Note: Descriptions are shown in the official language in which they were submitted.
CA 02904634 2015-09-08
WO 2014/160106 PCT/US2014/025827
TITLE
Methods and Systems for Dynamic Spectrum Arbitrage
CROSS REFERENCE TO RELATED PATENT APPLICATIONS
[0001] This claims the benefit of priority to U.S. Patent Application Serial
No.
13/800,906 filed on March 13, 2013, the entire contents of which are hereby
incorporated by reference for all purposes.
BACKGROUND
[0002] With the ever increasing use of wireless communication devices for
accessing
networks and downloading large files (e.g., video files), there is an
increasing demand
for radio frequency spectrum. Smart phone users complain about dropped calls,
slow
access to the Internet and similar problems which are due largely to too many
devices
trying to access finite RF bandwidth allocated to such services. Yet parts of
the RF
spectrum, such as the RF bands dedicated to emergency services (e.g., police,
fire and
rescue, etc.) go largely unused due to the non-continuous and episodic
employment of
such voice-radio communication bands.
SUMMARY
[0003] According to a first embodiment, a method for dynamically managing
radio
frequency (RF) spectrum resources in frequency, space and time includes
monitoring
the use of RF spectrum resources at a first network and determining an amount
of
unused RF spectrum resources in the first network. The method includes
allocating a
portion of the amount of unused RF spectrum resources of the first network for
use by
secondary users and receiving a request for additional RF spectrum resources
from a
second network. The method includes providing the second network access to the
unused RF spectrum resources of the first network. The method may include off-
loading a secondary user from the first network.
[0004] According to another embodiment, a communication system comprising a
server configured with server-executable instructions to perform operations
comprises
,
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
a dynamic spectrum arbitrage and management. The management enables radio
frequency spectrum to be made available to RF devices in frequency, space and
time
as described herein. In another embodiment, a server configured with server-
executable instructions to perform operations comprises a dynamic spectrum
arbitrage
and management. The management enables radio frequency spectrum to be made
available to RF devices in frequency, space and time.
[0005] In another embodiment, radiofrequency spectrum clearinghouse includes a
server for monitoring the use of RF spectrum resources. The clearinghouse
determines an amount of unused RF spectrum resources in a first communication
system and allocates a portion of the amount of unused RF spectrum resources
for use
by secondary users. The server forms allocated shares of the unused RF
spectrum
resources of the first communication system. The allocated shares are to be
utilized
by a second communication system. The server may communicate the availability
of
the allocated shares to the second communication system.
BRIEF DESCRIPTION OF THE DRAWINGS
[0006] The accompanying drawings, which are incorporated herein and constitute
part
of this specification, illustrate exemplary embodiments of the invention, and,
together
with the general description given above and the detailed description given
below,
serve to explain features of the invention.
[0007] FIG. 1 is a system block diagram illustrating call volume requests made
to a
cellular communication network under normal conditions.
[0008] FIG. 2 is a system block diagram illustrating call volume requests made
to a
cellular communication network under an emergency situation condition.
[0009] FIG. 3 is a system block diagram illustrating call volume requests made
to a
cellular communication network under an emergency situation condition when a
first
responder arrives on the scene.
2
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0010] FIG. 4 is a system block diagram illustrating call volume requests made
to a
cellular communication network as additional emergency response personnel
arrive on
the scene.
[0011] FIG. 5 is a system block diagram illustrating call volume requests made
to a
cellular communication network after an emergency situation has been
alleviated.
[0012] FIG. 6 is a process flow diagram of an embodiment method for managing
Tiered Priority Access (TPA) operations on a network.
[0013] FIG. 7 is a process flow diagram of another embodiment method for
managing
TPA operations on a network.
[0014] FIG. 8 is an example hierarchical table of classes of users given
priority access
to emergency communication resources.
[0015] FIG. 9 is a communication system block diagram of a Dynamic Spectrum
Arbitrage (DSA) communication system according to an embodiment.
[0016] FIG. 10 is a communication system block diagram of a DSA communication
system according to an embodiment.
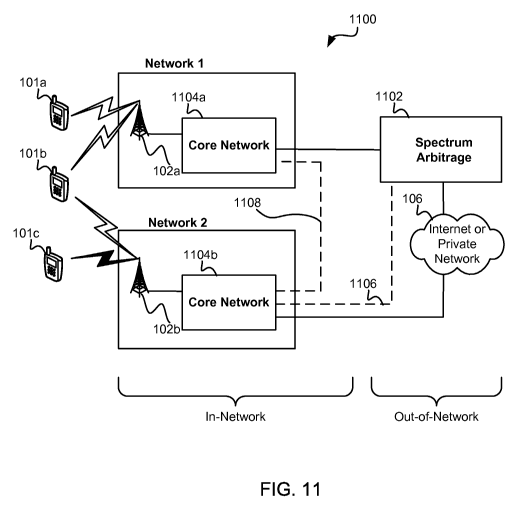
[0017] FIG. 11 is a communication system block diagram of a DSA communication
system according to an embodiment.
[0018] FIG. 12 is a communication system block diagram of a DSA communication
system illustrating an embodiment for providing master control for the
arbitrage
process.
[0019] FIG. 13A is a diagram of RF spectrum illustrating its allocation
according to an
embodiment.
[0020] FIG. 13B is a diagram illustrating a manner in which RF spectrum may be
allocated for use according to an embodiment.
[0021] FIG. 14 is a block diagram illustrating the manner in which RF spectrum
may
be allocated with a guard band for use according to an embodiment.
3
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0022] FIG. 15 is a diagram illustrating a manner in which RF spectrum may be
pooled for use allocation according to an embodiment.
[0023] FIGs. 16A-16C are block diagrams illustrating a manner in which
spectrum is
allocated for Mobile Virtual Network Operators (MVNO).
[0024] FIG. 17 is a communication system block diagram of a DSA communication
system illustrating communication between components of the system for
allocating
resources according to an embodiment.
[0025] FIG. 18 is a communication system block diagram illustrating
communications
between components of two networks in a DSA communication system during
resource reservation according to an embodiment.
[0026] FIG. 19 is a communication system block diagram of a DSA communication
system illustrating bifurcation of resources at an eNodeB according to an
embodiment.
10027] FIG. 20 is a communication system block diagram of a DSA communication
system illustrating Serving Gateway (SGW) and Packet Gateway (POW) link
bandwidth allocation and capacity control according to an embodiment.
[0028] FIG. 21 is a communication system block diagram of a DSA communication
system illustrating combining the x-furcation of resources at an eNodeB and
SGW and
PGW link bandwidth allocation with capacity control according to an
embodiment.
[0029] FIG. 22 is a communication system block diagram of a DSA communication
system illustrating spectrum allocation based on license and regional area
methods
according to an embodiment.
[0030] FIG. 23A is a diagram illustrating typical RF spectrum allocation in a
licensed
area according to an embodiment.
[0031] FIG. 23B is a diagram illustrating RF spectrum allocation in a DSA
communication system based on license area according to an embodiment.
[0032] FIG. 24 is a diagram illustrating spectrum allocation in a DSA
communication
system based on regional area according to an embodiment.
4
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0033] FIG. 25A is a communication system block diagram of a DSA communication
system illustrating a situation where the subscriber is using a first carrier
(carrier A)
according to an embodiment.
[0034] FIG. 25B is a communication system block diagram of a DSA communication
system illustrating a situation in which a subscriber is using a second
carrier (carrier
B) in a de facto type roaming arrangement for spectrum off-loading according
to an
embodiment.
[0035] FIG. 26A is a communication system block diagram of a DSA communication
system illustrating a situation in which the subscriber is using a first
carrier (carrier A)
for both public safety and commercial DSA schemes according to an embodiment.
[0036] FIG. 26B is a communication system block diagram of a DSA communication
system illustrating a situation in which based on the services being used,
geographic
location or time the subscriber can use carrier B resources in a de facto
short term
lease using DSA according to an embodiment.
[0037] FIG. 27A is a communication system block diagram of a DSA communication
system illustrating a normal operation situation according to an embodiment.
[0038] FIG. 27B is a communication system block diagram of a DSA communication
system illustrating additional capacity and spectrum made available for use by
a
subscriber according to an embodiment.
[0039] FIG. 28 is a process flow diagram illustrating an embodiment method for
network selection and reselection in a DSA communication system.
[0040] FIG. 29 is a communication block diagram of a DSA communication system
illustrating TAI routing areas where the home non-DSA user equipment uses one
TAI
element (TAI) and DSA user equipment use another TAI.
[0041] FIG. 30 is a communication block diagram of a DSA communication system
illustrating high level tracking and monitoring of RF spectrum resource
allocations
and use according to an embodiment.
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0042] FIG. 31 is a communication block diagram of a DSA communication system
illustrating integration required for full mobility between visiting and home
networks.
[0043] FIG. 32 is a communication block diagram of a DSA communication system
illustrating media independent handover of user equipment from one network to
another according to an embodiment.
[0044] FIG. 33 is a communication block diagram of a DSA communication system
illustrating data flow for initiating a network handover according to an
embodiment.
[0045] FIG. 34 is a communication system block diagram of a DSA communication
system illustrating providing user equipment access to several Radio Access
Terminals (RAT) according to an embodiment.
[0046] FIG. 35 is a message flow diagram illustrating message communications
between components of a DSA communication system according to an embodiment.
[0047] FIGs. 36-40 are process flow diagrams of embodiment methods for
allocating
and accessing resources using the DSA communication system.
[0048] FIG. 41 is a message flow diagram illustrating in more detail message
communications between components of a DSA communication system according to
an embodiment.
[0049] FIGs. 42-44 are process flow diagrams of embodiment methods for off-
loading
communication sessions from a host network.
[0050] FIGs. 45-49 are process flow diagrams of embodiment methods for
allocating
and accessing resources in a public safety network using the DSA communication
system.
[0051] FIGs. 50-53 are process flow diagrams of embodiment methods for off-
loading
communication sessions from a public safety network.
[0052] FIGs. 54-56 are process flow diagrams of embodiment methods for
enabling an
authorized public safety authority to access the public safety network using a
wireless
device from another network.
6
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0053] FIG. 57 is a system block diagram illustrating network components in an
example communication system having components suitable for implementing an
embodiment DSA telecommunications commodity exchange (TCE) system.
[0054] FIG. 58 is a system block diagram illustrating example information
flows and
functional components in an embodiment DSA-TCE system configured to conduct an
auction and allocate telecommunication resources purchased via the auction.
[0055] FIG. 59 is a process flow diagram illustrating an embodiment DSA-TCE
validation method for authorizing a bidder network to participate in a
telecommunications commodity exchange.
[0056] FIG. 60 is a process flow diagram illustrating an embodiment DSA-TCE
resource validation method for validating/verifying that that a requested
telecommunication resources may be used by a bidder network requesting the
telecommunication resources.
[0057] FIG. 61 is a process flow diagram illustrating an embodiment DSA-TCE
auction method for determining which of a plurality of bidder networks are to
be
allocated a telecommunication resource.
[0058] FIG. 62 is a process flow diagram illustrating an embodiment DSA-TCE
allocation method for allocating a telecommunication resource to a bidder
network.
[0059] FIG. 63 is a process flow diagram illustrating an embodiment DSA-TCE
futures auction method for determining if a bidder network may purchase a
futures
contract that promise delivery or allocation of a telecommunication resource
to the
purchaser at a future date/time for a currently-agreed to price.
[0060] FIG. 64 is a process flow diagram illustrating an embodiment DSA-TCE
post-
bid resource allocation method for requesting and receiving telecommunications
resources for immediate use outside of the auction process.
7
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0061] FIG. 65 is a process flow diagram illustrating another embodiment DSA-
TCE
post-bid resource allocation method for requesting and receiving
telecommunications
resources for immediate use.
[0062] FIG. 66 is a system block diagram illustrating an embodiment DSA-TCE
system having a single dynamic spectrum policy controller (DPC).
[00631 FIG. 67 is a system block diagram illustrating an embodiment DSA-TCE
system that includes a centralized DPC coupled to plurality of DPCs.
[0064] FIG. 68 is a process flow diagram illustrating embodiment DSA-TCE post-
bid
resource reallocation method for receiving a leased telecommunication resource
at the
conclusion of its lease period and submitting the newly available resource to
telecommunication exchange network to be auctioned.
[0065] FIG. 69 is a component block diagram of a server suitable for use with
an
embodiment.
DETAILED DESCRIPTION
[0066] The various embodiments will be described in detail with reference to
the
accompanying drawings. Wherever possible, the same reference numbers will be
used throughout the drawings to refer to the same or like parts. References
made to
particular examples and implementations are for illustrative purposes, and are
not
intended to limit the scope of the invention or the claims.
[0067] As used herein, the terms "mobile device," "wireless device" and "user
equipment (UE)" may be used interchangeably and refer to any one of various
cellular
telephones, personal data assistants (PDA's), palm-top computers, laptop
computers
with wireless modems, wireless electronic mail receivers (e.g., the Blackberry
and
Treo devices), multimedia Internet enabled cellular telephones (e.g., the
iPhone6),
and similar personal electronic devices. A wireless device may include a
programmable processor and memory. In a preferred embodiment, the wireless
device is a cellular handheld device (e.g., a mobile device), which can
communicate
via a cellular telephone communications network.
8
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0068] As used in this application, the terms "component," "module," "engine,"
"manager" are intended to include a computer-related entity, such as, but not
limited
to, hardware, firmware, a combination of hardware and software, software, or
software in execution, which are configured to perform particular operations
or
functions. For example, a component may be, but is not limited to, a process
running
on a processor, a processor, an object, an executable, a thread of execution,
a program,
a computer, a server, network hardware, etc. By way of illustration, both an
application running on a computing device and the computing device may be
referred
to as a component. One or more components may reside within a process and/or
thread of execution and a component may be localized on one processor or core
and/or
distributed between two or more processors or cores. In addition, these
components
may execute from various non-transitory computer readable media having various
instructions and/or data structures stored thereon.
[0069] A number of different cellular and mobile communication services and
standards are available or contemplated in the future, all of which may
implement and
benefit from the various embodiments. Such services and standards include,
e.g.,
third generation partnership project (3GPP), long term evolution (LTE)
systems, third
generation wireless mobile communication technology (3G), fourth generation
wireless mobile communication technology (4G), global system for mobile
communications (GSM), universal mobile telecommunications system (UMTS),
3GSM, general packet radio service (GPRS), code division multiple access
(CDMA)
systems (e.g., cdmaOne, CDMA2000TM), enhanced data rates for GSM evolution
(EDGE), advanced mobile phone system (AMPS), digital AMPS (IS-136/TDMA),
evolution-data optimized (EV-DO), digital enhanced cordless telecommunications
(DECT), Worldwide Interoperability for Microwave Access (WiMAX), wireless
local
area network (WLAN), public switched telephone network (PSTN), Wi-Fi Protected
Access I & II (WPA, WPA2), Bluetooth , integrated digital enhanced network
(iden),
and land mobile radio (LMR). Each of these technologies involves, for example,
the
transmission and reception of voice, data, signaling and/or content messages.
It
should be understood that any references to terminology and/or technical
details
9
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
related to an individual telecommunication standard or technology are for
illustrative
purposes only, and are not intended to limit the scope of the claims to a
particular
communication system or technology unless specifically recited in the claim
language.
[0070] A high priority in responding to any emergency or disaster situation is
establishing effective communications. In large scale emergency or disaster
(both
manmade and natural) situations, it is paramount to maintain communications
between all first responders and emergency personnel in order to respond,
manage,
and control the emergency situation effectively. In the absence of effective
communication among first responders and other emergency personnel, resources
may
not be effectively mobilized to the areas which need the resources most. Even
in
minor emergency situations (e.g., traffic accidents and fires), first
responders must be
able to call on support assets and coordinate with other services (e.g.,
public utilities,
hospitals, etc.). With the ubiquity of wireless device ownership and usage,
emergency
communication via wireless devices using commercial cellular communication
networks often are the most efficient and effective means to mobilize
emergency
response personnel and resources. Enabling wireless devices to provide
effective
emergency communications obviates the technical challenges and expense of
coordinating radio frequencies among various first responder agencies (e.g.,
police,
fire, ambulance, FEMA, public utilities, etc.). Also, qualified first
responders to an
accident who are off duty or not ordinarily equipped with radios (e.g.,
doctors, nurses,
retired police, or military personnel) will have or can quickly borrow a
wireless
device.
[0071] Emergency communications over cellular communication networks is not
without problems, however. As discussed above in the Background, cellular
communication networks ("networks") are designed to accommodate access
requests
from only a fraction of the total number of wireless devices in a particular
cell. At
times of emergency or crisis, network resources may become overtaxed when
predictable human responses to the situation prompt an extraordinary number of
wireless device users within a particular cell to access the network at the
same time.
Wireless device users may be attempting to alert emergency personnel of the
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
emergency situation (such as a 911 emergency call) or to alert friends or
family
members that the user is safe despite being in the area of an emergency
situation.
Some users may be transmitting images of the emergency condition (fire,
accident,
etc.) to news services or friends. In a wide scale situation, emergency
responders
using wireless devices for emergency communications will add to the call
volume.
Regardless, the predictable increase in call volume during an emergency
situation can
overwhelm a commercial cellular communications network, particularly in the
cell
zone encompassing the emergency, thus rendering the network unreliable for
emergency response personnel communication usage.
[0072] To illustrate the problem, consider the case of a traffic accident
occurring on
the highway. FIG. 1 illustrates a cellular communication network under normal
conditions. As illustrated, multiple wireless devices 101(a-g) are wirelessly
connect
to the cellular communication network via a base station 102 servicing a
particular
cell 100. The base station 102 connects via a base station controller
(BSC)/radio
network controller (RNC) 103 to a Mobile Switching Center (MSC) 104. The MSC
104 contains both a public switched telephone network (PSTN) interface and an
Internet interface. Calls made to and from any of the multiple wireless
devices 101(a-
g) may be routed via conventional landlines over the PSTN 105 or Internet 106
using
VOlP. Calls between conventional landline telephone stations and any one of
wireless devices 101(a-g) may be routed over via the PSTN or Internet. Calls
between
wireless devices 101(a-g) may be routed over the PSTN or Internet to similar
MSC
104, BSC/RNC 103, and base station 102 located near the initiating or intended
wireless device 101(a-g).
[0073] FIG. 1 illustrates the typical situation in which a fraction of the
wireless devices
within a cell access the network at the same time. For example, FIG. 1 shows
seven
separate wireless devices 101(a-g) located within the cell, only three of
which (101c,
101d, and 101e) are currently accessing the network. Thus, the network is
operating
well within its operating parameters and all requests to the network from
wireless
devices 101(a-g) are granted. It is noted that all wireless devices 101(a-g)
that are
turned on but not in use continue to communicate with the base station 102 via
a link
11
CA 02904634 2015-09-08
WO 2014/160106 PCT/US2014/025827
management channel (not illustrated). The network uses these communications to
keep track of the wireless devices 101(a-g) within each cell to support call
routing.
However, the amount of information communicated between all wireless devices
101(a-g) and the base station 102 for such tracking purposes is small
(particularly in
contrast to the bandwidth required for a normal telephone call), so the number
of on-
but-inactive wireless devices 101 within a cell normally will not overwhelm
the
network.
[0074] This normal functioning of the cellular network can be disrupted when,
for
example, an accident stops traffic, prompting delayed drivers to
simultaneously use
their wireless devices to alert emergency personnel of the traffic accident
(emergency
911 call) or contact friends, family members, business associates, etc., to
inform them
of the delay. FIG. 2 illustrates a cellular communication network in such an
emergency situation. In this illustration, a truck 107 in the vicinity of base
station 102
is on fire. Predictably, the truck 107 fire prompts most of the wireless
devices 101(a-
g) users within the vicinity to access the cellular network at approximately
the same
time. This causes an overload condition in the cell by exceeding the bandwidth
of the
carriers on the local base station 102. Consequently, some of the wireless
devices
101b, 101f will not be granted access to the network, and new network access
requests
may be denied until communication channels open up. This communication
bottleneck may worsen the emergency situation by delaying the response by
emergency personnel and denying first responders with effective communication
over
the network.
[0075] This problem is exacerbated in disaster situations involving many
victims and
large areas, such as wildfires, floods, hurricanes, tornados and terrorist
attacks. As
witnessed during the September 11th attack and Hurricane Katrina, large
disasters can
destroy part of the cellular and landline telephone network infrastructure,
leaving the
remaining network more vulnerable to overload conditions. Network overloads
during disaster events are particularly troublesome since such situations
naturally
involve widespread confusion and require close coordination among a large
number of
emergency and relief personnel.
12
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0076] If a disaster situation will persist long enough (e.g., a flood or
hurricane
situation), additional cellular communication capacity can be added to a
region by
activating a deployable cellular communication system to provide emergency
response teams and personnel with the ability to communicate. Such recently
developed deployable units, referred to herein as a "switch on wheels," can
include a
CDMA2000 base station and switch, Land Mobile Radio (LMR) interoperability
equipment, a satellite Fixed Service Satellite (FSS) for remote
interconnection to the
Internet and PSTN, and, optionally, a source or remote electrical power such
as a
gasoline or diesel powered generator. A more complete description of an
example
deployable switch on wheels is provided in U.S. Patent Application No.
12/249,143,
filed October 10, 2008, the entire contents of which are hereby incorporated
by
reference in their entirety.
[0077] These switch on wheels are effectively mobile cellular base stations
which may
be deployed in a disaster area and operate as a cellular tower antenna. The
switch on
wheels sends and receives communication signals from a plurality of wireless
devices
101 and serves as a gateway portal to the rest of the conventional
communications
infrastructure. Communications between the switch on wheels and a wireless
device
101 is broken down into packets for transport as a VOIP communication, and may
be
transmitted via satellite to a ground station outside the disaster area from
which the
call is forwarded through the telephone network to the recipient. Even with
the added
bandwidth provided by deployable switch on wheels, network overloads may still
cause communication delay and frustration to emergency response personnel.
[0078] To overcome such problems in the event of a national emergency, the WPA
system was developed. Conventional WPA systems provide selected emergency
leadership with preemptive access to cellular communication networks. However,
conventional WPA systems do not permit calls made to the wireless device of a
registered WPA authority. In other words, while wireless devices registered
for WPA
service may be given priority access for placing calls on the network, there
are no
provisions in the WPA system enabling those very same wireless devices to
receive
calls. Incoming calls to wireless devices in a command center may be just as
13
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
important as outgoing calls. Also, conventional WPA systems assume that if an
authorized user needs to make a call, the call will be made from their pre-
registered
wireless device. However, there may be instances where the authorized
personnel do
not have their pre-registered wireless device. Alternatively, the wireless
device may
be damaged. Provisions must be made to enable the authorized personnel access
to an
overloaded network. Also, emergency personnel who have not previously
registered
their wireless device on the WPA system cannot access overloaded cellular
communication networks "on the fly." Many times, off duty, junior, volunteer
emergency response personnel may be the first responders on the scene on an
incident.
Such personnel may not be entitled to conventional WPA which is designed to
address
the needs of the leadership. Thus, precisely the personnel who can quickly
alleviate a
situation given their proximity on the scene are unlikely not pre-registered
and
authorized for conventional WPA.
[0079] To overcome these limitations with conventional cellular communication
networks and conventional WPA, the various embodiments provide Tiered Priority
Access (TPA) capabilities to deliver Quality of Service (QoS)/Grade of Service
(GOS) wireless device communications for first responders for calls both
originated
and terminated at a mobile handset. The various embodiments are particularly
aimed
at the needs of first responders at the very start of an emergency event.
[0080] TPA as its name implies aims to provide a tiered response to network
capacity
requirements. The tiered response mirrors typical communication requirements
at the
incident scene as more responders appear to help resolve the problem(s) at
hand.
When an incident occurs first responders are either at the incident scene or
begin to
respond. First responders reporting to an incident initially arrive on scene
in small
numbers and may grow in direct response to the magnitude and severity of the
incident.
[0081] To accommodate this predictable response, TPA enables an escalation and
de-
escalation process based upon call volume as first responders arrive on scene
and
depart as the situation is restored to normal.
14
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0082] In overview, the various embodiments work as follows. During normal
operation, cellular call volume through particular base stations is monitored
to
determine if the network is reaching capacity limits. Call volume may be
monitored
based on current calls, attempts to access the network, engaged bandwidth, or
other
methods known to cellular service providers. Call volume may be locally
monitored
at the base station 102, at a BSC/RNC 103, or an MSC 104 or, in an embodiment,
centrally, such as in a Network Operation Center (NOC). Such monitoring is at
the
cellular level, since normal emergency situations are most likely to impact
one or two
cell zones, although TPA will work in a similar fashion in the event of a
widespread
emergency. When call volume in a cell exceeds a threshold value preselected by
the
service provider and/or emergency response planners, the system allocates one
channel in the affected cell tower to TPA operation.
[0083] FIG. 2 illustrates a situation in which call volume has exceeded a
threshold
indicating that TPA should be implemented. As shown in FIG. 2, more wireless
devices 101 in the cell supported by the base station 102 are attempting to
access the
network than the network can connect. As a result, only some of the wireless
devices
101a, 101c, 101d, 101e and 101g will be able to place or receive calls (shown
as solid
black), while others will be denied access to the network (shown as white). In
this
situation, call volume within the cell served by the base station 102 has
exceeded the
threshold, so one of the communication channels on the antenna will be
allocated to
TPA operation. However, the channel remains available to general public use
until a
TPA-authorized call is placed. Thus, no change in the communication network is
shown in FIG. 2.
[0084] The various embodiments address this overload condition in order to
allow
emergency personnel to use the cellular communication network as they arrive
on
scene, as is illustrated in FIG. 3. When an emergency responder 108 arrives on
scene,
that individual may initiate a wireless telephone call. If a communications
channel
has been allocated to TPA operation and the emergency responder's wireless
device is
pre-registered as a TPA-authorized wireless device, the network can recognize
the
pre-registered TPA authorized wireless device from the wireless device's
unique ID
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
and recognizes the call as a TPA-call. The base station 102, BSC/RNC 103 or
the
MSC 104 may ensure the TPA call is connected. If necessary, the bandwidth
allocated to civilian wireless device users is reduced and one or more non-
emergency
calls may be dropped to enable the TPA call to be connected. This is
illustrated in
FIG. 3 as the connection to wireless device 101c has been dropped and denied
further
access to the network (illustrated as a white lightning bolt), and the TPA
call
(illustrated as a dashed black lighting bolt) by the emergency responder 108
is
connected.
[0085] As additional emergency personnel 109 arrive on scene of the emergency,
additional TPA calls may need to be connected as illustrated in FIG. 4. To
accommodate the increase in TPA calls, additional network resources may be
automatically allocated to TPA operation in order to provide emergency
responders
reliable cellular communications. This is illustrated in FIG. 4 which shows
connected
TPA calls with police 108 and fire 109 personnel (illustrated as a dashed
black
lighting bolts), while wireless devices 101c and 101d have been disconnect
(illustrated
as a white lightning bolts). Automatically allocating more resources to TPA
use
reduces the bandwidth available to the general public, which will limit
general access
to the network. However, emergency personnel are provided reliable access to
the
network so long as the heavy call volume persists.
[0086] Eventually the emergency situation will be resolved and emergency
personnel
will begin to scene. As conditions return to normal, civilian call volume
should return
to normal levels while the number of emergency responders requiring TPA-access
will also decline. This is illustrated in FIG. 5 which shows that the fire has
been
extinguished and firemen have left the scene. As traffic begins returning to
normal
flow fewer general population wireless devices 101a-g access the network
simultaneously. With cellular communications returning to normal, cellular
communications resources may be released from TPA operations, restoring the
network to normal operations. As illustrated, the remaining emergency
personnel 108
are connected to the cellular communication network in the normal fashion as
the call
volume has decreased to the point that TPA operation has been terminated.
16
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0087] When TPA operation is implemented on one or more communication
channels,
the cellular system (e.g., locally in the base station , BSC/RNC, or MSC, or
in a
central location such as a NOC) monitors incoming and outgoing calls to
determine
whether any calls are coming from or directed to emergency response personnel.
This
may be accomplished by recognizing an originating or destination wireless
device as
being TPA pre-registered wireless device. Alternatively, the system may
recognize
emergency response personnel when they complete a special dialing procedure
such
as the *272 dialing procedure described below.
[0088] Wireless devices can be pre-registered for TPA use by authorized users.
This
may be accomplished by registering as a qualified emergency responder (e.g.,
according to criteria established by governmental authorities) with the
cellular
network provider. As is well known in the telecommunications art, all wireless
devices 101 which access the cellular communication are assigned a unique
identification number. In the pre-registration process, the cellular network
provider
stores the wireless device's unique identification number in a database of
authorized
TPA personnel. The cellular network provider may also issue the individual a
unique
Personal Identification Number (PIN) for use in implementing TPA preemption
from
a non-TPA wireless device as described more fully below.
[0089] If the emergency responder's wireless device is not pre-registered
(such as a
borrowed phone), and the network is overload, the emergency responder may be
unable to access network resources. In this situation, the emergency responder
can
activate the embodiment TPA from a non-registered wireless device 101 by first
dialing *272 followed by a personal identification number (PIN) and the
telephone
number. The nearest base station 102 to the non-registered wireless device 101
receives the transmission from the wireless device 101 indicating that the
wireless
device is initiating a call. The base station 102 (or BSURNC 103 connected to
the
receiving base station) recognizes the *272 special dialing prefix and starts
to route
the call to the appropriate destination. Alternatively, recognition and
routing of the
#272 dialing prefix may be accomplished at the MSC 104. This destination may
be
the closest PSAP or central location with a database of PINs. The *272 call is
17
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
similarly processed at the BSC/RNC 103 and later MSC 104 as the call proceeds
through the communication network system. The BSC/RNC 103 and MSC 104
controlling the base station antenna 102 and other associated antennae are
programmed to recognize the special dialing procedure using a database of pre-
registered first responder PINs. This PIN database may be stored at the MSC
104 or at
another central location such as a NOC. If the received PIN matches a record
in the
PIN database, the MSC 104 may immediately give the caller preemptive access to
the
network just as if the call had been made from a TPA-registered wireless
device as
described above. In order to support this capability, a TPA-allocated channel
reserves
sufficient open capacity during TPA-operation to receive and recognize *272
dialed
calls. If the communication channel is at capacity and a dialed number does
not begin
with *272, the call is promptly dropped with no attempt to complete the call.
