Note: Descriptions are shown in the official language in which they were submitted.
CA 02638878 2009-06-16
WIRELESS EMAIL COMMUNICATIONS SYSTEM PROVIDING SUBSCRIBER
ACCOUNT UPDATE FEATURES AND RELATED METHODS
Field of the Invention
[0001] The present invention relates to the field of
communications systems, and, more particularly, to
wireless electronic mail (email) communications systems
and related methods.
Background of the Invention
[0002] Electronic mail (email) has become an integral
part of business and personal communications. As such,
many users have multiple email accounts for work and home
use. Moreover, with the increased availability of mobile
cellular and wireless local area network (LAN) devices
that can send and receive emails, many users wirelessly
access emails stored in source mailboxes of different
email storage servers (e.g., corporate email storage
server, Yahoos, Hotmail', AOL*, etc.) .
[0003] Yet, email distribution and synchronization
across multiple mailboxes and over wireless networks can
be quite challenging, particularly when this is done on a
large scale for numerous users. For example, different
email accounts may be configured differently and with
*Trade-mark
1
CA 02638878 2008-09-26
WO 2007/111598 PCT/US2006/011249
non-uniform access criteria. That is, different user
devices will have different capabilities such as the
ability to display images, receive file attachments, etc.
Moreover, different devices may access the email system
through different interfaces (e.g., HTML, WML, etc.).
Further, individual user accounts may have different
services or features enabled. Accordingly, it may become
difficult to maintain service account information when
certain events occur, such as a user switching to a
different mobile wireless communications device or when a
service provider updates service platforms.
[0004] Various attempts have been made in the prior
art to modify mobile telephone subscriber services. Once
such example is disclosed in U.S. Patent No. 6,449,479 to
Sanchez. This patent is directed to an apparatus for
changing a mobile subscriber's feature profile in a
telecommunications network. The apparatus includes a Home
Location Register (HLR) with a memory for storing the
feature profile, which includes one or more service
features, such as call waiting, call blocking, etc. The
apparatus also includes a node that communicates
electronically with the HLR. The node recognizes a
subscriber feature profile change request, validates the
request, determines whether the subscriber is currently
using the mobile phone to which the profile is assigned,
and prevents changes in the profile except for changes
specifically requested by the subscriber if the
subscriber is not using the mobile phone to which the
profile is assigned.
[0005] While such systems may be helpful for allowing
users to update basic phone service features, a user
typically does not have the knowledge or the access
2
CA 02638878 2009-06-16
required to make changes to information such as
device/subscriber identifications (IDs), personal
identification numbers (PINs), and device capability
settings in wireless email service accounts. As a result,
the user typically has to contact a wireless network
provider's customer service when switching devices or
when system upgrades are'made that effect the user's
ability to send and receive emails. Not only is this an
inconvenience for users, but the increased man hours
needed staff a service center to handle large call
volumes can be expensive for the network provider as
well.
[0006] Intesnaticual Published Application No. WD 2005/015935 is
directed to a mobile wireless camunicatic i device capability proxy
server. abe server includes a database of subscriber data including
custarer data, handset profiles, and application profiles. For
example, data may include the IMSI, equipment. serial
number, or equipment phone number (MSISDN). An event
handler checks for the existence of a consumer or device,
and if the device has changed, details of the change are
requested. The changes are recorded in the database, and
subscribed applications, are notified of the capability
changes.
(00071 Maes et al., "Push Ectensicns of the IMAP Protocol"
discloses Push Exte sicns to the IMP Protocol (P-IM AP) and defines
extansiens to the fl Pv4 Revl protocol for optimization in a mobile
setting. It is aimed at delivering exta d functionality for mobile
devices with limited resources. The first enhancement of
P-IMAP is extended support to push crucial changes
actively to a client, rather then requiring the client to
initiate contact to ask for state changes. In'addition,
P-IMAP contains extensions for email filter management,
3
CA 02638878 2009-06-16
message delivery, and maintaining up-to-date personal
information. Bindings to specific transport are also
defined.
[0008] U.S. Published Application No. 2006/030368 is directed
to a system for alerting a mobile network subscriber to capabilities
of a mobile station associated with a contact of the subscriber. The
system includes a database including the IMEI numbers and
phone numbers of mobile stations. When a phone call to
the mobile station is received, the system associates the
phone number with the mobile IMEI number stored in the
database, information including the contact'mobile
station capabilities stored in the IMEI database are then
forwarded to the mobile station and displayed on the
mobile station.
100091 Polystar Instninaits, " iDec-lbe RAKE DeteCtIM System for
Consistent WS Quality" is directed to as system that provides correct
handset information when transmitting uultunedia within a network. A
probe-based system, with IMEI incorporated as part of the location
update procedure, is installed and generates cannmicatiais detail
records (xI s) in real timre, based on the signalling information
in the network. The xDRs are correlated in real time and
sent for processing and stored in a database. The
records can. be sent to the Multimedia Messaging Service
Centers and/or service providers in real time to report
changes of handsets.
Brief Description of the Drawings
[009.0] FIG. i is schematic block diagram of. a wireless
communications system in accordance with the-present
invention.
4
r}; 1 PM -- - NO 260 US2006011249-
!5-01-2008.08 CA 02638878 2008-09-26
30823--WO-PCT (80275-PCT)
[0011] FIGS. 2 and 3 are flow charts of wireless
communications methods in accordance with the present
invention.
[0012] PIG. 4 is schematic block diagram of an
alternate embodiment of a wireless communications system
in accordance with the presezit invention.
[0013] FIGS. S and 6 are flow charts of alternative
embodiments of wireless communications methods in
accordance with the present invention.
.[0014] FIG. 7 is a schematic block diagram
illustrating an unreconciled user service account.
