Note: Descriptions are shown in the official language in which they were submitted.
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
SYSTEMS AND METHODS FOR ACCESSING OR MANAGING SECURED
STORAGE SPACE
FIELD OF TIRE INVENTION
This application relates to storage areas and, more specifically to systems
and methods for
accessing or otherwise managing these storage areas.
BACKGROUND OF THE INVENTION
Different approaches have been used through the years to control the access to
secured
spaces or areas. In one example, a locked door protects a secured space such
as a storage
locker. The lock that secures the door can be opened manually (e.g., by
manually turning
to a key and moving the handle) or, in some examples, automatically from a
remote location.
When locks are remotely opened, some determination is typically made that a
user is
allowed access to the secured space (e.g., the user enters some code that is
verified as
being authentic) and then the lock is actuated. After the lock is actuated,
the door is
opened and the user accesses the secured space.
is Different types of packages are delivered to recipients at various
locations. in one
example, packages are delivered to residents of apartment buildings. In this
situation, a
delivery person from a delivery service typically drops off a group of
packages at the front
desk of the apartment building where the packages are stored. When the
recipient of the
package returns to the apartment building, they can ask an attendant at the
front desk for
20 any packages that have been delivered during the day. The delivery
person may leave a
note at the recipient's door indicating that delivery was attempted and
reminding the
recipient to pick up the package.
This delivery approach suffers from various problems. To mention one
shortcoming, a
human attendant is required to receive and sign for the package. This can be
costly for
25 many apartment buildings to provide. This delivery approach also relies
on the presence
of the human attendant and/or the recipient to complete the delivery process.
More
specifically, the attendant has to retrieve the packages to give to the
recipient. The
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
packages are often unsorted and the attendant has to take time to find the
correct package
once the recipient arrives.
In addition, the recipient often has to periodically check to see if there are
any packages
waiting for them at the front desk. Further, the packages are often in an
unsecured
location which is susceptible to unauthorized entry and package theft. Package
theft is a
very common form of delivery theft, especially in locations where packages are
not
secured in a locked location until recipient pick-up. Records of package
delivery, if they
are maintained at all, are often hand-written and prone to error.
Consequently, efficient
management of package deliveries is difficult or impossible to achieve.
io Additionally, many different types of spaces need to be secured from
unauthorized entry.
For example, garages, rooms, and offices are often secured. However, there are
often
much smaller areas within these larger spaces that need protection. For
example, in a
hospital different cabinets within the same room or facility may secure
tissue, medicine,
and surgical instruments.
These smaller spaces (sometimes referred to as "micro-areas" or "micro-
spaces") often
need varying levels or different types of protection. For instance, different
personnel may
have differing levels of access to different spaces. In a hospital, for
instance, file clerks
may have access to some cabinets (e.g., cabinets containing hospital records)
while only
doctors and nurses have access to others (e.g., cabinets containing medicine
or human
tissue). Further, in some situations the environmental conditions at the
secured space
must be carefully monitored and controlled. In the present example of the
hospital, the
temperature of the cabinets holding the medicine or human tissue typically
needs to be
maintained at predetermined levels, or the contents of these cabinets may
become
destroyed or become otherwise un-usable.
Previous approaches have proved inadequate for both controlling access to and
managing
conditions of small, micro-areas. Although remotely controlling locks to
access rooms is
known, an integrated approach for controlling access to various areas
(including micro-
areas), managing the environments of these areas, and/or otherwise
controlling/managing
these areas has not been attempted, Since integrated approaches were never
attempted,
2
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
previous systems were complicated in design, costly to create, expensive to
operate, hard
to maintain, and burdensome to update or change.
It is an object of the present invention in its various aspects to overcome or
at least
substantially alleviate some or all of these problems or at least provide a
useful
alternative.
SUMMARY OF THE INVENTION
Accordingly, in a first aspect, this invention provides a method for
controlling access for a
storage enclosure, the method including the steps of:
- upon delivery of an item to the storage enclosure, transmitting an
access code to a
io recipient,
- accepting the access code when input by the recipient and
- permitting access to the storage enclosure.
The invention also provides a system for controlling access to a storage
enclosure secured
by a closure, the system including a processor configured to transmit an
access code to a
is recipient upon delivery into the enclosure of an item for the recipient,
recognize the access
code input by the recipient and allow the recipient access to the enclosure by
releasing the
closure.
Preferably, the storage enclosure is a locker which optionally forms part of
an array of
lockers, each having one or more walls and an opening defined by at least one
of the
20 walls, a closure for the opening and a fastener for the closure. In such
an array, the
enclosures may be, of the same size and shape or may differ in size and/or
shape.
The closure is preferably a flap or door fitting the opening, but may take
other forms. As
one non-limiting example, the closure may be a drawer.
The item may be anything capable of delivery. In the description below, the
item is often
25 referred to as a packaged asset, but is not necessary that the item is
actually packaged.
3
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
A user interface for input of the access code may be located on the front of
each enclosure
or there may be one user interface servicing a plurality of enclosures,
located, for
example, in the vicinity of the plurality of enclosures.
The user interface may take any suitable form but preferably is in the form of
a keypad or
computer touch screen. Once the access code is accepted, the interface will
prompt the
user as to the enclosure that is to be accessed. A visual indicator, if
present, may light up
or change colour or blink to help the user identify the correct enclosure. At
the same
time, a signal may be sent to unlock the closure and allow the user access
into the
enclosure.
to In preferred embodiments of the invention, access to one or more secured
areas is
controlled. These spaces may be relatively large spaces (e.g., moms,
factories, or
laboratories to mention a few examples) or micro-spaces (e.g., cabinets or
lockers within
.these large areas to name two examples). In the approaches described herein,
various
control and management functions associated with these areas may be integrated
together
is into one integrated server. For example, access control, event logging,
environmental
monitoring, and other functions may be integrated using a single server.
In many of these embodiments, access to one or more storage areas is
controlled. An
indication that a packaged asset is available for delivery to an intended
recipient, an
indication of a size of the asset, and an identity of the intended recipient
are received. An
20 available storage space is determined based at least in part upon the
size and/or weight of
the asset and the identity of the intended recipient. When a storage space is
determined to
be available for the packaged asset, an access code is transmitted to the
intended recipient
allowing the intended recipient to access the available storage space using
the access
code.
zs When determining the available storage space, a real-time determination
of the identity of
a storage space may be made. The available storage space may be a storage
space that is
not currently being used by the recipient. In other aspects, the available
storage space may
be a storage space that is currently being used by the recipient. In still
other aspects, the
available storage space may be a storage space that is being shared by the
recipient with
so another user.
4
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
The access code may be used to access the available storage space and retrieve
the
packaged asset from the storage space. A visual indicator may be deployed to
identify the
available storage space to the recipient so that the recipient can easily
locate the space. In
other aspects, once the access code actuates the locking apparatus, the
closure securing the
available storage space may be pushed to open the storage space to the
recipient.
Alternatively, the closure may be opened automatically (i.e., it may swing
outward) upon
receiving the access code. The closure may be any type of device or structure
used to
control access to a secured area. For example, the closure may be a swinging
door, gate,
garage door, or sliding door to mention a few examples.
lo In other examples, an electronic log of received packaged assets and
intended recipients
may be maintained. In some aspects, the log is accessible to a system
administrator at
substantially all times. This log may also maintain details of internal
factors within the
storage space, such as weight, temperature, and other environmental factors.
The access code may be transmitted by the recipient in a variety of different
ways. In one
is example, the access code is transmitted to the intended recipient via
email. In another
example, the access code is transmitted to the recipient over a wireless
connection. In
another example, the access code may be transmitted on a set or possibly
delayed schedule
depending upon the user's needs. Access codes may also be encrypted upon
transmittal.
Other examples of transmission approaches are possible,
20 The access code may be a number, letters, a combination, other syrnboli,
or any other
suitable identifier. In one embodiment, the access code is a bar code which
can be
transmitted to the recipient's cell hone, for example and read by a bar code
reader on the
system. Other forms of access code are possible.
In an especially preferred embodiment, the access code is a cell phone number
of the
25 recipient. In this embodiment, upon delivery of an item the deliverer
may contact the cell
phone in order to transmit the access code or the system itself may contact
the cell phone.
In either case, the system stores the cell phone number as the access code.
Contact may be
by sms or voice message, for example.
5
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
When the recipient receives the contact, the recipient is notified that the
item has been
delivered. The cell phone message may include the address of the enclosure if
this is not
already known to the recipient. The recipient approaches the enclosure (which
may be part
of an array) and calls a telephone number of the system from the recipient's
cell phone.
s This system number is preferably clearly displayed on the enclosure or
nearby, for
example, on a banner at the top of the array. The system is configured to
recognize the
recipient's cell phone by its telephone number (access code) and allow the
recipient
access to the enclosure. For security, direct contact from the recipient's
cell phone may
be required,
to The method and system of the invention may be embodied in a relatively
simple way
combined with social networking, such as that facilitated by Facebook. For
example, a
person may wish to provide a gift for one or more friends, using an array of
enclosures
according to the invention. The person may deposit the gift or gifts in one or
more
enclosures and transmit an access code to each of the friends via Facebook.
Each friend
is then accesses the enclosure and the gift using the assigned access code.
This embodiment
may be particularly effective if the access code is the cell phone number of
each friend, as
described above.
In some examples, the recipient may pay for the storage space. For example,
the recipient
may pay a predetermined cost for a predetermined time period allowing them
access to the
20 space during that time period, pay higher costs for certain time
periods, or pay higher
costs for additional features (e.g., special indicator arrangements,
additional electronic
reminders, and so forth).
In some embodiments, the storage space may be mobile and can be moved from one
location to another easily. The storage space may be on wheels or other
suitable means to
25 move the storage space. Other examples of approaches the provide
mobility are possible.