However, if the dialed number begins with *272, the MSC 104 completes the
process
of comparing the entered PIN to the PIN database and the temporarily
registering the
call as a TPA-authorized wireless device. Non-TPA calls may be dropped if
necessary in order to retain sufficient capacity to receive and recognize *272
calls.
[0090] While reference is made throughout the application to the MSC 104
monitoring
and providing the TPA capability, it should be appreciated by one of skill in
the art
that other elements of the communication system may implement the various
method
steps. These elements may include, but are not limited to equipment collocated
with
the base station antenna 102, the BSC/RNC 103, or a NOC.
[00911 Once a wireless device has been recognized as a TPA-phone by means of
the
*272 dialing procedure, the MSC 104 will track the wireless device and
continue to
treat it as if it were a TPA-registered wireless device so long as at least
one
communication channel is allocated to TPA operation. Using the unique
identification
number assigned to the wireless device, the MSC 104 will recognize subsequent
calls
from the wireless device as TPA-calls without the need for the user to repeat
the *272
dialing procedure. Similarly, the MSC 104 can identify incoming calls to the
first
responder that should receive TPA preemption service. Thus, a first responder
108
using a non-registered wireless device can register the wireless device "on
the fly"
18
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
when TPA is implemented for both incoming and outgoing calls by using the *272
dialing procedure to call one number (such as a dispatcher or "911").
[0092] In an embodiment, a TPA authorized user with a PIN can authenticate any
number of wireless devices using the *272 dialing procedure described above.
This
embodiment will enable first responders, such as a policeman, fireman or
emergency
medical technician, to "deputize" volunteers, such as military personnel,
doctors or
retired policemen that they fmd on the scene, thus creating a reliable ad hoc
emergency communication network. Since the temporary TPA-authorization of a
wireless device established by the *272 dialing procedure is rescinded as all
communication channels in the affected area return to normal operation (i.e.
cease
TPA operation), there is limited concern that the TPA system could be
compromised
for subsequent emergencies provided the authorized user's PIN is not revealed.
Even
if the PIN is revealed, the PIN can be easily changed without significant
impact since
TPA implementation is expected to be an infrequent, random and episodic event.
[0093] In a further embodiment, a user of a TPA-registered wireless device who
does
not have (or forgot) a PIN can register another phone "on the fly," thereby
"deputizing" it for the duration of the TPA event by simply initiating the
special
dialing procedure on any wireless device. For example, the first responder may
use a
TPA-registered wireless device to dial the number of the wireless device to be
"deputized" followed by *272 (any dialing prefix or postscript may be used).
When
this call is received by the MSC 104, the *272 prefix or postscript is
recognized as
indicating that the dialed number is to be treated as a temporary TPA-
authorized
wireless device, allowing it to store the unique ID of the called wireless
device in a
database for tracking such temporary TPA authorizations. Using this
capability, a first
responder can quickly deputize one or more volunteers simply by calling their
numbers.
[0094] In still a further embodiment, emergency response personnel whose
position
does rise to the level of qualifying for pre-registration TPA service or PIN
may still be
the first emergency personnel on the scene of an emergency situation. The user
may
19
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
use his/her non pre-registered wireless device to initiate a *272 special
dialing
procedure. The call may be forwarded to a PSAP which may issue a temporary PIN
and add the wireless device to the database of temporary TPA authorizations.
[0095] Alternatively, if the user initiates a *272 special dialing (or similar
dialing
procedure such as 911), the call may be forwarded to a PSAP. In large scale
crisis
situations, the answering PSAP may be disabled or unable to answer quickly due
to
the large incoming call volume. In such situations, if the *272 call is not
answered by
the PSAP within a predetermined time frame a temporary TPA authorization may
be
automatically issued. Since the circumstances surrounding the issuance of the
temporary TPA authorization have not been fully analyzed by a PSAP operator,
it is
unclear whether the user receiving the temporary TPA authorization is properly
authorized. Accordingly, the temporary TPA authorization may be flagged on the
PSAP monitor for possible deactivation or investigation.
[0096] In a further embodiment, the cellular network is configured to give
calls from a
TPA-registered wireless device and (optionally) temporary TPA-authorized
wireless
devices priority when dialing to a civilian (i.e., non-TPA authorized)
wireless device
within the cell zone(s) implementing TPA operations. When such a call is made,
the
MSC 104 is programmed to route the call to the dialed wireless device through
the
communication channel or channels allocated to TPA operation. If a TPA-
allocated
channel is at capacity when the call from a TPA-authorized wireless device is
received
for a civilian wireless device, another civilian wireless device call is
dropped in order
to provide sufficient capacity to complete the call, with the associated
preemption
process being used to prevent another 911 call from being dropped. This
embodiment
gives emergency personnel the ability to dial-into an emergency. For example,
emergency personnel can use this capacity to call back a civilian who
initially called
911 to report an emergency in order to request an update from a potential eye
witness.
As another example, a first responder can call volunteers within the emergency
scene
without deputizing their phones, assured of being able to reach the volunteers
even
though the communications network is otherwise overwhelmed.
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[0097] TPA operations may be implemented in at least two embodiments of the
present disclosure. In a first embodiment described below with reference to
FIG. 6,
one or more cellular communication channels are dedicating to TPA calls,
providing
emergency personnel with dedicated communication capacity while leaving the
remaining communication channels to the general public. In a second embodiment
described below with reference to FIG. 7, call preemption for TPA calls is
implemented only as a TPA allocated communication channel reaches capacity.
These embodiments are described separately below.
[0098] FIG. 6 illustrates an example process flow of steps that may be taken
to
implement the first embodiment of TPA that may be operable with a computing
device having a processor. During normal operations cellular communication
network
call volume is monitored, block 201. In particular, the cellular communication
network call volume (or number of access requests or engaged bandwidth) are
compared against a predetermined threshold (for example 85% of maximum
capacity), block 202. If the call volume is below the predetermined threshold
a
normal situation is assumed to exist, so the monitoring process returns to
block 201 to
continue monitor call volume. If, however, the call volume (or number of
access
requests or engaged bandwidth) exceeds the predetermined threshold, an
abnormal
situation exists which may indicate that an emergency situation is unfolding.
To
prepare for an emergency situation, network resources (e.g., communication
channels
on a particular base station antenna) are partitioned and reserved for TPA
use, block
203. By automatically allocating a communication channel to TPA use, the
system
permits a TPA-authorized wireless device to gain access to the network, even
when
the network is otherwise overloaded. However, TPA preemption does not occur
until
a TPA-qualified caller attempts to access an overloaded network.
[0099] Since the increased call volume may or may not be in response to an
emergency situation, a communication channel allocated to TPA continues to
function
normally, by handling civilian (i.e., non-TPA) calls in the ordinary fashion.
In
instances where the increased call volume is simply due to coincidental
network
requests and no TPA-qualified user is attempting to place a call, call
preemption
21
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
enabled by TPA is not needed. Thus, the TPA threshold may be exceeded and TPA
implemented even when there is no actual emergency incident. Delaying actual
implementation of TPA preemption until the service is required by a first
responder
increases the reliability of the network under normal circumstances.
[00100] The system may be informed that an actual emergency situation is
occurring
indicated by a TPA-authorized emergency response personnel placing a TPA call
within the affected cell zone. When the communication channel is in TPA mode,
the
cellular system (be it at the base station, BSC/RNC/MSC, or in a central
location such
as a NOC) monitors incoming and outgoing calls to determine whether any
emergency
response personnel is using a TPA-pre-registered wireless device or has
completed a
special dialing procedure invoking TPA preemption, block 204. If no emergency
response personnel has initiated a call using a TPA-authorized wireless device
or the
special dialing procedure, the system may continue to monitor access requests,
in
block 204, as well as call volume, in block 201, to determine if the
communication
channel should be released from TPA operation, block 202.
[00101] If a call is initiated by a TPA-authorized wireless device, or if the
call is
generated from a non pre-registered wireless device using the *272 dialing
procedure,
TPA is initiated, block 205. When TPA is initiated, block 205, only emergency
personnel previously registered or given clearance "on the fly" will be
permitted
access to the partitioned and reserved network resources. As noted above, TPA
will
normally be implemented on a single communication channel initially, leaving
the
remaining channels to general public use. Then, if TPA-use exceeds the
capacity of
the TPA-allocated network resources another resource can be converted to TPA
operation. By dedicating network resources to emergency personnel use one
channel
or one resource at a time, the remaining network resources are left available
for non-
essential general public use. In addition, by dedicating network resources for
emergency personnel communication, emergency personnel are able to both send
and
receive calls on their wireless devices.
22
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00102] In an optional embodiment, upon the initiation of TPA, block 205, the
MSC
104 may survey the wireless devices 101 located within the affected cell or
serviced
by other base station antennae 102 within the same BSC/RNC 103, to identify
all
registered or temporarily registered first responders. These first responders
may be
advised via SMS message (or other methods) that they can utilize the TPA
service by
placing a call or using the special dialing procedure, block 206.
[00103] In a further optional embodiment, the base station 102, BSC/RNC 103,
or
MSC 104 may also send messages to all non-emergency wireless devices 101a-g
within the affected area/cell 100 advising them to avoid using their wireless
device
101a-g except for Emergency 911 calls and to indicate that emergency services
have
been notified, block 207. This messaging may be initiated by the PSAP
responsible
for the incident area, by the local incident Command and Control authority, or
by the
network service provider. Such messages may be delivered via SMS message or
other
communication means. The system may also notify callers connected to the
channel
allocated to TPA use that their calls are being terminated prior to
disconnecting the
calls.
[00104] As the emergency situation continues to unfold and additional
emergency
response personnel appear on the scene, additional network resources may be
required
to support emergency personnel communication. Accordingly, the partitioned and
dedicated network resource may be monitored to determine if additional network
resources should be partitioned and allocated to TPA. This may be accomplished
by
comparing the call volume on the partitioned and dedicated network resource to
a
predefined maximum or minimum threshold, block 208. If call volume exceeds a
predefmed maximum (indicating an escalating situation), for example 25% usage
of
the partitioned and dedicated network resources in the cell site/sector,
additional
dedicated network resources may be partitioned to TPA operation, block 211, to
allow
emergency response personnel to communicate.
[00105] In an embodiment, before terminating calls in order to allocate the
additional
channel to TPA operation, non-essential (i.e., non-emergency personnel)
wireless
23
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
devices 101 that have a call or data sessions in progress with the allocated
channel
may be informed with a warning tone and/or recorded announcement that their
call is
being terminated unless a defined code is entered, block 210. This permits
first
responders to maintain their calls by quickly entering a code (e.g., their
PIN). If an in
process call is an emergency 911 call, the defined code may be supplied by a
PSAP.
[00106] In an embodiment, the system will continue to automatically retrieve
and re-
allocate network resources for emergency response personnel communication
until all
available network resources are dedicated to emergency response personnel use.
Such
an embodiment will maximize communication capabilities of emergency response
personnel. Other embodiments may reserve at least a minimum portion of network
resource (e.g., one communication channel) to enable the general public the
ability to
alert emergency response personnel to new or developing emergency situation,
such
as by placing 911 calls. Accordingly, other embodiments may impose maximum
limits to the amount of network resources that are taken away from the general
population and dedicated to emergency response personnel communication. To
accomplish this, the MSC 104 may determine whether the maximum amount of
network resources have been partitioned and dedicated to emergency response
personnel communication, in block 209. If the maximum amount of network
resources have already been partitioned and dedicated, the MSC 104 may
continue to
monitor the level of utilization of the partitioned and dedicated network
resources, in
block 208. If the maximum amount of network resources that can be partitioned
and
dedicated has not been reached, the MSC 104 may (optionally) inform current
callers
that calls are being terminated, block 210, and reallocate network resources
from
general population usage to emergency response personnel communication use,
block
211. Once the additional communication channel has been dedicated, the MCS 104
will return to monitoring the level of utilization of the partitioned and
dedicated
network resources to determine if the emergency situation is escalating or de-
escalating, block 208.
[00107] As emergency response personnel work to alleviate the emergency
incident
and return conditions to normal, the need for network resources will decrease
as
24
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
emergency personnel exit the scene. To enable the system to return to normal
operations, the MSC 104 may continually monitor the call volume on the
partitioned
and dedicated network resources for an indication of escalation or de-
escalation, block
208. When the level of use of the partitioned and dedicated network resource
drops
below a predefined minimum, the MSC 104 may begin to re-allocate network
resources back to general public usage, block 212. Network resources may be
automatically re-allocated channel by channel, incrementally reducing the
resources
allocated to emergency personnel usage, returning to normal operations in a
stepwise
fashion.
[00108] By demobilizing network resources one channel or network resource at a
time,
the embodiment provides a flexible communication system which may adapt to the
situation as it evolves. If the situation requires more or less network
resources for
emergency personnel communication, the embodiment system and method can meet
the demand while still providing some network resources for the general public
to use.
The system may wait for a period of time after each release of a TPA-dedicated
channel in order to accommodate surges in emergency personnel use during the
event
wind-down phase, thereby avoiding having to repeat the process of dropping
callers,
block 210, unnecessarily.
[00109] Once the cellular communication channel has been re-allocated for
general
public usage, the MSC 104 determines if there are any more network resources
that
are currently partitioned and dedicated for emergency personnel communication,
block 213. If additional network resources are currently partitioned and
dedicated for
emergency personnel communication, the MSC 104 returns to block 208 to
determine
whether the emergency situation is escalating or de-escalating. As the
emergency
situation further de-escalates and returns to normal, emergency response
personnel
require less and less network resources to support their communications. Thus,
the
MSC 104 will continue to automatically re-allocate network resources to
general
public usage in response to call volume, block 212, until all network
resources are in
normal operating configuration for general public use. The MSC 104 may return
to
block 201 and may monitor call volume waiting for the next emergency
situation.
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00110] In the second embodiment, illustrated in the process flow diagram in
FIG. 7,
network resources are incrementally allocated to TPA use at level of
individual calls
by way of call preemption so that public access to the network is maximized
while
meeting emergency personnel use requirements. During normal operations,
cellular
communication network usage is monitored, block 302. Network access requests,
call
volume or engaged bandwidth may be compared to a predetermined threshold (for
example 85% of maximum capacity), block 304. If the usage is below the
predetermined threshold, a normal situation is assumed to exist, so the
monitoring
process returns to block 302 to continue monitoring call volume. If, however,
the
usage exceeds the predetermined threshold, an abnormal situation exists which
may
indicate that an emergency situation is unfolding. To prepare for an emergency
situation, network resources, such as a communication channel on an affected
base
station antenna, are partitioned and reserved for TPA use, block306. By
automatically
allocating a communication channel to TPA use, the system permits a TPA-
authorized
wireless device to gain access to the network, even when the network is
otherwise
overloaded. However, TPA preemption does not occur until a TPA-qualified
caller
attempts to access an overloaded network.
[001111 Since the increased call volume may or may not be in response to an
emergency situation, a communication channel allocated to TPA continues to
function
normally by handling civilian (i.e., non-TPA) calls in the ordinary fashion.
In
instances where the increased call volume is simply due to coincidental call
volume
and no TPA-qualified user is attempting to place a call, call preemption
enabled by
TPA is not needed. Thus, the TPA threshold may be exceeded and TPA implemented
even when TPA call preemption is not required. Delaying actual implementation
of
TPA preemption until preemption is required by a first responder increases the
reliability of the network under normal circumstances.
1001121 With a network resource allocated to TPA operation, the cellular
system (be it
at the base station, BSC/RNC or in a central location such as an MSC) monitors
incoming and outgoing calls, block 308. The TPA-allocated channel continues to
function as a normal cellular communication channel until (a) the channel is
at
26
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
capacity (i.e., current call volume through the channel equals its maximum
capacity)
and (b) a TPA-qualified wireless device attempts to access the network to
place or
receive a call. Call volume on the TPA-allocated communication channel is
monitored to determine if a call must be dropped in order to connect a TPA-
qualified
call. Thus, when a new call is received (incoming or outgoing) that will be
allocated
to the TPA-allocated channel, the system may first determine if that channel
is
presently at capacity (i.e., has as many calls connected as the channel can
reliably
maintain), block 310. If the channel is not at capacity (i.e., there is excess
capacity on
the network), the call may be connected, block 315. This monitoring of the TPA
channel may prevent disconnecting a civilian call if sufficient capacity
exists on the
channel to enable connection of a new incoming or outgoing TPA call.
[00113] As discussed above, the system can recognize a TPA-authorized call by
determining if the source or destination wireless device is a TPA-registered
wireless
device, block 312, and if not by the caller completing a special dialing
procedure. The
dialing procedure may invoke TPA preemption, block 316. In block 315, the call
may
be connected. For example, if the caller is using (or the call is placed to) a
TPA-
registered wireless device the call may be connected. The call may be
connected if at
least one non-TPA call is connected on the TPA-allocated channel, block 314
and
capacity is released to sufficient to connect the TPA call, block 315. This
allows the
TPA-qualified first responder to make a call without delay even though the
network is
at capacity. Similarly, if an incoming call is directed to a TPA-qualified
wireless
device, at least one non-TPA call on the TPA channel is terminated in order to
connect
the incoming call to the TPA-qualified wireless device. The process of
terminating
non-TPA calls from the allocated channel may continue as more calls to TPA-
qualified wireless devices access the network. If the caller is not using a
TPA-
registered phone and did not enter a *272 type dialing sequence, the call may
be
blocked, block 320, as a non-emergency call at a time when system resources
are at
capacity. If the caller has entered the special dialing sequence (such as *272
plus a
PIN), the entered PIN is compared to PIN values stored in a database (e.g., at
the base
station 102, BSC/RNC 103, or MSC 104,) in block 318. If the PIN matches a
27
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
registered emergency personnel, a non-TPA call connected on the TPA-allocated
channel, block 314, in order to release capacity sufficient to connect the TPA
call,
block 315.
1001141 The system may also monitor call volume on the TPA-allocated channel,
block 322 to ensure sufficient capacity remains to accommodate further
emergency
personnel requirements. TPA-call volume (i.e., the volume of calls to/from TPA-
qualified wireless devices) on a TPA-allocated communication channel may be
compared to a threshold value in block 322 to determine when to allocate
another
communication channel to TPA use. If the TPA call volume threshold is exceeded
(i.e., test 322 = "Yes"), another channel will be allocated to TPA functions
block 306,
which is discussed above.
[00115] TPA-call volume on each TPA-allocated channel, block 322, as well as
call
volume on all channels, block 324, may continue to be monitored. This may
determine when TPA calls are no longer being made, as will occur when the
emergency is resolved and first responders leave the scene, or when total call
volume
returns to a level at which TPA operation is no longer required. If call
volume
continues to exceed the TPA threshold, the system may continue to operate at
least
one channel in TPA mode, accepting calls, block 308, checking for TPA channel
call
volume, block 310 and connecting calls, block 315, if the call is from/to a
TPA
authorized wireless device block 312 or if call volume is less than capacity.
As TPA-
call volume declines, the number of channels allocated to TPA-operation can be
reduced by releasing a TPA channel, block326. The monitoring call volume and
releasing of channels from TPA allocation will continue until all
communication
channels are returned to normal operations. Also, if call volume on non-TPA
channels drops back to normal, the system may deactivate TPA operation on all
allocated channels since the normal capacity of the network can accommodate
TPA-
qualified callers without the need for TPA preemption.
[00116] This second embodiment allows TPA-allocated channels to be operated in
a
fashion that ensures every TPA-authorized caller can access the network while
28
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
providing maximum bandwidth possible to the general public. Monitoring of TPA
channel call volume allows the system to avoid dropping civilian calls if
sufficient
capacity exists on the channel to enable connection of a new incoming or
outgoing
TPA call. If no emergency response personnel initiated a call using a TPA-
authorized
wireless device or the special dialing procedure, the system may continue to
monitor
access requests, block 308, and the call volume, block 324, to determine if
the
communication channel should be released from TPA operation, block 326.
[00117] An additional embodiment provides prioritizing access to TPA-dedicated
network resources to enable highest priority callers to use the cellular
communication
network. In a situation where the number of emergency responders can exceed
the
capacity of the cellular network resources, this embodiment may enable high
priority
users, such as national leadership and on-site commanders, to preempt other,
lower
priority users in order to gain instant access to the network. High priority
users can
use their pre-registered wireless devices to gain access to the network. The
unique ID
of their wireless devices can be used to determine the priority of the user
from a
database of unique IDs. Similarly, high priority users can identify themselves
to the
network using the special dialing procedure, with a code or PIN providing
sufficient
information for the network (e.g., the MSC 104) to determine the priority of
the user
from a database of PINs. Using the priority value determined from a database,
the
network (e.g., the MSC 104) can determine whether the present caller has a
higher
priority than any callers already connected to TPA-allocated network
resources.
Assuming the wireless device 101 is properly authorized, the call may be given
priority in the queue on the TPA-allocated network resource so that the
emergency
personnel member using the pre-registered authorized wireless device may be
able to
complete the call. If the network resource is at capacity, a call from a
person with a
lower priority level may be dropped in order to free-up sufficient capacity to
complete
the call.
[001181 FIG. 8 illustrates an example hierarchy of emergency response
personnel.
Various other configurations are possible and other personnel may be included,
and
personnel roles or status may change based on events, for example, the
military
29
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
commander 302 may assume the role of executive leadership, etc. As shown in
FIG.
8, Executive Leaders and Policy Makers 301 may be given highest priority
status.
Members of this class may pre-register their wireless devices 101 such that
the
wireless device 101 unique identifier is stored in a hierarchy database. If a
call is
placed from any wireless device pre-registered to a member of the executive
leader
and policy maker class 301, the call is placed first in any queue of
partitioned and
dedicated network resources. Similarly, Disaster Response/Military Command and
Control personnel 302 may be provided the next highest priority class,
followed by
Public Health, Safety, and Law Enforcement Command 303, Public
Service/Utilities
and Public Welfare 304, and Disaster Response Team 305. Lower level priority
may
be afforded to line police and firefighters 306 and emergency medical
technicians 307.
In all cases, wireless devices may be pre-registered so their unique
identifiers and/or
the user's PIN can be stored in a hierarchy database to support this
embodiment.
[00119] The foregoing embodiments may also be implemented in a cellular system
using a deployable "switch on wheels" cellular communication system. Since
such
systems may be implemented in large scale emergency/disaster situations with
access
limited to emergency responders and command authority, network overload will
occur
from too many authorized (i.e., non-civilian) users placing calls at the same
time. To
ensure reliable communications in such cases, the deployable switch on wheels
can
implement the caller priority embodiment so that callers with highest priority
(e.g.,
national and regional commanders) have assured access to cellular
communications,
while lowest priority authorized users may be disconnected if necessary. In
this
embodiment, a database of authorized users indicating individual priority
(hierarchy)
levels (e.g., illustrated in FIG. 8) may be maintained in a server within the
deployable
switch on wheels.
[00120] The foregoing embodiments have been described as being implemented by
the
MSC 104. One of skill in the art would appreciate that the foregoing
embodiments
may be implemented within a number computer switching system elements within
the
cellular communications network, including but not limited to the base station
102,
BSC/RNC 103 or NOC. Monitoring of call volume on communication channels and
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
within a cell is performed automatically already. Such systems may be
reprogrammed
to implement the foregoing embodiments so that the implementation of TPA
operations is performed automatically. Thus, the system can automatically
recognize
when call volumes exceed thresholds so that a communication channel should be
allocated to TPA operation. The system can further recognize TPA authorized
calls as
described above and dedicate network resources and perform the call
connections and
disconnections described above automatically. Similarly, as call volume
declines
below the TPA threshold levels, the systems can automatically return the
network to
normal configuration. In this manner, the cellular communication network can
respond to emergency situations to enable assured communications for emergency
personnel without the need for human action or intervention. For example, even
if an
event goes unreported (e.g., no one bothers to dial 911), the system will
nevertheless
respond to excess call volume to enable an emergency responder to use the
network.
This capability also ensures police, fire and EMT personnel (typical
individuals who
may be authorized to implement TPA) can use the cellular communication network
during times of peak usage, such as during rush hour on the freeway or
following
conclusion of a major sporting event.
[00121] The hardware used to implement the forgoing embodiments may be
processing elements and memory elements configured to execute a set of
instructions,
wherein the set of instructions are for performing method steps corresponding
to the
above methods. Such processing and memory elements may be in the form of
computer-operated switches, servers, workstations and other computer systems
used
in cellular communications centers and remote facilities (e.g., base station
antenna
locations). Some steps or methods may be performed by circuitry that is
specific to a
given function.
[00122] Wireless devices use the portions of radio frequency (RF) spectrum
dedicated
to cellular telephone communication. This RF spectrum is shrinking at a fast
pace
primarily due to the increasing number of wireless devices using the already
burdened
RF bandwidth and inefficient allocation of bandwidth in the marketplace. Since
the
total RF spectrum is finite, as the number of users of the RF spectrum grows,
more
31
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
efficient methods of RF spectrum management may be required to ensure that the
growing need for RF spectrum is properly addressed.
[00123] The currently available RF spectrum is divided among cellular service
providers based upon static allocation models such as speculation models and
archaic
licensing deals. The currently practiced static allocation models rely on a
command
and control scheme allowing for allocation of spectrum to providers in defined
blocks
of frequency and space. For example, one static method of leasing RF spectrum
includes assigning, based on a leasing agreement, an entire block or sub-block
of
spectrum to one operator for their exclusive use. Such wholesale allocation of
spectrum is inefficient because the licensee provider is purchasing spectrum
based on
a speculation that the spectrum may be used in the future.
[00124] However, the spectrum usage and traffic are dynamic and may depend
upon
different variables including the time of the day the spectrum is used and the
geographic location of the wireless device using that spectrum. Traffic usage
may be
time dependent since usage may vary during peak as compared to non peak hours.
Traffic may also be geographically based since the location where subscribers
use the
network may also vary. For instance, during the day, time and geographically
based
usage of spectrum on a network may vary while subscribers are traveling to
work, at
work, traveling back from work or during off hours.
[00125] Because spectrum usage and traffic are dynamic and impossible to
predict,
providers inevitably waste spectrum resources by speculating regarding its
future use.
Thus, the current spectrum allocation schemes fail to take into consideration
real-time
data about traffic patterns, encourage under utilization and segmentation of
spectrum,
and create further inefficiencies through the implementation of guard bands
and
bandwidth throttling or bandwidth intensive features and services.
[00126] The various embodiment methods and systems provide a Dynamic Spectrum
Arbitrage (DSA) system for dynamically managing the availability, allocation,
access
and use of RF spectrum by using real-time data. Currently, RF spectrum is
licensed or
purchased in frequency and space based upon speculation of future usage and
without
32
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
taking into account real-time data. The DSA communication system makes RF
spectrum available based on frequency, space (i.e., geographical regions) and
time,
thus, providing a flexible and dynamic spectrum management method and system
as
compared to the current static command and control methods. Since the RF
spectrum
resources are available based on time, frequency and space, spectrum allocated
through the DSA communication system may be available for short term leases
and
free from interference. Short term leasing of spectrum may increase
competition in a
given market area and improve spectrum efficiency without negatively impacting
the
carriers' ability to deliver service. By efficiently and dynamically managing
spectrum
availability, allocation, access and use, the DSA communication system may in
effect
increase the RF spectrum availability.
[00127] In an embodiment, the DSA communication system may be a stand-alone
business affiliated with the participating providers. In such a scenario,
components of
the DSA communication system may be integrated units participating network
providers to allow providers to monitor their resources vs. bandwidth traffic
and
determine whether they need or can provide additional resources. The non-
integrated
components of the DSA communication system may manage the overall exchange of
resources between participating providers. Benefits of using the DSA
communication
system may include optimizing commercial yield and providing wider and more
efficient use of bandwidth on physical (geographic) and time bases.
[00128] In an embodiment, the DSA communication system may enable allocation
oVaccess to RF spectrum resources by requiring that the participating
providers
subscribe to the DSA communication system. For example, the subscription may
be
based on a pricing arrangement. As a participant in the DSA communication
system,
the RF spectrum requesting providers may be enabled to use any available RF
spectrum by slipping in and out of the RF spectrum's "swim lanes" in
accordance with
their need for bandwidth and their preparedness to pay for it. One spectrum's
"swim
lane" would be the RF spectrum bandwidth that is owned/controlled by one
provider.
33
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00129] To participate in the DSA communication system, initially the carrier
or
carriers may agree to allow secondary use of their spectrum in the market. DSA
communication system may enable each provider to purchase available spectrum
in
the network of providers or offer to sell additional spectrum to a buyer
provider.
[00130] In an embodiment, the DSA communication system may determine the
compatibilities of the subscriber wireless devices 101 for using the secondary
networks and clusters. Incompatible Radio Access Networks (RAN) may be used if
subscriber devices are capable. Thus, if wireless devices 101 are capable of
accessing
different RANs, the DSA communication system may facilitate the devices'
access to
spectrum from other RANs even if the switch is between incompatible RANs. DSA
communication system is policy based and may offer unique implementations for
spectrum and capacity management. The DSA communication system may be based
on Long Term Evolution (LIE), Evolution-Data Optimized or Evolution-Data only
(EVDO), Evolved High-Speed Packet Access (HSPA) and any known wireless access
platform.
[00131] FIG. 9 illustrates a communication component diagram 900 of an
embodiment
DSA communication system in a wireless access platform based on Long Term
Evolution, LTE. The DSA communication system may include the Dynamic
Spectrum Policy Controller (DPC) 902 connected to a Home Subscriber Server
(HSS)
904 which may communicate with network components of a provider network. The
HSS 904 may be a master user database that supports the Dynamic Spectrum
Policy
Controller (DPC) 902. The HSS 904 may include the subscription-related
information
(i.e., subscription-profile), perform authentication and authorize the
secondary users,
and can optionally provide information about subscriber's location and IP
information. The HSS 904 may contain users' (SAE) subscription data such as
the
EPS-subscribed QoS profile and any access restrictions for roaming. It may
also hold,
store or retain information about the PDNs to which the user can connect. This
could
be in the form of an access point name (APN) (which is a label according to
DNS
naming conventions describing the access point to the PDN) or a PDN address
(indicating subscribed IP address(es)). In addition the HSS 904 holds dynamic
34
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
information such as the identity of the Mobility Management Entity ("MME") to
which the user is currently attached or registered. The HSS 904 may also
integrate the
authentication center (AUC), which generates the vectors for authentication
and
security keys.
[00132] The HSS 904 may be connected to a Signaling Server 7 (SS7) 906. Both
the
Dynamic Spectrum Policy Controller (DPC) 902 and the HSS 904 may be connected
to the Internet 106. The HSS 904 may independently communicate with the in-
network components of a network via the SS7 network 906.
