Note: Descriptions are shown in the official language in which they were submitted.
WO 2014/151935 PCT/US2014/026698
MISPLACED ITEM DETERMINATION USING RADIO
=
FREQUENCY IDENTIFICATION DATA
10
BACKGROUND
Embodiments of the disclosure relate generally to data processing, and more
particularly to methods and systems for identifying radio-frequency
identification tags or
identifying and configuring a RFID reader.
Radio-frequency identification (RFID) has been used for inventory management,
i.e., by reading identification information stored on RFID tags attached to
various objects,
such as retail products. RFID is a wireless, non-contact system that uses
radio-frequency
electromagnetic fields to transfer data from a tag attached to an object for
automatic
identification and tracking. A conventional RFID system includes one or more
RFID tags
and an RFID reader. Each RFID tag includes a transponder having a radio
frequency
integrated circuit (RFIC) and an antenna for receiving an interrogation signal
from the
RFID reader and emitting a response signal. The RFIC can store identification
information or other data and output such data in the response signal upon
receiving the
interrogation signal. The RFID reader includes an antenna and a transceiver.
The
transceiver includes a transmitter, a receiver, and a decoder for processing
data in the
signal emitted by the RFID tag. The RFID reader can be a mobile, handheld
device, or the
RFID reader can be mounted in a fixed location, depending on the particular
application.
Conventionally, the user of a mobile RFID reader manually enters location
information into the REID reader so that the location of items having RFID
tags can be
determined as the RFID tags are scanned. However, if the manually entered
location
information is incorrect, the location of the scanned RFID tags will also be
incorrect.
CA 2903717 2018-10-04
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
When the antenna of the RFID reader is within an effective range for
activating the
transponder, the transponder is activated by the electromagnetic field from
the antenna of
the RFID reader. Data can be transmitted by the transponder in the RFID tag to
the
transceiver of the RFID reader wirelessly. The transceiver of the RFID reader
can decode
the data received from the transponder. The decoded information can be
processed by the
RFID reader or transmitted to another computing device for processing.
RFID tags may include active, passive, or semi-active transponders. Active and
semi-active transponders are powered by a battery, while passive transponders
obtain
power from the interrogation signal emitted by the RFID reader. Active
transponders can
initiate communication with an RFID reader, whereas passive and semi-passive
transponders are typically activated only when interrogated by the RFID
reader. Multiple
RFID tags may be located in the same radio frequency field and may be read one
at a time
or simultaneously.
SUMMARY
According to various embodiments, RFID tag data can be used to identify a
misplaced or orphaned product or good using, for example, pattern matching
based on one
or more characteristics of several products or goods each having an RFID tag.
For
example, if several products have a common characteristic that is different
than a
characteristic of one other product, the one other product may be considered
misplaced or
orphaned based at least in part on the RFID tag data.
According to embodiments of the present disclosure, a computer-implemented
method of managing inventory includes receiving, at an antenna operatively
coupled to a
radio-frequency identification (RFID) reader, product identification
information encoded
in an RF signal transmitted by a plurality of RFID tags. Each of the RFID tags
is
associated with a respective one of a plurality of products. The method
further includes
processing, by a processor, the product identification information contained
in a portion of
the encoded RF signal to identify a characteristic associated with each of the
products, and
identifying, by the processor using the product identification information,
one of the
products having a characteristic different from another one of the products.
In some embodiments, determining the characteristic may include retrieving, by
the processor from a database, machine-readable product data representing the
characteristic associated with the respective one of the products. In some
embodiments,
2
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
the characteristic may include a product stock keeping unit (SKU) number, a
manufacturer
product number, a brand identifier, a model identifier, a product category, a
department
number, a package quantity, a package identifier, a style, a season, a size,
and/or a color.
In some embodiments, the product identification information may include a
product stock
keeping unit (SKU) number, a manufacturer product number, a brand identifier,
a model
identifier, and/or a product name.
In some embodiments, the method may further include identifying, by the
processor using the product identification information, a majority of the
products having a
characteristic in common, and identifying the at least one of the products
having a
characteristic different from the majority. In some embodiments, the method
may further
include displaying, by the processor via a display, information representing
at least one of
the items having the characteristic different from at least two other
products. In some
embodiments, the product identification information may be read over a
predetermined
period of time.
According to embodiments of the present disclosure, an inventory management
system includes a programmable processor, and a memory operatively coupled to
the
processor. The memory has stored thereon computer-executable instructions that
when
executed by the processor cause the processor to receive, at an antenna
operatively
coupled to a radio-frequency identification (RFID) reader, product
identification
information encoded in an RF signal transmitted by a plurality of RFID tags.
Each of the
RFID tags is associated with a respective one of a plurality of products. The
memory has
further stored thereon computer-executable instructions that when executed by
the
processor cause the processor to process the product identification
information contained
in a portion of the encoded RF signal to identify a characteristic associated
with each of
the products, and identify, using the product identification information, one
of the products
having a characteristic different from another one of the products.
In some embodiments, the memory may further include instructions that when
executed by the processor cause the processor to determine the characteristic
by retrieving,
from a database, machine-readable product data representing the characteristic
associated
with the respective one of the plurality of products. In some embodiments, the
memory
may further include instructions that when executed by the processor cause the
processor
to identify, using the product identification information, a majority of the
products having
3
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
a characteristic in common based on the product identification information,
and identify
the at least one of the products having a characteristic different from the
majority.
In some embodiments, the memory may further include instructions that when
executed by the processor cause the processor to display, via a display,
information
representing the at least one of the items having the characteristic different
from at least
two other products.
According to embodiments of the present disclosure, a non-transitory computer-
readable medium has stored thereon computer-executable instructions that when
executed
by a computer cause the computer to receive, at an antenna operatively coupled
to a radio-
frequency identification (RFID) reader, product identification information
encoded in an
RF signal transmitted by a plurality of RFID tags, process a portion of the
encoded RF
signal to identify a characteristic associated with each of a plurality of
products based on
the product identification information, and identify, using the product
identification
information, one of the products having a characteristic different from
another one of the
.. products. Each of the plurality of RFID tags is associated with a
respective one of the
products.
In some embodiments, RFID readers can use different interrogation modes to
read
RFID tags. The choice of which interrogation mode to use may, for example, be
based at
least in part on which interrogation mode is most suitable for the task at
hand (e.g., reading
.. all RFID tags or reading only previously unread RFID tags). When several
different tasks
are to be performed, it is advantageous to select an interrogation mode or
modes that are
most suitable for completing the different tasks in an efficient and effective
manner.
According to embodiments of the present disclosure, a computer-implemented
method of managing inventory performed by a processor includes receiving in a
digital or
.. analog format, from a first computing device, a first request for first
radio frequency
identification (RFID) tag data associated with a first plurality of RFID tags
and receiving
in a digital or analog format, from a second computing device, a second
request for second
RFID tag data associated with a second plurality of RFID tags. In response to
the first
request and the second request, the method further includes automatically
selecting a
.. selected one of a first interrogation mode and a second interrogation mode
based on the
first request and the second request, and automatically transmitting
configuration
information to an RFID reader to operate in the selected interrogation mode.
4
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
In some embodiments, the second plurality of RFID tags may include a portion
of
the first plurality of RFID tags, and the second RFID tag data may include a
portion of the
first RFID tag data. In some embodiments, operating in the selected
interrogation mode
may cause the RFID reader to read the first RFID tag data and the second RFID
tag data
.. using the fewest number of RFID tag read operations. In some embodiments,
operating in
the selected interrogation mode may cause the RFID reader to read the first
RFID tag data
and the second RFID tag data in the least amount of time.
In some embodiments, the method may include receiving the first RFID tag data
from the first plurality of RFID tags via the RFID reader while the RFID
reader is
operating in the selected interrogation mode, receiving the second RFID tag
data from the
second plurality of RFID tags via the RFID reader while the RFID reader is
operating in
the selected interrogation mode, transmitting the first RFID tag data to the
first computing
device, and transmitting the second RFID tag data to the second computing
device.
In some embodiments, the selected interrogation mode may be automatically
selected when the first request and the second request each include a request
to receive
RFID tag data via the RFID reader from a common subset of the plurality of
RFID tags.
In some embodiments, the common subset of the plurality of RFID tags may
include
previously read ones of the plurality of RFID tags. In some embodiments, the
method
may include automatically configuring the RFID reader to operate in one of an
Electronic
Product Code (EPC) Gen2 standard-compatible session 0, 1, 2 and 3 and/or
automatically
configuring a pre-selection criterion filter of the RFID reader based on the
selected one of
the first interrogation mode and the second interrogation mode.
