as
the sender ICS user address. Next, the intra-corporation
communication address of the terminal connected to the LAN 100-2 froin
which the application was made is decided by the ICS logic terminal
of the access control apparatus 110-5 to which the LAN 100-2 is
connected, in this case t.he ICS network address being set as "9922",
and this is used as the receiving ICS network address. Further, the
ICS user address used by the terminal connected to the LAN 100-2 is
set as "0034", and this is used as the receiver ICS user address.
CA 02538190 1997-11-07
The number "1" is set as the request identification, indicating the
intra-corporation communication service that was applied for, and the
above is registered to the conversion table 113-1 in FIG.16.
The items to be set for the VAN-3 are as follows. Vali.ies
necessary for reverse communication (communication from the LAN 100-2
to the LAN-i) are set to the conversion table of the access control
apparatus 110-5 connecting the LAN 100-2 from which application was
made. That is, data is set reverse to the transmitting ICS network
address and the receiving ICS network address, and at the same time,
data is set reverse to the sender ICS user address and the receiver
ICS user address. The ICS network address of the LAN 100-2 is set as
"9922", and this is used as the transmitting ICS network address.
The address "0034" is set as the sender ICS user address for the
intra-corporation ICS user address of the terminal connected to the
LAN 100-2, and the ICS user address "0012" of the terminal of the
other party is used as the receiver ICS user address. Also, the ICS
user address "7711" of the LAN 100-1 is used as the receiving ICS
network address and the value "1" is set as the request
identification, indicating the intra-corporation conununication
services. The above is written to the conversion table in the access
control apparatus 110-5 and registered.
<<Operation of intra-corporation communication>>
The terminal having an ICS user address "0012" sends an ICS
user frame Pl to the receiver "0034". This ICS user frame P1 has set
as the sender ICS user address "0012", and as the receiver ICS user
31
CA 02538190 1997-11-07
address has set "0034".
The operation will be explained with reference to FIG.18.
The ICS user frame P1 is sent to the access control apparatus 110-1
via the logic communication line 180-1. The access coritrol apparatus
110-1 refers to the conversion table 113-i of FIG.16 from the
transmitting ICS network address "7711" (Steps S100 and S101) and the
receiver ICS user address "0034"of the received ICS user frame, it
knows that the communication is the intra-corporation communication
due to the value "1" of the request identification (Step S102). The
access control apparatus 110-1 obtains that the receiving ICS network
address corresponding to the receiver ICS user address "0034" is
"9922", and then it is ICS-encapsulized (Step S106). The above
procedures illustrated in a flowchart are as shown in FIG.18, with
the intra-corporation being flow (1) therein. The sender ICS user
address may be used to specify the transmitted original of the ICS
frame.
The access control apparaf'us 110-1 sends the ICS network
frame P2 to the relay apparatus 120-1 by the ICS encapsulation.
Since the network address of the network control field is ensured of
its uniqueness within the ICS, there is no conflict with other ICS
frames. The ICS network frame P2 passes through the relay apparatus
120-1 and 120-2 based on the receiving ICS network address, and
reaches the access control apparatus 110-5 of the VAN-3. The access
control apparatus 110-5 removes the network control field from the
ICS network frame P4 and performs the ICS reverse encapsulation, and
32
CA 02538190 1997-11-07
re-creates an ICS user frame P5 which is the same as the ICS user
frame P1 from the network data field of the ICS frame, and sends it
to the LAN 100-2. The ICS user frame is routed through the LAN 100-
2, and is transferred to the termiilal which has the ICS user address
"0034" .
<<Preparation for inter-corporation communication>>
As an example of performing the inter-corporation
communication, a communication between a terminal whicli has an ICS
user address "0012" and is connected to a LAN 100-1 under the address
system ADX, and a terminal which has an ICS user address "1156" and
is connected to a LAN 100-3 under the address system ADY, will be
described. The users of the LANs 100-1 and 100-3 specify the
terminal to the VAN each is connected to so as to be able to perform
the communication via VAN-1 and VAN-2, and make application to the
VAN operator. The VAN operator sets the necessary items in the
conversion table of the access control apparatus wliich is connected
to the LANs 100-1 and 100-3, in accordance with the application.
The items to be set regarding the VAN-1 are as follows. The
ICS network address of the LAN 100-1 is made to be "7711", the intra-
corporation communication address held by the terminal connected to
the LAN 100-1 from which there was application is made to be "0012",
and this is made to be the sender ICS user address. The inter-
corporation communication address provided to the terminal of the
above ICS user address is made to be "2212", and this is made to be
the sender ICS user address (inter-corporation). The ICS network
33
CA 02538190 1997-11-07
address is determined by the ICS logic terminal of the access control
apparatus 110-4 connected to the ICS network address of the LAN 100-3
from which there was application, the ICS network address here being
"8822", and this is made to be the receiving ICS network address.
Also, the ICS user address of a terminal connected to the LAN 100-3
is made to be "1156", and this is made to be the receiver ICS user
address. Further, number "2" is set as the request identification,
indicating the inter-corporation communication service that was
applied for, and the above is registered to the conversion table 113-
1.
The items to be set regarding the VAN-2 are as follows. As a
conversion table for the access control apparatus 110-4 to which the
LAN 100-3 is connected, a temporary conversion table 114-2 which
holds reverse data for a certain time, e.g., 24 hours, is set. That
is, regarding the ICS network address "8822" to which is connected
the LAN 100-3 which uses the inter-corporation communication service,
the following are provided within the access control apparatus 110-4:
a teinporary conversion table 114-2 which includes a transmitting ICS
network address, sender ICS user address, receiver ICS user address,
receiving ICS network address, request identification and so forth.
The setting of the temporary conversion table will be explained
hereinafter.
<<Operation of inter-corporation communication>>
The terminal having an ICS user address "0012" transmits the
ICS user frame Fl in which the sender ICS user address "0012" and the
34
CA 02538190 1997-11-07
receiver ICS user address "1156" are set. The ICS user frame Fl is
transferred to the access control apparatus 110-1 via the user logic
communications line 180-1.
The access control apparatus 1.10-1 refers to the conversion
table 113-1 from the transmitting ICS network address "7711" (Steps
S100 and S101) and the receiver ICS user address "1156", it knows
that the request identification is "2", that is, the communication is
the inter-corporation communication (Step S102). Next, the access
control apparatus 110-1 obtains that the receiving ICS network
address corresponding to the receiver user address "1156" is "8822"
(Step S104), and then converts the sender ICS user address "0012"
into an inter-corporatioiz communication user address "2212" (Step
S105). The access control apparatus 110-1 performs the ICS
encapsulation by adding a network control field as the transmitting
ICS network address "7711", the sender ICS user address "2212", the
receiver ICS user address "1156" and the receiving ICS network
address "8822", and sends it to the relay apparatus 120-1 as the ICS
network frame F2 (Step S106). The above procedures illustrated in a
flowchart are as showii in FIG.18, with the inter-corporation
communication being flow (2) therein.
In the above inter-corporation communication, in the event
that the sender ICS user address within the ICS user frame Fl is made
to be the inter-corporation communication address "2212", the sender
and receiver perform the inter-corporation communication using an
inter-corporation communication address (Steps S102 and S104). In
CA 02538190 1997-11-07
this case, the access control apparatus 110-1 does not perform the
process of converting the sender ICS user address "2212" into the
inter-corporation communication address "2212", as such is not
necessary. The above procedures are illustrated in a flowchart shown
in FIG.18, with the inter-corporation communication as flow (3). The
sender ICS user address may be used to specify the transmitted
original of the ICS frame.
The relay apparatus 120-1 transfers the ICS network frame to
the access control apparatus 110-4 within the VAN-2 via the relay
apparatus 120-2 within the VAN-1, the inter-VAN gateway 130, and the
relay apparatus 120-3 within the VAN-2, based on the receiving ICS
network address. It will be described with reference to FIG.19. The
access control apparatus 110-4 receives the ICS network frame (Step
S110), forms an ICS user frame F5 from the network data field (Step
S1ll: ICS reverse encapsulation), decides from the receiving ICS
network address the ICS logic terminal for sending ((1) in Step
S112), and sends to the LAN 100-3 (Step S113). At the same time, in
the event that the relation among the transmitting ICS network
address "7711", the sender ICS user address "2212", the receiver ICS
user address "1156" and the receiving ICS network address "8822" is
not registered in the conversion table within the access control
apparatus 110-4, a temporary conversion table 114-2 is compiled ((2)
in Step S112). 'I'he registration conterits of the teinporary conversion
table 114-2 are updated accordiiig to a process such as the contents
being deleted if there is no usage thereof for 24 hours. The ICS use
36
CA 02538190 1997-11-07
frame is routed through the LAN 100-3, and is transferred to the
terminal having the ICS user address "1156".
In this embodiment, it is not set in the temporary conversion
table 114-2. In another embodiment of this, the conversion table 113-
1 does not include the sender ICS user address (intra-corporation)
and the sender ICS user address (inter-corporation), and further does
not contain the flowchart (2) in FIG.18, i.e., Step S105. A merit of
this embodiment is that the register number to the conversion table
can be reduced to one of the sender ICS user address if there are the
sender ICS user address for one of the receiver ICS user address.
Embodimeilt-2 (Virtual dedicated line):
Now, description of the operation of virtual dedicated line
connection according to the present invention will be made with
reference to FIG.20. Here, the virtual dedicated line connection
refers to communication wherein the ICS user frame is transferred in
a fixed manner to a receiving ICS network address already registered
in the conversion table, regardless of the ICS user address within
the user control field of the ICS user fraine, in which the format
taken is one-on-one or one-on-N. While the components of FIG.20 are
the same as those of Embodiment-i shown in FIGs.14 and 15, what is
different is the contents of registration in the conversion table
shown in FIG.21. In the conversion table of the access control
apparatus, the receiving ICS network address is determined from the
transmitting ICS network address in a fixed manner, so that either
37
CA 02538190 1997-11-07
the sender ICS user address (intra-corporation), the sender ICS user
address (inter-corporation) and the receiver ICS user address are
either not registered, or ignored if registered.
Description will now be given regarding a case in which the
corporation X uses virtual dedicated line connection, and the
communication is conducted between the LAN 200-1 of the corporation X
which is connected to the access control apparatus 210-1, and the LAN
200-2 of the corporation X which is connected to the access control
apparatus 210-5.
<<Preparation>>
The user applies to the VAN operator for the virtual
dedicated line connection. The VAN operator determines the ICS
network address "7711" of the ICS logic terminal at the connection
point between the access control apparatus 210-1 for connecting the
LAN 200-1 of the corporation X and the user logic communications line
240-1, and similarly determines the ICS network address "9922" of the
ICS logic terminal at the connection point between the access control
apparatus 210-5 for connecting the LAN 200-2 of the corporation X and
the user logic communications line 240-2. Next, the VAN operator
performs setting to the conversion table 213-1 of the access control
apparatus 210-1 of the following: the transmittiilg ICS network
address "7711", the receiving ICS network address "9922" and the
request identification. Illustrated in FIG.21 is an example wherein
the request identification "3" has been made to serve as the virtual
dedicated line connection. Similarly, the VAN operator performs
38
CA 02538190 1997-11-07
setting to the conversion table of the access control apparatus 210-5
of the following: the transmitting ICS network address "9922", the
receiving ICS network address "7711" and the request identification.
<<Procedures>>
The operation will be explained with reference to FIG.22.
The LAN 200-1 of the corporation X sends an ICS user frame F10 to the
ICS 200 via the user logic communications line 240-1. The access
control apparatus 210-1 receives the ICS user frame F10 from the ICS
logic terminal of the ICS network address "7711" (Steps S200 arid
S20].), references to the reqtiest identification "3" of the
originating ICS network address "7711" in the conversion table 213-1,
identifies this as a virtual dedicated line connection (Step S202),.
and reads the receiving ICS network address "9922" (Step S203).
Next, the access control apparatus 210-1 adds a network control field
to the ICS user frame F10 in which the receiving ICS network address
is set to "9922" and the transmitting ICS network address is set to
"7711", thus forming an ICS network frame F11 (Step S204; ICS
encapsulation), and sends the fraine F1.1 to the relay apparatus 200-1
(Step S205). The relay apparatus 220-1 which received the ICS
network frame F11 determines the destination based on the receiving
ICS network address of the ICS network frame F11, and sends an ICS
network frame F12 to the relay apparatus 220-2. The ICS network
frame F12 is transferred to the access control apparatus 210-5 via
the relay apparatus 220-4 within the VAN-3.
The access control apparatus 210-5 removes the network
39
CA 02538190 1997-11-07
control field from the ICS network frame F13 (ICS reverse
encapsulation), and sends the ICS network frame F14 from the ICS
logic terminal of the ICS network address "9922" to the user logic
communications line 240-2. Then, the LAN 200-2 of the corporation X
receives the ICS user frame F14. Transmission can be made in the
same say as described from the LAN 200-2 to the LAN 200-1, and thus,
interactive communication is available. Since it is clear that the
sender and the receiver are not necessary to be the same corporation
X, using the same method, an ICS user frame can be transferred from
the LAN 200-1 of the corporation X to a LAN 200-3 of another
corporation Y.
While the above description has been made with reference to a
case of one-on-one, one-on-N communication can also be performed.
For example, a plurality of ICS network addresses may be set to the
conversion table 213-1 of the access control apparatus 210-1 shown in
FIG.20, as indicated by the transmitting ICS network address "7712".
In the present example, two ICS networlc addresses "6611" aild "8822"
are set. The access control apparatus 210-1, upon receiving the ICS
user fraine from the ICS logic terminal with an ICS network address
"7712", forms a first ICS network frame wherein an ICS network
control field set with "6611" for the receiving ICS ne-twork address
is added thereto, and a second ICS network frame wherein a network
control field set with "8822" for the receiving ICS network address
is added thereto, these being sent to the relay apparatus 220-1.
Consequently, one-on-two communication can be performed. Further,
CA 02538190 1997-11-07
one-on-N communication can be performed by transferring each ICS
network frame in the same manner as described above.
Embodiment-3 (ICS network server):
AS shown in FIG.23, an ICS network server 330 is comprised of
a processing device 331 and an ICS network database 332, the data
held by the ICS network database 332 comprising: question item, type,
contents of answer, and network addresses of other ICS network
servers. The ICS network server 330 analyzes the data portion of the
ICS frames received from the access control apparatus 310-1, refers
to the ICS network database 332 based on this, obtains answer
contents corresponding with the question items (in the event that the
identification is "1"), and sends the obtained answer to the access
control apparatus 310-1. In the event that the ICS network database
332 does not have answer contents corresponding with the question
items (in the event that the identification is "2"), questions
another ICS network server and obtains the answer contents
corresponding with the question items therefrom, using the ICS
network server communication function, based on the ICS network
address of another ICS network server, and sends the answer obtained
thus to the access control apparatus 310-1.
In further detail, the following are registered to the
conversion table 313-1 shown in FIG.24 as preparatory items: the ICS
user address "2000" of the ICS network server 330, the ICS network
address "7721" and the request identification "4". Here, the request
41
CA 02538190 1997-11-07
identification "4" indicates that the ICS user address "2000" is a
number used in common with other users (called an "ICS special
number"), like the telephone number "119" in Japan. Next, it is
written to the ICS network database 332 that the type of the question
Qi is "1" and that the answer contents are "Al", that the type of
question Q2 is "2", the answer contents field is left blank, and the
ICS network address for the other ICS network server 340 is written
as "8844".
Next, the user of the ICS user address "0012" sends an ICS
frame F20 (including question Qi) to the ICS user address "2000" of
the ICS network database 332. The access control apparatus 310-1
receives the ICS user frame F20 from the ICS logic terminal of the
line portion 311-1, obtains the ICS network address "7711",
references the conversion table 313-1, and sends an ICS network frame
which is ICS encapsulated to the ICS network server 320 as
illustrated in the flowchart shown in FIG.26. The ICS network
database 332 finds the answer Al corresponding to the c.F.itstion Ql
contained in the ICS frame F20 (Step S300 and S301), and retur.ns the
answer Al to the access control apparatus 310-1. The access control
apparatus 310-1 sends an ICS frame containing the answer Al to the
ICS user address "0012".
The user of the ICS user address "0012" sends an ICS frame
F21 (including question Q2) to the ICS user address "2000". The
access control apparatus 310-1 refers to the conversion table 313-1,
and upon obtaining the ICS network address "7721", sends an ICS frame
42
CA 02538190 1997-11-07
comprised of the ICS encapsulated frame F21. The ICS network
database 332 recognizes the type "2" corresponding to the question Q2
contained in the ICS frame F21 (Step S300) and knows that the ICS
network database 332 itself does not have the answer (A2).
Therefore, the ICS network database 332 performs information exchange
with another ICS network server 340 using ICS network communication
functions, based on the ICS network address "8844" of the ICS network
server 340 (Step S302), and returns the answer A2 to the access
control apparatus 310-1. The access control apparatus 310-1 sends an
ICS frame containing the answer A2 to the ICS user address "0012".