[00133] The DPC 902 may also communicate with the network components of a
network provider through a commercial or private wireless carrier 903 and
Dynamic
Spectrum Controller (DSC) 910 or directly through the DSC 910 without using a
commercial or private carrier. The DSC 910 component may be added to network
components for networks which participate with the DSA communication system
and
may communicate with the OMC/NMS 910. In various embodiments, the DSC 910
component may include a wired or wireless connection to a Policy Control and
Charging Rules Function (PCRF) 905 component/server.
[00134] AVAILABILITY OF SPECTRUM RESOURCES
[00135] In the various embodiments, the DSA communication system may enable a
spectrum provider to monitor and assess its RF spectrum usage and
availability, and
make available unused RF spectrum for use by other providers or unsubscribed
users
(i.e., secondary users). The DSA communication system may provide different
methods to determine RF spectrum availability, such as location and database
lookup,
signal detectors and spectrum usage beacon. The DSA communication system may
enable one provider (host network) to identify spectrum resources which may be
offered for use by another provider or provider subscribers (a secondary
user), such as
on a pay per use or pay per minute basis.
[00136] In an exemplary embodiment, as illustrated in FIG. 9, the DSA
communication system 900 may enable a network to determine availability of RF
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
resources. At each network or sub-network, the DSC 910 may monitor call
traffic
through OMC/NMS 912 to receive detailed status of the various network elements
in
real-time without inserting another device into the network. The DSC 910 may
carry
out policy based QoS decisions based on the status of the existing traffic,
projected
traffic margins and the system policies to determine whether a network or sub-
network has resources to allocate for secondary use or requires resources from
another
provider.
[00137] The DSC 910 may be configured with software to communicate data
regarding the availability of spectrum resources to the DPC 902 using capacity
policy
criteria. The data that is communicated to the DPC 902 may include data
relating to
current excess capacity and expected future capacity of the network or sub-
network.
[00138] The available resources at a network provider may be dynamically
allocated
and de-allocated. The resource poll information may be controlled by the DSC
910
and relayed to the DPC 902 for central coordination. However, based on rule
sets in
the DSA communication system, the DSC 910 may identify resources available for
secondary use on a system level and cluster level as traffic in the system
fluctuates by
increasing and decreasing the resource pool for secondary usage may increase
and
decrease and may be reported to the DPC 902 via the DSC 910.
[001391 ALLOCATION OF AVAILABLE RESOURCES
[00140] In the various embodiments, the Dynamic Spectrum Arbitrager (DSA)
system
may further manage allocation or assignment of RF spectrum resources of a
network
provider for specific uses, such as use by secondary users. The DSA
communication
system may manage RF spectrum allocation based on the providers' varying
criteria,
such as degrees of prioritization (e.g., low priority or no priority), type of
connection
(e.g., "always on" and "surge" guaranteed access and bandwidth), and price.
[00141] In contrast to the currently available spectrum allocation techniques,
allocation of spectrum resources by the DSA communication system may rely on
real-
time traffic status of participating providers. The DSA communication system
36
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
resource allocation may further depend on different factors, such as
availability of
resources, the type of services that are being delivered and the policies
associated with
those services. Some of the key policy criteria that may be considered for
allocating
resources in the DSA communication system may include Radio Access Selection,
Capacity Augmentation, Quality of Service (QoS), bearer selection, Congestion
Control, Routing, Security, and Rating. The DPC and DSC 910 may perform policy
definition and control.
[00142] Radio Access Selection: The DSA communication system may be configured
to make the best available spectrum assignment from the available pool of
resources.
Factors considered in the selection of spectrum assignment may include
spectrum
bandwidth, location of spectrum in the frequency band, geographic zone along
with
the requested service, and QoS.
[00143] Capacity Augmentation: The DSA communication system may be configured
to make the best available capacity augmentation assignment from the available
pool
of resources. Factors considered in the decision may include spectrum
bandwidth,
location of spectrum in the frequency band, geographic zone along with the
requested
service, and QoS.
[00144] Bearer Selection: The DSA communication system may be configured to
select the resources required to support the requested QoS profile at the
radio and
transport bearer services.
[00145] Admission Control: The DSA communication system may be configured to
maintain information of available/allocated resources in both the radio and
the FP
transport network and perform resource reservation/allocation in response to
new
service requests.
[00146] Congestion Control: The DSA communication system may be configured to
monitor traffic conditions on the primary network, and seek alternative
methods for
capacity off load. Additionally, The DSA communication system may be
configured
37
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
to monitor the primary network arid perform back-off of secondary users as
traffic
demand increases on the primary network.
[00147] Routing: The DSA communication system may be configured to ensure that
the optimum route for the service is used based on the bearer traffic and
available
network resources.
[00148] Security: The DSA communication system may be configured to provide
security for the traffic streams by segregating the traffic into tunnels to
ensure no cross
pollination of information.
[00149] Rating: The DSA communication system may be configured to coordinate
rating schemes including prioritization and carrier usage fee and other
metering
processes.
[00150] The DSA communication system resource allocation may be based on
different methods, such as stateless and stateful methods. By employing
different
allocation methods, the DSA communication system may enable providers to
tailor
spectrum allocation and utilization based on their individual spectrum traffic
demands.
The stateless method may involve coordinating spectrum usage between networks
on
a real-time basis. The stateful method may include storing and forwarding
spectrum
resources following defmed time intervals. RF spectrum resources may further
be
allocated on a need basis, which may be based on committed and peak
bandwidth/traffic requirements. The need based allocation method may allow for
the
greatest flexibility and spectrum utilization. The DSA communication system
may
further employ a just-in-time allocation method in enabling the providers to
allocate
spectrum resources. By employing the just-in-time allocation method, the DSA
communication system may improve the overall spectrum utilization for a given
market and provide a revenue source for wireless carriers.
[00151] In an embodiment, the DSA communication system may provide the
command and control functions to enable spectrum to be leased for the entire
license
area or for a defined sub-license area, and for a term. For example, the DSA
38
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
communication system may facilitate spectrum resource allocation using a sub-
spectrum block approach with the ability to increase or decrease the spectrum
consumed dynamically. For example, multiple different communication networks
can
allocate spectrum to the same user.
[00152] As shown in FIG. 9, the components of the DSA communication system
which are not part of a provider's network, such as the DPC 902, may manage
spectrum allocation between different networks or sub-networks.
[00153] In an embodiment, the DSA communication system may enable host
networks
to allocate resources which are currently assigned for use by primary users
for use by
secondary users. In such a scenario, the secondary users may be granted access
to the
host networks' spectrum capacity or resources regardless of existing available
capacity at of the host network.
[00154] GOVERNANCE AND POLICY MANAGEMENT
[00155] The DSA communication system may operate based on pre-determined rules
and parameters which may be based on the statistics of the channel
availability. For
example, operating rules may enable the DSA communication system to monitor
the
level of access to RF spectrum at any given time to allow the system to
determine
whether capacity is available for allocation.
[00156] As described above, resource allocation may be done through the DSA
communication system components, such as the DPC 902 and DSC 910 following the
rules defmed by the business arrangement, device compatibility, target system
RAN,
and capacity and services requested.
[00157] FIG. 9 further illustrates the network architecture 900 of an
embodiment
method for implementing DSA policy governance. The DSA communication system
may require that the participating parties adhere to the governing rules and
policies.
[00158] In implementing the DSA policies, the Policy Control and Charging
Rules
Function (PCRF) 905 of a participating network may provide the policy and
service
39
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
control rules and the Rivada Policy Control Network (RPCN) may provide policy
changes and corrections based on the DSA rules and DPC 902 requirements. The
PCRF may be responsible for policy control decision-making, as well as for
controlling the flow-based charging fimctionalities in the Policy Control
Enforcement
Function (PCEF), which resides in the PGW. The PCRF provides the QoS
authorization (QoS class identifier [QCI] and bit rates) that decides how a
certain data
flow will be treated in the PCEF and ensures that the data flow and
authorization
meets and is in accordance with the user's subscription profile. The RPCN may
be a
part of each network DSC 910. The RPCN may further maintain a Hot List for
public
safety users who may also be linked to the commercial system.
[00159] For example, when resources of a host network is depleting, the
network
PCRF 905/RPCN may instruct the host network to take an action to recover
additional
resources for the preferred users of the home network. The instructions sent
by the
PCRF 905/RPCN may be used to determine the course of action needed to be taken
to
free-up resources for the use of the preferred users. For example, the PCRF
905/RPCN instructions may be to reduce QoS for secondary user wireless devices
101
or certain applications, or shed secondary user wireless devices 101 from the
network
based on a set of conditions. While managing the level of its resources by
reducing
traffic, the host network may implement time slot allocations.
[00160] Some optional subcomponents of the EPC may include the MME 914
(Mobility Management Entity), which is a key control-node for the LTE access-
network and may be responsible for idle mode UE (User Equipment) tracking and
paging procedure including retransmissions and may be involved in the bearer
activation/deactivation process and is also responsible for choosing the SGW
for a UE
at the initial attach and at time of intra-LTE handover involving Core Network
(CN)
node relocation. MME 914 may be responsible for authenticating the user (by
interacting with the HSS). The Non Access Stratum (NAS) signaling terminates
at the
MME 914 and may also be responsible for generation and allocation of temporary
identities to UEs. MME 914 may check the authorization of the UE to camp on
the
service provider's Public Land Mobile Network (PLMN) and enforces UE roaming
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
restrictions. SGW 922 (Serving Gateway) may route and forward user data
packets,
while also acting as the mobility anchor for the user plane during inter-
eNodeB
handovers and as the anchor for mobility between LTE and other 3GPP
technologies.
The POW 908 (PDN Gateway) provides connectivity from the UE to external packet
data networks by being the point of exit and entry of traffic for the UE. A UE
may
have simultaneous connectivity with more than one PGW 908 for accessing
multiple
PDNs. HSS 926 may be a central database that contains user-related and
subscription-
related information. The functions of the HSS 926 include, for example,
mobility
management, call and session establishment support, user authentication and
access
authorization. ANDSF 918 (Access Network Discovery and Selection Function)
provides information to the UE about connectivity to 3GPP and non-3GPP access
networks (such as Wi-Fl). The purpose of the ANDSF 918 is to assist the UE to
discover the access networks in their vicinity and to provide rules (policies)
to
prioritize and manage connections to these networks. Network 900 may also
include
ePDG (Evolved Packet Data Gateway) is to secure the data transmission with a
UE
connected to the EPC over an untrusted non-3GPP access.
[00161] DSA communication system policy and governance may have the same
attributes as those found in a commercial network. However, in the DSA
communication system, the combination of policy driven QoS with dynamic
spectrum
arbitrage/allocation may enhance both the primary and secondary (e.g., lessor
and
lessee) spectrum utilization and reduce the overall costs.
[00162] In an embodiment DSA system, the policy/governance may be set for
specific
levels of network resources per session, per "pipe," per user or a group of
users. The
policy may also relate to the priorities, such as emergency calls getting
highest
priority, or preferences, such as allowing degrading quality for ongoing calls
or
rejecting new ones at near congestion time. DSA policy and governance may also
invoke routine policies which may be applied to facilitate the best route for
a
particular type of communication session and service offering.
[00163] ACCESS TO ALLOCATED RESOUCES OF ANOTHER NETWORK
41
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00164] In an embodiment, the DSA communication system may manage the access
of
users to available RF spectrum resources of a network. For example, the DSA
communication system may manage the access of secondary users to spectrum
resources of a primary host network that are allocated for secondary use.
[00165] The secondary users may access spectrum resources of a primary host
network
using different methods such as, by acting as a dynamic roamer or using a
coordinated
spectrum scheme with compatible access techniques. In allowing the secondary
user
to access a primary host spectrum resources, the DSA communication system may
enable the wireless device 101 of a subscriber of one provider to change
bandwidths
from the spectrum belonging to the home network provider of the wireless
device 101
to one belonging to a host network provider based on different parameters such
as
price, quality of reception, geographic area and location.
[00166] The DSA communication system may provide access to a secondary user
based on different access conditions. The DSA communication system may provide
access to available spectrum either temporarily or by sharing traffic
throughput for a
radio access technique with a primary user of a primary provider. Temporary
access
may involve accessing defined spectrum that was allocated for usage based on
the
policies of the DSA communication system. Sharing spectrum may involve
allowing
the subscribers of one provider to access radio spectrum at a host provider on
a
secondary basis.
[00167] Secondary users' home network providers may employ different methods
to
dynamically contract for allocated RF spectrum resources of a primary
provider. For
example, the primary provider may auction and the secondary provider may bid
for
available spectrum resources. The bidding may be a fee based process; which
may
involve managing the reselling of unused spectrum on temporary or permanent
basis
to efficiently manage excess resources that might otherwise go unused for that
time;
or managing leasing of excess RF spectrum on temporary or permanent basis.
[00168] FIG. 10 illustrates network architecture 1000 of two wireless network
providers using the DSA communication system to share spectrum resources. The
42
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
DSA communication system may be comprised of two general components: Out-of-
network and in-network components. The out-of-network component of the DSA
communication system may include a DPC 902 connected to a HSS 904. The DPC
902 may enable the DSA communication system to dynamically manage the access
to
the allocated spectrum resources of a network. For example, the DPC 902 may
manage the access of secondary users of a network provider to the allocated
spectrum
resources of a primary network provider.
[00169] The DPC 902 may further coordinate DSA communication system policies
and effectuate sharing of relative information between network providers. The
DPC
902 may further facilitate the charging policy and resource requests which may
be
communicated with the networks.
[001701 The DPC 902 may be configured to communicate with one or several
networks (e.g., Network 1 and Network 2) through in-network DSC 910 component
of
each DSA communication system participating provider. In an embodiment, each
Network 1 and Network 2 may include a DSC 910a, 910b which may be an add-on to
the online management center/network management system (OMC/NMS) 912a, 912b
of a wireless carrier. At each network, the DSC 910a, 910b may manage traffic
and
capacity of each network and continuously monitor nodes for capacity
constraints
based upon commands received from or policies and rule sets of the DPC 902.
The
DSC 910 may communicate its findings with the DPC 910.
[00171] Each network may include an OMC/NMS 912a, 912b which may be in
communication with a wireless network 1002a, 1002b. The wireless network
1002a,
1002b may be in communication with wireless access nodes 102a, 102b.
Subscriber
wireless devices 101 may communicate with a wireless access node 102a, 102b.
The
relationship and interconnectivity of these components of the network are
known.
[00172] In an embodiment, the DSC 910a of Network 1 may determine that
additional
resources may be required by Network 1. The DSC 910a of Network 1 may be
configured to send a request for additional resources to the DPC 902. The DPC
902
43
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
may receive information regarding a secondary user wireless device 101a
location and
the network.
[00173] The DPC 902 may be configured to also receive data from other
affiliated
networks such as from the DSC 910b of Network 2. The DSC 910b of Network 2
may be further configured to report to the DPC 902 that specified amounts of
resources are available in Network 2.
[00174] The DPC 902 may be configured to process data received from the
requesting
network (i.e., Network 1) and the supplying network (i.e., Network 2) and
facilitate a
real-time access to the resources of Network 2 by the requesting Network 1.
Once
spectrum resources from Network 2 are made available for access by users of
Network 1, the DSC 910a may instruct the wireless devices 101a to change
networks
and access the spectrum resources provided by Network 2. For example, when a
wireless device 101a of Network 1 requests communication resources, its rule
set may
be validated by the DSC 910 of Network 2. Network 2 may receive the wireless
device's 101a updated information in the PCRF 905 (shown in FIG. 9). The PCRF
905, with other platforms, may allow the secondary user wireless device 101a
to
access the allocated resources of Network 2.
[00175] In an embodiment, the accessibility of resources to a secondary user
through
the DSA communication system may also depend on Host Network Operators policy
and use criteria for those resources. The criteria can include both Radio
Access and
Core Network Resources.
[00176] For example, some of the policy and resource criteria imposed by the
Host
Network Operator may include: Availability of spectrum (e.g., separate or co-
existence); availability of capacity/bandwidth (e.g., RF and Core); overhead
criteria
(e.g., percent total available capacity versus used capacity); existence of
back-off
criteria (e.g., reselection, handover (intra system and inter-system),
termination);
treatment (how specific services/applications are treated/routed); barred
treatments
(e.g., services/applications which are barred for use); rating (e.g., how
services are
rated, i.e., possible special discount for off-peak usage); geographic
boundary (e.g.,
44
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
defining zones or cells for inclusion); time (e.g., defining time and day(s)
for inclusion
including); duration (e.g., defining incremental allocation based on time and
geographic boundary); user equipment types.
[00177] The DSA communication system may enable a secondary network to request
spectrum resources based on: time (e.g., when are resources requested);
required
capacity/bandwidth; treatment (e.g., what services are desired, including
QoS);
geographic boundary (e.g., where services are requested); and duration (e.g.,
for how
long are the resources requested).
[00178] In an embodiment, the communications that may be performed by the DSC
910a, 910b may be transparent to the secondary users. In another embodiment,
the
communication may not be transparent.
[00179] FIG. 11 illustrates a network component diagram 1100 of an embodiment
DSA communication system where spectrum usage and traffic data may be
processed
by a third party or spectrum clearinghouse. The out-of-network component 1102
of
the DSA communication system may include sub-components such as the DPC 902
(shown in FIG. 9). The DPC 902 may communicate with the wireless Networks 1
and
2, by communicating with sub-components of the core network I104a, 1104b. The
out-of-network component 1102 may also communicate with one or both networks
using the Internet or a private network 106. For example, the DSA
communication
system out-of-network component 1102 may communicate with the core network
1104b of Network 2 via the Internet 106 while directly communicating with the
core
network 1104a of Network 1. The core networks 1104a, 1104b may include sub-
components such as the DSC 910, Long Term Evolution (LTE), (EVDO), (HSPA)
and OMC/NMS 912a.
[00180] When Network 1 becomes overburdened and requires additional spectrum
resources, the core network 1104a, may determine a need for spectrum and
request for
additional spectrum resources from the DSA communication system out-of-network
component 1102. Network 2 may determine that it has available an excess amount
of
spectrum resources due to low call traffic. Network 2 may also report the
availability
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
of excess resources to the out-of-network component 1102. Communication
between
the DSA out-of-network component 1102 and Network 2 may be through the
Internet
106. Alternatively, the out-of-network component 1102 and Network 2 may
communicate directly as shown by dashed line 1106. The DSA out-of-network
component 1102 may facilitate the allocation of spectrum resources from
Network 2
to Network 1 which is shown here by the dashed line 1108.
[00181] The wireless device 101b may access the allocated resources by
different
methods. Network 1 may instruct the wireless device 101b to switch networks to
Network 2 to use the allocated resources as a secondary user on Network 2.
Alternatively, the allocated resources of Network 2 may be made available
through
Network 1 enabling the wireless device 101b to use the resources of Network 2
without having to change communications session from Network 1 to Network 2.
For
example, networks 1, 2, and 3 may pool spectrum that can be allocated for use
by
multiple entities.
[00182] FIG. 12 illustrates a communication system 1200 of an embodiment DSA
network. The DPC 902 may provide the master control for the arbitrage process
while
serving several different networks. The DPC 902 may include the policy and
time
dependent arbitrage rules for current allocations. The DSC 910 may be
configured to
also have a local copy of the policy and time dependent arbitrage rules for
the current
allocation. The local copy of the policy and time dependent arbitrage rules
may
ensure that the local control of the network resources may be maintained. In
addition,
the DSCs 910a-910c may be separate platforms interfacing with the network
operations system providing a demarcation point for future network operation
issues.
[00183] In an embodiment, to ensure disaster recovery of the system in the
event of an
incident, the DPC 902 may be configured as a dual mirrored server site (e.g.,
DPC
902a and DPC 902b) or include several servers in a geographically dispersed
cluster.
To secure the network, the DPC 902a, 902b may have a secured link to defined
and
pre-approved network operators 1204a, 1204b, 1204c (e.g., spectrum resource
providers) and system resource requesters 1206, 1208, 1210(e.g., bidders).
46
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00184] In the event of a failure of communication between the DPC 902a, 902b
and
DSC 910a, 910b, 910c, the DSC 910 a, 910b, 910c may be configured to use its
locally saved policy and rule contents to maintain continuity in an arbitrage
process
that has been initiated by the DPC 902a, 902b. However, because of the lack of
connection with the DSC 902a, 902b, the DSC 910a, 910b, 910e may not be able
to
facilitate additional new resource allocations or bids. To ensure that local
control is
always maintained, the DSC 910a, 910b, 910c may be further configured to
control
and locally override components and functions that enable the local operators
to
prematurely terminate or back-off resources from a secondary user.
[00185] For example, DSC 910a may locally store policy and rules of any
communicating DPCs 902a, 902b. As such, if communication between the DPCs
902a, 902b and DSC 910a is compromised after a bid has been processed by a DPC
902a, 902b, the DSC 910a may continue to provide resources to secondary users
of
bidder 1 1206 without having to terminate the secondary users. Additionally,
when
Network A 1204a requires more resources to provide service to its own primary
users,
the DSC 910a may locally control the off-loading of secondary users from
Network A
to free-up resources based on the policies and rules of the DPC 902a, 902b.
[00186] In an embodiment, the process involved in the DSA communication system
may be similar in all cases for flow. As illustrated in FIG. 13A, resources of
a block
of spectrum 1300A may be categorized based on how they are used by a network.
Resources for a given spectrum may be categorized as occupied resources,
uncertain
resources and available resources. The occupied resources may be those
resources
which are currently in use by the carrier and may not be allocated by the DSA
communication system. The uncertain resources may provide a margin for the
carrier
to manage peak loads. The uncertain resources may be used up during the peak
loads
and not used during low peak loads. The available resources may be the subset
of
resources which are not used at all by the network. The available resources
may be
made available for allocation to other secondary providers.
47
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00187] In an embodiment, spectrum resources may be allocated to secondary
users by
different methods. FIG. 13B illustrates allocation of spectrum resources of a
block of
spectrum 1300 licensed by a host network, according to an embodiment. The host
network may license a RF spectrum block 1300a including four channels. The
host
network may dedicate three of the four channels of the RF spectrum block for
use by
the network 1 subscribers. The dedicated channels 1-2 are shaded in the RF
spectrum
block 1300b. As shown by RF spectrum 1300b, Channel 4 may remain unassigned by
the provider. Channel 3 may be partially allocated, partially transitional and
partially
unassigned as illustrated by spectrum block 1300c. The transitional section of
the
spectrum block 1300c may be reserved for use during high traffic periods by
the
provider's subscriber. The unassigned portions of the licensed spectrum 1300c
may
never be used.
[00188] In an embodiment, the host network may sublicense the unassigned
portion of
the licensed spectrum to secondary users using the DSA communication system.
In
such a scenario, the host operator may make available to secondary users the
unassigned portion of channel 3 and all of channel 4.
[00189] FIG. 14 illustrates allocation of spectrum resources including a guard
band
channel of a licensed spectrum 1400, according to an embodiment. The licensed
spectrum 1400 may include a guard band 1404 that is either defined or set
aside by
operators as part of a spectrum deployment policy and program. Such guard
bands
may include usable resources that currently remain unused. The host network
may
allow the resources available in the guard bands to be used by secondary users
using
the DSA communication system. By using the DSA the host network may make
available for use the unused guard band resources by combining the guard band
into a
single usable channel 1402 for resource allocation.
[00190] FIG. 15 illustrates pooling and allocation of spectrum resources of
more than
one host networks using the DSA communication system, according to an
embodiment. In an embodiment, the DSA communication system may be configured
to survey the available spectrum from different networks and pool the
available
48
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
together for allocation. In an exemplary embodiment as shown by spectrum block
(1),
each of the host networks, network A and network B, may license a block of
spectrum
including four channels each. For example, the block of spectrum 1502A
licensed by
network A may include channels 1A, 2A, 3A, and 4A. The block of spectrum 1502B
licensed by network B may include channels 1B, 2B, 3B, and 4B.
[00191] In the exemplary embodiment as shown by spectrum block (2), the
spectrum
block 1504A of network A may include available channel 4A and partially
assigned
channel 3A. Channel 3A may be partially assigned for use by the network,
partially
transitional and partially available for use by other networks. The spectrum
block
1504B of network B may include available channels 1B and 4B and partially
assigned
channel 3B. Channel 3B may be partially assigned for use by the network,
partially
transitional and partially available for allocation to other networks.
[00192] In an exemplary embodiment as shown by spectrum block (3), each
spectrum
block 1506A, 1506B of network A and network B may make available their
resources
using the DSA communication system. The DSA communication system may pool
the available resources from each network and allocate them for secondary use.
For
example, the DSA communication system may pool the resources available in
channels 1B and 4B and make them available to secondary users. The DSA
communication system may pool the resources available in channel 4A and the
partial
resources available in channel 3A and make them available to secondary users.
[00193] The DSA communication system may pool available resources from
different
networks for allocation to secondary users. In an exemplary embodiment, as
shown in
spectrum block (4), the DSA communication system may pool available resources
from channel 4A in network A, spectrum block 1508A and channels 1B and 4B in
network B, spectrum block 1508B, and make them available to secondary users.
[00194] In an exemplary embodiment, as shown by spectrum block (5), the DSA
communication system may pool available resources from all channels in
different
networks, including channels with resources that are fully committed for use
by the
network and channels which include available resources. The DSA communication
49
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
system may pool spectrum resources from channels 3A and 4A in network A,
spectrum block 1510A, and channels 1B, 3B and 4B in network B, spectrum block
1510B, and make them available to secondary users.
[00195] In an embodiment, the DSA communication system may enable Mobile
Virtual Network Operators (MVNO) to utilize unused spectrum capacity. For
example, the DPC 902 may aggregate multiple MVNO's to utilize unused spectrum
capacity in a prioritization scheme. This would enable an MVNO to sell its
unused or
under used capacity to another MVNO thereby ensuring that both MVNO's
operating
efficiently.
[00196] FIGs. 16A-16C illustrate MVNO spectrum aggregation according to an
embodiment. FIG. 16A illustrates the allocation or capacity of spectrum for
MVNO
A 1602A and MVNO B 1602B where both operators possess unassigned spectrum
capacity. FIG. 16B illustrates an exemplary embodiment method by which the DSA
communication system may enable the MVNO B 1604B to increase or augment its
available spectrum capacity by receiving unassigned spectrum from MVNO A
1604A.
FIG. 16C illustrates an exemplary embodiment method by which the DSA
communication system may be enabled one MVNO C 1606C to receive additional
spectrum capacity from two other MVNO's 1606A, 1606B. The MVNO C 1606C
may be a new or additional MVNO and may obtain the available unassigned
spectrum
capacity from MVNO A and B 1606A, 1606B for its potential use. In this
scenario,
MVNO A and MVNO B 1606A, 1606B may or may not operate on the same host
carrier and may or may not have the same Radio Access Technology (RAT). In
another embodiment, a conversion may be provided to provide access between
different RAT.
[00197] In an embodiment, to measure the quantity of the resources that are
used by
secondary users, the host network may use similar processes as used for pre-
paid users
to facilitate the time/duration and usage metering of secondary uses which can
be
done at an individual or global account basis.
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00198] Depending on the method used by secondary users to access available
resources, several fundamental types of DSA allocation methods may be
implemented, including: 1) virtual-best effort method; 2) virtual-secondary
users
method; and 3) spectrum allocation method which may include License area and
Regional area spectrum allocation. Each of these allocation methods may have
several variations. For example, in a virtual-best effort method, the DSA
communication system may be configured to make available spectrum resources
for
an entire license area or on a regional, sub-license area basis. Classes of
the users may
also be defined in user's wireless devices 101 by their home network providers
and
may be assigned either secondary user or best effort user statuses.
[00199] In an embodiment, Resources in the virtual-best effort method may be
available to the MVNO through a grant of access to the network involved.
Prioritization may occur within the host network based on PCRF rules of the
home
and host networks.
[00200] In the virtual-best effort method, the host network may enable the
secondary
user wireless devices 101 to use the same network as the host network but on a
virtual
basis, i.e., an MVNO type of arrangement. Different variations of this
arrangement
may include situations when 1) the secondary user uses the host network with
the
same rights as the host network subscribers and 2) the secondary user uses the
host
network as a secondary user or on a secondary basis where primary users (host
subscribers) have higher priority and rights than the secondary user
subscribers.
Access priority for primary users may be established in networks where the
primary
users are public safety users. During emergency situations, the host network
may
drop secondary users due to an increase in use of its spectrum by other users
such as
public safety primary users.
[00201] FIG. 17 illustrates a communication system 1700 of a DSA communication
system for allocating resources according to an embodiment. In a virtual-best
effort
method, the wireless device 101 may be considered a valid roamer as shown in
FIG.
17.
51
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00202] During the bidding process, the DSA communication system may implement
a
rule sets which may be used to define the types of services, treatments and
duration of
services for the wireless devices that are granted access to the host network.
The rule
sets may include information such as: 1) requested capacity/boundary; 2)
treatment of
services such as when they are required and the QoS; 3) geographic boundaries
based
on the requested service; 4) time for when resources are requested; and 5)
duration for
which requested resources would be used by the secondary user. It is
contemplated
that all or a sub-set of these rules may be used depending on the arbitrage
scheme.
[00203] In the virtual-best effort method, the DSA communication system may
follow
the industry roaming process in that access to spectrum may be granted to the
secondary users provide the service requesting wireless devices meet the
required
authentication processes. Validation/authentication of the secondary user
wireless
devices 101 may be performed following standard MAP/IS-41 processes through
the
use of the host's HSS 926 and AAA.
[00204] Additional criteria that the DSA communication system may add to the
process of roaming may include different billing schemes. For example,
secondary
user's wireless device's 101 access duration or total usage permissions may be
governed by the host network. Such governing schemes enable the host network
to
control the access of the secondary users locally and on a real-time basis. In
the
virtual-best effort method, the DSA communication system may not reserve
resources
and merely track the consumption of resources.
[00205] In the virtual-best effort method, the primary or host network
provider may
not grant prioritization to the secondary users except through differentiation
afforded
by the PCRF 905 and PDN Gateway (PGW) 908 of the host network provider. To use
the resources of a DSA communication system using the virtual-best effort
method,
the secondary users may either use the PGW(s) 908 of the host network of or
the
secondary network's PGW which may be either connected to the appropriate
Serving
Gateway (SGW) 922 of the host network or connected to the PGW of the host
through
an intermediate PGW 908 that is governed by the host network.
