Note: Descriptions are shown in the official language in which they were submitted.
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
DATA AUTHENTICATION METHOD, DEVICE AND SYSTEM, AND COMPUTER
STORAGE MEDIUM
Technical Field
The present invention relates to data process field, especially to data
process method, device
and system, and computer storage medium.
Background Technology
With the development of network technology, the continuous development of e-
commerce, the
traditional use of various kinds of objects, tickets, receipts, etc. are
replaced by electronic, its
manifestations are mainly three kinds: character data, image data and
streaming media data. The
kind of e-commerce activity is replaced by the image data, the image
represents the actual attribute
of the item, and the security is important in the e-commerce activity.
Traditional e-commerce activities used in the electronic certificate image
goods can be copied
freely, or even tamper with low security.
Summary of the invention
Based on this, it is necessary to improve the security of data in the e-
commerce activities by
providing data authentication method, device and system, and computer storage
medium for solving
the problem that the data in the traditional e-commerce activity is easily
copied and tampered.
A data authentication method also comprises:
Separating the data image electronic certificate to obtain a digital signature
and an image in
which the key is embedded;
Performing a signature identity authentication according to the digital
signature;
After the signature identity authentication is passed, the data is verified
according to the image
in which the key is embedded;
After the data is checked, the key is extracted from the image in which the
key is embedded;
And the data of each state of each party in the e-commerce transaction is
obtained based on the
key query data.
A data authentication device for authenticating an electronic image of a data
image encrypted
by digital signature and key encryption, comprising:
A separating module for separating the data image electronic certificate to
obtain a digital
signature and an image in which the key is embedded;
An identity authentication module for performing signature authentication
according to the
digital signature;
A data checking module for performing data checking according to an image in
which the key
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
is embedded after the signature authentication is passed;
An extraction module for extracting a key from an image in which the key is
embedded after
the data checking is passed;
And a query module for obtaining data of each state of each party in the e-
commerce
transaction based on the key query data.
A data authentication system. It is applied in application of the data image
electronic certificate
through digital signature and key encryption, a checking server, a signature
server and a cloud
database server connected to each other through a network;
The image generation processing server for separating the data image
electronic certificate to
obtain a digital signature and an image in which the key is embedded;
The signature server for performing signature identity authentication
according to the digital
signature;
The checking server is used to perform data checking according to the image in
which the key
is embedded after the signature authentication is passed;
The image generation processing server is further configured to extract a key
from an image in
which the key is embedded after the data checking is passed;
Wherein the cloud database server is configured to obtain data of each state
in the original
e-commerce transaction based on the key query data and to return the data of
each state of the
obtained e-commerce transaction to the terminal.
One or more computer storage media contains computer-executable instructions,
the said
computer executable instruction is used for executing a kind of data recording
method, and the
method comprises the following steps:
Separating the data image electronic certificate to obtain a digital signature
and an image in
which the key is embedded;
Performing a signature identity authentication according to the digital
signature;
After the signature identity authentication is passed, the data is verified
according to the image
in which the key is embedded;
After the data is checked, the key is extracted from the image in which the
key is embedded;
And the data of each state of each party in the e-commerce transaction is
obtained based on the
key query data.
In the data authentication method, device and system, and the computer storage
medium,
separation processing is performed on the data image electronic certificate to
obtain the digital
signature and the image having the embedded key, the identity authentication
is performed via the
digital signature, and the data checking is performed on the image having the
embedded key; after
the identity authentication and checking are passed extract the key, obtain
the data of each state of
2
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
each party in the e-connnerce transaction according to the key, conduct the
identity authentication
via the digital signature to ensure the validity of the data image electronic
certificate, conduct data
checking for the image that is embedded with the key, prevent the data from
being tampered, and
improve the security of the data of each state in the e-commerce transaction.
Brief Description
Figure 1 is an architectural block diagram of the data authentication system
in one example.
Figure 2 is a flow chart of the data recording method in one example;
Figure 3 is a flow chart of the data authentication method in one example;
Figure 4 is a block diagram showing the structure of the data authentication
device in one
example.
Figure 5 is a block diagram of the structure of the data authentication device
in one example;
Figure 6 is a block diagram showing the internal structure of the generation
module in one
sample;
Figure 7 is an internal schematic diagram of the server in one example.
