Note: Descriptions are shown in the official language in which they were submitted.
CA 02701077 2015-08-27
1
Anti-Tamper Techniques
The present invention relates generally to the field of software security and
to
techniques for increasing the resistance of a computer program to unauthorized
tampering. In particular, the present invention relates to program protection
techniques which seek to provide a degree of protection from unauthorized
modification and/or access to program code.
In releasing a software application for execution on end users' hardware, a
program
developer is effectively providing a user with complete access to the program
code
of that application. Unfortunately, it is a fact that some end-users will
attempt to
compromise a software application in order, for example, to obtain illegal
copies,
gain unlicensed access to certain features, steal IP from the application,
inject
malicious code or cheat in online games. Indeed, in the context of online
gaming,
which often seek to support hundreds or thousands of players simultaneously
over a
network, the occurrence of online cheating can seriously undermine honest
players'
experience of the game. Free access to executable code by unauthorised users
can
often result in loss of intellectual property and provides the user with an
easy means
for probing the application for security vulnerabilities. Also, applications
may be
reverse engineered and then modified to remove metering or usage control
before
being recompiled, ultimately resulting in a loss of revenue for the code
provider.
Thus, the environment into which publishers release their programs can be
considered to be a hostile one. There is therefore a need to protect programs
from
tampering or misuse, which may involve unauthorised modification and/or
copying.
A number of anti-tamper techniques have been previously proposed for deterring
would-be hackers or for protecting computer prograMs from being modified
and/or
copied. For example, it is known for software programs to utilise copy
protection
techniques or to have limitations encoded into them which, for example,
require
CA 02701077 2015-08-27
2
password or serial number access, prevent copying or restrict the use of the
program in some way.
Techniques for "obfuscating" software code have also been proposed. Obfuscated
code, or shrouded code as it is also known, is a type of executable code,
which is
intentionally made very difficult to read and understand. It is also known to
employ a
sub-set of obfuscation known as program-folding, e.g. to try to protect
firmware in
electrical equipment. Program folding involves calling routines from random
places
in the source-code, essentially causing the program to jump around during
execution.. Although obfuscated code can deter reverse engineering, there is a
still a
distinct possibility that the code could be read and understood, and therefore
modified. As such, obfuscated code provides only low-level security means, and
it is
often necessary to use in conjunction with additional security procedures,
e.g.
encryption. Additionally, the most common software reverse engineering attacks
target copy protection schemes. These schemes generally rely heavily on
existing
operating system procedure calls, making basic code obfuscation easily
bypassed
using the same tools used with unobfuscated code. Furthermore, obfuscated code
being difficult to read and understand is not only a problem for would-be
software
abusers but also for the software creators themselves, as obfuscated code is
inherently very difficult to debug. As a result, it is often necessary to
maintain two
versions of the code: the unobfuscated code for debugging, and the obfuscated
code for distribution. Due to the low level of security provided, this
additional effort is
often considered to outweigh the benefits of obfuscated code and therefore
alternative methods are required.
Preferred embodiments described herein may provide a program, or a portion
thereof, with some protection for attributes specified by the program
developer, in
order to try to ensure those attributes are enforced for as long as possible.
Some
embodiments also seek to protect against the unauthorised tampering of a
computer
program, e.g. modification of the program, that is against the wishes of the
original
3
author or program developer. More specifically, some embodiments of the
present
invention seek to provide a degree of protection against unauthorised
modification of
the application and/or data in order to prevent an end-user from disabling
attributes of
the program, for example, features which serve to enforce
usage/access/dissemination policies.