Embodiment-4 (ICS address administration server):
As shown in FIG.27, the ICS address administration server 430
is connected with via the access control apparatus 410-1 via the ICS
network communication line 460 and holds a correspondence table 432
regarding an ICS network address having an ICS logic terminal at the
line portion 411-1 of the access control apparatus 410-1 and the ICS
user address corresponding thereto. Examples of the conversion table
413-1 aiid the correspondence table 432 are respectively shown in
FIGs.28 and 29. That is, the ICS address administration server 430
holds ICS user addresses "2013", "2014", "1234" and "4500", and the
corresponding ICS network addresses "7711", "7711", "7712" and
"7713". At the same time, all the information to be described in the
conversion table, address related information such as records dealing
with VAN operation may be included, as well. Further, the ICS
43
CA 02538190 1997-11-07
address administration server 430 holds the ICS network addresses of
a plurality of other ICS address administration servers, and the ICS
network addresses of a plurality of ICS name servers. Also, the ICS
address administration server 430 is capable of communicating using
the ICS name server described in Embodiment-5 and the ICS network
server communication function, thus obtaining ICS names corresponding
with ICS user addresses.
The processing device 412-1 of the access control apparatus
410-1 can perform the communication with the ICS address
administration server 430 using the ICS network server communication
function, and disclose the value of the ICS network address and have
the corresponding ICS user address, or disclose the value of the ICS
user address and have the corresponding ICS network address. The
operation will be explained with reference to FIG.30. The ICS
address administration server 430 checks or not whether the ICS
network address or the'ICS user address questioned from the access
control apparatus server 410-1 is registered in its correspondence
table 432 (Step S400), and answers a reply if it is registered (Step
S401). If the ICS network address or the ICS user address is not
registered in the correspondence table, the ICS address
administration server 430 communicates with another ICS address
administration server 440 using the ICS network server communication
function, thus obtaining the ICS user address or the ICS network
address (Step S402), the results thereof being replied to the access
control apparatus 410-1 (Step S403). According to such a
44
CA 02538190 1997-11-07
configuration, the access control apparatus 410-1 is able to request
of the ICS address administration server 430 and to obtain one of the
ICS network address or ICS user address based on the otller.
Embodiment-5 (ICS name server):
The ICS user address is problematic in that it is a 32-bit
binary expression or 128-bit binary expression for example, and thus
is difficult to remember. There is a method wherein an "ICS name"
which is easily remembered, is used.
First, description will be made regarding the ICS name. The
ICS address expressed in binary form is, as shown in FIG.11,
expressed by e.g., a district administration code, country code, VAN
code, VAN district code, VAN access point code, and user logic code,
witli these ntuneric values being arrayed to form an expression such as
district administration code II country code II VAN code II VAN district
code II VAN access point code II user logic code. In the ICS name, the
district administration code which can be expressed in the binary
form as described above, for example, is expressed as follows: AS (an
ICS name component which indicates Asia), JP (Japan), VAN#1
(identification of a VAN), DIS#1 (identification of a VAN district
code which comprises the VAN#1), ACS#1 (identification of a VAN
access point code restricted by the DIS#1), USR#1 (identification of
a user logic code). The components of the ICS name thus decided are
reversed and separated by dots ".", thus forming the ICS name
"USR#1.ACS#l.DIS#1.VAN#1.JP.AS". In the above-described case, this
CA 02538190 1997-11-07
ICS name may be even further divided, so that the USR#1 is divided
into USR#10 and COMP#10, and ACS#1 is divided into ACS#11 and ACS#12,
thus giving the overall ICS name "USR#10.COMP#10.ACS#11.ACS#12.DIS#1.
VAN#1.JP.AS".
The ICS name server, which is a type of ICS network server,
will now be described. As shown in FIG.31, the ICS name server 550
is made up of a processing device 551 and an ICS name conversion
table 552, with the ICS name conversion table 552 being comprised of
e.g., ICS name, type (identification of existence of an ICS user
address corresponding to the ICS name), ICS user address and so
forth. The type "2" indicates that the ICS network database 332 does
not hold an ICS network address corresponding to the ICS name, and
thus the ICS network address corresponding to the ICS name is to be
obtained'from another ICS name server. An example of the conversion
table 513-1 is shown in FIG.32. Here, another ICS name server
administrating the ICS name "USR#2.ACS#2.DIS#2.VAN#2. JP.AS" can be
called up "DIS#2.VAN#2.JP.AS" with "USR#2" and "ACS#2" removed. The
ICS name server 550 analyzes the ICS frame data field received from
the access control apparatus 510-1, refers to the ICS name conversion
table 552 based on the above analysis, obtains an ICS user address
corresponding to the ICS name, and sends it to the access control
apparatus 510-1. Further based on the ICS user address, a reply is
made regarding the ICS name corresponding tliereto. In the event that
an ICS user address corresponding thereto does not exist within the
ICS name conversion table 552, the ICS network communication function
4 G
CA 02538190 1997-11-07
is used to request the questioned ICS user address from another ICS
name server which has the ICS user address, and the ICS user address
obtained therefrom is sent to the access control apparatus 510-1.
Now, description will be made the method whereby the terminal
of the sender ICS user address "0012" connected to the LAN 500-i
obtains an ICS user address corresponding to the ICS name #1 "USR#1.
ACS#1.DIS#1.VAN#1.JP.AS". Here, two cases will be described: that
wherein the access control apparatus 510-1 obtains data from the ICS
naine server 550, and that wherein the access control apparatus 510-1
obtains data from another ICS name server 560.
First, in preparation, an ICS network address "7741"
corresponding to the ICS user address "1000" of the ICS name server
550, and a request identification "4" thereof are registered in the
conversion table 513-1 of the access control apparatus 510-1. Here,
the request number "4" indicates that asthe ICS user address "1000"
is the telephone number "119", it is a special ICS number to be
common to another user. The receiver ICS user address "2014"
corresponding to the ICS name "USR#l.ACS#1.DIS#l.VAN#i. JP.AS" is
registered in the ICS name conversion table 552 of the ICS name
server 550. Then, the terminal user of the sender ICS user address
"0012" of the LAN 500-1 sends an ICS user frame F40 to the access
control apparatus 510-1, and requests a conversion from the ICS name
#1 "USR#1.ACS#1.DIS#1.VAN#1.JP.AS" to an ICS user address. The
processing device 512-1 within the access control apparatus 510-1
receives the ICS user frame F40 from the ICS logic terminal in the
47
CA 02538190 1997-11-07
line portion 511-i, obtains the ICS network address "7711" and then
refers to the conversion table 513-1 based on the receiver ICS user
address of the ICS user frame F40. If the corresponding request
identification is "4" (connection to an ICS name server of the ICS
special number), the processing device 512-1 performs the ICS
encapsulation of the ICS user frame F40 by using the obtained ICS
network address "7711", and sends an ICS network frame including an
ICS name to the ICS name server 550.
As shown in FIG.34, the ICS name server 550 analyzes the ICS
name within the ICS frame received from the access control apparatus
510-1 with the processing device 551, and refers to the ICS name
conversion table 552 (Step S500). Then, in the event that an ICS
user address corresponding to the ICS name exists within the ICS name
conversion table 552, the ICS user address is.obtained, and the ICS
network frame F45 including the ICS user=address "2014" is sent to
the aqcess control apparatus 510-1 (Step S501). In the event that
the questioned ICS name does not exist within*the ICS name conversion
table 552, the access control apparatus 512-1 receives an ICS user
frame F41 for example, and in the event that the ICS name #2 (i.e.,
"USR#2.ACS#2.DIS#2.VAN#2.JP.AS") described in the ICS user frame F41
is not described in the ICS name conversion table 552, the ICS name
server 550 obtains the ICS network address of another ICS name server
from the ICS name conversion table 552 based on the ICS name (i.e.,
"DIS#2.VAN#2.JP.AS"), and then obtains the ICS user address "1130"
corresponding to the questioned ICS name, by means of performing an
48
CA 02538190 1997-11-07
information exchange by using the ICS name server 560 and the ICS
network server communication function (Step S502). The obtained
result is sent to the access control apparatus 510-1 (Step S503).
The access control apparatus 510-1 exchanges informations with the
ICS address administration server 570 based on the receiver ICS user
address which is received from the ICS name server 550 and is
described in the ICS network frame F45, obtains the ICS network
address corresponding to the ICS user address and the address related
information contained in the correspondence table, and writes the
data comprised of the obtained ICS user address, ICS network address
and address-related information, to the conversion table 513-1. The
access control apparatus 510-1 sends the ICS user address "2014" (or
"1130") obtained from the ICS name server 550 to a ter.minal user of
the sender ICS user address "0012" of the LAN 500-1. The ICS user
address "0012" is written in the ICS network frame F45. The terminal
user of the sender ICS user address "0012" of the LAN 500-1 obtains
the receiver ICS user address "2014" (or "1130") obtained from the
access control apparatus 510-1.
Embodiment-6 (ICS name server):
In Embodiment-5, the access control apparatus 510-1 does not
write the data such as the obtained ICS user address, the ICS network
address and so on to the conversion table 513-1, but rather writes
this obtained data to a temporary conversion table 514-1. In this
case, the aforementioned address written to this temporary conversion
49
CA 02538190 1997-11-07
table are deleted after 24 hours, for example.
Embodiment-7 (ICS name server):
In Embodiment-5, the access control apparatus 510-1 does not
call up the address administration server 570 and only performs
service of telling the obtained ICS user address "2014" (or "1130")
to the terminal of the ICS user address "0012".
Embodiment-8 (hccounting server):
There are three types of charging systems: the "network
charging system" wherein the charging is performed by counting ICS
user frames to be sent or received wlien a communication is made, the
"information charging system" wlierein the charging is performed by
counting the transferred information in the ICS user frame, and the
"fixed charging system" wherein no charging is performed regarding
the transferred ICS user frames, but a constant amount is charging
for a certain period (month, year, etc.) of a time when the
registration of the ICS user address or the like continues in the
conversion table of the access control apparatus. The information
charging system counts and charges by designating the identification
which indicates the information charging to the user control field of
the ICS user frame. The network charging system and the information
charging system are "transmitting account" if the transmitter of the
communication bears the charges, and are "receiviilg account" if the
receiver does. Each of the network charging system and the
CA 02538190 1997-11-07
information charging system is called as "charge-by-qiiantity charging
system".
<<Configuration>>
The charging system in the ICS network according to the
present invention will be explained with reference to FIGs.35 and 36.
Each example of the conversion table 813-1, the definition table for
fixed charges 843 and the account information database 842 are
respectively shown in FIG.37, FIG.38 and FIG.39.
Setting information of the charging system is held in the
conversion table 813-1 in the access control apparatus 810-1 and the
definition table for fixed charges 843 in the account server 840, and
a set value indicating the network charging or the information
charging and a set value indicating the charge-by-quantity charging
system (identify the transmitting account and the receiving account)
or the fixed charging system (identify the transmittiiig account and
the receiving account) are held in the conversion table 813-1. The
operation will be explained with reference to FIG.40. The access
control apparatus 810-1 receives the ICS user frame F50 (Step S800),
and reads out the type of charging system for each ICS frame held in
the conversion table 813-1 us read out based on the ICS user address
contained in the ICS user frame F50 and checks up the account
condition (Step S801). The access control apparatus 810-1 forms the
account information in the event that the read type indicates the
charge-by-quantity charging system, and transfers the accotmt
information in the form of an account information frame F51 to the
51
CA 02538190 1997-11-07
account server 840 which is one of the ICS network servers (Step
S810). However, in the event that the read type indicates the fixed
charging system, no formation of account information not transferring
the account information in the form of an account information frame
F51 to the account server 840 is performed (Step S820).
The account server 840 receives the account information frame
F51 sent from each of the access control apparatuses, and stores the
account information contained within the account i.nformation frames.
There is an account processing device 841 and an account information
database 842 witliin the account server 840, whereby the account
processing device 841 receives the accounting information frame F51
sent from the access control apparatus 810-1, analyzes the account
information contained within the account information frame F51, and
stores the information in the account information database 842. The
account information database 842 uses the ICS network address and the
ICS user address as identifiers, and stores the account information
as a database. Also, in the event that the charging system is the
charge-by-quantity charging system, the account information database
842 stores the information regarding the quantity in the form of a
count number, which the count number may be set with an upper limit,
and in the event that the count exceeds the set upper limit, the
account server 840 notifies to the access control apparatus 810-1
that the upper limit has been exceeded, and the access control
apparatus 810-1 which receives the no-tification terminates the
communication of the user. The account server 840 is capable of.
52
CA 02538190 1997-11-07
handing the stored account information to other VANs and users using
the ICS network server communication function.
(1) Example of communication with an arrangement of network
charging, transmitting charging and charge-by-quantity charging
system:
Description will be made regarding a case wherein the
corporation X and the corporation Y perform inter-corporation
communication using the ICS 800 according to the present invention.
In this case, the charging system for the LANs 800-1 and 800-3 is the
charge-by-quantity charging system for the network charging, with the
entire bill being borne by the LAN 800-1, and no information charging
being conducted.
<<Preparations to make for communication>>
The LANs 800-1 and 800-3 are each connected to the respective
access control apparatuses 810-1 and 810-4.
<<Preparations to make for charging>>
The charging condition for the LANs 800-1 and 800-3 which are
to conduct the communication is registered in the conversion table
813-1. The charging conditions are set for registering in the
conversion table 813-1 based on the transmitting ICS network address,
the receiver ICS user address, the receiving ICS network address, and
the receiver ICS user address. A value "1" is set to indicate that
network charging is to be conducted by charge-by-quantity charging
with transmitting charging. Also, a value "1" is set for the
charging unit price. Since the information charging is not to be
3
CA 02538190 1997-11-07
performed, a value "0" indicating non-charging is set to the charging
conditions in the information charging condition of the conversion
table 813-1. A value "0" indicating the fixed charging system is set
in the conversion table of the access control apparatus 810-4
containing the LAN 800-3, to keep the access control apparatus 810-4
from performing the account processing, since the LAN 800-1 is to be
billed.
<<Description of operation of charging>>
Regarding the ICS user frame F50 sent from the terminal of
the ICS network address "0012" connected to the LAN 800-1, the
charging condition fields are specified from the sender ICS user
address and the receiver ICS user address in the ICS user frame at
the processing device 812-1 within the access control apparatus 810-i
(Steps S800 and S801), and a reference is made to the charging
conditions in order to specify the charging system relating to the
network charging from the field (Step S810). Since this is "1"
indicating that the charging system is the charge-by-quantity
charging and that transmitting charging is to be performed, the
charging unit price is referred to (Step S811), the charging
information is formed (e.g., charging unit price "1" is formed as one
unit of charging information) (Step S812), and that charging
information is transferred to the account server 840 in the form of
an account information frame F51 (Step S813). In the account
processing device 841 within the account server 840, the network
account counter of the account information database 842 is
54
CA 02538190 1997-11-07
incremented, according to the charging information within the account
information frame F51 received from the access control apparatus 810-
1 (Step S814). In the event that the charging conditions is neither
in examples described later, the charging described here is
performed.
(2) Example of communication with an arrangement of network
charging, transmitting charging and fixed charging system:
Description will be made regarding a case wherein the
corporation X performs the intra-corporation communication using the
ICS 800 according to the present invention. In this case, the
charging system for the LANs 800-1 and 800-2 is the fixed charging
system for the network charging, with the entire bill being borne by
the LAN 800-1, and no information charging being conducted.
<<Preparations to make for communication>>
The LANs 800-1 and 800-2 are each connected to the respective
access control apparatuses 810-1 and 810-5.
<<Preparations to make for charging>>
The charging condition for the LANs 800-1 and 800-2 which are
to conduct the communication is registered in the conversion table
813-1. The charging conditions are set for registering in the
conversion table 813-1 based on the transmitting ICS network address,
the sender ICS user address, the receiving ICS network address and
the receiver ICS user address. A value "0" is set to indicate that
network charging is to be conducted by the fixed charging system, and
also, a value "1" indicating the transmitting charging is set to
CA 02538190 1997-11-07
billing bearing of the definition table for fixed cliarges 843,
indicating the party bearing the charges. Since the information
charging is not to be performed, a value "0" indicating non-charging
is set to the chargiilg conditions in the information cliarging
condition of the conversion table 813-1. A value "0" indicating the
fixed charging system is set in the conversion table of the access
control apparatus 810-5 containing the LAN 800-2.
<<Description of operation of charging>>
Regarding the ICS user frame sent from the terminal of the
ICS network address "0012" connected to the LAN 800-1, the charging
condition fields are specified from the sender ICS user address and
the receiver ICS user address and in the ICS user frame at the
processing device 812-1 within the access control apparatus 810-1
(Steps S800 and S801), and a reference is made to the charging
conditions in order to specify the charging system relating to the
network charging from the field (Step S810). Since this is "0"
indicating that the charging system is fixed charging, no charging
processing such as forming the charging information is performed
(Step S820). The processing for billing is performed with reference
to the definition table for fixed charges 843. That is, billing is
performed to the LAN 800-1, since the value "0" indicating
transmitting cliarging is set to the definition table for fixed
charges 843.
(3) Example of communication with an arrangement of network
charging, receiving charging and charge-by-quantity charging system:
56
CA 02538190 1997-11-07
Description will be made regarding a case wherein the
corporation X and the corporation Y perform inter-corporation
communication. In this case, the charging system for the LANs 800-1
and 800-3 is the charge-by-quantity charging system for network
charging, with the entire bill being borne by the LAN 800-3, and no
information charging being conducted.
<<Preparations to make for communication>>
The LANs 800-1 and 800-3 are each connected to the respective
access control apparatuses 810-1 and 810-4.
