Note: Descriptions are shown in the official language in which they were submitted.
CA 02588771 2007-05-22
Notification System and Method for a Mobile Data Communication
Device
BACKGROUND OF THE INVENTION
The present invention is directed toward the field of notifications for a
mobile
communications device.
The mobile data communication device is preferably coupled to the host system
via a wireless network and one or more landline networks. Due to the bandwidth
limitations of wireless networks, only a portion of a user-selected data item
is generally
redirected to the user's mobile device, with the user given the option of then
retrieving the
entire data item (or some other portion of the data item) from the host
system.
Instead of warehousing (or storing) the user's data items at the host system
and the
"synchronizing" the mobile data communication device to data items stored at
the host
system when the mobile device requests that such items of information be
communicated
to it, the present invention employs a "push" paradigm that continuously
packages and
retransmits the user-selected items of information to the mobile data
communication
device in response to a
1
CA 02588771 2007-05-22
triggering event detected at the host system. Wireless mobile data
communications devices, especially those that can return a confirmation signal
to the host that the pushed data has been received are- especially well suited
for
this type of push paradigm.
Present systems and methods for replicating information from a host
system to a user's mobile data communication device are typically
"synchronization" systems in which the user's data items are warehoused (or
stored) at the host system for an indefinite period of time and then
transmitted
in bulk only in response to a user request. In these types of systems and
methods, when replication of the warehoused data items to the mobile device is
desired, the user typically places the mobile device in an interface cradle
that is
electrically connected to the host system via some form local, dedicated
communication, such as a serial cable or an infrared or other type of wireless
link. Software executing on the mobile data communication device then
transmits commands via the local communications link to the host system to
cause the host to begin transmitting the user's data items for storage in a
memory bank of the mobile device. In these synchronization schemes, the
mobile unit "pulls" the warehoused information from the host system in a batch
each time the user desires to replicate information between the two devices.
Therefore, the two systems (host and mobile) only maintain the same data
items after a user-initiated command sequence that causes the mobile device to
download the data items from the host system. A general problem with these
synchronization systems is that the only time that the user data items are
1)
CA 02588771 2007-05-22
replicated between the host system and the mobile data communication device
is when the user commands the mobile device to download or pull the user data
from the host system. Five minutes later a new message could be sent to the
user, but the user would not receive that message until the next time the user
fetches the user data items. Thus, a user may fail to respond to an emergency
update or message because the user only periodically synchronizes the system,
such as once per day. Other problems with these systems include: (1) the
amount of data to be reconciled between the host and the mobile device can
become large if the user does not "synchronize" on a daily or hourly basis,
leading to bandwidth difficulties, particularly when the mobile device is
communicating via a wireless packet-switched network; and (2) reconciling
large amounts of data, as can accrue in these batch-mode synchronization
systems, can require a great deal of communication between the host and the
mobile device, thus leading to a more complex, costly ar)d energy-inefficient
system. A more automated, continuous, efficient and reliable system of
ensuring that user data items are replicated at the user's mobile device is
therefore needed.
The user's mobile device is in many instances removably stored in a
holster that is detachably connected to the user's belt or other piece of
clothing.
Traditionally, upon the detection of a new data item, an audible signal and/or
the vibration of the device is the form of notification provided to the user.
Such traditional notification is problematic at best and do not provide the
user
any flexibility for rapid decision-making. A heavy user of the system and
3
CA 02588771 2007-05-22
method for pushing information from a host to a mobile communication device
disclosed herein is quickly overcome with persistent data item notification
during the busiest time periods in a business day. After receiving a
traditional
notification, the user reaches for his mobile device in the holster to examine
the
displayed data item associated with the notification. Frequent traditional
notifications can become annoying to a heavy user; thereby causing the user to
switch off the audible and/or vibrate notifications all together.
Traditional mobile communication devices, which implement the system
and method of pushing information from a host as described herein, also lack
the facility of an assistant or secretary to screen pages, emails, voice
mails, etc
that arrive at the mobile communication device. In many ways, more work is
created for the user when using such a device because a form of wireless
umbilical cord extends from the user's host system to the user via the mobile
communication device without the facility of a secretary orl assistant to
manage
and/or screen the notifications. The user cannot differentiate unimportant
data
item notifications from those data items that are relevant or very important
without having to commit to the physical action of reviewing the display of
the
device. An additional feature of the present invention is that the push
paradigm,
in combination with a return communications pathway, lends itself well to a
system that permits a user to control remotely, through the user's mobile
device, a number of aspects of the host system.
There remains a general need in this art for a system and method of
continuously pushing user-selected data items (or certain portions of the
4
CA 02588771 2007-05-22
selected data items) stored at a host system to a user's mobile data
communication device.
There remains a more particular need for such a system and, method
where user-selected data items are continuously "pushed" from the host system
to the mobile data communication device upon the occurrence of one or more
user-defined triggering events.
There remains an additional need for such a system and method that
provides flexibility in the types and quantities of user data items that are
pushed
from the host system to the mobile data communication device and that also
provides flexibility in the configuration and types of events that can serve
to
trigger the redirection of the user data items.
There remains yet an additional need for such a system and method that
can operate locally on a user's desktop PC or at a distance via a network
server.
There remains still another need for such a system and method that
provides for secure, transparent delivery of the user-selected data items from
the host system to the mobile device.
There remains still another need for such a system and method that
provides for notification in a user-selectable manner of user-selectable data
items arriving at the mobile device.
There remains yet another need for such a system and method that
provides for notification of mobile-specific event occurrences such as, but
not
5
CA 02588771 2007-05-22
limited to calendar event reminders and unsuccessful transmission of user data
items originating from the mobile device.
There also remains still another need for such a system and method that
provides for notification of user-selected data items from the host system to
the
mobile device in a user-selectable manner that allows the user of the mobile
communication device the quick and hands-free ability to determine whether or
not to act on a notification.
There also remains yet another need to integrate secretarial-like features
into a mobile communication device using the system and method of pushing
information from a host to a mobile communication device.
SUMMARY OF THE INVENTION
The present invention overcomes the problems noted above and
satisfies the needs in this field for a system and method of pyshing user-
selected
data items from a host system to a user's mobile data communication device
upon detecting the occurrence of one or more user-defined event triggers. As
used in this application, the term host system refers to the computer where
the
redirector software is operating. In the preferred embodiment of the present
invention, the host system is a user's desktop PC, although, alternatively,
the
host system could be a network server connected to the user's PC via a local-
area network ("LAN)", or could be any other system that is in communication
with the user's desktop PC.
6
CA 02588771 2007-05-22
According to the present invention a system and method is provided
such that an event-driven redirection computer program ("redirector program")
operating at the host system, which, upon sensing a particular user-defined
event has occurred, characterizes user-selected data items and then redirects
them from the host system to the user's mobile data communication device.
Upon arrival of the user-selected data items at the mobile data communication
device, the present invention notifies the user in a user-selectable manner.
In
addition to the arrival of data items on the device, the occurrence of certain
events that are specific to the mobile communication device and the
transmission status of data items are events that are within the scope of the
invention to notify the user.
A redirector program operating at the host system enables the user to
redirect or mirror certain user-selected data items (or parts of data items)
from
the host system to the user's mobile data communication device upon detecting
I
f
that one or more user-defined triggering events has occurred. Also operating
at the host system are various sub-systems that can be configured to create
triggering events, such as a screen saver sub-system or a keyboard sub-system,
as well as sub-systems for repackaging the user's data items for transparent
delivery to the mobile data device, such as a TCP/IP sub-system or one or
more E-Mail sub-systems. Other sub-systems for creating triggering events
and repackaging the user's data items could also be present at the host
system.
The host system also includes a primary memory store where the user's data
items are normally stored.
7
CA 02588771 2007-05-22
Using the redirector program, the user can select certain data items
types for redirection, such as E-mail messages, calendar events, meeting
notifications, address entries, journal entries, personal reminders etc.
Having
selected the data items for redirection, the user can then configure one or
more
event triggers to be sensed by the redirector program to initiate redirection
of
the user data items. These user-defined trigger points (or event triggers)
include external events, internal events and networked events. Examples of
external events include: receiving a message from the user's mobile data
communication device to begin redirection; receiving a similar message from
some external computer; sensing that the user is no longer in the vicinity of
the
host system; or any other event that is external to the host system. Internal
events could be a calendar alarm, screen saver activation, keyboard timeout,
programmable timer, or any other user-defined event that is internal to the
host
system. Networked events are user-defined messages that are transmitted to
F
the host system from another computer coupled to the host system via a
network to initiate redirection. These are just some of the examples of the
types of user-defined events that can trigger the redirector program to push
data items from the host to the mobile device. Although in the preferred
embodiment it is anticipated that the configuration that specifies which data
items will be redirected and in what form will be set at the host system, it
is
within the scope of this invention that such configuration may be set or
modified through data sent from the mobile communications device.
8
CA 02588771 2007-05-22
In addition to the functionality noted above, the redirector program
provides a set of software-implemented control functions for determining the
type of mobile data communication device and its address, for programming a
preferred list of message types that are to be redirected, and for determining
whether the mobile device can receive and process certain types of message
attachments, such as word processor or voice attachments. The determination
of whether a particular mobile device can receive and process attachments is
initially configured by the user of that mobile device at the host system.
