Note: Descriptions are shown in the official language in which they were submitted.
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
BIOMETRIC AUTHENTICATION SYSTEM AND METHOD
CROSS-REFERENCE TO RELATED APPLICATION
The present patent application claims priority
on United States Provisional Patent Application
No. 61/425,473, filed on December 21, 2010, and
incorporated herein by reference.
FIELD OF THE APPLICATION
The present application relates to systems and
method for the automatic surveillance of individuals at
a remote location or in out-of-prison detainment, such
as in house arrest or parole instances.
BACKGROUND OF THE ART
In various justice systems, house arrest is a
common method of detention. House arrest involves
monitoring an individual through actual visit to the
home or phone calls to ensure that the house arrest or
curfew conditions are being respected. In some
instances, the monitoring is done 24/7 by correctional
service agents.
Home detention provides an alternative to
imprisonment and aims to reduce re-offending while also
coping with expanding prison numbers and rising costs.
It allows eligible offenders to retain or seek
employment, maintain family relationships and
responsibilities and attend rehabilitative programs that
contribute towards addressing the causes of their
offending.
In some countries, house arrest is often
enforced through the use of technology products or
services. One method is an electronic sensor locked to
the offender's ankle (technically called an ankle
monitor, sometimes referred to as a tether) . If the
subject and the sensor venture too far from the home,
-1-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
the violation is recorded and the proper authorities are
summoned. To discourage tampering, many ankle monitors
can now detect attempted removal.
In operation, at timed intervals, the ankle
monitor sends a radio frequency signal containing
location and other information to a receiver. If an
offender moves outside of an allowed range, the
authorities will be notified. Ankle monitors are
designed to be tamper-resistant and can often alert
police to tampering attempts.
The most common configuration is a radio-
frequency transmitter unit that sends a signal to a
fixed-location receiving unit in the offender's
residence. The residence unit uses either a land line or
a cellular network to relay information to a service
center server. If the offender is not at the residence
at times stipulated, an alert message is sent to the
service center, and then relayed to the supervising
probation or parole officer. GPS units are similar in
design, but the offender also carries a GPS cell phone
unit that receives a signal from the ankle unit, or both
functions may be combined into one ankle unit.
However, this type of system can only confirm
that the `ankle monitor' in inside the allowed range and
not necessarily the offender who is supposed to be
wearing it. This is why the monitors are designed with
tamper-resistant devices.
The monitoring service is often contracted out
to private companies, which assign employees to
electronically monitor many convicts simultaneously. If
the sensors detect a violation, the monitoring service
calls the convict's probation officer. The electronic
surveillance together with frequent contact with the
probation officers, and checks by the security guards
all provide for a secure environment.
-2-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
Another method of ensuring house arrest
compliance is achieved through the use of automated
calling services that require no human contact to check
on the offender. Random calls are made to the residence
and the respondent's answer is recorded and compared to
the offenders' voice pattern. Authorities are notified
only if the call is not answered or if the recorded
answer does not match the offenders' voice pattern.
Electronic monitoring is considered a highly
economical alternative to the cost of imprisoning
offenders, especially considering that the convict is
often required to pay for the monitoring as part of his
or her sentence.
While house arrest can be applied to common
criminal cases when prison does not seem an appropriate
measure, the term is often applied to the use of house
confinement as a measure of repression by authoritarian
governments against political dissidents.
The challenge is to design a system that will
locate a `specific person' within a range. For this it
will require to have strong authentication of the
offender using an identification capability
SUMMARY OF THE APPLICATION
It is therefore an aim of the present
disclosure to provide a biometric authentication system
and method that address issues associated with the prior
art.
Therefore, in accordance with a first
embodiment of the present application, there is provided
a biometric authentication apparatus comprising: a
biometric reader for capturing biometric data of an
individual; a movement sensor unit comprising at least
one micro-electromechanical sensor for detecting
movement, the movement sensor unit recording movement
data from the movement detected by the at least one
-3-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
micro-electromechanical sensor; and an authentication
processor for triggering authentication checks of the
individual by emitting an authentication demand signal,
and for transmitting a status signal related at least to
the captured biometric data and the recorded movement
data to an authentication server.