In some embodiments, the RFID reader may be a first RFID reader, and the
method may include automatically transmitting configuration information to a
second
RFID reader to operate in an interrogation mode different than the selected
one of the first
interrogation mode and the second interrogation mode. In some embodiments, the
method
may further include receiving the first RFID tag data from the first plurality
of RFID tags
via the first RFID reader while the first RFID reader is operating in the
selected one of the
first interrogation mode and the second interrogation mode, receiving the
second RFID tag
data from the second plurality of RFID tags via a second RFID reader while the
second
RFID reader is operating in an interrogation mode different than the selected
one of the
first interrogation mode and the second interrogation mode, transmitting the
first RFID tag
5
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
data to the first computing device, and/or transmitting the second RFID tag
data to the
second computing device.
According to embodiments of the present disclosure, an inventory management
system includes a programmable processor, and a memory operatively coupled to
the
processor. The memory has stored thereon computer-executable instructions that
when
executed by the processor cause the processor to receive in a digital or
analog format,
from a first computing device, a first request for first radio frequency
identification
(RFID) tag data associated with a first plurality of RFID tags and receive in
a digital or
analog format, from a second computing device, a second request for second
RFID tag
data associated with a second plurality of RFID tags. The memory has further
stored
thereon computer-executable instructions that when executed by the processor
cause the
processor to, in response to the first request and the second request,
automatically select a
selected one of a first interrogation mode and a second interrogation mode
based on the
first request and the second request, and automatically transmit configuration
information
to an RFID reader to operate in the selected interrogation mode.
In some embodiments, the second plurality of RFID tags may include a portion
of
the first plurality of RFID tags, and the second RFID tag data may include a
portion of the
first RF1D tag data. In some embodiments, operating in the selected
interrogation mode
may cause the RFID reader to read the first RFID tag data and the second RFID
tag data
using the fewest number of RFID tag read operations. In some embodiments,
operating in
the selected interrogation mode may cause the RFID reader to read the first
RFID tag data
and the second RFID tag data in the least amount of time.
In some embodiments, the memory may further include instructions that when
executed by the processor cause the processor to receive the first RFID tag
data from the
first plurality of RFID tags via the RFID reader while the RFID reader is
operating in the
selected interrogation mode, receive the second RFID tag data from the second
plurality of
RFID tags via the RFID reader while the RFID reader is operating in the
selected
interrogation mode, transmit the first RFID tag data to the first computing
device, and
transmit the second RFID tag data to the second computing device.
In some embodiments, the selected interrogation mode may be automatically
selected when the first request and the second request each include a request
to receive
RFID tag data via the RFID reader from a common subset of the plurality of
RFID tags.
In some embodiments, the common subset of the plurality of RFID tags may
include
6
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
previously read ones of the plurality of RFID tags. In some embodiments, the
memory
may further include instructions that when executed by the processor cause the
processor
to automatically configure the RFID reader to operate in one of an Electronic
Product
Code (EPC) Gen2 standard-compatible session 0, 1, 2 and 3 and/or automatically
configure a pre-selection criterion filter of the RFID reader based on the
selected
interrogation mode.
According to embodiments of the present disclosure, a non-transitory computer-
readable medium has stored thereon computer-executable instructions that when
executed
by a computer cause the computer to receive in a digital or analog format,
from a first
computing device, a first request for first radio frequency identification
(RFID) tag data
associated with a first plurality of RFID tags and receive in a digital or
analog format,
from a second computing device, a second request for second RFID tag data
associated
with a second plurality of RFID tags. The non-transitory computer-readable
medium has
further stored thereon computer-executable instructions that when executed by
a computer
cause the computer to, in response to the first request and the second
request,
automatically select a selected one of a first interrogation mode and a second
interrogation
mode based on the first request and the second request, and automatically
transmit
configuration information to an RFID reader to operate in the selected
interrogation mode.
In some embodiments, the non-transitory computer-readable medium may have
stored thereon computer-executable instructions that when executed by a
computer cause
the computer to receive the first RFID tag data from the first plurality of
RFID tags via the
RFID reader while the RFID reader is operating in the selected interrogation
mode,
receive the second RFID tag data from the second plurality of RFID tags via
the RFID
reader while the RFID reader is operating in the selected interrogation mode,
transmit the
first RFID tag data to the first computing device, and transmit the second
RFID tag data to
the second computing device.
According to embodiments of the present disclosure, a computer-implemented
method of managing inventory includes receiving, at an antenna operatively
coupled to a
radio-frequency identification (RFID) reader, product identification
information encoded
in an RF signal transmitted by a plurality of RFID tags. Each of the RFID tags
is
associated with a respective one of a plurality of products. The method
further includes
processing, by a processor and using the product identification information,
information
contained in a portion of the encoded RF signal to compare apparent location
information
7
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
associated with the RFID reader with prior location information associated
with at least
one of the products, and updating, by the processor, the apparent location
information to
match the prior location information where the apparent location information
is different
than the prior location information. In this manner, the location of the RFID
reader may
be updated if the apparent location information (e.g., manually entered
location) is
incorrect.
In some embodiments, comparing the apparent location information may include
retrieving, by the processor from a database, machine-readable product data
representing
the prior location information associated with each of the products. In some
embodiments,
updating the apparent location information may further include updating the
apparent
location information to match the prior location information where the prior
location
information associated with a majority of the products is different from the
apparent
location information. In some embodiments, the prior location information may
include
product location information associated with at least one of the products
received on at
least two different occasions prior to comparing the apparent location with
the prior
location information.
In some embodiments, the method may include displaying, by the processor via a
display, the prior location information and/or the apparent location
information. In some
embodiments, the prior location information and the apparent location
information may
each represent at least one physical location. In some embodiments, the method
may
further include displaying, by the processor via the display, information
representing the
physical location(s).
In some embodiments, the product identification information may be received
while the physical location of the reader is substantially static. In some
embodiments, the
product identification information may be read over a predetermined period of
time.
According to embodiments of the present disclosure, an inventory management
system includes a programmable processor, and a memory operatively coupled to
the
processor. The memory has stored thereon computer-executable instructions that
when
executed by the processor cause the processor to receive, at an antenna
operatively
coupled to a radio-frequency identification (RFID) reader, product
identification
information encoded in an RE signal transmitted by a plurality of RFID tags.
Each of the
RFID tags is associated with a respective one of a plurality of products. The
memory has
further stored thereon computer-executable instructions that when executed by
the
8
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
processor cause the processor to process, using the product identification
information,
information contained in a portion of the encoded RE signal to compare
apparent location
information associated with the RFID reader with prior location information
associated
with each of the products, and update the apparent location information to
match the prior
location information where the apparent location information is different than
the prior
location information.
In some embodiments, the memory may further include instructions that when
executed by the processor cause the processor to compare the apparent location
information by retrieving, from a database, machine-readable product data
representing
the prior location information associated with each of the products. In some
embodiments,
the memory may further include instructions that when executed by the
processor cause
the processor to update the apparent location information to match the prior
location
information where the prior location information associated with a majority of
the
plurality of products is different from the apparent location information. In
some
embodiments, the prior location information may include product location
information
associated with the respective one of the plurality of products received on at
least two
different occasions prior to comparing the apparent location with the prior
location
information.
In some embodiments, the memory may further include instructions that when
executed by the processor cause the processor to display, via a display, the
prior location
information and/or the apparent location information. In some embodiments, the
prior
location information and the apparent location information each represent at
least one
physical location. In some embodiments, the memory may further include
instructions
that when executed by the processor cause the processor to display, via a
display,
information representing the at least one physical location.
In some embodiments, the product identification information may be received
while the physical location of the reader is substantially static. In some
embodiments, the
product identification information may be read over a predetermined period of
time.
According to embodiments of the present disclosure, a non-transitory computer-
readable medium has stored thereon computer-executable instructions that when
executed
by a computer cause the computer to receive, at an antenna operatively coupled
to a radio-
frequency identification (RFID) reader, product identification information
encoded in an
RF signal transmitted by a plurality of RFID tags. Each of the plurality of
RFID tags is
9
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
associated with a respective one of a plurality of products. The non-
transitory computer-
readable medium has further stored thereon computer-executable instructions
that when
executed by a computer cause the computer to process, using the product
identification
information, information contained in a portion of the encoded RF signal to
compare
apparent location information associated with the RFID reader with prior
location
information associated with at least one of the products, and update the
apparent location
information to match the prior location information where the apparent
location
information is different than the prior location information.