In one embodiment there is provided an anti-tamper method for protecting a
program
code portion against tampering. The anti-tamper method involves dividing the
program code portion into a plurality of code segments, defining a sequence of
code
segments from the code segments, wherein the sequence of code segments
includes
a root code segment and a plurality of sub-code segments and providing each
sub-
code segment with an integrity checking portion for checking the integrity of
a
respective target code segment, the respective target code segment of a given
sub-
code segment being the code segment that is sequentially adjacent in a
checking
direction towards the root code segment. The integrity checking portion of a
given
sub-code segment is operable to carry out a checking procedure on the
respective
target code segment to obtain a runtime result, and to compare the runtime
result
with a reference result comprised in the given sub-code segment and the
integrity
checking portion of a given sub-code segment is further operable to write the
runtime
result into memory associated with the given sub-code segment, such that the
integrity checking procedure of a further sub-code segment sequentially
adjacent in a
checking direction away from the root code segment carries out the checking
procedure on memory including the runtime result.
In another embodiment there is provided an anti-tamper system for protecting a
program code portion against tampering, the anti-tamper system including a
computer readable storage medium having a plurality of program code segments
of a
program code portion stored thereon, the program code segments defining a
sequence of code segments, wherein the sequence of code segments includes a
root
code segment and a plurality of sub-code segments. Each sub-code segment
includes an integrity checking portion for checking the integrity of a
respective target
CA 2701077 2017-08-23
4
code segment, the respective target code segment for a given sub-code segment
being the code segment that is sequentially adjacent in a checking direction
towards
the root code segment. The integrity checking portion of a given sub-code
segment is
operable to carry out a checking procedure on the respective target code
segment to
obtain a runtime result, and to compare the runtime result with a reference
result
comprised in the given sub-code segment. The integrity checking portion of a
given
sub-code segment is further operable to write the runtime result into memory
associated with the given sub-code segment, such that the integrity checking
procedure of a further sub-code segment sequentially adjacent in a checking
direction
away from the root code segment carries out the checking procedure on memory
including the runtime result.
In another embodiment there is provided an anti-tamper method for protecting a
program code portion against tampering. The anti-tamper method involves
dividing
the program code portion into a plurality of code segments, defining a
sequence of
code segments from the code segments, wherein the sequence of code segments
includes a root code segment and a plurality of sub-code segments and carrying
out
a reference result computation process in order to obtain a reference result
for each
sub-code segment. The reference result computation process involves carrying
out,
for a given sub-code segment, an implementation checking procedure on a
respective target code segment, the respective target code segment of a given
sub-
code segment being the code segment that is sequentially adjacent in a
checking
direction towards the root code segment; and writing the reference result into
memory
associated with the given sub-code segment, such that a runtime checking
procedure
for a further sub-code segment sequentially adjacent in a checking direction
away
from the root code segment carries out the implementation checking procedure
on
memory including a runtime result of the runtime checking procedure for the
given
sub-segment.
In another embodiment there is provided an integrity checking method for
checking
the integrity of a program code portion including a plurality of code
segments, the
CA 2701077 2017-08-23
5
program code portion having at least one sequence of code segments including a
root code segment and a plurality of sub-code segments. The integrity checking
method involves for a given code segment performing a runtime checking
procedure
which checks the integrity of a respective target code segment to obtain a
runtime
result, the respective target code segment for the given sub-code segment
being the
code segment that is sequentially adjacent in a checking direction towards the
root
code segment, comparing the runtime result with a reference result and writing
the
runtime result into memory associated with the given sub-code segment, such
that
the integrity checking procedure of a further sub-code segment sequentially
adjacent
in a checking direction away from the root code segment carries out the
checking
procedure on memory including the runtime result.
In another embodiment there is provided an integrity checking system for
checking
the integrity of a program code portion, the integrity checking system
including a
computer readable storage medium having a plurality of program code segments
of
the program code portion stored thereon, the program code segments defining a
sequence of code segments, wherein the sequence of code segments includes a
root
code segment and a plurality of sub-code segments. The integrity checking
system
further includes a runtime checking portion operable to check the integrity of
a
respective target code segment for a given sub-code segment of the sub-code
segments, to obtain a runtime result, the respective target code segment for
the given
sub-code segment being the code segment that is sequentially adjacent in a
checking
direction towards the root code segment; compare the runtime result with a
reference
result comprised in the given sub-code segment; and write the runtime result
into
memory associated with the given sub-code segment, such that the integrity
checking
procedure of a further sub-code segment sequentially adjacent in a checking
direction
away from the root code segment carries out the checking procedure on memory
including the runtime result.
