Note: Descriptions are shown in the official language in which they were submitted.
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
HYBRID CLOUD BROKER
TECHNICAL FIELD
[0001] The present invention relates generally to a system and method of
managing
information technology infrastructure or cloud resources by automatically
adapting
hardware and software components of the cloud resources to the dynamic real-
time business
transaction requirements.
BACKGROUND
[0002] Information technology (IT) service providers are companies that
maintain
sophisticated hardware and software capabilities to manage data for the
services they
provide to their customers, herein referred to as "business clients." Backend
IT services are
used by such businesses as online retailers, e-commerce companies, and banks.
By way of
an example, a banking business client utilizes backend IT services to offer
its customers
several online banking services. The online banking services are provided via
a web-
enabled software application and involve a number of business transactions
from which a
bank customer can choose. Some examples of online banking transactions include
balance
inquiry, bill payments, and money transfers. Another example of an online
business is an e-
commerce company, such as e-Bay , which sells auction services online. Such
businesses
utilize business transactions in the form of online billing, payment
processing, order
tracking, and account maintenance.
[0003] Further, online businesses differ from each other by a number of
factors
including the nature of the business, its customers, and seasonality of the
business. For
example, an online retail store typically needs to service more customers
during the holiday
season than a banking business, which might be more consistent in the number
of customers
over the same period. In another example, a social networking service
utilizing multiple
java applications tends to stress the application server tier more than the
database server tier.
In yet another example, a news website attracts different customer types than
an e-
commerce website. When a news aggregator website provides weblinks to a
smaller local
website, there is a sudden spike of visitors to the local website. This may be
considered a
"slashdot" effect, where the traffic to the local website spikes as it is
being linked by a
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
website of higher popularity. Here, the type of visitor is in a broader
interest category than,
for example, a website selling VOIP (voice over intern& protocol) services and
phone cards
online.
[0004] Even as businesses seek to expand online offerings, it is important
to be able to
tie business results from online service offering to investments in
infrastructure required to
implement and maintain the online business. Many businesses try to strike a
balance
between owning or renting backend IT infrastructure to enable the online
business. One
form of backend IT infrastructure, herein referred to as "cloud resources,"
comprises many
components including physical components (e.g., servers, network equipment,
and
accessories - power supply, stabilizer), virtual components (e.g., software
licenses), and
technical manpower. A datacenter is the physical core of a cloud resources
system and can
comprise server farms, which are a plurality (typically hundreds or thousands)
of servers
with varying functions and capacities along with backup and supporting
equipment like
generators, uninterrupted power supplies ("UPS"), routers, switches, etc. The
cost of
ownership is high and there is an increased need to tie resource utilization
to income and
investments. Although the capital costs associated with creation of a
datacenter are high, the
maintenance and support costs associated with the datacenter can quickly
exceed the capital
costs over a very short time. Thus, the total cost of owning and maintaining a
datacenter, or
even a presence within a datacenter, can be very high, and businesses are
increasingly
looking to justify these costs by tying resource utilization, and the revenue
generated
therefrom, to the costs associated with those resources.
[0005] As a result of high ownership costs to maintain and upgrade IT
infrastructure
along with the need to protect data and ensure systems for redundancy and
reliability, many
businesses have moved to using a third party cloud resources model. In this
model, an IT
service provider is third party business that owns and operates the IT
infrastructure for
several businesses that offer web-based products and services. The service
provider enables
sharing of cloud resources among multiple business clients, thereby forming a
cloud
resources system, where the integration of the resources is dependent on
different price-to-
efficiency models. In one model, the business client pays a fee for leasing
certain backend
IT hardware for certain periods of time. The business client can add resources
during peak
seasons or remove resources during regular business seasons. In another model,
the
2
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
business client is charged only for the utilization of resources (e.g., energy
use, service use -
processing, memory). Further, some IT companies offer cloud computing
resources, where
the entire physical and virtual infrastructure is located in multiple
locations, business clients
still own their data and the fees are strictly usage-based. From a service
provider's
perspective, a single IT hardware and software resources can be re-allocated
to multiple
business clients or business functions for the same client depending on
resource utilization.
[0006] The services offered by the service provider to a business client
are frequently
based on the level of involvement of the service provider in the client's web-
enabled
businesses. The negotiated agreement between the service provider and the
client is called a
service level agreement (SLA). The SLA defines the level and quality of
service provided
to the business client. It also includes performance metrics (e.g., processing
(CPU) and
memory consumption), reporting procedures, duration of involvement, issue
resolution, and
security procedures as well as the transaction times, costs, and penalties
involved when a
business client uses the service provider's resources. More detailed metrics
for the quality
parameters are typically listed in a service level objectives ("SLO")
document. The SLA
defines business policies at a very high level, for example, the description
of the service to
be provided.
[0007] As an example of an SLA-based engagement, in an e-commerce
implementation, the SLA would describe, among other things, the service to be
provided
and the various component modules that are required to enable the system to
function. The
service to be provided in this e-commerce example could be either the sale of
goods or
services while the components required include hardware and software resources
to enable a
payment module, customer tracking, coupons, order tracking, e-mailing
procedures, security
modules, and other related components. The SLO would provide greater details
on the
payment modules, such as transaction descriptions and transaction times.
Following the
disclosure in the SLA, business policies are instituted that are generally
broad abstract
business statements that target the goals and visions of a business, but are
supported by the
SLA. An exemplary business policy supported by the SLA would be to increase
customer
retention, which can be supported by the customer tracking and coupon
capabilities under
the SLA. In view of the business policy, IT business analysts generate
business rules to link
the abstract business policy to measurable business parameters. Using the same
e-commerce
3
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
business example, a business rule to achieve the customer retention policy is
to offer
discounts to repeat customers. Another business rule example to increase
customer retention
is to offer coupons to new customers to draw them back for second purchases.