In some embodiments, the prior location information may include product
location
information associated with the at least one of the plurality of products
received on at least
two different occasions prior to comparing the apparent location with the
prior location
information.
Any combination and/or permutation of embodiments is envisioned. Other objects
and features will become apparent from the following detailed description
considered in
.. conjunction with the accompanying drawings. It is to be understood,
however, that the
drawings are designed as an illustration only and not as a definition of the
limits of the
invention.
BRIEF DESCRIPTION OF THE DRAWINGS
The accompanying drawings are not intended to be drawn to scale. In the
drawings, each identical or nearly identical component that is illustrated in
various figures
is represented by a like numeral. For purposes of clarity, not every component
may be
labeled in every drawing. In the drawings:
FIG. 1 depicts an example plan view of a retail store for illustrating certain
aspects
of embodiments described herein;
FIG. 2 depicts an example perspective view of a shelf containing various RFID-
tagged products for illustrating certain aspects of embodiments described
herein;
FIG. 3 depicts an example of an RFID reader, antenna and computing device, in
accordance with embodiments described herein;
FIG. 4 is an example flow diagram of a process of identifying misplaced or
orphaned items, in accordance with embodiments described herein;
FIG. 5 is an example block diagram of an inventory management environment, in
accordance with embodiments described herein;
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
FIG. 6A is an example flow diagram of a process for automatically configuring
an
RFID reader, in accordance with embodiments described herein;
FIG. 6B is an example flow diagram of a process for providing RFID tag data,
in
accordance with embodiments described herein;
FIG. 7 is an example flow diagram of a process of determining the location of
an
RFID reader, in accordance with embodiments described herein;
FIG. 8 is an example block diagram of an RFID tag for use with embodiments
described herein;
FIG. 9 is an example functional block diagram of an RFID reader for use with
embodiments described herein;
FIG. 10 is an example block diagram of an inventory management system for
canying out one or more embodiments;
FIG. 11 is an example block diagram of an inventory management system for
canying out embodiments described herein; and
FIG. 12 is an example functional block diagram of a client-server inventory
management environment for implementing embodiments described herein.
DETAILED DESCRIPTION
According to various embodiments, computer-implemented methods, computer-
readable media and physical inventory management systems are disclosed for
identifying
radio-frequency identification (RFID) tags, identifying and configuring a RFID
reader or
are disclosed for identifying RFID tags and RFID readers and configuring the
RFID
reader.
Exemplary embodiments of the present disclosure provide for computer-
implemented methods, computer readable media and physical inventory management
systems that identify misplaced or orphaned products or other goods using
radio frequency
identification tags. As used herein, the terms misplaced and orphaned can each
refer to one
or more items that are located in an undesired location within a retail store;
that is, a
misplaced item is an item that is not where it is supposed to be. While
conventional
inventory tracking techniques use RFID technology to manage inventory supplies
in a
particular retail store, these techniques do not identify products or other
goods that are
misplaced or orphaned.
11
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
Exemplary embodiments of the present disclosure also provide for computer-
implemented methods, computer-readable media and physical inventory management
systems that automatically configure radio frequency identification (RFID)
readers in
response to different requests for various RFID tag data. The RFID reader can
be
configured in such a way as to read the requested RFID tag data based on the
requests.
Exemplary embodiments of the present disclosure further provide for computer-
implemented methods, computer-readable media and physical inventory management
systems are disclosed for identifying the location of a mobile radio frequency
identification (RFID) reader using RFID tag data.
As will be understood by one of skill in the art, RFID tags, and the data
received
from the RFID tags, can be used to identify individual items, such as goods,
in various
environments (e.g., a retail store, warehouse, storage facility, manufacturing
facility,
freight container, staging area or other space). Being able to identify each
item using
RFID offers many useful advantages for, among other purposes, inventory
management.
As used herein, the term inventory management includes, but is not limited to,
tracking the
presence, location and/or quantity of various items in one or more
environments. For
example, it may be desirable to track when an item arrives at a store, where
the item is
located in the store, and when the item leaves the store. Such inventory
tracking can be
accomplished using data read from the RFID tags associated with the various
items.
In a retail environment, various products or other goods are usually stocked
at
specific locations within a store. FIG. 1 depicts a plan view of an exemplary
retail store
100 having various locations (e.g., departments) indicated at A-L throughout
the store.
Merchandise items may be stocked at any location A-L in the store 100. It will
be
understood that the store 100 may include any number of distinct locations for
stocking
merchandise items. For example, men's clothing may be stocked in one location
while
women's clothing may be stocked in a different location. Furthermore, often
multiple
units of the same products are stocked together, for example, twenty pairs of
Brand A
men's jeans may be arranged in one pile on a display shelf, and another twenty
pairs of
Brand B men's jeans may be arranged in a separate pile on the same shelf or a
different
display shelf in the same department. In addition to items that are stocked in
retail areas,
some items may be stored or held in other areas, such as backrooms, loading
docks,
storage containers or storage closets.
12
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
In one example, multiple items of one product may be preferably stocked in one
or
more usual locations, such as men's clothing in the men's clothing department
A, and
women's clothing in the women's clothing department B. Certain products may be
stocked in more than one location (e.g., departments A and F), or temporarily
moved to a
different location, such as a more prominent location near a store entrance
102 during a
promotional event. Certain products may be temporarily held in a stockroom or
other
location prior to or after being moved to a usual location. Thus, while the
items are at the
store, they may be placed in more than one location before they are sold to
customers and
taken from the store. According to some embodiments, it is desirable to
identify the
location of the items using, for example, RFID technology, such as by using
RFID tag
readers to read RFID tags associated with the various items.
Any item that is not in one of the usual locations for that item is considered
to be
misplaced or orphaned. For instance, this occurs when a customer picks up an
item from
its usual location (e.g., Department A), and then goes to a different part of
the store (e.g.,
Department B). While at the different location, the customer decides not to
purchase the
item and places it on a nearby shelf, at which point the item may be
considered misplaced
or orphaned.
FIG. 2 is a perspective view of an exemplary retail store shelf 210 upon which
various merchandise items 220, 230, 240 and 250 are placed. The shelf 210 may,
for
example, be located in any one of the departments A-L in the store 100 of FIG.
1. In this
example, the shelf 210 contains eight pairs of Brand A men's jeans 220, five
pairs of
Brand B men's jeans 230, one pair of Brand C women's jeans 240, and a package
of
playing cards 250. RFID tags 260 attached to each item contain product
identification
data that, when read, or scanned, by an RFID reader located within the reading
range of
the RFID tags, can be used to identify individual units of stock. The data may
include, but
not be limited to, transponder identification, product identification,
location information,
Universal Product Codes (UPC). and/or Electronic Product Codes (EPC). The EPC
is a
standardized identifier that provides a permanent and unique digital, machine-
readable
identity for all products. In some embodiments, each RFID tag 260 includes a
transponder
that is configured to emit a machine-readable signal containing the product
identification
data for uniquely identifying the item and/or location of the item to which it
is attached.
The transponder can be active, passive or battery assisted passive. If the
transponder is
passive or battery assisted passive, and power can be applied (e.g., to an
antenna within
13
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
range of the RFID tag) to provoke the RFID tag to emit a signal. If the RFID
tag is active,
such power may not be necessary.
FIG. 3 depicts an exemplary RFID reader 300. In some embodiments, the RFID
reader can be mobile (e.g., handheld), having an antenna 310 for receiving the
product
identification information stored in the RFID tag and a display 320 for
displaying the
product identification information or other information, such as an indication
of whether
an item is misplaced or orphaned, to a user. The RFID reader 300 can, in some
embodiments, further identify the location (e.g., Department A-L) in which it
is being
used. The RFID reader 300 may, for example, include a R1000/R2000 RFID
integrated
circuit (IC) chip, manufactured by Impinj. Inc. of Seattle, Washington. The
RFID reader
300 can be configured to receive and process the signal emitted by the RFID
tag 260 while
the antenna 310 is within reading range of the signal. In some embodiments,
the antenna
can be separate from the RFID reader 300, for example, antenna 312, which can
be
mounted on a wall, shelf or ceiling, and remotely connected to the RFID
reader. In some
embodiments, the RFID reader 300 is not mobile, but instead in a fixed
location.