In some embodiments there is provided an anti-tamper method for protecting a
program code portion against tampering, the anti-tamper method comprising:
CA 2701077 2017-08-23
CA 02701077 2015-08-27
6
dividing said program code portion into a plurality of code segments;
defining a sequence of said code segments, wherein said sequence of code
segments comprises a root-code segment and a plurality of sub-code segments;
providing each sub-code segment with an integrity checking portion for
checking the integrity of a target code segment, said target code segment of a
given
sub-code segment being the code segment that is sequentially adjacent in a
checking direction towards said root-code segment;
wherein the integrity checking portion of a given sub-code segment is
operable to carry out a checking procedure on the respective target code
segment to
obtain a runtime result, and to compare said runtime result with a reference
result.
The reader will appreciate that a "sequence" of code segments implies that
code
segments follow one after the other, i.e. a succession of code segments or a
series
of code segments forming chain. The integrity checking functions built into
each of
the sub code segments therefore effectively binds the segments together to
form a
linked chain of checks.
It should be appreciated that, within the context herein, a sequentially
adjacent code
segment refers to the adjacent code segment within the defined sequence of
code
sequence and not, necessarily, the physically adjacent code segment.
The, or each, sequence may comprise at least one segment having an attribute
defining program portion which specifies an attribute set by the developer.
For
example, the attribute may define a rule, a requirement of use or a limitation
to
restrict or control the use of the program. Thus, some embodiments may allow a
variety of appealing protections to be applied to candidate programs,
including the
ability to support business models such as up selling to pirate users of a
protected
application. Furthermore, by appropriately selecting the content of the
attribute
defining program portion, which will typically define a proper use policy of
the
application, some embodiments can be applied to a wide range of protection
needs,
CA 02701077 2015-08-27
7
such as: client protection; DRM protection; licence management; IP protection;
pirate distribution tracing and the like.
In the context of a computer game the program may, for example, specify a
trial
period of 30 days or may limit use of the computer game up to level five.
Thus, in
these circumstances and according to one embodiment, a code sequence may be
defined in which the length of the trial period forms one attribute to be
protected by
the sequence. Thus, a hacker may wish to try to change the program code to
lengthen the trial period or raise the allowed upper level of play. However,
in the
case of a program portion which has been protected by an anti-tamper method of
the type described herein, in order to achieve this without the inherent
integrity
checking system failing, the hacker would have to modify not only the code of
the
attribute defining program portion, but also the code for every code segment
in the
code sequence to ensure that the runtime result obtained for a given target
code
segment could be verified with reference to the stored reference result.
Whilst the
modification of each code segment in this manner may not be particularly
difficult,
the process of making consequential changes to all the sub-code segments in
the
sequence in order to defeat the protection would be extremely laborious and
time-
consuming, and could take hundreds or even thousands of hours depending on the
number of sequences of checks embedded within a given application and the
number of code segments comprised in each sequence.
Preferably, the root code segment will comprise the program portion defining
an
attribute of the program. Although it is convenient for a sequence of code
segments
to be defined such that the root code segment comprises, or is associated
with, code
or memory which specifies or defines a given attribute, it should be
appreciated that
the attribute-defining segment of a sequence may be any code segment,
including a
sub-code segment.
CA 02701077 2015-08-27
8
According to one embodiment, the anti-tamper method will involve establishing
the
distribution or "topology" of the checks embedded in the program code portion.