52
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00206] The PGW is responsible for EP address allocation for the wireless
device 101,
as well as QoS enforcement and flow-based charging according to rules from the
PCRF. It is responsible for the filtering of downlink user IP packets into the
different
QoS-based bearers. This is performed based on Traffic Flow Templates (TFTs).
The
PGW performs QoS enforcement for guaranteed bit rate (GBR) bearers. It may
also
serve as the mobility anchor for interworking with non-3GPP technologies such
as
CDMA2000 and WiMAX networks.
[00207] All user IP packets may be transferred through the SGW, which serves
as the
local mobility anchor for the data bearers when the wireless device moves
between
eNodeBs. The local mobility anchor point for inter-eNodeB handover includes
downlink packet buffering and initiation of network-triggered service
requests, lawful
interception, accounting on user and QCI granularity, and UL/DL charging per
wireless device. SGW also retains the information about the bearers when the
wireless devices are in the idle state (known as "EPS Connection Management ¨
IDLE" [ECM-IDLE]) and temporarily buffers downlink data while the Mobility
Management Entity (MME) initiates paging of the wireless devices to
reestablish the
bearers. In addition, the SGW performs some administrative functions in the
visited
network such as collecting information for charging (for example, the volume
of data
sent to or received from the user) and lawful interception. It may also serve
as the
mobility anchor for interworking with other 3GPP technologies such as general
packet
radio service (GPRS) and UMTS.
[00208] The MNIE is the control node that processes the signaling between the
wireless device and the CN. The protocols running between the wireless device
and
the CN are known as the Non Access Stratum (NAS) protocols (eMM, eSM) and
security, AS security, tracking area list management, PDN GW and S-GW
selection,
handovers (intra- and inter-LTE), authentication, bearer management. The MIVIE
also
contains mechanisms for avoiding and handling overload situations.
[00209] An eNodeB performs Radio Resource Management functions, such as radio
bearer control, radio admission control, radio mobility control, scheduling
and
53
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
dynamic allocation of resources to wireless devices in both uplink and
downlink. The
eNodeB may perform Header Compression which refers to the process of
compressing the IP packet headers that could otherwise represent a significant
overhead, especially for small packets such as VolP to help ensure efficient
use of the
radio interface. The eNodeB may perform Security functions by ensuring that
all data
sent over the radio interface is encrypted.
[00210] In an embodiment, the virtual-best effort method may enable the DSA
communication system to manage resources allocation by using different
methods.
For example, the host network's PCRF 905 may control the secondary users'
wireless
devices 101 that access the host network and track the usage of the resources.
The
host network's billing system may be used to bill the secondary user.
[00211] Alternatively, the host network's billing system may control/track the
usage of
the resources by the secondary user, and the secondary user's home network
PCRF
905 may provide preferred services. In such a scenario, the PCRF 905 of the
host
network may retain final control.
[00212] Alternatively, the host network may provide access and secondary
user's
home network's PCRF 905 may define the preferred services. Additionally, as
part of
the allocation process using the virtual-best effort method, different TAI's
may be
assigned to the secondary user's wireless devices which roam onto the host
network.
The TAIs may provide differential service areas or defined geographic zones
for
potential usage. In an embodiment, the subscriber wireless devices may be
allowed to
access the home network through identification of a valid PLMN that it has in
USIM
that is either pre-programmed or provided through OTA provisioning. The home
network may direct subscribers to use a host network as secondary users for
different
reasons. Additionally, if the wireless device 101 is capable of accessing two
networks
at the same time, the wireless device 101 may potentially use the home network
for
one type of service and be directed to use a host network for other services.
[00213] In an embodiment, available resources may be allocated to secondary
users
using a virtual-secondary user method (e.g., an Intra-System (i.e., Infra
freq¨lessor, or
54
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
Intra freq prime¨lessee)). In the virtual-secondary user method, the primary
host
network may allow the secondary users of the secondary network to operate
using the
primary network's system spectrum resources with different usage rights as
compared
to the primary users, such as on a de facto lease but with a different SID.
This may be
achieved by allowing the secondary users to include spectrum allocation from
the
primary host network when there is technology compatibility between the
primary
network systems and the secondary user wireless device 101. This allocation
may be
applied to the mobile virtual network operator mobile that provides mobile
phone
services but does not have its own licensed frequency allocation of radio
spectrum,
nor infrastructure required to provide mobile telephone service.
[00214] In a virtual-secondary user method, the prioritization of the
secondary users
may follow the host network's PCRF 905 and PGW 908 rules. The PGW(s) 908 that
may be used by the secondary wireless devices 101 may either be controlled by
the
host network or available through the secondary user's home network. If the
PGW
908 is available through the secondary users' home network, it may either be
connected to the appropriate SGW 922 or provided through an intermediate PGW
908
that is governed by the host network. In such a scenario, a secondary user may
be
considered a valid roamer in the DSA communication system using the virtual-
secondary user method as shown in FIG. 17.
[002151 In a virtual-secondary user method, the DSA cormnunication system may
use
five fundamental bidding rule sets, which are used to defme the types of
services,
treatment and duration for the secondary user wireless devices 101. The rule
sets may
include information such as: 1) requested capacity/boundary; 2) treatment of
services
such as when they are required and the QoS; 3) geographic boundaries based on
the
requested service; 4) time for when resources are requested; and 5) duration
for which
requested resources would be used by the secondary user, and other rule sets
as
applicable. It is contemplated that all or a sub-set of these rules may be
used
depending on the arbitrage scheme.
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00216] In an embodiment, when employing the virtual-secondary user method, a
host
network may grant access to a secondary user wireless device 101 provided it
meets a
predetermined required authentication process. The host network using a
virtual-
secondary user method may use different billing schemes where the wireless
devices
101 access or usage total is governed by the rules and specifications of the
host
network, allowing the secondary user devices 101 to be controlled locally. As
secondary users in the system, the wireless devices' 101 access to the host
network
can be restricted, reduced, or barred depending on the conditions of the host
network.
The restrictions, reduction or barring may be imposed on a call, on a regional
or
system wide basis depending on the conditions set forth by the host network in
the
bidding system. The restrictions, reductions or barring may further be
performed on
dynamic basis by overriding the bidding conditions (e.g., in public safety
networks).
[00217] Authentication or validation of the secondary wireless device user may
be
performed following the standard MAP/IS-41. Using MAP/IS-41, the host HSS 926
and AAA may authenticate secondary user wireless device.
[00218] In an embodiment, when using the virtual-secondary user method, the
DSA
communication system may require that different components of the host and/or
home
networks be used for resource allocation. For example, the host network
billing
system and PCRF 905 may control the secondary user's access to the network and
track its usage. Alternatively, the host network's billing system may control
and/or
track usage and the secondary users' home network PCRF 905 may provide
preferred
services and the network PCRF 905 may perform the final control.
Alternatively, the
host network may provide access in the home network PCRF 905 may defme the
preferred services.
[00219] When resources that are allocated using the virtual-secondary user
method are
near exhaustion either based on time, usage or other criteria, the DPC 902 may
notify
the home network operator in the host network that the resources may expire.
The
home network operator, if allowed, may be enabled to top off or replenish the
resources available to the secondary user by requesting foreign bidding on
additional
56
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
resources at the host network or otherwise provide additional RF spectrum
resources.
To provide additional flexibility to the resource allocation process,
different TAI's
may be assigned to the secondary user's wireless device that is roaming the
host
network. The TAI's may provide differential service areas or different
geographic
zones for potential use.
[00220] In an embodiment, the secondary user's wireless device may be able to
access
the home network through identification of a valid public land mobile network
or
PLMN that it may have stored in its universal subscriber identity module
("USIM").
The USIM may be either pre-programmed or provided through OTA provisioning.
When using the home network, the secondary user's wireless device 101 may be
redirected to search for a host network from which it can receive services.
Once a
host network is identified, the secondary user wireless device 101 may use the
host
network for all services, or use the host network for one type of service.
Additionally,
the use the home network can be for other services if the wireless device 101
has the
capability of accessing two networks at the same time. Various configurations
are
possible and within the scope of the present disclosure.
[00221] FIG. 18 illustrates a communication system block diagram 1800
illustrating
communications between components of two networks in a DSA communication
system during resource reservation according to an embodiment. In an
embodiment,
the host network's (i.e., lessor) configuration may be controlled by the OMC
912.
Additionally the home network (i.e., lessee) 1802 may be separate from the
host
network 1804.
[00222] In an embodiment, the host network using the virtual-secondary user
method,
may reserve resources by using different methods, including: 1) X-furcating of
the
eNodeB; 2) SGW and PGW link bandwidth; 3) combined resource allocation (PGW
and eNodeB); and 4) PCRF (host) control. These resource reservation methods
may
be used in combination or may be mutually exclusive depending on the host
networks
requirements and the bidding process.
57
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00223] By x-furcating the eNodeB, resources may be reserved for secondary
users.
In an exemplary embodiment, as illustrated in FIG. 19, the eNodeB 916b may be
bifurcated to reserve resources for secondary users. The eNodeB 916b may
receive
bifurcating instructions from the PCRF 905, MIVIE 914 and SGW 922 to partition
a
percentage if its resources which may be used for another PLMN network. The
PGW
908 may be located at the host network or may be located remotely. According
to the
received instructions, the eNodeB 916b may reserve X% of the resources for the
use
of the primary users and Y% of the resources for use by secondary users. The
eNodeB 916b may transmit an enhanced PLMN (ePLMN) which may be recognizable
to the secondary user wireless device 101h and camp on the cell.
[00224] In an embodiment, resources may also be reserved through controlling
of the
connectivity between the SGW 922 and the PGW 908 to which the secondary user
wireless device is assigned.
[00225] FIG. 20 illustrates an embodiment method for controlling the SGW 922
and
PGW 908a, 908b link bandwidth allocation scheme according to an embodiment.
Resource reservation may be controlled by controlling the host SGW 922
connectivity
to the various PGW 908a, 908b. The SGW 922 connectivity to the PGW 908a, 908b
may be controlled through altering the available bandwidth between SGW 922 and
PGW 908a, 908b on a dynamic basis. The PGW 908a, 908b may be local and/or
remote with respect to the host network. The SGW 922 and PGW 908 link
bandwidth
may be altered through the OMC/NMS 912 which may be connected to the DSC 910.
PGW 908a may be located at a host network or remotely.
[00226] In an embodiment, illustrated in FIG. 21, resources may be reserved
for
allocation purposes by combining eNodeB x-furcation and SGW-PGW link
bandwidth control methods.
[00227] In an embodiment, the host PCRF 905 may control resource reservation
for
allocation to secondary users. The host PCRF 905 may prioritize the secondary
user
wireless device 101 based on the services requested using a combination of the
QCFARQ ARQ may be an automatic repeat request. In this scenario, the PCRF 905
58
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
may assign a QCJJARQ to the primary user wireless devices 101a and the
secondary
user wireless devices 101b.
[00228] In an embodiment, the RF spectrum allocation method may be used to
make
resources available for allocation. In the spectrum allocation method (e.g.,
Inter-
System (Inter freq¨lessor, Inter freq prime ¨lessee)) the primary network may
assign
spectrum resources for the use of the secondary users in a geographic region.
Based
on this, the secondary network providers may make available the primary
network
resources as channels/spectrum of their own normal operational network (i.e.,
can be
compatible or IRAT). This, also, may be applied to MVNO. Thus, secondary users
may access the primary network resources on their home networks and without
having
to roam onto the primary network.
[00229] The spectrum allocation method may be based on a) licensed area; or b)
regional area. In both the license and regional area methods of spectrum
allocation,
spectrum available for use by the primary network provider operators (i.e.,
lessor or
Network 1) may be programmable through the OMC/NMS 912. Spectrum allocation
method may enable the host network to allocate spectrum based on desired
bandwidth,
geographic boundary of the secondary user, time the secondary user request
resources,
and duration of time for which the secondary user request resources.
[00230] In an embodiment, the spectrum allocation method may make spectrum
resources available to secondary users on a dynamic basis. The billing process
for the
spectrum allocation method may not involve the use of the host or the visiting
networks billing platforms. Instead, the DPC 902 may coordinate the billing
for this
effort.
[00231] In contrast to the virtual-best effort or virtual-secondary user
methods, the
spectrum allocation method may enable the home network operator (Network 2) to
use the allocated resources for the secondary user wireless device 101 and not
share
the allocated resources with the primary host network. Therefore, the
allocated
spectrum resources may be used by the secondary users for the duration of the
lease.
59
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
The secondary user home networks may also be enabled to control the allocated
resources for the duration of the lease by using their radio access network
nodes 102.
[002321 FIGs. 23A and 23B illustrate an embodiment for allocating spectrum
resources to a license area 2300 using the spectrum allocation method. When
allocating spectrum resources to a license area 2300, the primary host network
may
allocate a defmed amount of spectrum resources to be used by secondary user
home
networks. Each network operator of the secondary home network may be granted
use
of the allocated spectrum over a geographically defmed license area. As
illustrated in
FIG. 23A, a block of spectrum license 2300 may belong to a specific license
area
2300.
[00233] The license area spectrum allocation method may involve partitioning
the
block of spectrum 2302 which may be used over the entire license area.
Partitioning
may be accomplished in various different channels, by sharing channels, or by
other
methods. As shown in FIG 23B, the block of spectrum 2302 may be partitioned to
provide three channels 2304a, 2304b, 2304c for use by the primary users and
channel
2304d for leasing.
[00234] FIG. 24 illustrates an embodiment for allocating spectrum resources to
a
regional area using the spectrum allocation method. The regional area spectrum
allocation may involve allocating spectrum within the host network's defined
license
area 2300. The primary host network may allocate certain defined geographic
areas.
The areas border the secondary users which may use the allocated spectrum
resources.
Therefore, the geographic area designated for the use of the allocated
resources may
be a sub-area of the entire license area 2300 in which operators have access
to the
spectrum. The host network (i.e., lessor) may lease, sell, option, or
otherwise transfer
resources on a temporary basis to other secondary operators for their use in
the
geographically defined sub-areas. This may allow the primary host operator to
reserve the use of other geographic areas to the use of their primary users or
for
leasing to other secondary networks.
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00235] A single resource allocation may be defined for possible use in an
operator's
license area 2300. For example, Channel (4) 2302d may be licensed through the
DSA
communication system to a successful secondary user bidder for regions A 2402.
The
same Channel 4 may also be licensed to another secondary user bidder for
region B
2404. Outside of regions A 2402 and B 2404, the full spectrum (Channels 1-4)
2302
may be used by the primary network. In regions A 2402 and B 2404, only
Channels
(1-3) 2302a, 2302b, 2302c may be used by the primary network operators. In
regions
A 2402 and B 2404, the primary user may not use Channel (4) 2302d which is
licensed to secondary network providers. For example, a bidder for a resource
may
engage in many different contractual relationships for spectrum including
leasing,
buying, optioning, trading, pool, or otherwise transfer spectrum.
[00236] Once available resources are allocated, they may be accessed based on
different methods. The spectrum access methods may depend on the method of
allocation used by the network which is providing the resources. In general,
spectrum
access methods may be divided into two categories of roaming and non-roaming
methods. When resources are accessed based on a roaming method, a secondary
user
wireless device 101 may be required to use the available resources by roaming
onto
the primary network. When resources are accessed based on non-roaming methods,
the secondary user wireless device 101 may be allowed to remain on its home
network
while using the allocated resources.
[00237] FIGs. 25A and 25B illustrate two network diagrams showing access to
resources using roaming arrangements to allow a wireless device 101 to use
resources
of another network according to an embodiment. As illustrated in FIG. 25A, a
wireless device 101 may currently use the spectrum of Network 1. Network 1 may
communicate to DPC 902 that the additional spectrum resources may be required
to
continue service to the wireless device 101. DPC 902 may also receive
information
from Network 2 which may have additional or excess spectrum resources that may
be
allocated for use to the wireless device 101 from other networks.
61
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00238] As illustrated in FIG. 25B, once the DPC 902 confirmed that Network 2
has
spectrum for allocation, based on the services being used, time and/or
geographic
location, the wireless device 101 may be instructed to switch carriers from
Network 1
to Network 2.
[00239] In an embodiment, a secondary user network provider may license or
lease the
right to use spectrum resources that are allocated by a primary network. In
such a
scenario, the secondary user device 101 may not be required to roam onto the
primary
network to use the allocated spectrum resources. The secondary user device 101
may
remain on the secondary home network which may make available the resources of
the primary network through the secondary network access points based on the
licensing terms.
[00240] FIGs. 26A and 26B illustrate a further spectrum allocation method
using short
term leasing of resources according to an embodiment. Available spectrum may
be
leased to other networks by employing the DSA communication system, based on a
license area, sub-license area or by individual nodes, cell site. DSA
communication
system may make available such leased spectrum for secondary use through other
networks following a geographic and space boundary determination. In an
embodiment, a secondary user may access allocated spectrum of a host network
through its own secondary network and without having to switch to the host
network.
[00241] FIG. 26A illustrates a wireless device 101 in communication with the
wireless
access node 102a of Network 1. Network 1 may have a licensing agreement with
Network 2 to use a designated block of the spectrum of Network 2. In such a
scenario, when the spectrum resources of Network 1 are exhausted and
additional
resources are required, Network 1 may use the licensed secondary spectrum
resources
to communicate with the subscriber wireless devices 101. FIG. 26B illustrates
a
wireless device 101 in communication with Network 1 using licensed secondary
spectrum resources of Network 2.
[00242] Licensing of spectrum resources may enhance the capacity of a network
as
illustrated in FIGs. 27A and 27B. As shown in FIG. 27A, network provider A may
62
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
serve a wireless device 101 through different wireless access points 102a,
102b, 102c
depending on the geographic location of the wireless device 101. The wireless
access
points 102a, 102b, 102c may serve the wireless device 101 using spectrum
resources
from network provider A.
[00243] Due to increased traffic, network provider A may requires additional
spectrum
resources to properly serve its subscribers. Network provider A may license or
lease
spectrum resources from network provider B to enhanced and augment its
available
spectrum resources. As illustrated in FIG. 27B, spectrum capacity enhancement
of
provider A may be achieved through co-use of the radio access platform with
provider
B. In such a scenario, the wireless access point 102a, 102b, 102c may
broadcast
spectrum signals received from both providers A and B.
[00244] INITIAL CELL SELECTION
[00245] Cell selection or origination may involve the situation where the
wireless
device 101 of one network is directed to another network for accessing
additional
resources available on the new network. Currently, wireless devices 101 are
programmed to establish connection with the correct networks for receiving
services.
To find the correct networks, once the wireless device 101 is powered on, it
may
search preferred Public Land Mobile Networks (PLMN), preferred roaming list
(PRL)
and radio carriers that the device is authorized to use. The PLMN/PRL and list
of
radio carriers may be provisioned on the wireless device. The PLMN/PRL list
may
include PLMN identifications of authorized networks and carrier in ranked
order.
[00246] Because the DSA communication system may provide dynamic and real-time
access to spectrum resources, when using the DSA system, spectrum resources
may be
available at networks which are not listed on the wireless device's PLMN/PRL.
[00247] As part of the DSA communication system process the wireless device
101
may be programmed in advance with the appropriate PLMN list. Further, the
wireless
device 101 may also be provisioned over-the-air on the secondary home network.
The
63
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
over-the-air provisioning may provide instructions to one or a group of
wireless
devices 101 to reinitiate the cell selection process with an updated PLMN
list.
[00248] Alternatively, the wireless device 101 may be configured with a client
application which upon receipt of a WAP/SMS message enables the wireless
device
101 to search for a PLMN that has been made available in the DSA process.
[00249] Several methods may be used to allow the wireless devices to access
available
resources on different networks. In the DSA communication system, there are at
least
two types of networks or source systems: virtual or existing networks. Virtual
networks may include networks that utilize the Radio Access Network (RAN) of
the
primary network. When wireless devices 101 are required to access virtual
networks,
the regulatory features and requirements for emergency calls (e.g., 911 calls)
and
other regulatory stipulations may need to be addressed.
[00250] When connecting to virtual networks, the DPC 902 of the primary
network
may control the access of the secondary user wireless device 101 and access RF
spectrum resources and the subscriber records of the primary system to allow
the
secondary users to appear as roamers on the primary network. The secondary
user
wireless devices 101 may use a list of preferred networks to access virtual
networks.
[00251] Alternatively, when originating using existing networks, the secondary
user
wireless device 101 may make a cell selection based upon a priority list of
networks
participating in the DSA communication system. Once the secondary user
wireless
device 101 is authenticated, the DPC 902 of the primary host network may
validate
the secondary user to access resources on the primary network. If
authentication or
validation is not successful, the DPC 902 of the primary user may send a
request to
the secondary wireless device 101 via a client in the device to re-originate
onto the
proper system.
[00252] Wireless devices 101 may include a universal subscriber identity
module or
USIM. The USIM may be a single or dual USIM. Critical information such as data
required to select the correct network may be stored on the USIM. By using a
USIM,
64
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
a wireless device 101 may be enabled to no longer use a PLMN. USIM may have
stored upon it information such as home International Mobile Subscriber
Identity, or
IIVISI (HPLMN), prioritization list of permitted VPLMNs and forbidden PLMNs
list.
[00253] If a wireless device 101 uses a dual USIM, it may be enabled to
immediately
access spectrum resources available in an alternative network. The dual USIM
may
further enable a multiband, multimode wireless device 101 to access a variety
of
networks in the DSA as well as using standard roaming arrangements.
[00254] FIG. 28 illustrates an embodiment method 2800 for network and cell
initialization by a wireless device 101 in the DSA system. The initial network
and cell
selection may begin with the wireless device 101 when it is either powered on
or
trying to reestablish connectivity, block 2802. The wireless device 101 may
initially
search the PLMN/PRL list that is stored on the device, block 2804, and select
a cell by
receiving, reading and determining the strength of nearby cell site broadcast
channels,
block 2806.
[00255] The wireless device 101 may read the cell site broadcast channel and
determine whether the cell site offers the correct system, determination 2808.
The
wireless device 101 may select and establish a connection to the best cell
site
available. To identify the best cell site available, the wireless device 101
may
measure the adjacent cells based upon the access technology to determine which
cell
is the best to utilize.
[00256] If, at initiation, a suitable cell is not available (i.e.,
determination 2808 =
"No"), the wireless device 101 may use the Any Cell Selection process/stage
and
continue to search for a suitable cell site by selecting the next PLMN/PRL
listing until
it finds a site that allows normal access following the access protocol in the
appropriate PLMN list, block 2810.
[00257] If the correct system is available through the selected cell site
(i.e.,
determination 2808 = "Yes"), the wireless device 101 may receive and read the
System Information Block (SIB)/Master Information Block (MIB) transmitted by
the
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
selected cell site, block 2812. The SIB/MIB may include information about the
network that the cell site is serving and available services through that
network.
[00258] In an embodiment, SIB/MIB may include a host of information such as
PLMN
ID(s), Cell ID, traffic allocation identifiers (TAI) (routing area), LTE
neighbor list,
LTE non system sites, GSM cCells, UMTS cells, and CDMA cells. This information
may be used by the wireless device 101 for different purposes. For example,
when the
wireless device 101 moves from eNodeB to eNodeB, it may use the SIB/MIB
information sent from the new eNodeB to determine that a change has occurred
in the
serving eNodeB. To detect the change in eNodeB, the wireless device 101 may
identify the change in SIB/MIB information which may include a change in
change in
the PLMN availability and TAI parameters. TAI defines specific routing areas
that
can further be used to refine a geographic region in which the wireless device
101 can
use available resources.
[00259] SIB/MIB information may be transmitted to the cell site by the
network. The
cell site may receive the network information through the HSS 926 of the
network. In
addition to the data transmitted through the SIB, the HSS 926 of the network
may also
provide the information as to which PGW(s) 908 the wireless device 101 may use
to
access resources on the network.
[00260] Upon reading the SIB/MIB, the wireless device 101 may determine
whether
reselection is required, at determination block 2814. If no reselection is
required (i.e.,
determination block 2814 = "Yes"), the wireless device 101 may camp on the
cell
channel, in block 2816. If system reselection is required (i.e., determination
block
2814 = "No"), the wireless device 101 may be instructed to reselect a new cell
or
system based on the cell selection/reselection process, block 2818.
[00261] While camping on the selected cell site, the wireless device 101 may
receive
additional information and instructions over the air from the selected
network, such as
updated list of public land mobile network or PLMN/PRL. The wireless device
101
may also continue to monitor the SIB/MIB for any changes or additional
information.
66
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00262] In an embodiment, the SIB/MEB may provide a Secondary Access Class
which may enable the wireless device 101 to determine which channels based on
the
DSA process it can use for access through the reselection process. The SIB/MIB
may
also include data to enable the camping wireless device 101 to reselect
another radio
access technology (IRAT) and attempt to acquire a control channel on the new
Radio
Access Terminal (RAT). The information in the SIB/MIB may, thus, be used to
instruct a wireless device 101 to reselect another RAT that is associated with
the same
or another network which may be on a another frequency band.
[00263] Cell reselection, which may trigger PLMN selection, may be controlled
via
specific parameters. For example, the DSA communication system may employ
barred PLMN-id to prevent a wireless device 101 using resources from one
network to
attempt to roam on to other networks. For example, the DSA communication
system
may prevent a secondary user wireless device 101 using resources of a primary
host
network to roam back to or establish connection with the secondary home
network.
Similarly, the DSA communication system using a PLMN id prioritization scheme
that is over the air (OTA), client activated or dual USIM driven may also
prevent a
wireless device 101 using resources of a network to reestablish connection
with other
networks unless the DSA communication system rules permit.
[00264] In an embodiment, a wireless device 101 that is camping at a cell site
may be
instructed to perform cell reselection when the capacity of the current cell
reaches a
predetermined level. In such a scenario, the DSC 910 of the current camping
network,
using the OMC 912, may change the SIB/MIB of the current network to include
instructions the camping wireless device 101 to perform a cell reselect and
search for
another TAI area or system. The instructions to perform a cell reselect may
also be
forwarded by the WAP/SMS message to the wireless device 101.
[00265] FIG. 29 illustrates an embodiment network diagram for cell reselection
using
changes in the TAI. When using a network, different wireless devices 101 may
be
assigned different TAI's depending on their particular uses and device types.
For
example, a network may assign one TAI to DSA communication system users. The
67
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
network may also assign another TAI to devices which do not use the DSA
communication system. The advantage of using multiple and layered TAI's may
enable the TAI assigning network to selectively tailor usage traffic. The
multiple and
layered TAI's may further enable the TAI assigning networks to prevent the
wireless
devices 101 that may have correct PLMN-id but are not supposed to use the
selected
area from selecting the cells but may be denied service or may be forced into
cell
reselection.
[00266] In an embodiment, a special client may be installed on DSA
communication
system compatible wireless devices 101 to enable the wireless devices 101 to
determine which system and RAT is supposed to use on secondary bases. The
PLMN/PRL list of the client application may be updated by receiving an SMS or
WAP that may be transmitted to the handset via a text message or through a
data (IP)
session. The updated client application may instruct the wireless device 101
to go to
the proper channel for accessing allocated resources of a primary network.
[00267] Using a client application may facilitate the implementation of the
DSA
communication system in legacy networks and systems which may or may not
possess
the ability (e.g., due to software load) to have a secondary access channel
defined in
the SIB.
[00268] In idle mode, the wireless device 101 may be instructed to perform
intra and
inter frequency measurements in the cell reselection process. Using
information in the
SB3/MIB or from the client application, the wireless device 101 may perform
infra-
frequency search, inter-frequency, or inter-radio access tech (iRAT). This
process
may be controlled by UTRAN. The Intra and Inter frequency measurements or
inter-
radio access technologies may be on a region or cell/sector bases, depending
on
configuration of the wireless device 101.
[00269] AUTHENTICATION OF SECONDARY USER WIRELESS DEVICES:
[00270] Once the wireless device 101 selects the appropriate cell site and
before it
enters an idle mode, the wireless device may need to be authenticated by the
system
68
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
on which it is camping. The selected network requires validation and
authentication
of the wireless device 101 to ensure that the device possesses the required
permissions
to access the network.
[00271] The DSA communication system may authenticate a wireless device 101
using different methods. Authentication of the wireless device with the DSA
may
depend on the business arrangements between different providers and the DSA
system. For example, authentication may be based on general or prioritization
levels.
The authentication process may be followed using the DPC 902 HSS 904 as the
anchor and this may be accessed by the AAA/AuC of the 3G/2.5G networks of the
PCRF 904 in LTE or similar platform. The Host Network may authenticate the
secondary users by using standard MAP/IS-41 signaling.
[00272] Upon authentication, each entrant may be assigned: (a) defined usage
level
allowed on host network; duration permitted on system; purchase type (e.g.,
wholesale
or a range of EMI's); HSS would allow redirecting of inbound calls;
applications
would continue where they relied on a server which is accessible from the
backend.
[00273] MONITORING AND TRACKING OF ALLOCATED RESOURCES:
[00274] The DSA communication system may ensure that the primary network
provider always has adequate resources to manage traffic on the primary
provider
network (e.g., Network 2). Therefore, depending on the volume of traffic, the
DSA
communication system may dynamically on a real-time and/or statistical basis
alter
the spectrum/capacity available to secondary users.
[00275] For example, at peak hours, call traffic may increase in the primary
network.
When call traffic increases in the primary network, the DSA communication
system
may reduce the amount of spectrum available for allocation to secondary users
to
ensure that the primary users have adequate resources.
[00276] The DSA communication system may manage allocation of and access to
resources based on different factors including priority level of the users,
time the
spectrum is used and the geographic location of the user. In an embodiment,
when the
69
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
secondary access to the primary network is related to certain events such as
disasters,
emergencies, first responders or public safety, the DSA communication system
may
manage the secondary use of the primary system by using different
prioritization. For
example, when secondary users are first responders who are using the primary
network resources, the DSA communication system may maintain or increase the
resources allocated to the secondary users by the primary network provider to
allow
the emergency calls to go through successfully, even to the detriment of the
primary
network users.
[00277] In an embodiment, the use of spectrum resources of one network by a
secondary user may be managed and controlled by different components of the
DSA
communication system such as the DPC 902. For example, the DPC 902 of a
primary
network may monitor the use of the allocated spectrum resources to ensure
appropriate steps are taken when allocated resources are exhausted or no
longer
available for secondary use.