In operation, the RFID reader 300 communicates with the RFID tags 260 in a
conventional manner. For example, with a passive RFID tag 260, the RFID reader
300
interrogates and powers the RFID tag 260 so that the RFID tag 260 communicates
information stored in the RFID tag 260 to the RFID reader 300. The RFID reader
300
then processes the information and/or transmits the information to a remote
computer 330
for further processing.
Each RFID reader 300 can be associated with a reader antenna, such as antenna
310 (e.g., via a wired connection) or fixed position antenna 312 (e.g., via a
wireless
connection). In an embodiment, the RFID reader 300 is a handheld, mobile unit
that can
be carried to different locations A-L in the retail store 100. The associated
antenna 310 is
placed into proximity of the reading range of the RFID tags 260, and the RFID
tags 260
are read. In another embodiment, the RFID reader 300 is mobile, but the
associated
antenna 310 is located in a fixed position within reading range of the RFID
tags 260. In
yet another embodiment, the RFID reader 300 is located in a fixed position and
connected
(e.g., through a communication network) with the fixed position antenna 312.
The size
and configuration of the antennas 310 and 312 can be designed to provide
various reading
ranges (e.g., one antenna for coverage of the entire shelf 210 or multiple
antennas for
14
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
coverage of different portions of the shelf 210), as will be understood by one
of skill in the
art.
In an alternate embodiment a retail environment, such as the retail store 100
of
FIG. 1, is potentially susceptible to multipath errors due to metal or other
structures in the
store 100 that reflect the electromagnetic waves emitted and received by the
RFID antenna
300, 302. Multipath errors are caused when a radio signal is received directly
by an
antenna and when the same signal is received again as it is reflected off an
interfering
structure. The use of preprocessing filters can minimize the effects of
multipath by
filtering out erroneous signals.
The RFID reader 300 can extract and process the product identification data,
or
other data (e.g., a transponder identification code), contained in the signal.
In some
embodiments, the product identification data may include, for example, a stock
keeping
unit (SKU) number, an Electronic Product Code, a manufacturer product number,
a brand
identifier, a model identifier, a product category, a department number, a
style, a package
quantity (e.g., six units per package, twelve units per package, etc.), a pack
type identifier,
a season, a size, and/or a color associated with the product to which the RFID
tag is
attached. In some other embodiments, the data received from the RFID tag can
be used to
identify the product in other ways, such as by cross-referencing the RFID tag
data to
product data stored in a database. The product data may include one or more
characteristics associated with the product, such as brand name, product name
or model
number, product category (e.g., men's pants, vitamins, paper towels. etc.),
SKU number,
manufacturer identification number, or other characterizing information. In
the example
of FIG. 2, items 220 and 230 are both men's jeans, while items 240 is a pair
of women's
jeans and item 250 is a pack of playing cards. Accordingly, all of the items
220 and 230
share a common characteristic, i.e., they are all men's jeans, while items 240
(women's
jeans) and 250 (playing cards) are not men's jeans. In this example, it is
therefore likely
that either or both of items 240 and 250 are misplaced or orphaned because
they are
located on the same shelf 210 as the men's jeans 220 and 230, which have a
characteristic
in common.
The product identification data received from the RFID tag 260 can be
collected
and analyzed, e.g., using pattern matching, to identify misplaced or orphaned
items.
Generally, the product identification data is received from each of the RFID
tags 260 over
a limited period of time (e.g., several seconds or minutes) and/or while the
RFID reader
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
300 is in a substantially static location so as to avoid reading RFID tags
from other
products in different locations (e.g., if the RFID reader 300 or antenna 310
is moved to a
different location). It may, for example, be presumed that the RFID tags 260
do not move
substantially while the product identification data is being acquired by the
RFID reader
300. If multiple items 220, 230, 240, 250 have a characteristic in common, or
any other
distinctive comparison that can be obtained using the product identification
information, it
can be determined whether any of the items 220, 230, 240, 250 having a
different
characteristic among all of the items scanned by the RFID reader are, or are
likely to be,
misplaced or orphaned. One or more characteristics associated with the items
220, 230,
240, 250 may be determined, for example, using the product identification data
directly or
by cross-referencing the product identification information with product
characteristics
stored in a database. For example, a product may be associated with
characteristics such
as brand name, model number, SKU number, and/or manufacturer identification
number.
In some embodiments, the location of the RFID reader 300 can be determined
using one or more positioning algorithms, such as those utilizing the Global
Positioning
System (GPS) or fixed position beacons, or by cross-reference to predetermined
locations
of the fixed antenna 312 using a Wi-FiO location-determining system or video
analytics.
The rate at which RFID tag data is read by the RFID reader 300 is based at
least in
part on the interrogation mode of the RFID reader 300 and/or the settings of
the RFID tags
260, and may depend on the nature of the task to be performed using the RFID
tag data.
Examples of such tasks include tracking the ingress and/or egress of items for
inventory
control, and tracking the location of items in inventory for location control.
For instance,
when an item arrives at the store, it may be desirable to read the associated
RFID tag 260
once as early as possible after arrival so that the presence of the associated
item in the
store is known. However, once the presence of the item is known, it may not be
necessary
to re-read the same RFID tag 260 on a repeated basis, for instance, while the
item is
stocked on the floor of the store, for the purpose of tracking the presence of
the item. On
the other hand, it may be desirable to read the same RFID tag 260 more than
once for the
purpose of tracking the location of the item so that the known location of the
item is
current in the event that the item is moved from one location to another.
Some conventional RFID readers have several limitations that may affect their
performance under certain conditions. For instance, the rate at which RFID
tags can be
read depends on several factors, including the number of tags to be read and
the amount of
16
WO 2014/151935 PCT/US2014/026698
data to be read. Many conventional RFID readers can only read one or a small
number of
RFID tags simultaneously, thus requiring a sequential polling process for
reading multiple
RFID tags. As a result, it can take a significant amount of time to read a
large number of
RFID tags. Some RFID readers can be configured to operate in different
interrogation
modes for reading REID tags in different ways. For example, in a first
interrogation
mode, all RFID tags within reading range of the interrogation signal may be
read
regardless of whether or not the tag has been previously read by the same or a
different
RFID reader. One advantage of the first interrogation mode is that every RFID
tag will be
read, providing current data representing associated items located within the
reading range
of the RFID reader. However, one disadvantage of the first interrogation mode
(e.g., using
EPC C1G2 standard protocol) is that the total time to complete the RFID tag
reads is
relatively long, increasing the risk that while some RFID tags are being read,
others may
arrive or depart from the reading range of the RFID reader undetected.
Furthermore, in a
large area, such as the sales floor of a large retail store, many RFID tags
may only have
power for brief moments of time as they are moved from one location to
another. In that
case many such RFID tags may miss a read cycle of the RFID reader and
consequently not
be detected as the associated items move out of an area being inventoried
before a new
read cycle begins.
By contrast, in a second interrogation mode, only those RFID tags that have
not
been previously read may be read by the RFID reader. One advantage of the
second
interrogation mode is that, because it is likely that a smaller population of
RFID tags are to
be read, it is more likely that any RFID tags that have not yet been read are
read relatively
promptly and do not pass undetected. However, one disadvantage of the second
interrogation mode is that any RFID tags that have been previously read and
subsequently
moved to a different location may not be detected at the different location.
Therefore, according to some embodiments, it is desirable to automatically
configure the RFID reader 300 to operate in the interrogation mode that will
read the
RFID tag data needed for performing the desired task. One related technique
for
automatically configuring an RFID reader is disclosed in U.S. Patent
Application Serial
No. 12/900,201 by Wilkinson et al., entitled "Method and Apparatus Pertaining
to Use of
a Plurality of Different RFID Tag Interrogation Modes" and published as U.S.
Patent
Application Pub. No. 2012/0086554.
17
CA 2903717 2018-03-19
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
In some embodiments, the first interrogation mode and the second interrogation
mode can comprise any of the four sessions supported by the Electronic Product
Code
(EPC) Gen2 standard, as will be understood by one of skill in the art. For
instance, the
first interrogation mode may be session 2 or 3, and the second interrogation
mode may be
session 1. Each EPC GEN 2 compliant tag has two states per session: "A" and
"B." The
"A" state comprises the default state and hence represents the tag's state
when initially
powering up. Once a tag has been read its state changes from "A" to "B."