The
defined topology represents the way in which code segments are effectively
"linked"
to each other within the divided source code or within the compiled code, in
the
sense that each integrity checking portion will carry out a checking procedure
on a
specified target code segment at runtime. Preferably, a topology is
established for a
candidate program portion in which the code segments of that program portion
define a plurality of sequences of code segments, wherein one or more code
segments forms a part of more than one code sequence. A topology may be
established in which one or more of the sub-code segments comprises an
integrity
checking portion having a plurality of target code segments defined therefore
such
that, at runtime, that sub-code segment will be operable to carry out a
checking
procedure on more than one target code segment. According to one embodiment, a
topology may be established for a given program portion which comprises a so-
called "inverted tree structure". According to such an embodiment, the sub-
code
segments can be considered as forming different "levels" of the structure,
with a root
code segment defining the "top" of the tree, wherein every sub-code segment at
a
given level is operable to perform a checking procedure on each of the sub-
code
segments comprised in the level "above" (towards the root code segment).
The implementation of an anti-tamper method according to some embodiments will
typically involve a reference result computation process whereby the, or each,
reference result of each sub-code segment is computed. This process may
involve
carrying out a sequence of computations to obtain reference results for each
of the
defined sequences of code segments.
A reference result computation process that may be performed for a given code
sequence according to one embodiment will now be briefly described. The
reference
result for a first sub-code segment which is sequentially adjacent in a
direction
opposite to the checking direction to the root-code segment is obtained by
CA 02701077 2015-08-27
9
performing an implementation checking procedure, defined by the integrity
checking
portion of the sub-code segment, on its defined target code segment namely the
root
code segment. This may involve carrying out a cyclic redundancy check on code
or
memory of the root code segment that specifies an attribute of the program to
be
protected, to obtain a first value or first "reference result". At runtime,
the integrity
checking portion will be operable to perform a runtime checking procedure on
the
predefined area of memory of the root code segment in order to obtain a first
"runtime result" and will be further operable to compare this runtime result
with the
reference result associated therewith. The integrity of the root code segment
is
verified according to this comparison, which may require the runtime result to
be
equal to the reference result or related by some predetermined relationship.
Similarly, the reference result for a second sub-code segment which is
sequentially
adjacent in a direction opposite to the checking direction to the first sub-
code
segment, is obtained by performing an implementation checking procedure on its
defined target code segment, namely the first sub-code segment. The
implementation checking procedure is carried out, for example, on memory or
code
of the first code-segment that specifies the first reference result. Thus, a
second
reference result (which will be dependent upon the first reference result) is
obtained.
At runtime, the integrity checking portion of the second sub-code portion is
operable
to carry out a runtime checking procedure on memory or code that specifies the
value of the first runtime result, as opposed to the first reference result,
and is then
further operable to compare the resultant second runtime result with the
second
reference result associated with the second sub-code segment.
This reference result computation process continues in this manner until the
(or
each) reference result for each of the sub-code segments comprised in the
sequence has been defined.
CA 02701077 2015-08-27
According to another embodiment, there is provided an integrity checking
method for
checking the integrity of a program portion comprising a plurality of code
segments,
said program portion having at least one sequence of code segments comprising
a
root code segment and a plurality of sub-code segments, the integrity checking
method comprising, for a given code segment:
i) performing a runtime checking procedure which checks the
integrity of a target code segment to obtain a runtime result, said target
code segment for said given sub-code segment being the code
segment that is sequentially adjacent in a checking direction towards
said root-code segment; and
ii) comparing said runtime result with a reference result.
When an application or program portion that has been derived according to one
of
the above described embodiments is executed within an execution environment or
runtime system of a computer, the program will be operable to conduct, at
runtime,
an integrity checking method according to an embodiment of the second aspect.
It
should be appreciated that the runtime checking procedure defined for a given
sub-
code segment will be initiated when that sub-code segment is executed as part
of
the program portion.