In a second aspect, the invention provides a method for managing secured
storage spaces,
including the steps of monitoring the spaces via sensors, receiving a request
from a user
to access one of the secured spaces, determining whether to permit access to
the space as
requested by the user and allowing or refusing access to the space.
6
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
The invention in this second aspect may include the further step of logging
activity with
respect to the spaces.
The invention also includes a system for managing secured storage spaces,
which enable
the method of the second aspect of the invention.
hl some embodiments, the system for controlling access to or managing one or
more
storage spaces includes an interface and a processor. The interface has an
input and an
output. The interface is configured to receive at the input an indication that
a packaged
asset is available for delivery to the intended recipient, an indication of
the size (e.g.,
dimensions or general size) of the packaged asset, and the identity of the
intended
to recipient.
The processor is coupled to the interface and is configured to determine an
available
storage space based at least in part upon the asset size and the identity of
the intended
recipient. The processor is further configured, when a storage space is
determined to be
available for, the packaged asset, to transmit an access code to the intended
recipient at the
is output of the interface allowing the intended recipient to access the
available storage
space using the access code.
As mentioned, the available storage space may be in one of several usage
states with
respect to the recipient. For example, the available space may not be
currently used by the
recipient, may be currently used by the recipient, or may be currently shared
by the
20 recipient with another user.
In other aspects, the processor is further configured to maintain a log of
received
packaged assets and intended recipients in a memory storage device. In some
examples,
the log in the memory storage device is accessible to a system administrator
at
substantially all times.
25 In some approaches, the output is coupled to an Internet connection and
the access code is
transmitted to the recipient in an email via the Internet connection. In still
other
examples, the processor is configured to receive a payment from the recipient
for use of
the available storage space via the input of the interface.
7
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
In still others of these embodiments, a system for controlling access to one
or more
storage spaces includes a local network and a plurality of locking
arrangements
communicatively coupled to the local network. Each of the plurality of locking
arrangements secures a storage space. The system also includes a data entry
device that is
coupled to the local network; a wide area network that is coupled to the local
network;
and a system controller that is coupled to the wide area network.
The data entry device is configured to receive an indication that a packaged
asset is
available for delivery to an intended recipient, an indication of the asset
size, and the
identity of the intended recipient. The system controller is configured to
determine an
to available storage space based at least in part upon the asset size and
the identity of the
intended recipient received from the data entry device via the wide area
network. The
system controller is further configured, when a storage space is determined to
be available
for the packaged asset, to transmit an access code to the intended recipient
via the wide
area network. The intended recipient can use the access code to open the
locking
arrangement that secures the available storage space and obtain the packaged
asset.
The wide area network may be one or more networks such as the Internet, a
cellular
wireless network, and the plain old telephone system (POTS). Other examples of
networks and combinations of networks are possible,
The local network may be a network such as a campus-wide network; a network
covering
a building or portions thereof; or a network covering an office or portions
thereof. Other
examples are possible. In this respect and as used herein, "local network"
refers to a
network (or combination of networks) that are limited in geographic scope to a
local area
such as a building, apartment complex, campus, military base, or the like. A
local
network provides less geographic coverage than a wide area network (that, for
example,
covers states or countries) such as the Internet.
In some aspects, the available storage space is secured with a first locking
arrangement
disposed at a first end of the storage space and a second locking arrangement
disposed at a
second end of the storage space, The access code unlocks one of the first
locking
arrangement or the second locking arrangement.
8
The data entry device may be a device such as a touch screen device, a
personal digital assistant, a
cellular phone. or a personal computer. Other examples of data entry devices
are possible.
The management of micro-areas may be provided. in some embodiments, these
approaches can
provide protection for micro-areas from both unauthorized human interaction
and adverse
environmental conditions (e.g., temperature variations, pressure variations,
and so forth). Monitoring
and reporting of activities (both human-related and environmental related) may
also be provided.
The integrated approaches to secured space management described herein
frequently use a single
hardware and/or software platform to manage/control the one or more secured
areas. Since a single
hardware/software platform is used (as opposed to previous approaches where
unconnected and
disparate elements were frequently deployed), the design of the system is
simple and stream-lined,
operation is simple. and access to system elements (e.g.. software modules) by
users is easy. Further.
maintenance can easily be accomplished and updates to the system are easy to
achieve. In this regard,
the single integrated approach allows modularity to be accomplished. That is.
new software modules
can easily be loaded into the server, updates to existing modules can be
easily and quickly made, and
problems with individual modules can be easily identified and corrected.
Different modules can be
used in different environments allowing custom solutions to be easily
configured and deployed.
Further, since the server integrates various functions, traceability of
problems. messages, and activity
is easily provided. Additionally, a much more granular control scheme is
implemented providing
control of micro-areas. Because of these advantages, the overall cost of the
system is significantly
reduced compared to previous approaches. It will be appreciated that these are
only some of the
advantages of the present approaches and that other advantages may also exist.
According to one aspect of the invention, there is provided a method for
securely delivering a
packaged asset through an apparatus haying an interface and processor. the
method comprising:
providing a plurality of storage spaces, each storage space having a usage
status of occupied or
unoccupied:
the interface receives data, the data including an indication that the
packaged asset is available for
delivery to an intended recipient, an indication of a size of the asset. and
an identity of the intended
recipient:
9
CA 2811317 2017-07-25
the processor processing the data to identify in real time an available
storage space from the plurality
of storage spaces, based at least in part upon the size of the packaged asset
and the identity of the
intended recipient;
the processor associating the available storage space with the intended
recipient to determine the
usage status;
the processor. transmitting an access code to the intended recipient, for
accessing the available storage
space: and
the processor receiving the access code and allowing the intended recipient to
access the available
storage space. wherein the available storage space includes an occupied
storage space capable of
housing the packaged asset.
According to another aspect of the invention, there is provided an apparatus
for controlling access to a
plurality of storage spaces. each storage space having a respective locking
arrangement
communicatively coupled to a network hub, the apparatus comprising:
an interface configured to receive an indication that a packaged asset is
available for delivery to an
intended recipient, an indication of size of the packaged asset. and an
identity of the intended
recipient of the packaged asset; and
a processor coupled to the interface, the processor configured to maintain a
log of received packaged
assets and intended recipients in a memory storage device to generate usage
status of occupied or
unoccupied for each storage space, the processor further configured to
identify in real time an
available storage space from the plurality of storage spaces, based at least
in part on the usage status
of the storage space. the size of the packaged asset and the identity of the
intended recipient, the
processor further configured to associate the available, storage space with an
access code and transmit
the access code to the intended recipient allowing the intended recipient to
access the available
storage space using the access code,
wherein the available storage space includes an occupied storage space capable
of housing the
packaged asset.
According to a further aspect of the invention, there is provided a system for
securely delivering a
packaged asset, the system comprising:
9a
CA 2811317 2017-07-25
a network hub:
a plurality of storage spaces. each storage space having a respective locking
arrangement
communicatively coupled to the network huh:
an asset manager in communication with the network huh;
a network for communication between the asset manager and an intended
recipient:
an interface having an input and an output. the interface in communication
with the asset manager, the
interface configured at the input to receive data including, an indication
that the packaged asset is
available for delivery to the intended recipient, identity of the intended
recipient of the packaged
asset. and an indication of size of the packaged asset;
the asset manager configured to process the data to identify in real time an
available storage space
from the plurality of storage spaces, based at least in part on the size of
the packaged asset and the
identity of the intended recipient:
the asset manager further configured to associate the available storage space
with an access code and
transmitting the access code at the output of the interface via the network to
the intended recipient. the
access code configured to open the locking arrangement associated with the
available storage space;
wherein the available storage space includes a storage space having the usage
state used by the
intended recipient or shared by the intended recipient with another user and
is capable of housing the
packaged asset.
BRIEF DESCRIPTION OF THE DRAWINGS
The invention will now be described with reference to preferred embodiments
which are not intended
to be limiting on the scope of the invention. In the drawings:
9b
CA 2811317 2017-07-25
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
FIG. 1 is a block diagram showing a system for packaged asset delivery
according
to various embodiments of the present invention;
FIG. 2 is a flowchart showing an approach for controlling access to a secured
area
according to various embodiments of the present invention;
FIG. 3 is a block diagram showing an apparatus for controlling access to a
secured
area according to various embodiments of the present invention;
FIG. 4 is a block diagram showing a system for controlling access to one or
more
secured areas according to various embodiments of the present invention;
FIGs. 5A-D are flowcharts showing an approach for controlling access to one or
more secured areas according to various embodiments of the present invention;
FIG. 6 shows one example of a series of display screens displayed during
package
drop off according to various embodiments of the present invention;
FIG. 7 shows one example of a series of display screens displayed during
package
pick-up according to various embodiments of the present invention;
FIG, 8 is a block diagram of a system for managing one or more secured spaces
according to various embodiments of the present invention;
FIG. 9 is a block diagram of another example of a system for managing one or
more secured spaces according to various embodiments of the present invention;
FIG. 10 is a block diagram of server architecture for managing one or more
secured spaces according to various embodiments of the present invention;
FIG. 11 is a block diagram of server architecture for managing one or more
secured spaces according to various embodiments of the present invention;
FIG. 12 comprises a message flow diagram of one example of a message flow in a
bridge registration process according to various embodiments of the present
invention;
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
FIG. 13 comprises a message flow diagram of one example of a message flow for
a bridge discovery process according to various embodiments of the present
invention;
FIG. 14 comprises a message flow diagram of one example of a message flow for
a opening process a locking device according to various embodiments of the
present invention;
FIG. 15 comprises a message flow diagram of one example of message flow for a
locking process according to various embodiments of the present invention;
FIG. 16 comprises a message flow diagram of one example of message flow for an
io unlocking process according to various embodiments of the present
invention;
FIG. 17 comprises a message flow diagram of one example of message flow for an
unlocking process using a card reader according to various embodiments of the
present invention; and
FIG. 18 comprises flowcharts of example server logic flows according to
various
embodiments of the present invention.