During the "A"
state a tag will respond to any reader that offers a session query. During the
"B" state the
tag will not again respond to a reader using the same session query. EPC
Gen2's four
different sessions provide for differences with respect to how a read tag
persists a "B"
state. In Session "0" a read tag will persist this "B" state until power is
lost and then the
tag reverts immediately to the "A" state. In Session "1" a read tag will
persist its "B" state
for a period of time ranging from 500 milliseconds to 5 seconds and will then
automatically revert to the "A" state. In Session "2" and "3" a read tag will
remain in the
"B" state until power is lost. Then, once power is lost, the read tag will
persist its "B" state
for at least an additional 2 seconds (the actual persistence duration is left
to the
manufacturer and can reach minutes in some cases). Generally speaking, for
many
application settings it may be useful for the first interrogation mode to
comprise an EPC
Gen2 standard-compatible session 2 or session 3 interrogation mode. In this
case, "A"
state tags are read and then remain quiet and will not respond to further same-
session
queries unless and until power has been absent for at least 2 seconds and
possibly longer
(depending upon the characterizing performance of the tags themselves).
It will be understood that any number of different interrogation modes or
other
operating modes of RFID readers supporting other standards may be utilized in
accordance with various embodiments, and the disclosed examples are not
intended to be
limiting. For example, in some embodiments, the RFID reader can be configured
with one
or more pre-selection criteria. In such a configuration, the RFID can
determine whether
the RFID data received from an RFID tag meets the pre-selection criteria, and
discard or
filter out any RFID data that does not meet the pre-selection criteria. Other
data that meets
.. the pre-selection criteria may be processed further (e.g., sent to another
device or system,
etc.). In another example, in some embodiments, the RFID reader can be
configured using
certain C1G2 optimization techniques, as will be understood by one of skill in
the art.
18
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
In another embodiment, the product identification data can be received from
the
RFID tag 260 more than once over a period of time, for example, once per hour,
once per
day, etc. Thus, historical information about the items and the location of the
items can be
accumulated over time and stored, for example, in a memory or database. For
example,
the product identification data associated with the men's jeans 220 can be
read by the
RFID reader 300 at time tj while the jeans 220 are stored in a first location
(e.g., a
backroom), and subsequently read by the same RFID reader 300 at a later time
/2 after the
jeans 220 have been moved from the first location to a second location (e.g.,
Department
A). In this manner, a history of the location of the jeans 220 can be
established. The
RFID tags 260 may be read multiple times while the jeans 220 are at the second
location.
In some embodiments, the RFID reader 300 is in a handheld or portable device.
Before reading an RFID tag 260, the location of the RFID reader 300 is input
by the user
via, for example, the user interface 320 of the RFID reader 300. This
technique depends
on the user to input the correct location when moving the mobile RFID reader
300 from
one location to another because the location of the RFID reader 300 is used to
determine
the location of the RFID tags 260, and thus the location of the associated
products. If the
incorrect location is input, or if the updated location is not input when the
RFID reader
300 is moved from one location to another, then the product information data
corresponding to the RFID tags 260 being read will contain incorrect location
information.
Data collected by the RFID reader 300 can be used to identify items that have
moved over time. For example, if a user of the RFID reader 300 is on the sales
floor and
reads an RFID tag 260 that was previously read in the backroom, the location
of the RFID
tag 260 can be updated to reflect having been moved from the backroom to the
sales floor.
However, in many instances, groups of products (e.g., two, three, four, five,
six, seven,
eight, nine, or ten or more) are not moved from one location in the store 100
to another
location often, particularly after the products have been placed into stock on
the sales
floor. Therefore, the data collected by the RFID reader 300 can also be used
to
automatically identify the location of the RFID reader 300 based on the
historical
information for the RFID tags 260, including historical product location
information. For
instance, if the jeans 220 have been at location A for several consecutive
RFID tag reads,
the next time the RFID tags 260 for the jeans 220 are read, it can be assumed
that the
jeans, and therefore the RFID reader 300, are still at location A, even if the
user entered an
incorrect location into the RFID reader 300. Accordingly, the historical
product location
19
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
information can be used to determine if the user-entered location of the RFID
reader 300 is
consistent with the previously known location of the RFID tags 260 and to
correct the
location of the RFID reader 300 if it was incorrectly entered by the user or
if the user
moved to a different location without updating the location of the RFID reader
300. For
example, if the user of the RFID reader 300 indicated that the reader 300 was
being used,
for example, in the backroom of the store 100 to read RFID tags for a certain
product, but
previously the same reader 300 was used to read the same tags on the sales
floor of the
store 100, it can be determined that the user-entered location of the reader
300 is incorrect
based on the discrepancy (i.e., the reader 300 is most likely being used on
the sales floor
where the tags were previously read, and not in the backroom as indicated by
the user).
As described herein, exemplary embodiments of the present disclosure can be
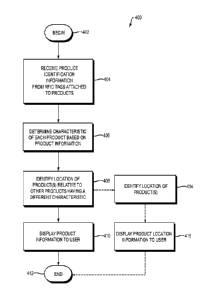
implement to identify misplaced or orphaned products in a store. FIG. 4 is a
flow diagram
of one example of a computer-executable process 400 for identifying such
misplaced or
orphaned products using RFID tags. Process 400 begins at step 402. At step
404, product
identification information, or other data that can be used to uniquely
identify a product, is
received from a plurality of RFID tags (e.g., RFID tag 260 of FIG. 2). Each
RFID tag is
attached to a product directly or indirectly (e.g., products 220, 230, 240 and
250 of FIG.
2). The product identification information can be received using, for example,
an RFID
reader (e.g., RFID reader 300).
At step 406, one or more characteristics associated with each of the products
can
be determined based on the product identification information or other data
received from
the RFID tags, such as discussed above. At step 408, the location of any first
product
relative to one or more other products each having at least one different
characteristic than
the first product can be identified. For instance, any product having a
characteristic that is
different from at least two other products in the same location may be
identified as
misplaced or orphaned. For example, referring to FIG. 2, items 240 and 250
(one of each)
have different characteristics (women's jeans, playing cards) than items 220
(men's jeans,
quantity of eight) and 230 (men's jeans, quantity of five). Accordingly, items
240 and 250
can each be identified as misplaced or orphaned. At step 410, information
about the first
product (e.g., product name, SKU number. or other identifying information) can
be
displayed to a user, for instance on the display 320 of the RFID reader 300.
At step 412,
process 400 ends.
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
In one embodiment, at step 414, the location of the first product can be
identified.
For example, the location of the misplaced or orphaned can be determined based
on the
usual location of the other items that are not identified as misplaced or
orphaned. For
instance, in the above example, items 240 and 250 were identified as misplaced
or
orphaned based on the presence of more than two each of items 220 and 230.
Therefore,
because the location of items 240 and 250 is the same as the location of items
220 and
230, and the usual location of items 220 and 230 is on shelf 210, the location
of items 240
and 250 is also shelf 210. This location information may be useful, for
example, when the
information about the misplaced or orphaned products is displayed, at step
416, at a
location other than the display of the RFID reader 300 (e.g., if the RFID
reader is mobile),
such as at a user terminal in a back office of the retail store 100 or other
location remote
from shelf 210.
FIG. 5 is an example block diagram of an inventory management environment 417,
according to an embodiment. The environment 417 may include or be part of, for
example, the retail store 100 of FIG. 1, as well as other environments outside
of the store
100, such as a data center for housing at least some computing components that
are
integrated with or operatively coupled to other components within the
environment 417.
Within the environment 417 is an RFID reader configurator 424, which includes
a
configuration module 422 for configuring one or more RFID readers 300a, 300b,
300c,
(such as the RFID reader 300 of FIG. 3). The configuration module 422 may
include
hardware, software and/or firmware for performing all or parts of one or more
of the
exemplary techniques described herein. The RFID readers 300a, 300b, 300c may,
for
example, be located in various locations throughout the environment 417 (e.g.,
proximate
to any of the locations A-L of the retail store 100).
One or more inventory management and/or location systems 418a. 418b, 418c, or
other computing systems can also be included within the environment 400. One
or more
RFID tags 260a, 260b, 260c (such as the RFID tags 260 of FIG. 2) may also be
present
within the environment 400, although it will be understood that due to the
nature of their
use such tags may transit into, out of, and between different locations within
the
environment 417 over time. Each of the RFID tags 260a, 260b, 260c transmits,
via an RF
signal, RFID tag data stored in the RFID tag when interrogated by one or more
of the
RFID readers 300a, 300b, 300c, depending on the interrogation mode in which
the
respective RFID reader 300a, 300b, 300c is configured to operate in.
Correspondingly,
21
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
one or more of the RFID readers 300a, 300b, 300c receives the RFID tag data
from one or
more of the RFID tags 260a, 260b, 260c. This process is also referred to
herein as reading
the RFID tags.