00l$] FIGS. 8-18 are flow' diagrams illustrating logic
paths for updating the user service accounts of FIG. 7.
[0016] FIG. 19 is another schematic block diagram
illustrating unreconciled user service accounts.
[0017] FIGS. 20 and 21 are tabular views of user
accounts illustrating various unreconciled information
therein.
[0018] FIG. 22 is a schematic block diagram
illustrating exemplary components of a mobile wireless
communications device for use with the present invention.
ed at the EPO on -Jan 25, 2008 22:53:56. Page 15 of 44
AMENDED SHEET
?5-01-2008 p 2 US2006011249 -
_,08 4:51 PM CA 02638878 2008-09-26
30823-WO-PCT (80275,PCT)
Detailed escription oche Preferred Ripbodim,ents
[0019] The present description is made with reference
to the accompanying drawings, in which preferred
embodiments are shown. However, many different
embodiments may be used, and thus the description should
not be construed as limited to the embodiments set forth
herein. Rather, these embodiments are provided so that
this disclosure will be thorough and complete. Like
numbers refer to like elements throughout, and prime and
multiple prune notation are used tc indicate similar
elements in alternative embodiments.
[00207 Generally speaking, a wireless communications
system is disclosed hereiz which may include a plurality
of mobile wireless communications devices each having a
subscriber account associated therewith including a
respective personal identification number (PIN) and a
unique identification (ID). The system may further
include at least one electronic mail (email) server
comprising a database of subscriber accounts and for
sending .mails to and receiving emails from the mobile
wireless communications devices based upon the PINs and
unique IDs. The at least one email server _may compare a
given PIN and unique in, based upon a communication from
a given mobile wireless device, with a correspondinc PIN
and unique ID for the corresponding subscriber account in
the database, and update the corresponding subscriber
account based upon a discrepancy,
[00213 More particularly, the discrepancy may be a
difference between the unique ID associated with the
communication from the given mobile wireless
communications device and the unique in in the
corresponding subscriber account. In addition, the at
ed at the EPO on Jan 25, 2008 22:53:56. Page 16 of 44
AMENDED SHEET
25-01-2008 Q 8 4: 5 2 PM N0, US2006011249
CA 02638878 2008-09-26
30823-WO-PCT (80275_PCT)
least one emai], server may prompt the give,, mobile
wireless communications device to provide the
communication. By way of example, the unique IL7e may he
international Mobile Subscriber Identities (IMSIS) and/or
international Mobile Station Equipment Identities
(IMEIs). Furthermore, the at least one email sexver may
interface with the given wireless communications device
via a Hypertext Markup Language (HTML) interface and/or a
.Wireless Markup Language (WML) interface, for example.
[0022] The wireless communications system may further
include at. least one wireless communications network for
establishing wireless communications links with the
mobile -wireless communications devices. Moreover, the at
least one email server may send emails to and receive
emalls from the mobile wireless communications devices
via the at least one wireless communications network:
[0023] A wireless communications method aspect may
include establishing a respective subscriber account for
each of a plurality of mobile wireless communications
devices, with each subscriber account including a
respective personal identification number (PIN) and a
unique identification (ID). Further, emalls may be sent
to and received from the mobile wireless communications
devices based upon the PINs and unique IDs. The method
may further include comparing a given PIN'and unique ID,
based upon a communication from a given mobile wireless
device,.'with a corresponding PIN and unique ID for the
corresponding subscriber account, and updating the
corresponding subscriber account based upon a
discrepancy.
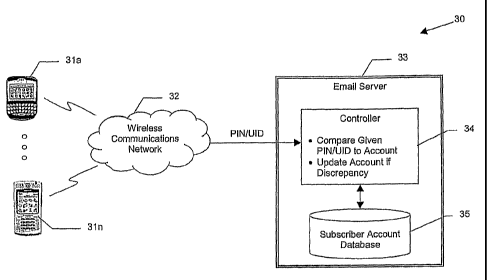
[00241 Referring initially to FIG. 1, a wireless
communications system 30 illustratively includes a
7
ived at the EPO on Jan 25, 2008 22:53:56. Page 17 of 44
AMENDED SHEET
CA 02638878 2009-06-16
plurality of mobile wireless communications devices 31a-
31a, each having a subscriber account associated
therewith. More particularly, the subscriber accounts
include a respective personal identification number (PIN)
and a unique identification (U1D). In the case of a
Global System for Mobile communication (GSM) based
system, the unique identifiers may be International
Mobile Subscriber Identities (IMSls) and/or International
Mobile Station Equipment Identities (IMEIs), for example,
as will be appreciated by those skilled in the art. Of
course,. other unique identifiers may also be included in
different systems and/or implementations. The service
accounts may also'have associated therewith user
integrations or settings (email filters,
archiving/deleting parameters, etc,), as well as the
capabilities-of the particular device associated with the
account, as will be discussed further below.
[0025] The system 30 further illustratively includes a
wireless communications network 32 for establishing
wireless communications links with the mobile wireless
communications devices. By way of example, the wireless
communications network 32 may be a cellular
communications network and/or a local/wide area network.
[00.26] One or more email servers 33 are used for
sending emails to and.receiving emails from the mobile
..wireless communications devices 31a-!1n. ,More
particularly, the email server 33 may aggregate emails
from one or more user email accounts (e.g. Gmail*,
Hotmail*, AOL*, etc.) and send the email messages to the
user, as well as distribute emails generated on the
mobile wireless communications devices 31s-31n to
*Trade-mark
8
25-01 -2008 0 8 4: 5 2 PM CA 02638878 2008-09-26 N 2 6 0 US2006011249
30823-Wo-PCT (8O275_PCT)
designated addressees via the World Wide Web, as will be
appreciated by those skilled in the art.