Some preferred embodiments may advantageously provide a robust and effective
means for protecting a program portion from tampering In order to crack or
undermine the protection afforded by some embodiments in order, for example,
to
modify an attribute defining a proper use of the program, it would be
necessary in
the case of a program protected by an anti-tamper method according to an
embodiment, for an end-user to identify and alter the properties of every
single code-
segment comprised in the code sequence which is associated with that defined
attribute. Thus, only by removing all the checks can the application be
modified at
will. While this is not an impossible task, it is an extremely laborious and
time-
consuming one which may take hundreds or even thousands of hours to complete.
CA 02701077 2015-08-27
10a
Some embodiments are advantageous in that they provide an effective protection
mechanism which will deter hackers from making undetected modifications to an
application.
In particular, some embodiments allow one or more attributes of the program
specified by the provider to be protected against unauthorised tampering by
means
of a large number of simple, inter-connected checks which verify the integrity
of the
program and of themselves. The checks are "inter-connected" in the sense that
each
one checks another, eventually providing a huge web of checks. This makes for
a
mutually self-buttressing, distributed integrity checking mechanism.. Any
unauthorised modification made by an end-user will be advantageously detected
by
this system, and attempts to circumvent these checks will preferably be
prevented.
There are numerous types of checking algorithms or functions which would be
suitable for the checking procedure. Preferably, the integrity checking
portion of one
said subcode segment defines a checking procedure which involves performing a
checksum procedure on the target code segment. This may be, for example,
cyclic
redundancy check.
According to one embodiment, a candidate application, or program code portion,
is
divided into code segments such that each segment comprises a function of the
program code portion. This may be advantageous in that it ensures that the
critical
components of the application are subjected to the integrity checking
procedures.
The segments are preferably defined to include code adjacent to a function in
order
to ensure that there is not code of the program portion which does not form
part of a
defined segments.
It is envisaged that some embodiments will involve the insertion of a very
large
number of checks in a given program portion or application, for example
between a
CA 02701077 2015-08-27
10b
thousand and ten thousand checks in an application which is a few megabytes in
size. A program code portion may comprise a plurality of code sequences, such
that
one or more segments form part of more than one code sequence.
According to another embodiment, there is provided an anti-tamper system for
protecting a program code portion against tampering, the anti-tamper system
comprising a computer readable storage medium having a plurality of program
code
segments of a program code portion stored thereon, said program code segments
defining a sequence of code segments, wherein said sequence of code segments
comprises a root-code segment and a plurality of sub-code segments;
wherein each sub-code segment comprises an integrity checking portion for
checking the integrity of a target code segment, said target code segment for
a given
sub-code segment being the code segment that is sequentially adjacent in a
checking direction towards said root-code segment;
and wherein the integrity checking portion of a given sub-code segment is
operable to carry out a checking procedure on the respective target code
segment to
obtain a runtime result, and to compare said runtime result with a reference
result
comprised in said given sub-code segment.
According to earlier described embodiments it is possible for the required
checking
code or integrity checking functionality, i.e. an integrity checking portion
and a
reference portion (which comprises a reference result) for each sub-code
segment,
to be inserted at source code level, i.e. directly into the source code.
Alternatively, it is possible for the checking code to be inserted into the
application
following after it has been compiled. Thus, according to an anti-tamper method
of
one embodiment, the program portion comprises source code.
Alternatively, according to an anti-tamper method of another embodiment, the
program portion comprises compiled code.
CA 02701077 2015-08-27
10c
The insertion of the check portions into the underlying application or program
portion, either as source code or as object code, may be achieved in a number
of
ways. For example, it is possible for the checks to be inserted in the code
manually,
whereby a program developer inserts the checking code into he defined program
code segments. This, however, will be very labour intensive. Alternatively, it
is
possible for the integrity checking portion and the reference result to be
inserted into
the sub-code segments by means of pre-processing techniques involving the use
of
one or more macros written for this purpose.
As a further alternative, metaprogramming techniques may be useful to apply
the
network of checks at source code level. Such techniques may be particularly
advantageous since they will allow automation of the injection of the checking
portions into the application. In particular, metaprogramming techniques which
utilise
a data structure, such as an abstract syntax tree (AST), allow analysis of a
given
program code portion or application in a form that is amenable to making
modifications. Thus, integrity checking portions and reference results can be
conveniently installed throughout the divided segments of the application.