The RFID reader configurator 424 receives one or more requests 420a, 420b,
420c
for RFID tag data from one or more of the systems 418a, 418b, 418c in a
digital or analog
format (e.g., electronically). The configuration module 422 processes each
request 420a,
420b, 420c to select a selected interrogation mode for one or more of the RFID
readers
300a, 300b, 300c based at least in part on the requests 420a, 420b, 420c. One
example of
the operation of the configuration module 422 is described below with respect
to FIG. 5,
The selected interrogation mode is one of the operating modes supported by the
RFID
readers 300a, 300b, 300c and is at least one of the modes in which the
requests 420a,
420b, 420c for RFID tag data can be satisfied, preferably in an efficient
manner. In
particular, if more than one request 420a, 420b, 420c is to be processed at
substantially the
same time, there may be one interrogation mode that is better suited to
satisfying all of the
requests. Examples of satisfying all of the requests include performing the
fewest number
of tag read operations and/or performing all of the tag read operations in the
least amount
of time with respect to performing the same operations in an interrogation
mode that
causes the RFID reader 300a, 300b, 300c to operate differently from the
selected
interrogation mode.
In some embodiments, some of the requests 420a. 420b, 420c may include
requests
for different portions of the RFID tag data. For example, one request 420a may
include a
first request, received from the first system 418a, for RFID tag data from all
RFID tags in
the environment 400, while a second request 420b, received from the second
system 418b,
may include a request for RFID tag data from only RFID tags in certain
locations of the
environment 400, or for RFID tag data from only previously unread RFID tags in
the
environment 400 (i.e., a portion of the RFID tag data from all of the RFID
tags in the
environment 400). In this example, therefore, it is possible to automatically
configure the
appropriate RFID readers 300a, 300b, 300c to operate in a selected
interrogation mode via
configuration commands 426a, 426b, 426c for receiving RFID tag data from all
RFID tags
in the environment 400, which will satisfy both the first request 420a and the
second
request 420b.
Once the RFID readers 300a, 300b, 300c are configured to operate in the
selected
interrogation mode, the RFID readers 300a, 300b, 300c may operate in a
conventional
22
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
manner to receive RFID tag data as appropriate for the corresponding
interrogation mode.
The RFID tag data can then be transmitted to the RFID reader configurator 424,
or other
computing device, for further processing. In the above example, since the
second request
420b is for only a portion of the RFID tag data requested in the first request
420a, the
RFID reader configurator 424 can transmit only the corresponding portion of
RFID tag
data to the second system 418b, while transmitting all of the RFID tag data to
the first
system 418a, in satisfaction of both the first request 420a and the second
request 420b
using a minimal number of RFID tag reads. After all of the requests 420a,
420b, 420c
have been satisfied, the RFID reader configurator 424 can configure one or
more of the
RFID readers 300a, 300b, 300c to operate in a different interrogation mode
(e.g., a default
interrogation mode), or wait for additional requests 420a, 420b, 420c before
changing the
configuration of the RFID readers 300a, 300b, 300c according to the exemplary
techniques described herein or other operational rules that may be programmed
into the
RFID reader configurator 424.
In some embodiments, each RFID reader 300a, 300b, 300c can be configured to
operate in a different interrogation mode. For instance, if each RFID reader
300a, 300b,
300c has a reading range or coverage area that overlaps at least partially
with at least one
other RFID reader 300a, 300b, 300c, then one of the RFID readers 300a, 300b,
300c may
be configured to operate in one interrogation mode while at least one other
RFID reader
.. 300a, 300b, 300c may be configured to operate in a different interrogation
mode, as
suitable for satisfying the first request 420a and/or the second request 420b.
As an
example, if two RFID readers are within reading range of the same set of RFID
tags, a first
RFID reader may be configured to read, in a first interrogation mode, one
subset (or all) of
the set of RFID tags for satisfying the first request 420a, while a second
RFID reader may
be configured to read, in a second interrogation mode, a different subset (or
all) of the set
of RFID tags for satisfying the second request 420b.
In some embodiments, the interrogation mode of each RFID reader 300a, 300b,
300c can change dynamically based on certain conditions, such as the
arrival/activation or
departure/deactivation of one or more RFID readers within a particular area.
For example,
if a first RFID reader 300a is active within a particular area and operating
in a first
interrogation mode while a second RFID reader 300b becomes active (e.g., is
turned on) in
the same area, the first RFID reader 300a may be configured to operate in a
second
interrogation mode in response to the activation of the second RFID reader
300b.
23
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
As described herein, in exemplary embodiments, RFID readers can be configured
to operate in different integration modes in response to read request, tag
data or a
combination thereof. FIG. 6A is an example flow diagram of a process 500 for
automatically configuring an RFID reader, such as RFID reader 300 of FIG. 3,
according
to an embodiment. Process 500 begins at step 502. At step 504, a first request
for a first
set of RFID tag data and a second request for a second set of RFID tag data is
received.
The first request and the second request may, for example, be received from
the same
source (an inventory management system) or different sources (different
inventory
management systems and/or location systems). The first request and the second
request
can be the same or different. For example, the first request may include a
request to read
all RFID tags, while the second request may include a request to read only
previously
unread RFID tags. The nature of each request may depend on the purpose for
which the
RFID tag data is to be used. For example, an inventory system may need to know
which
RFID tags are anywhere in the store, while a location system may need to know
where
each RFID tag is located on the sales floor or backroom. Thus, both of these
system
would need to have different sets of the same RFID tag data; in some
instances, the second
set of RFID tag data can include a subset of the first set of RFID tag data.
Put in other
terms, the first request and the second request may both include requests for
RFID tag data
from a common subset of RFID tags, if not all of the RFID tags. These separate
needs for
RFID tag data by different systems can be represented by the first request and
the second
request, respectively. It will be understood that, in some embodiments, any
number of
requests may be received.
At step 506, an interrogation mode of the RFID reader is selected based on the
first
and second requests. It will be understood that any number of requests can be
processed
(e.g., three, four, five, six, seven, etc.) For example, as discussed above,
if the first request
includes a request to read all RFID tags and the second request includes a
request to read
only previously unread RFID tags, then the selected interrogation mode may be
the mode
in which all RFID tags will be read (e.g., the first interrogation mode as
described above),
since the RFID tag data from all RFID tags is necessary to satisfy the first
request, unless,
for instance, some portion of the RFID tag data has already been read. At step
508, the
RFID reader is automatically configured to operate in the selected
interrogation mode. In
some embodiments, the selected interrogation mode may be one of a set of
predefined
interrogation modes of a single RFID reader, or the selected interrogation
mode may be a
24
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
combination of different predefined interrogation modes of multiple RFID
readers (e.g.,
one RFID reader may be configured to operate in a first interrogation mode and
another
RFID reader may be configured to operate in a second interrogation mode.) The
determination of the selected interrogation mode can, in some embodiments, be
based on
the first request and/or second request as well as the location and
capabilities of the RFID
reader. For instance, if two or more RFID readers have overlapping coverage
areas, it
may be desirable to configure each of the RFID readers to operate in different
interrogation modes in a manner that satisfies the first request and/or the
second request.
Process 500 ends at step 510. In some embodiments, process 500 can repeat
indefinitely or any number of times.
FIG. 6B is an example flow diagram of a process 550 for providing RFID tag
data
in response to the first request and the second request, according to an
embodiment. In
some embodiments, process 550 is performed subsequent to process 500, for
example,
after the RFID reader has read one or more RFID tags. Process 550 begins at
step 552. At
step 554, the first RFID tag data is transmitted in response to the first
request (e.g., to the
system that generated the first request) and the second RFID tag data is
transmitted in
response to the second request (e.g., to the system that generated the second
request).
Continuing the above example, if the RFID reader is configured to read all
RFID tags
(e.g., operate in the first interrogation mode), then the first RFID tag data
may include all
of the RFID tag data read by the RFID reader at step 554. The second RFID tag
data,
accordingly, may include only RFID tag data read from previously unread RFID
tags,
which may include a subset of the first RFID tag data. Thus, the first request
and the
second request can each be satisfied. Subsequent to step 554, at step 556, the
RFID reader
can continue to operate in the same (i.e., selected) interrogation mode, or
the RFID reader
can be configured to operate in a different interrogation mode, as
appropriate. For
example, at step 556, if there are no further requests to read all RFID tags,
but there is an
outstanding request to read only previously unread RFID tags, then the RFID
reader may
be configured to read only previously unread RFID tags (e.g., operate in the
second
interrogation mode).