Description of the Preferred Examples
The present invention will be described in further detail with reference to
the accompanying
drawings and the accompanying examples, so as to describe the invention
purposes, technical
solutions and advantages more clearly. It is to be understood that the
specific examples described
herein are merely illustrative of the invention and are not intended to limit
the invention.
Figure 1 is an architectural block diagram of the data authentication system
in one example. As
shown in Figure 1, the data authentication system includes an image generation
processing server
110, a checking server 120, a digital certificate management server 130, a
signature server 140, and
a cloud database server 150. The image generation processing server 110, the
verification server
120, the digital certificate management server 130, the signature server 140,
and the cloud database
server 150 are connected via a local area network and connected to the
Internet 170 through the
firewall 160.
The image generation processing server 110 collects the data of the each state
in the
e-commerce transaction and generates an image based on the collected data and
acquires the key of
the data to embed the key in the image. Specifically, the data of each state
in the e-commerce
transaction may include information such as the warehouse information, the
generation order
information, the delivery information, the end of the goods receipt
transaction, and the ownership of
the goods. Among them, the warehouse information can include the items belong
to the warehouse,
for an example, No. 1 Warehouse, ABC Building, Futian District, Shenzhen. The
order information
can include order generation time, item information in order, order number,
and consignee
information. The consignee information may include the name of the consignee,
and the consignee
3
address of the consignee. The shipping information may include the name of the
logistics company,
the delivery time, and the consignor information. The consignor information
may include the name
of the consignor, the address of the consignor, and the contact information of
the consignor. The
receipt information may include receipt information, and receipt time. The
signer information can
sign the recipient name, picture, ID information and so on.
The data of each state of each party in the e-commerce transaction may be
generated in various
aspects and stored on the cloud database server 150.
The image generation processing server 110 may obtain data of each state in
the e-commerce
transaction from the cloud database server 150.
In one example, the image generation processing server 110 is further
configured to generate a
key for the data using an order number, or a key for generating the data using
an order number and a
system clock.
Specifically, the key of the data is generated by the order number, and the
key of the data may
be the same as the order number. Using the order number and the system clock
to generate the data
key, you can obtain the Message-Digest algorithm 5 (MD5) value after
calculating the order number
and the system clock to generate the corresponding key. The key can also be a
UUID (Universally
Unique Identifier) algorithm. The UUID refers to the number generated on a
machine, which
guarantees that all machines in the same space and time are unique. The key
can be represented by
8-bit, 16-bit, 32-bit, 64-bit, and so on. Using the order number or order
number and the system to
generate data key, simple and convenient, and high security.
In one example, the image generation processing server 110 is also used to add
the key to the
binary code of the image.
Specifically, the key is a string in which the key can be embedded in the
binary code of the
image, and the specific typing position may be at the head of the image binary
code, either in the
middle or in the tail, as long as the original image file is not destroyed.
The checking server 120 is configured to generate the check data for the image
that is
embedded into the key.
Specifically, the checking server 120 may generate a check data by performing
a function
operation on an image that is embedded into the key by other algorithms, for
an example, a hash
algorithm.
The digital certificate management server 130 is used to provide a digital
certificate. The data
certificate management server 130 is used to issue and manage digital
certificates. The digital
certificates can be used to encrypt, sign and so on.
The signature server 140 is used to digitally sign an image that is embedded
into the key to
generate a data image electronic certificate.
4
Date Recue/Date Received 2020-09-04
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
In particular, the signature server 140 is further configured to digitally
generate an electronic
image of the data image by digitally signing the embedded image with the
supplied digital
certificate.
The digital signature is a generic physical signature similar to that written
on paper, but uses a
technique of public key encryption to identify digital information. A set of
digital signatures usually
defines two complementary operations, one for signing and the other for
authentication. The digital
signature is to encrypt the digest information with the sender's private key
and send it to the
recipient along with the original text. The recipient can decrypt the
encrypted digest information
only with the public key of the sender, and then use the hash function to
generate a summary
information on the original text received, compared with the deciphered
summary information, if
the same, then the received information is complete, but has not been modified
in the transmission
process, otherwise the information has been modified, so the digital signature
can verify the
integrity of the information.