[00271 The email server 23 illustratively includes a
controller 34 and a subscriber account database 35. It
should be_ noted that while these components are shown as
being in a same email server, it will be appreciated that
the control and database functions may in fact be
distributed across multiple servers or computing devices
in some embodiments, particularly in large scale network
implementations.
[00281 The subscriber account database 35 is where
subscriber account information is stored. By way of
example, each account may include the PINE, IMSIs, and
IMEIs associated with the given subscriber/device; as
well as a Subscriber Identity Module (SIM) identifier
associated with the given device, the particular wireless
network ( i . e . , carrier) and services a. subscriber uses,
user settings (e.g., filters, notification preferences,
etc.), and account status information (e.g., active,
suspended, etc.).
[00291 Knowing the given device, carrier, and services
a user has allows the controller 34 to determine a device
capability set that the given device can support. For
example, some mobile wireless communications devices have
enhanced processing, display, and memory capabilities and
can therefore upload and view images, videos,
attachments, etc., while older model devices may not
support such features. Moreover, even if a given device
can support certain features, these features may not be
permitted under the subscriber's service plan with the
carrier. Thus, the controller 34 may cooperate with the
database 35 to determine and keep track of the respective
9
ived at the EPO on Jan 25, 2008 22:53:56. Page 19 of 44
AMENDED SHEET
CA 02638878 2008-09-26 --- US2006011249
25-01-2008 NO. 2 6 0*
) 08 4: 2 PM
30823-WO-PCT (80275 PCT)
device capability sets respectivrely associated with the
mobile wireless communications devices 31a-31n based upon
knowledge of the various device types and carrier systems
that the email server 33 is operating with, as will be
appreciated by those skilled in the art.
[00301 The controller 34 uses the PINS and unique IDs
(e.g., IMEIs and/or IMSIs) to associate emails with
respective mobile -wireless communications devices 3L.a-
31n. In particular, when a given device attempts to
access the email server 33, it communicates a request to
the server. Depending upon the type of interface used
between the given device and the server 33, the request
may already include the PIN and unique ID IMEI) of
the requesting device. For example, with a Wireless.
Markup Language (WML) interface, this information may be
automatically embedded in the request. With other
interfaces, such as a Hypertext Markup Language (HTML)
interface, the server 33 may be required to prompt the
given device for such information, as will be discussed
further below.
[0031) As noted above, there are circumstances when
the PIN/unique ID stored in a subscriber account do not
match the PIN/unique ID provided by a given device. For
example, if a user upgrades to a new device and switches
his SIM card from an old device to the new one, the
PIN/ID information provided by the device to the email
sever 33 will not match the information stored in the
subscriber's account (i.e., the given device ID (IMEI)
provided by the device will not match the device ID in
the account) -. As a result, the email server 33 may
otherwise fail to complete an email request from the
given device until the account information is
ived at the EPO on Jan 25, 2008 22:53:56. Page 20 of 44
AMENDED SHEET
CA 02638878 2008-09-26 11S2006011249
25-01-2008)08 4: 52 PM' _ ._NO, 260
30823-WO-PCT (80275_pcT)
reconciled/updated, which ordinarily would require the
subscriber to call customer service, and a representative
would manually update the account information.
[00323 Another circumstance in which the given PIN/ID
provided by a given device may not match the information
stored in the user account is when, the carrier or email
server 33 administrator updates the platform or software
of the server. In particular, when the email server
administrator rolls out new versions of the server
platform, customer accounts may need to be migrated to
the new platform. For a variety of reasons, it is
possible, that during the migration certain account
information (.IDs, settings, etc.) is not readily
available or cannot be moved to the new accounts on the
new platforms, In such case, the accounts may have nulls
or placeholders for certain. Ins, settings, etc., which do
not match the actual PIN/IDs provided by the given
device.
[00331 Accordingly, the controller 34 advantageously
compares a given PIN and unique ID, based upon a
communication from a given mobile wireless device 31,
with a corresponding PIN and unique ID for the
corresponding subscriber account in the database 35, and
updates the corresponding subscriber account based upon a
discrepancy. More particularly, the discrepancy may be a
difference between the unique ID (e.g., IM2I and/or IMSI)
associated with the communication from the given mobile
wireless device 31 axzd the unique ID in the corresponding
subscriber account. As noted above, the given PIN/ID may
be included in the communication (i.e., request) from the
given mobile wireless-device 31, or the server 33 may
prompt the given device for this information upon
11
eived at the EPO'on Jan 25, 2008 22:53:56. Page 21 of 44
AMENDED SHEET
25-01-2008 00- 4; 52PM" NO. 260 US2006011249 --
CA 02638878 2008-09-26
30823-WO-PCT (80275_PCT)
receiving a request (and the given device provides the
information in a follow up communications). As such, the
email server 33 may therefore automatically detect when
account discrepancies occur and update the account
accordingly with the need for subscriber and/or customer
service intervention.
[0034] Turning now additionally to FIGS. 2 and 3, a
wireless communications method aspect illustratively
begins at Block 50 with establishing a respective
subscriber account for a plurality of mobile wireless
communications devices 31a-31n, at Block 51. As discussed
further above, each subscriber accounting includes a
respective PIN, unique ID(s), etc. Further, emails are
sent to and received from the mobile wireless
communications devices 3la-31n based upon the PINs and
unique IDs, at Block 52.' The method further includes
comparing a given PIN and unique It, based upon a
communication from a given mobile wireless device, with a
corresponding PIN and unique ID for the corresponding
subscriber account, and updating the corresponding
subscriber account based upon a discrepancy, at Blocks
53-54, as discussed above, thus concluding the
illustrated method (Block 55).