In accordance with the first embodiment of the
present application, a biometric authenticator
determines the authenticity of the captured biometric
data with respect to a biometric profile of an
individual at the authentication checks.
Still in accordance with the first embodiment
of the present application, a biometric profile database
stores the biometric profile of the individual.
Still in accordance with the first embodiment
of the present application, a media reader obtains the
biometric profile of the individual from a medium at the
authentication checks.
Still in accordance with the first embodiment
of the present application, a media authenticator
authenticates the medium when obtaining the biometric
profile, the status signal indicating a failed
authentication of the medium.
Still in accordance with the first embodiment
of the present application, a geographic localization
unit provides location data of the apparatus at the
authentication checks, the status signal indicating a
location of the apparatus.
Still in accordance with the first embodiment
of the present application, the biometric reader is a
finger vein reader.
Still in accordance with the first embodiment
of the present application, the movement sensor unit
comprises a time-measuring device for recording a
duration of movements detected by the at least one
micro-electromechanical sensor.
-4-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
Still in accordance with the first embodiment
of the present application, the movement sensor unit
identifies when the recorded movement data exceeds a
preset threshold, the status signal indicating a faulty
movement.
Still in accordance with the first embodiment
of the present application, the movement sensor unit
comprises at least one of a movement magnitude value and
a movement duration value in the preset threshold.
In accordance with a second embodiment of the
present disclosure, there is provided a biometric
authentication system comprising: at least one of the
biometric authentication apparatus; and an
authentication server comprising for receiving the
status signal from the at least one biometric
authentication apparatus, and for outputting
authentication monitoring data.
In accordance with the second embodiment of
the present application, the authentication server
further comprises a driver for driving a demand for
authentication check to the biometric authentication
station as a function of an individual profile schedule.
Still in accordance with the second embodiment
of the present application, the authentication server
further comprises a profile authenticator for confirming
the data received from the biometric authentication
apparatus, and for producing an alert for a wrongful
authentication.
Still in accordance with the second embodiment
of the present application, a location comparator
compares a location of the at least one biometric
authentication station to an expected location, and
produces an alert for wrongful location.
In accordance with a second embodiment of the
present disclosure, there is provided a method for
authenticating a presence of an individual at an
-5-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
authentication station comprising: continuously
recording movement data using at least one micro-
electromechanical sensor in the authentication station;
demanding an authentication of an expected individual at
the authentication station; capturing biometric data
from an individual present at the authentication
station; authenticating an identity of the present
individual by comparing the captured biometric data to a
biometric file of the expected individual; determining
from the recorded movement data if the authentication
station is at an expected location; and outputting a
fault signal if the identity is not of the expected
individual and/or if the authentication station is not
at the expected location.
In accordance with the third embodiment of the
present application, a medium is read to obtain the
biometric file at the authentication station prior to
authenticating the identity.
Still in accordance with the third embodiment
of the present application, the medium is authenticated
when read.
Still in accordance with the third embodiment
of the present application, location data is produced at
the authentication station and comparing the produced
location data to the expected location.
BRIEF DESCRIPTION OF THE DRAWINGS
Fig. 1 is a block diagram illustrating a
biometric authentication system in accordance with the
present disclosure;
Fig. 2 is a block diagram of a biometric
authentication station of the biometric authentication
system of Fig. 1.;
Fig. 3 is a block diagram of an authentication
server of the biometric authentication system of Fig. 1;
and
-6-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
Fig. 4 is a flow chart of a method for
authenticating a presence of an individual at an
authentication station.
DESCRIPTION OF THE PREFERRED EMBODIMENTS
Referring to the drawings and more
particularly to Fig. 1, there is generally illustrated
at 10 a biometric authentication system. The biometric
authentication system 10 (hereinafter the system 10) is
used to localize individuals A (e.g., offenders,
detainees, dissidents, etc) by authorities B in specific
incarceration conditions, such as house arrest, parole,
or the like. The system 10 may also be used to localize
individuals A in other types of conditions, such as
during exam in schooling matters, etc.