There are many digital signature algorithms, which can be RSA (public key
encryption
algorithm), ECC, and so on. RSA public key encryption algorithm was introduced
in 1977 by Ron
Rivest, Adi Sliamir and Leonard Adleman. ECC is an elliptic encryption
algorithm, which is a
public key cryptography system, originally proposed by Kobiitz and Miller in
1985, whose
mathematical basis is to use the rational points on the elliptic curve to
compose the calculation of
elliptic discrete logarithms on Abel additive group.
The cloud database server 150 stores the data and the key corresponding to the
image and the
check data that is embedded into the key.
The digital certificate management server 130 may not be included in other
data recording
systems.
The image generation processing server 110 is used for separating the data
image electronic
certificate to obtain a digital signature and an image in which the key is
embedded.
In particular, the separated digital signature includes the identity data of
the signer.
The signature server 140 is used for signature authentication based on the
separated digital
signature.
The identity data of the signer in the separated digital signature is compared
with the identity
data of the signer stored on the cloud data server 150. If the authentication
is the same, the identity
authentication passes, otherwise, the authentication fails.
The checking server 120 is used to perform data checking based on the image in
which the key
is embedded after the signature authentication is passed.
In the present sample, the checking server 120 is further configured to
generate the check data
based on the separated image in which the key is embedded and to compare the
generated checking
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
data with the stored checking data, and if the same, the data checking is
passed, otherwise, the data
checking fails.
In one sample, the data checking based on an image embedded with a key
comprises
processing the collected image through a hash function to form an MD5 code,
searching the query
in the cloud database server, and forming the MD5 code in the above Step. If
so, the image has not
been tampered with, if not, then the image was tampered with.
In another sample, the data checking based on an image embedded with a key
includes
extracting a key from an image in which the key is embedded, and searching the
cloud storage
server for a pre-stored key corresponding to the key MD5 code, and then do the
hash by the image
processing to form an MD5, before and after the two MD5 are consistent; if the
same, the image has
not been tampered with; if different, the image was tampered with.
The image generation processing server 110 is further configured to extract
the key from the
image in which the key is embedded after the data checking is passed.
The cloud database server 150 is used to query the data based on the key to
obtain data of the
each state in the original e-commerce transaction and to return the data of
the each state in the
original e-commerce transaction to the terminal.
The data authentication system separates the digital signature and the
embedded key image by
the data image electronic certificate, performs the identity authentication by
the digital signature,
performs the data checking on the image that is embedded with the key , after
passing the identity
authentication and the checking, extract the key, obtain the data of each
state of each party in the
e-commerce transaction according to the key, ensure the validity of the data
image electronic
certificate by the digital signature, conduct the data checking on the image
that is embedded with
the key to prevent the data from being tampered with, and improves the
security of the data of each
state in the e-commerce transaction.
Figure 2 is a flow chart of the data recording method in one sample. Figure 2
depicts the
premise of the data authentication method, at first, record the data, and
conduct the data key
encryption and the digital signature to generate data image electronic
certificates. As shown in
Figure 2, the data recording method includes:
Step 202, and collects the data of each state of the parties.
Specifically, the data of each state in the e-commerce transaction may include
warehouse
information, order generation information, shipping information, receipt
information, end of
transaction, and ownership of the goods. Among them, the warehouse information
can include the
items belong to the warehouse, for an example, No. 1 Warehouse, ABC Building,
Futian District,
Shenzhen. The order information can include order generation time, item
information in order, order
number, and consignee information. The consignee information may include the
consignee's name,
6
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
the consignee's address, and the consignee's contact details. The shipping
information may include
the name of the logistics company, the invoice number, the delivery time, and
the consignee
information. The consignor information may include the name of the consignor,
the address of the
consignor, and the contact information of the consignor. The receipt
information may include
receipt information, and receipt time. The signer information can sign the
recipient name, picture,
ID information and so on.
The data of each state of the each party in the transaction can be generated
in all aspects and
stored on the cloud database server.
Step 204 generates an image based on the collected data.
Step 206 obtains the key of the data.
In one example, the step of obtaining the key of the data comprises:
generating the key of the
data using the order number; or generating the key of the data using the order
number and the
system clock.
Specifically, the key of the data is generated using the order number, and the
key of the data
can be the same as the order number. Using the order number and the system
clock to generate the
data key, you can obtain the MD5 value after calculating the order number and
the system clock to
generate the corresponding key. The key can also be generated using the LTUID
algorithm, which is
a number generated on a machine that guarantees that all machines in the same
space are unique.