[0008] The processes described above require significant manual
intervention and are
further complicated by variables in the IT architecture including, without
limitation,
scalability, reliability, repeatability, and security. With the advent of
cloud computing
methods, there is an increased demand for highly secure, scalable, and
reliable automated
data management systems with deeper integration between IT and dynamic
business
requirements. There is also a demand for IT service provider companies to be
able to offer
agility in infrastructure management services to match changing business
methods. Further,
IT service providers are attempting to devise better metrics to analyze
resource consumption
and enable better sharing of resources with minimal human intervention.
Conventionally,
data management is primarily a mix of manual and automated methods. In some
cases, the
cloud resources are fixed to be responsive to certain business services
offered by the client.
Transaction requirements for a business activity are fed into a system
management software
and alarms are triggered to indicate if the infrastructure requirements are
exceeded or under-
used. The resources are then altered manually to support additional
transaction loads.
SUMMARY
[0009] The systems and methods described herein attempt to overcome the
drawbacks
discussed above by automatically adapting hardware and software components of
the cloud
resources to the dynamic real-time business transaction requirements.
[0010] In one embodiment, a computer-implemented method for automatically
adapting a service provider's cloud resources to the requirements of business
transactions
comprises providing, by a computer, a first computer-coded business rule,
wherein the first
computer-coded business rule comprises limiting parameters related to at least
one business
transaction; providing, by the computer, at least one computer-coded resource
policy,
wherein the computer-coded resource policy comprises managing parameters to
manage the
distribution of cloud resources within the limiting parameters in the first
computer-coded
business rule; monitoring, by the computer, the utilization parameters of the
cloud resources
for the business transaction, wherein an alarm is generated when the
utilization parameters
4
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
exceed the limiting parameters defined in the first computer-coded business
rule; updating,
by the computer, the limiting parameters of the first computer-coded business
rule with new
limiting parameters in response to the alarm, thereby generating a second
computer-coded
business rule; and rendering, by the computer, the second computer-coded
business rule,
wherein the managing parameters of the computer-coded resource policy manage
the
distribution of cloud resources within the limiting parameters in the second
computer-coded
business rule.
[0011] In another embodiment a computer-implemented system for
automatically
adapting a service provider's cloud resources to the requirements of business
transactions
comprises providing, by a computer, a first computer-coded business rule,
wherein the first
computer-coded business rule comprises limiting parameters related to at least
one business
transaction; providing, by the computer, at least one computer-coded resource
policy,
wherein the computer-coded resource policy comprises managing parameters to
manage the
distribution of cloud resources within the limiting parameters in the first
computer-coded
business rule; monitoring, by the computer, the utilization parameters of the
cloud resources
for the business transaction, wherein an alarm is generated when the
utilization parameters
exceed the limiting parameters defined in the first computer-coded business
rule; updating,
by the computer, the limiting parameters of the first computer-coded business
rule with new
limiting parameters in response to the alarm, thereby generating a second
computer-coded
business rule; and rendering, by the computer, the second computer-coded
business rule,
wherein the managing parameters of the computer-coded resource policy manage
the
distribution of cloud resources within the limiting parameters in the second
computer-coded
business rule
BRIEF DESCRIPTION OF THE DRAWINGS
[0012] The accompanying drawings constitute a part of this specification
and illustrate
an embodiment of the invention, and together with the specification, explain
the invention.
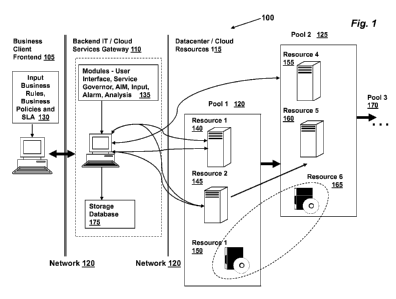
[0013] FIG. 1 illustrates a system architecture according to an exemplary
embodiment.
[0014] FIG. 2 illustrates a method of managing multiple cloud site
resources using
multiple autonomous infrastructure management software modules controlled by a
single
governing software module according to an exemplary embodiment.
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
[0015] FIG. 3 illustrates a method of managing information technology
infrastructure
by automatically adapting hardware and software resources to business
requirements
according to an exemplary embodiment.
[0016] FIG. 4 illustrates a method of managing information technology
infrastructure
by automatically adapting hardware and software resources to business
requirements during
a business transaction according to an exemplary embodiment.
[0017] FIG. 5a illustrates the content of the business policy or business
rule application
logic used to allocate the cloud site resources according to an exemplary
embodiment.
[0018] FIG. 5b illustrates the content of the computer coded resource
policy used to
control the cloud site resources according to an exemplary embodiment.
DETAILED DESCRIPTION
[0019] Reference will now be made in detail to the preferred embodiments,
examples
of which are illustrated in the accompanying drawings.
[0020] Dynamic real-time requirements of business transactions are managed
by
automatically adapting the information technology (IT) hardware and software
resources (or
cloud resources) after negotiating between the business policy requirements
and the cloud
resources. A business client's web-enabled business application offers the
customer several
business transactions as a business service. By way of an example, an account
balance
inquiry business service may consist of a savings account balance inquiry
transaction, a
checking account balance inquiry transaction, and a credit account balance
inquiry
transaction An SLO is then defined for the business service, and can contain
more
information on each transaction, including, for example, transaction
descriptions and
transaction times. Each transaction functions within an application and is
initiated as a user
request by the user using the application. The transaction interacts with a
backend web
server and application server to secure the information from backend database
servers. A
service level agreement (SLA) between the business client and a service
provider determines
how each transaction should be managed - including the intended transaction
times and the
required backend servers to process the transaction. The SLA can also include
additional
performance metrics like traffic capacity, energy consumed, redundancy, and
data security
to each transaction depending on the transaction type.