This
configuration can be altered on a global or per message basis by transmitting
a
command message from the mobile device to the host system. If the redirector
is configured so that the mobile data device cannot receive and process word
processor or voice attachments, then the redirector routes these attachments
to
an external machine that is compatible with the particular attachment, such as
an attached printer or networked fax machine or telephone. Other types of
-It
attachments could be redirected to other types of external machines in a
similar
fashion, depending upon the capabilities of the mobile device. For example, if
a
user is traveling and receives a message with an attachment that the user's
mobile device can process or display, the user may from a mobile
communications device send a command message to the host system indicating
that that attachment is to be sent to a fax machine at a hotel where the user
will
be spending the evening. This enables the user to receive important E-mail
attachments as long as the host system is provided with sufficient information
about the destination where the attachment is to be forwarded.
9
CA 02588771 2007-05-22
Once an event has triggered redirection of the user data items, the host
system then repackages these items in a manner that is transparent to the
mobile data communication device, so that information on the mobile device
appears similar to information on the user's host system. In one embodiment
of the present invention, the repackaging of these items includes
characterizing
the data item type and the priority ranking associated therewith. As discussed
above, data item types preferably include E-mail messages, calendar events,
meeting notifications, address entries, journal entries, personal reminders,
instant email notifications, etc. Priority rankings preferably include regular
importance, very important and emergency. It is to be understood that it is
clearly within the scope of the invention to expand or decrease the levels of
priority rankings in an alternative embodiment of the invention. By
characterizing the data item, the mobile data communication device can act on
the characterization according to the user-selectable notification scheme as
set
forth on the mobile device, or alternatively as set forth on the host system.
The
preferred repackaging method includes wrapping the user data items in an E-
mail envelope that corresponds to the address of the mobile data
communication device, although, alternatively, other repackaging methods
could be used with the present invention, such as special-purpose TCP/IP
wrapping techniques, or other methods of wrapping the user selected data
items. The repackaging preferably results in E-mail messages generated by the
user from the mobile device to be transmitted from the host system, thus
enabling the user to appear to have a single E-mail address, such that the
CA 02588771 2007-05-22
recipients of messages sent from the mobile communications device do not
know where the user was physically located when the message was first sent.
The repackaging also permits both messages to the mobile device and sent
from the mobile device to be encrypted and decrypted as well as compressed
and decompressed.
In an alternative system and method, the redirector program executes
on a network server, and the server is programmed to detect numerous
redirection event triggers over the network from multiple user desktop
computers coupled to the server via a LAN. The server can receive internal
event triggers from each of the user desktops via the network, and can also
receive external event triggers, such as messages from the users' mobile data
communication devices. In response to receiving one of these triggers, the
server redirects the user's data items to the proper mobile data communication
device. The user data items and addressing information for a particular mobile
device can be stored at the server or at the user's PC. Using this alternative
configuration, one redirector program can serve a plurality of users. This
alternative configuration could also include an internet- or intranet-based
redirector program that could be accessible through a secure webpage or other
user interface. The redirector program could be located on an Internet Service
Provider's system and accessible only through the Internet. An example of an
Internet-based redirector program can allow various Internet-based email and
calendar event information companies to redirect their user data items to a
11
CA 02588771 2007-05-22
particular mobile device. Instant message notifications are one such type of
data items that would fall into this category.
In a preferred embodiment of the present invention, a client-based
software program operates at the mobile communication device to manage and
execute the user-selectable notification scheme ("notification module").
Preferably, the notification module is a component of the primary client
software program residing on the mobile device that manages the redirected
data items arriving and departing therefrom. In the preferred embodiment, the
notification module is called upon on or before presenting any information on
the display of the mobile device that is the result of a (1) data item
arriving
onto the mobile device from the wireless network, (2) data item event
reminder, or (3) data item transmission status report. Collectively, these
examples and others like them are herein referred to as "notifiable data
items".
In another alternative configuration of the prlesent invention, a
redirector program operates at both the host system and at the user's mobile
data communication device. In this configuration, the user's mobile device
operates similarly to the host system described below, and is configured in a
similar fashion to push certain user-selected data items from the mobile
device
to the user's host system (or some other computer) upon detecting an event
trigger at the mobile device. This configuration provides two-way pushing of
information from the host to the mobile device and from the mobile device to
the host.
12
CA 02588771 2007-05-22
In another aspect of the invention, there is provided a method of
pushing and pulling data items from a host system from a mobile
communication device, comprising the steps of receiving a message at the
mobile communication device; determining a characterization of the received
message; if the received message is characterized as a priority message, then:
(a) determining if the complete message was pushed from the host system to
the mobile communication device; if not, then automatically requesting a
remaining portion of the message from the host system; pushing the remaining
portion of the message from the host system to the mobile communication
device via a wireless network; notifying the user of the mobile data
communication device that a priority message has been received; and,
displaying the priority message on the mobile data communication device. The
method further comprises the step of sending a command to the host system for
the remaining portion of the message at the requesting step.
The primary advantage of the present invention is that it provides a
system and method for triggering the continuous and real-time redirection of
user-selected data items from a host system to a mobile data communication
device with user-selectable notification of the data items at the device.
Other
advantages of the present invention include: (1) flexibility in defining the
types
of user data to redirect, and in defining a preferred list of message types
that
are to be redirected or preferred senders whose messages are to be redirected;
(2) flexibility in configuring the system to respond to numerous internal,
external and networked triggering events; (3) transparent repackaging of the
13
CA 02588771 2007-05-22
user data items in a variety of ways such that the mobile data communication
device appears as though it were the host system; (4) integration with other
host system components such as E-mail, TCP/IP, keyboard, screen saver,
webpages and certain programs that can either create user data items or be
configured to provide trigger points; (5) the ability to operate locally on a
user's desktop system or at a distance via a network server; (6) flexibility
in
defining a user-selectable notification scheme to notify the user; (7)provides
for
notification in a user-selectable manner of user-selectable data items
arriving at
the mobile device; (8) provides for notification of mobile-specific event
occurrences such as, but not limited to calendar event reminders and
unsuccessful transmission of user data items originating from the mobile
device;
(9) provides for notification of user-selected data items from the host system
to
the mobile device in a user-selectable manner that allows the user of the
mobile
communication device the quick and hands-free ability to determine whether or
not to act on a notification; and, (10) provides for integrated secretarial-
like
features into the mobile communication device. These are just a few of the
many advantages of the present invention, as described in more detail below.
As will be appreciated, the invention is capable of other and different
embodiments, and its several details are capable of modifications in various
respects, all without departing from the spirit of the invention. Accordingly,
the drawings and description of the preferred embodiments set forth below are
to be regarded as illustrative in nature and not restrictive.
14
CA 02588771 2007-05-22
In one aspect there is provided a method of replicating data items from a host
system to a mobile data communication device, comprising the steps of
receiving a
plurality of data items at the host system, wherein the plurality of data
items are
transmitted to the host system from a plurality of remote systems;
characterizing the
plurality of data items at the host system by the host system automatically
determining a
data item type and a data item priority for each of the received data items;
generating an e-
mail message for each of the received data items, wherein the e-mail message
includes the
received data item and a header that includes the data item type and the data
item priority
determined by the host system in the characterizing step; configuring a
plurality of
notification schemes at the mobile data communication device, wherein each of
the
plurality of notification schemes includes a plurality of notification fields
that determine
whether a particular notification scheme should be applied to a particular
data item and an
alert type, and wherein the plurality of notification fields includes a party
specific field
that identifies a person associated with the data item, a data item type field
that identifies a
type of the data item, and a data item priority field that identifies a
priority ranking of the
data item;, redirecting the e-mail messages from the host system to the mobile
communication device; recovering the data items, the data item types and the
data item
priorities from the redirected e-mail messages at the mobile data
communication device;
and applying the plurality of notification schemes to the redirected data
items at the
mobile data communication device by determining whether each data item and its
characterized data item type and data item priority matches the party specific
field, the
data item type field and the data item priority field, respectively, of a
particular
notification scheme of the plurality of notification schemes, and if so, then
enabling the
alert type at the mobile data communication device for the particular
notification scheme
that matches the data item.
In another aspect, there is provided a method of redirecting e-mail messages
and
meeting notices from a host system to a mobile data communication device via a
wireless
network, comprising the steps of receiving e-mail messages and meeting notices
from a
plurality of remote systems at the host system; generating a plurality of
electronic
envelopes at the host system, wherein the electronic envelopes include the
received e-mail
messages or the meeting notices; the host system automatically generating
characterization
information regarding the electronic envelopes, the characterization
information including
a data item type that indicates whether the electronic envelope contains an e-
mail message
CA 02588771 2009-01-21
or a meeting notice and a data item priority ranking that indicates a priority
of the e-mail
message or meeting notice; the host system appending the characterization
information to
the electronic envelopes and redirecting the electronic envelopes from the
host system to
the mobile data communication device via the wireless network; receiving the
electronic
envelopes at the mobile data communication device; extracting the
characterization
information from the electronic envelopes; comparing the characterization
information to
a plurality of stored notification schemes at the mobile data communication
device to
determine whether to enable a particular alert type associated with the
notification scheme,
wherein the notification scheme includes a user defined field for the data
item type and the
data item priority.