Skilled artisans will appreciate that elements in the figures are illustrated
for simplicity
and clarity and have not necessarily been drawn to scale. For example, the
dimensions
and/or relative positioning of some of the elements in the figures may be
exaggerated
relative to other elements to help to improve understanding of various
embodiments of the
present invention. Also, common but well-understood elements that are useful
or
necessary in a commercially feasible embodiment are often not depicted in
order to
facilitate a less obstructed view of these various embodiments of the present
invention. It
= will further be appreciated that certain actions and/or steps may be
described or depicted
in a particular order of occurrence while those skilled in the art will
understand that such
specificity with respect to sequence is not actually required. It will also be
understood
that the terms and expressions used herein have the ordinary meaning as is
accorded to
such terms and expressions with respect to their corresponding respective
areas of inquiry
and study except where specific meanings have otherwise been set forth herein.
11
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
DETAILED DESCRIPTION OF THE DRAWINGS
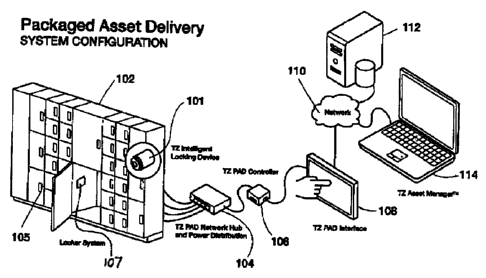
Referring to FIG. 1, one example of a system for packaged asset delivery is
described.
The system includes a locker system 102, a network hub 104, an interface
controller 106,
a data entry device 108, a network 110, memory storage 112, and an asset
manager 114.
s The locker system 102 is any type of storage arrangement where one or
more storage
spaces are secured by one or more locking arrangements. Each of the lockers
has a
locking arrangement (e.g., an electronic lock) that is communicatively coupled
to the hub
104. The locking arrangements are actuated by reception of an access code that
opens/releases the locking arrangement so as to allow a barrier securing the
storage space
io to be opened thereby allowing access to the storage space. For
simplicity, only one
locking arrangement 105 is identified in FIG. I although it will be
appreciated that each
locker has a locking arrangement. It will be further appreciated that the
locking
arrangement 105 may be coupled to the hub 104 by any type of connection such
as wired
connection, wireless connection, and optical connection to mention a few
examples. The
is lockers may have one or more environmental control devices 107 that
control, adjust, or
otherwise affect one or more environmental or physical conditions within the
locker. For
example, the environmental control device 107 may adjust lighting,
temperature, pressure,
or any other condition within the locker. In this respect, the environmental
control device
107 may be a fan, light, air conditioner, freezer unit, or heating unit. Other
examples are
zo possible. Control of the environmental control device 107 may be
accomplished from the
asset manager 114 or the interface 108. For example, conditions within the
locker may be
monitored (e.g., via sensors) and commands may be issued from the asset
manager 114 or
the interface 108 to operate the environmental control device 107 and maintain
various
conditions within the locker within predetermined limits.
25 The network hub 104 is any type of network hub that connects the many
connections from
the locker system 102 to a single output connection coupled to the interface
controller
106. The hub 104 may also provide for power distribution to the locker system
102.
The interface controller 106 is an interface connection that converts signals
from one
communication protocol to another. In one example, the controller 106 converts
signals
12
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
between a USB-typc protocol and the RS-485 protocol. Other communication
protocols
and other types of conversions can also be used.
The data entry device 108 is any type of data entry device. The data entry
device may be a
device such as a touch screen device, a personal digital assistant, a cellular
phone, and a
personal computer. Other examples of data entry devices are possible. In the
example of
FIG. 1, the data entry device is a touch screen device.
The network 110 is any type of computer network including any type of local
network,
micro network, or wide area network. Combinations of these networks may also
be used.
If the network 110 is a wide area network, the wide area network may be one or
more
networks such as the Internet, a cellular wireless network, or the plain old
telephone
system (POTS). Other examples of wide area networks are possible.
If the network 110 is a local area network, the local network may be a network
such as a
campus-wide network; a network covering a building or portions thereof; or a
network
covering an office or portions thereof, Other examples of local networks are
possible.
The memory storage 112 may be any type of memory storage device used to store
information regarding the locker storage 102. For example, logs describing
assets that
were delivered and/or intended recipients may be stored in the memory storage
112.
The asset manager 114 may be any combination of hardware/software that manages
information related to the locker system 102 and the available storage spaces
in the locker
system 102. It may generate reports of available space, usage, and so forth.
These reports
may be stored in the memory storage 112 or communicated to an administrator
(or others)
for viewing via the network 110.
In one example of the operation of the system of FIG. 1, a delivery person
delivers a
packaged asset and enters an indication that a packaged asset is available for
delivery to
an intended recipient at the device 108. Alternatively, the delivery person
may provide
the packaged asset to another person (e.g,, an attendant at the front desk of
an apartment
complex) and that person may perform the packaged asset delivery actions
described
13
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
below. The packaged asset as described herein may be a package (large, small,
medium,
oversized), an envelope, or any other type of package/enclosure.
The delivery person also enters an indication of a size of the asset and an
identity of the
intended recipient at the device 108. The size may be a general size (e.g.,
large, small,
medium, oversized) or may be one or more dimensions (or a weight). The device
108
determines an available storage space in the lockers 102 based at least in
part upon the
size of the asset and the identity of the intended recipient. When a storage
space is
determined to be available for the packaged asset, an access code is
transmitted from the
= = device 108 to the intended recipient via the network 110 allowing the
intended recipient
to to access the available storage space using the access code. The access
code, in one
example, is a randomly generated number. The locking arrangement 105 of the
locker
system 112 may be programmed to accept this access code and allow this access
code to
open the locking arrangement 105. The asset manager 114 may create and
maintain a log
of transactions and store these in memory storage 112.
To retrieve the packaged asset, the recipient may go to the device 108, enter
the code, and
thereby access the packaged asset in the assigned locker. The access code may
actuate a
locking arrangement that allows or causes a barrier (e.g., a locker door) to
be opened. The
code entered by the recipient may be compared to a list of acceptable codes at
the device
108. An indicator 101 may alert the user as to the correct locker. The
indicator may be an
zo LED in one example. There may be an indicator for a group of lockers, or
one indicator
for each locker. The color of the indicator may change depending upon the
state of the
secured space. For example, one color may be used when the locker is closed,
another
color (or another action such as the indicator flashing) when the recipient
accesses the
space, and still another color when the secured space is opened.
In some examples, the available storage space in the lockers 102 is secured
with a first
locking arrangement disposed at a first end of the storage space and a second
locking
arrangement disposed at a second end of the storage space. The access code
unlocks one
of the first locking arrangement or the second locking arrangement. This
allows a
delivery person to use one door to access the storage space and the recipient
to use a
14
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
second door to access the same space. Advantageously, these doors may be
disposed
opposite to each other.
The door of the locker 102 securing the available storage space may be pushed
once the
code allows access. This prevents the door flying open and causing potential
injury to the
s recipient. Alternatively, the door may be opened automatically upon
receiving the access
code.
Referring now to FIG. 2, one example of an approach for controlling access to
a secured
area is described. At step 202, an indication that a packaged asset is
available for delivery
to an intended recipient is received. For example, a delivery person may enter
this via a
to touch screen or some other data entry device. In another example, at
least some of this
information may be scanned in (e.g., scanning an RFID tag). At step 204, an
indication of
a size of the asset is received. As with step 202, a delivery person may enter
this
information via a touch screen or some other data entry device. At step 206,
an identity of
the intended recipient is received. In another example, at least some of this
information
15 may be scanned in (e.g., scanning an RFID tag). As with steps 202 and
204, a delivery
person may enter this information via a touch screen or some other data entry
device. In
another example, at least some of this information may be scanned in (e.g.,
scanning an
RFID tag).
At step 208, an available storage space is determined based at least in part
upon the size of
zo the asset and the identity of the intended recipient. For instance, a
determination may be
made if a space is available and the identity of that space. If there is no
available space, at
step 210 a report/message is sent to the recipient and/or the system
administrator. At step
212, when a storage space is determined to be available for the packaged
asset, an access
code is transmitted to the intended recipient allowing the intended recipient
to access the
25 available storage space using the access code.
When determining the available storage space at step 208, a real-time
determination of the
identity of a storage space may be made. The available storage space may be a
storage
space that is not currently being used by the recipient. In other aspects, the
available
storage space may be a storage space that is currently being used by the
recipient. In still
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
other aspects, an available storage space may be a storage space that is being
shared by the
recipient with another user.
= The access code may be used to access the available storage space and
retrieve the
packaged asset from the available storage space. A visual indicator (e.g.,
LED) may be
deployed to identify the available storage space to the recipient. This
indicator may also
be used during the package delivery process to indicate to the agent the
location of the
storage space where to store the packaged asset.
In other examples, an electronic log of received packaged assets and intended
recipients
may be maintained. In some of these examples, the log is accessible to a
system
to administrator at substantially all times.
The access code may be transmitted to the recipient at step 212 in a variety
of different
Ways. hi one example, the access code is transmitted to the intended recipient
via email
across the Internet. In another example, the access code may be sent to a
cellular phone or
personal digital assistant of the user via a Wireless network. Other examples
of delivery
approaches are possible.