6
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
[0021] One exemplary embodiment allows for closer integration between
business and
IT where, when business transactions are deployed with requirements defined in
the SLA,
those transactions are dynamically supported within minutes or seconds by the
cloud
resources. Business rules derived from the business policy are supported by
the metrics
defined in the terms of the SLA. Business transactions are then determined
based on the
business rules and are offered as paid or free additional services to the
business client's
customers. These business rules are then scripted in a computer program,
herein referred to
as computer-coded, with metrics that determine the type of server tiers that
are required to
generate the responsive data as well as transaction times that the transaction
can afford
among other related metrics. Additional metrics include the time and date
rules and
associated priority information. By way of example, without limitation, some
transactions
can be configured as having higher priority at certain times the transaction
request is made.
These computer-coded business rules are related to the business transactions
and are
initiated when the user requests certain transactions from several transaction
options on the
business clients' web-enabled software application. Using the previously
discussed e-
commerce business example, a conventional business rule to achieve a customer
retention
policy is to offer discounts to repeat customers. Another business rule
example to increase
customer retention is to offer coupons to new customers to draw them back for
second
purchases. An embodiment converts the business rule to a computer-coded
business rule
comprising limiting parameters to define the priority metrics, cloud resources
usage metrics,
user information, and the discount or coupon information for the business
rule. As a result,
a returning user of a business client, on recognition (e.g., using the same
login name or
internet protocol address), will have their new transaction requests subject
to a faster
interaction process with more discounts or coupons in the options. The final
result is an
enhanced user experience for a returning customer.
[0022] In another exemplary embodiment, the resource usage for a type of
business
transaction is monitored and statistics are collected concerning the energy
used, processor,
and memory utilization, and software utilization, among other utilization
parameters. An
analysis module obtains the usage data from a monitoring module and analyzes
this data for
each business rule that accompanies a transaction. The analyses module
determines if the
resources are being improperly used including over-used, under-used or not
matching to one
7
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
of the metrics defined in the computer-coded business rules. The allocation of
resources for
each business transaction is a result of the business rules, which means that
if a business
deploys a new business transaction and defines the applicable business rules
for the
transaction, the resources are available, instantly (typically within minutes
or seconds), to
enable full functionality for the new service. Alternatively, an existing
business rule can be
applied to the newly deployed transaction, thereby ensuring a quick deployment
time and
effective use of resources to support the new transaction. The existing
business rule can be
applied automatically after the system determines, by intelligent analysis,
the historical
business rules and resource utilization for previous business transaction that
could be similar
to the new transaction.
[0023] In further embodiments, the business rules are defined so as to
convert abstract
human-readable logic that are the business policies into application logic for
computer
implementation via an automated service governor software module comprising a
business
rules engine module and a business rules manager module. The service governor
software
module works with an autonomic infrastructure management (AIM) software module
which
comprises smaller modules for resource discovery, monitoring, and management.
Discovery
is a process wherein the types of hardware, software and personas are
identified along with
their status (e.g., available, unavailable, or shared). The service governor
module further
comprises a business rules engine module and a business rules manager module.
The
computer-coded business rules are defined in the business rules engine module
while
autonomous programming script resource policies, herein referred to as
computer-code
resource policies, are defined in the business rules manager. The output of
the business
rules manager module is essentially limited by the output from the business
rules engine
module which contains historic rules responsive to previous transactions and
new custom
defined business rules if the system administrator intervenes on an alarm. The
alarm is
generated when the thresholds set by the computer-coded business rules and the
computer-
coded resource policies are breached. For example, the threshold for an
acceptable business
transaction is less than 80% or more than 30% of resource usage, where 'less
than 80%' or
'more than 30%' serves as the threshold, if more resources are required or
less resources are
being utilized by the transactions, then the alarm is triggered.
8
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
[0024] In one embodiment, the automated computer-coded business rules can
be
generated in an intelligent server module using a server-size algorithm, where
the algorithm
calculates the server size (or server instances) and threshold based on a
delta workload as
disclosed in equations (1) and (2). The delta workload is defined as the
inverse ratio of the
previous rule threshold and the product of the absolute threshold and the
difference of the
current rule threshold and previous rule threshold. The suggested number of
server
instances will then be the product of the delta workload calculated from the
above method
and the number of server instances from the current rule. In another exemplary
embodiment, the automated computer-coded business rules can be generated in
the
intelligent server module using an approximation algorithm. The approximation
algorithm
can be used to generate computer-coded business rules by changing either the
server size or
both the service size and the service thresholds. When the maximum threshold
is affected
by the current business transactions, the approximation algorithm is
implemented by
calculating the current delta workload for the current and maximum thresholds.
The server
size is then calculated as the product of the delta workload and the maximum
number of
servers as shown in equation (1); the server size is then added to the maximum
number of
server instances as disclosed in equation (3). In another embodiment, if the
minimum
threshold is affected then, as disclosed in equation (4) the minimum number of
servers are
further reduced by the server size calculated from the current delta workload
and the
minimum number of servers for the transaction using the method described
above.
Server size = Delta Workload * Number of current server instances (1)
1 Absolute threshold*
Delta workload = rCurrrent rule threshold - ' Previous rule
threshold (2)
Previous rule threshold
_ 2
New server size = Server size from equation (1) +current maximum number
of server instances (3)
New server size = Current mimimum number
of server instances - Server size from equation (4)
[0025] In a yet another exemplary embodiment for generating automated
computer-
coded business rules, if the number of server instances and the threshold are
affected by the
9
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
current business transaction volume, the following exemplary calculation can
be used. For
the minimum and maximum threshold violations, the delta workload is calculated
using the
forecasted minimum and maximum thresholds, the server size is then calculated
using the
delta workload (equation (2)) and the maximum or minimum number of servers as
described
in the previous embodiment. Accordingly, the maximum or the minimum number of
servers
will be increased or decreased, respectively, by the calculated server size.