This
approach may also be advantageous in that inserted checks applied at source
code
level are naturally hidden, or obfuscated, since they are compiled with the
application code. Thus, using a source code level meta-programming approach is
beneficial in that it allows injected checks to be disguised by the optimising
compiler
that runs over the resultant source code which will intersperse integrity
checking
code with the underlying application code.
In any of the above embodiments or aspects, the various features may be
implemented in hardware, or as software modules running on one or more
processors. Features of one aspect or embodiment may be applied to any of the
other aspects or embodiments.
CA 02701077 2015-08-27
10d
One embodiment also provides a computer program or a computer program product
for implementing the techniques described herein, and a computer readable
storage
medium having stored thereon a program for implementing the techniques
described
herein. A computer program for this purpose may be stored on a computer-
readable
medium, or it could, for example, be in the form of signal such as a
downloadable
data signal provided from an internet website, or it could be in any other
form.
For a better understanding of the embodiments described herein, and to show
how
the same may be carried into effect, reference will now be made by way of
example
to the accompanying drawings in which:
Figure 1 illustrates an anti-tamper system according to one embodiment;
Figure 2 illustrates a code sequence of the anti-tamper system shown in Figure
1 ;
and
Figure 3 illustrates a reference result computation process P according to one
embodiment, and an integrity checking process performed at runtime;
Figure 4 shows a simplified illustration of an anti-tamper system having an
inverted
tree structure; and
Figure 5 illustrates the steps involved according to an anti-tamper method
utilising
meta-programming.
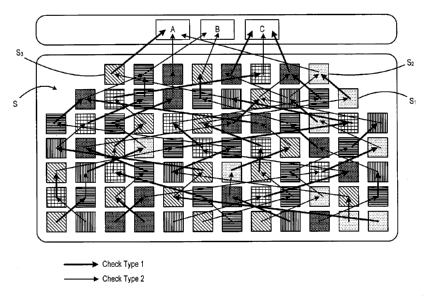
Figure 1 shows a program code portion which has been divided into a plurality
of
code segments comprising three root code segments A, B and C and a plurality
of
sub-code segments S forming eight sequences of code segments. In this
embodiment, the program code portion has been compiled and, thus, the
positions
CA 02701077 2015-08-27
10e
of the sub-code segments represents their distribution throughout the compiled
application.
In this embodiment, the root code segments represent segments of code which
comprise means defining attributes of proper use of the program which have
been
specified by the developer. These attributes may include, for example:
limitations
imposed on the use of the program or checks that are to be performed by the
program such as checking that the user of the program has purchased the full
version of the application, or has a licence to use the application.
The different shading of the segments represents the method that is used to
disguise the presence of the checking code within the application code. Each
arrow
from a given sub-code segment is to a target code segment which is
sequentially
adjacent to the given sub-code segment in a checking direction. For example,
the
target code segment of sub-code segment S1 is sub-code segment S2.
Furthermore,
the target code segment of sub-code segment S3 is root code segment A. The
thickness of the arrow represents the type of checking process that is
employed by
the integrity checking portion of the originating code segment. Thus,
according to
this embodiment, two types of checking procedure are employed. These may be,
for
example, a cyclic redundancy check operable to obtain a checksum of a defined
area of the target code segment to obtain a value, or some other sort of
checksum
or other checking method.
CA 02701077 2010-03-26
WO 2009/044129 PC
T/GB2008/003318
11
Figure 2 shows one of the sequences of the Figure 1 embodiment which is
associated
with root-code segment B. In order to compute the reference result for each of
the sub-
code segments Ba to Bg, a reference result computation process is performed.
This
may be implemented as described below.