Process 550 ends at step 558. In some embodiments, process 550 can repeat
indefinitely or any number of times.
As described herein, in exemplary embodiments, locations of RFID readers can
be
determined based on RFID tags read by the readers. FIG. 7 is a flow diagram of
one
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
example of a computer-executable process 560 for determining a location of an
RFID
reader using RFID tags. Process 560 begins at step 562. At step 564, apparent
location
information of the RFID reader (e.g., RFID reader 300 of FIG. 3) is
determined. For
example, the apparent location of the RFID reader may be manually input into
the RFID
reader by the user, determined from a default location or obtained from
another source.
The apparent location of the RFID reader may be, but is not necessarily, the
actual
location of the RFID reader. The apparent location is the location the RFID
reader
believes it is in. For instance, if the user inputs that the RFID reader is in
location A, but
the RFID reader is actually in location B, then the apparent location of the
RFID reader is
incorrect. This may occur, for example, if the user inputs the wrong location
or if the user
moves the RFID reader to a different location without inputting the correct,
actual
location.
At step 566, product identification information, or other data that can be
used to
uniquely identify a product, is received from a plurality of RFID tags (e.g.,
RFID tag 260
of FIG. 2). Each RFID tag is attached to a product directly or indirectly
(e.g., products
220, 230, 240 and 250 of FIG. 2). The product identification information can
be received
using the RFID reader (e.g., RFID reader 300).
At step 568, the apparent location information of the RFID reader is compared
to
the prior location of the products as determined using the product
identification
information received at a prior time (e.g., during a previous read of the RFID
tag
associated with the product). This prior product information may be historical
information
acquired using the same RFID reader or a different RFID reader and stored in a
memory
or database. At step 570, if the apparent location information of the RFID
reader is
different than the prior location of the products on at least two different
occasions prior to
comparing the apparent location with the prior location information, then the
apparent
location of the RFID reader is automatically updated to match the prior
location of the
product at step 572. Otherwise, process 560 ends at step 574. In some
embodiments,
instead of, or in addition to. using the prior location of the products, the
RFID reader can
be used to read several RFID tags, and the apparent location of the RFID
reader can be
automatically updated based on the prior location of a majority of products
associated with
the read RFID tags. For example, if a majority of the read RFID tags are
associated with
men's jeans, then the apparent location of the RFID reader can be
automatically updated to
26
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
the prior or current location of the men's jeans (e.g., on the sales floor or
in a storage
area).
FIG. 8 is a block diagram of an example of the RFID tag 260 of FIG. 2, which
is
suitable for use with various embodiments of the present disclosure. The RFID
tag 260
includes a passive resonant radio frequency (RF) circuit 610 for use in
detecting when the
tag 260 is within proximity of a reading range of a reader or interrogator,
such as RFID
reader 300 of FIG. 3. One example of the circuit 610 includes a coil antenna
612 and a
capacitor or battery 614, which together form a resonant circuit with a
predetermined
resonant frequency, i.e., a selected radio frequency. Power for the RFID tag
260 is
derived from the antenna 612 in the case where the tag is passive, or from the
battery 614
where the tag is active or semi-passive. Furthermore, the RFID tag 260
includes an
integrated circuit (IC) 620 for providing processing capabilities to the tag,
as will be
understood by one of skill in the art. The IC 620 is connected to the circuit
610. The IC
620 may, for example, include a programmable memory 622, such as a 96 bit
memory, for
storing identification data. It will be appreciated that other RFID tag
designs may be used
with certain embodiments, and embodiments are not limited to the particular
tag design
260 described herein. For instance, the capacitor 614 may be located on the IC
620, with
only an inductor coil (i.e., the antenna 612) being outside the IC 620.
The IC 620 can be configured to output a data stream of the data stored in the
memory 622 when sufficient power is applied to the RFID tag 260. In one
embodiment,
the data stream creates a series of data pulses by switching an extra
capacitor (not shown)
across the coil antenna 612 over a period of time. This changes the resonant
frequency of
the RF circuit 610, detuning it from the operational frequency. Thus, instead
of the RF
circuit 610 returning a simple response signal, it returns, for example, a
signal containing a
packet of preprogrammed information (e.g., the identification data). The
packet of data is
received and processed by interrogator receiving circuitry and is decoded (if
necessary) to
provide identification information about the item 220, 230, 240. 250 to which
the RFID
tag 260 is attached. Other methods of using the data in the IC memory 622 to
output
identification data from the tag 260 are contemplated and the above embodiment
is not
intended to be limiting. The IC 620 may be a passive device and is powered in
the same
manner as the RF circuit 610 (i.e., by using energy received at the antenna
612 from the
RFID reader 300 transmitter signal). Other types of RFID tags may be used. In
some
embodiments, the RFID tags 260 are not reused; that is, they are not removed
from the
27
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
product when the product is sold or otherwise disposed of; however, in some
embodiments
the RFID tags 260 may be reused.
FIG. 9 is a block diagram of an example of the RFID reader 300 of FIG. 3,
which
is suitable for use with the RFID tag 260 described with respect to FIG. 6.
The RFID
reader 300 and the RFID tag 260 can communicate by radio. The RFID reader 300
includes a transmitter 702, receiver 704, antenna 706, and data processing and
control
circuitry 708. An output of the transmitter 702 is connected to an input of
the antenna
706. An output of the antenna 706 is connected to an input of the receiver
704. Outputs
of the data processing and control circuitry 708 are connected to an input of
the transmitter
702 and to an input of the receiver 704, respectively. An output of the
receiver 704 is
connected to an input of the data processing and control circuitry 708.
FIG. 10 is a block diagram of an inventory management system configured in an
exemplary computing device 1000 that may be used to implement exemplary
embodiments described herein. In some embodiments, the computing device 1000
is
included in an RFID reader (such as RFID reader 300 of FIG. 3), back office
system
and/or other computing resource. The computing device 1000 includes one or
more non-
transitory computer-readable media for storing one or more computer-executable
instructions or software for implementing exemplary embodiments. The non-
transitory
computer-readable media may include, but are not limited to, one or more types
of
hardware memory, non-transitory tangible media (for example, one or more
magnetic
storage disks, one or more optical disks, one or more flash drives), and the
like. For
example, memory 1006 included in the computing device 1000 may store non-
transitory
computer-readable and computer-executable instructions or software for
implementing
exemplary embodiments, such as processes 400, 500, 550, and 560 described
herein. The
computing device 1000 also includes configurable and/or programmable processor
1002
and associated core 1004, and optionally, one or more additional configurable
and/or
programmable processor(s) 1002a and associated core(s) 1004a (for example, in
the case
of computer systems having multiple processors/cores), for executing non-
transitory
computer-readable and computer-executable instructions or software stored in
the memory
1006 and other programs for controlling system hardware. Processor 1002 and
processor(s) 1002a may each be a single core processor or multiple core (1004
and 1004a)
processor.
28
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
Virtualization may be employed in the computing device 1000 so that
infrastructure and resources in the computing device may be shared
dynamically. A
virtual machine 1014 may be provided to handle a process running on multiple
processors
so that the process appears to be using only one computing resource rather
than multiple
computing resources. Multiple virtual machines may also be used with one
processor.
Memory 1006 may include a computer system memory or random access memory,
such as DRAM, SRAM, EDO RAM, and the like. Memory 1006 may include other types
of memory as well, or combinations thereof. Memory 1006 may be used to store
information such as RFID tag identification data 1050, product identification
data 1052,
product data 1054 (e.g., information about the characteristics of the
product), and/or any
other information.
A user may interact with the computing device 1000 through a visual display
device 1018, such as a computer monitor or touch screen display integrated
into the
computing device 1000, which may display one or more user interfaces 1020
(e.g., the
display 320 of FIG. 3) that may be provided in accordance with exemplary
embodiments.
The computing device 1000 may include other I/0 devices for receiving input
from a user
or data from an RFID tag, for example, an antenna 1007, a keyboard or any
suitable multi-
point touch interface 1008, or a pointing device 1010 (e.g., a mouse). The
keyboard 1008
and the pointing device 1010 may be coupled to the visual display device 1018.
The
computing device 1000 may include other suitable conventional I/O peripherals.