In another aspect of the invention, there is provided a method of replicating
data
items from a computer system to a mobile data communication device,
comprising:
automatically detecting arrival of the data items at the computer system;
characterizing the
data items based on a characterization process operable in association with
the computer
system; and redirecting the characterized data items from the computer system
to the
mobile data communication device, wherein the characterization process is
adapted to
correspond with a user-selectable notification scheme operable at the mobile
data
communication device.
In another aspect, there is provided a system for replicating data items from
a
computer system to a mobile data communication device, comprising: means for
automatically detecting arrival of the data items at the computer system;
means for
characterizing the data items based on a characterization process operable in
association
with the computer system; and means for redirecting the characterized data
items from the
computer system to the mobile data communication device, wherein the
characterization
process is adapted to correspond with a user-selectable notification scheme
operable at the
mobile data communication device.
In another aspect, there is provided a message notification method operating
at a
mobile data communication device, comprising: receiving data items redirected
from a
computer system; determining if the data items include characterization
information based
on a characterization process operable in association with the computer
system; and if so,
extracting the characterization information and comparing the characterization
information
15a
CA 02588771 2009-01-21
to a plurality of stored notification schemes at the mobile data communication
device to
provide an appropriate alert associated with a select notification scheme.
In another aspect, there is provided a mobile data communication device,
comprising: means for receiving data items redirected from a computer system;
means for
determining if the data items include characterization information based on a
characterization process operable in association with the computer system;
means for
storing a plurality of notification schemes; and means for extracting the
characterization
information from the data items and comparing the characterization information
to the
plurality of stored notification schemes to provide an appropriate alert
associated with a
select notification scheme.
BRIEF DESCRIPTION OF THE DRAWINGS
The present invention satisfies the needs noted above as will become apparent
from the following description when read in conjunction with the accompanying
drawings
wherein:
FIG. 1 is a system diagram showing the redirection of user data items from a
user's
desktop PC (host system) to the user's mobile data communication device, where
the
redirector software is operating at the user's desktop PC.
FIG. 2 is a system diagram showing the redirection of user data items from a
network server (host system) to the user's mobile data communication device,
where the
redirector software is operating at the server.
FIG. 3 is a block diagram showing the interaction of the redirector software
with
other components of the host system in FIG. 1 (the user's desktop PC) to
enable the
pushing of information from the host system to the user's mobile data
communication
device.
FIG. 4 is a flow chart showing the steps carried out by the redirector
software
operating at the host system.
FIG. 5 is a flow chart showing the steps carried out by the mobile data
communication device to interface with the redirector software operating at
the host
system.
15b
} CA 02588771 2009-01-21
FIG. 6 is illustrative of the variety of notification options for a typical
notification
scheme available to the user.
15c
CA 02588771 2007-05-22
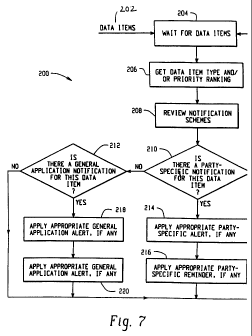
FIG. 7 is illustrative of the steps undertaken by the notification module
at the mobile device 24 of the present invention prior to presenting to the
user
a notifiable data item.
FIG. 8 is a block diagram of the major subsystems and elements
comprising a palm-sized, mobile, two-way messaging device 24 that preferably
incorporates the invention.
FIG. 9 is an alternative embodiment of FIG. 8.
DETAILED DESCRIPTION OF THE DRAWINGS
Referring now to the drawings, FIG. 1 is an example system diagram
showing the redirection of user data items (such as message A or C) from a
user's office PC (host system) 10 to the user's mobile data communication
device 24, where the redirector software 12 is operating at the user's PC.
Message A in FIG. I represents an internal message sent from desktop 26 to
the user's host system 10 via LAN 14. Message C in G. I represents an
external message from a sender that is not directly connected to LAN 14, such
as the user's mobile data communication device 24, some other user's mobile
device (not shown), or any user connected to the Internet 18. Message C also
represents a command message from the user's mobile data communication
device 24 to the host system 10. As described in more detail in FIG. 3, the
host system 10 preferably includes, along with the typical hardware and
software associated with a workstation or desktop computer, the redirector
program 12, a TCP/IP subsystem 42, a primary message store 40, an E-mail
subsystem 44, a screen saver subsystem 48, and a keyboard subsystem 46.
16
... CA 02588771 2007-05-22
In FIG. 1, the host system 10 is the user's desktop system, typically
located in the user's office. The host system 10 is connected to a LAN 14,
which also connects to other computers 26, 28 that may be in the user's office
or elsewhere. The LAN 14, in turn, is connected to a wide area network
("WAN") 18, preferably the Internet, which is defined by the use of the
Transmission Control Protocol/Internet Protocol ("TCP/IP") to exchange
information, but which, alternatively could be any other type of WAN. The
connection of the LAN 14 to the WAN 18 is via high bandwidth link 16,
typically a TI or T3 connection. The WAN 18 in turn is connected to a variety
of gateways 20, via connections 32. A gateway forms a connection or bridge
between the WAN 18 and some other type of network, such as an RF wireless
network, cellular network, satellite network, or other synchronous or
asynchronous land-line connection.
In the example of FIG. 1, a wireless gateway 20 s connected to the
Internet for communicating via wireless link 22 to a plurality of wireless
mobile
data communication devices 24. Also shown in FIG. I is machine 30, which
could be a FAX machine, a printer, a system for displaying images (such as
video) or a machine capable of processing and playing audio files, such as a
voice mail system. The present invention includes the ability to redirect
certain
message attachments to such an external machine 30 if the redirector program
configuration data reflects that the mobile device 24 cannot receive and
process
the attachments, or if the user has specified that certain attachments are not
to
be forwarded to mobile device 24, even if such device can process those
17
_ CA 02588771 2007-05-22
attachments. By way of example, consider an E-mail sent to a user that
includes three attachments -- a word processing document, a video clip and an
audio clip. The redirection program could be configured to send the text of
the
E-mail to the remote device, to send the word processing document to a
networked printer located near the user, to send the video clip to a store
accessible through a secure connection through the internet and to send the
audio clip to the user's voice mail system. This example is not intended to
limit
the breadth and scope of the invention, but rather to illustrate the variety
of
possibilities embodied in the redirection concept.
The preferred mobile data communication device 24 is a hand-held two-
way wireless paging computer, a wirelessly enabled palm-top computer, a
mobile telephone with data messaging capabilities, or a Tirelessly enabled
laptop computer, but could, alternatively be other types of mobile data
communication devices capable of sending and receiving messages via a
network connection 22. Although it is preferable for the system to operate in
a
two-way communications mode, certain aspects of the invention could be
beneficially used in a "one and one-half' or acknowledgment paging
environment, or even with a one-way paging system. The mobile data
communication device 24 includes software program instructions that work in
conjunction with the redirector program 12 to enable the seamless, transparent
redirection of user-selected data items. FIG. 4 describes the basic method
steps
of the redirector program 12, and FIG. 5 describes the steps of the
corresponding program operating at the mobile device 24.
18
CA 02588771 2007-05-22
In an alternative embodiment of the present invention, not explicitly
shown in the drawings, the mobile device 24 also includes a redirector
program. In this embodiment, user selected data items can be replicated from
the host to the mobile device and vice versa. The configuration and operation
of the mobile device 24 having a redirector program is similar to that
described
herein with respect to FIGs. 1-4.
A user of the present invention can configure the redirector program 12
to push certain user-selected data items to the user's mobile data
communication device 24 when the redirector 12 detects that a particular user-
defined event trigger (or trigger point) has taken place. User-selected data
items preferably include E-mail messages, calendar events, meeting
notifications, address entries, journal entries, personal alerts, 1 alarms,
warnings,
stock quotes, news bulletins, etc., but could, alternatively, include any
other
type of message that is transmitted to the host system 10, or that the host
system 10 acquires through the use of intelligent agents, such as data that is
received after the host system 10 initiates a search of a database or a
website or
a bulletin board. In some instances, only a portion of the data item is
transmitted to the mobile device 24 in order to minimize the amount of data
transmitted via the wireless network 22. In these instances, the mobile device
24 can optionally send a command message to the host system to receive more
or all of the data item if the user desires to receive it.
Among the user-defined event triggers that can be detected by the
redirector program 12 are in the preferred embodiment external events,
internal
19
CA 02588771 2007-05-22
events and networked events. External events preferably include: (1) receiving
a command message (such as message C) from the user's mobile data
communication device to begin redirection, or to execute some other command
at the host, such as a command to enable the preferred list mode, or to add or
subtract a particular sender from the preferred list; (2) receiving a similar
message from some external computer; and (3) sensing that the user is no
longer in the vicinity of the host system; although, alternatively, an
external
event can be any other detectable occurrence that is external to the host
system. Internal events could be a calendar alarm, screen saver activation,
keyboard timeout, programmable timer, or any other user-defined event that is
internal to the host system. Networked events are user-defined messages that
are transmitted to the host system from another computer cqupled to the host
system via a network to initiate redirection. These are just some of the
events
that could be used with the present invention to initiate replication of the
user-
selected data items from the host system 10 to the mobile device 24.
