Note: Descriptions are shown in the official language in which they were submitted.
CA 02553081 2006-07-24
A METHOD FOR BINDING A SECURITY ELEMENT
TO A MOBILE DEVICE
Field of the Invention
[0001]
The present invention relates to the field of security and encryption. In
particular, it relates to methods of binding security elements, such as
passwords, to
mobile devices, such as mobile phones.
Background of the Invention
[0002]
The rapid increase in the use of online services for shopping, banking and
other financial transactions has brought with it an increase in identity theft
and fraud.
The most common existing security techniques rely on the user having a
password
associated with an online identity (user name). However, schemes such as
keystroke
logging, phishing and similar techniques are used to improperly record or
intercept
passwords and the associated user names. Thus, the username/password data can
be
taken and used in fraudulent transactions, leading to loss of money, loss of
time and loss
of reputation, not only for the user whose identity was taken, but also for
those parties
who were fraudulently induced into believing they were transacting with the
user.
[0003]
The flaws in the username/password system have lead to the development of
two-factor (also known as "strong") authentication systems. Two-factor
authentication is
based on two elements: 1) something the user knows (i.e. a password or PIN);
and 2)
something the user has (an authenticator, often a physical device referred to
as a "fob").
The fob and the password are used together to provide an additional level of
security, as
either one, individually, is of no use without the other.
[0004]
Despite the improved security, two-factor authentication is still of limited
use
due to the requirement of the hardware fob. Furthermore, each secure system
requires its
own fob, creating a problem for the user who then needs to keep track of the
multiple
fobs necessary for access to multiple services.
[0005]
One method of two-factor authentication is the use of One-Time Password
(OTP) authentication. Using OTP authentication, a new OTP value (OTP token) is
- 1 -
57522-2[CA-121(KB)
CA 02553081 2006-07-24
generated for use on a per-event basis (e.g. each remote logon attempt) or on
a time-
window basis (e.g. once per minute). The user is typically required to use a
fob, either to
generate the OTP, or to contact the system and receive the OTP.
[0006]
Ideally, the fob can be replaced by another device already carried by the
user,
such as a mobile phone or PDA, which stores a set of OTP credentials for use
when
access the secure system. However, this creates a new problem that must be
addressed,
namely, the requirement that the OTP credentials be properly encrypted and
bound to the
device.
Summary of the Invention
[0007]
According to an aspect of the present invention there is provided a method of
binding a security element to a device, comprising: generating a passkey to
encrypt the
security element, the passkey being a combination of attributes, and one of
the attributes
being a Device ID associated with said device, encrypting the security element
on the
device using the passkey, and retrieving the Device ID from the device to
decrypt the
security element.
[0008]
Preferably, the device is a mobile device. Also preferably, the combination of
attributes includes the following: a) a build secret, the build secret
consisting of a random
alphanumeric string; b) a salt, the salt consisting of a random alphanumeric
string; and
wherein the build string and the salt are stored as non-printable strings
within encryption
code of the passkey.
[0009]
Preferably, the security element is an OTP credential for use with a secure
server.
[0010]
Other preferable attributes used include a user passphrase, a software
application ID associated with a software program used by said device and/or a
network
ID associated with a network service provider used by said mobile device.
[0011]
Other and further advantages and features of the invention will be apparent to
those skilled in the art from the following detailed description thereof,
taken in
conjunction with the accompanying drawings.
- 2 -
57522-2[CA-12](KB)
CA 02553081 2010-04-01
Brief Description of the Drawings
[0012]
The invention will now be described in more detail, by way of example only,
with reference to the accompanying drawings, in which like numbers refer to
like
elements, wherein:
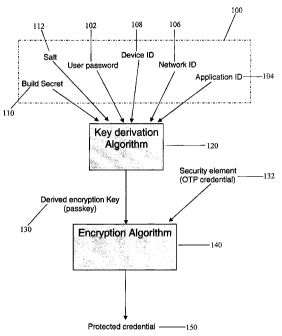
Figure 1 is a block diagram of the passkey creation and credential encryption
method.
Detailed Description of the Preferred Embodiments
[0013]
The inventive method presented herein consists of binding a chosen security
element to a specific mobile device used by a user at the time the security
element is
being supplied to the user. The method is of particular application when the
security
element needs to be generated by the secure server at the time of the first
request by the
user for access to the secure server. The security element is then used by the
user for
future access to the secure server from the mobile device.
[0014] The
security element can be of any known type and is typically application
and sever dependent. A preferred embodiment of security element is an OTP (One
Time
Password) credential which is stored on the mobile device to enable access to
a secure
server. The OTP credential is then used by the user during future transactions
with the
secure server as part of a two-factor authentication process.