The
corresponding thresholds, if affected, can be updated using the new maximum or
minimum
thresholds based on the newly calculated server size. A combination for the
minimum and
maximum forecasted thresholds can be implemented if both thresholds are
simultaneously
breached. The automated computer-coded business rules generated from these
calculations
contain new limiting parameters, which are then used to update the old
parameters in the
previous computer-coded business rules as a result threshold and/or server
size breach
alarms.
[0026] In
an exemplary embodiment, if a business transaction requires the use of an
Apache application server from the cloud resources, the business rules manager
deploys
resource specific policies that define the available metrics for the Apache
server. The
metrics in these policies are resource specific and include the maximum and
minimum
number of server instances, the server threshold information, and scale-in and
scale-out
actions. When these policies are deployed to the AIM module, they instruct the
module to
use resources in the manner designated by the rule for the incoming business
transaction.
The policies within the business rules manager, herein referred to as computer-
code resource
policies, are limited by the computer-code business rules which essentially
add resource
utilization limiting metrics like priority and time period application of the
computer-code
resource policies beyond which an alarm is triggered for out-of-limitation
resource uses.
[0027] In
another embodiment, the discovery module recognizes the status of the cloud
resources and lets the administrator know about the availability of resources
for new
transactions. The monitoring module monitors resource utilization and informs
the AIM
module so that the policies can be updated where required. The service
governor module
also ensures that the computer-code business rules generated at the business
rules engine are
within the policies of resource usage established through the SLA. The
availability and
usage of resources should be aligned with the SLA requirements regarding
resource
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
consumption, transaction time, and energy usage, while the resource usage per
transaction
should be within the bounds of the computer-coded business rules. If there is
an improper
use of resources as a result of the usage being out of policy, alarms can be
triggered in the
system.
[0028] In another exemplary application, the service governor module is a
web-enabled
application accessible via a browser and comprises event handler function
modules which
receive and respond to all alerts from the system. The event handler function
module
determines the actions to be applied in response to the alarms. In an example,
the event
handler function modules and logs are implemented using a .NET framework and a
common
runtime language. Further, a publisher-subscriber pattern is implemented in a
C# .NET
environment. There are multiple event handlers that are used to track
information, for
example, an ICustomerEventHandler function can be used to define the policy or
rule to be
implemented on an event alarm, an INotifier handler function that defines the
method of
applying the rule, and an ISubscriber function that defines the rule.
[0029] A SQL database can be used to manage and store status information of
the
alarms generated, action response information, resource usage, and related
information. The
web-enabled application comprising the service governor module further
comprise options
to manually or automatically define metrics in the computer-coded business
rules, wherein
the rules are within the business policy. The automated definition computer-
coded business
rules are based on an intelligent learning module that uses historical metrics
used in previous
computer-coded business rules responsive to new business transactions. An
example of an
intelligent learning module is a neural networks module that associates
metrics in the
computer-coded business rules to the certain historical transaction types and
identifies
similarity of transaction types using the metrics. One method of using an
intelligent learning
module compares the type of business transaction and the date of the
transaction to historical
transactions and then offers the administrator a choice of computer-coded
business rules or
automatically applies the best choice to the business rules manager module.
[0030] In yet another embodiment, the intelligent learning module is
configured to
negotiate with the business rules engine to add or remove resources and to
learn from the
updates to the computer-coded business rules to derive intelligent new
computer-coded
business rules for certain transactions. The web-enabled software application
coupled to the
11
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
service governor also comprises a reports module to generate real-time reports
of the status,
alarms, resource usage and resolutions based on user requests. Additional web-
enabled
software applications also provide the system administrator with a user
interface to the AIM
module that implements the rules so that the emergency changes in resource
management
can be implemented while bypassing the business rules manager. The output of
the AIM
module provides physical as well as virtual provisioning of the cloud
resources using an
orchestrating and a resource adapting module. The service governor is also
capable of
interacting with multiple applications that analyze, monitor, discover, and
orchestrate
between the business transactions and the service provider's resources.
[0031] In additional embodiments, the service governor software is designed
to accept
business rules across a multi-tier IT architecture for the business backend.
For the quality of
service (QoS) benchmark in the SLA, it can be advantageous if the architecture
described is
extensible with support for .NET clients. The graphical user interface (GUI)
used to provide
business rules to the governor is developed on a .NET WPF framework and
contains a Rule
editor with capabilities to define, create, update, and delete rules. The
rules can be stored in
event handler function modules for future references, to train the system for
intelligent
responses, and to record error parameter for manual intervention. The result
of any
deployment of business rules and the utilization information is also recorded
for reporting
and billing purposes. In other embodiments, a Drools .NET engine can be used
to generate
and manage workflow rules in a .NET environment.
[0032] In yet another embodiment, resources are made available in the form
of multi-
tier network architectures using web servers like Apache servers, IBM HTTP
Servers, and
Sun Web Servers which can be used in the web tier of the backend architecture.
Also,
IBM's Websphere, BEA's Weblogic, Tomcat, SAP's NetWeaver, and Caucho Resin are
exemplary application server types that can be implemented herewith. In the
Database tier,
the Oracle Database, Sybase, and SQL Servers can be configured into the
architecture.
Further, existing third party modules can also be used with the service
governor software.