FIG. 1 shows an E-mail message A being communicated over LAN 14
from computer 26 to the user's desktop system 10 (also shown in FIG. I is an
external message C, which could be an E-mail message from an Internet user,
or could be a command message from the user's mobile device 24). Once the
message A (or C) reaches the primary message store of the host system 10, it
can be detected and acted upon by the redirection software 12. The redirection
software 12 can use many methods of detecting new messages. The preferred
method of detecting new messages is using Microsoft's Messaging API
CA 02588771 2007-05-22
(MAPI), in which programs, such as the redirector program 12, register for
notifications or `advise syncs' when changes to a mailbox take place. Other
methods of detecting new messages could also be used with the present
invention.
Assuming that the redirector program 12 is activated, and has been
configured by the user (either through the sensing of an internal, network or
external event) to replicate certain user data items (including messages of
type
A or C) to the mobile device 24, when the message A is received at the host
system 10, the redirector program 12 detects its presence and prepares the
message for redirection to the mobile device 24. In preparing the message for
redirection, the redirector program 12 could compress the original message A,
could compress the message header, or could encrypt the entire message A to
create a secure link to the mobile device 24.
The data items that are exchanged between the byost system and the
mobile device via the wireless network may include sensitive information or
confidential information, for example in a corporate or other local area
network
in which the host system is arranged to operate. A user of a mobile device may
also prefer that data items are not accessible outside the secure environment
of
the host system. It is therefore contemplated that all or some data items will
be
encrypted before transmission. In the case of transmissions/redirections from
the host system, the encryption preferably takes place prior to the data item
departing beyond the security of the one or more corporate firewalls
protecting
the information stored at or associated with the host system. In the case of
21
CA 02588771 2007-05-22
transmission/redirections from the mobile device, the encryption preferably
takes place prior to the data item departing the secure environment of the
device or prior to transmission from the device itself. An encryption scheme
is
therefore preferably implemented between each host and any device with which
the host communicates. In a private key encryption scheme, the device and all
hosts communicating with the device share a key using which encrypted
messages may be decrypted. Public key encryption involves encrypting a
message with a publicly available encryption key associated with the message
addressee. A resultant encrypted message may only be decrypted using a
private key held by the addressee. Public or private key encryption may be
implemented within a system according to the invention. Since data items are
repackaged at the host, device and gateway without regard to message content,
an encrypted message remains encrypted between a host and device thereby
creating an end-to-end secure communication link. Un1ikj known encryption
schemes, encrypted messages are only encrypted to recover the contents of the
messages at the communication endpoints, i.e. the host and device. In a
preferred embodiment, the gateway merely repackages encrypted messages and
need not decrypt such messages, the gateway does not have access to host or
device encryption keys and therefore is unable to decrypt any messages routed
therethrough. If the host operates in a corporate network behind a corporate
firewall (not shown) for example, data items therein that are encrypted at the
host system behind the corporate firewall, remain encrypted and thus secure
until decrypted by a recipient device, effectively extending the firewall to
the
CA 02588771 2007-05-22
device. Messages encrypted at a device similarly remain secure until decrypted
at a host system (preferably behind the corporate firewall). In order to
reduce
wireless network bandwidth requirements, data items may also be compressed
prior to encryption. A message recipient then simply decompresses a received
data item following decryption of the message.
Also programmed into the redirector 12 is the address of the user's
mobile data communication device 24, the type of device, and whether the
device 24 can accept certain types of attachments, such as word processing or
voice attachments. If the user's type of mobile device cannot accept these
types of attachments, then the redirector 12 can be programmed to route the
attachments to a fax or voice number where the user is located using an
attached fax or voice machine 30.
The redirector may also be programmed with a preferred list mode that
is configured by the user either at the host system 10, oo remotely from the
user's mobile data communication device by transmittinga command message
C. The preferred list contains a list of senders (other users) whose messages
are to be redirected or a list of message characteristics that determine
whether
a message is to be redirected. If activated, the preferred list mode causes
the
redirector program 12 to operate like a filter, only redirecting certain user
data
items based on whether the data item was sent from a sender on the preferred
list or has certain message characteristics that if present will trigger or
suppress
redirection of the message. In the example of FIG. 1, if desktop system 26 was
operated by a user on the preferred list of host system 10, and the preferred
list
23
CA 02588771 2007-05-22
option was activated, then message A would be redirected. If, however,
desktop 26 was operated by a user not on the host system's preferred list,
then
message A would not be redirected, even if the user of the host system had
configured the redirector to push messages of type A. The user of the host
system 10 can configure the preferred list directly from the desktop system,
or,
alternatively, the user can then send a command message (such as C) from the
mobile device 24 to the desktop system 10 to activate the preferred list mode,
or to add or delete certain senders or message characteristics from the
preferred list that was previously configured. It should be appreciated that a
redirection program could combine message characteristics and preferred
sender lists to result in a more finely-tuned filter. Messages marked as low
priority or that are simple return receipts or message read receipts, for
example,
could always be suppressed from redirection while messages from a particular
sender would always be redirected.
In yet another aspect of the present invention, a description of the
notification system and method is now further described. In general, each data
item that is redirected to the mobile preferably is characterized as to the
data
item type and the priority ranking associated therewith. Data item types
preferably include E-mail messages, calendar events, meeting notifications,
address entries, journal entries, personal reminders, instant email
notifications,
etc. Priority rankings preferably include at least three different levels of
importance, namely regular importance, very high importance and emergency.
It is to be understood that it is clearly within the scope of the invention to
24
CA 02588771 2007-05-22
expand or decrease the levels of priority rankings in an alternative
embodiment
of the invention. By characterizing the data item, the mobile data
communication device can act on the characterization according to a user-
selectable notification scheme. In addition to the user-selectable
notification
scheme, the mobile preferably executes a variety of secretary-like actions.
The
collective features of the present invention provide the mobile the ability to
advantageously operate very much like a virtual secretary thereby providing
many of the aforesaid advantages of the present invention.
Characterization preferably takes place at the host system. In a second
embodiment, the characterization may take place at the mobile. In a third
embodiment, a first portion of characterization may take place at the host
system and a second portion of characterization may take place at the mobile.
In this third embodiment, the user can set which of the two characterizations
can take precedence (i.e. which wins in a conflict). In the preferred
embodiment, the characterization as to the type of the data item and as to the
priority ranking are undertaken at the host system. However, the user,
preferably, may override the host-side characterization settings regarding the
priority rankings at the mobile. It is to be understood that it is preferable
that
the host system and the mobile are initially synchronized at either an initial
hard
link or via an over-the-air synchronization to match characterization
protocols
and notification schemes.
By way of example of the characterization process, after step 68 in Fig.
4, the redirector program may characterize the data item with a unique data
CA 02588771 2007-05-22
item type identifier and a unique priority ranking in the header of the data
item. The data
item type information may be taken from the results of the determinations at
steps 62, 64
and 66. Other suitable means of determining the data type are well within the
scope of the
present invention. Characterization as to the priority ranking of the data
item may be
accomplished in a number of ways. For instance, a data item software
application, such as
an email messaging client or a message server such as Microsoft ExchangerM or
Lotus
Notes DominoTM, may associate priority ranking with outbound data items such
as email
messages. This ranking is generally embedded in the header of the email
message.
However, solely relying on the sender and/or the sender's software package to
embed
priority ranking is not desirable for the following reasons: (1) some software
packages do
not have the ability to characterize the priority associated with the data
item or where is
the ability priority ranking is not associated with all outgoing data items,
(2) the sender
does not prioritize the data item as the mobile user desires, (3) the priority
rankings
created by the sender are in conflict with the user-defined rankings. In the
preferred
embodiment, the priority ranking is created and incorporated into the data
item header by
the notification element of the redirector program prior to wrapping the outer
envelope,
such as at step 70 of FIG. 4. In the preferred embodiment, the filter rules
described herein
for the redirection of data items from the host system to the mobile device
may include
priority ranking characterization of data items. In such an instance, the
priority ranking
may be incorporated into the headers of data items as they successfully
qualify for
redirection to the
26
CA 02588771 2007-05-22
mobile. Data items may be prioritized according an infinite number of user-
selected criteria including but not limited to: sender of the data item;
recipients
of the data items and, subject of the data item. It is within the scope of the
present invention to create a number of other criteria where the priority
ranking
may differ according to user-selected criteria.
In addition to characterization, the present invention utilizes what is
known herein as a "notification scheme". The notification scheme is a
plurality
of filtering and action rules that are applied to a notifiable data item using
some
or all of the characterization of the data item. In the preferred embodiment,
a
set of default rules will be available in the interim for the user until he
gets an
opportunity to personalize his notification scheme. In the preferred
embodiment, there is a plurality of notification schemes on the device, each
customizable for the user's benefit. As an example, a first notification
scheme
may apply only to meeting requests from a certain group of individuals, while
a
second notification scheme may apply only to the failure of any data items
transmitted from the mobile. A third notification scheme may apply to email
messages from a certain sender. The infinite variety of combinations will be
appreciated with the following description-
The notification scheme provides the user with a plurality of notification
alerts such as, but not limited to, audible, visual and vibrating alerts.
Continuing with the example, the user would then select whether any reminders
are necessary. If so, the user may select the same alert scheme earlier
selected
or alternatively, choose a different style of reminder. In this manner, the
level
27
CA 02588771 2007-05-22
of intrusion to the user due to the notification may be minimized and yet
still be
beneficial to the user. To illustrate this point, take for example a calendar
event
such as a meeting request that includes party Y is to be audibly alerted, but
an
email message from the same party is just visually alerted.