As illustrated in Fig. 1, the system 10 has a
plurality of biometric authentication stations 12 to
which individuals A will report. The biometric
authentication stations 12 are also referred to as
biometric authentication apparatuses. The system 10
also has an authentication server 14 to manage the
authentication statuses provided by the various stations
12. In Fig. 1, four of the biometric authentication
stations 12 (hereinafter, the station 12) are
illustrated. It is understood that more or less of the
stations 12 could be related to the server 14. In an
embodiment, a system 10 comprises a high number of
stations 12 for a single server or network of servers
14. The authentication server 14 may contact authorities
B in special circumstances to be described in detail
hereinafter.
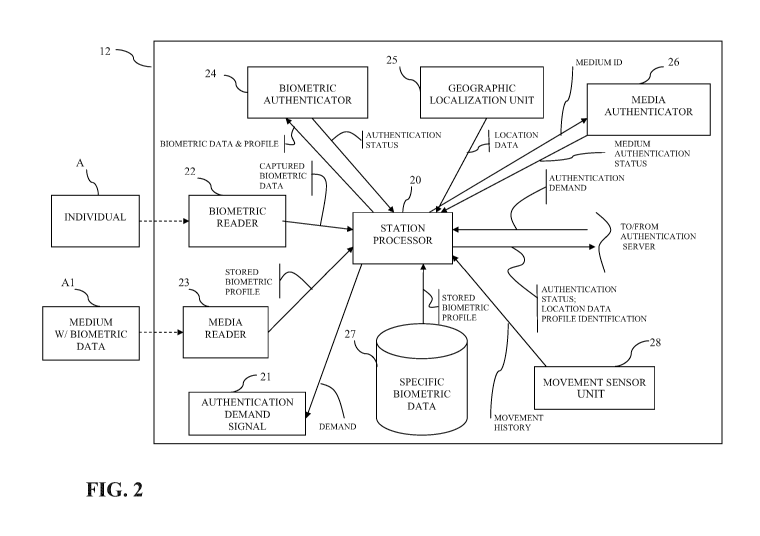
Referring to Fig. 2, one of the stations 12 is
illustrated in more detail. The station 12 is typically
a telephone-like unit that could use a wireless
connection like cellular phone or WiFi or could be wired
to a telecommunication system, such as the public-switch
-7-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
telephone network (hereinafter PSTN), cable, etc. Any
appropriate telecommunication system that can be used to
link stations 12 to the server 14 is considered. The
station 12 has a station processor 20 comprising a
processing unit (e.g., CPU of any appropriate type) to
perform various functions via different algorithms, some
of which are detailed hereinafter. The processor 20
comprises any appropriate telecommunications component
to transmit data to the authentication server 14.
The station 12 receives or generates an
authentication demand signal 21 so as to initiate an
authentication check (i.e., transaction, step, process)
with the individual A. The authentication demand signal
21 is driven by a schedule provided by the
authentication server 14 or programmed into the station
processor 20 specifically for individual A. When an
authentication demand signal 21 is initiated, the
individual A is notified that an authentication check
must take place, that he/she must report to the station
12. The signaling is typically performed by the station
12 via sound or light (e.g., a bell ring, an alarm,
visual cue).
In answering the demand for an authentication
check, the individual A must be biometrically recognized
by the station 12. Accordingly, the station 12 has a
biometric reader 22 that will capture biometric data
related to the individual A.
Any appropriate biometric reader 22 may be
used, for the biometric recognition of any selected
biometric characteristic of the individual A.
According to one embodiment, the vein pattern
presents one acceptable biometric characteristic to be
captured for the type of application of the present
disclosure.