[00278] The DSC 910 of the primary network may be configured to monitor or
receive
data regarding the traffic levels associated with the primary network on which
the
wireless devices 101is operational as a secondary user. The DSC 910 may
further be
configured to off-load the secondary user by downgrading resources, forcing to
terminate (i.e., off-load) a connection of a secondary user or redirecting a
secondary
user to another carrier or channel set if the primary network capacity
threshold is
reached.
[00279] The DSC 910 of a primary network may also inform the DPC 902 when off-
loading of secondary users may be required. For example, an unexpected surge
of
primary callers may cause the DSC 910 to request that secondary users be off-
loaded
to make available resources for the primary users. When off-loading of
secondary
users is initiated, technical access parameters may be sent to (OTA) to the
wireless
device 101. Alternatively, the system may dynamically assign resources via LTE
using the X2 link instructing the defined wireless device 101 to handover to
the new
LTE network.
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00280] Off-loading of secondary users may include redirecting the secondary
users'
connections back to the secondary user's own network, to another provider
network or
channel or disconnecting the secondary users' connections with the primary
provider
network. For example, when a primary host network may be required to terminate
a
secondary user due to increased demand on the primary network, the DPC may be
configured to determine whether other networks are available to redirect the
secondary user's connection instead of terminating. The DPC 902 may inquire
for
resources from DSC 910 of other networks. If the resources are available for
use in
other networks, the DPC 902, using a rule set, may determine the most cost
effective
connection with another host network which satisfies the resource request
requirements. Once the DPC 902 has identified another host network to which
the
secondary user wireless device 101 may be redirected, the DPC 902 may instruct
the
wireless device 101 to transition over to the new host network for the
communication
session. The process of off-loading of secondary users may include handover or
back-
off processes which are explained in more detail below.
[00281] In a further exemplary embodiment, the DPC 902 of the host network may
also be configured to instruct the primary host network to release the
secondary user
wireless device 101 back to the secondary home network after the use of the
primary
network resources is completed. The DPC 902 may further be configured to force
terminate the secondary user's connection with the primary network if the DPC
902
determines that additional capacity is required for use by primary users.
[00282] If sufficient capacity is available, the DPC 902 may force the
secondary user
to continue to use the resources of the primary host network until the traffic
volume
on the primary host network requires additional action based on rule sets.
[00283] In the various embodiments, the DSA may further manage the use of the
allocated and accessed spectrum. For example, the DSA communication system may
manage the use of the host network's RF spectrum by employing a back-off
mechanism. When the host spectrum network is accessed by high priority users,
the
71
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
spectrum may rid of lower priority users to make available spectrum to higher
priority
users.
[00284] FIG. 30 illustrates a network architecture diagram 3000 for monitoring
and
tracking of spectrum usage according to an embodiment. Tracking and monitoring
of
the use of spectrum resources may be performed using different methods. In a
DSA
communication system using the virtual-best effort method of resource
allocation, the
DSC 910 may monitor usage of spectrum resources based on pre-arranged billing
information and communication with the primary network billing platform.
[00285] The DSC 910 may monitor the usage level for the group and also track
usage
level with the POW 908. The usage may be compared and monitored against what
was anticipated or rather successfully bid. Once a predefined amount of the
allocated
resources are used by a secondary user, the DSC 910 of the primary network may
be
configured to generate a notice that resources are reaching a critically low
level and
send it to the secondary network provider through the DPC 902. The secondary
user
may receive the notice through its own DSC 910. Upon receipt of the notice,
the
secondary user provider network may rebid for additional resources or simply
let the
remaining resources to run out.
190286] In the event that a secondary user is actively using a primary network
when
allocated resources are fully consumed, the primary network may instruct the
secondary user wireless device 101 to reconnect to the home network (secondary
user
network provider), terminate the wireless device's connection, or charge an
overage or
supplemental fee to the secondary network based on a previously negotiated
contract.
Upon termination of connection, the secondary user wireless device may not be
able
to access the primary network resources unless additional resources are
allocated for
the secondary user.
[Q0287] In a DSA communication system using the virtual-secondary user method,
the
DSC 910 may monitor the usage of the allocated resources based on pre-arranged
billing information and communication with the host primary network billing
platform. The process of monitoring the usage of the allocated resources based
on a
72
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
virtual-secondary user method may involve mentoring the usage level for the
group
and also tracking usage of the level with the PGW 908.
[00288] Similar to the DSA communication system using the virtual-best effort
method, the DSA communication system using the virtual-secondary user method
may monitor the usage by comparing the usage against the amount of resources
that
was allocated to the secondary user network provider. Once a predefined amount
of
the allocated resources are used by the secondary user, the DSC 910 of the
primary
network may be configured to generate a notice that resources are reaching a
critically
low level and send it to the secondary network provider through the DPC 902.
The
secondary user may receive the notice through its own DSC 910. Upon receipt of
the
notice, the secondary user provider network may rebid for additional resources
or
simply let the remaining resources to run out.
[00289] In the DSA communication system that is using the virtual-secondary
user
method, after allocated resources are exhausted, the secondary user may be
terminated
by different methods, for example by 1) No prioritization back-off; or 2)
prioritization
back-off as discussed below.
[00290] In the no prioritization back-off method, when the allocated spectrum
resources at the pre-determined level are consumed, no further usage may be
permitted. Once allocated spectrum resources are exhausted, the primary
network
DSC 910 may instruct the secondary user wireless device to connect to the
secondary
user home network, terminate the secondary user wireless device's connection
with
the primary network, or charge an overage free based on previously negotiated
contracts. Upon termination from the primary network, the secondary user
wireless
device may not be able to access the primary network resources unless
additional
resources are obtained by the secondary home network provider.
[00291] In the prioritization back-off method, when the allocated spectrum
resources
are at critically low levels and before the resources are completely consumed,
the
primary network may commence a back-off process during which the primary
network may place the secondary user wireless device 101 on another suitable
73
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
network. If not, other suitable networks are available to accept the secondary
user
wireless device 101, the primary network may handover the secondary user
wireless
device 101 back to the secondary user home network. The primary network may
credit the secondary network for any allocated resources that were not used by
the
secondary users.
[00292] When using the resource allocation method, the primary host network
may
monitor allocated resources differently depending on whether resources are
allocated
based on a license area or regional area method.
[00293] If the allocation of resources is preformed based upon a license area
method,
the primary network may monitor the usage of the resources by the secondary
users.
When the allocated resources are near exhaustion, the DSC 910/DPC 902 may
inform
the secondary user network that the temporary lease of the resources is about
to expire
and provide an opportunity to the secondary network to bid for and purchase
additional resources.
[00294] If the secondary network fails to or refuses to obtain additional
resources, the
primary network may terminate or back-off the secondary user from the primary
network using different methods, such as, 1) no prioritization back-off; or 2)
prioritization method.
[00295] In the no prioritization back-off method, when the lease of the
resources is
expired, the spectrum resources may no longer be available to the secondary
users.
The primary network may instruct the secondary user wireless devices 101 to
either
handover to another radio access system in their network or terminate their
use.
[00296] In the prioritization back-off method, the primary network's DSC
910/DPC
902 may coordinate resources with the DSC 910 of the secondary network with
respect to the affected sites. The secondary network may attempt to handover
the
secondary user wireless network to another network, base station, radio access
channel or system for the affected area. The primary network may credit the
secondary network for unused allocated resources.
74
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00297] If the allocation of resources is preformed based upon a regional area
method,
the primary network may monitor the usage of the resources by the secondary
users.
When the allocated resources are to expire and near a predetermined completion
level,
the DSC 910/ DPC 902 of the primary host network may inform the secondary home
network that the impending termination of resources. The primary network may
provide the secondary network an opportunity to rebid for additional
resources.
[00298] If the secondary network fails or refuses to obtain additional
resources, the
primary network may terminate or back-off the secondary user from the primary
network using different methods, such as, 1) no prioritization back-off; or 2)
prioritization method.
[00299] In the no prioritization back-off method, when the leased term for the
allocated resources is expired, the secondary user may no longer have access
to the
spectrum resources of the primary network. The primary network may either hand
over the secondary user to another radio access system in their network, which
can be
a host network or another network or terminate the secondary user's access to
the
primary network resources.
[00300] In the prioritization back-off method, the DSC 910 and DPC 902 of the
primary network and the DSC 910 of the secondary network may coordinate
resources
with the affected sites and commence the back-off process before the lease of
allocated resources is expired. The secondary network may attempt to handover
the
secondary user wireless network to another network, base station, radio access
channel or system for the affected area. The primary network may credit the
secondary network for unused allocated resources.
[00301] HANDOVER OF SECONDARY USERS DURING OFF-LOADING:
[00302] In an embodiment, the DSA communication system may employ handover
methods to prevent interruptions during or maintain communication sessions
between
wireless devices 101, the DSA communication system and/or network providers.
For
example, a communication session may include a wireless device 101
establishing
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
connection with a network. Handover may occur when the wireless device's 101
connection migrates from the home network to a host network and back to the
home
network during the period of one communication session. The SIB/IVIIB
generated by
the network may include the list of cells and networks that may be used to
handover a
communication session.
[00303] Outside of the DSA communication system, mobile assisted handovers may
involve the wireless device 101 informing the servicing network that a better
server is
available and changing the connection from the current server to the better
server.
Such mobile assisted handovers may be performed when wireless devices are
roaming
on host networks. However, the DSA communication system may not allow such
mobile assisted handovers, because the best server for roaming purposes may
not be
the most optimum cell for capacity relief. Communication sessions with the DSA
communication system may involve circuit switch or packet switched services.
[003041 FIG. 31 illustrates a network component diagram of an embodiment
network
capable of performing handover of communication sessions. To implement a
handover of a communication session, certain connectivity between components
of
the host and home networks (e.g., network A and network B) may exist. For
example,
the PGW 908 of the host and the home networks may be connected. The PGW 908 of
the host and home networks may communicate through the Internet or a private
data
network. The PGW 908 of the host may also be connected to the SGW 922 of the
home network. The ANDSF 918 of the host and home networks may also be
connected to allow handover to the legacy system and to invoke the back-off
process
when the wireless device is required to migrate from the host to the home
network.
[00305] Access Network Discovery and Selection Function (ANDSF) is used to
manage intersystem mobility policy and access network discovery information
stored
in a wireless device supporting provisioning of such information from an
ANDSF.
The ANDSF may initiate the provision of information from the ANDSF to the
wireless device as specified in 3GPP TS 24.302 [3AA].
76
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00306] FIG. 32 illustrates a network diagram of an embodiment method for
media
independent handover. The ANDSF through the DSA process may initiate the
handover by sending a SMS/WAP message to the wireless device 101 instructing
it to
go a gap or non-gap handover. The handover process may be initiated under
different
circumstances and for different reasons. For example, a network may commence a
handover process based on contract specifications between the host and the
home
network, based on the level of resources at the host network and whether the
resource
has reached a predetermined threshold, based on resources leased by the home
network being exhausted or based on whether a back-off process is initiated.
[00307] When the host resources are no longer available for use or a back-off
process
is initiated, the DSA communication system may employ additional components or
schemes to handover a communication session. In such a scenario, the eNodeB of
the
host network may perform a back-off process based on the QCI and ARP
designations. The eNodeB 916 back-off may involve handing over the current
communication session from the host eNodeB 916b to another eNodeB through the
use of the X2 link between the exchanging networks. This process may also be
achieved by using the DSMPTA process with the ANDSF.
[00308] To initiate and implement a handover process, the host network may
generate
and send certain commands to the wireless device 101. For example, three
different
types of handover include: 1) Interfreq; 2) intrafreq; and 3) TRAT.
[00309] In the interfreq handover, the network currently serving a wireless
device
101(i.e., the current network) may initiate handover of the wireless device
101 from
the current network to another network. In the intrafreq handover, the current
network
may initiate a handover of the wireless device 101 from one cell in the one
network to
another cell in the same network for capability offload. In the TRAT handover,
the
current network may initiate wireless device 101 handover to another RAT.
[00310] The interfreq handover may be initiated when the current network sends
instruction to the secondary user wireless device 101 to begin using the
resources of
77
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
another network. For example, a wireless device 101 on a home network may be
instructed to use a host network for large upload/downloads of files.
[00311] The interfreq handover may be used to offload a secondary user from a
host
network based on the policy decision in place. The interfreq handover may
further be
used when a wireless device 101 no longer needs to use the services of the
host
network as a secondary user and thus may be sent back to the its home network.
The
interfreq handovers may further be used when a wireless device 101 leave the
DSA
communication system cluster or cell area and requires to continue its
communication
session. In such a scenario, the wireless device 101 may be either transferred
to
another network/cluster or sent back to the home network. The interfreq
handovers
may further be used to relieve network capacity constraints by allowing some
primary
users to use the services of another network as secondary users.
[00312] The intrafreq handovers may be used in current network to relieve cell
congestion by shedding traffic from one cell to another. To avoid a ping-pong
effect
which may prevent resolving capacity issues, the intrafreq handover commands
may
bar wireless devices 101 from using the neighboring cell/sector, as appears on
the
PLMN/PRL list, for defined periods of time.
[00313] [RAT handovers may be used to redirect wireless devices 101 to another
RAT. During a handover from one IRAT to another, both ratio access technology
and
frequency of operation may be changed. This type of handover may be used when
the
DSA communication system is available and the wireless device 101 is initially
active
on a particular channel. The current network may instruct the wireless device
101 to
change to another RAT through the IRAT handover process. In one embodiment,
the
handover command may be initiated from a current network, or alternatively the
handover command may be initiated from a different network or entity. Thus, if
the
wireless device 101 communication session is dropped during the handover
process,
the wireless device 101 may be able to reestablish the communication session
with the
target RAT and not revert back to the previous network.
78
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00314] In one non-limiting embodiment, the session may be dropped during
1NTERFREQ and/or INTRAFREQ handovers. In this embodiment, the device may
reestablish connections by reverting back to a previous network.
[00315] FIG. 33 illustrates a network component diagram of an embodiment
system
required for initiating a network handover as part of the DSA process. The
handover
process may be initiated by the DSC 910 based on its rule sets which are
established
prior to the bidding or during the bidding process. The use of the ANDSF 918
may
enable both intrafreq, interfreq and IRAT handovers to take place allow for
maximum
flexibility.
[00316] BACK-OFF OF SECONDARY USERS FROM THE HOST NETWORK:
[00317] The DPC 902 may continuously monitor the host network resources to
ensure
that sufficient levels of resources are available for the use of the primary
users of the
host network. When the capacity of available resources at the host network
reaches a
predefined threshold, the host network may instruct the wireless device 101 to
begin a
back-off process of the secondary users. The back-off process may be initiated
to
free-up resources at the hosting network.
[00318] When resources need to be made available to primary users or
subscribers of a
network, the DSA may initiate a back-off of the secondary users to free-up
additional
resources. The back-off process may involve different or combined methods
depending on the DSA configuration. However, commonality of the back-off
policy
is done using the wireless device 101 type and any special flags associated
with the
device, policy decision for redirecting active and idle traffic, policy
decision as to
whom and the order to shed traffic, and re-provisioning either OTA or via
activating a
client application.
[00319] In an embodiment, the DSA communication system may be configured to
employ tiered priority access (TPA) rules (as explained in detail above with
respect to
FIGs. 1-8) when initiating back-off processes. For example, the back-off
process may
be initiated when a resource level reaches a predetermined threshold level
which may
79
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
be user defined. The threshold detection process may include traffic
monitoring of the
Radio Access Network (RAN) and Core Network resources and determining whether
a predetermined threshold level is reached which may trigger QoS or require
shedding
of secondary users to free-up resources.
[003201 Threshold levels for RAN and Core Network resources may be determined
based on the traffic usage that secondary users may generate. For example,
when
more than 85% of the RAN resources are used, back-off process may be
implemented
to either reduce the throughput of the secondary users or shed secondary users
from
the host network or both. By initiating the back-off process, the host network
ensures
that amount of available RAN and Core Network resources always remain above
15%.
[003211 In an embodiment, the back-off process of the DSA which would allow
each
host network to maintain certain amount of resources free at all times may be
proactive and independent of actual incidents. In the event of an incident,
such as a
natural disaster, the DSA communication system may have the capacity to make
available free resources to first responders and employ the TPA process if
additional
resources are necessary.
[00322] In an embodiment, the DSA communication system may monitor the traffic
during the back-off process and begin to release RAN resources for secondary
use at
user defined intervals.
[00323] In an embodiment, each host network may employ certain back-off
policies
and resource criteria in deciding whether to initiate a back-off process.
These policy
and resource criteria may include: spectrum availability (separate or co-
existence);
capacity/bandwidth availability (RF and Core); overhead criteria (percent
total
available capacity vs. used capacity); back-off criteria (reselection,
handover ¨ intra
system and inter-system) termination); treatment (how specific
services/applications
are treated/routed); barred treatments (which services/applications are barred
for use);
rating (how services are rated, i.e., possible special discount for off-peak
usage);
geographic boundary (define zone or cell for inclusion); time (define time and
day(s)
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
for inclusion); duration (define incremental allocation based on time and
geographic
boundary); user equipment types.
[00324] Back-off process may be implemented differently for different resource
allocation methods. In an embodiment, the back-off process for the virtual-
best effort
(pure roaming) allocation method may be governed by the PCRF 905 policy rules
set
forth in the (EPC). The eNodeB may also be configured to initiate traffic
reducing
actions based on capacity loads by using the X2 link. In such a scenario, the
eNodeB
may enable the host network to shed secondary users by handing off traffic to
the
adjacent cell sites. In one embodiment, the eNodeB may send instructions to
one or
more entities including the UE. In another embodiment, the eNodeB may initiate
the
process.
[00325] Additionally the back-off process for DSA may also involve one or more
items which will be governed or instituted through the DSC following the
agreed upon
policy based rule sets and are meant to ensure session continuity or re-
allocation of the
UE to another access method in an attempt to ensure the user experience is
maintained
during the back-off process.
[00326] In an embodiment, the (DSMPTA) back-off process for virtual-best
effort may
be above and beyond the typical rule sets which are part of the Access and
EPC.
When traffic reaches a pre-defined threshold, the DSA communication system may
initiate one or a combination of processes to implement a DSMPTA back-off
process.
The PCRF 905 may dynamically adjust the QCl/ARQ values for the secondary user
wireless device 101. This may involve restricting the bandwidth or placing
usage onto
a best effort or lower priority scheme. The cells which are experiencing
capacity
constraint may be placed on a barred cell list so that no additional secondary
user may
access the cells. The updates to the barred cell list may be communicated to
the
wireless devices 101 through re-provisioning the broadcast message that is
sent to the
wireless devices 101. The broadcast message may be updated with information
regarding the barred cells and the neighboring available cells.
81
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
1003271 To ensure that the wireless devices 101 receive and read the broadcast
messages regarding the barred cells and the available neighboring cells, the
DSA
communication system may send WAP/SMS messages to the configured wireless
devices 101 to force them to reselect. The wireless devices 101 will have to
read the
broadcast messages when they enter the reselection process.
[00328] In an embodiment, the DSA may initiate close service groups to
restrict the
use of particular cells sites to the roaming wireless devices 101. The
combination of
CSG and TAI's which may be involved with the capacity issue may restrict the
secondary user wireless device 101 from accessing the network. For example,
the
CSG and TAI may drop callers, may reduce quality, may expand the network, or
may
provide other items to deal with the capacity issue.
[00329] In an embodiment, during a back-off session, the ANDSF 918 may
facilitate a
handover of the secondary users to another network or back to the secondary
user
home network. ADDSF 918 may initiate a network handover if connectivity is
available with another network. The wireless devices 101 may be handed over to
another network or another access network (RAT/IRAT).
[00330] In an embodiment, the back-off process in DSA using a virtual-
secondary
user method of resources allocation may be governed by the PCRF 905 policy
rules
set forth in the EPC and DPC 902. The PCRF 905 policy rules of a primary host
network which apply to the secondary users may take priority over those
enforced by
the DPC 902. However, the PCRF 905 policy rules of the primary host network
may
be dynamically changed or amended based on the conditions set forth by the
primary
host network operations requirements. Additionally, the back-off process in a
DSA
communication system may involve additional items. The implementation of these
additional items may be controlled and governed through the DSC 910 of the
primary
host network based on the agreed upon policies and rules sets. The DSC 910
policies
and rules are designed to ensure communication session continuity and good
user
experience during the back-off process.
82
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00331] In the event that the existing policies and rule sets in the Access
and EPC fail
to apply to a back-off process, the DSA back-off process for secondary users
may be
implemented. For example, when primary host network traffic reaches a
predetermined threshold level, the host DSC 910 may instruct the host eNodeB
to
handover the secondary user to adjacent cell sites within the host network
using the
X2 link and based upon the secondary user wireless device 101 QCl/ARQ rule
sets.
Alternatively, the DSC 910 may instruct the host eNodeB to handover the
secondary
user to the home network using the X2 link when the host and home networks are
connected for full mobility.
[00332] Based upon instructions received from the host DSC 910, the host PCRF
905
may dynamically adjust the QCl/ARQ values for the secondary user wireless
devices
101. For example, the host PCRF 905 may restrict the bandwidth, change
resources
allocation method to virtual-best effort, or change priority schemes to low
priority.
[00333] The DSC 910 may instruct the host network to update or generate a list
of
barred cells and include the cells which are currently experiencing traffic
capacity that
is above the predetermined traffic capacity threshold. The DSC 910 may further
instruct the host network to broadcast a message to re-provision the secondary
user
wireless devices 101 with the updated barred cell list. The broadcast message
may
further include information regarding the next ring or multiple rings of cells
adjacent
to the constrained cell or group of cells. The broadcast message may include
changed
and valid PLMN-ids, altered TAI for the cell or cells, and altered neighbor
lists for the
use of the secondary user wireless device 101 to perform a handover process or
network reselection. To ensure that secondary user wireless devices 101 check
for the
re-provisioning broadcast messages, the host network may send a WAP/SMS
message
to configured wireless devices 101 to force them to perform network
reselection.
[00334] The host DSC 910 may further instruct the host network to initiate
Close
Service Groups (CGS) to restrict the use of particular cell sites to the
roaming
secondary user wireless devices 101. The combination of CGS and TAI involved
with
the network capacity may restrict access of the roaming secondary user
wireless
83
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
devices 101 to the host network. The access restriction effectuated by the
combination of CGS and TAI may render the host network only accessible to
designated primary users.
[00335] In the event that connectivity exists between the primary host and
another
network (e.g., the secondary home network), the host DSC 910 may instruct the
host
AND SF 918 to initiate a network handover of the secondary user wireless
device 101
to another connected network or access network (RAT/IRAT).
[00336] To reduce capacity overload when eNodeB is x-furcated for resources
allocation and access, the host OMC 912 (or other policy based controls
configured to
manage capacity) may instruct the eNodeB to shed the resources accessible to
the
secondary user wireless devices 101. Accordingly, the resources designated for
secondary use and associated with an eNodeB for the affected area may be
reduced.
The reduction in available resources of an eNodeB may be force handovers to or
reselection of adjacent cell with resources.
[00337] The reallocation of eNodeB resources may be balanced by host network
initiated handovers to force the secondary user wireless devices 101 to
handover to
another network on which they can roam and be provided with adequate
resources.
For example, the handovers may be interfreq RAT or IRAT handovers.
[00338] The host PGW 908 may also be used as part of the back-off process. The
SG
of the secondary user wireless devices 101 may be connected to the appropriate
host
PGW 908 based on the policies and rules of the host HSS 904 and PCRF 905. The
host DSC 910 may control the bandwidth of the connection between the host PGW
908 and wireless device's 101 SG. During the back-off process, the host DSC
910
may initiate the host network to reduce the bandwidth between the PGW 908 and
secondary user wireless device's 101 SG which are being moved out of the host
network. The process by which the DSC 910 may reduce bandwidth between the
PGW 908 and SG may be governed by predetermined policy and rules. The host DSC
910 may continue to monitor the host network cells which may be overburdened
by
84
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
high traffic and assess additional bandwidth reduction to the host PGW 908-
device SG
connection to reduce traffic.
[00339] Not all the processes initiated by the DSC 910 as part of the DSMPT
back-off
process may be necessary and the implementation of these processes and the
order in
which they may occur may depend on the agreements between the host and home
networks.
[00340] In an embodiment, the back-off process may be implemented in the DSA
communication system using a spectrum allocation method of resources
allocation.
The spectrum allocation method may include the license area and regional area
methods for resources allocation.
[00341] In an embodiment, the back-off process for a DSA using a license area
method may involve the reallocation of the spectrum resources from the
secondary
home network (i.e., lessee) to primary host network (i.e., lessor). The host
network
using the license area method may initiate the back-off process to handover
all the
existing secondary user wireless devices 101 from the lessor's spectrum to
another
network or back to the home network. The time frame for the reallocation will
be
predetermined based on rule sets defined by the lessor and lessee agreements.
Depending on the time frame defined in the rule sets, not all the secondary
users may
be migrated out the host network in time and as a result, some secondary users
may be
dropped.
[00342] Based upon pre-negotiated agreements between the lessor and the
lessee, the
host network may determine whether the back-off process may be applied to a
portion
of or the entire license area. Based on the geographic region involved for
capacity
relief, spectrum reallocation may not be required for every cell of the entire
license
area. Accordingly, back-off processes may be implemented in sub-license areas
of the
licensed area.
[00343] In implementing the back-off process for an entire license area, the
host DSC
910 may inform the DPC 902 that the host network has reached a predefined
threshold
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
of traffic capacity. The DPC 902 may communicate that message to the home DSC
910. The home DSC 910 may reduce the host resources available to the home
eNodeB in a stepwise marmer and handover the secondary user traffic to a non-
leased
spectrum. The steps of reducing the available resources to the eNodeB may be
performed on a predefined time intervals basis. If traffic is not migrated in
a timely
manner, the home DPC 902 may initiate network handovers to migrate the
secondary
users from the host network to another appropriate channel. Once the resources
are
freed, the home eNodeB may remove the channel from its available channel
lists.
[00344] In implementing the back-off process for sub-license areas (in opposed
to the
entire license area), the process above may be implemented except that defined
cells
or TAI's may be used instead of the entire license area.
[00345] Once the capacity restrictions are resolved by the host network, the
spectrum
may be reallocated to the home network. To reallocate resources, the host DSC
910
may inform the DPC 902 that spectrum resources are again available for use by
the
home network. The home DPC 902 may inform the home DSC 910 that resources are
again available. The resources may be reallocated to the home network based
upon
predetermined policies and rule sets.
[00346] For back-off processes which are not governed by rules and policies in
the
Access and EPC, the host may initiate a DSMEPTA back-off process. It may be
possible that based on the rules sets.
[00347] In an embodiment, the back-off process for a DSA communication system
using a Regional area method may depend on the policies and rule sets agreed
upon
by the lessor and the lessee.
[00348] The back-off process in a DSA using the Regional area method of
resources
allocation may include handing over all the existing secondary wireless
devices 101
using the host spectrum in the regional area or sub-regional area back to the
home or
another network. The host DSC 910 and DPC 902/DSC 910 rule sets may define
86
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
whether the secondary users should be moved from the entire or a sub-set of
regional
area.
[00349] The timeframe for the reallocation of resources during the back-off
process
may be predetermined based on policies and rule sets agreed upon by the lessor
and
lessee. Not all the traffic may be successfully migrated to the home or
another
network during the back-off process if the timelines set forth in the
agreement is not
met. In such a scenario, some connections may be dropped or lost as soon as
the
predetermined timeframe is expired.
[00350] Upon initiation of the back-off process, the lessee network resources
associated with the home eNodeB may be reduced in a stepwise manner. The home
OMC 912 may initiate reduction of the resources by the eNodeB. Other policy
based
components of the home network, such as the DPC 902 may also initiate the
reduction
of resources by the eNodeB. The home network may facilitate the handover of
the
secondary users from the host network spectrum to the home network spectrum.
If the
home network does not have the capacity to handle the traffic volume or
handover is
not being performed in a timely fashion, it may either handover the
communication
session to another network or channel or force the secondary user wireless
devices
101 to perform a reselection process. Once the eNodeB has handed over all the
secondary users from the host spectrum, it may remove the spectrum channel
from the
available list of channels accessible to secondary users.
[00351] Once the capacity restrictions are resolved by the host network, the
spectrum
may be reallocated to the home network. To reallocation resources, the host
DSC 910
may inform the DPC 902 that spectrum resources are again available for use by
the
home network. The home DPC 902 may inform the home DSC 910 that resources are
again available. The resources may be reallocated to the home network based
upon
predetermined policies and rule sets.
[00352] FIG. 34 shows a smart phone 101a, a laptop 101b, and a cell phone 101c
communicating with an element 3402 that is connected to a prime 3404 and a
secondary 2306 and which communicates with a base station 102a and 102b via a
87
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
primary RAT and a secondary RAT. The base station 102a connects with a primary
network and the base station 102b connects with a secondary network 102b. In
an
embodiment, as illustrated in FIG. 34, the DSA communication system may allow
wireless devices 101a-101c to access several Radio Access Technologies (i.e.,
primary and secondary RATs) simultaneously. For example, the DSA may enable a
wireless device 101 using a primary RAT of a primary network to access a
secondary
RAT on a secondary network only for certain types of services. For example,
when
the wireless device 101 use of the primary network causes high volume or
bursty
traffic, the DSA communication system may enable the primary network to
offload
and send the high volume and bursty traffic to the secondary network. For
example,
prime and secondary element 2306 and 3404 may provide data to route traffic
over to
the primary and secondary wireless networks and base stations using a header.
Switching may occur using a DSA to switch between the networks. In another
embodiment, the switching may occur using the element 3402, prime component or
secondary component 3404 or 3406. In yet another embodiment, the switching may
be
initiated by the prime or secondary DSA networks, or by another entity that
views the
capacity of the network.
[00353] FIG. 35 illustrates a message flow diagram 3500 of the arbitrate
process in a
DSA communication system according to an embodiment. In this embodiment, one
bidder (i.e., Network 1) is used for simplicity, however, it is contemplated
that
multiple bidders may use this process. Network 1 3501 may send a request for
resources message 3502 to the DPC 902. The DPC 902 may receive the request
message and send queries 3504, 3506 to participating DSCs 910a, 910b of
Network 2
and Network 3 based on pre-defined criteria which may include types and
capabilities
of the user wireless device 101 in addition to the geographic criteria of the
requesting
wireless device 101. Geographic criteria may include geographic location,
geographic
polygon or license area of the user wireless device 101. The geographic
criteria
request may include parameters that are greater than those that the host
network may
permit. The DPC 902 may receive resource inquiry responses 3508, 35010 from
each
DSC 910a, 910b that was contacted.