<<Preparations to make for charging>>
The charging condition for the LANs 800-1 and 800-3 which are
to conduct the communication is registered in the conversion table
813-1. The charging conditions are set for registering in the
conversion table 813-1 based on the transmitting ICS iietwork address,
the sender ICS user address, the receiving ICS network address and
the receiver ICS user address. A value "2" is set to indicate that
network charging is to be conducted by the charge-by-quantity
cliarging system, and also, a value "1" is set for the charging unit
price. Since the information charging is not to be performed, a
value "0" indicating non-charging is set to the charging conditions
in the information charging condition of the conversion table 813-1.
A value "2" indicating the charge-by-quantity charging system and the
receiver charging is set to the conversion table of the access
control apparatus 810-4 containing the LAN 800-3, since the LAN 800-3
is to be billed.
57
CA 02538190 1997-11-07
<<Description of operation of charging>>
Regarding the ICS user frame sent from the terminal of the
ICS network address "0012" connected to the LAN 800-1, the charging
condition fields are specified from the sender ICS user address and
the receiver ICS user address in the ICS user frame at the processing
device 812-1 within the access control apparatus 810-1 (Steps S800
and S801), and a reference is made to the charging conditions in
order to specify the charging system relating to the network charging
from the field (Step S810). Since this is "2" indicating that the
charging system is charge-by-quantity and that the receiving charging
is to be performed, the charging information is formed (e.g.,
charging unit price "1" is formed as two units of the charging
information), and that the account information frame is transferred
to the account server 840. In the account processing device 841
within the account server 840, the network account counter of the LAN
800-3 of the account information database 842 is incremented,
according to the charging information within the account information
frame received from the access control apparatus 810-4.
(4) Example of communication with an arrangement of network
charging, receiving charging and fixed charging system:
Description will be made regarding a case wherein the
corporation X performs intra-corporation. In this case, the charging
system for the LANs 800-1 and 800-2 is the fixed charging system for
the network charging, with the entire bill being borne by the LAN 800-
2, and no information charging being conducted.
58
CA 02538190 1997-11-07
<<Preparations to make for communication
The LANs 800-1 and 800-2 are each connected to the respective
access control apparatuses 810-1 and 810-5.
<<Preparations to make for charging>>
The charging condition for the LANs 800-1 and 800-2 which are
to conduct the communication is registered in the conversion table
813-1. The charging conditions are set for registering in the
conversion table 813-1 based on the transmitting ICS network address,
the receiver ICS user address, the receiving ICS network address, and
the receiver ICS user address. A value "0" is set to indicate that
network charging is to be conducted by fixed charging, and also, a
value "2" indicating receiving charging is set to billing bearing of
the definition table for fixed charges 843, indicating the party
bearing the charges. Since the information charging is not to be
performed, a value "0" indicating non-charging is set to the charging
conditions in the information charging condition of the conversion
table 813-1. A value "0" indicating the fixed chargiiig system is set
to the conversion table of the access control apparatus 810-5
containing the LAN 800-2.
<<Description of operation of charging>>
Regarding the ICS user frame sent from the terminal of the
ICS network address "0012" connected to the LAN 800-1, the charging
condition fields are specified from the sender ICS user address and
the receiver ICS user address in the ICS user frame at the processing
device 812-1 within the access control apparatus 810-1 (Steps S800
59
CA 02538190 1997-11-07
and S801), and a reference is made to the charging conditions in
order to specify the charging system relating to the network charging
from the field (Step S810). Since this is "0" indicating that the
charging system is fixed charging, no charging processing such as
forming charging information is performed (Step S820). The
processing for billing is performed with reference to the definition
table for fixed charges 843. That is, billing is performed to the
LAN 800-2, since a value "2" indicating transmitting billing is set
to the definition table for fixed charges 843.
(5) Example of communication with an arrangement of information
charging, transmitting charging and charge-by-quantity charging
system:
Description will be made regarding a case wlierein the
corporation X and the corporation Y perform the communication. Iri
this case, the charging system for the LANs 800-1 and 800-3 is the
information charging, with no network charging being conducted. The
entire bill is borne by the LAN 800-1.
<<Preparations to make for communication>>
The LANs 800-1 and LAN 800-3 are each connected to the
respective access control apparatuses 810-1 and 810-4.
<<Preparations to make for charging>>
For the charging conditions for the network charging
conditions, a value "0" indicating non-cllarging is set in the
conversion table 813-1, and since charging itself is not performed,
there is no setting of the charging unit price. A value "3" is set
6 0
CA 02538190 1997-11-07
to indicate that informatioii charging condition is to be conducted by
charge-by-quantity charging and transmitting charging. Also, a value
"2" is set for the charging unit price.
<<Description of operation of charging>>
Regarding the ICS user frame sent from the terminal of the
ICS network address "0012" connected to the LAN 800-1, the charging
condition fields are specified from the seiider ICS user address and
the receiver ICS user address in the ICS user frame at the processing
device 812-1 within the access control apparatus 810-1 (Steps S800
and S801), and a reference is made to the charging conditions in
order to specify the charging system relating to the network
communication from the field (Step S810). Since this is "0"
indicating non-charging is set, network charging is not performed
(Step S820). Next, a reference is made to the charging conditions of
the information charging conditions, in order to specify the
conditions of charging related to the information charging. In this
case, a value "1" is set which indicates charging-by-quantity which
is to be borne by the transmitter, so the charging-by-quantity
charging is performed. Also, the chargirig unit price which indicates
the weighting of this charging-by-quantity is referred to, which in
the case is set at a value of "2". Next, based on the obtained
information, the charging information for each ICS user frame is
formed (e.g., charging unit price "2" is formed as two units of the
charging information), and that the charging information is
transferred to the account server 840 in the form of an account
61
CA 02538190 1997-11-07
information frame F51. The account processing device 841 withiii the
account server 840 which received the charging information specifies
the information storage field of the account information database 842
based on the transmitting ICS network address, the sender ICS user
address, the receiving ICS network address and the receiver ICS user
address from the account information frame F51, and the network
account counter is incremented according to the cllarging information
within the account information frame F51.
(6) Example of communication with an arrangement of information
charging, receiving charging and charge-by-quantity charging system:
Description will be made regarding a case wherein the
corporation X and the corporation Y perform the inter-corporation
communication. In this case, the charging system for the LANs 800-1
and 800-3 is the charge-by-quantity charging system for the
information charging, and no network charging being conducted. The
entire bill is borne by the LAN 800-3 which is a receiver.
<<Preparations to make for communication>>
The LANs 800-1 and 800-3 are each connected to the respective
access control apparatuses 810-1 and 810-4.
<<Preparations to make for charging>>
For the charging conditions for network cllarging conditions,
a value "0" indicating non-charging is set in the conversion table
813-1, and since charging itself is not performed, there is no
setting of the charging unit price. A value "2" is set to the
information charging conditions to indicate that information charging
62
CA 02538190 1997-11-07
condition is to be conducted by charge-by-quantity charging and
transmitting charging. Also, a value "2" is set for the charging
unit price.
<<Description of operation of charging>>
Regarding the ICS user frame sent from the terminal of the
ICS network address "0012" connected to the LAN 800-1, the charging
condition fields are specified from the sender ICS user address and
the receiver ICS user address and in the ICS user frame at the
processing device 812-1 within the access control apparatus 810-1
(Steps S800 and S801), and a reference is inade to the charging
conditions in order to specify the charging system relating to the
network communication from the field (Step S810). Since this is "0"
indicating non-charging is set, network charging is not performed
(Step S820). Next, a reference is made to the charging conditions of
the information charging conditions, in order to specify the
conditions of charging related to the information charging. In this
case, a value "2" is set which indicates the charging-by-quantity
charging which is to be borne by the receiver, so the charging-by-
quantity charging is performed. Also, the charging unit price which
indicates the weighting of the charging-by-quantity charging is
referred to, which in this case is set at a value of "2". Next,
based on the obtained information, the charging information for each
ICS user frame is formed (e.g., charging unit price "2" is formed as
two units of the charging information), and that the charging
information is transferred to the account server 840 in the form of
6 3
CA 02538190 1997-11-07
an account information frame F51. The account processing device 841
within the account server 840 which received the charging information
specifies the information storage field of the account information
database 842 based on the transmitting ICS network address, the
sender ICS user address, the receiving ICS network address and the
receiver ICS user address from the account information frame F51, and
the network account counter is incremented according to the charging
information within the account information frame F51.
(7) Example of communication with an arrangement of information
charging, transmitting charging and charge-by-quantity charging
system, wherein the charging conditions have not been registered in a
conversion table beforehand:
Description will be made regarding a case wherein the
corporation X and the corporation Y perform a communication. The
charging conditions for a communication between the LANs 800-1 and
800-3 are the same as described above, but there is a difference in
this case in that values for stipulating the charging conditions are
not registered in the conversion table 813-1 of the access control
apparatus 810-1 connected to the LAN 800-1.
<<Preparations to make for communication>>
The LANs 800-1 and 800-4 are each connected to the respective
access control apparatuses 810-1 and 810-2.
<<Preparations to make for charging>>
In this case, there are no charging conditions registered in
the conversion table 813-1, so there is no need to make a preparation
64
CA 02538190 1997-11-07
in the access control apparatus 810-1 containing the LAN 800-1. The
receiving charging conditions for the LAN 800-4 are set in the
conversion table in the access control apparatus 810-2 containing the
LAN 800-4. A value "0" indicating non-charging is set to the
charging conditions in the information charging conditioii of the
conversion table 813-1. Since the charging itself is not performed,
there is no setting of the charging.unit price. A value "3" is set
to the information charging conditions to indicate that the
information charging is to be conducted by the charge-by-quantity
charging and the transmitting cliarging. Also, a value "1" is set for
the charging unit price.
<<Description of operation of charging>>
Regarding the ICS user frame sent from the terminal of the
ICS network address "0012" connected to the LAN 800-1, specification
of the charging condition fields is attempted using the sender ICS
user address, and the receiver ICS user address in the ICS user frame
from the conversion table 813-1 at the processing device 812-1 within
the access control apparatus 810-1 (Steps S800 and S801), but since
there are no fields indicating the pertinent charging conditions in
this case, a contact is made with the access control apparatus 810-4
containing the receiver user, based on the receiver ICS user address
of the receiver user (Step S802). The access control apparatus 810-4
refers to the charging conditions of the receiver user with the
conversion table in the access control apparatus 810-4, and replies
of the charging conditions to the access control apparatus 810-1.
6 5
CA 02538190 1997-11-07
The charging conditions which the access control apparatus 810-1 has
obtained from the access control apparatus 810-4 are registered in a
temporary conversion table 814-1 (Step S803). Subsequently, a
reference is made in the processing device 812-1 to the charging
conditions in order to specify the charging conditions relating to
the network communication from the charging conditions. Since this
is "0" indicating non-charging is set, network charging is not
performed (Step S820). Next, a reference is made to the charging
conditions of the information charging conditions, in order to
specify the conditions of charging related to the information
charging. In this case, a value "1" is set which indicates charging-
by-quantity which is to be borne by the transmitter, so the charging-
by-quantity charging is performed. Also, the charging unit price
which indicates the weighting of the charging-by-quantity charging is
referred to, which in this case is set at a value of "1", and thus
the weighting of this charging is known. Next, based on the obtained
informatioii, the charging information for each ICS user frame is
formed (e.g., charging unit price "1" is formed as one unit of the
charging information), and that the chargiiig information is
transferred to the account server 840 in the form of an account
information frame F51. The account processing device 841 within the
account server 840 which received the charging information specifies
the information storage field of the account information database 842
based on the transmitting ICS network address and the receiver ICS
user address from the account information frame F51, and the network
66
CA 02538190 1997-11-07
account counter is incremented according to the account information
within the account information frame F51.
Embodiment-9 (ICS frame database server):
FIGs.41 and 42 show an example of an ICS 900 which includes
ICS frame database servers 950 and 960 which are a type of ICS
network servers. The ICS frame database servers 950 and 960 store
data based on requested timing from the side of the terminals
(hereafter referred to as "ICS-using terminal") using the ICS 900, or
removes the stored data and sends the data to the requester. The ICS
frame database servers 950 and 960 are respectively comprised of
processing devices 951 and 961, storage information administration
tables 952 and 962, and BOXs 953 and 963. Examples of storage
information administration tables 952 and BOX 953, and storage
information administration tables 962 and BOX 963 are respectively
shown in FIGs. 43 and 44.
The processing devices 951 and 961 receive ICS user frames
from the ICS-using terminals, refer to the usage requests of ICS
frame database servers explicitly indicated by the ICS-using
terminals, perform storage commanding of the ICS user frames to the
storage information administration tables 952 and 962, and perform
storage instruction of information to the BOXs 953 and 963. The
storage information administration tables 952 and 962, upon receiving
the instruction from the processing devices 951 and 961, store itenis
regarding which administration is necessary for each separate ICS-
67
CA 02538190 1997-11-07
using terminal, such as the index number of stored information. The
BOXs 953 and 963, upon receiving the instruction from the processing
devices 951 and 961, store administration number of stored
information for each separate ICS-using terminal, user information
and so forth. The following is a description of the preparatory
items for using ICS frame database servers 950 and 960 and examples
of communication therewith.
<<Preparatory items>>
The operator of the VAN-1 registers the information (in the
present embodiment, ICS user address "0012", etc.) regarding the user
in the storage information administration table 952 and the BOX 953
beforehand, so that the storage of information can be performed for a
terminal having the ICS user address "0012", being connected to the
LAN 900-1 of the corporation X. Also, in the same way, the operator
of the VAN-3 registers the informatiori (in the present embodiment,
ICS user address "0034", etc.) regarding the user in the storage
information administration table 962 and the BOX 963 beforehand, so
that the storage of information can be performed for a terminal
having the ICS user address "0034", being connected to the LAN 900-2
of the corporation X. The ICS-using user sends an ICS user frame F60
as shown in FIG.45 to the ICS 900. This ICS user frame F60 is
provided with the following to the user control field tllereof: a
usage request identifier (an identifier which explicitly indicates
using the ICS frame database server) for using the ICS frame database
server, and an information operating identifier (an identifier which
68
CA 02538190 1997-11-07
explicitly indicates operation of information stored in the ICS frame
database server). Incidentally, although the description of -the
present embodiment involves the user attaching the usage request
identifier and the information operating identifier to the user
control field of the ICS user frame F60, thus achieving the usage
request of the ICS frame database server by the user, but the usage
request identifier and the information operation identifier may be
attached to the ICS user data field, instead.
<<Examples of communication>>
(1) Communication example-1 (Operation of the ICS frame database
server on the sending side):
A terminal which is connect-ed to the LAN 900-1 of the
corporation X and has an ICS user address "0012" performs a
communication to a terminal which is connected to the LAN 900-2 of
the corporation X and has an ICS user address "0034", using the ICS
franie database server. A flowchart is shown in FIG.46, describing
the operation thereof.
The transmitter terminal sends an ICS user frame F60 for
using the ICS frame database server 950 to the ICS 900, the ICS user
frame F60 being provided at the user control field with a usage
request identifier (transmitting storage user administration number:
a code which the user using the ICS provides optionally, used as a
search index number in the event that the ICS user operates the
stored information) and an infbrmation operating identifier (transfer
schedule time, information storage, information transfer, information
69
CA 02538190 1997-11-07
elimination, information completion, etc.). The access control
apparatus 910-1 received this (Step S900) refers to the usage request
identifier of the ICS user frame F60 at the processing device 912-1
(Step S901), and in the event that the number of the user request
identifier set by the transmitter terminal exists, the ICS user frame
F60 is transferred to the processing device 951. The processing
device 951 received the ICS user frame F60 refers to the usage
request identifier and the information operating identifier (Step
S910), and executes the operation indicated in the information
operating identifier.
In the event that information storage is indicated, the
processing device 951 receives the usage request identifier
(transmitting storage user administration number) and the information
operating identifier (information storage) of the ICS user frame F60
sent from the transmitter terminal, thereby storing the receiver ICS
user address and the usage request identifier in the storage
information administration table 952 corresponding to the sender ICS
user address of the frame, and then stores the ICS user data frame in
the BOX 953 (Step S911). Since the user frame to be stored is sent
from the transmitter in the form of being divided into a plurality of
ICS user frames, this operation is performed until the last frame of
the ICS user frames to be stored is indicated, by means of the
information operation identifier (information completion) indicated
in the ICS user frame F60 (Step S912)
In the event that the transfer schedul time is indicated
CA 02538190 1997-11-07
(Step S913), the processing device 951 receives the usage request
identifier (transmitting storage user administration number) and the
information operating identifier (transfer schedule time) of the ICS
user frame F60 sent from the transmitter terminal, thereby storing
the specified time in the storage information administration table
952 (Step S914), and the processing device 951 also transfers the
information stored in the BOX 953 to the receiver terminal at a pre-
determined time, by means of constantly monitoring the transfer
schedul time (Step S915).
In the event that the information transfer is indicated, the
processing device 951 receives the usage request identifier
(transmitting storage user administration number) and the information
operating identifier (transfer request) of the ICS user frame F60
sent from the transmitter terminal, thereby sending the information
(ICS user frame) stored in the BOX 953 to the receiver terminal (Step
S916). Also, in.the event that the information elimination is
indicated, the processing device 951 receives the usage request
identifier and the information operating identifier (information
elimination) of the ICS user frame F60 sent from the transmitter
terminal, thus eliminating the information stored in the storage
information administration table 952 and the BOX 953 (Step S917).