FIG. 6 is illustrative of the variety of notification options for a typical
notification scheme available to the user. In the preferred embodiment, the
user
at his mobile will have a notification scheme screen that will intelligently
navigate the user through the various options and combinations illustrated in
FIG. 6. The reference numerals 222 - 272 identify some of the user selectable
choices available for any one notification scheme. Not all choices are
illustrated for brevity sake. In essence, the user is prompted through a first
series of restriction criteria. Preferably, some of these restriction criteria
would
then be further restricted a second series of restriction criteria, if so
desired by
the user.
As a first step 222, in the notification scheme screen, the user is
prompted on whether the current scheme is to be party-specific 224 or to be
generally applied 226. When the party-specific option 224 is activated, the
notification scheme only applies to certain predetermined individuals or
groups
of individuals identified in notifiable data items. User may select from pre-
existing individuals in the mobile's address book or create new ones. User may
then set parameters of where the individual must be identified. For instance,
in
the preferred embodiment, the user may require that the individual be
identified
in any number of ways including at least one of. (1) senders of the data
items,
28
CA 02588771 2007-05-22
(2) attendees of calendar events, (3) individuals listed in the cc: of an
email message, or
(4) recipients of the data items. In the preferred embodiment, a variety of
combinations
are possible and user-selectable. In the alternative, the user may choose
option 226 such
that the notification scheme 220 applies generally without reference to the
party identified
in the notifiable data item.
At step 228, the user is prompted to choose from a plurality of data item
types. By
choosing at least one of the plurality of data item types 230, 232, 234, the
notification
scheme is restricted in its applications to those data item types selected. It
is preferable
that a user restriction selection may initiate the user to further restrict in
sub-selections. In
this manner, the notification scheme may be more finely tuned. For example, in
the
preferred embodiment, if the user selects email message 230 as a data item
restriction to
be applied, the user is further prompted to select from one or at least,
preferably, three sub-
choices, namely: inbound email messages 236, outbound email messages 238, or
transmission status of email messages 240.
As a pre-step before selecting the alert step 242, the user is prompted as to
the
priority ranking the data item must have before the alert is executed. Such
ranking
restriction is designated as steps 241 and 261. Although not fully illustrated
in FIG. 6, it is
to be understood that the alert selection (steps 242 - 260) is repeated for
each different
priority ranking the user selects. Therefore, the user may have a certain
alert section for
data items having regular importance, while a completely different alert
selection for data
items
29
CA 02588771 2007-05-22
having very high importance. Preferably, however, such subsets of alert
selections will be make up only one notification scheme.
At step 242, the user is prompted to choose from a plurality of alert
types, including preferably, audible 244, visual 246 and vibrate 248 signals.
As
illustrated in FIG. 6, the user is provided in the case of an audible signal
244, a
plurality of audible variants 250-256. In the case where the user has selected
audible signal, the user is given the opportunity to choose from a plurality
of
tune variants and a plurality of verbal variants. The verbal variants are very
useful in the case where the mobile includes a cooperating headset that
includes
an earpiece. By way of example, a verbal variant may be the spoken name of
the sender of the email message. The mobile would audibly present a computer
generated verbal announcement of the fact that an email message was received
from a particular sender via a speaker in the mobile or via a headset device.
In
the present invention, notification may be delivered via the mmobile device
itself
and/or an associated headset device. The headset device preferably includes an
ear and integrated mouthpiece. In a preferred embodiment, the headset device
may have all the notification signal capabilities, but the vibrating signal.
Returning back to FIG. 6, at step 262, the user is prompted to choose
from a plurality of reminder features 264-272. Choice 264 relates to the
number of times the user is reminded of the notifiable data item with the
foregoing user-selected alert. Choice 266 is the auto snooze feature. This
feature allows the user to acknowledge an alert in any number of ways such as
pulling the mobile of the holster or opening and viewing notifiable data item
CA 02588771 2007-05-22
while at the same returning the mobile to a rest mode such as returning the
mobile to the holster, but get reminded of the notifiable data item in a user-
selected predetermined time interval. It can be appreciated by those skilled
in
the art that a wide number of reminder styles are possible, and such styles
are
within the scope of the invention. The mobile device 24 will reference a user-
selectable notification scheme store (not shown) at step 206 to make a
determination of whether or not the data item requires notification. If a
determination at step 206 results in the affirmative, a series of possible
notification types and actions are possible as set forth in steps 208 - 218.
It is
to be understood that other notification types and combinations thereof are
within the scope of the present invention. The user-selectable notification
scheme store will preferably have a default notification scheme that the user
may modify. As can be inferred from the description of the present invention,
a
plurality of combinations may be applied to the notification scheme.
Advantageously, the notification rules may be fine-tuned and very
comprehensive so as to allow a user an extremely wide ambit of freedom and
control of reviewing notifiable data items. In effect, notification is
optimized
for the user; thereby creating for the user a virtual secretary at the mobile
device.
Virtual Secretary.
The virtual secretary may be invoked in a number of ways. For
example, a message arrives having an emergency ranking, the mobile notifies
the user accordingly, the users reviews the message, upon cursoring to the end
31
--CA 02588771 2007-05-22
of the message, software on the mobile either (1) prompts the user to reply to
the sender, or (2) opens a new message to reply to the sender. In this manner,
time which may be of the essence is advantageously saved and navigation
through GUIs are avoided for a response.
To further illustrate another feature of the virtual secretary described in
the present invention, take for example, an attachment to an email message
arrives at the handheld that is not openable or viewable at the mobile. In one
embodiment of the present invention, the mobile device will upon or while
contemporaneously acting on the user-selected notification scheme will locate
a
suitable peripheral or other device that will allow the attachment to be
presented to the user. More specifically, the software on the mobile will,
upon
detection of an attachment not presentable to the user, automatically
wirelessly
transmit an attachment agent from the handheld through a cooperating wireless
LAN or WAN. The attachment agent will seek and to sate a peripheral or
device that is willing and capable to open and present the attachment for the
user. The agent will use a variety of user-selectable parameters to determine
the most suitable external device to present the attachment. Such parameters
include what will constitute a reasonable distance for the user to walk (i.e
anywhere on the same floor of an 'office building, but no further than 250
metres). Upon successfully seek and locate, the agent will return to the
device,
or alternatively, some form of acknowledgment will be reported to the mobile
about the opportunity and details regarding logistics to present the
attachment
32
CA 02588771 2007-05-22
to the user. At that time the user can choose to either view the attachment at
the suggested external device or ignore the same.
Ambient Noise Detection.
In another embodiment of the present invention, the mobile modifies the
audible alert of notifiable data-items according to the noise level around the
user. Fig. 8 is a block diagram of the major subsystems and elements
comprising a palm-sized, mobile, two-way messaging device 24 that preferably
incorporates the invention. In this embodiment, the device prior to notifying
the user of a notifiable data item carries through with the following
additional
steps: (1) detecting the ambient noise, (2) measuring the ambient noise, (3)
determining whether to adjust the volume level associated with notification,
(4)
if adjustment is required, adjusting the volume of audible signal accordingly.
Naturally, the ambient noise detection routine is only executed where there is
an audible signal associated with the notification. Preferably, the messaging
device 24 includes a transmitter/receiver subsystem 300 connected to a digital
signal processor (DSP) 302 for digital signal processing of the incoming and
outgoing data transmissions, power supply and management subsystem 304,
which supplies and manages power to the overall messaging device
components, microprocessor 306, which is preferably an X86 architecture
processor, that controls the operation of the messaging device, display 308,
which is preferably a full graphic LCD, FLASH memory 310, RAM 312, serial
input and output 314, keyboard 316, thumbwheel 318 and thumbwheel control
logic (not shown). In its intended use, a message comes via a wireless data
33
CA 02588771 2007-05-22
network into subsystem 306, where it is demodulated via DSP 302 and
decoded and presented to microprocessor 306 for display on display 308. To
acknowledge a notification provided pursuant to the present invention, access
the display of the message, the user may choose from functions listed under a
menu presented as a result of user interaction with thumbwheel 318. If the
message is an email message, the user may chose to respond to the email by
selecting "Reply" from a menu presented on the display through interaction via
thumbwheel 318 or via menu selection from keyboard 316. When the
microprocessor 306 receives an indication that the message is to be sent, it
processes the message for transport and, by directing and communicating with
transmitter/receiver subsystem 300, enables the reply message to be sent via
the
wireless communications data network to the intended recipient. Similar
interaction through I/O devices keyboard 316 and thumbwheel 318 can be used
to initiate full-text messages or to forward messages to another party. The
device 24 is preferably BluetoothTM enabled.
After the redirector has determined that a particular message should be
redirected, and it has prepared the message for redirection, the software 12
then sends the message A to a secondary memory store located in the mobile
device 24, using whatever means are necessary. In the preferred embodiment
this method is to send the message A back over the LAN 14, WAN 18, and
through the wireless gateway 20 to the mobile data communication device 24.