In some examples, the recipient may pay for the storage space. For example,
the recipient
may the same cost for a predetermined time period, pay higher fees for certain
time
periods (e.g., for use during the Christmas holidays to mention one example),
or pay
higher fees for additional features (e.g., a higher number/frequency of
reminder emiails).
zo Referring now to FIG. 3, one example of an apparatus 300 for controlling
access to a
secured area is described. The apparatus 300 includes an interface 302 and a
processor
304. 'The interface 302 has an input 301 and an output 303 and is configured
to receive a
the input 301 an indication 306 that a packaged asset is available for
delivery to an
intended recipient, an indication 308 of asset size, and an identity 310 of
the intended
recipient.
The processor 304 is coupled to the interface 302 and is configured to
determine an
available storage space based at least in part upon the asset size 308 and the
identity of the
intended recipient 310. The processor 304 is further configured, when a
storage space is
determined to be available for the packaged asset, to transmit an access code
312 to the
16
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
intended recipient at the output 303 of the interface 302 allowing the
intended recipient to
access the available storage space using the access code 312.
As mentioned, the available storage space may be a space that is not currently
being used
by the recipient, currently being used by the recipient, or currently being
shared by the
recipient with another. Other examples and combinations of storage usage
patterns are
possible.
In other aspects, the processor 304 is further configured to maintain a log
311 of received
packaged assets and the intended recipients in a memory storage device 314. In
some
examples, the log 311 in the memory storage device 314 is accessible to a
system
o administrator at substantially all times.
In some approaches, the output 303 is coupled to an Internet connection and
the access
code 312 is transmitted to the recipient in an email via the Internet
connection. In still
other examples, the processor 304 is further configured to receive a Payment
from the
recipient for use of the available storage space via the input 301 of the
interface 302.
The apparatus includes a touch screen 315 that is coupled to the processor
304. The touch
screen 315 allows a delivery person (or attendant) to enter delivery
information (e.g., that
a package is available, the package size, and/or the intended recipient). The
screen 315
also provides an interface for the package recipient to enter the access code
the retrieve =
the packaged asset. The memory 314 may also store a list of possible
recipients that can
be displayed on the screen 315. The input 301 and output 303 may be coupled to
the
locking arrangements and to other networks/network elements.
It will be understood that the apparatus 300 may be a wide variety of devices.
For
example, the apparatus 300 may be a touch screen device. In other examples,
the
apparatus 300 may be a personal computer and the screen 315 may be disposed at
a
personal computer.
It will be appreciated that the elements shown in FIG. 3 may he housed in a
single and
compact housing unit that can be located near a storage center (e.g., a locker
arrangement). This allows the apparatus 302 to be disposed in compact areas.
However,
17
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
some or all of the elements may be moved to other and separate locations
(e.g., to a
system controller that controls locking arrangements via a wide area network).
Referring now to FIG. 4, one example of a system for controlling access to one
or more
secured areas is described. The system 400 includes a first local network 402
and a
plurality of locking arrangements (e.g., electronic locks) at lockers 406.
These locking
arrangements are communicatively coupled to the first local network 402. Each
of the
plurality of locking arrangements 406 secures a storage space. A data entry
device (e.g.,
touch screen) 404 is coupled to the local network 402. A wide area network 422
is
coupled to the local network 402 and a system controller 424 is coupled to the
wide area
io network 422. The local network 402, touch screen 404 and lockers 406 may be
disposed
in a first building 408.
A second local network 410 is coupled to locking arrangements at lockers 414,
locking
arrangements at storage facility 416, locking arrangements at storage facility
418, and a
data entry device 421. Each of the lockers 414, storage facility 416, and
storage facility
418 includes individual secured storageareas (e.g., lockers) that are secured
by one or
more of the respective locking arrangements. The data entry device (e.g., a
touch screen
device) 421 is coupled to the local network 410, The local network 410, data
entry device
421, lockers 414, storage facility 416, and storage facility 418 may be in a
second building
412.
29 The data entry devices 404 and 421 are configured to receive an
indication that a
packaged asset is available for delivery to an intended recipient, an
indication of asset
size, and an identity of the intended recipient. For example, a delivery
person or attendant
may enter this information via the particular data entry device 404 or 421.
The system
controller 424 is configured to receive this information (that is transmitted
to the
controller 424 via the local area networks 402 or 410, and the wide area
network 422) and
determine an available storage space based at least in part upon the asset
size and the
identity of the intended recipient.
The system controller 424 is further configured, when a storage space is
determined to be
available for the packaged asset, to transmit an access code to the intended
recipient via
the wide area network 422. For example, the access code may be emailed to the
intended
18
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
recipient, or sent to the recipient's cellular phone or personal digital
assistant. The
intended recipient can use the access code to open the locking arrangement
securing the
available storage space and obtain the packaged asset. More specifically, the
recipient
may go to the data entry device 404 or 421 and enter the code.
The wide area network 422 may be one or more networks such as the Internet, a
cellular
wireless network, or the plain old telephone system (POTS). Other examples and
combinations of wide area networks are possible.
The local networks 402 or 410 may be networks such as campus-wide networks,
networks
covering a building or portions thereof or networks covering an office or
portions thereof.
to Other examples of local networks are possible.
In some aspects, the available storage space is secured with a first locking
arrangement
disposed at a first end of the storage space and a second locking arrangement
disposed at a
second end of the storage space. The access cede unlocks one of the first
locking
arrangement or the second locking arrangement.
The data entry devices 404 or 421 may be a device such as a touch screen
device, a
personal digital assistant, a cellular phone, and a personal computer. Other
examples of
data entry devices are possible.
It will be understood that some or all of the functions of the controller 424
may be moved
to the data entry device 404 or 421. For example, the code-generating function
in the
controller 424 may be moved to the touch screen 404 or 421. in some examples,
all
functions are moved and the system controller need not be used. In other
aspects, the data
entry devices 404 and/or 421 may he moved to he coupled to the locking
arrangements
without being coupled to an intervening local network.
A log of recipients, drop off times, and recipients may be maintained at a
memory 426
that is coupled to the controller 424. Other types of information and other
types of reports
may be generated at the system controller 424 and stored at the memory 426.
Referring now to FIGs. 5A-D one example of an approach for controlling access
to one or
more secured areas is described. It will be appreciated that this example
illustrates
19
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
approaches particularly useful for an apartment building with a locker system.
It will also
be appreciated that the steps described for this particular example may be
changed to suit
the needs of the particular user and/or system. It will also be understood
that the steps be
applied, changed, or otherwise modified to suit the particular needs of other
deployment
= environments or locations.
The process begins when a delivery truck (or other vehicle) delivers packages
to the front
desk of the apartment complex at step 502. An attendant at the front desk
signs once for
all packages.' Alternatively, the attendant may be omitted and the delivery
person can
perform the delivery steps.
to At step 504, if the package is too large or damaged, the attendant at
the front desk can
reject the package and return the package to the delivery person. In this
case, the
packages can be returned immediately or at a later time.
At step 506, the front desk attendant acts as a delivery agent and moves the
packages to
the mail room (or other location where the lockers are physically located). At
step 508,
is the delivery agent drops off the packages at the locker system. There
need be no
dedicated employee at the locker system to receive the packages. However, all
employees
may act as an agent for drop off as needed.
At step 510, the package drop-off process begins. The agent may begin at
either step 512
or 514.
20 At step 512, an agent "badges-in" with an RFLD card. At this step, a
card presented by the
agent is read by an RF1D reader device and a determination is made if the
agent is a
legitimate agent. Control continues at step 516, where it is determined if the
RFID badge
is accepted. If the answer at step 516 affirmative, then execution continues
at step 522. If
the answer at step 516 negative, execution continues at step 514.
25 At step 514, the "agent" option is selected at the keypad. For example,
the agent presses
an icon on the touch screen to provide this option. At step 518, the agent
enters login
(e.g., user name information) and a password and it is determined if the login
information
has been accepted. If the answer is negative at step 518, control returns to
step 514. If the
answer is affirmative at step 518, control continues at step 520 where it is
determined if
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
the password is accepted. If the answer at step 520 is negative, execution
continues at
step 514, If the answer at step 520 is affirmative, execution continues at
step 522 where
the agent selects options for "drop off," "packages" or "log off." If "log-
off' is selected,
then control returns to step 514. Otherwise control continues at step 524.
At step 524, the "drop-off' option is selected and one or more of the
apartment number,
first name, and second name are filled in at the touch screen by the agent.
Two paths, one
beginning at step 526 and the other with step 528, may be followed.
If the path beginning at step 526 is followed, the agent enters the apartment
number. In
many of these examples, the apartment number is alphanumeric. A user list may
also auto
filter as the apartment number is entered (such that as particular characters
are entered,
'entries with those characters are displayed). At step 530, the apartment
number is selected
(or step 532 is followed where the user is selected from a list). At step 534,
the primary
resident of the apartment may be selected automatically. Execution continues
at step 538.
If the path beginning at step 528 is followed, the agent enters the
recipient's name. Auto-
filtering may also occur at this step. At step 532, the user may be selected
from the user
. list. At step 536, it is determined if the user is on the list, If the
answer is negative,
control returns to step 530. If the answer is affirmative, control. continues
at step 538.
At step 538, the package size is selected by the agent. Some package size
options include
envelope, small, medium, large or oversize. Alternatively, dimensions and/or
weights can
zo be entered. Other options are possible.
lithe package is "oversize," at step 540 package is placed somewhere besides
the lockers.
At step 541, the screen flow jumps to show confirm drop-off that is high-
lighted. Control
continues at step 564,
If the package is not "oversize," at step 542, it is determined if the
resident already has a
package of the same size or larger that has been recorded by the system as
being stored in
the lockers. If the answer is negative, at step 548, it is determined if there
are any empty
lockers. At step 552, an empty locker is opened and control continues at step
554.
21
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
If the answer at step 542 is affirmative, at step 544 it is determined if the
locker is full. If
the answer is negative, execution continues at step 550 and if the answer is
affirmative,
control continues at step 546.