Vein pattern recognition offers advantages
over other biometric techniques, including an ease of
-8-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
feature extraction - Veins provide large, robust,
relatively stable and hidden (to the naked eye)
biometric features. Infrared absorption patterns are
easily compared through the use of near-IR (infrared
red) which may be controlled to cause no injurious
effects on the human body. Vein pattern recognition also
provide spoof resistance - Vein patterns are not easily
observed, damaged, obscured or changed. They generally
do not exhibit latency properties; and they are quite
difficult to replicate. This makes vein patterns highly
resistant to spoofing. Moreover, vein-pattern
recognition systems commonly digitize and encrypt the
data in the templates.
Vein pattern recognition systems are also
accurate - Vein patterns have low false acceptance
levels (e.g., < 0.0001%) or low false reject levels
(e.g., < 0.01%), and failure-to-enroll (FTE) rates less
than 0.08% of most populations. Finger vein patterns may
be used in some cases to differentiate between identical
twins; such claim is currently shared by few biometric
characteristics, such as iris and retina recognition
modalities. Moisture, precipitation, minor dirt and cuts
do not impact the accuracy of vein-pattern recognition
systems.
Vein-pattern recognition systems are also
environmentally independent - Vein patterns are much
less susceptible to many external factors in the way
that fingerprinting, facial recognition, or iris
scanning can be. For example, indoor lighting has little
effect on vein authentication. Some vein-pattern
recognition systems can achieve authentication under
sunlight as well, rendering authentication possible
whether the individual is indoor or outdoor.
Moreover, vein-pattern recognition technology
can be privacy enhancing; it is fast (e.g., < 2
seconds), user intuitive regarding the placement of
-9-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
one's finger, hygienic, and is generally bereft of
cultural bias and criminal stigmas. Additionally,
automated audio and visual guidance during both
enrollment and authentication checks provide helpful
feedback.
Two examples of vein-pattern recognition
systems that could be used for the application of the
present disclosure are provided, for illustrative
purposes and shall not exclude other systems. One
example is the HitachiTM FingerVeinTM. This module is
highly accurate, and has a small portable form factor
that enables it to be mounted inside a variety of larger
devices. The FingerVeinTM readers are relatively small
and support a template of approximately 500 bytes, small
enough to support rapid processing and large enough to
support both 1:1 and 1:N matching.
Another example is the FujitsuTM Palm Secure TM
FujitsuTM provides a highly reliable biometric
authentication system based on palm vein pattern
recognition technology. PalmSecure"' features
authentication accuracy with low false rates, and the
non-intrusive and contactless reader device provides
ease of use with virtually no physiological restriction
for all users. PalmSecureT'M also allows contactless
authentication that is hygienic and non-invasive. An
authentication algorithm of the reader may produce a
high level of accuracy. In some circumstances, the
authentication algorithm of this device has shown a FAR
(false accept rate) of 0.00008%, a FRR (false reject
rate) of 0.01%, and may comprises a software development
kit for developers integrating this technology.
Other technologies may be used as well, using
other vein-pattern recognition technologies, or any
other recognition technology for other biometric
features.
-10-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
Referring to Fig. 2, according to an
embodiment, the individual A must carry a medium Al with
a personal biometric data. The medium Al is for instance
a non-writable smart card that is readable via the media
reader 23 of the station 12. Accordingly, the station
processor 20 receives both the captured biometric data
and the stored biometric profile, respectively from the
biometric reader 22 and the media reader 23. The medium
Al comprises a biometric profile that is stored thereon
when a profile is made for the individual A. For
instance, the medium Al is created by authorities when
defining the house arrest or the parole detainment
conditions of the individual A. Medium Al comprises all
security data to confirm that medium Al has not been
tampered. For instance, medium Al may comprise an
encrypted security code, whereby the media reader 23
will confirm the security code.
One type of smart card and reader technology
that can be used is contactless smart cards or tokens
using MifareTM technology. The cards or tokens will have
32k bits of storage to meet the demanding data storage
requirements (e.g., ISO 14443A standards). This
contactless smart card operates on a 13.56 MHz frequency
and also utilizes high-security encrypted data which is
mutually authenticated in communication between the card
and reader, providing an almost infinite number (many
trillions) of unique badge ID codes. With the
contactless smart or token using MifareTM technology,
there is very little wear and tear ensuring longer life.