[0035] As noted above, for some interfaces (e.g.,
HTML), it may be necessary for the email server 33 to
prompt the given mobile wireless. communications device 31
to provide the given PIN/unique ID via a follow up
communication to the original request (Block 561) , More
particularly, the discrepancy may be a difference between
the unique ID IMEI and/or IMSI) associated ,with
the communication from the given mobile wireless device
12
ived at the EPO, on Jan 25, 2008 22:53:56. Page 22 of 44
AMENDED SHEET
25-01-2008 'N 260 US2006011249
08 4:52PM CA 02638878 2008-09-26
30823-WO-PCT (80275 PCT)
31 and the unique ID in the correspondthg subscriber
account, at,Block 531.
[0036) Referring now additionally to FIGS. 4 through
6, the email server 331 may not only update the unique
IDa IMEI, IMSI) associated with a given account,
it may also update the device characteristic set for the
account. This could be done, for example, when it is
detected that a subscriber is using a new device which
has enhanced display, processing, memory, or
communication capabilities. Of course, if a user switches
to a device with lesser capabilities than a prior device,
the device characteristic set may also be downgraded
accordingly.
[0037] In particular, the email server 33' compares a
given, PIN and device ID (e.g., IMEI), based upon a
communication from a given mobile wireless device, with a
corresponding PIN and device ID for the corresponding
subscriber account in the database, as discussed above,
and updates a corresponding device capability set for the
corresponding subscriber account based upon a discrepancy
(Slacks 5711-5811). Again, the device capability set may
include capabilities such a$ image display capabilities,
file attachment handling capabilities, communications-
interface type/capability, etc. (Block 58,11).
[00381 A set of scenarios centered around migration to
an email system platform BI5 from a prior platform BWC
will now be described. In the following scenarios, a
subscriber/user is unable to associate, his 'device PIN
(e . g . IMEI), as recorded in an account maintained by a
provisioning system PRV (which conceptually corresponds
to the above-noted subscriber account database 33), with
the BIS account that he is being logged, into via,a
13
ved at the EPO on Jan 25, 2008 22:53:56. Page 23 of 44
AMENDED SHEET
NI n US2006011249
25-01-2008 Q8 4,,52PM - -' CA 02638878 2008-09-26 fy~
30823-WO-PCT (8027$_PCT)
carrier Ili (e . g . , an IMSI) via an RTML or WMM user
interface.
[0039] Referring to PIG. 7, when the migration occurs
an initial subscriber account A is created for the BIS
system. However, for reasons which will be described
further below, in some situations the data being
populated in the new account may be incomplete, i.e., the
PIN is not properly associated with a carrier subscriber
ID (IMSI) , etc. In these scenarios the user's PIN may
therefore be "held hostage" by the prior PRV account
(i.e., BIS account A), which has a carrier ID A. In some
scenarios the PRV account belongs to the user and may
include integrations (i.e., user--defined preferences,
available services, etc.) that the user wishes to retain.
[0040] The effects of the above-described
discrepancies will depend upon the particular scenario.
More particularly, in a scenario where the PI1 cannot be
set, the user may be unable to login. In any scenario
where a "wrong" PIN is set, the user will be unable to
control the email being sent to his device. Further, in, a
scenario where a PIN is being held hostage, the
integrations in that account will continue to send email
to the PIN, which. might be acceptable if the other
account (BIS account. P) also belongs to the user, and the
user is still interested is those integrated sources, hut-
if not, then the result will' likely require user/customer
service intervention to correct.
[0041] Various logic and user interface (UI) 'changes
may be made to the HTML and WAP proxies to help users
self-service themselves in reclaiming their PITS and/or
integrations. Some of these changes may be made in the
carrier login code. This code will detect the scenarios
jived at the EPO on Jan 25, 2008 22:53:56. Page 24 of 44
AMENDED SHEET
25-01-2008 08- 4:53PM CA 02638878 2008-09-26 - - - NO. 260- US2006011249
30823-WO-PCT (80275_PCT)
where a user's PIN cannot be set because it is already
associated with another account. In a case where PRV
gives the `wrong" PIN and this is not detectable, then
the problem may be addressed when the user uses a change
handheld feature. Part of the reclaiming logic may
require user input for the user to prove that the PIN
belongs to him. Furthermore, there may also be
integrations for which the user may need to provide
'`proof" of Ownership.
[0042] The potential changes to the login process will
now be discussed, including detection, UI flow, and
resolution. FIG. 7 illustrates a general situation. where
a PIN is detected as being held hostage. When the user
enters the HTML or WML site an YID, injected by the
carrier gateway, is passed in. The ID can be used to
lookup the account, or if the account does not exist can
be used to create a new one.. A'PIN is associated with
that account by correlating the Ili to an IMSI via the
carrier Application Program Interface (API), and then
correlating the IMSI to a PIX via PRV. if the PIN is
e
already associated with another account then a failure to
set up the PIN will, occur and the PIN hostage situation
is detected,
[0043] Referring now to FIGS. B through 18, these flow
diagrams-illustrate the seamless login and account
creation logic, and how the various scenarios are dealt
with. Table 1, below describes conventions used in the
flowcharts.
Table 1
Account The account identified by the external I]/
Mobile Station. International ISDN Number
(MSISDN) passed in the request: header.
Hostage The account that is associated with the PIN that
eived at the EPO on Jan 25, 2008 22:53:56. Page 25 of 44
AMENDED SHEET
?5-01-2008 0$ 4.53PM ..-NO2260' US200601.1249 --
CA 02638878 2008-09-26
30823-WO-PCT (80275 PCT)
Account has been determined to belong to another
account.
PIN A Pin is determined to be free if it is NOT
Free? associated with any other account other than the
desired account to be associated with.