At step 550, the recipient's unfilled locker is opened and the package can be
placed there
by the agent. Execution continues at step 554.
At step 546, it is determined if the resident has another assigned locker that
is not full, If
the answer is negative, execution continues with step 548. If the answer at
step 546 is
affirmative, execution continues at step 550.
At step 554, it is determined if the package fits in the locker. In this
respect, the agent
io may attempt to fit the package into the locker. If the answer is
negative at step 554, at
step 556 the agent closes the door of the locker without placing the package
in the locker.
At step 558, the agent may be provided the option to set the locker state as
"full." At step
560, the screen may display "open next locker." Execution then continues at
step 542 as
described above.
If the answer at step 554 is affirmative, at step 562 the agent closes the
locker with the
package placed in the locker. At step 564, a "Confirm drop off' is displayed
on the
screen. The expiry time for all packages in this locker for this resident is
reset to begin
expiring from when the latest package that has been dropped off.
At step 566, it is determined if there is another package to drop off. If the
answer is
zo affirmative, control returns to step 538. If the answer is negative, at
step 568 an email
notification (or other type of notification) is sent to the resident. The drop-
off process is
now complete.
The retrieval process is now described. At step 570, the resident enters the
code that they
have been provided. At step 571, it is determined if the code is accepted.
This
acceptance may be accomplished by comparing the code to a set of authorized
codes
(stored at the touch screen device in one example). If the answer is negative,
control
continues at step 570 and execution continues as has been described above.
22
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
lithe answer at step 571 is affirmative, then at step 572 the screen shows
instructions for
the user to follow, for example, to identify a particular locker (or lockers)
associated with
the code when the user has been assigned multiple lockers.
At step 573, it is determined if the package is "oversize." If the answer is
affirmative, at
step 583 the recipient goes to the agent and at step 582 the office hours of
the agent may
be determined by the recipient. At step 582, the agent gives the "oversize"
package to the
recipient and at step 583 agent clears the package from the system.
If not an "oversize" package, at step 574 the locker indicator begins to flash
orange (or
some other appropriaticolor). The lock securing the locker is set to push-to-
release
to mode. At step 576, the recipient moves to the locker indicated by the
flashing light and
pushes on the door. The door opens and indicator shows "open" (for example, by
displaying a different color and/or ceasing flashing). At step 577, the
recipient has not
opened the door within the time out period, so the indicator shows "closed"
(for example,
by displaying a particular color) and the lock-push-to-release mode is
cleared. At step
578, the recipient is logged out and system logs failed to pick up
transaction.
At step 579, after the door opens and the indicator shows open, the user
removes the
packages. The indicator shows "closed" and at step 580 the locker state is set
to "clear."
A transaction log is updated with picked up package and with the time. At step
581, it is
determined if the user has another locker. If the answer is affirmative, step
570 is
zo executed and control continues as described above. If the answer is
negative, the resident
leaves the locker area/ mailroom with the packages.
At step 584, the administrative process begins. It will be appreciated that
the functions
and sequence of functions described here with respect to the administrative
function can
be varied according to the particular needs of the user and the system. At
step 585
transaction logs are maintained. At step 586, daily transactions histories are
emailed to
the system administrator.
At step 587, package and locker management process begins. At step 588, a
package
expiration time can be set by the administrator. This time is the time allowed
by the
system for the recipient to retrieve their package after a code is entered
and/or after the
23
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
package has been received. At step 589, an expiration warning may be emailed
to the
resident to prompt pick-up of the packages. At step 590, package expiration
notice is
mailed to the recipient. At step 592, the agent takes action to clear
unclaimed packages
from the locker system.
Referring now to FIG. 6, one example of touch screen displays presented to a
drop-off
agent is described. In this example, a package is dropped off at a locker
system by the
agent. The agent may be a delivery person, an attendant, or some other
employee that is
tasked with entering packages into the locker system. It will be appreciated
that although
the displays are presented as being touch-screen displays, other display or
data entry units
te or devices (e.g., personal computers) can also be used. In addition,
although this example
involves the use of a locker arrangement, other storage areas can also be
used. Finally,
the example displays presented here are examples only and their sequence,
content, and
number can be varied to meet the needs of a particular user or application.
At step 601, the agent button is selected by the delivery agent from the home
screen. At
is step 602, an agent login (e.g., user name) is entered on the key pad or
the touch screen. At
step 603, an agent password is entered from the touch screen or the keypad.
The
password and user name are verified. At step 604, a drop-off option is
selected on the
touch screen in order to begin the drop-off process as described elsewhere
herein.
At step 605, the locker size is selected by the drop-off agent. At step 606, a
recipient is
20 selected from a list by the agent and "enter" is pushed on the screen by
the agent. At step
607, a locker is opened by the application to allow the agent to place the
package in the
locker. Now, instructions are presented on the screen for the agent to scan
the package,
drop off the package, scan the door (to record the locker used), and close the
door to the
locker.
25 At step 608, the agent presses the confirm scan button after all
scanning has been
completed. At step 609, the complete button is selected and pressed by the
agent. At step
610, a message is displayed notifying the agent that an email (or other
message) is sent to
the recipient. At step 611, a message is also displayed "Would you like to
drop off
another package?" In this example, the agent presses "no." Al step 612, the
home screen
30 returns and another package can be dropped off,
24
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
Referring now to FIG. 7, one example of screen presented to a recipient
picking up
packages is described. As with the example of FIG. 6, it will be appreciated
that
although the displays are presented as part of a touch-screen display, other
display or data
entry units or devices can also be used. In addition, although this example
involves the
s use of a locker arrangement, other storage areas can also be used.
Finally, the example
displays presented here are examples only and their sequence, content, and
number can be
varied to meet the needs of a particular user or application.
At step 701, the pickup button is selected from the home screen by the
recipient. In this
example, a package is dropped off at a locker system by an agent and the
recipient has
to arrived at the locker system to retrieve their package(s). At step 702,
the recipient enters
the pickup code that has been sent to them. At step 703, after the code has
been verified,
the locker door opens and the locker number is displayed on the touch screen.
Additionally an indicator at the actual locker may be activated to identify
the locker to the
recipient and make retrieval of the package easier. At step 704, the home
screen returns.
15 Referring now to FIG. 8, one exampleof a system that manages secured
spaces is
described. The system 8100 includes a network 8102, a bridge 8104, and a radio
frequency identification (RFID) reader device 8108. Coupled to the bridge 8108
are port
links 8136 and 8138. Port link 8135 is coupled to port link 8138; port link
8134 is
coupled to port link 8135; and port link 8132 is coupled to port link 8134. An
electronic
20 lock 8120 is coupled to port link 8132. An electronic lock 8122 is
coupled to the port
link 8134 and locking device 8124 is coupled to port link 8135. A locking
device 8126 is
coupled to port link 8136; locking devices 8128 and 8130 are coupled to port
link 8138.
A coMputing device 8106 is coupled to the network 8102.
A sensor 8120 is coupled to port 8132; a sensor 8112 is coupled to port link
8134; and a
2S sensor 8112 is coupled to port link 8135. Further, a sensor 8116 is
coupled to port link
8136; and a sensor 8118 is coupled to port link 8138.
The different locks and sensors protect various secured spaces 8119, 8121,
8123 and 8125
from unauthorized entry and/or environmental concerns. The secured space 8125
is
protected by two locks 8128 and 8130, for example, each deployed on a separate
door at
30 each end of the secured space 8125. In one example, the secured spaces
are lockers. In
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
other examples, the secured spaces are cabinets or other enclosures in a
medical facility
(e.g., a hospital). In still another example, the secured spaces are cabinets
are other
secured spaces in an office. In yet another example, the secured spaces are
different
protected areas (e.g., safes, closets, OT cabinets) is a home. Other examples
of secured
s spaces are possible. The secured spaces may have one or more environmental
control
devices 8109 that control, adjust, or otherwise affect one or more
environmental or
physical conditions within the locker. For example, the environmental control
device
8109 may adjust lighting, temperature, pressure, or any other condition within
the locker.
In this respect, the environmental control device 8109 may be a fan, light,
air conditioner,
io freezer unit, or heating unit. Other examples are possible. Control of
the environmental
control device 8109 may be accomplished from the server 8107. For example,
conditions
within the locker may be monitored (e.g., via sensors) and commands may be
issued from
the server to operate the environmental control device 8109 and maintain
various
conditions within the locker within predetermined limits.
16 It will be appreciated that many of the secured spaces managed according
to the
approaches described herein are micro-areas or micro-spaces. As used herein,
micro-
spaces and micro-areas refer to spaces less in extent than a room (or some
other space that
is demarcated or separated from other areas in some way). To mention a few
examples,
micro-spaces or micro-areas are less in area than larger spaces such as closed
door offices,
20 office cubicles, office areas that includes cubicle and open spaces,
rooms or other areas in
apartments or homes, storerooms, mailrooms, rooms in a retail stores, hospital
rooms, or
class rooms in schools. In this regard and to give a few examples, the micro-
spaces may
be cabinets, closets, lockers, chests, boxes, or safes. The micro-areas and
micro-spaces
may be disposed in different rooms or larger areas. For examples, in a
hospital where the
25 micro-spaces arc cabinets, the cabinets can be situated in different
rooms within the
hospital.
The network 8102 is any type of network that can transmit communications. For
example, the network 8102 can be a local area network (LAN) or wide area
network
(WAN). The network 8102 can also employ any type of communication technology
(or
30 combinations of these technologies). In this respect, the network can be
a computer
26
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
network, a cellular network, any other type of wireless network, the Internet,
or any
combination of these or other networks.
The bridge 8104 is any computer device that is configured to route messages to
and from
different locations. In one example, the bridge 8104 is a TZ Centurion Tm
bridge
manufactured byTelezygology, Inc. of Chicago, Illinois. Other examples are
possible.