The key can be represented by 8-bit, 16-bit, 32-bit, 64-bit, and so on. Using
the order number or
order number and the system to generate data key, simple and convenient, and
high security.
In Step 208, the collected data is stored corresponding to the key of the
data.
Specifically, the collected data and the data key are stored in the cloud
database server
together.
Step 210, embedding the key in the image.
In one example, the step of embedding the key in the image comprises adding
the key to the
binary code of the image.
Specifically, the key is a character that embeds the key in the binary code of
the image, and the
specific typing location may be at the head of the image binary code, either
in the middle or in the
tail, as long as the original image file is not destroyed.
In Step 212, an image that is embedded into the key is stored.
In Step 214, the data of the embedded key is digitally signed to generate a
data image
electronic certificate.
Specifically, a data signature electronic certificate is generated by
digitally signing the
embedded image with a digital certificate provided in advance. Digital
signatures are many ways,
through RSA, ECC and other algorithms to achieve.
7
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
In Step 216, the check data is generated for the image that is embedded into
the key.
The algorithm is used to generate the calibration data for the image embedded
with the key by
using other algorithms such as hash algorithm.
Step 218 stores the check data.
The data recording method, converts the data into the image and embeds the key
of the data
into the image, digital signature is performed on the image having the
embedded key to generate the
data image electronic certificate, it is not easy to tamper with the generated
image and the data
image electronic certificate, the data and the key are correspondingly stored,
and the image having
the embedded key and the check data are stored separately, not easily obtained
at the same time,
subject to multiple instances of security protection, and highly secure. The
data of each state of each
party in the e-commerce transaction generates an image, and the transaction
data of each stage is
relatively fixed, which ensure the continuity and integrity of the data. The
generated data image
electronic certificate can be circulated in various electronic devices,
through the background
authentication system to identify its authenticity, after identifying the
authenticity, and then
extracted the important transaction state data from the image.
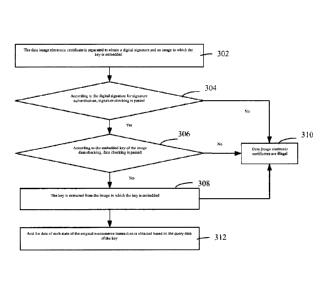
Figure 3 is a flow chart of the data authentication method in one example; As
shown in Figure
3, the data authentication method is applied to the authentication of the data
image electronic
certificate (including Figure 2) after digital signature and key encryption,
including:
In Step 302, the data image electronic certificate is subjected to a
separation process to obtain a
digital signature and an image in which the key is embedded.
Step 304, the signature identity authentication is performed according to the
digital signature,
and whether or not the signature authentication is passed. If so, Step 306 is
executed. If not, Step
308 is performed. Specifically, the identity data of the signer in the
separated digital signature is
compared with the identity data of the signer stored on the cloud data server.
If the authentication is
the same; the identity authentication fails and the authentication fails. If
the authentication fails, it
indicates that the data image electronic certificate is illegal.
In Step 306, data checking is performed based on the image in which the key is
embedded,
whether or not the data checking is passed, and if so, Step 310 is performed.
If not, Step 308 is
performed.
In the present sample, the Step 306 includes generating a check data based on
the separated
image in which the key is embedded and comparing the generated checking data
with the stored
checking data, and if the, the data is checked; if different, the data
checking fails.
In one sample, the step of performing data checking on the basis of the image
in which the key
is embedded comprises processing an image in which the key is embedded by a
hash function to
form an MD5 code which is searched from the cloud database server according to
the MD5 code; if
8
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
the search succeeded, then that the image has not been tampered with; if not
found, then that the
image was tampered with.
In another sample, the step of performing data checking based on the image
embedded in the
key includes obtaining a key from the image in which the key is embedded,
searching from the
cloud database server for the key corresponding to the key MD5 code, the hash
function of the
image processing to form an MD5 code, the key corresponding to the MD5 code
and the formation
of MD5 code comparison; if the same, that the image has not been tampered
with; if different, that
the image was tampered with.
In Step 308, the data image electronic certificate is illegal.
Specifically, the data image electronic certificate illegal indicates that the
data image electronic
certificate may be tampered with.
In Step 310, the key is extracted from the image in which the key is embedded.