In doing so, the redirector preferably repackages message A as an E-mail with
an outer envelope B that contains the addressing information of the mobile
34
CA 02588771 2007-05-22
device 24, although alternative repackaging techniques and protocols could be
used, such as a TCP/IP repackaging and delivery method (most commonly used
in the alternative server configuration shown in FIG.2). The wireless gateway
20 requires this outer envelope information B in order to know where to send
the redirected message A. Once the message (A in B) is received by the mobile
device 24, the outer envelope B is removed and the original message A is
placed in the secondary memory store within the mobile device 24. By
repackaging and removing the outer envelope. in this manner, the present
invention causes the mobile computer 24 to appear to be at the same physical
location as the host system 10, thus creating a transparent system.
In the case where message C is representative of an external message
from a computer on the Internet 18 to the host system 10, and the host 10 has
been configured to redirect messages of type C, then in a'similar manner to
message A, message C would be repackaged with an outer envelope B and
transmitted to the user's mobile device 24. In the case` where message C is
representative of a command message from the user's mobile device 24 to the
host system 10, the command message C is not redirected, but is acted upon by
the host system 10.
If the redirected user data item is an E-mail message, as described
above, the user at the mobile device 24 sees the original subject, sender's
address, destination address, carbon copy and blind carbon copy. When the
user replies to this message, or when the user authors a new message, the
software operating at the mobile device 24 adds a similar outer envelope to
the
CA 02588771 2007-05-22
reply message (or the new message) to cause the message to be routed first to
the user's host system 10, which then removes the outer envelope and redirects
the message to the final destination, such as back to computer 26. In the
preferred embodiment, this results in the outgoing redirected message from the
user's host system 10 being sent using the E-mail address of the host mailbox,
rather than the address of the mobile device, so that it appears to the
recipient
of the message that the message originated from the user's desktop system 10
rather than the mobile data communication device. Any replies to the
redirected message will then be sent to the desktop system 10, which if it is
still
in redirector mode, will repackage the reply and resend it to the user's
mobile
data device, as described above.
FIG. 2 is an alternative system diagram showing the redirection of user
data items from a network server 11 to the user's mobile data communication
device 24, where the redirector software 12 is operating at the server 11.
This
is configuration is particularly advantageous for use with message servers
such as
Microsoft's @ Exchange Server, which is normally operated so that all user
messages are kept in one central location or mailbox store on the server
instead
of in a store within each user's desktop PC. This configuration has the
additional advantage of allowing a single system administrator to configure
and
keep track of all users having messages redirected. If the system includes
encryption keys, these too can be kept at one place for management and update
purposes.
36
CA 02588771 2007-05-22
In this alternative configuration, server 11 preferably maintains a user
profile for each user's desktop system 10, 26, 28, including information such
as
whether a particular user can have data items redirected, which. types of
message and information to redirect, what events will trigger redirection, the
address of the users' mobile data communication device 24, the type of mobile
device, and the user's preferred list, if any. The event triggers are
preferably
detected at the user's desktop system 10, 26, 28 and can be any of the
external,
internal or network events listed above. The desktop systems 10, 26, 28
preferably detect these events and then transmit a message to the server
computer 1 I via LAN 14 to initiate redirection. Although the user data items
are preferably stored at the server computer 11 in this embodiment, they
could,
alternatively, be stored at each user's desktop system 10, 26, 28, which would
then transmit them to the server computer 11 after an event has triggered
redirection.
As shown in FIG. 2, desktop system 26 generates a message A that is
transmitted to and stored at the host system 11, which is the network server
operating the redirector program 12. The message A is for desktop system 10,
but in this embodiment, user messages are stored at the network server 11.
When an event occurs at desktop system 10, an event trigger is generated and
transmitted to the network server 11, which then determines who the trigger is
from, whether that desktop has redirection capabilities, and if so, the server
(operating the redirector program) uses the stored configuration information
to
37
CA 02588771 2007-05-22
redirect message A to the mobile computer 24 associated with the user of
desktop system 10.
As described above with reference to FIG. 1, message C could be either
a command message from a user's mobile data communication device 24, or it
could be a message from an external computer, such as a computer connected
to the Internet 18. If the message C is from an Internet computer to the
user's
desktop system 10, and the user has redirection capabilities, then the server
11
detects the message C, repackages it using electronic envelope B, and
redirects
the repackaged message (C in B) to the user's mobile device 24. If the
message C is a command message from the user's mobile device 24, then the
server 11 simply acts upon the command message.
Turning now to FIG. 3, a block diagram showing the interaction of the
redirector software 12 with additional components of the host system 10 of
FIG. I (the desktop PC) to enable more fully the pushing of information from
the host system 10 to the user's mobile data communication device 24 is set
forth. These additional components are illustrative of the type of event-
generating systems that can be configured and used with the redirector
software 12, and of the type of repackaging systems that can be used to
interface with the mobile communication device 24 to make it appear
transparent to the user.
The desktop system 10 is connected to LAN 14, and can send and
receive data, messages, signals, event triggers, etc., to and from other
systems
connected to the LAN 14 and to external networks 18, 22, such as the Internet
38
-- CA 02588771 2007-05-22
or a wireless data network, which are also coupled to the LAN 14. In addition
to the standard hardware, operating system, and application programs
associated with a typical microcomputer or workstation, the desktop system 10
includes the redirector program 12, a TCP/IP sub-system 42, an E-mail sub-
system 44, a primary data storage device 40, a screen saver sub-system 48, and
a keyboard sub-system 46. The TCP/IP and E-mail subsystems 42, 44 are
examples of repackaging systems that can be used to achieve the transparency
of the present invention, and the screen saver and keyboard sub-systems 46, 48
are examples of event generating systems that can be configured to generate
event messages or signals that trigger redirection of the user selected data
items.
The method steps carried out by the redirector program 12 are
described in more detail in FIG. 4. The basic functions of this program are:
(1)
configure and setup the user-defined event trigger points that will start
redirection; (2) configure the types of user data items for redirection and
optionally configure a preferred list of senders whose messages are to be
redirected; (3) configure the type and capabilities of the user's mobile data
communication device; (4) receive messages and signals from the repackaging
systems and the event generating systems; and (5) command and control the
redirection of the user-selected data items to the mobile data communication
device via the repackaging systems. Other functions not specifically
enumerated could also be integrated into this program.
39
CA 02588771 2007-05-22
The E-Mail sub-system 44 is the preferred link to repackaging the user-
selected data items for transmission to the mobile data communication device
24, and preferably uses industry standard mail protocols, such as SMTP, POP,
IMAP, MIME and RFC-822, to name but a few. The E-Mail sub-system 44
can receive messages A from external computers on the LAN 14, or can
receive messages C from some external network such as the Internet 18 or a
wireless data communication network 22, and stores these messages in the
primary data store 40. Assuming that the redirector 12 has been triggered to
redirect messages of this type, the redirector detects the presence of any new
messages and instructs the E-Mail system 44 to repackage the message by
placing an outer wrapper B about the original message A (or C), and by
providing the addressing information of the mobile data communication device
24 on the outer wrapper B. As noted above, this outer wrapper B is removed
by the mobile device 24, and the original message A (or C) is then recovered,
thus making the mobile device 24 appear to be the desktop system 10.
In addition, the E-Mail sub-system 44 receives messages back from the
mobile device 24 having an outer wrapper with the addressing information of
the desktop system 10, and strips this information away so that the message
can be routed to the proper sender of the original message A (or Q. The E-
Mail sub-system also receives command messages C from the mobile device 24
that are directed to the desktop system 10 to trigger redirection or to carry
out
some other function. The functionality of the E-Mail sub-system 44 is
controlled by the redirector program 12.
CA 02588771 2007-05-22
The TCP/IP sub-system 42 is an alternative repackaging system. It
includes all of the functionality of the E-Mail sub-system 44, but instead of
repackaging the user-selected data items as standard E-mail messages, this
system repackages the data items using special-purpose TCP/IP packaging
techniques. This type of special-purpose sub-system is useful in situations
where security and improved speed are important to the user. The provision of
a special-purpose wrapper that can only be removed by special software on the
mobile device 24 provides the added security, and the bypassing of E-mail
store
and forward systems can improve speed and real-time delivery.
As described previously, the present invention can be triggered to begin
redirection upon detecting numerous external, internal and networked events,
or trigger points. Examples of external events include: receiving a command
message from the user's mobile data communication device 24 to begin
redirection; receiving a similar message from some external computer; sensing
that the user is no longer in the vicinity of the host system; or any other
event
that is external to the host system. Internal events could be a calendar
alarm,
screen saver activation, keyboard timeout, programmable timer, or any other
user-defined event that is internal to the host system. Networked events are
user-defined messages that are transmitted to the host system from another
computer that is connected to the host system via a network to initiate
redirection.
The screen saver and keyboard sub-systems 46, 48 are examples of
systems that are capable of generating internal events. Functionally, the
41
CA 02588771 2007-05-22
redirector program 12 provides the user with the ability to configure the
screen
saver and keyboard systems so that under certain conditions an event trigger
will be generated that can be detected by the redirector 12 to start the
redirection process. For example, the screen saver system can be configured so
that when the screen saver is activated, after, for example, 10 minutes of
inactivity on the desktop system, an event trigger is transmitted to the
redirector 12, which starts redirecting the previously selected user data
items.
In a similar manner the keyboard sub-system can be configured to generate
event triggers when no key has been depressed for a particular period of time,
thus indicating that redirection should commence. These are just two examples
of the numerous application programs and hardware systems internal to the
host system 10 that can be used to generate internal event triggers.