[0015] With
reference to Figure 1, a combination of attributes 100 is used to create
an encryption key, herein referred to as a passkey 130, is used to encrypt the
security
element. The attributes used to create the passkey can include one or more of:
a user
passphrase (i.e. a password or PIN) 102 (not the same password/PIN used in the
two-
factor authentication), an application (software) ID 104, a network ID 106, a
device ID
108, and other randomly-generated strings 110, 112. Of these, the device ID
108
provides the strongest binding of the passkey 130 to the specific device.
[0016] An
example of a passkey 130 meeting requirements for a Triple DES (Data
Encryption Standard) key as generated by the inventive method is shown using
four
separate attributes combined to generate the passkey 130:
- 3 -
57522-2[CA-12](KB)
CA 02553081 2006-07-24
100171
1) The Device ID 108. This is number, alphanumeric string or code that
identifies the device being used by the user to connect to the server. Device
IDs can be
unique, such as the device's serial number or IMEI (International Mobile
Equipment
Identity) number. Alternatively, this can be a SHA-1 hash or other hash or
digest of the
phone number or email address associated with the device. In any case, the
Device ID is
read from the device every time the protected security element is accessed.
[0018]
2) The build secret 110. A build secret is a randomly generated string (e.g.
20
characters) which is generated during the build of the application. The build
secret is
stored in the encryption code as a non-printable (non-accessible) string. For
additional
security, the build secret 110 may be stored as a set of segmented non-
printable strings in
different parts of the code to make it more difficult to discover.
[0019]
3) The salt 112. A salt is a random number generated during the build
process. The salt is stored in the encryption code as a non-printable (non-
accessible)
string. As with the build secret 110, the salt 112 may be stored as a set of
segmented
non-printable strings in different parts of the code.
[0020]
4) The user passphrase 102. This is a string of characters input by the user
during the first access attempt. The passphrase can be changed by the user on
their
device at a later time. The user passphrase 102 is only known by the user and
is not sent
over the connection to the server.
100211 The attributes are combined using a derivation algorithm 120 to
create the
passkey 130. Once the passkey 130 is created, it is used to encrypt 140 the
security
element (i.e. OTP credential) 132 stored on the device. The result is an
encrypted,
protected security element 150. When the user needs to decrypt the security
element,
they input the user passphrase 102, the Device ID 108 is read off the device,
and the
security element 150 is decrypted for use.
100221
Thus, a form of two-factor authentication is now provided for the stored
security element 150. If the device falls into the hands of an unauthorized
user, the
security element 150 is inaccessible without the user passphrase 102.
Conversely, if the
security element 150 is somehow removed from the device and the passphrase 102
obtained, it remains inaccessible as the proper Device ID 108 cannot be read.
- 4 -
57522-2[CA-12](KB)
CA 02553081 2006-07-24
[0023]
This method can be modified or further expanded by using an application
(software) ID 104 as an additional attribute of the passkey generation method
or as a
replacement for one of the existing attributes. An application ID 104 is a
unique
identifier associated with the software application instance used by the user,
either to
decrypt the security element, or to access the secure system. The application
ID 104 is
similar to the Device ID 108 in that it is a number, alphanumeric string or
code that
identifies the software application instance. The application ID 104 is
created at the time
the software is downloaded or installed on the device.
[0024]
Another potential attribute is a network ID 106 associated with the network
service provider used by the mobile device. Given that it is generally
desirable to allow
users to have the ability to switch service providers of their own volition,
use of this
attribute is likely to be limited. However, the network ID 106 could be used
to restrict
access to certain providers or certain geographic areas.
[0025]
While the above method contemplates binding and protecting the security
elements on the device, it is equally applicable for use in protecting the
security element
during the provisioning or transportation to the device. The binding process
can be
applied by repackaging or recompiling the software application for a specific
user and
device at the time of download.
[0026]
While the above method has been presented in the context of mobile devices,
such as mobile phones, the method is equally applicable to fixed devices, such
as laptop
or desktop PCs, as well. While fixed devices generally have superior
integrated security
measures than mobiles devices, the simplicity and device-branding capabilities
of the
method presented herein provide these same security benefits to fixed devices
as well.
[0027]
This concludes the description of a presently preferred embodiment of the
invention. The foregoing description has been presented for the purpose of
illustration
and is not intended to be exhaustive or to limit the invention to the precise
form
disclosed. Many modifications and variations are possible in light of the
above teaching
and will be apparent to those skilled in the art. It is intended the scope of
the invention be
limited not by this description but by the claims that follow.
- 5 -
57522-2[CA-121(KB)