The computing device 1000 may also include one or more storage devices 1024,
such as a hard-drive, CD-ROM, or other non-transitory computer-readable media,
for
storing data and non-transitory computer-readable instructions and/or software
that
implement exemplary embodiments described herein. The storage devices 1024 may
be
integrated with the computing device 1000. The computing device 1000 may
communicate with the one or more storage devices 1024 via a bus 1035. The bus
1035
may include parallel and/or bit serial connections, and may be wired in either
a multi-drop
(electrical parallel) or daisy-chain topology, or connected by switched hubs,
as in the case
of USB. Exemplary storage device 1024 may also store one or more databases
1026 for
storing any suitable information required to implement exemplary embodiments.
For
example, exemplary storage device 1024 can store one or more databases 1026,
for storing
information, such as product identification information 1052, product location
data 1053
product characteristics 1054, and/or any other information. The storage device
1024 can
29
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
also store an engine 1030 including logic and programming for performing one
or more of
the exemplary processes or methods disclosed herein (e.g., processes 400, 500,
550, and
560).
The computing device 1000 can include a network interface 1012 configured to
interface via one or more network devices 1022 with one or more networks, for
example,
Local Area Network (LAN), Wide Area Network (WAN) or the Internet through a
variety
of connections including, but not limited to, standard telephone lines, LAN or
WAN links
(for example, 802.11, Ti, T3, 56kb, X.25). broadband connections (for example,
ISDN,
Frame Relay, ATM), wireless connections, controller area network (CAN), or
some
combination of any or all of the above. The network interface 1012 may include
a built-in
network adapter, network interface card, PCMCIA network card, card bus network
adapter, wireless network adapter, USB network adapter, modem or any other
device
suitable for interfacing the computing device 1000 to any type of network
capable of
communication and performing the operations described herein. Moreover, the
computing
device 1000 may be any computer system, such as an RFID reader, workstation,
desktop
computer, server, laptop, handheld computer, tablet computer (e.g., the iPad0
tablet
computer), mobile computing or communication device (e.g., the iPhone0
communication
device), or other form of computing or telecommunications device that is
capable of
communication and that has sufficient processor power and memory capacity to
perform
the operations described herein.
The computing device 1000 may run any operating system 1016, such as any of
the
versions of the Microsoft Windows operating systems, the different releases
of the
Unix and Linux operating systems, any version of the Mac0S0 for Macintosh
computers,
any embedded operating system, any real-time operating system, any open source
operating system, any proprietary operating system, or any other operating
system capable
of running on the computing device and performing the operations described
herein. In
exemplary embodiments, the operating system 1016 may be run in native mode or
emulated mode. In an exemplary embodiment, the operating system 1016 may be
run on
one or more cloud machine instances.
FIG. 11 is an alternate embodiment of a block diagram of a system for
automatically configuring an RFID reader configured in an exemplary computing
device
1000' that may be used to implement exemplary embodiments described herein. In
some
embodiments, the computing device 1000' is included in an RFID reader
configurator
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
(such as the RFID reader configurator 424 of FIG. 5), back office system
and/or other
computing resource.
In an alternate embodiment a user may interact with the computing device 1000'
through a visual display device 1018, such as a computer monitor or touch
screen display
integrated into the computing device 1000', which may display one or more user
interfaces 1020 (e.g., the display 320 of FIG. 3) that may be provided in
accordance with
exemplary embodiments. The computing device 1000' may include or be
operatively
coupled to other I/0 devices for receiving input from a user or data from an
RFID tag, for
example, an antenna 1007, an RFID reader 260, a keyboard or any suitable multi-
point
touch interface 1008, or a pointing device 1010 (e.g., a mouse). The keyboard
1008 and
the pointing device 1010 may be coupled to the visual display device 1018. The
computing device 1000' may include other suitable conventional I/0
peripherals.
FIG. 12 is a block diagram of an exemplary network environment 1100 suitable
for
a distributed implementation of exemplary embodiments of an inventory
management
system, methods and non-transitory computer-readable media. The network
environment
1100 may include one or more servers 1102 and 1104, one or more clients 1106
and 1108,
and one or more databases 1110 and 1112, each of which can be communicatively
coupled
via a communication network 1114. The servers 1102 and 1104 may take the form
of or
include one or more computing devices 1000a and 1000b, respectively, that are
similar to
the computing device 1000 illustrated in FIG. 10. The clients 1106 and 1108
may take the
form of or include one or more computing devices 1000c and 1000d.
respectively, that are
similar to the computing device 1000 illustrated in FIG. 10. For example,
clients 1106 and
1108 may include mobile user devices. Similarly, the databases 1110 and 1112
may take
the form of or include one or more computing devices 1000e and 1000f,
respectively. that
are similar to the computing device 1000 illustrated in FIG. 10. While
databases 1110 and
1112 have been illustrated as devices that are separate from the servers 1102
and 1104,
those skilled in the art will recognize that the databases 1110 and/or 1112
may be
integrated with the servers 1102 and/or 1104 and/or the clients 1106 and 1108.
The network interface 1012 and the network device 1022 of the computing device
1000 enable the servers 1102 and 1104 to communicate with the clients 1106 and
1108 via
the communication network 1114. The communication network 1114 may include,
but is
not limited to, the Internet, an intranet, a LAN (Local Area Network), a WAN
(Wide Area
Network), a MAN (Metropolitan Area Network), a wireless network, an optical
network,
31
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
and the like. The communication facilities provided by the communication
network 1114
are capable of supporting distributed implementations of exemplary
embodiments.
In exemplary embodiments, one or more client-side applications 1107 may be
installed on client 1106 and/or 1108 to allow users of client 1106 and/or 1108
to access
and interact with a multi-user service 1032 installed on the servers 1102
and/or 1104. For
example, the users of client 1106 and/or 1108 may include users associated
with an
authorized user group and authorized to access and interact with the multi-
user service
1032. In some embodiments, the servers 1102 and 1104 may provide client 1106
and/or
1108 with the client-side applications 1107 under a particular condition, such
as a license
or use agreement. In some embodiments, client 1106 and/or 1108 may obtain the
client-
side applications 1107 independent of the servers 1102 and 1104. The client-
side
application 1107 can be computer-readable and/or computer-executable
components or
products, such as computer-readable and/or computer-executable components or
products
for presenting a user interface for a multi-user service. One example of a
client-side
application is a web browser configured to display a web page containing the
report data
124 and/or the workload estimate 126, the web page being hosted by the server
1102
and/or the server 1104, which may provide access to the multi-user service.
Another
example of a client-side application is a mobile application (e.g., a smart
phone or tablet
application) that can be installed on client 1106 and/or 1108 and can be
configured and/or
programmed to access a multi-user service implemented by the server 1102
and/or 1104.
The servers 1102 and 1104 can also provide one or more engines 1034, 1036
including
logic and programming for receiving the product identification data 1052
and/or other data
(e.g., product location data 1053), for performing one or more of the
exemplary methods
disclosed herein.
The databases 1110 and 1112 can store user information, manifest data, report
data
and/or any other information suitable for use by the multi-user service 1032.
The servers
1102 and 1104 can be programmed to generate queries for the databases 1110 and
1112
and to receive responses to the queries, which may include information stored
by the
databases 1110 and 1112.
While embodiments have been discussed in the context of products in an retail
environment, it will be appreciated that some embodiments may be used in a
similar
manner in other environments, such as warehousing, distribution, shipping,
storage, or any
other environment in which products or other objects having RFID tags may be
tracked.
32
CA 02903717 2015-09-01
WO 2014/151935 PCT/US2014/026698
For example, some embodiments may be used to determine the location of an RFID
reader
with respect to medical supplies in a hospital, cargo on a vessel, pallets in
a distribution
center and/or animals in a shelter. It will also be appreciated that, in some
embodiments,
the RFID tags may be attached to, for example, product packaging or shipping
containers
rather than, or in addition to, being attached directly to individual units of
a product.
A variety of commercially available RFID tags, readers and integrated circuits
are
contemplated for use with various embodiments. For example, RFIC suppliers
include
NXP Semiconductors N.V. of Eindhoven, The Netherlands, Impinj of Seattle,
Washington, and Alien Technology of Morgan Hill. California. In some
embodiments,
the RFID tags 260 can be embedded, affixed to or inlayed onto label material
attached to
each product.
Having thus described several exemplary embodiments of the disclosure, it is
to be
appreciated various alterations, modifications, and improvements will readily
occur to
those skilled in the art. For example, it is contemplated that any item,
product or good
having an RFID tag associated with it can be the object of the disclosed
systems and
methods. Accordingly, the foregoing description and drawings are by way of
example
only.
33