Specifically, according to the present embodiment, the reference result for
sub-code
segment Ba is obtained by performing an implementation checking procedure on
its
target code segment, namely the root code segment B. This involves carrying
out a
cyclic redundancy check (for example), on a predetermined portion of memory
which
is associated with root code segment B and which specifies an attribute of the
program,
to obtain a first value or first "reference result". At runtime, the integrity
checking
portion will be operable to perform a runtime checking procedure on the
defined part of
the memory of root code segment B in order to obtain a first "runtime result",
and will
be further operable to compare this runtime result with the reference result
associated
therewith. The integrity of the root code segment is verified according to
this
comparison, which may require the runtime result to be equal to the reference
result or
related by some predetermined relationship.
Similarly, the reference result for a second sub-code segment Bb, is obtained
by
performing an implementation checking procedure on its target code segment,
namely
sub-code segment Ba. The implementation checking procedure is carried out on a
predefined area of memory associated with sub-code segment Ba that contains
the first
reference result. Thus, a reference result for Bb, which will be dependent
upon the first
reference result for Ba, is derived and is subsequently stored. At runtime,
the integrity
checking portion of sub-code segment Bb is operable to carry out a runtime
checking
procedure on part of memory associated with 13, that stores the first runtime
result (as
opposed to the first reference result), and is then further operable to
compare the
resultant second runtime result with the second reference result associated
with sub-
code segment Bb.
This reference result computation process continues in this manner until the
(or each)
reference result for each of the sub-code segments Ba to Bg has been derived
and
stored.
CA 02701077 2010-03-26
WO 2009/044129
PCT/GB2008/003318
12
Figure 3 illustrates, on the left-hand side thereof, a reference result
computation
process P according to an embodiment of the present invention, for a code
sequence
comprising a root code segment C and sub-code segments Ca and Cb. Reference
result computation process P comprises carrying out, in sequence, a first
reference
result computation process P1, for defining a reference result R1 of sub-code
segment
Ca, followed by a second reference result computation process P2 for deriving
a
reference result R2 of sub-code segment Cb. Process P1 involves carrying out
an
implementation checking process, whereby a checksum procedure is performed on
a
memory portion Mc of root-code segment C. Memory portion MG specifies an
attribute A
defined by, for example, the program developer. The checksum procedure derives
a
value which is employed as first reference value R1. The value R1 is
stored/written into
memory portion McaRl= A second reference result computation process P2 is
performed
for sub-code segment Cb in which an implementation checking process comprising
a
checksum is performed on the memory potion MõRi of sub-code segment Ca to
derive
a value which is employed as second reference value R2, The value of R2 is
stored in
memory portion M
¨cbR2.
The right-hand side of Figure 3 illustrates an integrity checking method that
will be
performed by sub-code segments Ca and Cb at runtime. Thus, the integrity
checking
potion of sub-code segment Ca is operable to perform an integrity checking
method
that will be initiated when, or shortly after, the execution of sub-code
segment is
commenced. According to the integrity checking method that is to be performed
by Ca,
a runtime checking process is carried out, whereby a checksum procedure is
performed on a memory portion MG of root-code segment C to obtain a runtime
result
r1. This result is compared with the reference result R1 stored in memory
portion Mc1R1.
According to the outcome of this comparison, the integrity checking procedure
will
either pass or fail. Furthermore, runtime result r1 is written to memory
portion Mewl. A
checksum procedure performed on memory portion M
¨carl will be generate the same
result as the same checksum procedure performed on memory portion McIRlif r1
equals
R1.
The integrity checking portion of sub-code segment Cb is operable to carry out
an
integrity checking procedure, which involves checking the memory portion Mean
i of sub-
code segment Cb, to obtain a runtime result r2 Thus, the value of r2 will
depend on the
value of 1.1 obtained by the integrity checking portion of sub-code segment
Ca.
CA 02701077 2010-03-26
WO 2009/044129
PCT/GB2008/003318
13
Moreover, a comparison with r2 and R2 will only "pass" if the comparison with
r1 and R1
also passes.