(2) Communication example-2 (Operation of the ICS frame database
server on the receiving side):
A terminal which is connected to the LAN 900-2 of the
corporation X and has an ICS user address "0034" receives a
71
CA 02538190 1997-11-07
communication from a terminal which is connected to the LAN 900-1 of
the corporation X and has an ICS user address "0012", using the user
BOX. A flowchart is shown in FIG.47, describing the operation
thereof.
The transmitter terminal sends an ICS user frame F60 for
using the receiver side ICS frame database server 960 to the ICS 900,
the ICS user frame F60 being provided at the user control field with
a usage request identifier (receiving storage user administration
number: a code which the user using the ICS provides optionally, used
as an index ninnber in the event that the ICS user operates the stored
information) and the information operating identifier. The ICS user
frame F60 is sent through the ICS 900 to the access control apparatus
910-5 containing the receiver terminal (Step S920). The processing
device 912-5 refers to the usage request identifier of the ICS user
frame F60 (Step S921), and if the number of the usage request
identifier set by the transmitter terminal exists, transfers the ICS
user frame F60 to the processing device 961.
The processing device 961 received the ICS user frame F60
checks up the information operating identifier (information storage,
information transfer, information elimination, information
completion, etc.) of the ICS user frame F60 (Step S930), in a case of
the information storage, stores the usage request identifier in the
storage information administration table 962 corresponding to the
sender ICS user address and the receiver user address of the frame,
and then stores the ICS user frame in the BOX 963 (Step S931). The
72
CA 02538190 1997-11-07
ICS user frame to be stored is sent from the transmitter in the form
of being divided into a plurality of ICS user frames, so in the
present embodiment, this operation is performed until the last frame
of the ICS user frames to be stored is indicated, by means of the
information operating identifier (information completioii) indicated
in the ICS user frame F60 (Steo S932). The processing device 962
notifies to the terminal of the receiver that there is information
addressed to the receiving terminal in the ICS frame database server
960 by attaching the receiving storage user administration number, at
a timing (e.g. noon) agreed on beforehand with the receiver terminal
(Step S933). The receiver terminal which has been notified sends an
ICS user frame F60 which set the usage request identifier and
information operating identifier (information transfer), to the
access control apparatus 910-5, the ICS frame database server 960
sends the information stored in the BOX 963 to the receiver terminal
(Step S936) and then the receiver terminal receives the information
(ICS user frame) stored in the ICS frame database- server 960.
The processing device 961, upon receiving a frame explicitly
indicating the usage request identifier and the information operating
identifier (information elimination) of the ICS user frame F60,
eliminates the information stored in the storage information
administration table 962 and the BOX 963 (Step S937).
(3) Communication example-3 (Case of the receiving side
temporarily cannot receive):
In a case that a terminal which is connected to the LAN 900-1
73
CA 02538190 1997-11-07
of the corporation X and has an ICS user address "0012" performs a
conirnunication to a terminal which is connected to the LAN 900-2 of
the corporation X and has an ICS user address "0034", even if a
connection cannot be made temporarily between the transmitter
terminal and the LAN 900-2 of the corporation X, the ICS frame
database server 960 temporarily stores information addressed to the
receiving terminal, and executes the communication when the
connection becomes possible. A flowchart is shown in FIG.48,
describing the operation thereof.
The transmitter terminal sends an ICS user frame F60 to the
ICS 900, the ICS user frame F60 being provided at the user control
field with an information operating identifier (temporary storage)
which allows informations to be distributed even if the communication
with the receiver terminal is impossible, by storing the informations
in the ICS frame database server 960 temporarily. The ICS user frame
F60 is sent through the ICS 900 to the access control apparatus 910-5
containing the receiver terminal, the access control apparatus 910-5
receives the ICS user frame F60 (Step S940), and the processing
device 912-5 checks us whether or not the usage request identifier in
the ICS user frame F60 exists (Step S941) and refers to the
information operating identifier (temporary storage) of the ICS user
frame F60 (Step S942). If there is a request for temporary storage,
a judgment is made whether the receiving side terminal is in a state
in which communication is available. In the event that the
communication is available, the ICS user frame F60 is transferred to
74
CA 02538190 1997-11-07
the receiving terminal (Step S950), in the event that the
communication is not available, the ICS user frame F60 is transferred
to the processing device 961 of the ICS frame database server 960.
The processing device 961, stores the sender ICS user
address, the receiver ICS user address and the usage request
identifier of the ICS user frame F60 in the storage information
administration table 962, and then stores the ICS user frame in the
BOX 963 (Step S951). The ICS user frame to be stored is sent from
the transmitter in the form of being divided into a plurality of ICS
user frames, so in the present embodiment, this operation is
performed until the last frame of the ICS user frames to be stored is
indicated, by means of the information operating identifier
(information completion) indicated in the ICS user frame F60 (Step
S952). The processing device 912-5 constantly monitors the
communication state with the receiving terminal, and when the
receiving terminal becomes to be possible to receive, it notifies to
the processing device 961 that the communication with the receiver is
available. Upon receiving the notification, the processing device
961 notifies to the receiver terminal that there is informatioii
addressed to the receiver in the ICS frame database server 960, at a
timing (e.g. after 5 minutes) agreed on beforehand with the receiver
terminal (Step S953). The receiver terminal which has been notified
sends an ICS user frame F60 which is set the usage request identifier
(ICS storage user administration number) and the information
operating identifier (information transfer), to the access control
CA 02538190 1997-11-07
apparatus 910-5, the ICS frame database server 960 sends the
information stored in the BOX 963 to the receiver terminal (Step
S956), and the receiver terminal receives the stored information from
the ICS frame database server 960 (Step S945).
When the processing device 961 receives a frame explicitly
indicating the usage request identifier and the information operating
identifier (information elimination) of the ICS user frame F60 sent
from the receiver terminal, it eliminates the information stored in
the storage information administration table 962 and the BOX 963
(Step S957).
Embodiment-10 (transfer by X.25, FR, ATM, satellite communication,
and containment of te].ephone line, ISDN line, CATV line, satellite
line):
The data format from the user in the ICS according to the
present invention is not restricted to the ICS user frames following
the protocol of RFC 791 or RFC 1883, but can also be applied to
containment of telephone line, ISDN line, CATV line, satellite line,
IPX. Also, the relay network of the ICS network frame within the ICS
network may handle X.25, FR, ATM, satellite communication, etc. In
the present invention, the ATM exchanger includes cell-relay
equipment, and the ATM network includes cell-relay networks.
FIG.49 through FIG.51 are an example of interface conversioil
in an ICS 1000 according to the present invention, comprised of
access control apparatuses 1010-1 and 1010-2, ICS frame interface
76
CA 02538190 1997-11-07
network 1050, X.25 network 1040, FR network 1041, ATM network 1042,
satellite communication network 1043, X.25/ICS network frame
converting units 1031-1 and 1031-2, FR/ICS network frame converting
units 1032-1 and 1032-2, ATM/ICS network frame converting units 1033-
1 and 1033-2, satellite/ICS network frame converting units 1034-1 and
1034-2, telephone line converting units 1030-1 and 1030-2, ISDN line
converting units 1029-1 and 1029-2, CATV line converting units 1028-1
and 1028-2, satellite line converting units 1027-1 and 27-2, and IPX
converting units 1026-1 and 1026-2. An example of the conversion
table 1013-1 in the access control apparatus 1010-1 is shown in
FIG.52.
The ICS frame interface network 1050 is a relay network which
transfers the ICS network frame following the protocol of RFC 791 or
RFC 1883 in the format that it is in. The X.25 network 1040 is a
relay network for transferring frames of an X.25 format, and has as
the input/output portion thereof X.25/ICS network frame converting
units 1031-1 and 1031-2 for converting ICS network frames into frames
of an X.25 format, and for performing reverse conversion. The FR
network 1041 is a relay network for transferring frames of a frame
relay format, and has as the input/output portion thereof FR/ICS
network frame converting units 1032-1 and 1032-2 for converting ICS
network frames into frames of an FR format, and for performing
reverse conversion. The ATM network 1042 is a relay network for
transferring frames of an ATM format, and has as the inptit/output
portion thereof ATM/ICS network frame converting units 1033-1 and
77
CA 02538190 1997-11-07
1033-2 for converting ICS network frames into frames of an ATM
format, and for performing reverse conversion. The satellite
communication network 1043 is a relay network for transferring frames
of a satellite communication format, and has as the input/output
portion thereof satellite/ICS network frame converting units 1034-1
and 1034-2 for converting ICS network frames into satellite
communication network interface, and for performing reverse
conversion. The telephone line converting units 1030-1 and 1030-2
have the functions of converting a function equivalent to physical
layer or data link layer (first and second layers of OSI
communication protocol) between the telephone line and the access
control apparatus, and for performing reverse conversion. The ISDN
line converting units 1029-1 and 1029-2 have the functions of
converting a function equivalent to physical layer or data link layer
between the ISDN line and the access control apparatus, and for
performing reverse conversion. The CATV line converting units 1028-1
and 1028-2 have the functions of converting a functioil equivalent to
physical layer or data link layer between the CATV line and the
access control apparatus, and for performing reverse conversion. The
satellite line converting units 1027-1 and 1027-2 have the functions
of converting a function equivalent to physical layer or data link
layer between the satellite line and the access control apparatus,
and for performing reverse conversion. The IPX line converting units
1026-1 and 1026-2 have the functions of converting a function
equivalent to physical layer or data link layer between the IPX line
78
CA 02538190 1997-11-07
and the access control apparatus, and for performing reverse
conversion.
(1) Description will be made regarding a case wherein
communication is performed between the access control apparatus 1010-
1 and the access control apparatus 1010-2, via the X.25 network 1040.
The access control apparatus 1010-1 sends the ICS network
frame to the X.25 exchanger 10131-1. The X.25/ICS network frame
converting unit 1031-1 within the X.25 exchanger 10131-1 converts the
ICS network frame received from the access control apparatus 1010-1
into an X.25 format frame as shown in FIG.53. Then, the X.25
exchanger 10131-1 sends the X.25 format frame into the X.25 network
1040. The X.25 format frame sent from the X.25 exchanger 10131-1 is
transferred tllrough the X.25 network 1040, and reaches the X.25
exchanger 10131-2. Next, the X.25/ICS network frame converting unit
1031-2 within the X.25 exchanger 10131-2 performs reverse conversion
of the received X.25 format frame into ICS network frame format, and
outputs to the access control apparatus 1010-2. The access control
apparatus 1010-2 receives the ICS network frame. Network frames of
the ICS 1000 sent from the access control apparatus 1010-2 to the
X.25 exchanger 10131-2 are transferred to the access control
apparatus 1010-1 in the same manner.
(2) Description will be made regarding a case wherein a
communication is performed between the access control apparatus 1010-
1 and the access control apparatus 1010-2, via the FR network 1041.
The access control apparatus 1010-1 sends the ICS network
79
CA 02538190 1997-11-07
frame. The FR/ICS network frame converting unit 1032-1 within the FR
exchanger 10132-1 converts the ICS network frame received from the
access control apparatus 1010-1 into an FR format frame as shown in
FIG.54. Then, the FR exchanger 10132-1 sends the X.25 format frame
into the FR network 1041. The FR format fraine sent from the FR
exchanger 10132-1 is transferred through the FR network 1041, and
reaches the FR exchanger 10132-2. The FR/ICS network frame
converting unit 1032-2 within the FR exchanger 10132-2 performs
reverse conversion of the received FR format frame into ICS network
frame format, and outputs to the access control apparatus 1010-2.
The access control apparatus 1010-2 receives the ICS network frame.
ICS network frames sent from the access control apparatus 1010-2 to
the FR exchanger 10132-2 are transferred to the access control
apparatus 1010-1 in the same manner.
(3) Description will be made regarding a case wherein a
communication is performed between the access control apparatus 1010-
1 and the access control apparatus 1010-2, via the ATM network 1042.
The access control apparatus 1010-1 sends the ICS network
fraine to the ATM exchanger 10133-1. The ATM/ICS network frame
converting unit 1033-1 within the ATM exchanger 10133-1 converts the
ICS network frame received from the access control apparatus 1010-1
into an ATM format frame as shown in FIG.55. Then, the ATM exchanger
10133-1 sends the ATM format frame into the ATM network 1042. The
ATM format frame sent from the ATM exchanger 10133-1 is transferred
through the ATM network 1042, and reaches the ATM exchanger 10133-2.
CA 02538190 1997-11-07
Next, the ATM/ICS network frame converting unit 1033-2 within the ATM
exchanger 10133-2 performs reverse conversion of the received ATM
format frame into ICS network frame format, and outputs to the access
control apparatus 1010-2. The access control apparatus 1010-2
receives the ICS network frame. ICS network frames sent from the
access control apparatus 1010-2 to the ATM exchanger 10133-2 are
transferred to the access control apparatus 1010-1 in the same
manner.
(4) Description will be made regarding a case wherein a
communication is performed between the access control apparatus 1010-
1 and the access control apparatus 1010-2, via the satellite
commuriications network 1043.
The access control apparatus 1010-1 sends the ICS network
frame to the satellite receiver/transmitter 10134-1.- The
satellite/ICS network frame converting unit 1034-1 within the
satellite receiver/transmitter 10134-1 converts the ICS network fran-e
received from the access control apparatus 1010-1 into an interface
within the satellite communications network 1043. Then, the
satellite receiver/transmitter 10134-1 sends the ICS network frame
converted into an interface within the satellite communications
network 1043 into the satellite communications network 1043. The ICS
network frame converted into an interface within the satellite
communications network 1043 sent from the satellite
receiver/transmitter 10134-1 is transferred through the satellite
communications network 1043, and reaches the satellite
8 7
CA 02538190 1997-11-07
receiver/transmitter 10134-2. The satellite/ICS network frame
converting unit 1034-2 within the satellite receiver/transmitter
10134-2 performs reverse conversion of the received interface within
the satellite communications network 1043 into ICS network frame
format, and outputs to the access control apparatus 1010-2. The
access control apparatus 1010-2 receives the ICS network frame. ICS
network frames sent from the access control apparatus 1010-2 to the
satellite receiver/transmitter 10134-2 are transferred to the access
control apparatus 1010-1 in the same manner.
(5) Description will be made regardiiig a case wherein
communication is performed with an interface of a telephone line
between a user 1060-1 connected to a telephone line converting imit
1030-1 of an access control apparatus 1010-1, and a user 1060-2
connected to a telephone line converting unit 1030-2 of an access
control apparatus 1010-2, the first user originating the call.
The user 1060-1 applies a telephone line connection to the
VAN operator. The VAN operator specifies the access control
apparatus 1010-1 connecting the user 1060-1, and decides on an ICS
network address "7721" for the ICS logic terminal. Next, the VAN
operator sets informations in the conversion table 1013-1 of the
access control apparatus 1010-1, such as the transmitting ICS network
address "7721", the receiving telephone number "06-5555-9876", the
receiving ICS network address "5521", request identification and so
forth. In the present embodiment, the request identification "5"
indicates a telephone line connection. In the same way, the VAN
82
CA 02538190 1997-11-07
operator sets informations in the conversion table 1013-2 of the
access control apparatus 1010-2, such as the transmitting ICS network
address "5521", the receiving telephone number "03-5555-1234", the
receiving ICS network address "7721", request identification and so
forth.
The user 1060 sends the telephone number "06-5555-9876". The
telephone line converting unit 1030-1 converts the received telephone
number into a format which can be read by the processing device 1012-
1, and sends it to the processing device 1012-1. The processing
device 1012-1 received the telephone number information from the
telephone line converting unit 1030-1 with the ICS network address
"7721" refers to the request identification of the transmitting ICS
network address "7721" of the conversion table 1013-1, identifies it
as a telephone line connection, and reads the receiving ICS network
address "5521" from the receiving telephone number "06-5555-9876".
The access control apparatus 1010-1 forms an ICS network frame having
a network control field wherein the receiving ICS network address is
set to "5521" and the transmitting ICS network address is set to
"7721" and a network data field described information to notify that
there is a telephone reception, and seilds it into a network of ICS
1000. The ICS network frame sent froin the access control apparatus
1010-1 is transferred through the iietwork of the ICS 1000, and
reaches the access control apparatus 1010-2. The access control
apparatus 1010-2 received the ICS network frame having the network
data field described information to notify that there is telephone
83
CA 02538190 1997-11-07
reception, outputs a signal from the telephone line converting unit
1030-2 with the ICS network address "5521" to the user 1060-2
notifying the reception. Then, the.user 1060-2 sends a response
signal.
Upon receiving the response signal, the telephone line
converting unit 1030-2 converts it into a format which can be
transferred through the network of the ICS 1000. The access control
apparatus 1010-2 forms an ICS network frame having a network control
field wherein the receiving ICS network address is set to "7721" and
the transmitting ICS network address is set to "5521", and a network
data field described information to notify that there is reply of the
telephone, and sends it into a network of the ICS. The ICS network
frame sent from the access control apparatus 1010-2 is transferred
through the network of the ICS, and reaches the access control
apparatus 1010-1. The access control apparatus 1010-2 received the
ICS network frame having the network data field described information
to notify that there is a response, outputs a signal from the
telephone line converting unit 1030-1 having the ICS network address
"7721" to the user 1060-1, notifying the response. Thus, the user
1060-1 and the user 1060-2 begin full-duplex communication by analog
signals (voice, etc.) and the user 1060-1 sends analog signals. The
telephone line converting unit 1030-1 received the analog signals
converts the analog signals into an analog information format which
can be transferred through the ICS network.