Each bridge may be managed individually from a server, or otherwise part of a
larger
system.
The RFID reader 8108 is a device that is configured to read information from
RFID cards
that are swiped through the reader. These cards are associated with users, In
one
to example, the port links are the TZ CenturionTM RF1D device manufactured by
Telezygology, Inc. of Chicago, Illinois. Other examples of RF1D readers are
possible.
Port links 8132, 8134, 8135, 8136 and 8138 arc configured to provide a
connection
between the various locking devices and the network 8102 and one or more power
sources. In one example, the port links are the TZ Centurionrm Port Link
manufactured
by Telezygology, Inc. of Chicago, Illinois.
Electronic locks 8120 and 8122 are any type of electronic locking device. In
one
example, the lock 8120 and 8122 is a compact, lightweight, high-load locking
devices that
use jaw lecking mechanisms to capture and hold an inserted mating stud to
secure a door.
The mechanism may be controlled by a Shape Memory Alloy (SMA) actuator which
in
turn is managed and controlled by a server 8107 as described herein. Embedded
intelligence may be provided at the locks 8120 and 8122 that enables
networking,
switching and the ability to control other devices and connect with smart
objects such as
sensors, In one example, the locks 8120 and 8122 are TZ Radian.'" locks
manufactured
by Telezygology, Inc. of Chicago, Illinois. Other examples are possible.
zs Locking devices 8122, 8124, 8126, and 8128 are also electronic locking
devices, For
example, these may be intelligent locking devices that offer drop-in
replacements for
legacy manual swing-handle data center cabinet locks. These devices may
integrate a high
load Shape Memory Alloy (SMA) actuated locking mechanism with a touch-to-
release
option, a multi-color LED status indicator, manual key over-ride, electronic
door status
27
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
sensor, and a RJ-45 connector. In one example, the devices are TZ
SlideHandleThi devices
manufactured by Telezygology, Inc. of Chicago, Illinois. Other examples are
possible.
The locking devices 8122, 8124, 8126, and 8128 may also be managed and
controlled by
a server 8107 as described herein. It will also be appreciated that the
devices 8120, 8122,
8124, 8126, 8128, and 8130 may all be of the same type and that the
configuration shown
with respect to FIG. 8 is one example only.
Sensors 8110, 8112, 8114, 8116 and 8118 are any type of sensing device that
are
configured to sense any type of condition (e.g., environmental conditions, the
presence of
an object in a space, the dimensions of an object in a space, and so forth).
In one
example, each sensor is a TZ Sensor"m manufactured by Telezygology, Inc. of
Chicago,
Illinois that provides environmental monitoring at the cabinet enclosure level
across a
range of operating conditions such as temperature, humidity, door contact
and/or leak
detection to mention a few examples.
The computing device 8106 is any type of computing device that can be used to
operate or
s host the server 8107. In this respect, the computing device 8106 may be a
personal
computer, lap-top, or any other type of computer platform. Other examples of
computing
devices are possible. In one example, a server is located in the computing
device 8106.
However it will be understood that the server 8107 may be disposed at other
locations (or
multiple locations) as well.
20 In one example of the operation of the system of FIG.8, the server 8107
at the computing
device 8106 monitors environmental or other conditions of the spaces 8119,
8121, 8123,
and 8125 via the sensors 8110, 8112, 8114, 8116, and 8118. The server 8107
receives
requests from users to access the secured spaces 8119, 8121, 8123, and 8125
from users
and manages access to these spaces. For example, the server 8107 may determine
zs whether to open a space as requested by a particular user (e.g., after
the user logs into the
system or swipes their access card through the RFID reader 8108). The server
8107 also
stores a log of activity with respect to the spaces 8119, 8121, 8123, and 8125
(and the
locking arrangements used to secure these spaces) and may prepare various
types of
reports concerning these spaces and usages/activities related to these spaces.
The server
30 8170, using the sensors 8110, 8112, 8114, 8116, and 8118, may determine
when the
28
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
certain conditions in or at the secured spaces exceed certain thresholds and
take
appropriate actions. For example, when the temperature as measured by a sensor
at a
secured space exceeds a threshold an alert may be issued to appropriate
personnel so that
the item can be removed from the space. In another example, another device
(e.g., a fan
or air conditioner) may be activated when a particular sensor detects that a
temperature
has been exceeded. In this way, an integrated approach (e.g., a single server
providing all
functions through one or more interfaces) for managing and controlling access
to the
secured spaces is provided. It will be appreciated that only a few of the
possible server
functions have been described and that as described elsewhere herein other
functions are
to possible.
Referring now to FIG. 9, another example of a system 9200 that manages various
secured
spaces is described. The system 9206 includes a first network 9202, a bridge
9204, and an
RF1D reader 9208. Coupled to the bridge 9208 are port links 9236 and 9238, A
port link
9235 is coupled to port link 9238. A port link 9234 is coupled to port link
9235. A port
link 9232 is coupled to port link 9234. An electronic lock 9220 is coupled to
the port link
9232. An electronic lock 9222 is coupled to the port link 9234. A locking
device 9224 is
coupled to port link 9235. A locking device 9226 is coupled to port link 9236.
Locking
devices 9228 and 9230 are coupled to port link 9238. A computing device 9206
is
coupled to the network 9202.
al A sensor 9220 is coupled to the port link 9232. A sensor 9212 is coupled
to the port link
= 9234. A sensor 9212 is coupled to port link 9235. A sensor 9216 is
coupled to the port
link 9236 and a sensor 9218 is coupled to port link 9238.
The elements of FIG. 9 having like numbers with respect to similar elements of
FIG. 8
(e.g., element 8110 corresponds to element 9210 and so forth) have been
described above
with respect to FIG. 1 and these descriptions will not be repeated again here,
In addition,
for clarity the secured spaces are not shown in FIG. 9 although it will be
understood that
secured spaces of similar (or different) scope than those shown with respect
to the
example of FIG. 8 may be configured in the example of FIG. 9.
The system 9200 also includes a second network 9252, a bridge 9254, and an
RPM) reader
9258. Coupled to the bridge 9258 are port links 9286 and 9288. A port link
9285 is
29
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
coupled to port link 9288, A port link 9284 is coupled to port link 9285. A
port link
9282 is coupled to port link 9284. An electronic lock 9270 is coupled to the
port link
9282. An electronic lock 9272 is coupled to the port link 9284. A locking
device 9274 is
coupled to port link 9285. A locking device 9276 is coupled to port link 9286.
Locking
devices 9278 and 9280 are coupled to port link 9288. A computing device 9256
is
coupled to the network 9252.
A sensor 9260 is coupled to the port link 9282. A sensor 9262 is coupled to
the port link
9284. A sensor 9262 is coupled to the port link 9285. A sensor 9266 is coupled
to the
port link 9286. A sensor 9278 is coupled to the port link 9288.
to The elements associated with the second network 9252 are similar in
configuration to
like-numbered elements associated with the first network 9202 (e.g., element
9202
corresponds to element 9252 and so forth). Consequently, the description of
these
elements will not be repeated again here.
A third network 9240 is coupled to the bridges 9204 and 9254. The network 9240
is, in
one example, a network that operates according to the Internet Protocol (i.e.,
an IP
network). In one example, the network 9240 may be the Internet. Other examples
of
networks and other combinations of networks arc possible. In some aspects, the
third
network can be considered a wide area network while the networks 9202 and 9252
may be
considered local area networks.
zo Coupled to the third network 9240 are a personal digital assistant 9241,
a laptop 9242, a
personal computer 9244, and a tablet 9243. The personal digital assistant 9241
is any type
of personal digital assistant that may communicate with the network using, for
instance, a
wireless connection. The laptop 9242 is any portable computer such as a laptop
computer.
The personal computer 9244 is any computing device that is typically not
mobile (e.g., a
zs desk top computer). The tablet 9243 is personal computing tablet as
known to those
skilled in the art.
Various applications (together incorporated into or operated as a server 9239)
are
provided by some or all of the devices. These applications can be implemented
or
configured as software that operates at one or more of the devices 9240,9241,
9242,
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
9243, or 9244. These applications are scalable and modular in the sense that
particular
users can utilize some or all of the applications depending upon their
particular need,
requirement, budget, available bandwidth, or some other parameter or
combination of
parameters. Thus, the applications are scalable and easily interchangeable and
modifiable
as the needs of a particular user or system change over time.
The server application 9245 is any server application (e.g., a web service
such as a
Microsoft windows application) that supports execution or provides a software
framework
for any or all of the other software modules described herein,
Database 9246 is any type of database where information is temporarily and/or
permanently stored. In one example, the database 9246 is a Microsoft SQL
server.
Reporting analysis 9247 is a software module that manages data contained in
the database
9246. In one example, a facility management module logs all events associated
with a
particular space (e.g., the door opening or closing to the space, temperature
data
associated with the space, or pressure data associated with the space) and
generates
reports (or alarms) when predetermined thresholds are exceeded. Other reports
can be
generated over predetermined time periods and reported to authorized personnel
(e.g.,
system administrators).
A web portal module 9248 is any type of web client interface that allows a
user to log into
the system. A unified messaging module 9249 is a module that sends alarms or
zo notifications created by some of the other modules.
An access management module 9290 provides access control functions. For
example, the
module 9290 customizes permission to different users and/or associates
different locking
devices with different users. The module 9290 prevents access to the secured
spaces by
individuals merely passing through an area (e.g., individuals merely coming
through the
building). This function may be accomplished by deploying a card-based system
(users
are required to swipe the ID card) or biometric system or a log-in based
system (where
users log in through a computing device). Existing buildings service modules
could also
interface/be integrated with the module 9290.