88
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00354] The DPC 902 may send a resource availability message 3512 to inform
Network 1 that the requested resources are available through DSC 910a. Network
1
3501 may receive the resource availability message 3510 and in response send a
resources request message 3514 to the DPC 902 to reserve the available
resources at
DSC 910a. The DPC 902 may the send a resource reservation request 3516 to the
DSC 910a. Upon receiving the resource reservation request 3516, the DSC 910a
may
reserve the required spectrum and send a resources reserved message 3518 back
to the
DPC 902. The DPC 902 may receive a resource bid message 3520 from Network 1,
accept the bid (if the bid complies to the policies and rules of the DPC 902)
and send a
bid accepted message 3522 to Network 1 3501. Upon accepting the bid from the
bidder, the DPC 902 may also send an assign resources request 3524 to the DSC
910a
to allocate the reserved resources to Network 1 3501. The DSC 910a may receive
the
assign resources request 3524, allocate the resources to be used by Network 1
3501
and send a resources allocated message 3526 to the DPC 902. The DPC 902 may
inform Network 1 3501 that the requested resources are now allocated to be
used by
the wireless device 101 subscriber Network 1 3501 by sending a resources
allocated
message 3528 to Network 1 3501. The resources may be available for use by
Network 1 3501. Once the resources are used, the DSC 910a may send a resources
consumed/released message 3530 to the DPC 902. The DPC 902 may receive the
resources consumed/released message 3530 and send a resources
consumed/released
message 3532 to Network 1 3501. Network 1 3501 may settle the charges for the
spectrum that it used.
[00355] FIGs. 36 ¨ 40 illustrate flow diagrams of an embodiment method for
allocating and accessing resources using the DSA communication system. As
illustrated in FIG. 36, the Network 1 DSC 910a may monitor call traffic as
compared
to the total spectrum resources available to Network 1, block 3602. The DSC
910a
may record and report the resource status of Network 1 to the DPC 902. The DPC
902
may receive the resource status report from Network 1, block 3702, and store
it, block
3704. The DSC 910a of Network 1 may determine based on the resources status
report whether additional resources may be required to provide service to the
existing
89
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
users of Network 1, determination 3606. If additional resources are not
required (i.e.,
determination 3606 = "No"), the DSC 910a may continue to monitor resources
available vs. bandwidth traffic by going back to block 3602. If additional
resources
are required (i.e., determination 3606 = "Yes"), the DSC 910a may send a
request for
additional resources to the DPC 902, block 3608.
[00356] The Network 2 DSC 910b may also monitor resources available vs.
bandwidth
traffic in Network 2, block 3602, and report the resource status to the DPC
902, block
3804. The DPC 902 may receive the resource status report from DSC 910b, block
3702 and store the received data, block 3704. The DSC 910b may determine
whether
excess amount of resources are available in Network 2, determination 3804. If
excess
amounts of resources are not available in Network 2 (i.e., determination 3804
=
"No"), the DSC 910b may continue to monitor resources available vs. bandwidth
traffic by going back to block 3602. If excess amounts of resources are
available (i.e.,
determination 3804 = "Yes"), the DSC 910b may allocate the excess resources or
a
sub-part of the excess resources for secondary use, block 3806, and report to
the DPC
902 that resources are allocated for use by secondary users, block 3808. The
DPC 902
may receive the resource allocation report from DSC 910b, block 3702, and
store the
received data, block 3704.
[00357] The DPC 902 may receive resource status reports from many different
networks. However, in this embodiment, for ease of illustration, only
interactions of
DPC 902 with two networks are shown. The status reports received from the
networks may further include additional information such as network rules and
policies with respect to access and use to allocated resources. For example,
the status
reports from Network 2 may include system requirements for Network 2 which
must
be met before a wireless device 101 can successfully access the allocated
resources on
Network 2 as a secondary user.
[00358] The DPC 902 receives the request for additional resources from DSC
910a of
Network 1, block 3706, and based on data received from other networks selects
the
best available network from which Network 1 may purchase additional resources,
in
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
block 3708. In this example, the DPC 902 may select Network 2 as the most
suitable
network to provide resources to Network 1. The DPC 902 may send a resource
inquiry to the Network 2, block 3710, to determine the availability and
quantity of
allocated excess resources of Network 2.
[00359] The DSC 910b of Network 2 may receive the resource inquiry, block
3810,
and determine resource availability, block 3812. The DSC 910b may send a
resource
inquiry response to the DPC 902. The resource inquiry response may include
information about the quantity and quality of resources available for use by
secondary
users. The DPC 902 may receive the resources inquiry response, block 3712.
[00360] As illustrated in FIG. 37, the DPC 902 may determine whether resources
are
available based on the data received from the DSC 910b of Network 2, block
3714. If
data is not available (i.e., determination block 3714 = "No"), the DPC 902 may
send a
no resource available message to Network 1, block 3722. Resources may not be
available for use by a network for different reasons. For example, resources
may be
purchased to other bidders before they were reserved by the network. The DSC
910a
of Network 1 may receive the no resource available message, block 3614, and
search
for other available spectrum resources or terminate connection sessions with
users to
free-up resources on Network 1, block 3618.
[00361] If data is available (i.e., determination 3714 = "Yes"), the DPC 902
may send
a resource available message to the DSC 910a to inform Network 1 about the
quality
and quantity of resources available for secondary use at Network 2, block
3716. The
DSC 910a may receive the resources available message and send a request
resource
message to reserve the allocated resources of Network 2 for use by subscribers
of
Network 1, block 3612. The request resource message may include data such as
the
quantity of resources that Network 1 may require in this transaction.
[00362] The DPC 902 may receive the resources request message, block 3718, and
send a reserve resources request message to Network 2, block 3720. The DSC
910b at
Network 2 may receive the reserve resource request, block 3816, and reserve
the
requested quantity of the allocated resources for use by Network 1
subscribers, block
91
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
3818. The DSC 910b of Network 2 may confirm that the requested quantity of
allocated resources is reserved for use by Network 1 by sending a resource
reserved
message, block 3820. The DPC 902 may receive the resource reserved message
from
Network 2 and prepare for the bidding process as described in FIG. 38.
[00363J As illustrated in FIG. 38, the DSC 910a of Network 1 may send a
resource bid
to negotiate access to the reserved resources of Network 2, block 3620. The
DPC 902
may receive the resource bid and process it, block 3726. The DPC 902 may
determine
whether the bid received from Network 1 may be accepted, at determination
block
3728. The DPC 902 may evaluate a bid from a network provider based upon
policies
and rule sets of the DSA communication system in addition to requirements set
forth
by the resource offering network, such as prices and allocation or access
methods or
by other methods. If the bid is accepted (i.e., determination 3728 = "Yes"),
the DPC
902 may send an accept bid message to Network 1, block 3730. The DSC 910a may
receive the accept bid message and await resource access instructions, in
block 3622.
Once the bid is accepted, the DPC 902 may also send an assign resources
message to
the DSC 910b of Network 2, block 3732. The DSC 910b may receive the assign
resources message, block 3822, and assign reserved resources for use by
Network 1,
block 3824. The DSC 910b may send a resources access message to enable Network
1 to access the assigned resources of Network 2, block 3826, and configure to
establish communication session with the wireless device 101 of Network 1,
block
3828.
[003641 The DPC 902 may relay the resources access message to Network 1, block
3734. The DSC 910a may receive the resources access message, block 3624. The
resource access message may include data, such as, access parameters that may
be
used by secondary user wireless devices 101 to access resources on Network 2.
The
DSC 910a may send access parameters for Network 2 to wireless devices 101
which
have communication sessions with Network 1 and Network 1 has designated to
migrate to Network 2, block 3626. The designated wireless devices 101 may
receive
the access parameters for Network 2, block 3902, and establish a communication
session with wireless device 101 of Network 1, steps 3904 and 3830. Network 2
may
92
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
commence the settlement process as described in more detail below with
reference to
FIG. 40.
[00365] If the bid is rejected (i.e., determination block 3728 = "No"), the
DPC 902
may send a rejected bid message to Network 1, block 3736 (shown in FIG. 39).
As
illustrated in FIG. 39, the DSC 910a may receive the rejected bid message,
block
3736, and determine whether to rebid, determination 3640. If no rebid (i.e.,
determination 3640 = "No"), the DSC 910a may send a cancel resource request
message, block 3644. The DPC 902 may receive the cancel resource request
message,
block 3742, and send a release of resources message to Network 2, block 3744.
The
DSC 910b of Network 2 may receive the release of resources message, block
3832,
release the reserved resources for use by other networks, block 3834, and
report the
allocated resource status to DPC 902 by going back to block 3808 as shown in
FIG.
36 and follow the steps as described above with respect to FIG. 36.
[00366] If rebid (i.e., determination 3640 = "Yes"), the DSC 910a may send a
new bid
for the same resources, block 3642. The DPC 902 may receive the new bid, block
3738, and determine whether to accept the new bid, determination 3740. If the
new
bid is rejected again (i.e., determination 3740 = "No"), the DPC 902 may send
a
rejected bid message by going back to block 3736. If the bid is accepted
(i.e.,
determination 3740 = "Yes"), the DPC 902 may send an accept bid message by
going
back to block 3730 as shown in FIG. 38 and follow the same steps as described
above
with respect to FIG. 38.
[00367] FIG. 40 illustrates the settlement process after Network 2 provides
access to
the secondary user wireless devices 101 of Network 1. DSC 910b of Network 2
may
send invoices and payment instructions relating to the use of allocated
resources by
Network 1 to the DPC 902, block 3836. The DPC 902 may relay the invoice and
payment instructions from Network 2 to Network 1, block 3746. DSC 910a may
receive the invoices and payment instructions, block 3644, and settle the
charges with
Network 2, steps 3648 and 3840.
93
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00368] Optionally, the DSC 910b of Network 2 may send usage parameters and
payment instructions to the DPC 902, block 3838. The DPC 902 may receive the
usage parameters and payment instructions, block 3748, create an invoice,
block 3750,
and send the invoice to Network 2, block 3752. The DSC 910a may receive the
invoice and payment instructions, block 3646, and settle the charges with
Network 2,
steps 3648 and 3840.
[00369] FIG. 41 illustrates a message flow diagram 4100 of message
communication
between components of a network provider which is allocating available
resources to
other resources requesting networks. The DSC 910a at Network 1 3501 may send a
request for resources from, message 3502. The DPC 902 may receive the request
for
resources message and send a resource inquiry to Network 2, message 3504. At
Network 2, the resource inquiry may be received at the DSC 910b. The DSC 910b
may send a resource inquiry to the OMC 912 in Network 2 to determine whether
resources are available for Network 1, message 4106. The OMC 912 may receive
the
resource inquiry message from the DSC 910b and send a resource inquiry message
to
the Access Resources 4102, message 4108. The OMC 912 may also send a resource
inquiry message to the Core Resources 4204, message 4110. The Access Resource
4102 and the Core Resources 4204 each receive the resource inquiry messages
from
OMC 912 and send a resource response to the OMC 912, messages 4112, 4114
respectively. The resources response from the Access Resources 4102 may
include
message parameters. The resources response from the Access Resources 4102 may
include other message parameters.
[00370] The OMC 912 may receive the resource responses from the Access
Resource
4102 and Core Resource 4104 and send a resource response message to the DSC
910b
indicating status of resources availability in Network 2, message 4116. The
DSC
910b may receive the resource response message from the OMC 912 and send a
resource inquiry response to the DPC 902, message 3508. The DPC 902 may
receive
the a resource inquiry response from the DSC 910b, determine whether the type
of
resources requested are available at Network 2 and send a resources available
message
to the DSC 910a of Network 1, message 3512. The DSC 910a may receive the
94
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
resources available message and send a resources request message to direct the
DPC
902 to request the available resources from Network 2, message 3514. The DPC
902
may receive the resources request message and send a resources reservation
request
message to the DSC 910b to request that the available resources in Network 2
be
reserved for use by Network 1, message 3516. The DSC 910b may receive the
resources reservation request message and, via the OMC 912, send a resource
reservation request to the Access Resource 4102, message 4118, and a resource
reservation request to the Core Resources 4104, message 4120.
[00371] The Access Resource 4102 may receive the resource reservation request
from
the OMC 912, reserve the available resources and send a resources reserved
message
back to the DSC 910b via the OMC 912, message 4122. Similarly, the Core
Resources 4104 may receive the resource reservation request from the OMC 912,
reserve the available resources and send a resources reserved message back to
the
DSC 910b via the OMC 912, message 4124. The DSC 910b may receive the
resources reserved message from the Access Resources 4102 and Core Resources
4104 and send resources reserved message to the DPC 902 to inform the DPC 902
and
Network 1 that the requested resources are reserved for use by Network 1,
message
3518. The DPC 902 may receive a resource bid message from the DSC 910a of
Network 1, message 3520. The DPC 902 may send a bid accepted message to the
DSC 910a if the bid received by DPC 902 satisfies the price and contract
requirements
of Network 2, message 3522. If the bid is accepted, the DPC 902 may send an
assign
resources request to the DSC 910b, message 3524. The DSC 910b may receive the
assign resources request to the Access Resources 4102, message 4126, and an
assign
resources request to the Core Resources 4104, message 4128. The DSC 910b may
further send a policy for resources assigned message to the Policy Controller
905,
which can be the same or different relative to the PCFF, message 4130. The DSC
910b may further send a metering for resources assigned to the AAA/AuC 4106,
message 4132.
[00372] FIGs. 42 ¨44 illustrate process flow diagrams of an embodiment method
for
backing off secondary users by handing them over back to their home network or
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
terminating their communication session with the host network. A wireless
device
101 from Network 1 may establish a secondary user communication session with
Network 2 via the DSC 910b, steps 3904, 3830. The DSC 910b of Network 2 may
continuously monitor traffic on the network versus the available resources,
block
3602, and send a report to the DPC 902, block 3604. DPC 902 may receive the
resource status report from the DSC 910b. The DSC 910b may further determine
whether the network volume is greater than the capacity of the network based
on its
available resources, determination 4404. If the network volume is not greater
than the
capacity of the network (i.e., determination 4404 = "No"), the DSC 910b may
continue to monitor the network traffic versus the available resources by
returning to
block 3602. If the network volume is greater than the capacity of the network
(i.e.,
determination 4404 = "Yes"), the DSC 910b may identify a user on the network,
block 4406, and determine whether the user is a secondary user, determination
4408.
[00373] If the user is a secondary user (i.e., determination 4408 = "Yes"),
the DSC
910b may send disconnect session at t message, t being the amount of time left
before
the secondary user communication session will be terminated by Network 2,
block
4410. The disconnect session at t message may be received by the DPC 902 as
illustrated in FIG. 43, block 4306. Optionally, instead of sending a
disconnect session
at t message, the DSC 910b may terminate the communication session of the
secondary user to immediately provide additional resources for primary or
other
important users, block 4412. The decision regarding whether to immediately
terminate or transmit a warning before termination of a secondary user may be
based
on contractual terms between the primary and secondary network providers and
the
DSA communication system policies and rule sets.
[00374] If the user is not a secondary user (i.e., determination 4408 = "No"),
the DSC
910b may determine whether any other secondary users are present on the
network,
step 4414. If there are other secondary users still connected to Network 1
(i.e.,
determination 4414 = "Yes"), the DSC 910b may send try to disconnect their
sessions
first before the primary users by returning to steps 4410,4412. If there are
no other
secondary users on the primary network (i.e., determination 4414 = "No"), the
DSC
96
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
910b may keep or drop the primary user communication session based on tiered
priority access rules, block 4416. For example, premium primary users (i.e.,
those
with more expensive subscription plans) may be dropped last. Alternatively, in
an
embodiment (not shown), instead of terminating the primary user communication
sessions, the DSC 910b may try to handover the users to another network as
secondary users, thus, preserving the communication session connection while
reducing volume of Network 1. The DSC 910b may return to monitoring the
network
volume versus capacity to determine whether additional callers need to be off-
loaded
by returning to block 4404.
[00375] As illustrated in FIG. 43, the DPC 902 may relay the disconnect
session at t
message to the DSC 910a, block 4306. The DSC 910a may receive the disconnect
session at t message, block 4206, set a timer to count down from t, block
4208, and
monitor its available resources, block 4210, to determine whether there is
resources
available on Network 1 to receive the secondary user communication session
from
Network 2, determination 4212. If resources are not available on Network 1
(i.e.,
determination 4212 = "No"), the DSC 910a may send a request for resources to
the
DPC 902, block 3808, to reserve and purchase available resources from network
providers by returning to block 3706 of FIG. 36 and following the resources
allocation
steps as described above with respect to FIGs. 36 ¨ 40.
[00376] If resources are available on Network 1 (i.e., determination 4212 =
"Yes"), the
DSC 910a may allocate resources to the secondary user that is going to be
terminated
from Network 2, block 4212, and send instructions for the wireless device 101
to
disconnect from Network 2 and connect to Network 1 to the DPC 902 as shown in
FIG. 44, block 4308. The DSC 910a may also configure/prepare the Network 1
system to connect to the secondary user wireless device 101, block 4218.
[00377] As illustrated in FIG. 44, the DPC 902 may relay the instructions for
the
wireless device 101 to disconnect from Network 2 and connect to Network 1 to
the
DSC 910b of Network 2, block 4308. The DSC 910b may receive the instructions,
block 4418, and send them to the secondary user wireless device 101 which
currently
97
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
has a communication session with Network 2, block 4420. The wireless device
101
may receive the instructions to disconnect from Network 2 and connect to
Network 1,
block 4220, and end communication session with Network 2, block 4222, and
establish communication session with Network 1, steps 4224, 4226.
[00378] PUBLIC SAFETY NETWORK:
[00379] In an embodiment, the primary network provider of the DSA
communication
system may be a public safety network. A public safety network may be the
holder or
owner of public safety spectrum. Public safety spectrum is generally reserved
for
used by public safety authorities. The assigned public safety bandwidth
typically
includes more spectrum than is used by public safety authorities on an average
bases.
An excess amount of spectrum is assigned for public safety use in anticipation
of its
use during public safety emergencies such as disasters.
[00380] In an embodiment, the DSA communication system may allow the public
safety networks to lease spectrum resources to other networks when the public
safety
spectrum is available and not in use. During public safety emergency
situations when
all of the network resources may be required for use by public safety
authorities, the
DSA communication system may allow the network to retrieve all of its
allocated
resources from other networks by off-loading traffic from the public safety
network to
free-up resources.
[00381] In addition, if the assigned spectrum of a public safety network
proves
inadequate to handle a large volume of use by public safety authorities during
an
emergency, the DSA communication system may enable the public safety network
to
lease or take resources from other networks which are participating in the DSA
communication system. For example, the DSA communication system may require
that all participating networks to continuously keep a certain percentage
(e.g., 10%) of
their resources unassigned. The public safety networks may use the unassigned
resources of the participating networks to augment their resources for public
safety
communications during emergencies. The DSA communication system may further
98
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
off-load primary and/or secondary users of a primary network to free-up
resources for
use by the public safety authorities.
[00382] In an embodiment, access to public safety spectrum may be based on
tiered
priority access methods described above with respect to FIGs. 1-8. For
example,
police dispatchers may always have access to the spectrum. However, access of
other
non-governmental users of the public safety resources may be limited to
certain times
periods or dates depending on the contracts between the users and the public
safety
network providers.
[00383] In an embodiment, off-loading of non-public safety users from the
public
safety or other networks may be performed using a tiered priority access
methods
described above with respect to FIGs. 1-8. For example, in a public safety
network,
when resources are required for public safety use, the DSA communication
system
may enable the public safety network to off-load users in order of preferences
such as
first, off-loading secondary non-public safety users, second, off-loading
primary non-
public safety users, third, off-loading, lower ranked public safety users,
etc. Similar
tiered priority access method may be used to off-load users of another network
the
resources of which may be used by the public safety network.
[00384] In an embodiment, during an emergency, the DSA communication system
may restrict access to any resources of a public safety network which is
allocated for
secondary use. For example, once the DSA communication system determines that
there is a public safety emergency, the DSA communication system may no longer
consider the allocated resources from the public safety network which is
involved in
the emergency as available resources for use by other networks.
[00385] In an embodiment, the DSA communication system policies and rule sets
may
require that participating networks allocate a percent of their resources for
public
safety use and disasters response purposes. During an emergency, the DSA
communication system may enable public safety networks to access additional
resources which each non-public safety network may allocate for public safety
use. In
this scenario, if the allocated resources are in use, tiered priority access
methods may
99
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
be used to off-load users from the allocated resources. Other resources of the
non-
public safety network may not be used for public safety unless properly
negotiated.
[00386] FIGs. 45 ¨49 illustrate flow diagrams of an embodiment method for
allocating and accessing resources of a public safety network using the DSA
communication system. As illustrated in FIG. 45, the DSC 910a may monitor
resources versus bandwidth traffic in Network 1, block 3602. The DSC 910a may
record and report the resource status of Network lto the DPC 902. The DPC 902
may
receive the resource status report from Network 1, block 3702, and store it,
block
3704. The DSC 910a of Network 1 may determine, based on the resources status
report, whether additional resources may be required to provide service to the
existing
users of Network 1, determination 3606. If additional resources are not
required (i.e.,
determination 3606 = "No"), the DSC 910a may continue to monitor available
resources as versus bandwidth traffic by going back to block 3602. If
additional
resources are required (i.e., determination 3606 = "Yes"), the DSC 910a may
send a
request for additional resources to the DPC 902, block 3608.
[00387] The public safety network DSC 910b may reserve a predetermined amount
of
unused spectrum resources as a back-up for use only by public safety
authorities, in
block 4502. This may ensure that if there is a need for resources during an
emergency, such as a natural disaster, resources are readily available to be
dedicated
for public safety use until additional resources are released by off-loading
secondary
users from the network. The Public safety network DSC 910b may also monitor
resources available vs. bandwidth traffic in Public safety network, block
3602, and
report the resource status to the DPC 902, block 3804. The DPC 902 may receive
the
resource status report from DSC 910b, block 3702 and store the received data,
block
3704. The DSC 910b may determine whether excess amount of resources are
available in Public safety network, determination 3804. If excess amounts of
resources are not available in Public safety network (i.e., determination 3804
= "No"),
the DSC 910b may continue to monitor resources available vs. bandwidth traffic
by
going back to block 3602. If excess amounts of resources are available (i.e.,
determination 3804 = "Yes"), the DSC 910b may allocate the excess resources or
a
100
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
sub-part of the excess resources for secondary use, block 3806, and report to
the DPC
902 that resources are allocated for use by secondary users, block 3808. The
DPC 902
may receive the resource allocation report from DSC 910b, block 3702, and
store the
received data, block 3704.
[00388] The status reports received from the networks may further include
information
such as network rules and policies with respect to access and use to allocated
resources. For example, the status reports from Public safety network may
include
system requirements for Public safety network which must be met before a
wireless
device 101 can successfully access the allocated resources on Public safety
network as
a secondary user.
[00389] The DPC 902 receives the request for additional resources from DSC
910a of
Network 1, block 3706, and based on data received from other networks selects
the
best available network from which Network 1 may purchase additional resources,
block 3708. In this example, the DPC 902 may select Public safety network as
the
most suitable network to provide resources to Network 1. The DPC 902 may send
a
resource inquiry to the Public safety network, in block 3710, to determine the
availability and quantity of allocated excess resources of Public safety
network.
[00390] The DSC 910b of Public safety network may receive the resource
inquiry,
block 3810, and determine resource availability, block 3812. The DSC 910b may
send a resource inquiry response to the DPC 902. The resource inquiry response
may
include information about the quantity and quality of resources available for
use by
secondary users. The DPC 902 may receive the resources inquiry response, block
3712.
[00391] As illustrated in FIG. 46, the DPC 902 may determine whether resources
are
available based on the data received from the DSC 910b of Public safety
network,
block 3714. If data is not available (i.e., determination 3714 = "No"), the
DPC 902
may send a no resource available message to Network 1, block 3722. Resources
may
not be available for use by a network for different reasons. For example,
resources
may be sold to other bidders before they were reserved by a requesting
network. The
101
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
DSC 910a of Network 1 may receive the no resource available message, block
3614,
and search for other available spectrum resources or terminate connection
sessions
with users to free-up resources on Network 1, block 3618.
[00392] If data is available (i.e., determination 3714 = "Yes"), the DPC 902
may send
a resource available message to the DSC 910a to inform Network 1 about the
quality
and quantity of resources available for secondary use at Public safety
network, block
3716. The DSC 910a may receive the resources available message and send a
request
resource message to reserve the allocated resources of Public safety network
for use
by subscribers of Network 1, block 3612. The request resource message may
include
data such as the quantity of resources that Network 1 may require in this
transaction.
The DPC 902 may receive the resources request message, block 3718, and send a
reserve resources request message to Public safety network, block 3720. The
DSC
910b at Public safety network may receive the reserve resource request, block
3816,
and reserve the requested quantity of the allocated resources for use by
Network 1
subscribers, block 3818. The DSC 910b of Public safety network may confirm
that
the requested quantity of allocated resources is reserved for use by Network 1
by
sending a resource reserved message, block 3820. The DPC 902 may receive the
resource reserved message from Public safety network and prepare for the
bidding
process as described in FIG. 47.
[00393] As illustrated in FIG. 47, the DSC 910a of Network 1 may send a
resource bid
to negotiate access to the reserved resources of Public safety network, block
3620.
The DPC 902 may receive the resource bid and process it, block 3726. The DPC
902
may determine whether the bid received from Network 1 may be accepted, in
determination block 3728. The DPC 902 may evaluate a bid from a network
provider
based upon policies and rule sets of the DSA communication system in addition
to
requirements set forth by the resource offering network, such as prices and
allocation
or access methods.
[00394] If the bid is accepted (i.e., determination 3728 = "Yes"), the DPC 902
may
send an accept bid message to Network 1, block 3730. The DSC 910a may receive
102
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
the accept bid message and await resource access instructions, block 3622.
Once the
bid is accepted, the DPC 902 may also send an assign resources message to the
DSC
910b of Public safety network, block 3732. The DSC 910b may receive the assign
resources message, block 3822, and assign reserved resources for use by
Network 1,
block 3824. The DSC 910b may send a resources access message to enable Network
1 to access the assigned resources of Public safety network, block 3826, and
configure
to establish communication session with the wireless device 101 of Network 1,
block
3828.
[00395] The DPC 902 may relay the resources access message to Network 1, block
3734. The DSC 910a may receive the resources access message, block 3624. The
resource access message may include data such as access parameters that may be
used
by secondary user wireless devices 101 to access resources on Public safety
network.
It should be appreciated that other data may be included in the resources
access
message. The DSC 910a may send access parameters for Public safety network to
wireless devices 101 which have communication sessions with Network 1 and
Network 1 has designated to migrate to Public safety network, block 3626. The
designated wireless devices 101 may receive the access parameters for Public
safety
network, block 3902, and establish a communication session with wireless
device 101
of Network 1, steps 3904 and 3830. Public safety network may commence the
settlement process as described in more detail below with reference to FIG.
49.
[00396] If the bid is rejected (i.e., determination 3728 = "No"), the DPC 902
may send
a rejected bid message to Network 1, block 3736 (shown in FIG. 48). As
illustrated in
FIG. 48, the DSC 910a may receive the rejected bid message, block 3736, and
determine whether to rebid, determination 3640. If no rebid (Le.,
determination 3640
= "No"), the DSC 910a may send a cancel resource request message, block 3644.
The
DPC 902 may receive the cancel resource request message, block 3742, and send
a
release of resources message to Public safety network, block 3744. The DSC
910b of
Public safety network may receive the release of resources message, block
3832,
release the reserved resources for use by other networks, block 3834, and
report the
103
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
allocated resource status to DPC 902 by going back to block 3808 as shown in
FIG.
45 and follow the steps as described above with respect to FIG. 45.
[00397] If rebid (i.e., determination 3640 = "Yes"), the DSC 910a may send a
new bid
for the same resources, block 3642. The DPC 902 may receive the new bid, block
3738, and determine whether to accept the new bid, determination 3740. If the
new
bid is rejected again (i.e., determination 3740 = "No"), the DPC 902 may send
a
rejected bid message by going back to block 3736. If the bid is accepted
(i.e.,
determination 3740 = "Yes"), the DPC 902 may send an accept bid message by
going
back to block 3730 as shown in FIG. 47 and follow the same steps as described
above
with respect to FIG. 47.
[00398] FIG. 49 illustrates the settlement process after Public safety network
provides
access to the secondary user wireless devices 101 of Network 1. DSC 910b of
Public
safety network may send invoices and payment instructions relating to the use
of
allocated resources by Network 1 to the DPC 902, block 3836. The DPC 902 may
relay the invoice and payment instructions from Public safety network to
Network 1,
block 3746. DSC 910a may receive the invoices and payment instructions, block
3644, and settle the charges with Public safety network, steps 3648 and 3840.
[00399] Optionally, the DSC 910b of Public safety network may send usage
parameters and payment instructions to the DPC 902, block 3838. The DPC 902
may
receive the usage parameters and payment instructions, block 3748, create an
invoice,
block 3750, and send the invoice to Public safety network, block 3752. The DSC
910a may receive the invoice and payment instructions, block 3646, and settle
the
charges with Public safety network, steps 3648 and 3840.
[00400] FIGs. 50 ¨ 53 illustrate process flow diagrams of an embodiment method
for
backing off secondary users by handing them over back to their home network or
terminating their communication session with the host network. A wireless
device
101 from Network 1 may establish a secondary user communication session with
Public safety network via the DSC 910b, steps 3904, 3830. The DSC 910b of
Public
safety network may continuously monitor traffic on the network versus the
available
104
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
resources, block 3602, and send a report to the DPC 902, block 3604. DPC 902
may
receive the resource status report from the DSC 910b. The DSC 910b may further
determine whether the network volume is greater than the capacity of the
network
based on its available resources, determination 4404. If the network volume is
not
greater than the capacity of the network (i.e., determination 4404 = "No"),
the DSC
910b may continue to monitor the network traffic versus the available
resources by
returning to block 3602. If the network volume is greater than the capacity of
the
network (i.e., determination 4404 = "Yes"), the DSC 910b may identify a user
on the
network, block 4406, and determine whether the user is a secondary user,
determination 4408.
[00401] If the network volume exceeds the allocated capacity threshold of the
network
(i.e., determination 4408 = "Yes"), an abnormal situation exists which may
indicate
that an emergency situation is unfolding. In this scenario, the DSC 910b may
follow
the processes illustrated in the process flow diagrams of FIG. 50 to free-up
resources
for public safety use and FIG. 54 to incrementally allocate network resources
based on
a Tiered Priority Access regime.