The access control apparatus 1010-1 forms an ICS network
84
CA 02538190 1997-11-07
frame having a network control field wherein the transmitting ICS
network address is set to "7721" and the receiving ICS network
address is set to "5521", and a network data field described analog
information, and sends it into a network of the ICS 1000. The ICS
network frame sent from the access control apparatus 1010-1 is
transferred through the network of the ICS 1000, and reaches the
access control apparatus 1010-2. The access control apparatus 1010-2
received the ICS network frame having network data field described
the analog information outputs the analog information as analog
signals converted into a telephone line interface from the telephone
line converting unit 1030-2 having the ICS network address "5521" to
the user 1060-2. The analog signals sent from the user 1060-2 are
transferred to the user 1060-1 by means of the same procedure.
(6) Description will be made regarding a case wherein a
communication is performed with an interface of an ISDN line between
a user 1061-1 connected to an ISDN line converting unit 1029-1 of an
access control apparatus 1010-1, and a user 1061-2 connected to an
ISDN line converting unit 1029-2 of an access control apparatus 1010-
2, the first user originating the call.
The user 1061-1 applies an ISDN line connection to the VAN
operator. The VAN operator specifies the access control apparatus
1010-1 connecting the user 1061-1, and decides on an ICS network
address "7722" for the ICS logic terminal. Next, the VAN operator
set informations in the conversion table 1013-1 of the access control
apparatus 1010-1, such as the transmitting ICS network address
CA 02538190 1997-11-07
"7722", the receiving ISDN number "06-5555-2222", the receiving ICS
network address "5522", request identification and so forth. In the
present embodiment, the request identification "6" indicates a ISDN
line connection. In the same way, the VAN operator sets informations
in the conversion table 1013-2 of the access control apparatus 1010-
2, such as the traiismitting ICS network address "5522", the receiving
ISDN number "03-5555-1111", the receiving ICS network address "7722",
request identification and so forth.
The user 1061-1 sends the ISDN number "06-5555-2222". The
ISDN line converting unit 1029-1 converts the received ISDN number
into a format which can be read by the processing device 1012-1, and
sends it to the processing device 1012-1. The processing device 1012-
1 received the ISDN number information from the ISDN line converting
unit 1029-1 with the ICS network address "7722" refers to the request
identification of the transmitting ICS network address "7722" of the
conversion table 1013-1, identifies it as an ISDN line connection,
and reads the receiving ICS network address "5522" from the receiving
ISDN number "06-5555-2222". The access control apparatus 1010-1
forms an ICS network frame having a network control field wherein the
receiving ICS network address is set to "5522" and the transmitting
ICS network address is set to "7722", and a network data field
described information to notify that there is an ISDN reception, and
sends it into a network of the ICS 1000.
The ICS network frame sent from the access control apparatus
1010-1 is transferred through the network of the ICS 1000, and
86
CA 02538190 1997-11-07
reaches the access control apparatus 1010-2. The access control
apparatus 1010-2 received the ICS network frame having the network
data field described information to notify that there is a reception,
outputs a signal from the ISDN line converting unit 1029-2 with an
ICS network address "5522" to the user 1061-2, notifying the
reception. Then, the user 1061-2 sends a response signal. Upon
receiving the response signal, the ISDN line converting unit 1029-2
converts it into a format which can be transferred through the
network of the ICS 1000. The access control apparatus 1010-2 forms
an ICS network frame having a network control field wherein the
receiving ICS network address is set to "7722" and the transmitting
ICS network address is set to "5522", and a network data field
described information to notify that there is a reply of the ISDN,
and sends it into a network of the ICS 1000.
The ICS network frame sent from the access control apparatus
1010-2 is transferred through the network of the ICS 1000, and
reaches the access control apparatus 1010-1. The access control
apparatus 1010-2 received the ICS network frame having a network data
field described information to notify that there is a response,
outputs a signal from the ISDN line converting unit 1029-1 having the
ICS network address "7722" to the user 1061-1, notifying the
response. Tllus, the user 1061-1 and the user 1061-2 begin full-
duplex communication by digital signals (voice, etc.) and the user
1061-1 sends the digital signals. The ISDN line converting unit 1029-
1 received the analog signal converts into a digital information
87
CA 02538190 1997-11-07
format which can be transferred through the ICS 1000.
The access control apparatus 1010-1 forms an ICS network
frame having a network control field wherein the receiving ICS
network address is set to "5522" and the transmitting ICS network
address is set to "7722", and a network data field described digital
information, and sends it into a network of the ICS 1000. The ICS
network frame sent from the access control apparatus 1010-1 is
transferred through the network of the ICS 1000, and reaches the
access control apparatus 1010-2. The access control apparatus 1010-2
received the ICS network frame having a network data field described
the digital information, outputs the digital information as digital
signals converted into a ISDN line interface from the ISDN line
converting unit 1029-2 having the ICS network address "5522" to the
user 1061-2. The digital signals sent from the user 1061-2 are
transferred to the user 1061-1 by means of the same procedure.
(7) Description will be made regarding a case wherein a
communication is performed with an interface of a CATV line between a
CATV broadcasting station 1062-1 connected to a CATV line converting
tulit 1028-1 of an access control apparatus 1010-1, and a user 1062-2
connected to a CATV line converting unit 1028-2 of an access control
apparatus 1010-2.
The CATV broadcasting station 1062-1 applies a CATV line
connection witli the user 1062-2 to the VAN operator. The VAN
operator specifies the access control apparatus 1010-2 connecting the
user 1062-2, and decides on an ICS network address "5523" for -the ICS
88
CA 02538190 1997-11-07
logic terminal. Next, the VAN operator sets informations to a
portion of the conversion table 1013-1 of the access control
apparatus 1010-1 corresponding to the transmitting ICS network
address "7723", such as the receiving ICS network address "5523",
request identification and so forth. In the present embodiment, the
request identification "7" indicates a CATV line connection. In the
same way, the VAN operator sets informations in the conversion table
1013-2 of the access control apl::J.is 1010-2, such as the
transinitting ICS network address "5523", the receiving ICS network
address "7723", request identification and so forth.
The CATV broadcasting station 1062-1 sends CATV analog
signals. The CATV line converting unit 1028-1 converts the received
CATV analog signals into a format which can be transferred through
the ICS 1000. The access control apparatus 1010-1 forms an ICS
network frame having a network control field wherein the receiving
ICS network address is set to "5523" and the transmitting ICS network
address is set to "7723", and a network data field described the CATV
information, and sends it into a network of the ICS 1000. The ICS
network frame sent from the access control apparatus 1010-1 is
transferred through the ICS 1000, and reaches the access control
apparatus 1010-2. The access control apparatus 1010-2 received the
ICS network frame having network data field described the CATV
information, outputs the CATV information from the CATV line
converting iiilit 1028-2 with an ICS network address "5523" to the user
1062-2 as CATV analog signals converted to a CATV line interface.
89
CA 02538190 1997-11-07
The CATV analog signals outputted from the user 1062-2 are
transferred to the CATV broadcasting station 1062-1 with the same
procedures.
(8) Description will be made regarding a case wherein a
communication is performed with an interface of a satellite line
between a user 1063-1 connected to a satellite line converting unit
1027-1 of an access control apparatus 1010-1, and a user 1063-2
connected to a satellite line converting unit 1027-2 of an access
control apparatus 1010-2.
The user 1063-1 and the user 1063-2 applies a satellite line
connection between the user 1063-1 and the user 1063-2 to the VAN
operator. The VAN operator specifies the access control apparatus
1010-1 connecting the user 1063-1, and decides on an ICS network
address "7724" for the ICS logic terminal. In the same way, the VAN
operator specifies the access control apparatus 1010-2 connecting the
user 1063-2, and decides on an ICS network address "5524" for the ICS
logic terminal. Next, the VAN operator sets informations to a
portion of the conversion table 1013-1 of the access control
apparatus 1010-1 corresponding to the transmitting ICS network
address "7724", such as the receiving ICS network address "5524",
request identification and so forth. In the present embodiment, the
request identification "8" indicates the satellite line connection.
In the same way, the VAN operator sets informations in the conversion
table 1013-2 of the access control apparatus 1010-2, such as the
transmitting ICS network address "5524", the receiving ICS network
CA 02538190 1997-11-07
address "7724", request identification and so forth.
The user 1063-1 sends satellite signals. The satellite line
converting unit 1027-1 received interface satellite signals of the
satellite line converts the satellite signals into an information
format which can be transferred through the ICS 1000. The access
control apparatus 1010-1 forms an ICS network frame having a network
control field wherein the receiving ICS network address is set to
"5524" and the originating ICS network address is set to "7724", and
a network data field describing satellite signal information, and
sends this into the ICS 1000 network. The ICS network frame sent
from the access control apparatus 1010-1 is transferred through the
ICS network 1000, and reaches the access control apparatus 1010-2.
The access control apparatus 1010-2 received the ICS network frame
having a network data field described the satellite information,
outputs satellite signal information from the satellite line
converting unit 1027-2 with an ICS network address "5524" to the user
1063-2 as satellite signals converted to a satellite line interface.
The satellite line interface satellite signals outputted from the
user 1063-2 are also transferred to the user 1063-1 with the same
procedures.
(9) Description will be made regarding a case wherein a
communication is performed with an IPX interface between a terminal
having an IPX address "9901" of a user 1064-1 and a terminal llaving
an IPX address "8801" of a user 1064-2.
The users 1064-1 and 1064-2 apply an IPX connection between a
91
CA 02538190 1997-11-07
terminal having an IPX address "9901" of the user 1064-1 and a
terminal having an IPX address "8801" of the user 1064-2 to the VAN
operator. The VAN operator specifies the access control apparatus
1010-1 connecting the user 1064-1 and the IPX converting unit 1026-1
with an ICS network address "7725". In the same say, the VAN
operator specifies the access'control apparatus 1010-2 connecting the
user 1064-2 and the IPX converting unit 1026-2 with an ICS network
address "5525". Next, the VAN operator sets informations to a
portion of the conversion table 1013-1 of the access control
apparatus 1010-1 corresponding to the transmitting ICS network
address "7725", such as the sender IPX address "9901", the receiver
IPX address "8801", the receiving ICS network address "5525", request
identification and so forth. In the present embodiment, the request
identification "9" indicates an IPX connection. In the same way, the
VAN operator sets informations to a portion of the conversion table
1013-2 of the access.control apparatus 1010-2 corresponding to the
transmitting ICS network address "5525", such as the sender IPX
address "8801", the receiver IPX address "9901", the receiving ICS
network address "7725", request identification and so forth.
The terminal having an IPX address "9901" of the user 1064-1
sends an IPX frame with the sender IPX address set to "9901" and the
receiver IPX address set to "8801". The IPX converting unit 1026-1
of the access control device receives the IPX fraine, and reads the
sender IPX address "9901" and the receiver IPX address "8801", and
then reads the receiving network address "5525" of the receiver IPX
92
CA 02538190 1997-11-07
address "8801" of the sender IPX address "9901" of the transmitting
ICS network address "7725", from the conversion table 1013-1. The
access control apparatus 1010-1 forms an ICS network frame having a
network control field wherein the transmitting ICS network address is
set to "5525" and the receiving ICS network address is set to "7725",
and a network data field described IPX frame information, and sends
it into a network of the ICS 1000.
The ICS network frame sent from the access control apparatus
1010-1 is transferred through the network of the ICS 1000, and
reaches the access control apparatiis 1010-2. The access control
apparatus 1010-2 received the ICS network frame having a network data
field described the ICS network frame information, outputs IPX frame
information from the IPX converting unit 1026-2 with an ICS network
address "5525" to the user 1064-2, in the form of IPX frame converted
into IPX interface. The terminal having the IPX address "8801" of
the user 1064-2 receives the IPX frame. On the other hand, the IPX
frame set in the sender IPX address "8801" and the receiver IPX
address "9901" sent from the terminal having the IPX address "8801"
of the user 1064-2 is also transferred to the user 1064-1 with the
same procedures.
Embodiment-11 (transfer by X.25, FR, ATM, satellite communication,
and containment of telephone line, ISDN line, CATV line, satellite
line) :
In the above Embodiment-10, the X.25/ICS network frame
93
CA 02538190 1997-11-07
converting units 1031-1 and 1031-2, FR/ICS network frame converting
units 1032-1 and 1032-2, ATM/ICS network frame converting units 1033-
1 and 1033-2, satellite/ICS network frame converting units 1034-1 and
1034-2 are each located within relay networks, i.e., within the X.25
network 1040, FR network 1041, ATM network 1042 and satellite
communication network 1043. Conversely, as shown in FIGs.56 and 57,
with the Embodiment-I1., the X.25/ICS network frame converting units
1131-1 and 1131-2, FR/ICS network frame converting units 1132-1 and
1132-2, ATM/ICS network frame converting units 1133-i and 1133-2,
satellite/ICS network frame converting units 1134-1 and 1134-2 are
each located within the access control apparatuses 1110-1 and 1110-2.
That is, while with Embodiment-10, the received ICS network frames
are converted and reverse-converted into formats which can be
transferred on the side of each of the relay networks (X.25 network
1040, FR network 1041, ATM network 1042, satellite communication
network 1043), the conversion being performed by the relay networks,
with the Embodiment-11, conversion and reverse conversion into
formats which can be transferred in each of the relay networks is
performed on the side of the access control apparatuses.
Embodiment-12 (Containment of access control apparatuses within relay
networks):
In the above Embodiment-10, the X.25/ICS network converting
units 1031-1 and 1031-2, FR/ICS network converting units 1032-1 and
1032-2, ATM/ICS network converting units 1033-1 and 1033-2, satellite
94
CA 02538190 1997-11-07
communication network/ICS network converting units 1034-1 and 1034-2
are each located within relay networks, i.e., within the X.25 network
1040, FR network 1041, ATM network 1042 and satellite communication
network 1043, with the access control apparatuses 1010-1 and 1010-2
not being provided within the X.25 network, FR network, ATM network
and satellite communication network. Conversely, as shown in FIGs.58
and 59, with the Embodiment-12, the access control apparatuses 1120-
1, 1120-2, 1121-1, 1121-2, 1122-1, 1122-2, 1123-1 and 1123-2 are each
located within the relay networks, i.e., within the X.25 network 1240-
1, FR network 1241-1, ATM network 1242--i and satellite communication
network 1243-1. That is, while with the Embodiment-10, a conversion
from the ICS user frames to the ICS network frames and a reverse
conversion thereof based on the administration by the conversion
table was performed within the access control apparatuses set outside
of each relay network, in the present example, a conversion from the
ICS user frames to the ICS network frames (ICS encapsulation) and a
reverse conversion thereof (ICS reverse encapsulatioil) based on the
adniinistration by the conversion table is performed within each of
the aforementioned networks, i.e., within the X.25 network 1040,
within the FR network 1041, within the ATM network 1042 arid within
the satellite communication network 1043.
Embodiment-13 (Connection of relay network to relay apparatus):
In the above Embodiment-10, the X.25 network 1040, FR network
1041, ATM network 1042 and satellite communication network 1043 are
CA 02538190 1997-11-07
each connected to the access control apparatuses 1010-1 and 1010-2,
but are not connected to relay apparatuses. Conversely, as shown in
FIG.60, with the Embodiment-13, the X.25 network 2020-1 is connected
to the access control apparatus 2010 and the relay apparatus 2030,
the FR network 2021-1 is connected to the access control apparatus
2011 and the relay apparatus 2031, the ATM network 2022-2 is
connected to the access control apparatus 2012 and the relay
apparatus 2032, and the satellite communications network 2023-1 is
connected to the access control apparatus 2013 and the relay
apparatus 2033, and further, the X.25 network 2020-1 is connected to
the relay apparatuses 2030, 2034 and 2035, the FR network 2021-2 is
connected to the relay apparatuses 2031 and 2035, the ATM network
2022-2 is connected to the relay apparatuses 2031, 2032 and 2036, and
the satellite communications network 2023-2 is connected to the relay
apparatus 2033, 2036 and 2037. That is, in the present embodiment,
the access control apparatuses are arranged such that the X.25
network 2020-1 and 2020-2, the FR network 2021-1 and 2021-2, the ATM
network 2022-1 and 2022-2, and the satellite communication network
2023-1 and 2023-2 are each connected to relay apparatuses.
Embodiment-14 (Case where the access control apparatus is provided
outside of the ICS):
FIG.61 shows a 14th embodiment according to the present
invention, with the access control apparatus 1210-1 being provided
outside of the ICS 1200, i.e., within the LAN-1200 of the corporation
96
CA 02538190 1997-11-07
X. Accordingly, the ICS address administration server 1250-1 and the
ICS network server 1260-1 are also located outside of the ICS 1200,
i.e., within the LAN 1200-1. The access control apparatus
integrating administration server 1240 is located iilside of the ICS
1200, The access control apparatus integrating administration server
1240 has functions of communicating and exchanging information with
the access control apparatus 1210-1, the ICS network administration
server 1250-1 and the ICS network server 1260-1, using the ICS
network communication function. At a time that the VAN operator
enters into contract with the corporation X, and connects the user
communication line to the ICS 1200, the functions of the access
control apparatus integrating administration server 1240 are used to
write data in the conversion table within the access control
apparatus 1210-1. Also, the ICS address administration server 1250-1
and the ICS network server 1260-1 can each use respective ICS network
server communication function to communicates with the ICS address
administration server 1250-2 and the ICS network server 1260-2 within
the ICS 1200. Since the present invention is configured thus, a user
terminal within the LAN 1200 can perform the intra-corporation
communication and the inter-corporation communication, as described
with the above Embodiment-1. Also, it is clearly understood that the
intra-corporation communication and the inter-corporation
communication can be conducted with the user terminal as described
above, even in the event that the ICS address administration server
1250-1 and the ICS network server 1260-1 are located within the ICS
97
CA 02538190 1997-11-07
1200.