These credentials also have a passive design which
requires no batteries or maintenance for the life of the
card.
Referring to Fig. 2, the captured biometric
data and the stored biometric profile, as respectively
read by the biometric reader 22 and the media reader 23,
are directed to a biometric authenticator 24. The
-11-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
biometric authenticator 24 is provided to determine
whether the captured biometric data and the stored
biometric profile match one another and thus are for the
targeted individual A. Accordingly, the authentication
status will confirm whether the individual A is the
targeted individual that is expected to check in at the
authentication station 12. As an alternative to the
authenticator 24, the captured biometric data may be
directed to the server 14 where the authentication will
be performed.
The station 12 may also comprise a geographic
localization unit 25. The geographic localization unit
25 provides location data to the station processor 20 to
indicate where the station 12 is geographically located.
According to one embodiment, the localization unit 25 is
a GPS unit providing location data via the use of
satellites. The GPS unit advantageously provides world-
wide coverage.
Yet in another embodiment, the localization
unit 25 may be the caller identification of a PSTN
number or the like that will indicate to the
authentication server 14 the number of the land line
used by the station 12 to provide the authentication
status.
Caller identification is provided via a
telephone service, available in analog and digital phone
systems and in some Voice over Internet Protocol
applications. Caller identification transmits a
caller's number to the called party's telephone
equipment during the ringing signal, or when the call is
being set up but before the call is answered. Where
available, caller ID can also provide a name associated
with the calling telephone number. The information made
available to the called party may be displayed on a
telephone's display or on a separately attached device.
-12-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
The station 12 may also carry a secondary
localization step which will be embedded in the station
12. As an example, of caller identification is used as a
primary localization step, the station 12 may carry an
embedded GPS which will operate on the battery system.
The last GPS coordinates would be transmitted with every
transmission of the station 12. This way, it will be
possible to confirm that the coordinates correspond to
the offender's residence the first time the station 12
is put into service and also ensure that there are no
changes in GPS coordinates during the whole period of
house arrest.
The station 12 may also comprise a media
authenticator 26 to confirm the identity of the medium
Al. The expected medium code may be stored beforehand in
a database 27 of the station 12 or sent by the
authentication server 14.
Accordingly, by way of the biometric
authenticator 24 and the media authenticator 26, the
station processor 20 may indicate the authentication
status to the authentication server 14. The
authentication status confirms whether the individual A
that has checked in the station 12 is the targeted
individual of the medium Al, after the comparison of the
captured biometric data and the stored biometric
profile. Moreover, the station processor 20 may indicate
via the authentication status whether the medium Al is
the expected medium.
In some circumstances, the individual A may
always check in to the same station 12. In such a case,
it is possible to program a biometric profile for the
targeted individual A in the biometric database 27.
Therefore, in such a case, the media reader 23 is not
required in that the database 27 provides the biometric
profile that will be compared to captured biometric data
by the biometric authenticator 24. On the other hand,
-13-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
the use of the medium Al with media reader 23 and
optionally with the media authenticator 26 is well
suited for instances in which many individuals A must be
authenticated at a same station 12. As yet another
alternative, the server 14 may send a biometric profile
to the stations 12 with each authentication demand.
In another embodiment, a movement sensor unit
28 is provided inside the station 12 to record the
movement history of the station 12. The movement sensor
unit 28 comprises a movement sensor(s) which may be
various any single micro-electromechanical sensor or
arrangements of micro-electromechanical sensors (such as
various types of gyroscopes, accelerometers or the like)
with a time-measuring or timing device or an internal
clock. The movement sensor unit 28 therefore records
and provides movement data (e.g., movement history) of
the station 12 to the station processor 20. The
movement history may be reset at each authentication
check, or may over a period of time. The movement
history may comprise magnitude values, the measured time
during which movements are detected, etc. Moreover, the
movement sensor unit 28 may perform some form of
processing to determine whether the values of the
movement history exceed some preset threshold(s) . For
instance, the preset thresholds may be one or more of
measured time, total magnitude of movements, average
magnitude of movement over time, etc. Accordingly, data
from the station 12 pertaining to the movement history
or an indication that the movement criteria have
exceeded thresholds may be directed to the
authentication server 14 to indicate any abnormal
movement of the station 12. For instance, detection of a
two-hour period of movement beyond a given magnitude may
indicate that the station 12 was displaced
geographically, whereby the individual may not be
respecting the conditions of house arrest or parole. The
-14-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
movement sensor 28 may be provided in addition to or as
an alternative to the geographic localization unit 25.