31
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
A facility management module 9291 is configured to provide temperature,
pressure, or
other environmental management for a facility. A plant management module 9292
is
configured to maintain plant equipment, schedule equipment operation, or
provide other
services related to the management of a plant.
s A configuration management module 9293 is a software module that may be
telecommunication-based. All physical assets together within buildings and who
is using
these assets maybe documented and/or controlled.
A geographic information system module 9294 is a software module that allows
the
display of geographic information to a user. For example, the geographic
features of the
io network may be displayable and these may be zoom-able on a display screen
on any or all
of the devices 9240, 9241, 9242,9243, or 9244.
A service level agreement module 9295 is a software module that is used to
guarantee
service levels to users. In one specific example, the module9 295 guarantees
that a
particular space never exceeds a temperature of 75 degrees Fahrenheit. The
module 9295
15 may also report the temperatures of these spaces. A micrometer on a
computer may also
be monitored to ensure the power level used by the computer does not exceed a
predetermined level.
A customer billing module 9296 is a module that performs customer billing. In
one
example, customers may be charged different prices for different levels of
service or
20 access to different features.
A human resource management module 9297 is a software module that documents
human
interactions with the system or elements of the system. For example, the
module 9297
may determine (through the use of various sensors) when a user logged in to
the system,
what assets the user used, and what the user did with these assets.
25 In one example of the operation of the system of F1G.9, any of the
modules described
above may be deployed to provide various functions to any of the secured areas
secured
by the locking arrangements. For example, if the first network 9202 may be
disposed in a
jewellery store and the various locks and locking arrangements are configured
to control
cabinets for storage of specific types of jewellery, jewellery of specific
values, or
32
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
jewellery repair tools. The modules described above allow access to some
cabinets for
some individuals, but not for other individuals. Access to the cabinets is
monitored in
real time and alerts/alarms are issued as unauthorized individuals attempted
to access
some cabinets. Reports are also created and sent to the owner of the jewellery
store
regarding the access history (e.g., the individual who access the cabinet,
when access
occurred, and for how long) of the cabinets. The police or other authorities
could be
alerted under some conditions.
In another example of the operation of the system of FIG. 9, the second
network 9252 is
disposed in a hospital, and the various locks and locking arrangements control
access to
cabinets for specific types of medical instruments, medicines, and human
tissue. The
modules described above allow access to some cabinets by some individual, but
not for
others. Access to the cabinets is monitored in real time and alerts/alarms
issued as
unauthorized individuals attempted to access some cabinets. Reports are also
created and
sent to the hospital administrator. Environmental conditions are monitored by
the sensors
is and when predetermined conditions are exceeded, alerts issued or other
actions taken.
Polling is one approach that can be used to monitor conditions at various
devices. Other
approaches are possible.
In both of these examples, the server 9239 may be disposed and operate on the
Personal
computer 9244 and communicate over the network 9240 to the networks 9202 and
9252
and subsequently to the devices that monitor or control access to the various
secured
spaces.
Referring now to FIG. 10, an example of a server that manages secured spaces
is
described. The server 1300 interacts with a client 1302. The client 1302
includes a client
application 1304, isolated storage 1306, and a framework 1308.
The client application 1304 allows users to interact with the system. For
example, the
client application may provide login screens, login features, and so forth to
present to a
user allowing the user to login to the system, enter information, and access a
secured
space. Various types of information may also be presented to the user.
33
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
The isolated storage 1306 is a memory storage area that is configured to data
entered by
the user or to be presented to the user. For example, the isolated storage
1306 may be a
Microsoft Silverlight-compliant storage area. The framework 1308 is used to
provide a
software framework (e.g., generic procedures or functions) to the user. For
example, the
framework 1308 may be a Microsoft Silverlight-compliant framework,
The server 1300 includes a web services module 1322, a business layer 1324, a
framework 1326, a transaction database 1328, a reporting database 1330, and a
network
framework 1332.
The web services module 1322 is configured to provide communication services
with the
io client 1302 (for interaction with a user) and communicate with various
bridges (for
interaction with locking mechanisms, sensors, and so forth securing secured
spaces). For
example, the web-services module 1322 provides format conversions for
information/messages transmitted between the server 1300 and these other
entities.
The business layer 1324 is where the server functions are performed (e.g., the
modules of
is FIG. 9). The framework 1326 is framework for the operation of the
business layer 1324.
For example, this may be a Microsoft Entity framework and provide generic
functions and
subroutines used to perform various functions.
The transaction database 1328 is a database for the temporary storage of data
being
processed at the server 1300. The reporting database 1330 is permanent storage
for data
20 used by the server (e.g., device information and reports generated may
be stored here).
The network framework 1332 is a framework for the operation of the server
1300. For
example, this may be a Microsoft NET framework.
Messages 1318 are exchanged via a link 320 between the sever 1300 and the
client 1302.
The messages 1318 are any type of messages. In one example, Windows
Communication
25 Foundation ¨compliant (WCF) messages are used. Other examples are possible.
The communication link 1320 is any type of communication link. In one example,
the
communication link 1320 uses XML protocol. Instructions are also exchanged via
communication links 1315 and 1317 between the server 1300 and bridges 1314 and
1316.
34
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
The communication links .1315 and 1317 are high security communication links.
For
example, these links may utilize an encryption technology. The messages sent
across
links 1315 and 1317 may use any type protocol.
The bridges 1314 and 1316 are communication bridges as described herein. They
interact
s with devices 1310 and 1312. The device 1310 and 1312 may be locking
devices, sensors,
or combinations of these devices.
In one example of the operation of the system of FIG. 10, users access the
server 1300
using the client 1302 which operates at a personal computer. In another
example, the
client 1302 may be an RF1D reader and the user swipes an access card through
this device.
io The server 1300 determines if access is allowed, the locking
arrangement/secured space to
which access is allowed, and may open a locking arrangement (e.g., the devices
1310 and
1312) by sending messages to the locking device, The server 1300 may monitor
conditions at the secured spaces. In this regards, sensors may be deployed to
monitor
conditions. The sensed information from the sensors may be sent the server
1300 via
is communication links 1315/1317, The server 1300 determines if the sensed
conditions are
within predetermined limits. If the conditions are not within predetermined
limits, the
server 1300 may take action. For example, the server 1300 may create alert
messages and
transmit the alert messages to the client 1302 to be presented to the user.
The server 1300
may also generate reports and store these in the storage 1330 and/or present
these to a user
20 at the client 1302.
Referring now to FIG. 11, another example of a server architecture that
manages secured
spaces is described. The server 2405 interacts with a presentation business
layer 2402.
The layer 2402 includes a user interface 2404, isolated storage 2406, and a
framework
2408. The user interface 2404 allows users to interact with the system. For
example, the
25 interface 4204 may provide login screens, login features, and so forth
to present to a user
to allow the user to login to the system and access a secured space. In one
example, this is
a Microsoft Silverlight-compliant application.
The isolated storage 206 is a memory storage area that is configured to data
entered by the
user or to be presented to the user. For example, the isolated storage 2406
may be a
30 Microsoft Silverlight-compliant storage area. The framework 2408 is used
to provide a
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
software framework (e.g., generic procedures or functions) to the user. For
example, the
framework 2408 may be a Microsoft Silverlight-compliant framework.
The server 2405 includes a business logic layer 2424, a transaction database
2428, a
reporting database 2430, and a network framework 2432.
The business logic layer 2424 provides configuration management (e.g., the
configuration
of the predetermined environmental limits discussed herein). The layer 2424
may also be
configured to provide user/visit management (e.g., access to secured spaces);
remote
access and monitoring of the secured spaces; alarm logic (e.g., the logic to
issue alarms
when monitored conditions fail to meet predetermined thresholds; and cross-
bridge
to coordination of micro-protection of secured spaces.
The transaction database 2428 is a database for storage of configuration
information that
may be used by the business rules in the Business Layer and the temporary
storage of data
being processed at the server 2405. The reporting database 2430 is permanent
storage for
primarily historical data used by the server (e.g., reports generated). For
example, the
is databases may be Microsoft SQL databases.
The network framework 2432 is a framework for the operation of the server
2405. For
example, this may be a Microsoft NET 4.0 framework. Messages 2418 are
exchanged via
a link 2420 between the sever 2405 and the presentation business layer 2402.
The
messages 2418 are any type of messages. In one example, Windows Communication
20 Foundation-compliant (WCF) messages are used. Other examples are
possible.
The communication link 2420 is any type of communication link. In one example,
the
communication link 2420 uses XML protocol. Instructions are also exchanged via
communication links 2415 and 2417 between the server 2400 and the bridges 2414
and
2416. The communication links 2415 and 2417 may be high security communication
25 links. For example, the links 2415 and 2417 may utilize encryption
technologies. The
messages sent across the links 2415 and 2417 may use any type of protocol.
36
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
The bridges 2414 and 2416 are communication bridges as described herein. They
interact
with devices 2410 and 2412, which may be locking devices, sensors, or
combinations of
these devices.
In one example of the operation of the system of FIG. 11, users access the
server 2405
using the layer 4202 at a personal computer. in another example, the layer
2402 may be
deployed at an RFID reader and the user swipes an access card through this
device. The
server 4205 determines if access is allowed, the locking arrangement/secured
space to
which access is allowed, and may open a locking arrangement by sending
messages to the
locking device. The server 2405 may monitor conditions at the secured spaces.
In this
regards, sensors at the secured spaces may monitor conditions. The sensed
information
may be sent to the server 4205 via the communication links 2415/2417. The
server 2405
determines if the sensed conditions are within predetermined limits. If the
conditions are
not within predetermined limits, the server 2405 may take action. For example,
the server
may create alarms and transmit the alarms to the client 2402 (or other
locations) to be
presented to the user. The server 4205 may also generate reports and store
these in the
storage 2430 and/or present these to a user at the layer 2402.