Prompt Describes re fired user input,
[0044] FIGS. 8 and 9 illustrate typical login flows
with one branch, 3, detecting a hostage pin situation and
another branch, A, detecting either a lack of a PRV PIN
(PRV.PIN) or an invalid PVT. PIN. A typical login flow
will resolve the correct PIN for the user, make sure it
is free, create the account if it does not exist, and
prompt the user if the PIN is changed. For the WML login
case 90, the PIN is retrieved from the WML request, and
for the ITML login case 80 it is retrieved from PRV.
However, the PRV data may not always have the correct
IMSI to PIN mapping for the user, so it is therefore
desirable to prompt the user for confirmation.'
[0045] In the case where the PRV.PIN does not exist
but the account does exist- with a PIN, it may be assumed
that the current account PIN is correct and the user is
logged in. The path B is entered when the retrieved PIN
is not associated with the user's account and the user's
account already has a PIN associated therewith. in such
case, a decision is made as to whether the user desires
to change pins .
[0046] FIG. 10 illustrates the logic for when PRV has
no associated PIN for the user/IMSI. This occurs in the
HTML case. When this flow executes it is known that the
PP.v. PIN does not exist, and if the account exists it has
no PIN. if the PIN entered is being held hostage, then
the logic returns to path B, Otherwise, a new account is
created if it does not exist and the PIN is set, at 100.
ed at the EPO on Jan 25, 2008 22:53:56. Page 26 of 44
AMENDED SHEET
US200601 1 249 --
25-01-2008 Q8 53 PM CA 02638878 2008-09-26 N O.260
M
30823-WO-PCT (8027 PCT)
[0047] FIG. 11 illustrates the logic for when the PIN
is determined, and it is determined that the PITT is being
held hostage by another account, at 110. The PIN is
determined either by looking it up in PR.V, harvesting it
from WML, or from a validated user input. If the user has
an account with a PIN and,mailbox, then the PIN is taken
from the hostage account to avoid merging integrations
from both accounts. The user is only able to reclaim the
hostage account if this account has a. fake ID, a hosted
mailbox, and the user can enter the mailbox address of
the account. If these conditions are met then the ID and
MSISDN are-copied to the hostage account. If another
account has already been created for the user, then the
other account is preferably deleted first.
[0048] if a user does not claim to have a mailbox or
fails to prove ownership of it, then a new account may be
created if it does not already exist. The PIN is taken
from the hostage account, which is disabled. While
prompting for the User ID, the LTI may advantageously
allow the user to go back and respond differently to
having a mailbox already.
10049] The logic flow for TITML for the scenarios noted
above will now be described, The WKL case only varies
from the following scenarios in the way in which the PIN
is retrieved, as noted above. In the first scenario (FIG.
12), the user's account is migrated to BIS with a fake
TV. When the user logs in, PRV reports. the correct PIN
for the-user, which of course is being held hostage by
the fake account, along with his mailbox, at 120.
100503 A second scenario, illustrated in FIG, 13, is
essentially the same as scenario 1, except that the
user's account has an old PIN. The logic flow therefore
17
Dived at the EPO on Jan 25, 2008 22:53:56. Page 27 of 44
AMENDED SHEET
25-01-2008 0 $ 4: 5 3 PM CA 02638878 2008-09-26 -- nl 2 6 0 US200601 1 249 --
30823-WQ-PCT (80275_PCT)
remains the same, except that the user is asked if he
wishes to change the PIN, at 130. A third scenario is
also similar to scenario 1, with the exception that the
account holding the user's PIN does not include the
user's integrations. As such, the user would either
answer no to having a mailbox, or fail to enter the BWC
UserlD associated with the account, at 140.
t0051] Referring to FIG. 15, for the WILL case, it is
possible that the user is using a different device than
the one on record. It may be assumed that the device the
user is currently using is the one specified in the WML
request, and pre-populate the PIN/IMEI based thereon.
When a user enters the PZN/IMEI, the same hostage PIN
detection logic applied during login may be applied, at
150. Of course, it is simplified in this case since it is
known that the account exists and it has a PIN.
[00'522] The UI is now described with reference to FIGS.
16 through 18. Per HTML, when both the PRV and the user's
account have no PIN, then the user is asked for a
PIN/IMEI, If the PI1T/IMEI entered by the user is valid
but is being held hostage by a faked account with a
hosted mailbox, at 160, then the logic jumps to UI logic
flow B (at 170). That is, UI logic flow B is entered
when; (1) a PIN is proven to belong to a user; (2) the
pin is being held hostage by a faked account; and (3) the
user's current account (if it exists) has no mail
sources.
[0053] A. third U1 logic flow C is entered when the PRV
PIN is free and the user does not have an account with a
PIN, at 180. The idea here is that PRV may not
necessarily be,trustworthy, and it will be verified with
the user that this is his PIN. If-it is not his PIN, then
18
aived at the EPO on Jan 25, 2008 22:53:56. Page 28 of 44
AMENDED SHEET.
25-01-2008 Q q pp 4: 53 PM 78 20 0 8- 09 - -26 NO, 260 US2006011249 -
CA 026388
30823-WO-PCT (80275_P CT)
the user is prompted to enter a PIN, at which point the
logic flow is similar to logic flow A. The logic flow for
a new handheld would be the same as for TI logic flow A.
[00543 Some exemplary action handlers for implementing
the above-noted logic flows are now provided. The
following action handlers are written in Java script, and
the first action handler (Action Handler 1) is for a
seamless sign on scenario. It should be noted that in the
following action, handlers "context" refers to an object
that contains a user's session state information
an account data). "Proxy-state" is an object stored in the
context which pertains to a transient workflow state. For
example, this may include data that is used for a process
such as a login or a configuration wizard.