Modules to monitor and distribute resources, like Optier core first, BMC, and
TM-ART, as
well as statistical analysis modules can be implemented herewith. The AIM
monitors the
use of resources through an orchestration module which adapts physical tier
pools to work
based on the requirements of the business rules.
12
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
[0033] The AIM module can also monitor the use of the virtual machine (VM)
resources in the cloud, thereby enabling virtual provisioning of personas and
software.
Personas are software components containing metadata relating the component to
a certain
hardware platform which is required for the persona to operate. A few examples
of virtual
machines used herein include VMware Virtual center 2.x, VMWare, ESX VI3
Solaris
Zones, XEN, and Microsoft virtual center. The AIM module also comprises
internal
modules to monitor the computer-coded business rules and the cloud resources
while
working as an interface to the orchestrating module. A few examples of virtual
machines
used herein include VMware Virtual center 2.x, VMWare, ESX VI3 Solaris Zones,
XEN,
and Microsoft virtual center. Web-enabled user interface applications can also
be made
available to the business client and the administrator so that each may access
the cloud
resources, modules and functions of each of the modules including the AIM
service, the
orchestrating module, the service governor module, the alarm module, the SQL
database and
the analysis module.
[0034] FIG. 1 illustrates the architecture of an exemplary embodiment using
a cloud
computing architecture 100 where a business client front end or client
computing device 105
communicates through a network 120, e.g., the internet, with a cloud services
gateway 110
and cloud resources 115. The frontend computing device 105 can be any network-
enabled
computing device, e.g., a personal computer, laptop, palm top computer, tablet
computer,
smart phone, personal data assistant, mobile or cellular phone, or any other
device with at
least one processor, networking capability and one storage unit. The front end
computing
device 105 allows the user to communicate with the IT service provider on new
business
transactions, changes to the SLA, business policies, rules, and the like. The
gateway
computing device 110 is a secure server computing device with at least one
processor,
networking capability and one storage unit configured to execute a web-enabled
user
interface application. The user interface application comprising modules 135
allows a
system administrator to interact with several application modules 135 that
perform functions
including discovery, monitoring, and managing of backend IT resources,
analyzing business
rules and resource consumption, and storing and reporting analytical
information. The
computing device 110 is capable of handling large volume requests, data
analysis and multi-
tasking applications.
13
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
[0035] The client computing device 105 contains a web-enabled user
interface software
application comprising input module 130 that interacts with the backend cloud
services
gateway computing device 110 by providing inputs to application module
components 135
on gateway computing device 110. In the illustrated embodiment, the business
client
defines SLA terms, business policies and business rules on the client
computing device 105,
and this information functions as an input to the service governor application
through the
business rules engine on the gateway computing device. In an exemplary
embodiment, the
business rules broker, or negotiate, with the resource policy to adjust the
cloud resources for
the changing business transaction needs. This enables seamless business to
information
technology (IT) integration between the business client and the IT platform.
The web-
enabled user interface software application 130 contains fields or options to
provide inputs
for metrics that are generated on the cloud services gateway 110. The computer-
coded
business rules output from the cloud services gateway 110 are used to control
the cloud
resources 115.
[0036] The cloud resources 115 include server pools which could function as
a multi-
tier network cloud architecture. The pools 120, 125, 170 reflect a collection
of hardware,
software and persona (or virtual machine) resources that form a web-tier, an
application tier
and a database tier. Depending on the type of business transaction initiated
by a customer
using the business client's online services, the resource pools are adjusted
by moving
hardware resources 140, 145 in pool 120 to pool 125. This allows for re-
allocation of the
resources in the multi-tier cloud architecture. Further, software resources
150, 165 can be
shared between hardware components depending on the requirements of the
business
transaction in effect. The datacenter resources 115 in the form of hardware,
software and
personas (or virtual machines) are monitored by an orchestrator which receives
instructions
from the autonomic infrastructure management ("AIM") module. In some
embodiments,
both modules may be resident on the cloud gateway computing device 135.
[0037] The service governor module receives the business rules from the
application
inputs 130 on the business client computing device 105 and converts the rules
to measurable
metrics in a computer-coded business rules comprising limiting parameters. By
way of
example, without limitation, a business rule within a business policy is
defined by such
features as date and time of utilization, priority level and CPU utilization
parameters at the
14
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
time of implementation. This business rule can be converted to a computer-
coded business
rule which determines the limitations on the resources by the number of
instances and the
scalability options available with the resource, etc. Such information also
allows the AIM
module on the gateway 110 to review and allocate the resources that can be
tied to a
transaction. These resources in Pool 1 120 to Pool 3 170 can then be made
unavailable for
other transactions during the period. This is advantageous when the backend IT
service
provider uses the same cloud resources for multiple business clients. The two
software
resources 150, 165 also represent virtual machines or personas.
[0038] While transferring resources across tiers, the software required for
the
transferred resource may be different from the existing software. One
exemplary
implementation allows software to be ported or enabled on a different server
based on the
function of the server. In some embodiments, sharing of software can be
implemented using
a shared license for multiple systems, where when a first system is activated,
the license for
the software on that system is allocated to that system for a given time
period (e.g., until the
first system is deactivated) and can be de-allocated and allocated to a second
system at a
different time. It is appreciated that the cloud services gateway computing
device 110 may
be a network enabled device similar to device 105 and could be a personal
computer, laptop,
palm tops, Smart Phones, personal data assistant, mobile or cellular phones,
or any other
device with at least one processor, networking capability and one storage
unit.
[0039] The user interface application is used to define business related
limiting
parameters and abstract concepts including business policies and their
associated business
rules. The business rules might include metrics such as discount values and
period of
discount as well as customer tags to identify the user or the transaction
type. These business
rules are automatically converted into limiting parameters in the computer-
coded business
rules using input modules in the user application 130 on the cloud services
gateway 135.