Referring now to FIGs.12-17, one example of the messaging protocol used
between
various elements of the system (e.g., between user interfaces, bridges, and
servers) is
described. In one example, the protocol uses HTTP POST and GET actions and the
JSON and MAL protocols to communicate. The protocols typically require a host
system
to communicate with, but the bridge and the server host may both act as client
or server
depending on need.
The server may connect to a bridge as follows. The host sends an
authentication request
to the bridge. This request is an HTTP POST containing the usemame and
password in
the request body. If the usemame and password for the bridge were both "admin"
the
request body may, in one example, contain the URL encoded string:
txtUsemame=admin&txtPassword=admin. Other examples are possible.
The bridge confirms the credentials and reply with a session cookie named
"key" that
must be included in all future requests from the host to the bridge. The host
sends a
registration message to the bridge. This message contains the hosmame, port,
and URL
37
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
that serves requests from the bridge, in one example. The registration message
is sent as
an HTTP POST request containing a JSON body. The bridge responds to the
registration
message with a standard HTTP response. The body of the response contains XML
that
indicates which configuration elements were successfully set or an error
message if
something went wrong. During this exchange, the host (server) acts as the HTTP
client,
and the bridge acts as an HTTP server.
The bridge sends an HTTP POST request to the host (server) at the URL and port
specified in the configuration message.. In this case, the bridge is acting as
an HTTP
client. This response contains various details about the bridge, including
firmware
io version and serial number. Once the host receives this message, the
bridge is said to.be
registered with that host. All future client requests from the bridge will be
sent to the
registered host.
The bridge acts as a client whenever it needs to communicate with the host.
This removes
the need for the host to constantly poll each bridge that is registered with
it. Certain
events will cause the bridge to send information to the host. These events
include but are
not limited to the following': lock status has changed for a device (either
locked or
unlocked); an RFID tag was read by an RFID reader; a device was removed front
the
network or otherwise made unable to communicate; a device was returned to the
network
after being out of communication; and the device discovery process on the
bridge was
completed.
The bridge supports a command that will discover all of the devices attached
to the
bridge. When this command is finished running, the bridge will send a list of
devices to
the host. This list contains the device type and serial number for each
device. Each
device has an associated device descriptor file. The descriptor file describes
the available
commands and configuration settings for a device type.
When the bridge sends an update request to the host, it uses HTTP POST to the -
URI
specified during registration. The body of this message will contain XML
information
that describes the event. There are four types of events.
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
Bridge Registration events are events triggered whenever a host sends the
registration
message. The registration message contains some information about the bridge
sending
the message, but another purpose is to establish two-way communication with
the host
(server).
s Discovery Results events are triggered after the bridge has finished
discovering attached
devices. The discovery results message contains the device type and serial
number of
each device found.
Status Update events are triggered when the state of a lock changes (this
includes an error
state that indicates a disconnected device). This event is also triggered by
an RFID tag
to being scanned. A single status update can contain state information for
all devices
attached to the bridge (this will normally only happen immediately after
discovery).
Stream events are triggered when the bridge can be configured to send periodic
sensor
value updates, Stream update messages are used for logging and actions on the
host
(server) side, so they are sent regardless of changes to the sensor values. A
single stream
is update will include information from all devices attached to the bridge.
Referring now again to FIGS.12-17, specific message flows are now described.
In these
examples, it is assumed that a, server includes various modules (e.g., a
hardware event
handler, a card management service, a device communication service, a device
repository
service, a bridge management service) and that the server accesses memory
(e.g., a
20 database and a device repository). These modules are described in
greater detail below
and their functions may be changed or modified according to the needs of the
user and the
System.
Messages can have a wide variety of purposes and be formed according to a wide
variety
of forms and formats. For example, action messages include a command and may
be in
25 the form ("Action":"Command"), The command may be any command such as to
open a
lock, close a lock, and so forth. Configuration messages may include an array
of objects
containing name/value pairs of new configuration settings. Any number of
configuration
options can be included, but the array may in some examples only contain
elements that
will be changed. for example, a command that sets the primary name, secondary
name,
39
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
and unlock timeout of a radial or slide handle, but leaves the input and
output modes
unchanged is: "Configure:rinput 1 type": "temperature"), ("unlock
timeout":"20")).
Status messages may retrieve status information for a device. It will be
understood that the
above are only example messages and that the actions, data, format, scope, or
any other
features of these messages may be changed to suit the needs of a particular
application or
system.
=
Referring now to FIG. 12, a bridge registration process is described. At step
3502, and
authenticate message is sent from the user interface to the server. At step
3504, an
authenticate message is seat from the server to the bridge. At step 3506, the
server
o authenticates the request (or fails to authenticate) and sends either a
pass or fail message
to the server. If a failure, a fail message is sent from the server to the
user interface. At
step 3508, a configure bridge message is sent from the server to the bridge.
At step 3510,
configuration is accomplished and a configuration successful message is sent
from the
bridge to the server. At step 3512, this event is recorded in the database. At
step 3514, a
success message is sent from the server to the user interface.
Referring now to FIG. 13, a bridge discovery process is described. At step
4602, the
discovery process is started via a message from the user interface to the
server. At step
4604, the bridge serial number is obtained from a memory storage device. At
step 4606, a
discovery request is fomied and at step 4608 sent to the bridge. At step 4610,
the bridge
sends a result to a hardware event handler. At step 4612, discovery is
complete and this is
sent to the server. 'At step 4614, device status is updated if the device is
already in the
directory. lithe device is not in the directory at step 4616, an entry is
created. At step
4618, the device is added or updated in the directory.
Referring now to FIG. 14, an open locking device process is described. At step
5702, an
open lock request is sent from the user interface to the server. At step 5704,
the device
serial number (for the bridge or locking device) is obtained from the device
repository. At
step 5706, a message is sent from the server to the bridge to fire the lock
open.
Depending upon the result, either an action succeeded message is sent from the
bridge to
the server (at step 5708) or an action failed message is sent from the bridge
to the server
(at step 5710). At step 5712, the device status is updated in the data
repository. A
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
message is sent to an event management service at step 5712 that an opening
action was
attempted at a particular lock.
Referring now to FIG.! 5, a locking process is described. At step 802, a lock
request is
sent from the user interface to the server. At step 804, a message is sent
from the server
to the bridge to lock. If the action fails, at step 806 a fail message is sent
from the bridge
to the server. At step 808, the device repository is updated as to the status
of the lock. At
step 810 a message is sent from the server to a bridge management service that
a lock was
attempted.
Referring now to FIG, 16, an unlocking process is described. At step 902, an
unlock
to request is sent from the user interface to the server. At step 904, a
check is made as to the
unlock duration. If the unlocking duration is zero, then the lock is to be
opened. If the
unlock duration is not zero, a message is sent to a bridge management service
and the
status is recorded in the database. At step 906, an unlock request message is
sent from the
server to the lock. If the action fails, a fail message is sent from the
bridge to the server at
step 908. At step 910, the status of the lock is updated in the device
repository and the
data base.
Referring now to FIG. 17, an unlocking process using a card reader is
described. At step
1002, the RFID reader sends a request to a hardware event handler to open a
lock. At step
1004, the serial number of the lock is obtained from the device repository. At
step 1006,
the event handler sends the request to a card management service. At step
1008, the
device repository is updated. At step 1010, it is determined whether the card
schedule
allows card usage. If the answer is affirmative, it is determined at step 1012
if the device
is assigned to the RFID reader and the user. If the answer is affirmative, the
device is
unlocked at step 1014 and a message of this occurrence is sent to the device
communication service.
Referring now to FIG. 18, example server logic flows are described. It will be
appreciated
that this is one example of server logic and that other examples are possible.
At step 1102, a request to open a lock is received. At step 1104, a
determination is made
as to the lock and bridge referred to in the request. At step 1106, the IP
address of the
41
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
bridge is determined. At step 1108, a message is formatted to the bridge to
fire opening of
the lock. At step 1110, the message is sent to the bridge.
At step 1112, the device status is changed to unlocked. At step 1114, the
message is
processed. At step 1116, the new status is logged to the server database. At
step 1118, the
database is updated. At step 1120, the status is updated at the user interface
showing the
device is unlocked.
At step 1122, a stream of sensor data is received from the bridge. At step
1124, new
sensor values from the stream are logged to the database. At step 1126, it is
determined if
the sensor is configured as an alarm input. If the answer is affirmative at
step 1126, then
at step 1128 it is determined if the value is over a configured trigger value.
If the answer
is affirmative at step 1128, then at step 1130 an alarm entry is created.
Execution ends. If
the answers at either of steps 1126 or 1128 are negative, execution also ends.
It will be understood that many of the elements discussed herein are software
modules
that are implemented as computer code stored on a storage media and running on
is processing devices (e.g., microprocessor or the like). However, it will
be appreciated that
the elements described herein may be implemented by any combination of
hardware or
software as known to those skilled in the art.
While the invention herein disclosed has been described by means of specific
embodiments and applications thereof, numerous modifications and variations
could be
made thereto by those skilled in the art without departing from the scope of
the invention,
INDUSTRIAL APPLICABILITY
Approaches are provided that provide controlled access to or management of one
or more
secured areas. The approaches allow packaged assets to be delivered to a
recipient
securely and easily without the use of an intermediate human attendant. The
recipient is
automatically informed of the delivery of the packaged asset and provided with
an access
code to open the secured area and retrieve the packaged asset. Accurate
records are
automatically created and maintained to facilitate package tracking. The
recipient can
retrieve the packaged asset without the need of a human attendant.
42
CA 02811317 2013-03-14
WO 2012/034171
PCT/AU2011/001177
The recipient can potentially retrieve the packaged asset at all hours of the
day and night.
Since the packaged assets are stored in a secured area, theft and other such
problems are
substantially reduced or eliminated.
43