If the data checking fails, it indicates that the data image electronic
certificate is illegal.
Step 312, the data of each state of each party in the e-commerce transaction
is obtained based
on the key query data. The data authentication method obtains the digital
signature and the image in
which the key is embedded by separating the data image electronic certificate,
performs the identity
authentication by the digital signature, performs data checking on the image
of the embedded key,
and passes the authentication and checking, extracts the key, obtains the data
of each state of each
party in the e-commerce transaction according to the key, ensures the validity
of the data image
electronic certificate by the digital signature, and checks the data of the
embedded key to prevent
the data from being tampered with, and improve the security of the data of
each state in the
e-commerce transaction.
Figure 4 is a block diagram showing the structure of the data authentication
device in one
example. As shown in Figure 4, a data authentication device for authentication
of a digital image
and a key-encrypted data image electronic certificate including a separation
module 410, an
authentication module 420, a data checking module 430, an extraction module
440, and a query
module 450. Among them:
The separation module 410 is used to separate the data image electronic
certificate to obtain a
digital signature and an image in which the key is embedded.
The identity authentication module 420 is used for signature authentication
based on the digital
signature.
The data checking module 430 is used to perform data checking according to an
image in
which the key is embedded after the signature authentication is passed.
In one sample, the data checking module 430 is further configured to generate
check data
based on the separated image of the embedded key and to compare the generated
check data with
9
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
the previously stored check data; if the same, the data checking is passed; if
it is different, the data
checking fails.
In another sample, the data checking module 430 is further configured to
process an image
embedded in a key by a hash function to form an MD5 code that is searched from
the cloud
database server according to the MD5 code, and if it can be searched, the
image has not been
tampered with; if not then the image was tampered with.
In another sample, the data checking module 430 is further configured to
obtain a key from an
image in which the key is embedded, and the MD5 code corresponding to the key
is searched from
the cloud database server based on the key, and the image is processed by the
hash function to form
an MD5 code, and the MD5 code corresponding to the key is compared with the
MD5 code formed.
If it is the same, the image is not tampered with; if not, the image is
considered to be tampered with.
The extraction module 440 is used to extract the key from the image in which
the key is
embedded after the data checking is passed.
The query module 450 is used to query the data based on the key to obtain data
of each state of
the parties.
The data authentication device separates the digital signature and the image
in which the key is
embedded by the data image electronic certificate, performs identity
authentication by the digital
signature, performs data checking on the image of the embedded key, and passes
the authentication
and checking, Extracting the key, obtaining the data of each state of the
original electric business
transaction according to the key, ensuring the validity of the data image
electronic certificate by the
digital signature, and verifying the data of the embedded key image to prevent
the data from being
tampered with , Improve the security of the data of each state in the e-
commerce transaction.
Figure 5 is a block diagram showing the structure of the data authentication
device in one
example. As shown in Figure 5, a data authentication device includes a
separation module 410, an
identity authentication module 420, a data checking module 430, an extraction
module 440, a query
module 450, and also includes a generation module 460. Among them:
The generation module 460 is used to generate a data image electronic
certificate.
Figure 6 is a block diagram showing the internal structure of the module in
one sample. As
shown in Figure 6, the generation module 460 includes a collection unit 610,
an image generation
unit 620, a key generation unit 630, an embedding unit 640, a check generation
unit 650, a storage
unit 660, and a digital signature unit 670.
The collection module 610 is used to collect the data of the each state of
each party in the
e-commerce transactions.
Specifically, the data of each state in the e-commerce transaction may include
warehouse
information, order generation information, shipping information, receipt
information, end
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
transaction, and ownership of the goods. Among them, the warehouse information
can include the
items belong to the warehouse, for an example, No. 1 Warehouse, ABC Building,
Futian District,
Shenzhen. The order information can include order generation time, item
information in order, order
number, and consignee information. The consignee information may include the
consignee's name,
the consignee's address, and the consignee's contact details. The shipping
information may include
the name of the logistics company, the delivery time, and the consignor
information. The consignor
information may include the name of the consignor, the address of the
consignor, and the contact
information of the consignor. The receipt information may include receipt
information, and receipt
time. The signer information can sign the recipient name, picture, ID
information and so on.
The image generation unit 620 is configured to generate the image based on the
collected data.
The key acquisition unit 630 generates a key for the data.