FIGs. 4 and 5, set forth, respectively, flow charts showing the steps
carried out by the redirector software 12 operating at the host system 10, and
the steps carried out by the mobile data communication "device 24 in order to
interface with the host system. Turning first to FIG. 4, at step 50, the
redirector program 12 is started and initially configured. The initial
configuration of the redirector 12 includes: (1) defining the event triggers
that
the user has determined will trigger redirection; (2) selecting the user data
items for redirection; (3) selecting the repackaging sub-system, either
standard
E-Mail, or special-purpose technique; (4) selecting the type of data
communication device, indicating whether and what type of attachments the
device is capable of receiving and processing, and inputting the address of
the
42
CA 02588771 2007-05-22
mobile device; and (5) configuring the preferred list of user selected senders
whose messages are to be redirected.
FIG. 4 sets forth the basic steps of the redirector program 12 assuming
it is operating at a desktop system 10, such as shown in FIG. 1. If the
redirector 12 is operating at a network server 11, as shown in FIG. 2, then
additional configuration steps may be necessary to enable redirection for a
particular desktop system 10, 26, 28 connected to the server, including: (1)
setting up a profile for the desktop system indicating its address, events
that
will trigger redirection, and the data items that are to be redirected upon
detecting an event; (2) maintaining a storage area at the server for the data
items; and (3) storing the type of data communication device to which the
desktop system's data items are to be redirected, whether and what type of
attachments the device is capable of receiving and processing, and the address
of the mobile device. The configuration process may alsoinclude the priority
ranking of certain data items that are to be redirected. For instance, email
messages from individual K may be marked as very important priority ranking
while email messages all other individuals are regular importance priority
ranking. Likewise, calendar events having individual K as an attendee are
marked as very important priority ranking while all other calendar events are
normal priority. In this manner the redirector program may mark the data
items as data items are redirected in the user-selected prioritization for
appropriate notification at the user's mobile communication device.
43
,. CA 02588771 2007-05-22
Once the redirector program is configured 50, the trigger points (or
event triggers) are enabled at step 52. The program 12 then waits 56 for
messages and signals 54 to begin the redirection process. A message could be
an E-Mail message or some other user data item than may have been selected
for redirection, and a signal could be a trigger signal, or could be some
other
type of signal that has not been configured as an event trigger. When a
message
or signal is detected, the program determines 58 whether it is one of the
trigger
events that has been configured by the user to signal redirection. If so, then
at
step 60 a trigger flag is set, indicating that subsequently received user data
items (in the form of messages) that have been selected for redirection should
be pushed to the user's mobile data communication device 24.
If the message or signal 54 is not a trigger event, the program then
determines at steps 62, 68 and 66 whether the message is, respectively, a
system alarm 62, an E-Mail message 64, or some other type of information that
has been selected for redirection. If the message or signal is none of these
three items, then control returns to step 56, where the redirector waits for
additional messages 54 to act upon. If, however the message is one of these
three types of information, then the program 12 determines, at step 68,
whether
the trigger flag has been set, indicating that the user wants these items
redirected to the mobile device. If the trigger flag is set, then at step 70,
the
redirector 12 causes the repackaging system (E-Mail or TCP/IP) to add the
outer envelope to the user data item, and at step 72 the repackaged data item
is
then redirected to the user's mobile data communication device 24 via LAN 14,
44
r CA 02588771 2007-05-22
WAN 18, wireless gateway 20 and wireless network 22. At step 72, the
repackaging may also include the marking of the data item as to its data item
type and/or priority level. Control then returns to step 56 where the program
waits for additional messages and signals to act upon. Although not shown
explicitly in FIG. 4, after step 68, the program could, if operating in the
preferred list mode, determine whether the sender of a particular data item is
on
the preferred list, and if not, then the program would skip over steps 70 and
72
and proceed directly back to step 56. If the sender was on the preferred list,
then control would similarly pass to steps 70 and 72 for repackaging and
transmission of the message from the preferred list sender.
FIG. 5 sets forth the method steps carried out by the user's mobile data
communication device 24 in order to interface to the redirector program 12 of
the present invention. At step 80 the mobile software is started and the
mobile
device 24 is configured to operate with the system of th? present invention,
including, for example, storing the address of the user's desktop system 10.
At step 82, the mobile device waits for messages and signals 84 to be
generated or received. Assuming that the redirector software 12 operating at
the user's desktop system 10 is configured to redirect upon receiving a
message from the user's mobile device 24, at step 86, the user can decide to
generate a command message that will start redirection. If the user does so,
then at step 88 the redirection message is composed and sent to the desktop
system 10 via the wireless network 22, through the wireless gateway 20, via
the Internet 18 to the LAN 14, and is finally routed to the desktop machine
10.
CA 02588771 2007-05-22
In this situation where the mobile device 24 is sending a message directly to
the
desktop system 10, no outer wrapper is added to the message (such as message
C in FIGs. I and 2). In addition to the redirection signal, the mobile device
24 could transmit any number of other commands to control the operation of
the host system, and in particular the redirector program 12. For example, the
mobile 24 could transmit a command to put the host system into the preferred
list mode, and then could transmit additional commands to add or subtract
certain senders from the preferred list. In this manner, the mobile device 24
can dynamically limit the amount of information being redirected to it by
minimizing the number of senders on the preferred list. Other example
commands include: (1) a message to change the configuration of the host
system to enable the mobile device 24 to receive and process certain
attachments; (2) a message to instruct the host system to redirect an entire
data
item to the mobile device in the situation where only a portion of a
particular
1
data item has been redirected; (3) a message to instruct the host system to
modify the priority level associated with classes or subclasses of data items.
Turning back to FIG. 5, if the user signal or message is not a direct
message to the desktop system 10 to begin redirection (or some other
command), then control is passed to step 90, which determines if a message has
been received. If a message is received by the mobile, and it is a message
from
the user's desktop 10, as determined at step 92, then at step 94 a desktop
redirection flag is set "on" for this message, and control passes to step 96
where the outer envelope is removed. Following step 96, or in the situation
46
CA 02588771 2007-05-22
where the message is not from the user's desktop, as determined at step 92,
control passes. to step 98, which displays the message for the user on the
mobile device's display. The mobile unit 24 then returns to step 82 and waits
for additional messages or signals.
In an alternative embodiment of the invention relating to the notification
method and system of the present invention, following step 96 or step 92,
control passes to step 200, which notifies the user of the data item according
the present invention. FIG. 7 is illustrative of the steps undertaken by the
notification module at the mobile device 24 of the present invention prior to
presenting to the user at step 98. As will be understood upon the review of
FIG. 7, the notification module will allow notification to the user of not
only
the arrival of data items from the host system, but also is useful in
circumstances where the user would like distinct notification of (1) an
unsuccessful transmission of a data item from the mobile device 24 to the host
system x; (2) the arrival at the mobile device 24 of regular importance data
items; (3) the arrival at the mobile device 24 of high importance data items
(4)
reminders of calendar events such as appointments having regular importance;
(5) reminders of calendar events such as appointments having high importance;
(6) the arrival at the mobile device 24 of calendar events; and (7) the
arrival at
the mobile device 24 of emergency notifications. At step 202, the mobile
device 24 examines the data item and subsequently determines the data item
type and the priority ranking at step 204, if any, associated with the data
item.
In the preferred embodiment of the notification module, a counter number
47
CA 02588771 2007-05-22
embedded in the header of the data item may associate the data item type and
priority associated therewith. Alternative marking methods may used in
replace of or in conjunction with the counter number to indicate the data type
and priority, and such alternative methods are well within the scope of the
present invention. The mobile device 24 will get the data item type and any
priority ranking associated with the data item at step 206. Next, the
notification module will make reference to a user-selectable notification
scheme
store (not shown) at step 208. Upon reviewing the notification schemes in the
store, the module will be able to make a determination of whether or not the
data item requires notification via steps 210 and 212. More specifically, at
step
210, the module determines whether there is a party-specific notification
scheme for the data item. If a determination at step 210 results in the
affirmative, the appropriate party-specific alert is called and acted upon at
step
214. At step 216, the notification module will apply any reminder as set forth
in the party-specific notification scheme. Control passes then back to step
204.
An emergency notification setting is defaulted as true. When the
setting remains in this state, the emergency notification is useful in the
instance
where the user chooses to power down his entire mobile device 24 or just the
radio component of the device. In such an instance, the assumption is that the
user still desires to receive only extremely important data items, hence the
name
"emergency notification". In such an occurrence, a data item having a
command associated therewith re-activates the mobile device only long enough
to be received by the mobile device and powers down the radio component of
48
CA 02588771 2007-05-22
the mobile device promptly thereafter so as to prevent any other transmission
from arriving or departing from the device.
The present invention provides flexibility to the user by providing the
user the capability to predetermine a set of notification rules. For instance,
depending on the type of data item received by the notification module, the
user may choose the notification module to act differently. In the preferred
embodiment, notification types include visual, vibrate and audible
notifications
and within theses types of notifications there are sub-types of notifications
such
as tune 1, tune 2 and tune 3 for the audible signal notification. The user has
control over this selection via a user interface (not shown) on the device.
Alternatively, the user has control at the host system via a UI interface with
the
message server, or further alternatively, control is available at the host and
on
the device.