The cloud services gateway 135 can further be comprised of two independent
computing
devices - one which can be automated using intelligent processing and learning
methods and
the other which allows for manual interrupts to the intelligent systems. This
allows the user
to define the initial responses to the system alarms. In some embodiments, the
alarms are
primarily resident within the analysis modules on the cloud services gateway
135. These
alarms could trigger an internal silent alarm to the intelligent system, or
alternatively, the
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
alarms could trigger e-mail or similar messages to the system administrator.
Further, the
business client computing device 105 can be integrated with the cloud services
computing
device 110, wherein the business client computing device defines business
rules and e-mails
them to the cloud services administrator or the cloud computing device. The
administrator
can manually update the service governor or the cloud computing device can be
configured
to deconstruct the e-mail and automatically update the service governor with
the new
business rules.
[0040] The system 100 can be configured to work with third party software
applications
designed as modules to fit within an existing IT architecture. Certain
monitoring
applications like Optier0 core first, BMC and TM-ART can be used as modules
by
altering the input computer-codes of the service governor to accept the
monitoring outputs.
The outputs have to be analyzed along with the business rules to provide some
meaning to
monitoring data in view of the resource usage in SLA. The operating systems
that work
with the frontend 105 and the cloud services gateway 110 computing devices
include,
without limitation, Microsoft Windows , Apple Macintosh 0Sx, Solaris , Linux
and
AIXO. In some embodiments, the user interfaces can be managed using web-
browser
applications like Internet Explorer and Mozilla Firefox0 from a web-enabled
device.
[0041] The information related to utilization of resources, alarms,
business policies and
rules can be stored in storage database 175 which, in some embodiments, may be
a SQL
database. The SQL database can be accessed via the software application 135 on
the
gateway device 110. In some embodiments, the gateway device 110 may be capable
of
running multi-user applications and managing large traffic volumes. The actual
software
applications on the cloud services gateway can be controlled using a web
interface.
[0042] The event handler function modules in the service governor module
allow the
system to generate appropriate action responses in view of the alarms. Some
event handler
function modules are also used by user requests to generate reports or custom
actions from
user interface module 135. The reports function in the user interface module
135 is used to
generate usage statistics of the resources, current real-time status of the
system for each
business transaction or business client, the learning parameters of the
intelligent system, and
related information. The report can be configured to generate invoices with
fee values
calculated for the resources used based on a per unit fee established in the
SLA.
16
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
[0043] Fig. 2 illustrates an exemplary embodiment of the methods and
systems 200 of
this disclosure. A business client 202 defines the SLA 208 along with the
business policies
210 and the business rules 212. This can be done on a web-enabled software
application on
the client frontend as illustrated in Fig. 1 or by mutual agreements between
the business
client and the IT service provider. These definitions are then communicated to
the cloud
services gateway 204. Manual overrides to the business rules or the AIM can be
executed
by direct input into the software user interface 214. The service governor 224
software
module of the disclosure is resident on the gateway for the datacenter
operations as
illustrated in Fig. 1. This exemplary service governor software module accepts
abstract
business rules and policy statements from the business client 202 through the
input module
216 and computes the abstract statements to application logic for the AIM
modules 226.
The abstract business statements may specify exemplary business limitations,
such as a
transaction priority (e.g., in an e-commerce application, ordering can take
priority over
payment, or tracking status transactions). An exemplary application logic 500
generated
using the input business rules and business policy is illustrated in Fig. 5a.
The application
logic is then forwarded to an appropriate AIM 226 for a selected cloud site.
This logic is
stored in the AIM for future implementation. It is appreciated that a failure
in the service
governor module 224 will not affect the functioning of the backend resources
in the
datacenter 206, as a result of the storing the application logic in the AIM
modules 226.
[0044] The exemplary embodiments of the methods described herein enable a
single
service governor 224 module resident in the cloud services gateway 204 to
control multiple
AIM modules 226 located in the service gateway. Alternatively, it is
appreciated that the
AIM modules can be resident in a user interface at the datacenter/cloud
resources 206 for
each of a number of cloud sites. A cloud site, according to the exemplary
embodiments
herein, is a geographically disparate location comprising a number of backend
computing
devices to perform the functional requirements of a datacenter. The backend
computing
devices may be further divided in a multi-tier architecture as discussed above
with reference
to Fig. 1. The AIM 226 can be autonomous software enabled control module that
can
function independent of the service governor module to allocate physical and
virtual
resources of a each respective cloud resource sites 206. The AIM module
converts the
application logic from the service governor module into a resource specific
computer-coded
17
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
logic 510 as illustrated in Fig. 5b. The exemplary embodiments in Fig. 2, also
illustrates an
option of implementing business rules/business policies via a user interface,
where the user
interface interacts with multiple service governor software modules 224 in
different cloud
gateways 204 or the same cloud gateway. Such an implementation would enable
separation
of data and resources for different business clients within a private or
public cloud. A private
cloud is a method of restricting a set of cloud resources to a single business
client (e.g., a
single client company), versus, a public cloud, which allows multiple business
clients to
share a single set of cloud resources.
[0045] Further, according to an exemplary embodiment, each AIM module 226
communicates with an orchestrating and provisioning tool 232. The
orchestrating and
provisioning tool 232 is a software module that is responsible for
implementing the
computer-coded logic from AIM module associated with the cloud site 206.
Exemplary
cloud sites A, B, to X 206, are used to demonstrate the exemplary architecture
of the system
of this disclosure. The physical and virtual resources 234 are monitored by a
monitoring
software sub-module in each AIM module 226. This exemplary architecture allows
different
business transactions to access different cloud sites at any given time.