Embodiment-15 (Speed class and degree of priority):
<<Configuration>>
As shown in FIG.62 through FIG.64, the ICS 8000-1 includes
access control apparatuses 8010-1, 8010-2, 8010-3 and 8010-4, relay
apparatus 8020-1, ICS address administration server 8025-1 and ICS
network server 8027-1, these apparatuses being connected by ICS
network communication lines 8030-1, 8030-2, 8030-3, 8030-4, 8030-5
and 8030-6 which transfer ICS network frame. The line unit 8011-1,
processing device 8012-1 and conversion table 8013-1 are all provided
within the access control apparatus 8010-1. Connected to the
plurality of ICS logic terminals in the line unit 8011-1 are ICS
logic communication lines 8051-1, 8051-2, 8051-3 and 8051--4, these
each being provided with ICS network addresses "7721", "7723", "7724"
and "7725". Speed classes are given to the ICS communication lines
within the ICS 8000-1, indicating the speed of transferring the ICS
network frames. For example, the speed class of the ICS
communication lines 8030-1, 8030-2 and 8030-6 are all "4", the speed
class of the ICS communication lines 8030-3 and 8030-5 are each "3",
and the speed class of the ICS communication line 8030-4 is "2". An
example of the conversion table 893-1 is showii in FIG.65. The speed
class is determined by a standard with in the same as the speed class
registered within the conversion table 8013-1. An ICS network
address "7811" is provided to the ICS address administration server
98
CA 02538190 1997-11-07
8025-1, and an ICS network address "7821" is provided to the ICS
address administration server 8027-1, these being connected to the
access control apparatus 8010-1 by the ICS network communication
lines 8054-1 and 8054-2.
The user 8400-1 which is an ICS communication terminal has an
ICS user address "2500", is connected to the line unit 8011-1 via the
ICS logic communication line 8051-1; the user 8400-2 which is an ICS
communication terminal has an ICS user address "2510", is connected
to the line unit 8010-2 via the ICS logic communication line 8052-1;
the user 8400-3 which is an ICS communication terminal has an ICS
user address "3600", and the user 8400-4 which is an ICS
communication terminal has an ICS user address "3610", these being
connected to the line unit 8010-3 via the gateway 8041-1 and the ICS
logic communication line 8053-1, respectively.
The method for registering the ICS network address and the
ICS user address with the conversion table 8013-1 is the same as with
the aforementioned Embodiments-1 and -2, with the points differing
therewith being as follows: the speed registered in the conversion
table 113-1 in the Embodiment-1 is deleted, and iiistead, a speed
class and degree of priority are registered; and the speed class and
degree of priority are stored in the address administrating server
8025-1 along with the corresponding the ICS user address, as part of
the address-related information.
The speed class is a system where the communication speed is
represented with numeric values or the like, instead of with units of
99
CA 02538190 1997-11-07
speed. For example, the communication speed of 64 Kbps is Class 1,
the communication speed of 128 Kbps is Class 2, and so forth, with
the communication speed of 500 Mbps being Class 7. The greater the
number for the communication class is, the greater the speed. FIG.66
shows an example of correlation between the communication speed and
the speed class, but there is no need to make the speed class system
a 7-class system from "1" to "7". This may be, for example, finely
divided into a 20-class system, in accordance with progress in
technology. Also, there is not need for the communication speed to
accurately match the physical communication speed of the ICS network
lines within the ICS 8000-1, rather, the system may be made to
correspond with 25% of the physical communication speed, giving some
leeway with the communication speed. The degree of priority is
represented in numeric values, on an 8-tiered system, for example,
representing the order of priority compared within a single speed
class for when sending the ICS network frames from the access control
apparatus or the relay apparatus to the ICS network communication
line. The greater numeric value representing the degree of priority,
the higher the priority. For example, in the event that the relay
apparatus receives two ICS network frames F510 and F511 at almost the
same time, and the speed class of the two frames is the same value
"3", the degree of priority of the ICS network frame F510 is "3", and
the degree of priority of the ICS network frame F511 is "5", the
system sends the ICS network frame F511 with higher priority first.
In the present Embodiment-15, e.g., the ICS network
100
CA 02538190 1997-11-07
communication lines 8030-3 and 8030-4 are "in the same communication
channel" from the relay apparatus 8020-1 toward the access control
apparatus 8010-3, and the ICS network communication lines 8030-5 and
8030-6 are "in the same communication channel" from the relay
apparatus 8020-1 toward the access control apparatus 8010-4. The
communication line may be headed toward the relay apparatus from the
access control apparatus, or may be headed from one relay apparatus
toward another relay apparatus connected with the ICS network
communication line. A plurality of ICS network communication lines
of the same speed class may be se-t within the same channel, and in
this case, the same speed class may be in the same ICS network
communication line.
<<Operation>>
This operation will now be described with reference to the
flowcharts in FIGs.67 and 68.
The user 8400-1 sends the ICS user frame F500 with the sender
ICS user address "2500" and the recei.ver ICS user address "3600" to
the ICS logic communication line 8051-1. The processing device 8012-
1 of the access control apparatus 8010-1 receives the ICS user frame
F500 from the ICS logic terminal with the ICS network address "7721"
of the line unit 8011-1, and at the saine tiine, obtains the ICS
network address "7721" (Step S2001), and checks whether the ICS
network address "7721" has the request identification thereof
registered in the conversion table 8013-1 as "3" (virtual dedicated
line connection) or not (Step S2002). In this case, the registration
101
CA 02538190 1997-11-07
has not been made as such, so next, the receiver ICS network address
"3600" written in the ICS user frame F500 is obtained in accordance
with the ICS network address "7721" (Step S2004), and checks whether
the ICS network address "3600" has the request identification thereof
registered in the conversion table as "2" (inter-corporation
communication) or not (Step S2005). In this case, the registration
has been made, so next, the receiving ICS network address "5522" is
obtained from the conversion table 8013-1 as preparation to perform
the ICS encapsulation, and accounting-related information, namely
"speed class "3" and "degree of priority "3", is obtained from the
conversion table 8013-1 (Step S2006). Next, the ICS encapsulation is
performed by generating an ICS network frame F510 written therein
with "speed class "3" and degree of priority "3" (Step S2020), which
is sent to the ICS network communication line 8030-1 (Step S2021).
Although the above explanation has been made with regard to
the inter-corporation communication wherein the request
identification of the ICS network frame is set at "2" (inter-
corporation communication), in the event that the request
identification thereof is "3" (virtual dedicated line connection),
the receiving ICS network address, speed class, degree of priority
and the like are obtained from the conversion table 8013-1, and
further, information relating to account is obtaiiied (Step S2003).
In the event that the request identification thereof is "1" (intra-
corporation communication), the receiving ICS network address, speed
class, degree of priority and the like are obtained from the
102
CA 02538190 1997-11-07
conversion table 8013-1, and further, information relating to account
is obtained (Step S2011). In the event that the request
identification thereof is "4" (communication to an ICS network
server), the receiving ICS network address and the like are obtained
from the conversion table 8013-1, and further, information relating
to account is obtained (Step S2013), following which this is sent to
the ICS network server 8027-1 after encapsulation.
The ICS network frame F510 formed thus reaches the relay
apparatus 8020-1 via the ICS network communication line 8030-1. Let
us say that now, another ICS network frame F511 reaches the relay
apparatus 8020-1 via the ICS network communication line 8030-2, at
almost the same time. This ICS network frame F511 has been sent from
the user 8400-2 as an ICS user frame F501, has arrived at the access
control apparatus 8010-2 via the ICS logic communications line 8052-
1, been ICS encapsulated at that poiilt to become the ICS network
frame F511 there, and reached the relay apparatus 8020-1 by being
sent via the ICS network communication line 8030-2. Upon receiving
the ICS network frame F510 and the ICS network frame F511 (Step
S2030), the relay apparatus 8020-1, under the administration of the
processing device 8021-1, first checks the relay table 8022-1 to
decide which network communication line to use for the ICS network
frames F510 and F511, i.e., finds communication channels (Step
S2031), and separates these by channel (Step S2032). With the
present Embodiment-15, both of the two ICS network frames F510 and
F511 have a transmission destination of the communication channel
103
CA 02538190 1997-11-07
from the relay apparatus 8020-1 to the control apparatus 8010-3, and
two ICS network communication lines exist, namely, the ICS network
communication line 8030-3 and 8030-4. Next, the relay apparatus 8020-
1 reads the speed class described in the control field of the two ICS
network frames F510 and F511, and separates the ICS network frames by
speed class (Step S2041). Hereafter, the procedures are performed
separately for each separated speed class.
In the case of the present Embodiment-15 , the speed class of
the two ICS network frames F510 and F511 are both "3". Next, with
the ICS frames of the same speed class, the degree of priority
described in the control portion of the two ICS network frames is
read for each, and the ICS frame with the higher priority is sent
first (Step S2042). If the degree of priority is the same, either
may be sent first. As a result of the above process, the relay
apparatus 8020-1 sends the ICS network frame F511 first over the ICS
network communication line 8030-3, and subsequently sends the ICS
network frame F510 over the ICS network communication line 8030-3.
Incidentally, in the above procedures, in the eveilt that the
only ICS network communication lines available are of a communication
speed slower thail the speed class described in the control field of
the ICS network frame F510, information regarding slower service due
to slower speeds, i.e., the sender ICS user address and the receiver
ICS user address to be described in the relevant ICS network frame,
the time to communications service (year, month, day, hour, minute,
second), etc., are described in the relay operating file 8023-1. The
104
CA 02538190 1997-11-07
recorded contents of the relay operating file 8023-1 are notified to
the user according to requests of the ICS 8000-1.
According to the above procedures, of the two ICS network
frames F511 and F510, the ICS network frame F511 with the higher
priority leads time-wise, and reaches the access control apparatus
8010-3, having been transferred through the ICS network communication
line 8030-3. The ICS network frame F511 is subjected to the ICS
reverse-encapsulation, becomes the ICS network frame F501, and
reaches the user 8400-4 with the ICS user address "3610" via the ICS
logic communication path 8053-1. The ICS network frame F510 is
subjected to the ICS reverse-encapsulation, becomes the ICS network
frame F500, and reaches the user 8400-3 with the ICS user address
"3600" via the ICS logic communication path 8053-1.
Next, options will be described regarding how to user the
degree of priority. In the event that the speed class and the degree
of priority recorded in the conversion table 8013-1 are to be copied
to the ICS network frame at the point of the ICS encapsulation, the
processing device 8012 -1 checks the length written in the ICS user
frame control field which is to be processed, and only in the event
that the ICS user frame is equal to or shorter than the predetermined
value (e.g., 256 bytes) for example, a value with value representing
the degree of priority incremented by "1" is copied to the ICS
network frame. Thus, in the limited case of short ICS user frames,
the ICS user frames can be transferred within the ICS 8000-1 with
priority. This, the ICS 8000-1 operator is able to easily realizes
1.05
CA 02538190 1997-11-07
service wherein the priority of short ICS user frames is raised,
i.e., the communication service with raised communication charges.
As for the users, the short ICS user frames increases the surety of
throughput. Whether or not the option is used is determined
separately for each access control apparatus, for example.
A method may be employed wherein only the speed class is
implemented, and the above method is executed without the degree of
priority, i.e., with all ICS user frames at the same degree of
priority. With other embodiments, the conversion table 8013-1 does
not include the sender ICS user address (intra-corporation and inter-
corporation). In these cases as well, there is no change, since the
flowchart shown in FIG.67 does not refer to the sender ICS user
address, anyway.
Embodiment-16 (Assign.ment of electronic signature to ICS user frame):
Aii embodiment will now be described wherein ICS user frames
are electronically signed, and wherein there is proof that an ICS
user frame has passed through an access control apparatus. Also, the
embodiment will now be described wherein the ICS user frames are
encrypted upon request. First, description will be made regarding
the electronic signature technology used in the present embodiment.
In order for an electronic signature to be used, there is a signer to
form the electronic signature and a verifier to verify the electronic
signature. The signer simultaileously forms a pair of keys, signature
key KSa and verification key KPa. The signer keeps the signature key
106
CA 02538190 1997-11-07
KSa undisclosed, and discloses the verification key KPa one way or
another. The signer "a" uses the secret signature key KSa held by
the signer "a" lone to form an electronic signature Q which
dependent on data m and the signature key KSa. This is shown in the
following expression (1)
a = SIGN (KSa, h (m) ) === === (1)
Now, "SIGN" is a signature function representing the function of the
signature, with the function y = h (m) being a hash function for
electronic signing having a function for compressing the data m into
short data. The verifier "b" uses the disclosed verification key KPa
and verifies the authenticity of the electronic signature Q,
according to the following:
v = TEST ( cr , KPa, h (m) ) === === (2)
Then in the event that v= 1, this indicates that the electronic
signature a and the data m are both correct, that the electronic
signature a and the data m have not been re-written following
generation of the electronic signature Q, and that there are been no
unauthorized tampering. In the event that v= 0, this indicates
that the either one or both of the electronic signature a and the
data m are not correct. The verification key KPa is widely disclosed
by a public key information service forms which performs services
such as operational reports and information of public keys, or by
general advertisements. The art for forms the signature function
SIGN which makes calculation of the signature key KSa practically
impossible even with disclosure of the verification key KPa, is of.
107
CA 02538190 1997-11-07
public knowledge.
Next, the procedure for assigning an electronic signature to
the ICS user frame will be described. The objects of the electronic
signature are the following: a "time/location parameter P1"
representing conditions relating to the time or place of providing
the electronic signature, i.e., the year/month/day/hour/minute/second
of electronic signing, the operator of the access control apparatus,
or the identification code of the access control apparatus, and the
"signature function parameter P2" representing the signature function
SIGN, the type of the hash function h (m), or the length of the
signature key. In a numerical expression, this is expressed in the
following expression (2):
Q = SIGN (KSa, h (m) ) === === (3)
wherein m = UF II P1 II P2.
Now, UF represents the ICS user frame before the ICS encapsulation,
or the ICS user frame restored to the original form after the ICS
reverse-encapsulation. The user on the receiving side receives the
ICS user frame UF, the time/location parameter P1, the signature
function parameter P2, and electronic sigilature Gr to the ICS user
frame on the receiving side as UF II P1 II P2 II Q. This is
illustrated in FIG.69. Further, there is a method wherein the area
for writing the parameters P1 and P2, and the electronic signature Q
within the ICS user frame UF is left blank, as sliown in FIG.70. In
this case, the electronic signature Q is generated such as can be
represented as follows, with the open area in the ICS user frame tIF
108
CA 02538190 1997-11-07
represented by "Data":
o = SIGN (KSa, h (m) ) === === (4)
wherein m= Data(I P1 II P2.
Verification of the signature is performed as follows:
p = TEST ( a , KPa, h (m) ) === === (5)
wherein m= Data II P1 II P2.
Further, in the event of the ICS user frame UF is 2048 bytes
in length, for example, and the length of UF I{ P1 II P2 II a is 2448
bytes (2048 bytes + 400 bytes), there arises the necessity to re-
write the field representing the frame length within the control
field of the ICS user frame UF (e.g., the total-length field shown in
FIG.3) from 2048 bytes to 2448 bytes. Thus, the re-written ICS user
frame is represented as UF'. In the event that such an embodiment is
employed, the electronic signature or is represented as follows:
Q = SIGN (KSa, h (m) ) === === (6)
wherein m= UF' II P1 (I P2.
Verification of the signature is performed as follows:
p = TEST (a , KPa, h (m) ) === === (7)
wherein m= UF' II P1 II P2.
In the present Embodiment-16, UF, P1 and P2 may be re-
organized regarding the order thereof, so as to calculate, e.g., the
electronic signature a SIGN (KSa, h (m)) as m = P1 II P2 II tTF,
and set P1 II P2 II UF II a within the ICS user frame of the
receiving side. In the present embodiment, the encrypting function
109
CA 02538190 1997-11-07
is represented as y = ENC (Kl, x), and the decrypting function is
represented as x = DEC (K2, y). Here, "x" represents plaintext data,
"y" represents ciphertext data, ENC represents an encryption
function, DEC represents a decryption function, K1 represents an
encryption key, and K2 represents a decryption key. The art of
electronic signature is also called digital signature, and is
described in, e.g., "New Direction in Cryptography" (paper by W.
Diffie and M. E. Hellman, IEEE IT. Vol. IT-22 No. 6, pp.644-654,
1976), and "Encryption and Information Security" (Shigeo Tsujii,
1990, Shokodo, pp.127-138).
<<Configuration>>
As shown in FIG.71, the ICS 9000-1 includes access control
apparatuses 9010-1, 9010-2 and 9010-3, and relay apparatus 9120-1,
these apparatuses being connected by ICS network communication lines
9030-1, 9030-2 and 9030-3 which transfer ICS network frames. The
line unit 9011-1, the processing device 9012-1, the conversion table
9013-1 aiid the electronic signature linit 9017-1 are all provided
within the access control apparatus 9010-1. Provided within the
electronic signature unit 9017-1 are the following: program modules
for realizing the signature key KSa, the verification key KPa, the
electronic signature function SIGN and the hash function h(in), the
time/location parameter P1, and the signature function parameter P2.