The benefit of embodiments of the present invention can be appreciated by
considering
what would happen if a hacker were to modify attribute A, for example, to
become A'.
In this case, in order to prevent an integrity checking procedure that will be
performed
by Ca at runtime from failing, the hacker will also have to modify the value
of reference
value R1 so that runtime result r1 compares favourably with R1. Furthermore,
since the
validity of information stored in memory portion Moan will be checked by sub-
code
segment Cb, then in order to ensure that an integrity checking procedure that
will be
carried out by Cb at runtime does not fail, it would be necessary for the
hacker to
modify the value of reference value R2 so that runtime result r2 will compare
favourably
with R2. Effectively, in order to modify an attribute specified in the root
code segment
(for example), it would be necessary for a hacker to trace and modify every
sub-code
segment linked to that root-code segment.
Figure 4 shows a simplified illustration of a candidate program portion which
has been
divided into a plurality of code-segments, wherein a topology of checking
procedures
are defined in the form of an inverted tree structure. Thus, root code portion
D will be
checked at runtime by two primary level sub-code segments Dal and Da2.
Furthermore,
Dal and Da2 will be checked at runtime by each of four secondary level sub-
code
segments Db2 to Db4. Thus, in this example, a total of eight sequences of code
segments can be defined, with Dal forming a part of four sequences of code
segments
and 0b2 forming part of four sequences of code segments.
Figure 5 illustrates the steps involved in an anti-tamper method embodying the
present
invention for protecting a target application against tampering. As shown by
Figure 5,
the application's source code is parsed to generate a representation of it as
an Abstract
Syntax Tree (AST). Small meta-programs are then used to compile a set of
target
functions into which checking code can sensibly be inserted. Criteria used
here
include: the ability of the host code to adequately disguise an injected
check; suitability
in terms of performance e.g. is code in the target function part of a time-
critical inner
loop?; number of times the function is called by the application.
CA 02701077 2015-08-27
14
The target functions form the basis of the code segments into which the
underlying
target application is divided. The topology of the integrity checking network
is
determined.
Small meta-programs are used to insert checking code into the target
functions. The
injected code should, come runtime, contain references to the function that is
to be
checked. At this stage, dummy values are injected for the area of memory to
check,
and the value that that check should generate.
The code (with injected checks) is compiled, for example using a standard C++
compiler into an executable (EXE) file. At the linking phase of compilation, a
so-
called MAP file is generated which contains information about where in the EXE
the
code for each application function has ended up. From this, it is possible to
infer
where in runtime memory these functions will reside.
A number of steps are performed for each of the target code segments which
were
injected with checks:
-the compiled code for these code segments is located using data from the
MAP file;
-the code segment that this check should target is established (from the
topology decided above);
-the code for that code segment is located using the MAP file;
-the checksum (or other integrity checking procedure) of the code for that
function is computed;
-the dummy values inserted above are patched up so that this check does
indeed target the one required by the topology. Furthermore, the computed
checksum computed as the value that the run-time check should expect to
find is inserted. If this value is not found at runtime, the code segment in
question has been modified: a hack has taken place.
CA 02701077 2015-08-27
This process results in a protected EXE, i.e. a protected program portion or
anti-
tamper system embodiment.
It is important that the checks are patched up in the correct order, i.e.
starting at the
"top" of a code sequence with the root code segment, and working down. The
patched up functions at the top should themselves be check summed for the
checks
lower down.
Having illustrated and described several embodiments and examples, it should
be
apparent that the invention can be modified, embodied, elaborated or applied
in
various ways within the scope of the claims. Embodiments can be implemented in
software programs and data structures stored on portable storage media,
transmitted by digital communications, or other transmission medium, or stored
in a
computer memory. Such programs and data structures can be executed on a
computer, to perform the methods described herein and variants thereof, and to
operate as a machine, or part of apparatus, having the capabilities described
herein.