The detection of abnormal movement may cause the station
12 to request an intervention by authorities, or to send
an alarm signal to the server 14.
Referring now to Fig. 3, the authentication
server 14 is shown in greater detail. The server 14
typically has a server processor 40 as generally
illustrated, but the server processor 40 may consist of
the processing units of multiple servers to provide
suitable computational capacity to manage the network of
stations 12. However, for simplicity purposes, the
authentication server 14 is illustrated as having the
server processor 40.
A station driver 41 comprises data related to
authentication demands for the various individuals A and
thus for assigned stations 12. The station driver 41 may
be programmed with the profiles from authorities via the
authority network. Accordingly, the station driver 41
will direct an authentication demand to any specific
station 12, as scheduled. The station driver 41 may also
manage no-response actions: if the authentication demand
signal 21 is not answered by the individual in question,
the station driver 41 will repeat the demand according
to specific parameters in terms of lapsed time and
repetitions to provide the individual A with an
opportunity to respond. In the absence of a response
after the retry parameters have been respected, the
station driver 41 may direct a fault signal to
authorities to indicate a non-responsive authentication
demand signal.
A profile authenticator 42 is also part of the
server 14 and is used to approve the data received from
the stations 12, and determine whether it was the
targeted individual A that checked in at the
predetermined station 12. To perform this function, the
-15-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
profile authenticator 42 may access information from the
biometric authentication server (B.A.S.) file database
43, in which is stored the identifications of the
stations 12 along with the targeted individuals related
to each station. If the information received by the
profile authenticator 42 does not match the expected
data, the profile authenticator 42 may direct a fault
signal to the authorities to indicate that the
individual that has checked in is the wrong individual,
or is at an unexpected station 12.
Moreover, the profile authenticator 42 may
perform the biometric authentication centrally. In such
a case, the captured biometric data from the biometric
reader 22 (Fig. 2) is transferred to the server 14 for
centralized authentication. Thus, the profile
authenticator 42 receives the captured biometric data
and matches the data with a database of biometric
profiles, or seeks a corresponding profile using the
location data, or any identification data available
(e.g., code of a token or smart card entered at the
station 12 and accompanying the captured biometric
data).
A location comparator 44 is also provided to
verify that the location of the station 12 is within an
acceptable perimeter. The location comparator 44
receives data from the database 43 in which geographic
information is stored for each of the stations 12. As
mentioned previously, the geographic information may be
in the form of a PSTN number, global positioning data,
cellular network data or the like. The location
comparator 44 determines whether the actual location as
received from the station 12 falls within the acceptable
perimeter. If the location provided by the station 12 is
outside of the perimeter, authorities may be contacted
by a signal driven by the location comparator 44. The
location comparator 44 may also review the movement
-16-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
history from the movement sensor unit 28 (Fig. 2) to
determine whether measure movement values exceed
predetermined thresholds.
The biometric authentication system 10 and its
method of use are similar to the ankle monitor systems.
The system 10 and method add the capability to
authenticate that the actual person is in the allowed
range. At random or programmed timed intervals, the
station 12 will be triggered to have the individual A
authenticate him/herself and a communication through a
land line or a cellular network will relay positive or
negative information to the authentication server 14. If
the offender is not at the expected location at the
stipulated time or if the individual is not the targeted
individual, an authentication status will comprise this
information, whereby a fault signal may be relayed to
the supervising probation or parole officer. The
presence of a movement sensor unit 28 in the station 12
solves the problem of GPS signals being exposed to
interferences and being blocked temporarily, therefore
impacting the localization functions of the geographic
localization unit 25.