Now, the signature key KSa is a secret value held by the access
control apparatus 9010-1, and the electronic signature unit has the
secret signature key therewithin, so there is the necessity to
110
CA 02538190 1997-11-07
prevent the secret signature key from leaking out. For example, the
electronic key unit may be stored inside a physically strong box,
structured such that the signature key cannot be read from the
outside. The plurality of ICS logic terminals of the line unit 9011-
1 are provided with the ICS network addresses "7721", "7722", "7725",
"7726", "7727" and "7728". An example of the conversion table 9013-1
is shown in FIG.72.
The encryption/decryption means 9018-1 includes encryption
functions, and holds the encryption key Ki and the decryption key K2.
When an ICS user frame UFl is inputted, the ciphertext UF2 is
generated as UF2 = ENC (Kl, UF1), and when the ciphertext UF2 is
inputted, the plaintext thereof is obtained as UFl = DEC (K2, UF2).
<<Operation>>
This operation is described with reference to the flowchart
shown in FIG.73. The user 9400-1 sends the ICS user frame F900 with
the receiver ICS user address "3600" to the ICS logic communication
line 9051-1. The processing device 9012-1 of the access control
apparatus 9010-1 receives the ICS user frame F900 from the ICS logic
terminal with the ICS network address "7721" of the line unit 9011-1,
and at the same time, obtains the ICS network address "7721" (Step
S2001) and checks whether the ICS network address "7721" has the
request identification thereof registered in the conversion table
901.3-1 as "3" (virtual dedicated line connection) or not (Step
S2002). In this case, the registration has not been made as such, so
next, the receiver ICS network address "3600" written in the ICS user
111
CA 02538190 1997-11-07
frame F900 is obtained in accordance with the ICS network address
"7721" (Step S2004), and checks whether the ICS network address
"3600" has the request identification thereof registered in the
conversion table as "2" (inter-corporation communication) or not
(Step S2005). In this case, the registration has been made, so next,
the receiving ICS network address "5522" is obtained from the
conversion table 9013-1 as preparation to perform the ICS
encapsulation.
Next, information related to accounting for the speed class
and the degree of priority is obtained from the coi-iversion table 9013-
1 (Step S2006). The value "1" is specified in the signature space in
the conversion table 9013-1, and also "YES" is recorded in the space
for electronic signature transmission, so the processing device 9012-
1 uses the program modules for realizing the electronic signature
function SIGN and the hash function h (m), the time/location
parameter P1, and the signature function parameter P2 stored in the
electronic signature unit 9017-1, and using the electronic signature
method described above, generates an electronic sigiiature for the ICS
user frame F900, and forms a new ICS user frame (represei-ited by UF2)
(Step S2019). This is represented in an expression (8) as follows:
UF2 = m 11 a ...... (8)
wherein m F900 II P1 II P2,
a = SIGN (KSa, h (m)).
In the above procedures, even if "1" is specified in the signature
space in the.conversion table 9013-1, if "NO" is recorded in the
112
CA 02538190 1997-11-07
space for electronic signature transmission, the electronic signature
unit 9017-1 does not operate and an electronic signature is not
provided.
Next, since the encryption class is specified as "1", the ICS
user frame UF2 is encrypted by the encryption/decryption means 9018-1
to form a new user frame UF3 (= ENC (K1, UF2)). In the event that
the encryption class is "0", encryption is not performed.
Next, the ICS encapsulation is performed by generating an ICS
network frame F901 written therein with the speed class, the degree
of priority and the encryption class (Step S2020), which is sent to
the ICS network communication line 9030-i within the ICS 9000-1 (Step
S2021). Although the above explanation has been made with regard to
the inter-corporation communication wherein the request
identification of the ICS network frame is set at "2" (inter-
corporation communication), in the event that the request
identification is "3" (virtual dedicated line connection), the
receiving ICS network address, information relating to account and
the like are obtained from the conversion table 9013-1 (Step S2003).
In the event that the request identification is "1" (intra-
corporation communication), the receiving ICS network address,
information relating to account and the like are obtained from the
conversion table 9013-1 (Step S2011), and, in tlie event that the
request identification is "4" (communication to an ICS network
server), the receiving ICS network address, information relating to
account and the like are obtained from the conversion table 9013-1
1 1.3
CA 02538190 1997-11-07
(Step S2013).
The ICS network frame F901 thus generated by the above
procedures reaches the access control apparatus 9010-2 tllrough the
ICS network communication line 9030-1 and the relay apparatus 9120-1,
is subjected to the ICS reverse-encapsulation, becomes the ICS
network frame F902, and reaches the user 9400-4 with the ICS user
address "3600" via the ICS logic communication path 9051-3. Here,
F902 = m (I Q, m = UF1 II P1 II P2, UF1 represents the ICS user frame
F900 before sending, Pl is the time/location parameter, P2 is the
electronic signature parameter, Q represents the electronic
signature, with Q= SIGN (KSa, h (m)) holding.
<<Electronic signature and a decryption in ICS reverse-
encapsulation>>
The user 9400-3 sends an ICS user frame F930 with a sender
ICS user address "3610" and a receiver ICS user address "2510" to the
ICS logic communication line 9051-4. The access control apparatus
9010-3 receives the ICS user frame F930, performs the ICS
encapsulation using the internal conversion table, generates an ICS
network frame F931 and sends it to the ICS network communication line
9030-3. The ICS network frame F931 reaches the access control
apparatus 9010-1 through the ICS network communication line 9030-1
and the access control apparatus 9020-1, is subjected to the ICS
reverse-encapsulation under administration of the conversion table
9013-1, and becomes the ICS user frame UFI. Since the value "1." is
specified in the signature space in the conversion table 9013-1, the
114
CA 02538190 1997-11-07
ICS user frame (UF1) obtained by the ICS reverse encapsulation is
deciphered using the encryption/decryption means 9018-1, thus
obtaining an ICS user frame UF1'. Here, UF1' = DEC (K2, UF1) holds,
and in the event that the encryption class is "0", encryption is not
performed.
Next, since the value "1" is specified in the signature space
in the conversion table 9013-1, and also "YES" is recorded in the
space for the electronic signature transmission, so the electronic
signature unit 9017-1 operates, and provides the ICS user frame with
the parameters P1 and P2 and the electronic signature Q, thus
forming a new ICS user frame F932. This is represented as follows:
F932 = m IlQ, m= UF1 II P1 Il P2
electronic signature Q= SIGN (KSa, h (m)) ...... (9)
and in the event that the aforementioned encryption has been
performed, UF1' is used instead of UF1. In the above procedures,
even if the value "1" is specified in the signature space in the
conversion table 9013-1, if "NO" is recorded in the space for
electronic signature transmission, an electronic signature is not
provided. The ICS user frame F932 reaches the user 9400-4 with the
ICS user address "2510" via the line unit 9011-1 and the ICS logic
communication path 9051-4.
<<In the case of signature request>>
In the event that an ICS user frame F940 witll a sender ICS
user address "2800" and a receiver ICS user address "3700" is
inputted from the line unit 9011-1, the request identification
115
CA 02538190 1997-11-07
corresponding to the ICS network address "7728" is "2", the value "0"
is specified in the signature space in the conversion table 9013-1
corresponding to the receiver ICS user address "3700", and at the
same time "YES" is recorded in the space for the electronic signature
transmission. Then, since the value "1" is specified in the
signature request space in the ICS user frame F940, the electronic
signature unit 9017-1 operates, and forms a new ICS user frame
provided with the parameters P1 and P2 and the electronic signature
Q.
In a case that the signature space in the conversion table
9013-1 is either "0" or "1" and "NO" is recorded in the space for the
electronic signature transmission, an electronic signature is not
provided before the ICS encapsulation, even if the value "1" is
specified in the signature request space in the ICS user frame F940.
In the same way, in a case that the signature request space in the
conversion table 9013-1 is either "0" or "1" and "NO" is recorded in
the space for the electronic signature reception of the ICS user
frame, an electronic signature is not provided after the ICS reverse
encapsulation, even if the value "1" is specified in the signature
space in the conversion table 9013-1.
On the other hand, in the event that the ICS user frame is to
receive the electronic signature at the time of sending by the
transmitting side access control apparatus, and furtlier is to receive
the electronic signature by the receiving side access control
apparatus, an transmitting electronic signature and a receiving
116
CA 02538190 1997-11-07
electronic signature are assigned, as shown in FIG.74. Also, there
are other examples wherein the value of the verification key KPa is
included in the signature function parameter P2. Thus, the trouble
of the ICS user frame receiver obtaining the verification key KPa
from the public key information center or the like can be omitted.
Further, in the event that the contents of the ICS user frame is an
electronic bill (order slip, receipt, etc.), an electronic signature
is attached to the electronic bill, along with the identification
code of the access control apparatus through which the electronic
bill has passed. In the event that either the sender (former) of the
electronic bill, of the receiver (recipient) tampers with the
electronic bill, the tampering can be discovered by means of the
electronic signature principle. Accordingly, as long as the
electronic signature key is a secret value, i.e., as long as the
operator of the access control apparatus which holds the signature
key therein ensures that the signature key is a secret value, the
electronic signature can be used as a tamper-proof public system.
Embodiment-17 (Electronic signature server and encryption server):
As shown in FIG.71 of Embodiment-16, the electronic signature
unit 9017-1 and the encryption/decryption means 9018-1 are situated
within the access control apparatus 9010-1. Conversely, with the
present embodiment, as shown in FIG.75, the access control
apparatuses 9310-1, 9310-2, 9310-3 and 9310-4 do not include an
electronic signature unit therewithin. Instead, electronic signature
117
CA 02538190 1997-11-07
servers 9340-1, 9340-2, 9340-3 and 9340-4 and ICS network
communication lines 9341-1, 9341-2, 9341-3 and 9341-4 are connected,
respectively. Each electronic signature server includes the
functions of the electronic signature unit described in the
Embodiment-16, and the manner of operation wherein electronic
signatures are provided before the ICS encapsulation or providing
electronic signature after the ICS reverse encapsulation in
cooperation with the access control apparatus is the same as -the
function of the electronic signature unit 9017-1 described in the
Embodiment-16, with signature key, verification key, electronic
signature function, program module for realizing the hash function,
time/location parameter and signature function parameter. The
electronic signature servers 9342-1 and 9342-2 are connected to the
relay apparatuses 9320-1 and 9320-2 via the ICS network communication
lines 9344-1 and 9344-2, respectively. The electronic signature
server has an ICS network addresses unique in the entire ICS network,
and has the function of communication with other electronic signature
servers or access control apparatuses using the ICS network server
communication function, thereby mutually exchanging the information
that each has. The electronic signature server 9342-1 is an
electronic signature server representing the VAN 9301-1, which
communicates with the electronic signature servers 9340-1 and 9340-2
within the VAN 9301-1 using the ICS network server communication
function, and is capable of obtaining information held by the
electronic signature servers. Also, the electronic signature server
118
CA 02538190 1997-11-07
9340-1 is capable of obtaining information relating to electronic
signature held by the electronic signature server 9340-2 (such as a
verification key), via the electronic signature server 9342-1. The
electronic signature server 9342-1 is capable of communicating with
the electronic signature server 9342-2 which represents another VAN
9301-2 using the ICS network server communication function, thereby
mutually exchanging the information relating to electronic signature
that each has. The electronic signature servers do not exchange
information regarding the secret signature keys held therewithin, and
tightly guard the secrecy of the signature keys.
Further, with the present embodiment, as shown in FIG.75, the
access control apparatuses 9310-i, 9310-2, 9310-3 and 9310-4 do not
include encryption/decryption means therein. Instead, a connection
is made with the encryption servers 9343-1, 9343-2, 9343-3 and 9343-
4, via respective ICS network communication lines. Each encryption
server has the functions of the aforementioned encryption/decryption
means 9018-1, and the manner of operation wherein the encryption of
the ICS use frames is provided before the ICS encapsulation or the
decryption of the encrypted ICS user frames after the ICS reverse
encapsulation in cooperation with the access control apparatus is the
same as the function of the encryption/decryption means 9018-1, with
program module for realizing the encryption function and the
decryption function, the encryption key and the decryption key. The
encryption servers 9343-5 and 9343-6 are connected to the relay
apparatuses 9320-1 and 9320-2 via the ICS network communication
119
CA 02538190 1997-11-07
lines. Each encryption server has an ICS network addresses unique in
the entire ICS network, and has the function of communication with
other encryption servers or the access control apparatuses using the
ICS network server communication function, thereby miitually
exchanging the information that each has. The encryption server 9343-
is an encryption server representing the VAN 9301-1, which
communicates with the encryption servers 9343-1 and 9343-2 within the
VAN 9301-1 using the ICS network server communication function, and
is capable of obtaining the information held by the encryption
servers. Also, the encryption server 9343-1 is capable of obtaining
the information relating to the encryption held by the encryption
server 9343-2 (such as an encryption key), via the encryption server
9342-5. The encryption server 9343-5 is capable of communicating
with the encryption server 9343-6 which represents another VAN 9301-2
using the ICS network server communication function, thereby mutually
exchanging the information that each has.
Embodiment-18 (Open connection):
Description will now be made regarding the ICS open
connection, i.e., preparatory procedures performed by the user and
the VAN operator operated in order to change the other party and
conduct the inter-corporation communication.
<<User application>>
The user applies to the VAN operator for an ICS name and an
ICS user address, and at the same time, shows ICS connection
120
CA 02538190 1997-11-07
conditions, a user identification and a payment method (address,
corporation name, paying bank account, etc.). If there is the ICS
user address for intra-corporation communications that the user has
decided, this is also shown, but not if there is none. The VAN
operator follows common rules decided upon beforehand with other VAN
operators, and decides upon the ICS name and the ICS user address and
informs the user thereof. The items for the ICS connection
conditions include ICS name conditions, communication band
conditions, accounting conditions, electronic signature conditions,
encryption conditions, open-zone conditions and dynamic conditions,
with the contents of these conditions being as describe below.
the ICS name conditions specify only the left portion of the
ICS name. For example, in the event that the ICS name is
"USR#1.ACS#1.DIS#1.VAN#1.3P.AS", the user specifies only the leftmost
"USR#1" (the VAN operator decides upon the remaining right portion).
The communication band conditions are speed class and degree of
priority. The accounting conditions are determined regarding charges
for a fixed amount for a certain tin-e span, charges for network usage
(network accounting), or charges for the contents of information sent
and received via electronic communication (information account), in
relation to communication band conditions, signature conditions,
encryption conditions, etc. The electronic signature conditions
specify whether or not to provide an electronic signature which can
prove with the date and time the face that the ICS user frame has
passed through the access control apparatus. The encryption
121
CA 02538190 1997-11-07
conditions specify whether or not the encryption is performed when
the ICS user frame is transferred. The open-zone conditions specify
whether or not to reject at the access control apparatus, an ICS
frame received from an unknown sender not registered in the
conversion table, or whether to form a temporary conversion table and
receive, etc. The dynamic alteration conditions specify the
functions which can be changed upon request by the user via ICS
frames, regarding the above-described conditions. The dynamic
alteration conditions are set so that the signature conditions or the
encryption conditions can be changed, but items important for VAN
operation cannot, such as ICS addresses or accounting.
<<ICS address administration server and ICS name server>>
Describing with reference to FIG.76 and FIG.77 to show the
conversion table 11113-1, FIG.78 to show the conversion table
template, FIG.79 to show the correlation table and FIG.80 to show the
ICS name server, according to the present embodiment, inside the ICS
11000-1 are provided the following: access control apparatuses 11110-
1, 11110-2 and 11110-3, relay apparatus 11116-1, ICS address
administration servers 11150-1 and 11150-2, ICS name servers 11160-1
and 11160-2, ICS conversion table servers 11170-1 and 11170-2, and
users 11132-1 and 11132-2. The ICS address administration server
11150-2 has in the correlation table contained therein the ICS
network address "8210", ICS user address "4200", aiid user address
related information, of the user 11132-2. The ICS name server 11160-
2 has in the ICS name conversion table contained therein the ICS name
122
CA 02538190 1997-11-07
"USR#3.ACS#3.DIS#3.VAN#3.JP.AS" and the ICS user address "4200", of
the user 11132-2. The VAN operator decides upon an ICS network
address ("7777") to use in accordance with the ICS user address
"3333" of the user 11132-1, provides it to the ICS logic terminal
11111-2 of the access control apparatus 11110-1, and connects the ICS
logic communication path 11133-1 which connects the user 11132-1 via
the gateway 11000-2. The ICS network address "7777" is a non-
disclosed value, so the user is not notified of it.
Next, the VAN operator directly writes the following items in
the correlation table 11152-1 witl7in the ICS address administration
server 11150-1, and in the conversion table 11152-1 via the data path
11153-1 and the processing device 11151-1: the ICS network address
"7777" determined by the method described above, the ICS user address
(inter-corporation) "3333", the ICS user address indicated by the
user (intra-corporation) "1111", and user address related
information, i.e., communication band conditions, account conditions,
electronic signature conditions, eiicryptioii conditions, open-zone
conditions, dynamic alteration conditions, user identification,
payment method, etc. The VAN operator further directly writes the
following in the ICS name conversion table 11162-1 in the ICS name
server 11160-1, via the data path 111.63-1 and processing device 11161-
1: the ICS name "USR#1.ACS#1.DIS#1.VAN#1.JP.AS" decided as described
above, the ICS user address "3333", and type "1" (indicating that the
ICS user address "3333" is registered in the ICS name conversion
table 11162-1). The above results expressed are as shown by the
123
CA 02538190 1997-11-07
correlation table 11152-1 and the ICS name conversion table 11162-1
At the point that the above-described writing of the various
types of information to the new user is completed, the ICS address
administration server 11150-1 and the ICS name server 11160-1 use the
ICS network ICS communication functions to communicate with the
respective network addresses "8910" and "8920" to notify the ICS
conversion table server 11170-1 that information has been obtained
regarding the ICS address and the ICS connection conditions of a new
user. Now, the ICS conversion table server 11170-1 is a type of the
ICS network server, and in the present embodiment has an ICS network
address "8100" and an ICS user address "2100".