Action Handler 1
input; pin (will be ! null in wrtl scenario)
Pseudocode :
If (isBdaEnabled) {
.if (pin =~ null) {
Get i=i from [carrier] ;
prvPin = Get pin from prv;
if (pr'v'Pin == null) {
try {
Account acct = , ctntext . authenticate () ;
if (acct.pi,n -- null) {
Forward to prompt piri/imei handler;
}
Else {
?onward to mailboxes screen (user is
logged in)
}
}
Catch (authenticationexception) {
Forward to'prompt pin/imei T.andler;
}
}
Proxyystate. setPxvPin (prvPin) ;
Proxystate. setDevicePin (prVPin) ;
}
Else {
in = decrypt (pin) ;
Proxystate . setPrvPin ( .ull) ;
Proxystate. setDevicePin (pit].) ;
19
ed at the EPO on Jan 25, 2008 22:53:56. Page 29 of 44
AMENDED SHEET
25-01-2008 03 4 53PM CA 02638878 2008-09-26 NO. 260 US200601 1 249
30823-WO-PCT (842 7 PCT)
}
Forward to pincheckhandler();
}
Instead of going to PRAT to get the PIN, in some scenarios
the PIN is simply retrieved from the proxy state because
it will have been set previously by the login handler.
(0055] A second action handler (Action Handler 2)
validates the PIS'/IME t entered by the user.
Action Handler 2
Input: pin, .imei
Ps eu,d.ocode :
if (pin _- null imei null) {
Show pir,.Jimie screen;
}
Else
If (pin/imei are valid) {
Porward to PincheckEandler;
}
Else,(
Shaw pin/imei screen w/ error msg;
} }
100561 A third action handler (Action Handler'3) code
checks if the user's ?IN' has been taken hostage by
another account, or if the user's PIN needs to be
changed.
Action Handler 3
Input: none
Vseudocode:
pin r pr,xyetate.getnevicePin();
prvPin = proxystate.getPrvk?in();
If (pin is gree?) (
If (pin == prvPin) html scenario
Try {
Account acct context.authenticate();
If (aact.pin null) {
Forward to prvpinhaidler;
}
Else if (acct.pin == pin) {
Forward to mailboxes screen (user is logged,
in)
Else {
Show change pin prompt;
} }
catch (A.uthenticatio xception) {
ed at the EPO on Jan 25, 2008 22:53:56. Page 30 of 44
AMENDED SHEET
25-01-2008 4 ; 3 PM CA 02638878 2008-09-26 . NO, 26 US2006011249
08
30823-WO-PCT (80275_PCT)
Forward to p,rvpinhandler;
}
}
Else {
Try {
Account acct - context. authenticate ( )
if (acct.pin != pin) {
Acct.p,n. = pin;
Forward to mailboxes screen (user is logged
in)
}
Else {
Show change pin prompt;
}
}
Catch (AuthentiCationEXceptiOA)
Forward to CarritrAoctHan,dler;
}
}
}
Else {
Try {
Account acct = context .authenticste () ;
if (acct.pin null) {
Forward to hostage acct handler;
}
Else {
Forward to change pin handler;
}
Catch (aut1.entication.Exception) {
Forward to hostage acct handler;
}
}
10057] A. fourth action l.andler (Aotivn Handler 4) code
is used in both the HTML and WML sceriarios.
Action Handler 4
input ; Hoare
Pseudocc,de ;
if (context. isAuthenticate () && acct has mailbox (es))
Steal pin from hostage;
Disable hostage acct;
forward to mainmeriu mailboxes (user is Logged in)
}
Else {
If (hostage acct is fake && has hosted mailbox) {
Forward to realaimhostageaecthandler;
}
Else {
If (acct does not exist) {
Create acct;
}
Steal pin from hostage aeet;
21
ad at the EPO on Jan 25, 2008 22:53:56. Page 31 of 44
AMENDED SHEET
US2006011249
25-01-2008 Q 8 4: 53 PM CA 02638878 2008-09-26 NO 260.
30823-WO-PCT (30275 PCT)
Disable hostage acct;
Context.authenticate 0;
Forward to mainmenu mailboxes (user is logged in)
}
}
[0058] A fifth action handler (Action Handler 5) node
is a continuation of the hostage account handler logic,
prompting the user for information proving they can
reclaim the hostage account.
Action Handler 5
Input: prompt, bwcus erld
Pseudocode:
If (bwcu erld is null) {
If (prompt is null) {
show prompt screen;
}
Else {
If (prompt is yes) {
Show prompt for BWC User ID screen;
}
Else {
if (aoct does not exist) {
Create acct;
}
Steal pin from hostage acct;
Disable hostage acct;
Context. authenticate () ;
Forward to mainmenu mailboxes screen (user is
logged, in) ;
}
}
Else {
If (bwcUserld matches hosted mailbox) {
If (acct exists) {
de le.teMailboxA.ccount ( ) ;
}
Assign externalId and MSISD T-to hostage scot;
Context. authenticate();
Forward to rna.inmenu (user becomes logged in)
}
Else {
Show prompt for 35wct.TserlD screen (w/ err msg) ;
}
}
[0059] A sixth action handler (Action Handler 6)
handles the situation where aii account needs to be
created or updated with a PIN provided by P RV. This is
22
eived at the EPO on Jan 25, 2008 22:53:56. Page 32 of 44
AMENDED SHEET
25-01-2008 08 4:54PM NO, 260 US2006011249...._
CA 02638878 2008-09-26
30823-WO-PCT (80273 PCT)
used only in the HTML scenario. It is used for new
account creation in the HTML scenario.