The customizable functions of the station 12
may be programmed from the server 14. The main server 14
will also receive all required information from the
public safety organization server such as name, expected
location, phone number, level of criticality of the
offender and requested verification frequency. The
server 14 will either receive the schedule for on-demand
authentication from the public safety organization or
will automatically generate the schedule depending on
criticality of the offender and type of house arrest
rules.
On a regular basis, each station 12 will
communicate with the server 14 and send a health check
(which may comprise localization information and
-17-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
movement history) . If a health check is not received as
expected, an alert message may be relayed to the
supervising probation or parole officer.
In an embodiment, the station 12 is a self-
contained, ruggedized unit. Similarly to a phone, the
station 12 may have one or two connectors depending on
the connection type used. If the used connection is not
wireless, one connector is needed for the phone line and
another for the main power (110-115 Vac). If a wireless
connection is used, only the main power connector may be
needed. It will also contain a battery which is sized to
ensure an autonomous operation without main power (e.g.,
8 hours).
The station 12 may also have LED lights of
different colours to provide initiation sequence and
success or failure of authentication feedback. A LED
light will be used to invite the offender to retry if
the first authentication was not successful. A
loudspeaker will provide request for authentication
ringing sound (like a phone) with volume control. As
another embodiment, the station 12 may have a digital
display indicating the name of the individual A that
must be authenticated, with other information (e.g., the
finger that must be authenticated). The station 12 may
therefore be used in an environment with more than one
individual A.
The offender may be required to enroll more
than one biometric feature, such as the finger vein
template for two fingers. For instance, the offender may
be requested to enroll one finger from each hand to
ensure that the authentication can be done even if one
finger is not `usable'. The enrollment will be done at
the public security office and biographic information
entered in the server database through a dedicated user
interface. A photograph of the individual A will be
taken to be kept in the database and be used on the
-18-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
medium Al. It is not necessary to have a picture on the
card. In fact, a token can be used without any specific
information. When the medium Al is a smart card, it may
be printed with the proper personalization, i.e.,
personal information on the surface of the card (front
and back) , and stored biometric data on the smart card
chip. Depending of the type of offender and
restrictions, different card design can be used. If a
token id used instead, only the reference number will be
kept in the database. The smart card or token will then
be activated and verified for proper operation on the
public-security installed station 12.
Once the medium Al and the dedicated and
configured station 12 are ready to be issued, all
reference information is entered in the database 43 of
the server 14, as well as an issue date and expected
return date. All necessary instructions are provided for
connection as well as rules and regulations.
When the offender has reached his detention
location, he/she will connect the station 12 to the main
power and, depending on the connection type, could need
to connect the station 12 to the phone line. The station
12 may be programmed to identify itself automatically
and a localization step is performed. In an embodiment,
both the caller identification and the last available
GPS coordinates will be used to ensure proper location.
The server 14 will then download the timed
authentication schedule dedicated to the offender and a
first authentication will be required for verification
of operation.
Therefore, referring to Fig.4, a method for
authenticating a presence of an individual at an
authentication station 12 is generally shown as 50.
According to 51, movement data is continuously
recorded using the least one micro-electromechanical
sensor in the authentication station 12. According to
-19-
CA 02792873 2012-10-11
WO 2012/083456 PCT/CA2011/050795
52, an authentication of an expected individual at the
authentication station 12 is demanded. According to 53,
biometric data is captured from an individual present at
the authentication station 12. According to 54, an
identity of the present individual authenticated by
comparing the captured biometric data to a biometric
file of the expected individual. According to 55, it is
determined from the recorded movement data if the
authentication station is at an expected location.
According to 56, a fault signal is outputted if the
identity is not of the expected individual and/or if the
authentication station is not at the expected location.
These steps may be performed in any appropriate order,
and intervening steps may be performed as well in
accordance with the operation of the authentication
system 10 described above.
-20-