[00402] As shown in FIG. 50, to free-up resources for public safety use, the
Public
safety network may send disconnect session at t message, t being the amount of
time
left before the secondary user communication session will be terminated by
Public
safety network, block 4410. The disconnect session at t message may be
received by
the DPC 902 as illustrated in FIG. 43, block 4306. Optionally, instead of
sending a
disconnect session at t message, the DSC 910b may terminate the communication
session of the secondary user to immediately provide additional resources for
primary
or other important users, block 4412. The decision regarding whether to
immediately
terminate or transmit a warning before termination of a secondary user may be
based
on contractual terms between the primary and secondary network providers and
the
DSA communication system policies and rule sets.
[00403] If the user is not a secondary user (i.e., determination 4408 = "No"),
the DSC
910b may determine whether any other secondary users are present on the
network,
105
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
block 4414. If there are other secondary users still connected to Network 1
(i.e.,
determination 4414 = "Yes"), the DSC 910b may send try to disconnect their
sessions
first before the primary users by returning to steps 4410,4412. If there are
no other
secondary users on the primary network (i.e., determination 4414 = "No"), the
DSC
910b may keep or drop the primary user communication session based on tiered
priority access rules, block 4416. For example, premium primary users (i.e.,
those
with more expensive subscription plans) may be dropped last. Alternatively, in
an
embodiment (not shown), instead of terminating the primary user communication
sessions, the DSC 910b may try to handover the users to another network as
secondary users, thus, preserving the communication session connection while
reducing volume of Network 1. The DSC 910b may return to monitoring the
network
volume versus capacity to determine whether additional callers need to be off-
loaded
by returning to block 4404.
[00404] As illustrated in FIG. 51, the DPC 902 may relay the disconnect
session at t
message to the DSC 910a, block 4306. The DSC 910a may receive the disconnect
session at t message, block 4206, set a timer to count down from t, block
4208, and
monitor its available resources, block 4210, to determine whether there is
resources
available on Network 1 to receive the secondary user communication session
from
Public safety network, determination 4212. If resources are not available on
Network
1 (i.e., determination 4212 = "No"), the DSC 910a may send a request for
resources to
the DPC 902, block 3808, to reserve and purchase available resources from
network
providers by returning to block 3706 of FIG. 45 and following the resources
allocation
steps as described above with respect to FIGs. 45 ¨ 49.
[00405] If resources are available on Network 1 (i.e., determination 4212 =
"Yes"), the
DSC 910a may allocate resources to the secondary user that is going to be
terminated
from Public safety network, block 4212, and send instructions for the wireless
device
101 to disconnect from Public safety network and connect to Network 1 to the
DPC
902 as shown in FIG. 52, block 4308. The DSC 910a may also configure/prepare
the
Network 1 system to connect to the secondary user wireless device 101, block
4218.
106
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00406] As illustrated in FIG. 52, the DPC 902 may relay the instructions for
the
wireless device 101 to disconnect from Public safety network and connect to
Network
1 to the DSC 910b of Public safety network, block 4308. The DSC 910b may
receive
the instructions, block 4418, and send them to the secondary user wireless
device 101
which currently has a communication session with Public safety network, block
4420.
The wireless device 101 may receive the instructions to disconnect from Public
safety
network and connect to Network 1, block 4220, and end communication session
with
Public safety network, block 4222, and establish communication session with
Network 1, steps 4224, 4226.
[00407] In a further embodiment, the Public safety network may monitor all new
reserve resource requests and inquiries received from the DPC 902 to ensure
that
resources are provided only to those requests that are initiated by public
safety
authorities based on TPA at least until resource capacity is back to below the
threshold
levels. The Public safety network may receive a reserve resource request at
the DSC
910b, block 3810, and determine whether the resources inquiry is from a TPA-
authorized device, determination 312. If the resources requested are from a
TPA-
authorized device (i.e., determination 312 = "Yes"), the DSC 910b may
disconnect a
non-TPA communication session, such as a secondary user communication session,
block 314, and connect the TPA call, block 315. The DSC 910b may again monitor
the resources versus bandwidth available by returning to block 3602 of FIG.
50. If the
resource reserve message is received from a wireless device 101 other than an
authorized device (i.e., determination 312 = "No"), the Public safety network
may
block the call until excess resources are again available for use by secondary
users,
block 5302.
[00408] In an embodiment, for TPA-authorized personnel who may try to
establish a
communication session with the Public safety network using a wireless device
which
is subscribed to a network provider other than the public safety network
provider, the
Public safety authorities may be provided a prefix number which may alert the
receiving network provider about a request to transfer communication session
to a
public safety network and an access PIN. By using the prefix number and PIN, a
107
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
Public safety user may access the Public safety network using any device, even
if the
device is considered a secondary user wireless device 101 on the Public safety
network.
[004091 As illustrated in FIG. 54 to FIG. 56, when an authorized public safety
officer
requires to establish connection with a specific public safety network, he may
place a
call using any unauthorized wireless device 101 of Network 1 and dialing a
special
prefix number, such as *272, block 5402. The DSC 910a may receive and process
the
call, block 5404, and identify the prefix number as a request to transfer the
communication session to a public safety network, block 5406. The DSC 910a may
send a PIN request to the wireless device 101, block 5408. The wireless device
101
may receive the PIN request, block 5410, display the PIN request to the user
using
Graphical User Interface (GUI) and receive the user's PIN input, block 5412.
The
wireless device 101 may send the inputted PIN to the DSC 910a for processing,
block
5414. The DSC 910a may receive the PIN, block 5416, and send a request for a
network transfer along with the PIN to the DPC 902, block 5418. The DPC 902
may
receive the request for network transfer, block 5420, and determine whether
the PIN
matches a PIN database, determination 318. If the PIN does not match an entry
in the
PIN database (i.e., determination 318 = "No"), the DPC 902 may block the call,
block
5302. If the PIN matches an entry in the PIN database (i.e., determination 318
=
"No"), the DPC 902 may identify the target Public safety network based on the
received PIN, block 5422.
1004101 As illustrated in FIG. 55, the DPC 902 may determine whether the
wireless
device 101 of Network 1 includes compatible technology with the target Public
safety
network, block 5424. If the device and the public safety network are not
technologically compatible (i.e., determination 5424 = "No"), the DPC 902 may
send
a network incompatible message back to the device via the DSC 910a, block
5426.
The DSC 910a may relay the network incompatibility message, block 5428, and
terminate connection with the wireless device 101, block 5432. The wireless
device
101 may receive the network incompatible message, block 5430, display the
message
to the user, block 5434, and terminate connection with the Network 1, block
5436. If
108
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
the device and the public safety network technologies are compatible (i.e.,
determination 5424 = "Yes"), the DPC 902 may send a reserve resources request
with
PIN to the public safety network DSC 910b, block 5438. The DSC 910b may
receive
the reserve resources request with PIN, block 5440.
[00411] In an embodiment, as illustrated in FIG. 56, access to a public safety
networks
by authorized public safety authorities may be on a priority level. For
example, the
higher ranking officials of a public safety organization may have priority
access to the
network as compared lower ranking officials from the same organization. At any
given time, depending on the level of traffic and resources available, the
public safety
network may determine what level of authority may have access to the network.
Accordingly, the DSC 910b may be configured to allow those with required
levels of
priority and reject those with levels of priority lower than required. The DSC
910b
may continuously reevaluate the resource availability and change the access
level of
officials based on the availability of resources. The DSC910b may determine,
based
on the PIN, the level of priority of the user of the wireless device 101,
block 5442.
The DSC 910b may determine whether the level of priority of the device 101 is
allowed to access the public safety network at that time, determination 5444.
If the
device 101 priority level is authorized (i.e., determination 5444 = "Yes"),
the DSC
910b may disconnect a non-TPA session or a lower priority TPA session to free-
up
resources for the new request for resources, block 5446, and connect the new
TPA
session, block 5448, and return back to monitoring the resources of the
network versus
the bandwidth traffic, block 3602 of FIG. 45. If the request is from a TPA-
authorized
device which does not have the priority level to access the network at that
time (i.e.,
determination 5444 = "No"), the DSC 910b may block the call, block 5302.
[00412] As discussed above with reference to FIGs. 9 and 10, the Dynamic
Spectrum
Arbitrage (DSA) system may automatically determine an amount of radio
frequency
(RF) spectrum resources that are available within a first communication
network and
conduct an auction for the available RF spectrum resources among a plurality
of
network operators/providers to select a second communication network to which
the
available RF spectrum resources are to be sold, leased or otherwise allocated.
In this
109
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
manner, a primary provider may auction off, and a secondary provider may place
bids
on, the available RF spectrum resources of the first communication network.
This
allows the primary provider to make efficient use of excess RF spectrum
resources
that may otherwise go unused for significant periods of time by leasing the
excess RF
spectrum resources (on a temporary or permanent basis) to the highest bidder,
and for
the secondary providers to lease RF spectrum resources at competitive market
rates
that more accurately reflect the economic principles of supply and demand.
[00413] In an embodiment, the auctioning features and/or subsystems of the DSA
system may include a telecommunications commodity exchange (TCE) system or
module. The TCE system may be configured to utilize features provided by the
DSA
system, and the expandability and renewability characteristics of
telecommunication
assets, to allocate assets to networks and wireless providers when they are in
need of
additional resources, and enable investors to invest in the current or future
allocations
of such resources, likening telecommunication assets to other more traditional
commodities. For example, the TCE system may be configured to allow a first
network to allocate its unused resources to other networks, which may use the
resources to provide their customers with better or additional services and/or
resolve
network congestion during periods of high demand or usage. In addition, the
TCE
system may be configured to allow networks to' buy or sell futures contracts
with
such telecommunication assets. These futures contracts may provide an
assurance that
the lessor will allocate a specified quantity of telecommunication assets to
the lessee
at a future date for a currently presently agreed upon price, allowing lessees
to better
manage or hedge against future costs and/or to speculate regarding future
increases or
decreases in the costs or demand for the telecommunication assets.
[00414] The TCE system may allow telecommunication operators, investors and
new
market entrants an opportunity and the ability to buy, sell, exchange and
invest in
telecommunication commodities that include a wide array of expandable and
renewable resources; bandwidth, spectrum, radio resources and other network
assets.
The TCE system may be configured to make current and future allocations of
telecommunication assets such as bandwidth, spectrum, and radio resources
available
110
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
for auction or commodity exchange. The TCE system may be configured to allow
bidders to make monetary offers on resources based on the type, amount and/or
quality of services or resources.
[00415] FIG. 57 illustrates example network components and information flows
in an
embodiment communication system 5700 that includes two Long Term Evolution
(LTE or 4G LTE) systems interconnected by a DPC 5720 suitable for implementing
an embodiment TCE system. Each LTE communication system may include a
plurality of eNodeB 5704a, 5704b components coupled to a mobility management
entity (M:ME) 5706a, 5706b component and serving gateway (SOW) 5708a, 5708b.
The MME 5706a, 5706b and SGW 5708a, 5708b may be part of a core network
5730a, 5730b, such as a system architecture evolution (SAE) or evolved packet
core
(EPC) network. The eNodeB 5704a, 5704b may be outside of the core network
5730a, 5730b.
[00416] Each eNodeB 5704a, 5704b may be configured to communicate voice, data,
and control signals between mobile devices 5702 (e.g., cell phones) and to
other
network destinations. The eNodeB 5704a, 5704b may act as a bridge (e.g., layer
2
bridge) between the mobile device 5702 and the core network 5730a, 5730b by
serving as the termination point of all radio protocols towards the mobile
devices 5702
and relaying voice (e.g., VolP, etc.), data, and control signals to network
components
in the core network 5730a, 5730b. The eNodeB 5704a, 5704b may be configured to
perform various radio resource management operations, such as controlling the
usage
of radio interfaces, allocating resources based on requests, prioritizing and
scheduling
traffic according to various quality of service (QoS) requirements, monitoring
the
usage of network resources, etc. The eNodeB 5704a, 5704b may also be
configured
to collect radio signal level measurements, analyze the collected radio signal
level
measurements, and handover mobile devices 5702 (or connections to the mobile
devices) to another base station (e.g., a second eNodeB) based on the results
of the
analysis.
111
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00417] Generally, mobile devices 5702 send and receive voice, data and/or
control
signals to and from an eNodeB 5704a, 5704b via a wireless communication link
5722,
5724. The eNodeB 5704a, 5704b may send signaling/control information (e.g.,
information pertaining to call setup, security, authentication, etc.) to the
MME 5706a,
5706b via the S1-AP protocol on the S1-MME interface. The MME 5706a, 5706b
may request user/subscription information from a home subscriber server (HSS)
5710a, 5710b via the S6-a interface, communicate with other MME components via
the S10 interface, perform various administrative tasks (e.g., user
authentication,
enforcement of roaming restrictions, etc.), select a SGW 5708a, 5708b, and
send
authorization and administrative information to the eNodeB 5704a, 5704b and/or
SGW 5708a, 5708b (e.g., via the S1-MME and Sll interfaces).
[00418] Upon receiving the authorization information from the MME 5706a, 5706b
(e.g., an authentication complete indication, an identifier of a selected SGW,
etc.), the
eNodeB 5704a, 5704b may send data received from the mobile device 5702 to a
selected SGW 5708a, 5708b via GTP-U protocol on the Si-U interface. The SGW
5708a, 5708b may store information about the received data (e.g., parameters
of the IP
bearer service, network internal routing information, etc.) and forward user
data
packets to packet data network gateway (POW) and/or a policy control
enforcement
function (PCEF) 5714a, 5714b via the Sll interface.
[00419] In alternate embodiments, the PGW/PCEF 5714a, 5714b component(s) may
include a PCEF component coupled to a PGW component, a PCEF component
included in a PGW component, or a PCEF component configured to perform
operations typically associated with a PGW component. Since these structures
are
well known, certain details have been omitted in order to focus the
descriptions on the
most relevant features. Detailed information about policy and charging
enforcement
function operations may be found in "3rd Generation Partnership Project
Technical
Specification Group Services and System Aspects, Policy and Charging Control
Architecture," TS 23.203 (updated June 12, 2011), the entire contents of which
are
incorporated herein by reference.
112
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00420] The PCEF/PGW 5714a, 5714b may send signaling information (e.g.,
control
plane information) to a policy control rules function (PCRF) 5712a, 5712b
component, such as over a Gx interface. The PCRF 5712a, 5712b component may be
responsible for identifying the appropriate policy rules for a given
communication
session. The PCRF 5712a, 5712b component may communicate with external PCRF
components (not illustrated) via the S9 interface, access subscriber
databases, create
policy rules, and/or send policy rules to the PCEF/PGW 5714a, 5714b
component(s)
for enforcement.
[00421] The PCEF/PGW 5714a, 5714b may receive policy rules from the PCRF
5712a, 5712b component and enforce the received policy rules to control the
bandwidth, the quality of service (QoS), and/or other characteristics of the
data that is
to be communicated between the service network and the mobile devices 5702.
The
PCEF/PGW 5714a, 5714b may also coordinate, allocate, add, remove, and/or
adjust
various resources (e.g., network resources, subscriber resources, etc.) based
on the
received policy rules.
[00422] The eNodeB 5704a, 5704b may be configured to monitor network activity
(e.g., call volume, etc.) and partition, allocate, and/or adjust network
resources based
on the current network conditions. The eNodeB 5704a, 5704b may also be
configured
to dynamically "shape" the network activity of a mobile device 5702 based on
the
network conditions. Shaping the network activity of a mobile device may
include
reducing bandwidth, reducing QoS, restricting the number of services, shedding
a
connection, transferring a connected device to another tower (e.g., the second
eNodeB, etc.), performing handoffs, and/or other similar traffic management
activities
or operations.
[00423] The core networks 5730a, 5730b may be part of (or may include) a
dynamic
spectrum arbitrage communication system, such as any of the various DSA
systems
discussed above. For example, FIG. 57 illustrates that each core network
5730a,
5730b may include a DSC 5716a, 5716b component suitable for performing DSA
operations. The inclusion of the DSC 5716a, 5716b component in the core
network
113
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
may enable one or more eNodeBs 5704a, 5704b to send information concerning
network activity and/or the various steps taken to shape network activity to
the DSC
5716a, 5716b, which may use this information to make more informed spectrum
arbitrage determinations (e.g., whether spectrum should be leased, how much
spectrum should be shared, etc.).
[00424] In the example illustrated in FIG. 57, the DSC 5716a, 5716b is
connected
directly to the PCRF 5712a, 5712b. In various embodiments, the DSC 5722 may be
connected directly or indirectly to the PCEF/PGW 5714a, 5714b and/or various
other
components in the core network. In various embodiments, the DSC 5716a, 5716b
may be connected directly or indirectly with one or more eNodeBs 5704, such as
via a
direct communication link 5732 shown in FIG. 57.
[00425] In an embodiment, the DSC 5716a, 5716b may be connected to a DPC 5720
outside of the core network 5730a, 5730b. The DSC 5716a, 5716b may be
configured
with software to communicate data regarding the availability of spectrum
resources to
the DPC 5720 using capacity policy criteria. The data that is communicated to
the
DPC 5720 may include data relating to current excess capacity and expected
future
capacity of the network or sub-network, such as data received from one or more
eNodeB's 5704a, 5704b.
[00426] In various embodiments, spectrum and other resources may be allocated
to a
second network 5730b (i.e., lessee network) from a first network 5730a (i.e.,
lessor
network) as part of the dynamic spectrum arbitrage operations. A mobile device
5702
may be wirelessly connected to an eNodeB 5704b corresponding to the second
network 5730b via a connection 5724. The mobile device 5702 may be handed off
to
another eNodeB 5704a associated with the second network 5730a in order to use
the
allocated spectrum or radio resources. As part of the handoff procedure, a new
connection 5722 to the other eNodeB 5704a may be established and the wireless
connection 5724 to the original eNodeB 5704b may be terminated.
[00427] Various embodiments may include additional connections to accommodate
the data flow between the mobile device 5702 and the first network, such as a
114
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
connection 5728 from the second eNodeB 5704a to an SGW 5708b in the first
network or a connection 5726 between the second network's SOW 5708a to a PGW
5714b in the first network as shown in FIG. 57.
1004281 In various embodiments, all or portions of a telecommunications
commodity
exchange (TCE) system may be included in the dynamic policy controller (DPC)
5720
and/or dynamic spectrum controllers (DSC) 5716a and 5716b.
[00429] An important feature of the TCE system is the interaction between the
DPC
and DSCs. Each bidder and wireless network may have access to one or more DSC
components, which may be configured to reserve network resources and/or to
provision, allocate, or re-allocate resources to another network. The DPC may
be
configured to manage the interactions between multiple DSC's and networks,
which
may be state-wide networks or networks that cover an even larger geographical
area.
The DPC may also be configured to control which entities are allowed to place
bids
during an auction, coordinate start and end times for the bids, and perform
other
operations to manage the DSCs or the allocation, de-allocation and
reallocation of
resources between a first and or second network.
[00430] FIG. 58 illustrates example information flows and functional
components in
an embodiment DSA telecommunications commodity exchange (TCE) system 5800
configured to conduct an auction and allocate telecommunication resources
purchased
via the auction. In the example illustrated in FIG. 58, the DSA-TCE system
5800
includes three commercial bidder telecommunication networks (herein "bidder
networks") 5804, 5806, 5808, each of which may be associated with at least one
dynamic spectrum controller (DSC) 5810, 5812, 5814. Each DSC 5810, 5812, 5814
may include communication links to one or more dynamic policy controllers
(DPC's)
5816, 5818, which may be accomplished via a cloud/network 5820. Each DSC 5810,
5812, 5814 may also include communication links to a local control 5830, 5832,
5834
server/component.
[004311 The DPC's 5816, 5818 that may include communication links to a
telecommunication exchange network 5802 component/server suitable for
conducting
115
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
an auction or performing commodity transactions, and to a banking system 5822
suitable for processing monetary transactions. The telecommunication exchange
network 5802 component/server may include communication links to bidder 5824,
5826, 5828 servers/components.
[00432] The bidder networks 5804, 5806, 5808 may include network components or
servers that are owned, leased, or operated by a telecommunication network
operator,
a virtual network operator, or speculator (e.g., future telecommunication
resource
speculators, bandwidth speculators, etc.), or other similar entities or
parties. In the
various embodiments, the bidder networks 5804, 5806, 5808 may include any or
all of
the components of the lessor network 5730a and/or the lessee network 5730b
discuss
used above with reference to FIG. 57. In various embodiments, each bidder
5824,
5826, 5828 server/component may be included in, coupled to, or otherwise
associated
with at least one bidder network 5804, 5806, 5808.
[00433] The bidder 5824, 5826, 5828 servers/components may be configured to
communicate with a telecommunication exchange network 5802 component/server to
place bids, participate in auctions, purchase telecommunication commodity
futures,
and perform other similar operations to procure telecommunication resources
for use
by a bidder network 5804, 5806, 5808.
[00434] The telecommunication exchange network 5802 component/server may be
configured to perform various operations for managing and conducting an
auction for
telecommunication resources, including determining when a bidder or network is
registered to participate in a telecommunications commodity exchange,
verifying that
a telecommunication resource may be used by a bidder/network, authorizing a
bidder
to bid on a telecommunication resource during the auction, determining start
and stop
times for the auction, conducting the auction, receiving bids from bidders on
behalf of
a bidder network, determining an auction winner, determining which bidder
network
is to be allocated the telecommunication resources, etc.
[00435] The DPCs 5816, 5818 may be configured to coordinate the operations of
the
DSCs 5810, 5812, 5814 and communicate information regarding resource
allocations
116
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
and commodity transactions with the telecommunication exchange network 5802
component/server, the banking system 5822, and the DSCs 5810, 5812, 5814.
[00436] The DSCs 5810, 5812, and 5814 may be configured to allocate the
telecommunication resources procured by the bidder servers/components 5824,
5826,
5828 to a bidder network 5804, 5806, 5808. In an embodiment, the DSCs 5810,
5812,
5814 may allocate the resources via a local control 5830, 5832, 5834
server/component.
[00437] In an embodiment, a DPC 5816, 5818 component may be configured to
register a bidder network 5804, 5806, 5808 and/or verify that a bidder network
5804,
5806, 5808 is qualified to take part in an auction/exchange (i.e., to bid on
telecommunication resources, etc.). The DPC 5816, 5818 component may send the
telecommunication exchange network 5802 component a validation response
message
or an authorization message when the DPC 5816, 5818 component determines that
a
bidder or network is authorized to participate in an auction/exchange. The
authorization or validation response message may include information
indicating that
a bidder or network is a valid candidate, registered, verified, and/or
otherwise allowed
to participate in the auction/exchange.
[00438] In an embodiment, the telecommunication exchange network 5802
component
may be configured to verify that bidders are registered and authorized to
participate in
an auction/exchange. The telecommunication exchange network 5802 may allow
authorized bidder networks 5804, 5806, 5808 to participate in the
auction/exchange
and prevent unauthorized bidder networks 5804, 5806, 5808 from participating
in the
auction/exchange. In an embodiment, the telecommunication exchange network
5802
may be configured to determine that a bidder network 5804, 5806, 5808 is
authorized
to participate in the auction/exchange based on information included in a
validation
response message or authorization message received from a DPC 5816, 5818
component.
[00439] In an embodiment, a DPC 5816, 5818 may be configured to register or
verify
that a bidder/ network may participate in the auction/exchange when the bidder
or
117
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
network identifies itself as being one of a current network operator, virtual
network
operator or a speculator.
[00440] In an embodiment, a DPC 5816, 5818 may be configured to evaluate other
credentials or qualifications of a bidder or network before
registering/verifying the
bidder/network as being qualified to participate in the auction/exchange. For
example, the DPC 5816, 5818 may determine whether or not the telecommunication
resource being auctioned is compatible to or is supported by a bidder network
5804,
5806, 5808 before generating an authorization message indicating that the
bidder
network 5804, 5806, 5808 is qualified to participate in the auction/exchange.
As
another example, the DPC 5816, 5818 may verify that a bidder network 5804,
5806,
5808 is not in default or associated with an overdue bill, has sufficient
funds available
and/or is up to date with its payments, debts, etc. In an embodiment, this may
be
accomplished by the DPC 5816, 5818 accessing a telecommunication exchange
margin bank account associated with the bidder or the bidder network in the
banking
system 5822.
[00441] FIG. 59 illustrates an embodiment DSA-TCE validation method 5900 for
authorizing a bidder network to participate in a telecommunications commodity
exchange. The operations of the DSA-TCE validation method 5900 may be
performed by one or more server processors in one or more network components
included in a DSA-TCE system. In the example illustrated in FIG. 59, the DSA-
TCE
validation method 5900 is performed in a DSA-TCE system that includes a lessee
bidder network 5902 server, a telecommunication exchange server 5904, and a
dynamic policy controller (DPC) 5906.
[00442] The lessee bidder network 5902 server may be included in or associated
with a
commercial bidder telecommunication network, such as one of the bidder
networks
5804, 5806, 5808 discussed above with reference to FIG. 58. In an embodiment,
the
lessee bidder network 5902 server may be a bidder server, such as one of
bidder 5824,
5826, 5828 servers/components discussed above. Likewise, the telecommunication
exchange server 5904 may be the telecommunication exchange network 5802
118
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
component, and the DPC 5906 may be any of the dynamic policy controller
components (e.g., 5720, 5816, 5818, etc.) discussed above.
[00443] In operation 5906 of DSA-TCE validation method 5900, a processor of a
lessee bidder 5902 server may send a bidding access request message to a
telecommunication exchange server 5904. In operation 5908, the
telecommunication
exchange server 5904 may identify a suitable dynamic policy controller (DPC)
5904
component/server based on information included in the request, and send the
bidding
access request message to the identified DPC 5904 component/server. In
operation
5910, the DPC 5904 component may send a credential request message to the
telecommunication exchange server 5904, which may send the credential request
to
the lessee bidder 5902 in operation 5912.
[00444] In operation 5914, the lessee bidder 5902 may send the lessee's
credential
information to the telecommunication exchange server 5904. The lessee's
credential
information may include type of geographic area for the resource request,
wireless
access technologies, frequencies of operation that are compatible with the
predefined
bidder's user equipment, the amount of bandwidth required, a duration for use
of the
resources, begin and end times of the resource request, etc. In operation
5916, the
telecommunication exchange server 5904 may send the lessee's credentials to
the
DPC 5904 component. In operation 5918, the DPC 5904 component may perform
bidder validation operations to determine whether the lessee bidder 5902 is
qualified
to take part in an auction/exchange (i.e., to bid on telecommunication
resources, etc.)
and/or is associated with a network that is qualified to participate in the
auction/exchange. In an embodiment, as part of operation 5918, the DPC 5904
component may validate that the requested telecommunication resources may be
used
by a bidder network requesting the telecommunication resources.
[00445] In operation 5920, the DPC 5904 component may send a validation
response
message to 5920 to telecommunication exchange server 5904. In operation 5922,
the
telecommunication exchange server 5904 may send the validation response
message
to the lessee bidder 5902. In operation 5924, the lessee bidder 5902 may
determine if
119
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
it is allowed to participate in the auction/exchange based on information
included in
the received validation response message, and if authorized, perform various
initialization operations in preparation of participating in the
auction/exchange. Such
initialization operations may include notifying the corresponding bidder
network that
it is authorized participate in the auction and requesting information (e.g.,
price limits,
quantity, bidding strategies, etc.) from the bidder network for use during the
auction.
[00446] FIG. 60 illustrates an embodiment DSA-TCE resource validation method
6000 for validating/verifying that that a requested telecommunication
resources may
be used by a bidder network requesting the telecommunication resources. The
operations of the DSA-TCE resource validation method 6000 may be performed by
one or more server processors in a DSA-TCE system, which may include a lessee
bidder network 5902 server, a telecommunication exchange server 5904, a
dynamic
policy controller (DPC) 5906 component, and a lessor dynamic spectrum
controller
(DSC) 6002 component. In an embodiment, the lessee bidder network 5902 server
may be included in the lessee network 5730b discussed used above with
reference to
FIG. 57. In an embodiment, the lessor DSC 6002 component may be included in
the
lessor network 5703a discussed used above with reference to FIG. 57.
[00447] In an embodiment, the DSA-TCE resource validation method 6000 may be
performed as part of operation 5918 of the DSA-TCE validation method 5900
discussed above with reference to FIG. 59. In an embodiment, the DSA-TCE
resource
validation method 6000 may be performed after the bidder network has been
authorizing to participate in a telecommunications commodity exchange, which
may
be accomplished via the performance of the DSA-TCE validation method 5900.
[00448] In operation 6004 of the DSA-TCE resource validation method 6000, a
processor of a lessee bidder 5902 component may send a resource request
message to
a telecommunication exchange server 5904. In operation 6006, the
telecommunication exchange server 5904 may send the resource request message
to
the dynamic policy controller (DPC) 5904 component/server. In operation 6008,
the
DPC 5904 component/server may send a resource inquiry response message to a
120
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
lessor dynamic spectrum controller (DSC) 6002 component/server. In operation
6012,
the DPC 5904 component/server may send the telecommunication exchange server
5904 a compatibility message that includes information suitable for use in
determining
whether the requested resource is compatible with the lessee bidder's network.
The
compatibility message may include information regarding the number or types of
credentials checked, geographic area of the requested resource, wireless
access
technologies of the requested resource, operating frequencies of the requested
resources and their compatibility with the bidder's user equipment, the amount
of
bandwidth that is going to be required, the duration the resources are needed,
and
start/begin and end times of the resource request, and/or other similar
information.
[00449] In operation 6014, the telecommunication exchange server 5904 may
determine whether the requested resources are compatible with, or may be
utilized by,
the lessee bidder's network based on the compatibility message received from
the
DPC 5904 component/server. If telecommunication exchange server 5904
determines that the requested resources are compatible with or may be utilized
by the
lessee bidder's 5902 network, in operation 6016, the telecommunication
exchange
server 5904 may send a bid access authorization message to the lessee bidder
5902
component. On the other hand, when the telecommunication exchange server 5904
determines that the requested resources are not compatible with the lessee
bidder's
5902 network, in operation 6016, the telecommunication exchange server 5904
may
either not send any further messages (e.g., bid access authorization message)
to the
lessee bidder 5902 component or send the lessee bidder 5902 component bid
denial
message indicating that the lessee bidder 5902 component cannot bid on (or
receive
access to) the requested resource.