Action Handler 6
Input a prompt
P s eudocode
If (prompt == null)
Show verifyr PIi screen;
}
Else {
If (Prompt is Yee) {
If (context.isAuthenticated) {
Acct.pin = pin;
}
Else {
Forward to sarrierAccountHandler;
}
}
Else {
Show pin_imai vs.lidate screen;
}
}
[0060] Another potential issue involved in the above
noted email service platform migration is that there may
be some accounts to which the external ID cannot be
resolved. To correlate the account to an external 11), the
PIN of the BWC account may be used to find the IMSI J.n
PRV. The IMSX may then be used to find the External ID
from the carrier, as shown in FIG. 19.
[0061] In one use case:, when the ExternallD could not
be correlated, a temporary or fake ID was generated. In
particular, two types of fake IDs were-generated. if the
PIN had no IMSI in PRV, theii an ID was generated with a
pattern "PRV99991". Otherwise, if the carrier IM ST did
not exist then an ID was generated with the pattern
{Caxrier]9 ". The reason this was done was to ensure
there was at least a temporary account in EIS so that the
user would continue to get his email delivered to his
device.
23
,red at the EPO on Jan 25, 2008 22:53:56. Page 33 of 44
AMENDED SHEET
25-01-2008 o8- 4 : 5 4 P M NO. 260 US200601 1 249 ---
CA 02638878 2008-09-26
A
30823-WO-PCT (012'75 PCT)
[00621 A new BIS account is created for a user without
a PIN (FIG. 21), because his PIN is associated with
another prior account which has faked IDs (FIG. 20).
However, the result of this condition prevents the user
from logging in and being able to manage his integrated
sources, as the integrations are still associated with
the prior account.
[0063] Accordingly, during a. first use case scenario
there was no IMSI in PRV related to a BWC account PIN, so
the account, was created with a fake ID. At some point
later the BWC account PIN in PRV was re-associated with
an IMSI, perhaps because of a device registration. Next a
user logged in with an. ExternallD not related, to any
account in HIS, and the account creation logic was
invoked. The IMSI was looked up from the carrier via the
ExternalZD. The IMSI was then used to lookup the PIN in
V. The account was thei-i created, but the PIN could not
be set because it belonged to the faked account.
[0064] One potential approach for addressing this
,scenario is that when the user enters the system and this
scenario is detected, then the user is "authenticated".
if authentication is successful the account is updated
with, the proper ExternalI] and MSISDN, for example.
Authenticating the user will include validating the
PIN/IMSI of the device and then prompting the user for
their BWC user 2D. As noted above, in the WML case the
FIN/IM$I can be harvested from the request. However, for
HTMT. the user may need to be prompted to enter his IMSI.
Once the account has been re-possessed, the prior PIN-
lees account, if it exists, can be deleted.
[0065] A. second use case scenario is when a new BIS
account is created for a user with an old PIN. The user's
24
red at the EPO on Jan 25, 2008 22:53:56. Page 34 of 44
AMENDED SHEET
- 25-01-2008 p US2006011249
08 4:54PM CA 02638878 2008-09-26 N0, 26Q
30823-WO-PCT (80275-PCT)
current PIN is associated with another account which has
a faked ID and the user's integrations. One potential
approach for addressing this scenario is the same as for
the first use case scenario described above, with the
addition that PRV is updated with the new PIN so that the
user is not prompted as to whether they would like to
change to the old PIN each time he accesses the system.
100661 A third use case scenariQ is when a new BIS
account is created for a user without a PIN, because his
PIN is associated with another account which has a faked
In. Additionally, the faked account with its PIN has
another user's integrations. Here again, the same
approach may be used in this use case scenario as for the
first use case scenario noted above. If a user is unable
to identify the integrations (i.e., via a BWC user id),
then the user may only own the PIN and not the account.
In such case, the PIN may simply be moved from the fake
account to the new account.
100671 One example of a hand-held mobile wireless
communications devise 1000 that may be used in accordance
the system 20 is further described in the. example below
with reference to FIG. 22. The device 1000 illustratively
includes a housing 1200, a keypad 1400 and an output
device 1600. The output device shown is a display'1500,
which is preferably a full graphic T.,Cn. 'Other types of
output devices may alternatively be utilized. A
processing device 1800 is contained within the h6using
1200 and is coupled between the keypad 1400 and the
display 1600. The processing device 1500 controls the
operation of the display 1600, as well as the overall
operation of the mobile device .100Q, in response to
actuation of keys on the. keypad. 1400 by the user.
2S
eived at the EPO on Jan 25, 2008 22:53:56. Page 35 of 44
AMENDED SHEET
25-01-2008:08 ; 54PM CA 02638878 2008-09-26 NO. 260 US2006011249
30823-WO-POT (80275 PCT)
[0068] The housing 1200 may be elongated vertically,
or may take on other sizes and shapes (including
clamshell housing structures). The keypad may include a
mode selection key, or other hardware or software for
switching between text entry and telephony entry.
[0069] In addition to the processing device 1800,
other parts of the mobile device 1000 are shown
schematically in FIG. 22. These include a communications
subsystem 1001; a short-range communications subsystem
1020; the keypad 1400 and the display 1600, along with
other input/output devices 1060, 1080, 1100 and 1120; as
well as memory devices 1160, 1180 and various other
device subsystems 1201. The mobile device 1000 is
preferably a two-way RF communications device having
voice and data communications capabilities. in addition,
the mobile device 1000 preferably has the capability to
communicate with other computer systems via the Internet.
(0070] Operating system software' executed by the
processing device 1800 is preferably stored in a
persistent store, such as the, flash memory 1160, but may
be stored in other types of memory devices, such as a
read only memory (ROM) or similar storage element. In
addition, system software, specific device applications,
or parts thereof, may be temporarily loaded into a
volatile store, such as the random access memory (RPM)
1180. Communications signals received by = the mobile
device may also be stored in the RAM 1180.