Further, all the
business transaction requirements, as well as the resource requirements pass
through the
central gateway software module 204 for complete control over remote cloud
sites. An
analytics software module 228 analyzes the usage pattern information from the
monitoring
software sub-module and initiates the alarm processes 230, in the event of a
resource
overuse, under-use, or other related error types. The analytics module keeps
track of the
service governor 224 requirements set forth by the business rules from the
business client to
trigger a related alarm based on the error type. The event handler functions
module 220
comprises software code in the form of automated software functions to inform
the other
sub-modules in the service governor 224 of the alarm generated. In response,
the service
governor set new business rules, generated automatically, or uses manual
overrides to
correct the respective error type. All events generated by the alarm, the
response, and the
resource usage is stored in the storage database 218 for future reporting by
the reports
module 222.
[0046] The method and systems illustrated in Fig 2 also enables a business
client to
control the resources of multiple cloud sites for the client data. The
business client 202 can
18
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
choose to implement certain transaction on a different cloud site, depending
on the costs
associated with the physical resources (e.g., energy costs, data storage
costs, etc.). The AIM
module 226 maintains computer-coded resource policies for monitoring and
adjusting
resources 234 of its connected cloud site 206. The resource policies can be
updated using the
computer-coded business rules from the service governor 224 at any time during
the
operation of the datacenter. However, once the resource policy is set at the
respective AIM
modules, and should the service governor fail, the AIM modules will continue
to control the
backend resources at its respective cloud sites till a new rule is issued.
[0047] Fig. 3 illustrates an exemplary embodiment of a method 300 for
managing the
backend information technology infrastructure by automatically adapting
hardware and
software resources to the dynamic real-time business requirements. Fig. 3 is
an exemplary
implementation of the methods and systems disclosed herein for a single AIM
module
connected to its respective cloud resources 306. It is appreciated that this
exemplary
embodiment can be extended to include multiple cloud sites, with multiple AIM
modules,
where each AIM module controls its respective cloud site, via an orchestrating
and
provisioning tool 346. This extension to multiple sites is illustrated in Fig.
2 as discussed
above. A business client 302 defines the SLA 308 along with the business
policies 310 and
the business rules 312. This can be done on a web-enabled software application
on the
client frontend as illustrated in Fig. 1 or by mutual agreements between the
business client
and the IT service provider. These definitions are then communicated to the
cloud services
gateway 304. Alternatively, the definitions can be made via an e-mail that is
then
deconstructed and its contents are automatically recognized by the input
module 316 of the
cloud services gateway 304. Both the cloud services gateway 304 and the
business client
302 can be computing devices as described in Fig. 1. If the business rules,
business policy
and the SLA are identified by an analyst with the service provider, the
analyst can provide
the information directly to the user interface module 314.
[0048] In one embodiment, the business rules 312 are defined so as to
convert human-
readable logic for business policies 310 into application logic for computer
implementation
via an automated service governor software module 324. The service governor
software
module 324 works with an AIM software module 326 which comprises smaller
modules for
resource discovery 330, monitoring 332, and management 328. The service
governor
19
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
module further comprises a business rules engine module 320 and a business
rules manager
module 318 which feeds the application logic form of the business rules
(computer-coded
business rules and resource policies) to the AIM module 326 for deployment to
the backend
hardware and software resources in the cloud resources 306. The AIM module
deploys the
application logic form of rules via orchestrating and provision modules 346.
The computer-
coded business rules are defined in the business rules engine module 320 while
the
autonomous computer-coded resource policies are defined, with managing
parameters, in
the business rules manager 318. By default, the automatic actions of module
324 select a
response to an alarm from a database of previous computer-coded business rules
in the
business rules engine 320 via the automatic actions module 322. However, the
business
rules engine 320 can be forced to accept a custom rule from module 322, where
the custom
rule is defined by a user on manual intervention as a result of the alarm.
[0049] In another exemplary embodiment, the human-readable logic of the
business
rule can be converted to application-logic with added parameters (managing and
limiting)
which define the intended backend resources, user type, data, time, and
priority of the
transaction that the business rule is intended to cover. The conversion occurs
at module 324
and the application logic business rule output, also called a computer-coded
business rule, is
stored in the business rules engine 320. The business rules manager 318
generates cloud
resource specific computer-coded resource policies which are limited by the
computer-
coded business rules. The managing parameters in the computer-coded resource
policies are
tied to the individual resources (e.g., Apache server, Java server) and define
the number of
available instances, the status of the resources and other related
information. The computer-
coded business rule limits this information with priority, data and time
information for
allocation of resources tied to a particular business transaction.
[0050] The business rules manager 318 interacts with the AIM module 326 to
manage,
discover, and monitor the datacenter or cloud resources 306. When a new
business client is
introduced into the system, the discover datacenter resources 330 module sends
a request to
the orchestrating and provisioning module 346 in the cloud resources 306
asking the module
to determine the resources available, the time of availability, and
capacities. This
information, along with the new client business rules 310 and resource
policies from module
312 is used to allocate resources from the cloud resources 306 for use by the
business client
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
during the business transactions. In other embodiments, once a single
transaction has been
processed, the monitoring module 332 keeps track of the utilization of each of
the resources
focusing on several features including energy usage, processor (CPU) usage and
memory
usage among other available features.