[00450] FIG. 61 illustrates an embodiment DSA-TCE auction method 6100 for
determining which of a plurality of bidder networks are to be allocated a
telecommunication resource. The operations of DSA-TCE auction method 6100 may
be performed by one or more server processors or network components (e.g.,
DPC,
DSC, telecommunications exchange server, etc.) in any of the DSA systems
discussed
above, such as the DSA systems illustrated in FIGs. 57 and 58. In the example
121
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
illustrated in FIG. 61, the DSA-TCE auction method 6100 is performed in a DSA
system that includes a telecommunication exchange server 5904, a first bidder
network (Bidder A) 6102, a second bidder network (Bidder B) 6104, and a third
bidder network (Bidder X) 6106. In various embodiments, any or all of the
bidder
networks 6102, 6104, 6102 may be a lessee bidder network server included in or
associated with a commercial bidder telecommunication network, such as the
bidder
networks 5804, 5806, 5808 discussed above with reference to FIG. 58.
[00451] In an aspect, the DSA-TCE auction method 6100 may be performed after
the
bidder networks have been authorized (e.g., via the DSA-TCE validation method
5900) to participate in the auction and validated/verified to support the
telecommunication resource being auctioned (e.g., via the resource validation
method
6000).
[00452] In operation 6108 of DSA-TCE auction method 6100, the DSA system may
start an auction procedure or begin a bidding process during which the bidder
networks 6102, 6104, 6106 may bid for telecommunication resources. In an
aspect,
this may be achieved by the telecommunication exchange server 5904
broadcasting a
communication message indicating a start time or otherwise informing the
bidder
networks 6102, 6104, 6106 of a time in which the auction or bidding process is
to
commence. In another aspect, a DPC may start the auction procedure and bidding
process.
[00453] In operation 6110, the telecommunication exchange server 5904 may
generate
a communication message that includes bidding information, such a minimum
price,
starting price, bid increments, etc. Also in operation 6110, the
telecommunication
exchange server 5904 may send the generated communication message to each of
the
bidder networks 6102, 6104, 6106.
[00454] In operation 6112, the first bidder network (Bidder A) 6102 places a
bid for a
telecommunication resource by sending a bid message to the telecommunication
exchange server 5904. In operation 6114, the telecommunication exchange server
5904 may receive the bid message and determine if the amount identified in the
122
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
received bid is greater than the auction start price. If the received bid
price is greater
than the auction start price, in operation 6114, the telecommunication
exchange server
5904 may perform additional operations to accept the received bid, increase
the
current price for the telecommunication resource, generate a communication
message
that includes the new price and information identifying the first bidder
network
(Bidder A) 6102 as the top bidder, and send the generated communication
message to
each of the bidder networks 6102, 6104, 6106. In various aspects, in operation
6114,
the telecommunication exchange server 5904 may be configured to generate the
communication message to include only the new price and/or may send the
generated
message to only the bidder networks that are not in the lead (i.e., second and
third
bidder networks) to win access to or use of the requested telecommunication
resource.
[00455] In operation 6116, the second bidder network (Bidder B) 6104 may place
a
bid for the telecommunication resource by sending a bid message to the
telecommunication exchange server 5904. In operation 6118, the
telecommunication
exchange server 5904 may receive the bid message, determine if the amount
identified
in the received bid message is greater than the current price for the
telecommunication
resource and/or meets the bid increment requirements. If the received bid is
greater
than the current price and meets the bid increment requirements, in operation
6118,
the telecommunication exchange server 5904 may also perform operations to
accept
the bid, raise the current price for the telecommunication resource, generate
a
communication message that includes the new price and information identifying
the
second bidder network (Bidder B) 6104 as the top bidder, and send the
generated
communication message to each of the bidder networks 6102, 6104, 6106. In
various
embodiments, in operation 6118, the telecommunication exchange server 5904 may
be
configured to generate the communication message to include only the new price
and/or send the generated message to only the bidder networks that are not in
the lead
(i.e., first and third bidder networks) to win access to or use of the
requested
telecommunication resource.
[00456] In operation 6120, the third bidder network (Bidder X) 6106 may place
a bid
for telecommunication resources by sending a bid message to the
telecommunication
123
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
exchange server 5904. In operation 6122, the telecommunication exchange server
5904 may receive the bid, determine if the received bid is greater than the
current
price for the telecommunication resource and meets the bid increment
requirements,
accept the bid if the received bid is greater than the current price and meets
the bid
increment requirements, raise the current price for the telecommunication
resource,
generate a communication message that includes the new price and information
identifying the third bidder network (Bidder X) 6106 as the top bidder, and
send the
generated communication message to each of the bidder networks 6102, 6104,
6106.
In various aspects, in operation 6122, the telecommunication exchange server
5904
may generate the message to only include the new price and/or only send the
generated message to bidder networks that are not in the lead (i.e., first and
second
bidder networks).
[00457] In operation 6124, the first bidder network (Bidder A) 6102 may place
another
bid for the telecommunication resource by sending another bid message to the
telecommunication exchange server 5904. In operation 6126, the
telecommunication
exchange server 5904 may receive the bid, determine if the received bid is
greater
than the current price for the telecommunication resource and meets the bid
increment
requirements, accept the bid if the received bid is greater than the current
price and
meets the bid increment requirements, raise the current price for the
telecommunication resource, generate a communication message that includes the
new
price and information identifying the first bidder network (Bidder A) 6102 as
the top
bidder, and send the generated communication message to each of the bidder
networks
6102, 6104, 6106. In an aspect, in operation 6126, the telecommunication
exchange
server 5904 may generate the message to include only the new price and/or send
the
generated message to only the bidder networks that are not in the lead (i.e.,
second and
third bidder networks).
[00458] Any or all of operations 6110-6126 of the DSA-TCE auction method 6100
may be performed repeatedly and/or as needed until the DSA system closes the
bidding window in operation 6128. In an aspect, this may be achieved by the
telecommunication exchange server 5904 not accepting any further bids and/or
124
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
broadcasting a communication message indicating the end of the bidding window
or
informing the bidder networks 6102, 6104, 6106 that the auction is closed. In
operation 6130, the telecommunication exchange server 5904 may generate a
communication message that identifies the top/highest bidder (i.e., Bidder A)
as the
winner of the auction for the telecommunication resource, and send the
generated
message to each of the bidder networks 6102, 6104, 6106.
[00459] FIG. 62 illustrates an embodiment DSA-TCE allocation method 6200 for
allocating a telecommunication resource to a bidder network. The operations of
the
DSA-TCE allocation method 6200 may be performed by server processors or
network
components (e.g., DPC, DSC, telecommunications exchange server, etc.) in any
of the
DSA systems discussed above, such as one of the DSA systems illustrated in
FIGs. 57
and 58. In an aspect, the DSA-TCE allocation method 6200 may be performed in
response to a telecommunication exchange server 5904 determining that a bidder
network has won an auction for a telecommunication resource, such as after
operation
6130 of the DSA-TCE auction method 6100 discussed above with reference to FIG.
61. In an aspect, any or all of the operations of the DSA-TCE allocation
method 6200
may be performed at a time/date identified in a futures contract purchased via
a DSA-
TCE auction.
[00460] In operation 6204 of DSA-TCE allocation method 6200, a processor of a
server/component in the DSA system may determine that a resource auction has
been
completed and won by a bidder network (Bidder A) 6102 component. In operation
6206, the bidder network 6102 component may send a resource request message to
the
telecommunication exchange server 5904. In operation 6208, the
telecommunication
exchange server 5904 may send the resource request message to the dynamic
policy
controller (DPC) 5904 component/server.
[00461] In operation 6210, the DPC 5904 component/server may send a resource
inquiry message to a dynamic spectrum controller (DSC) in a lessor network
(herein
"lessor DSC") 6002. In operation 6210, the lessor DSC 6002 component/server
may
send a resource inquiry response message to the DPC 5904 component/server. In
125
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
operation 6214, the DPC 5904 component/server may send a resource allocation
request message to the lessor network component. In operation 6216, the lessor
DSC
6002 component/server may send a resource allocation response message to the
DPC
5904 component/server authorizing the DPC 5904 component/server to allocate a
telecommunication resource in a network associated with the lessor DSC 6002
component/server.
[00462] In operation 6218, the DPC 5904 component/server may send a resource
allocation message to a DSC 6202 component associated with the bidder network
(Bidder A) 6102 component. In operation 6220, the DSC 6202 component may
allocate the telecommunication resource for use by the lessee bidder network
5902. In
operation 6222, the components in the lessee bidder network 5902 may be
notified
that the telecommunication resource has been allocated and is available and/or
may
begin using the allocated telecommunication resource.
[00463] In various embodiments, the DSA-TCE system may be configured to
facilitate
the use margins and futures contracts by operating as a clearing house and
allowing a
bidder network to purchase or enter into a contract for the future use of a
telecommunication resource. For example, a telecommunication resource investor
knows that on a certain holiday, there is an exceptional amount of traffic in
a certain
coverage zone that they provide resources too. The resource investor would
then
place a trade order via the DSA-TCE system, and a DPC or DPC broker may
interact
with one or more DSCs/lessor networks to search for available and compatible
resources. At the initiation of the trading process the initial margin money
may be
automatically deposited in the trading account of the resource investor, and
after a
predefined period of bidding time (e.g., a business day or longer), the final
price of the
auctioned commodity may be set by a telecommunication exchange server.
Depending on whether or not the resource investor finds the final price
favorable,
funds are automatically added or removed from the investor's account.
[00464] FIG. 63 illustrates an embodiment DSA-TCE futures auction method 6300
for
determining if a bidder network may purchase a futures contract that promise
delivery
126
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
or allocation of' a telecommunication resource to the purchaser at a future
date/time for
a currently-agreed to price. The operations of DSA-TCE futures auction method
6300
may be performed by one or more server processors or network components (e.g.,
DPC, DSC, telecommunications exchange server, etc.) in any of the DSA systems
discussed above, such as the DSA systems illustrated in FIGs. 57 and 58. In
the
example illustrated in FIG. 63, the DSA-TCE futures auction method 6300 is
performed in a DSA system that includes a lessee bidder network 5902
component, a
telecommunication exchange server 5904, a DPC 5906 component, and a lessor DSC
6002 component.
[00465] In operation 6302, the lessee bidder network 5902 component may send a
futures resource request message to the telecommunication exchange server
5904. In
operation 6304, the telecommunication exchange server 5904 may send the
futures
resource request message to the DPC 5906 component. In operation 6306, the DPC
5906 component may send a futures resource inquiry message to the lessor DSC
6002
component.
[00466] In operation 6308, the lessor DSC 6002 component may determine whether
the requested telecommunication resource will be available at the future
time/date, and
send the DPC 5906 component a futures resource inquiry response message
indicating
that the resource is available when it determines that telecommunication
resource will
be available at the future time/date. In operation 6310, the DPC 5906
component may
send a futures resource available message to the telecommunication exchange
server
5904. In operation 6312, the telecommunication exchange server 5904 may send
the
futures resource available message to the lessee bidder network 5902
component.
[00467] In operation 6314, the DSA system may perform operations similar to
those
illustrated in FIG. 61 for the futures contract to determine a winner for the
auction and
end the bidding/auction process. In operation 6316, the telecommunication
exchange
server 5904 may send the DPC 5906 component a communication message
identifying the winner and indicating that the resource is to be allocated to
the winner
(or a network of the winner's choosing) at the future date/time indicated in
the futures
127
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
contract. In operation 6318, the telecommunication exchange server 5904 may
send
the lessee bidder network 5902 component a communication message identifying
the
winner of the auction and any necessary additional details of the futures
contract or
auction.
[00468] In an embodiment, the DSA-TCE system may be configured to allocate
resources outside of the auctioned resources if and when they are needed by an
investor. For example, if a service provider network encounters unpredicted
traffic at
a certain time and more resources are needed to uphold the quality of
telecommunication, it is possible to request resources that were not available
at the
time of auction, or are currently being offered for auction. A wireless or
telecommunication provider may send a request for resources to the DPC, which
may
in turn communicate with its DSCs and reallocate resources, if available, to
the lessee
experiencing unforeseen congestion and traffic.
[00469] FIG. 64 illustrates an embodiment DSA-TCE post-bid resource allocation
method 6400 for requesting and receiving telecommunications resources for
immediate use. The operations of the DSA-TCE post-bid resource allocation
method
6400 may be performed by one or more server processors or network components
(e.g., DPC, DSC, telecommunications exchange server, etc.) in any of the DSA
systems discussed above, such as the DSA systems illustrated in FIGs. 57 and
58. In
the example illustrated in FIG. 64, the DSA-TCE auction method 6100 is
performed
in a DSA system that includes a lessee network 6452, a lessee DSC 6454, a
bidder
component 6456, a telecommunication exchange server 6458, a DPC 6460, and a
lessor DSC 6462.
[00470] In operation 6402, the lessee network 6452 may detect network
congestion on
its network. In operation 6404, the lessee DSC 6454 may be informed of the
network
congestions and determine that the procurement of additional
telecommunications
resources would help alleviate the network congestion. In operation 6406, the
lessee
DSC 6454 may send a request for resources message to a bidder component 6456.
In
operation 6408, the bidder component 6456 may send a request for resources
message
128
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
to the telecommunication exchange server 6458. In operation 6410, the
telecommunication exchange server 6458 may send a request for resources
message to
the DPC 6460. In operation 6412, the DPC may send a resource inquiry message
to
the lessor DSC 6462.
[00471] In operation 6414, the lessor DSC 6462 component/server may send a
resource inquiry response message to the DPC 6460 component/server. In
operation
6416, the DPC 6460 may perform various validation and/or verification
operations to
determine whether the resource is compatible with the lessee network, and send
the
telecotnmunication exchange server 6458 a communication message indicating
that a
compatible resource is available when the DPC 6460 determines that the
resource is
compatible.
[00472] In operation 6460, the telecommunication exchange server 6458 may
determine whether the lessee is compatible to the existing bid, and allow the
bidder
component 6456 to participate in a bidding/auction process for the resource.
In
operation 6420, the telecommunication exchange server 6458 may send a bid
access
message to the bidder component 6456 to allow the bidder component 6456 to
participate in the auction. In operation 6422, the bidder component 6456 may
perform
bidding operations to place bids on the telecommunication resource being
auctioned.
[00473] In operation 6424, the telecommunication exchange server 6458 may
determine that the bidder component 6456 won the auction, inform the lessor
DSC
6462, and request that the lessor DSC 6462 allocate the telecommunication
resource.
In operation 6426, the lessor DSC 6462 may allocate the resources and send a
resources allocation message to the telecommunication exchange server 6458. In
operation 6428, the telecommunication exchange server 6458 may send a
resources
allocation message to the lessee DSC 6454 informing it that it may begin using
the
allocated resource. In operation 6430, the lessee DSC 6454 may allocate the
resources for use by the lessee network 6452.
[00474] FIG. 65 illustrates another embodiment DSA-TCE post-bid resource
allocation method 6500 for requesting and receiving telecommunications
resources for
129
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
immediate use. In the example illustrated in FIG. 65, the existing bids do not
match
the credentials of the bidder's existing network, and thus the DPC searches
for other
available resources on other DSCs to find and allocates suitable resources to
the
network experiencing congestion.
[00475] In operation 6502, the lessee network 6452 may detect network
congestion on
its network. In operation 6504, the lessee DSC 6454 may be informed of the
network
congestions and determine that the procurement of additional
telecommunications
resources would help alleviate the network congestion. In operation 6506, the
lessee
DSC 6454 may send a request for resources message to a bidder component 6456.
In
operation 6508, the bidder component 6456 may send a request for resources
message
to the telecommunication exchange server 6458. In operation 6510, the
telecommunication exchange server 6458 may send a request for resources
message to
the DPC 6460. In operation 6512, the DPC may send a resource inquiry message
to
the lessor DSC 6462.
[00476] In operation 6512, the DPC 6460 may check existing telecommunication
resource auctions to determine if one of the resources being auctioned is
compatible
with the lessee network 6452. In operation 6514, the DPC 6460 may determine
that
none the resources currently being auctioned are compatible with the lessee
network
6452.
[00477] In operation 6516, the DPC 6460 may send a resource inquiry to the
lessor
DSC 6462 to determine if there are any additional resources that the not
currently
being auctioned, that are available for allocation and which are compatible
with the
lessee network 6452. In operation 6518, the lessor DSC 6462 may send a
resource
inquiry response message to the DPC 6460. In operation 6520, the DPC 6460
component/server may send the telecommunication exchange server 6458 a
communication message indicating that a resource is available for allocation.
[00478] In operation 6522, the telecommunication exchange server 6458 may send
a
communication message indicating that a resource is available for allocation
to the
bidder component 6456. In operation 6524, the bidder component 6456 may send a
130
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
resource request to the telecommunication exchange server 6458. In operation
6526,
the telecommunication exchange server 6458 may send a resource request message
to
the DPC 6460 component/server. In operation 6528, the DPC 6460
component/server
may send a communication message requesting that the lessor DSC 6462 reserve
the
resource. In operation 6530, the lessor DSC 6462 may reserve the resource and
inform
the DPC 6460 that the resource has been reserved.
[00479] In operation 6532, the bidder component 6456 may submit a bid for use
of the
reserved resource to the DPC 6460 component/server. In operation 6534, the DPC
6460 component/server may accept the bid and send a communication message to
the
bidder component 6456 notifying it that its bid has been accepted. In
operation 6536,
the DPC 6460 component/server may send the lessor DSC 6462 a communication
message informing the lessor DSC 6462 requesting that the lessor DSC 6462
assign
the reserved resource for allocation to the lessee network 6452. In operation
6538, the
lessor DSC 6462 may send the DPC 6460 a communication message indicating that
the resources may be allocated for use by the lessee network 6452.
[00480] In operation 6540, the DPC 6460 component/server may send a
communication message to the lessee DSC 6454 informing it of the availability
of
allocated resources. In operation 6542, the lessee DSC 6454 may allocate the
resources for use by the lessee network 6452. In operation 6544, the resources
may be
used by the lessee network 6452.
[00481] In the various embodiments, a DPC 6460 may interact with multiple DSCs
belonging to different networks or entities to control the entire resource
allocation
process. The telecommunications exchange server 6458 provides the transaction
platform and performs the auction/bidding operations. The telecommunications
exchange server 6458 may offer the resources by region, technology, or via any
method and into any submarket that is available. In an embodiment, the
telecommunications exchange server 6458 may act as a broker between the
network
operators and bidders.
131
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00482] In an embodiment, each network operator may have one or more DSC's
that
are used to connect either to a DPC or a DPC cluster. The function of the DPC
in the
whole process is what makes the DSA unique. The role of the DPC is one that
can
either be centrally located, or distributed. In a centralized configuration,
all of the
DSC's will communicate with a DPC, if within the DPCs geodetic area. A DPCs
geodetic area can be an entire state, such as New York, or large region, such
as
Northeastern U.S. When there is a cluster of DPCs, the system may govern a
system
of multiple allocation zones, such as the Northeastern U.S. In any case, no
matter
how many DPCs are grouped together in a system (i.e., multiple DPCs or just a
single
DPC) they may communicate with a central telecommunication exchange network.
With this system, DPCs may interact with each other on any level, and
reallocate
resources according to whichever network is in need of resources. With the
entire
system being able to communicate internally such as this, the DSA system will
be a
vastly more efficient use of resources in comparison to existing solutions.
[00483] FIG. 66 illustrates an embodiment DSA-TCE system 6600 in which each
network has a single DSC. Each of the DSCs (A-X) communicate with a single DPC
6602, which in turn communicates with the telecommunication exchange network.
The DPC 6602 manages the multiple DSCs (A-X) so that resources may be
reallocate
between the multiple networks.
[00484] FIG. 67 illustrates an embodiment DSA-TCE system 6700 that includes a
centralized DPC 6702 and a plurality of DPCs (A-X) coupled to the centralized
DPC
6702. The centralized DPC 6702 manages the multiple DPCs (A-X) and
communicates with a single telecommunication exchange network so that
resources
may be reallocated between the multiple networks represented by the DPCs (A-
X).
[00485] Each of the plurality of DPCs (A-X) may govern multiple coverage zones
and
may be configured to allocate resources in a laissez faire fashion. Because
the DPCs
connect to multiple wireless providers DSC's, this arbitrage process creates a
new and
unique way to exchange wireless resources.
132
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00486] After a lease is terminated, a lessor may request for a return of
resources from
a lessee. This may be accomplished by the lessor sending a request message
through
the DPC, and the lessee sending the renewable resources through to the
lessor's
resource pool once they have been consumed. That is, through the DPC, a DSC is
now able to inform the telecommunications exchange broker of the newly
available
resources, which are now available for rebidding.
[00487] FIG. 68 illustrates another embodiment DSA-TCE post-bid resource
reallocation method 6800 for receiving returned resources and submitting the
newly
available resources to be auctioned. The operations of the DSA-TCE post-bid
resource reallocation method 6800 may be performed by one or more server
processors or network components (e.g., DPC, DSC, telecommunications exchange
server, etc.) in any of the DSA systems discussed above, such as the DSA
systems
illustrated in FIGs. 57 and 58. In the example illustrated in FIG. 64, the DSA-
TCE
auction method 6100 is performed in a DSA system that includes a lessee
network
6452, a lessee DSC 6454, a bidder component 6456, a telecommunication exchange
server 6458, a DPC 6460, and a lessor DSC 6462.
[00488] In operation 6802, the DSA system determines that the term of a
telecommunication resource lease has expired. In operation 6804, the DPC 6460
may
send a communication message to the lessee DSC 6454 requesting the return of
the
telecommunication resource. In operation 6806, the lessee DSC 6454 may return
the
telecommunication resource by ceasing use of the resource and informing the
DPC
6460 that the use of the resource has ceased. In operation 6808, the DPC 6460
may
inform the lessor DSC 6462 the telecommunication resource is now available for
reallocation. In operation 6810, the lessor DSC 6462 may renew the
telecommunication resource and inform the DPC 6460 of the renewal. In
operation
6812, the DPC 6460 may inform the telecommunication exchange server 6458 that
a
new resource is available for auctioning.
[00489] Various embodiments may include a dynamic spectrum arbitrage (DSA)
method of conducting a telecommunications commodity exchange (TCE) that
133
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
includes determining in a communications server that a telecommunication
resource
of a first communication network is available for allocation, broadcasting a
communication signal informing a plurality of communication networks that the
telecommunication resource is available for allocation via a auction and of a
start time
for the auction, receiving bids from the plurality of communication networks
for the
telecommunication resource determined to be available for allocation,
allocating the
telecommunication resource of the first communication network for access and
use by
a second communication network in the plurality of communication networks
based
on received bids, informing the second communication network that use of
allocated
telecommunication resource may begin, and recording a transaction in a
transaction
database identifying the telecommunication resource as being allocated for use
by the
second communication network.
[00490] In an embodiment, determining that a telecommunication resource of a
first
communication network is available for allocation includes determining that
the
telecommunication resource is available for allocation at a future date and
time. In a
further embodiment, receiving bids from the plurality of communication
networks for
the telecommunication resource determined to be available for allocation
includes
receiving bids for access and use of the telecommunication resource determined
at the
future date and time. In a further embodiment, allocating the
telecommunication
resource of the first communication network for access and use by a second
communication network in the plurality of communication networks based on
received bids includes allocating the telecommunication resource of the first
communication network for access and use by the second communication network
at
the future date and time.
[00491] In an embodiment, the method may also include determining whether the
telecommunication resource is compatible with each of the plurality of
communication networks, authorizing each of the networks in the plurality of
communication networks as being eligible to participate in the
telecommunications
commodity exchange based on their compatibility with the telecommunication
resource, and accepting bids from only the authorized networks.
134
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
[00492] In an embodiment, the method may also include requesting the return of
the
allocated telecommunication resource and broadcasting a second communication
signal informing the plurality of communication networks that the
telecommunication
resource is available for reallocation via a second auction.
[00493] Further embodiments may include a processor configured with processor-
executable instructions to perform operations of the various methods discussed
above.
[00494] Further embodiments may include means for performing functions of the
operations of the various methods discussed above.
[00495] Further embodiments may include a non-transitory processor-readable
storage
medium having stored thereon processor-executable instructions to cause a
processor
to perform operations of the various methods discussed above.
[00496] The various aspects may be implemented on a variety of mobile
computing
devices, an example of which is illustrated in FIG. 65. Specifically, FIG. 65
is a
system block diagram of a mobile transceiver device in the form of a
smartphone/cell
phone 6500 suitable for use with any of the aspects. The cell phone 6500 may
include
a processor 6501 coupled to internal memory 6502, a display 6503, and to a
speaker
6508. Additionally, the cell phone 6500 may include an antenna 6504 for
sending and
receiving electromagnetic radiation that may be connected to a wireless data
link
and/or cellular telephone transceiver 6505 coupled to the processor 6501. Cell
phones
6500 typically also include menu selection buttons or rocker switches 6506 for
receiving user inputs.
[00497] The embodiments described above, including the DSA-TCE operations, may
be implemented within a variety of commercially available server devices, such
as the
server 6900 illustrated in FIG. 69. Such a server 6900 typically includes a
processor
6901 coupled to volatile memory 6902 and a large capacity nonvolatile memory,
such
as a disk drive 6903. The server 6900 may also include a floppy disc drive,
compact
disc (CD) or DVD disc drive 6911 coupled to the processor 6901. The server
6900
may also include network access ports 6906 coupled to the processor 6901 for
135
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
establishing data connections with a network 6905, such as a local area
network
coupled to other communication system computers and servers.
1004981 The processor 6901 may be any programmable microprocessor,
microcomputer or multiple processor chip or chips that can be configured by
software
instructions (applications) to perform a variety of functions, including the
functions of
the various aspects described below. In some devices, multiple processors 6901
may
be provided, such as one processor dedicated to wireless communication
functions and
one processor dedicated to running other applications. Typically, software
applications may be stored in the internal memory 6902, before they are
accessed and
loaded into the processor 6901. The processor 6901may include internal memory
sufficient to store the application software instructions. In some servers,
the processor
6901 may include internal memory sufficient to store the application software
instructions. In some receiver devices, the secure memory may be in a separate
memory chip coupled to the processor 6901. The internal memory 6902 may be a
volatile or nonvolatile memory, such as flash memory, or a mixture of both.
For the
purposes of this description, a general reference to memory refers to all
memory
accessible by the processor 6901, including internal memory 6902, removable
memory plugged into the device, and memory within the processor 6901 itself.
[00499] Embodiments include methods for managing, allocating and arbitraging
RF
bandwidth as described above. Embodiments also include the communication
systems that enable the DPC methods. Embodiments also include the non-
transitory
computer-readable storage media storing computer-executable instructions for
performing the methods described above.
[00500] The foregoing method descriptions and the process flow diagrams are
provided merely as illustrative examples and are not intended to require or
imply that
the steps of the various embodiments must be performed in the order presented.
As
will be appreciated by one of skill in the art the order of steps in the
foregoing
embodiments may be performed in any order. Words such as "thereafter," "then,"
"next," etc. are not intended to limit the order of the steps; these words are
simply
136
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
used to guide the reader through the description of the methods. Further, any
reference to claim elements in the singular, for example, using the articles
"a," "an" or
"the" is not to be construed as limiting the element to the singular.
[00501] The various illustrative logical blocks, modules, circuits, and
algorithm steps
described in connection with the embodiments disclosed herein may be
implemented
as electronic hardware, computer software, or combinations of both. To clearly
illustrate this interchangeability of hardware and software, various
illustrative
components, blocks, modules, circuits, and steps have been described above
generally
in terms of their functionality. Whether such functionality is implemented as
hardware or software depends upon the particular application and design
constraints
imposed on the overall system. Skilled artisans may implement the described
functionality in varying ways for each particular application, but such
implementation
decisions should not be interpreted as causing a departure from the scope of
the
present invention.
[00502] The hardware used to implement the various illustrative logics,
logical blocks,
modules, and circuits described in connection with the embodiments disclosed
herein
may be implemented or performed with a general purpose processor, a digital
signal
processor (DPC), an application specific integrated circuit (ASIC), a field
programmable gate array (FPGA) or other programmable logic device, discrete
gate or
transistor logic, discrete hardware components, or any combination thereof
designed
to perform the functions described herein. A general-purpose processor may be
a
microprocessor, but, in the alternative, the processor may be any conventional
processor, controller, microcontroller, or state machine. A processor may also
be
implemented as a combination of computing devices, e.g., a combination of a
DPC
and a microprocessor, a plurality of microprocessors, one or more
microprocessors in
conjunction with a DPC core, or any other such configuration. Alternatively,
some
steps or methods may be performed by circuitry that is specific to a given
function.
[00503] In one or more exemplary embodiments, the functions described may be
implemented in hardware, software, firmware, or any combination thereof. If
137
CA 02904634 2015-09-08
WO 2014/160106
PCT/US2014/025827
implemented in software, the functions may be stored as one or more
instructions or
code on a non-transitory computer-readable medium or non-transitory processor-
readable medium. The steps of a method or algorithm disclosed herein may be
embodied in a processor-executable software module which may reside on a non-
transitory computer-readable or processor-readable storage medium. Non-
transitory
computer-readable or processor-readable storage media may be any storage media
that
may be accessed by a computer or a processor. By way of example but not
limitation,
such non-transitory computer-readable or processor-readable media may include
RAM, ROM, EEPROM, FLASH memory, CD-ROM or other optical disk storage,
magnetic disk storage or other magnetic storage devices, or any other medium
that
may be used to store desired program code in the form of instructions or data
structures and that may be accessed by a computer. Disk and disc, as used
herein,
includes compact disc (CD), laser disc, optical disc, digital versatile disc
(DVD),
floppy disk, and blu-ray disc where disks usually reproduce data magnetically,
while
discs reproduce data optically with lasers. Combinations of the above are also
included within the scope of non-transitory computer-readable and processor-
readable
media. Additionally, the operations of a method or algorithm may reside as one
or
any combination or set of codes and/or instructions on a non-transitory
processor-
readable medium and/or computer-readable medium, which may be incorporated
into
a computer program product.
[00504] The preceding description of the disclosed embodiments is provided to
enable any
person skilled in the art to make or use the present invention. Various
modifications to these
embodiments will be readily apparent to those skilled in the art, and the
generic principles
defined herein may be applied to other embodiments without departing from the
spirit or
scope of the invention. Thus, the present invention is not intended to be
limited to the
embodiments shown herein but is to be accorded the widest scope consistent
with the
following claims and the principles and novel features disclosed herein.
138