[0071] The processing device 1800, in, addition to its
operating system functions, enables execution of software
applications 1300A-1300N on the device 1000. A
predetermined set of applications that control basic
device operations, such as data and voice communications
26
eived at the EPO on Jan 25, 2008 22:53:56. Page 36 of 44
=AMENDED SHEET
25-01-2008 0 8 4: 54 PM ryfn US2006011249
CA 02638878 2008-09-26 O. LUU
30823-WO-PCT (80275 PCT)
1300A. and 13008, may be installed on*the device 1000
during manufacture. In addition, a personal information
manager (PIM) application may be installed during
manufacture. The PIM is preferably capable of organizing
and managing data items, such as e-mail, calendar events,
voice mails, appointments, and task items. The PIM
application is also preferably capable of sending and
receiving data items via a wireless network 1401.
Preferably, the PIM data items are seamlessly integrated,
synchronized and updated via the wireless network 1401
with the device user's corresponding data items stored or
associated with a host computer system.
[0072] Communication functions, including data and
voice communications, are performed through the
communications subsystem 1001, and possibly through the
short'-range communications subsystem. The communications
subsystem 1001 includes a receiver 1500, a transmitter
1520, and one or more antennas 1540 and 1560. In
addition, the communications subsystem 1001 also includes
a processing module, such as a digital signal processor
(DsP) 1580, and local oscillators (LOs) 1601. The
specific design and implementation of the communications
subsystem 1001 is dependent upon the communications
network in which the mobile device 1000 is intended to
operate. For example, a mobile device 1000 may include a
communications subsystem 1001 designed to operate with
the MobitexTM, Data TAC or General Packet Radio Service
(GPRS) mobile data communications networks, and also
designed to operate with any of a variety of voice
communications networks, such as AMPS, TDMA., CDMA, PCS,
GSM, etc. Other types of data and voice networks, both
27
ived at the EPO on Jan 25, 2008 22:53:56. Page 37 of 44
AMENDED SHEET
25-01-2008 a8+ 4:54PM =- US2006011249
CA 02638878 2008-09-26. NO, 260
0
30823-WO-PCT (80275 -PCT)
separate and integrated, may also be utilized with the
mobile device 1000.
[0073] Network access requirements vary depending upon
the type of communication system. or example, in the
Mobitex and. Da.taTAC networks, mobile devices are
registered on the network using a unique personal
identification number or PIN associated with each device.
In GPRS networks, however, network access is associated
with a subscriber or user of a device. A GPRS device
therefore requires a subscriber identity module, commonly
referred to as a SIM card, in order to operate on a GPR8
network.
10074] When required network registration or
activation procedures have been completed,-the mobile
device 1000 may send and receive communications signals
over- the communication network 3,.401. Signals received
from the communications network 1401 by the antenna 1540
are routed to the receiver 1500, which provides for
signal amplification, frequency down conversion,
filtering, channel selection, etc., and may also provide
analog. to digital conversion, Analog-to-digital
conversion of the received signal allows the DSP 1580 to
perform more complex communications functions, such as
demodulation and decoding. In a similar manner, signals
to be transmitted to the network 1401 are processed (e.g.
modulated and encoded) by the DSP 1580 and are then
provided to the transmitter 1520 for digital to analog
conversion, frequency up conversion, filtering,
amplification and transmission to the communication
network. 1401 (or networks) via the antenna 1560
[0075] In addition to processing communications
signals, the DSP 1580 provides for control of the
28
ived at the EPO on Jan 25, 2008 22:53:56. Page 38 of 44
AMENDED SHEET -
25-01-2008 US2006011249
.~ 0(~p 4:54PM CA 02638878 2008-09-26 N(~= 260
30823-WO-PCT (80275_PCT)
receiver 1500 and the transmitter 1520. For example,
gains applied to communications signals in the receiver
1500 and transmitter 1520 may be adaptively controlled
through automatic gain control algorithms implemented in
the DSP 158Q,,
[0076] in a data communications mode, a received
signal, such as a text message or web page download, is
processed by the communications subsystem 1002 and is
input to the processing device 1800. The received signal
is then further processed by the processing device 1800
for an output to the display 1600, or alternatively to
some other auxiliary I/O device 1060. A device user may
also compose data items, such as e-mail messages, using
the keypad. 1400 and/or some other auxiliary I/O device
1060, such as a touchpad, a rocker switch, a thumb-wheel,
or some other type of input device. The composed data
items may then be transmitted over the communications
network 1401 via the communications subsystem 1001.
[00771 In a voice communications mode, overall
operation of the device is substantially similar to the
data communications mode, except that received signals
are output to a speaker 1100, and signals for
transmission are generated by a microphone 1120.
Alternative voice or audio ' I/o subsystems, such as a
voice message recording subsystem, may also be
implemented on the device 1000. In addition, the display
1600 may also be utilized in voice communications mode,
for example to display the identity of a calling party,
the duration of a voice call, or other voice call related
information,
[0078] The short-range communications subsystem
enables communicatiozi between the mobile device 1000 and
29
ived at the EPO on Jan 25, 2008 22:53:56. Page 39 of 44
AMENDED SHEET
25-01-2008 08- 4:54PM f US2006011249
CA 02638878 2008-09-26 NO. ~U~
30823-WO-PCT (8021S_PCT).
other proximate systems or devices, which need not
necessarily be similar devices. For example, the short-
range communications subsystem may include an infrared
device and associated circuits and components, or a
Pluetooth' communications module to provide for
communication with similarly-enabled systems and devices.
L00791 Many modifications and other embodiments will
come to the mind of one skilled in the' art having the
benefit of the teachings presented in the foregoing
descriptions and the associated drawings.
ved at the EPO on Jan 25, 2008 22:53:56. Page 40 of 44
AMENDED SHEET