[0051] In an exemplary embodiment, the AIM is an autonomous software module
capable of automatically controlling the resources of its respective cloud
site using
previously set business rules, even if the service governor fails to provide
new rules. The
monitoring module 332 stores the computer coded business rules application
logic from the
service governor 324, and functions autonomously in implementing the business
rules. The
business rules are combined with resource policies from the service governor
to optimize the
use of the respective cloud site 306 resources 344, 348, and 350. Should the
service
governor software module fail to function correctly (e.g., fails to issue new
rules), the
monitoring module 324 continues to monitor and control the resource usage at
the respective
cloud site 306. In the event of a resource error, the monitoring module 324
intimates the
managing module 328 directly for new rules to re-allocate the datacenter
resources 328. This
module 328 then uses the stored business rules and resource policy logic to
generate a new
resource usage rule, thereby correcting the error generated during the
monitoring phase. In
an exemplary implementation of the service governor, the software modules of
the service
governor can be software coded using a Java stack in a Windows or Linux
operating system
machine.
[0052] Further, the analytics module 334 analyzes the raw numbers from the
monitoring module 332 using the computer-coded business rules from the service
governor
324 to determine if the resources are within the rule metrics and generally
within the SLA
requirements. If the analytics module 334 determines that the resources are
under-used,
over-used, that the rules do not match historical resolutions, or other such
noteworthy
occurrences are noted, an alarm 336 is triggered. The alarm could be a message
to the
system administrator via the user interface module 314, an e-mail sent to a
predetermined
list, a short message service ("SMS") message to one or more recipients, an
instant message
or the like.
[0053] In further embodiments, the event handler function module 338
monitors the
alarms and, after reviewing the available actions, triggers a pre-set
response. In one
21
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
embodiment, the module 336 could trigger an alarm to the system administrator
through
event handler 338, and the system administrator can manually edit the computer-
coded
business rules from the rules engine 320 or change the custom rules for the
business policy
via custom rules module 322, thereby setting new rules for the AIM module 326
to facilitate
reallocation of the cloud resources for the transaction. In some embodiments,
the alarm may
be registered at the event handler function module 338 which reviews the alarm
and triggers
an automated intelligent function in custom rules module 322 within the
service governor
324 to select a new computer-coded business rule from the business rules
engine 320, which
then limits and monitors the computer-coded resource policies to prevent an
alarm. This
limitation method by the computer-coded business rules can cause an
intervention at the
AIM module 370 and an adjustment of the resource usage to turn off the alarm.
By way of
example, without limitation, the resource usage should be above 50% and below
90% for
each of the features disclosed above, such as energy usage, processor (CPU)
usage and
memory usage, for each of these resources.
[0054] Further, as illustrated in Fig. 3, the alarm may also add
information from the
analytics module to the storage database 342. The storage database 342
interacts with the
user interface module 314 to present the user with real-time information on
rules, resources
and analytics. Should the user desire a report of a particular rule
implementation, a general
policy implementation comprising a number of rules within the policy, or the
like, the
reports module 340 can be used to combine certain elements from storage
database 342 into
a human-readable report for the user. Alternatively, if the service provider
needs to provide
a monthly usage invoice to the business client, the reports module 340 can be
used in
conjunction with the SLA fee terms from the SLA input 316 to calculate the fee
for resource
usage during a particular period.
[0055] Fig. 4 is an illustration of the use of the system 400 during a
business
transaction according to one embodiment. Fig. 4 is an exemplary implementation
of the
methods and systems disclosed herein for a business transaction, and its
lifecycle with a
single AIM module 444 and a single cloud site 464. It is appreciated that this
exemplary
embodiment can be extended to include business transactions to multiple cloud
sites, with
multiple AIM modules, where each AIM module controls its respective cloud
site, via an
orchestrating and provisioning tool 472. In the illustrated embodiment, the
business client
22
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
owns a web-enabled banking business application 404, such as a website
operated by an IT
service provider, from which the business client offers its customers services
in the form of
business transaction services 408. As illustrated in the figure, an exemplary
banking
business application 404 comprises multiple business transaction options,
including an
account balance inquiry in the transaction services 408. The user chooses this
service and
enters the specific account for which the balance inquiry is being requested.
The cloud
services gateway 412 comprises the service governor module 416 that determines
the
computer-coded business rules that should apply to the transaction depending
on the user
(e.g., frequent user, premium user, time of transaction, etc.). The business
rules engine 424
generates the computer-coded business rule containing the transaction
information and the
metrics for limiting the computer-coded resource policies from the business
rules manager
420. The supplemented computer-coded resource policies are then forwarded to
the AIM
module 444 which determines the resources to be used according to the business
rule for the
chosen transaction.
[0056] Fig. 4 further illustrates the orchestrating module 472 which
performs the
required transaction processes using the resources required by the managing
parameters in
the computer-coded resource policies, thereby incorporating in the database
tier server 475
and the application tier server 476 to respond to the business transaction
request. During
this data-mining operation, the monitoring module 452 monitors the time to
response, the
processor consumption, and memory usage, among other metrics, for the
transaction. As the
number of transactions increases because of additional users on different
computing devices,
and more resources are being consumed, the analytics module 456 combines
information
from the managing and limiting parameters with the utilization parameters from
monitoring
module 452 to determine if the system is functioning within the correct
utilization metrics
defined by the SLA and the business rules for the transaction load. When
alarms are
triggered, the event handler function module 432 reviews the alarm and
responds with an
action to module 428 for manual or automated responses. The business rules
manager 420
is initiated and the rules are altered by an intelligent learning function or
manual function
that feeds the business rules engine 424. The newly altered computer-coded
business rules
add new limitation parameters to the computer-coded resource policies and the
computer-
coded resource policies are applied to the AIM module 444 to rectify the
alarm. In the
23
CA 02821270 2013-06-11
WO 2012/082726 PCT/US2011/064619
absence of an alarm, the monitoring continues normally. The status of the
system is also
updated in the storage database 440.
[0057] The embodiments described above are intended to be exemplary. One
skilled in
the art should recognize that numerous alternative components and embodiments
that may
be substituted for the particular examples described herein and still fall
within the scope of
the invention.
24