In one example, the key acquisition unit 630 is also used to generate the key
for the data using
the order number, or to generate the key of the data using the order number
and the system clock.
Specifically, the key of the data is generated using the order number, and the
key of the data
can be the same as the order number. Using the order number and the system
clock to generate the
data key, you can obtain the MD5 value after calculating the order number and
the system clock to
generate the corresponding key. The key can also be generated using the UUID
algorithm, which is
a number generated on a machine that guarantees that all machines in the same
space are unique.
The key can be represented by 8-bit, 16-bit, 32-bit, 64-bit, and so on. Using
the order number or
order number and the system to generate data key, simple and convenient, and
high security.
The embedding unit 640 is used to embed the key in the image.
In one example, the embedding unit 640 is also used to add the key to the
binary code of the
image. Specifically, the key is a string in which the key can be embedded in
the binary code of the
image, and the specific typing position may be at the head of the image binary
code, either in the
middle or in the tail, as long as the original image file is not destroyed.
The checking generation unit 650 is used to generate the check data for the
image that is
embedded into the key. The algorithm is used to generate the calibration data
for the image
embedded with the key by using other algorithms such as hash algorithm.
The store unit 660 stores the data and the key correspondingly, and stores the
check data and
the image that is embedded into the key.
The digital signature unit 670 is used for digitally signing the embedded
image to generate the
data image electronic certificate. Specifically, the data signature electronic
certificate is generated
by digitally signing the embedded image with the digital certificate provided
in advance. There are
many digital signature algorithms, such as RSA, ECC and other algorithms. The
data authentication
device uses the data to generate the image, embeds the data key into the
image, and conducts digital
11
CA 02986837 2017-11-22
WO 2016/172986 PCT/CN2015/078148
signature for the image embedded with the key to generate the data image
electronic certificate; the
generated image and the data image electronic certificate are not easy to be
tampered with, the
security degree is high, each state in the e-commerce transaction is converted
into the image, and
the image generated by the original transaction data will not be changed all
the time, which ensures
the consistence and integrity of the data; the digital signature and the image
embedded with the key
are obtained by separating the data image electronic certificate; the identity
authentication is
conducted by the digital signature, and the image embedded with key is
conducted with the data
checking; after the identity authentication and checking are passed, it is
required to extract the key,
data of each state in the original e-commerce transaction is obtained as per
the key, the validity of
the data image electronic certificate is ensured via the identity
authentication, the data checking is
conducted to ensure the data being tampered, and security of the data of each
state in the
e-commerce transaction is improved.
Figure 7 is an internal schematic diagram of the server in one example. As
shown in Figure 7,
the server includes a processor, a storage medium, a memory, and a network
interface connected via
a system bus. Wherein the storage medium of the server stores operating
system, database and data
authentication device for storing data, keys, images and check data in the e-
commerce transaction,
and the data authentication device for realizing a kind of data authentication
method to the server.
The processor of the server is used to provide calculation and control
capabilities to support the
operation of the entire server. The memory of the server provides an
environment for the operation
of data authentication device in the storage medium. The display screen of the
server may be a
liquid crystal display screen or an electronic ink display screen. The input
device may be a touch
layer covered on the display screen or a button, a trackball or a touch panel
provided on the terminal
housing, or an external keyboard, touch pad or mouse. The network interface of
the server is used to
communicate with an external terminal over a network connection, such as a
request sent by the
receiving terminal and to return data to the terminal. The server can be
implemented as a separate
server or a server cluster of multiple servers.
The ordinary technicians in the field that can understand and implement all or
part of the
processes in the above mentioned method of the examples which can be
accomplished by means of
a computer program that can be stored in a computer-readable storage medium.
The program may,
when executed, include flows of all examples as described above. Among them,
the storage medium
can be a magnetic disk, an optical disk, a read-only memory (ROM) or a random
access memory
(RAM), etc.
The above-described examples show only a few methods of execution of the
present invention,
and its descriptions are comparatively specific and detailed, however, it can
not to be construed as a
limitation of the scope of the invention patent. It should be noted that
various modifications and
12
CA 02986837 2017-11-22
WO 2016/172986
PCT/CN2015/078148
improvements can be made by those skilled in the field without departing from
the inventive
concept, which belong to the protection scope of the present invention.
Accordingly, the protection
scope of patent of the present invention should be measured by the appended
claims.
13