<<ICS conversion table server>>
The ICS conversion table server 11170-1 reads the information
described in the correlation table 11152-1 of the ICS address
administration server 11150-1 using the ICS network communication
functions, and writes it in the conversion table template 11172-1.
That is, "7777" is written to the space for the transmitting ICS
network address (intra-corporation), "1111" is written to the space
for the sender ICS user address (inter-corporation), and "3333" is
written to the space for the sender ICS user address (inter-
corporation). In the event that there is no ICS user address for the
intra-corporation communication, the space for the sender ICS network
address (intra-corporation) is left blank. The request
identification number is set at "2" which indicates inter-corporation
communication. The other settings for the present embodiment are as
124
CA 02538190 1997-11-07
follows: the communication band conditions are set to the speed class
of "3" and the degree of priority "3", the electronic signature
conditions are set to "1", the transmitting signature specification
is "YES", the receiving signature specification is "NO", and the
account conditions are accounting class "4", the present embodiment
using an example of fixed charging system. The encryption conditions
are the encryption class "1", with the present embodiment being
arranged so as to specify the encryption of the ICS network frames
within the ICS. The open-zone class of the present embodiment is
"0". The dynamic alteration class "6" in the present embodiment
allows for the transmitting signature item to be changed upon request
by the user.
<<Usage of the ICS conversion table server (user)>>
The user 11132-1 writes "3333" as the sender ICS user address
and the ICS user address "2100" of the ICS conversion table server
11170-1 as the receiver ICS user address, and sends the ICS user
frame F1200 written with the receiver information (receiver ICS user
address or receiver ICS name) written to a user data portion of the
ICS user frame. The ICS conversion table server 11170-1 receives the
ICS user frame F1200 via the access control apparatus 11110-1, and
obtains the receiving ICS network address for the inter-corporation
communication according to whether the receiver informatioii in the
user data portion is a receiver ICS user address of a receiver ICS
name, using the method described below. Further, in the event that
the receiver ICS name has been specified, the receiver ICS user
125
CA 02538190 1997-11-07
address is also obtained.
(In the event there is specification of receiver ICS user address):
In the event that the aforementioned receiver information is
the receiver ICS user address "3800", the ICS conversion table sever
11170-1 by using the ICS network communication function inquires the
ICS address administration server 11150-1 coiinected to the access
control apparatus 11110-1, and obtains the ICS network address "7600"
(receiving ICS network address) corresponding to the ICS user address
"3800". Also, in the event that the receiver ICS user address is not
found in the correlation table 11152-1 (failure to find the ICS
network address), the ICS conversion table server 11170-1 receives a
"notification of failure to find the ICS network address" from the
ICS address administration server 11150-1.
(In the event that the receiver ICS name is specified):
In the event that the above receiver information is the
receiver ICS name "USR#3.ACS#3.DIS#3.VAN#3.JP.AS", the ICS conversion
table server 11170-1 by using the ICS network communication function
sends the ICS name "USR#3.ACS#3.DIS#3.VAN#3.JP.AS" to the ICS name
server 11160-1 connected to the same access control apparatus 11110-
1. The ICS name server 11160-1 holds the ICS network addresses of
other ICS name servers in a form corresponding to the ICS name (the
portion of the ICS name after removing the leftmost portion "USR#n"),
and in the present embodiment, the ICS name server 11160-1 searches
the ICS name conversion table 11162-1, finds the ICS network address
"8930" of the ICS name server 11160-2 administrating
126
CA 02538190 1997-11-07
"ACS#3.DIS#3.VAN#3.JP.AS" and inquires regarding the address "8930",
using the ICS network communication functions, and obtains the ICS
user address "4200" (receiver ICS user address) and the ICS network
address "8210" (receiving ICS network address) corresponding to the
aforemeiltioned ICS name "USR#3.ACS#3.DIS#3.VAN#3.JP.AS". In the
above procedures, the ICS name server 11160-2 has contacted the ICS
address administration server 11150-2 regarding the ICS network
address of the user 11132-2, and obtained the address "8210".
(Completion of the conversion table 11113-1):
In the event that the receiver ICS user address is specified,
the ICS conversion table server 11170-1 adds the receiver ICS user
address "3800" and the receiving ICS network address "7600" to the
conversion table 11113-1, thus completing the portion of the
conversion table 11113-1 corresponding to the receiving user. In the
event that the receiver ICS name is specified, the ICS conversion
table server 11170-1 adds the receiver ICS user address "4200" and
the receiving ICS network address "8210" to the conversion table
11113-1, thus completing the portion of the conversion table 11113-1
corresponding to the receiving user. Also, in the event that a
"notification of failure to find the ICS network address" is received
from the ICS address administration server 11150-1 or the ICS name
server 11160-1, the ICS coiiversion table server 11170-1 sends an ICS
frame indicating failure to add to the conversion table, to the
requesting user 11132-1.
<<Other usage of the ICS conversion table server (user)>>
127
CA 02538190 1997-11-07
The user 11132-1 requests a notification of the user-specific
information to the user, by means of sending an ICS user frame
written with a request for the notification of the contents of user-
specific information in the conversion table 11113-1 to the ICS
conversion table server 11170-1. Further, the user can use a dynamic
alteration class which has been agreed on beforehand with the VAN
operator to re-write a part of the conversion table 11113-1. The
dynamic alteration class is decided upon as 1, 2, ..., and the
contents thereof being as follows: the dynamic alteration class 1 is
a specification for increasing the user-specific degree of priority
by "1", the dynamic alteration class 2 is a specification for
decreasing the user-specific degree of priority by "1", and the
dynamic alteration class 3 sets the transmitting signature to "YES",
and at the same time, specifies changing the encryption class to "2".
<<Usage of the conversion table>>
The method of using the conversion table formed according to
the above procedures has been described in the Embodiment-i and so
forth. Although in the Embodiment-1, description was made regarding
the method of forming a temporary conversion table if there is no
conversion table at the time that the access control apparatus
receives the ICS network frame and is to perform the ICS reverse
encapsulation thereof, but with the present embodiment, the open-zone
class of the conversion table will be used. That is, at the time
that the access control apparatus receives the ICS network frame and
is to perform the ICS reverse encapsulation thereof, in the event
128
CA 02538190 1997-11-07
that the received "pair of receiving ICS network address and
tansmitting ICS network address contained in the network control
field of the ICS network frame" has not been registered in the
conversion table as a "pair of transmitting ICS network address and
receiving ICS network address", a temporary conversion table is set
in the same manner as with the aforementioned embodiment in the event
that the open-zone class is set to "2", but in the event that the
open-zone class is set to "1", a temporary conversion table is not
set. Further, in the event that the open-zone class is set to "0",
not only is a temporary conversion table not set, but the received
ICS network frame is discarded. In this case, the ICS user frame is
not delivered to the user. That is, in the event that the open-zone
,class is set to "0", reception of an unknown sender not registered in
the conversion table is rejected, thus realizing what is called a
"closed connection". Incidentally, in the above, in the event that
the request identification is "4", the open-zone class is always
handled as being set to "1", i.e., a temporary conversion table is
not set.
<<Variations of the embodiment>>
The method for the VAN operator to use the data path 11153-1
and the data path 11163-1 to input the ICS addresses, the ICS
connection conditions and the like to the ICS address administration
server 11150-1 and the ICS name server 11160-1 has been described
with regard to the above embodiment. Instead, the arrangement may be
such that the VAN operator does not use these data paths, but rather
129
CA 02538190 1997-11-07
forms a special ICS network server within the ICS 11000-1, so as to
directly input the ICS addresses, the ICS connection conditions and
the like to the ICS address administration server 11150-1 and the ICS
name server 11160-1, using the ICS network communication function,
thus re-writing the contents of the conversion table 11152-1 and the
ICS name conversion table.
Embodiment-19 (Separation of functions of the access control
apparatus):
As shown in FIG.76 of the Embodiment-18, the ICS address
administration server 11150-1, the ICS name server 11160-1., and the
ICS conversion table server 11170-1 are each connected to the access
control apparatus 11110-1, with the ICS encapsulation and the ICS
reverse encapsulation being performed within the access control
apparatus 11110-1 using the conversion table 11113-1. Conversely,
with the present embodiment, the functions of the access control
apparatus 11110-1 are separated into an aggregation access control
apparatus 14110-1 and a plurality of simplified access control
apparatuses 14210-1, 14210-2 and 14210-3. That is, as shown in
FIG.81, the access control apparatus 11110-1 is connected to the
simplified access control apparatuses 14210-1, 14210-2 and 14210-3,
via respective ICS network comnninication lines 14190-1, 14190-2 and
14190-3. The ICS address administration server 14150-1, the ICS name
server 14160-1, the ICS conversion table server 14170-1, the ICS
accounting server 14180-1, the electronic signature server 14181-1,
130
CA 02538190 1997-11-07
J
the encryption server 14182-1, the operation administration server
14183-1 and the ICS network server 14184-1 are connected with the
aggregation access control apparatus 14110-1 via the respective ICS
network communication lines 14191-1, 14191-2, 14191-3, 14191-4, 14191-
5, 14191-6, 14191-7 and 14191-8. Further, the conversion table 11113-
1 within the access control apparatus 11110-1 is separated into an
aggregation conversion table 14113-1 and a plurality of simplified
conversion tables 14213-1, 14213-2 and 14213-3. An example of the
aggregation conversion table 14113-1 is shown in FIG.82 and an
example of the simplified conversion table 14213-1 is shown in
FIG.83.
However, part of the aggregation conversion table and
simplified conversion tables overlap. That is, the following four
items are contained in both conversion tables: transmitting ICS
network address, request identification, speed class and degree of
priority. There is no fundamental difference between the temporary
partial conversion table 14214-1 with the temporary conversion table
described with the Embodiment-1 and otlierwise, with the items
contained in the temporary partial conversion table 14214-1 being the
same as the items contained in the simplified conversion table 14213-
1. The line unit 14211-1 within the simplified access control
apparatus 14210-1 has the same functions as the line unit 11111-1
within the access control apparatuses 11110-1.
The simplified access control apparatus 14210-1 uses the
simplified conversion table 14213-1 to perform the ICS eilcapsulation
131
CA 02538190 1997-11-07
at a time of sending and the ICS reverse encapsulation at a time of
receiving, and the aggregation access control apparatus 14110-1 uses
the aggregation conversion table 14113-1 to perform processing
relating to the electronic signature and the account, as described
above. Also, by means of the plurality of simplified access control
apparatuses 14210-1, 14210-2 and 14210-3 functioning together with
the aggregation access control apparatus 14110-1, the combined
functions are the same as those of the access control apparatus 11110-
1. The user 14132-1 sends an ICS user frame F1300 with a sender ICS
user address "3333" and a receiver ICS user address "4200" to the ICS
logic communication line 14133-1. As shown in the flowchart in
FIG.84, the processing device 14212-1 of the simplified access
control apparatuses 14210-1 receives the ICS user frame F1300 from
the ICS logic terminal within ICS network address "7777" of the line
unit 14211-1, and at the same time obtains the ICS network address
"7777" (Step S2501), and checks whether or not the address "7777" is
registered in the simplified conversion table 14213-1 with the
request identification thereof being "3", indicating a virtual
dedicated line connection (Step S2502). In this case, the
registration has not been made, so the receiver ICS user address
"4200" written on the ICS user frame F1300 is obtained corresponding
to the ICS network address "7777" (Step S2504), and it is further
checked whether the address "4200" is registered in the simplified
conversion table 14213-1 with the request identification thereof
being "2", indicating inter-corporation communication (Step S2505).
132
CA 02538190 1997-11-07
In this case, the registration has been made, so in preparation for
the ICS encapsulation, the receiving ICS network address "8210" is
obtained from the simplified conversion table 14213-1 (Step S2506).
The simplified access control apparatus 14210-1 next performs
the ICS encapsulation by means of generating in the ICS network frame
an ICS network frame F1301 inscribed with the speed class and the
degree of priority obtained from the simplified conversion table
14213-1 (Step S2520), and sending it to the aggregation access
control apparatus (Step S2521). Now, as described above, the speed
class "3", the degree of priority "3" and the encryption class "0"
which are items of the simplified conversion table 14213-1 are
written to the expansion portion of the ICS network controlling unit.
The aggregation access control apparatus 14110-i receives the
ICS network frame F1301 from the simplified access control apparatus
14210-1, and based on the face that the ICS network frame F1301
passes through the aggregation access control apparatus 14110-1,
forms an account information frame FK01 and sends it to the
accounting server 14180-1. The information sucli as the request
identification, the speed class, the degree of priority, the account
classand the encryption class which are registered in the
aggregation conversion table 14113-1 are referred to in order to form
the account information frame FKO1. The signature, transmitting
signature and receiving signature of the aggregation conversion table
14113-1 items are used for providing the electronic signature, and as
described in other embodiments, the electronic signing is performed
133
CA 02538190 1997-11-07
by applying for the electronic signature to the electronic signature
server 14181-1. In the same way, in the event that the encryption
class specification is "1" which indicates the encryption, the
encryption is performed by applying the encryption to the encryption
server 14182-1. Once the above processing has been completed, the
aggregation access control apparatus 14110-i sends the ICS network
frame F1302 to another access control apparatus 14110-2 and other
aggregation access control apparatuses, via the ICS network
communication line 14190-4. Incidentally, the format of the ICS
network frame F1302 changes in content in the event that the
electronic signature server or the encryption server operate, due to
an addition of the electronic signatures or a conversion to the
ciphertext as described above, but if neither the electronic
signature server nor the encryption server have operated, the ICS
network frame F1302 is the same as the ICS network frame F1301. Not
only can the simplified access control apparatus 14210-1 be realized
with practically no changes to the existing router, but there are
other economic advantages such as the nuniber of users contained in
the simplified access control apparatus 14210-1 not being great, and
in the event that the users are scattered over a wide geographic
area, the total number of each of ICS address administration servers,
ICS name servers, ICS conversion table servers, account severs,
electronic signature severs and encryption servers can be reduced.
The operating administration server 14183-1 is provided with
an ICS network address, is connected to the aggregation access
134
CA 02538190 1997-11-07
control apparatus 14110-1 and the relay apparatuses, and performs
exchange with other operation administration servers, access control
apparatuses, ICS address administration servers, etc. regarding
information regarding communication conditions within the ICS
(communication traffic, etc.) or trouble, using the ICS network
communication functions.
Now, the item open-zone class included in the simplified
conversion table 14213-1 of the simplified access control apparatus
14210-1 is used for the same processing as the processing of the open-
zone class registered in the conversion table of the access control
apparatus, as described above. That is, at the time that the
simplified access control apparatus 14210-1 receives the ICS network
frame and is to perform the ICS reverse encapsulation thereof, in the
event that the received "pair of receiving ICS network address and
transmitting ICS network address contained in the network control
field of the ICS network frame" has not been registered in the
simplified conversion table 14213-1 as a "pair of transmitting ICS
network address and the receiving ICS network address", a temporary
partial conversion table 14214-1 is set in the aforementioned manner
in the event that the open-zone class is set to "2", but in the event
that the open-zone class is set to "1", a temporary partial
conversion table is not set. Further, in the event that the open-
zone class is set to "0", not only is a temporary partial conversion
table not set, but the received ICS network frame is discarded. In
this case, the ICS user frame is not delivered to the user. In this
].35
CA 02538190 1997-11-07
arrangement, "0" indicates that reception of an unknown sender not
registered in the conversion table is to be rejected, thus realizing
what is called a "closed connection".
As described in the above embodiment, the ICS address
administration server and ICS name server may be integrated into a
single ICS address name administration server, with the aggregation
access control apparatus being used being connected to the ICS
address name administration server and ICS network communication
line. Also, an arrangement may be employed in the above embodiment
wherein items of the speed class and the degree of priority are not
provided in the simplified conversion table 14213-1, with a "0" being
written at the point of the ICS encapsulation to the expansion
portion of the ICS network controlling iinit for the speed class and
the degree of priority, indicating that there is no specification.
In the same way, an arrangement may be employed wherein specification
of the open-zone class is not provided in the simplified conversioii
table 14213-1, with a "0" being written to the expansion portion of
the ICS network controlling unit for the speed class and the degree
of priority, indicating that there is no specification.
Thus, according to the present invention, administration of
information communication is performed with a unified address system,
and various services can be provided, without using dedicated lines
or the Internet, thus enabling structuring a large-scale
communication system with high security and with relatively low
costs. Also, inter-corporation communication can be performed
136
CA 02538190 1997-11-07
between individual corporations (including government organizations,
universities, and so forth) which had conventionally been services
separately with practically no change to the address system for
computer communications. Further, since the network administrator
holds the network control authority, the overall administration of
the network becomes clear, increasing ease of securing reliability
and also markedly improving security.
137