If the mobile device 24 determines that a message has not been received
at step 90, then control passes to step 100, where the mobile determines
whether there is a message to send. If not, then the mobile unit returns to
step
82 and waits for additional messages or signals. If there is at least one
message
to send, then at step 102 the mobile determines whether it is a reply message
to
a message that was received by the mobile unit. If the message to send is a
reply message, then at step 108, the mobile determines whether the desktop
redirection flag is on for this message. If the redirection flag is not on,
then at
step 106 the reply message is simply transmitted from the mobile device to the
destination address via the wireless network 22. If, however, the redirection
49
CA 02588771 2007-05-22
flag is on, then at step 110 the reply message is marked as to its data item
type
and priority level and repackaged with the outer envelope having the
addressing information of the user's desktop system 10, and the repackaged
message is then transmitted to the desktop system 10 at step 106. As described
above, the redirector program 12 executing at the desktop system then strips
the outer envelope and routes the reply message to the appropriate destination
address using the address of the desktop system as the "from" field, so that
to
the recipient of the redirected message, it appears as though it originated
from
the user's desktop system rather than the mobile data communication device.
If, at step 102, the mobile determines that the message is not a reply
message, but an original message, then control passes to step 104, where the
mobile determines if the user is using the redirector software 12 at the
desktop
system 10, by checking the mobile unit's configuration. If the user is not
using
the redirector software 12, then the message is simply transmitted to the
destination address at step 106. If, however, the mobile determines that the
user is using the redirector software 12 at the desktop system 10, then
control
passes to step 110, where the message is marked for data item type and
priority
level and the outer envelope is added to the message. The repackaged original
message is then transmitted to the desktop system 10 at step 106, which, as
described previously, strips the outer envelope and routes the message to the
correct destination. Following transmission of the message at step 106,
control
of the mobile returns to step 82 and waits for additional messages or signals.
CA 02588771 2007-05-22
FIG. 9 is a block diagram of yet another mobile communication device
24 in which the instant invention may be implemented. The mobile
communication device 24 is preferably a two-way communication device
having at least voice and data communication capabilities. The device
preferably has the capability to communicate with other computer systems on
the Internet. Depending on the functionality provided by the device, the
device
may be referred to as a data messaging device, a two-way pager,, a cellular
telephone with data messaging capabilities, a wireless Internet appliance or a
data communication device (with or without telephony capabilities).
Where the device 24 is enabled for two-way communications, the
device will incorporate a communication subsystem 911, including a receiver
912, a transmitter 914, and associated components such tas one or more,
preferably embedded or internal, antenna elements 916 and 918, local
oscillators (LOs) 913, and a processing module such 4as a digital signal
processor (DSP) 920. As will be apparent to those skilled in the field of
communications, the particular design of the communication subsystem 911
will be dependent upon the communication network in which the device is
intended to operate. For example, a device 24 destined for a North American
market may include a communication subsystem 911 designed to operate
within the MobitexTm mobile communication system or DataTACIM mobile
communication system, whereas a device 24 intended for use in Europe may
incorporate a General Packet Radio Service (GPRS) communication subsystem
911.
51
CA 02588771 2007-05-22
Network access requirements will also vary depending upon the type of network
919. For example, in the MobitexTM and DataTACTM networks, mobile devices such
as 24
are registered on the network using a unique personal identification number or
PIN
associated with each device. In GPRS networks however, network access is
associated
with a subscriber or user of a device 24. A GPRS device therefore requires a
subscriber
identity module (not shown), commonly referred to as a SIM card, in order to
operate on a
GPRS network. Without a SIM card, a GPRS device will not be fully functional.
Local or
non-network communication functions (if any) may be operable, but the device
24 will be
unable to carry out any functions involving communications over network 919.
When
required network registration or activation procedures have been completed, a
device 24
may send and receive communication signals over the network 919. Signals
received by
the antenna 916 through a communication network 919 are input to the receiver
912,
which may perform such common receiver functions as signal amplification,
frequency
down conversion, filtering, channel selection and the like, and in the example
system
shown in FIG. 9, analog to digital conversion. Analog to digital conversion of
a received
signal allows more complex communication functions such as demodulation and
decoding
to be performed in the DSP 920. In a similar manner, signals to be transmitted
are
processed, including modulation and encoding for example, by the DSP 920 and
input to
the transmitter 914 for digital to analog conversion, frequency up conversion,
filtering,
amplification and transmission over the communication network 919 via the
antenna 918
52
CA 02588771 2007-05-22
The DSP 920 not only processes communication signals, but also
provides for receiver and transmitter control. For example, the gains applied
to
communication signals in the receiver 912 and transmitter 914 may be
adaptively controlled through automatic gain control algorithms implemented
in the DSP 920.
The device 24 preferably includes a microprocessor 938 which controls
the overall operation of the device. Communication functions, including at
least
data and voice communications, are performed through the communication
subsystem 911. The microprocessor 938 also interacts with further device
subsystems such as the display 922, flash memory 924, random access memory
(RAM) 926, auxiliary input/output (I/O) subsystems 928, serial port 930,
keyboard 932, speaker 934, microphone 936, a short-range communications
subsystem 940 and any other device subsystems generally designated as 942.
Some of the subsystems shown in FIG. 9 perform communication-
related functions, whereas other subsystems may provide "resident" or on-
device functions. Notably, some subsystems, such as keyboard 932 and display
922 for example, may be used for both communication-related functions, such
as entering a text message for transmission over a communication network, and
device-resident functions such as a calculator or task list.
Operating system software used by the microprocessor 938 is
preferably stored in a persistent store such as flash memory 924, which may
instead be a read only memory (ROM) or similar storage element (not shown).
Those skilled in the art will appreciate that the operating system, specific
device
53
CA 02588771 2007-05-22
applications, or parts thereof, may be temporarily loaded into a volatile
store
such as RAM 926. It is contemplated that received communication signals may
also be stored to RAM 926.
The microprocessor 938, in addition to its operating system functions,
preferably enables execution of software applications on the device. A
predetermined set of applications which control basic device operations,
including at least data and voice communication applications for example, will
normally be installed on the device 24 during manufacture. A preferred
application that may be loaded onto the device may be a personal information
manager (PIM) application having the ability to organize and manage data
items relating to the device user such as, but not limited to e-mail, calendar
events, voice mails, appointments, and task items. Naturlly, one or more
memory stores would be available on the device to facilitate storage of PIM
data items on the device. Such PIM application would preferably have the
r
ability to send and receive data items, via the wireless network. In a
preferred
embodiment, the PIM data items are seamlessly integrated, synchronized and
updated, via the wireless network, with the device user's corresponding data
items stored or associated with a host computer system. Further applications
may also be loaded onto the device 24 through the network 919, an auxiliary
1/0 subsystem 928, serial port 930, short-range communications subsystem 940
or any other suitable subsystem 942, and installed by a user in the RAM 926 or
preferably a non-volatile store (not shown) for execution by the
microprocessor
938. Such flexibility in application installation increases the functionality
of the
54
CA 02588771 2007-05-22
device and may provide enhanced on-device functions, communication-related
functions, or both. For example, secure communication applications may enable
electronic commerce functions and other such financial transactions to be
performed using the device 24.
In a data communication mode, a received signal such as a text message
or web page download will be processed by the communication subsystem 911
and input to the microprocessor 938, which will preferably further process the
received signal for output to the display 922, or alternatively to an
auxiliary I/O
device 928. A user of device 24 may also compose data items such as email
messages for example, using the keyboard 932, which is preferably a complete
alphanumeric keyboard or telephone-type keypad, in conjunction with the
display 922 and possibly an auxiliary I/O device 928. Such composed items
may then be transmitted over a communication network through the
communication subsystem 911. !
For voice communications, overall operation of the device 24 is
substantially similar, except that received signals would preferably be output
to
a speaker 934 and signals for transmission would be generated by a microphone
936. Alternative voice or audio I/O subsystems such as a voice message
recording subsystem may also be implemented on the device 24. Although
voice or audio signal output is preferably accomplished primarily through the
speaker 934, the display 922 may also be used to provide an indication of the
identity of a calling party, the duration of a voice call, or other voice call
related information for example.
CA 02588771 2007-05-22
The serial port 930 in FIG. 9 would normally be implemented in a
personal digital assistant (PDA)-type communication device for which
synchronization with a user's desktop computer (not shown) may be desirable,
but is an optional device component. Such a port 930 would enable a user to
set preferences through an external device or software application and would
extend the capabilities of the device by providing for information or software
downloads to the device 24 other than through a wireless communication
network. The alternate download path may for example be used to load an
encryption key onto the device through a direct and thus reliable and trusted
connection to thereby enable secure device communication.
A short-range communications subsystem 940 is a further optional
component which may provide for communication between the device 924 and
different systems or devices, which need not necessarily be similar devices.
For
example, the subsystem 940 may include an infrared device 1 and associated
circuits and components or a Bluetooth communication module to provide
for communication with similarly-enabled systems and devices.
Having described in detail the preferred embodiments of the present
invention, including the preferred methods of operation, it is to be
understood
that this operation could be carried out with different elements and steps.
This
preferred embodiment is presented only by way of example and is not meant to
limit the scope of the present invention which is defined by the following
claims.
56