Note: Descriptions are shown in the official language in which they were submitted.
DETECTING LOCATION WITHIN A NETWORK
BACKGROUND
1. Field of the Invention
[001] This disclosure is related to the field of object detection, and more
particularly to
systems and methods for detecting the presence of a biological mass within a
wireless
communications network.
2. Description of the Related Art
[002] Tracking objects may be done using a number of techniques. For example,
a moving
transceiver may be attached to the object. Examples of such systems include
global positioning
location systems such as GPS, which use orbiting satellites to communicate
with terrestrial
transceivers. However, such systems are generally less effective indoors,
where satellite signals
may be blocked, reducing accuracy. Thus, other technologies are often used
indoors, such as
BluetoothTM beacons, which calculate the location of a roaming or unknown
transceiver. The
roaming transceiver acts as a fiducial element.
[003] These systems have several disadvantages, among them that the object
tracked must
include a transceiver. In certain applications, the object to be tracked will
have no such fiducial
element, or will actively disable any such element, such as an intruder in a
home.
[004] Other technologies exist which can also detect and track objects without
the use of a
fiducial element. For example, radar is a venerable object-detection system
that uses RF waves
to determine the range, angle, or velocity of objects, including aircraft,
ships, spacecraft, guided
missiles, motor vehicles, weather foi mations, and terrain. Radar operates
by transmitting
electromagnetic waves, generally using waves in the radio frequency ("RF") of
the
electromagnetic spectrum, which reflect from any object in their path. A
receiver, typically part
of the same system as the transmitter, receives and processes these reflected
waves to determine
properties of the objects. Other systems similar to radar, using other parts
of the
1
7615577
Date Recue/Date Received 2022-07-04
electromagnetic spectrum, may also be used in similar fashion, such as
ultraviolet, visible, or
near-infrared light from lasers.
[005] Radar technologies do not require a fiducial element, but have other
shortcomings. For
example, radar signals are susceptible to signal noise, or random variations
in the signal caused
by internal electrical components, as well as noise and interference from
external sources, such
as the natural background radiation. Radar is also vulnerable to external
interference sources,
such as intervening objects blocking the beam path and can be deceived by
objects of particular
size, shape, and orientation.
2
7615577
Date Recue/Date Received 2022-07-04
SUMMARY
[006] The following is a summary of the invention in order to provide a basic
understanding
of some aspects of the invention. This summary is not intended to identify key
or critical
elements of the invention or to delineate the scope of the invention. The sole
purpose of this
section is to present some concepts of the invention in a simplified form as a
prelude to the
more detailed description that is presented later.
[007] Because of these and other problems in the art, there is described
herein, among other
things, is a method for detecting the presence of a human comprising:
providing a first
transceiver disposed at a first position within a detection area; providing a
second transceiver
disposed at a second location within the detection area; a computer server
communicably
coupled to the first transceiver; the first transceiver receiving a first set
of wireless signals from
the second transceiver via the wireless communications network; the computer
server receiving
a first set of signal data from the first transceiver, the first set of signal
data comprising data
about the properties of the first set of wireless signals, the property data
being generated as part
of ordinary operation of the first transceiver on the communication network;
the computer
server creating a baseline signal profile for communications from the second
transceiver to the
first transceiver, the baseline signal profile being based at least in part on
the wireless signal
properties in the received first set of signal data, and representing
characteristics of wireless
transmissions from the second transceiver to the first transceiver when no
human is present in
the detection area; the first transceiver receiving a second set of wireless
signals from the
second transceiver via the wireless communications network; the computer
server receiving a
second set of signal data from the first transceiver, the second set of signal
data comprising
data about the properties of the second set of wireless signals, the property
data being generated
as part of ordinary operation of the first transceiver on the communication
network; and the
computer server determining whether a human is present within the detection
area, the
3
7615577
Date Recue/Date Received 2022-07-04
determination based at least in part on a comparison of the wireless signal
properties in the
received second set of wireless signal data to the baseline signal profile.
[008] In an embodiment of the method, the first set of signal properties
comprise wireless
network signal protocol properties deteiiiiined by the first transceiver.
[009] In another embodiment of the method, the wireless network signal
protocol properties
are selected from the group consisting of: received signal strength, latency,
and bit error rate.
[010] In another embodiment of the method, the method further comprises:
providing a third
transceiver disposed at a third location within the detection area; the first
transceiver receiving
a third set of wireless signals from the third transceiver via the wireless
communications
network; the computer server receiving a third set of signal data from the
first transceiver, the
third set of signal data comprising data about the properties of the third set
of wireless signals,
the property data being generated as part of ordinary operation of the first
transceiver on the
communication network; the computer server creating a second baseline signal
profile for
communications from the third transceiver to the first transceiver, the second
baseline signal
profile being based at least in part on the wireless signal properties in the
received third set of
signal data, and representing characteristics of wireless transmissions from
the third transceiver
to the first transceiver when no human is present in the detection area; the
first transceiver
receiving a fourth set of wireless signals from the third transceiver via the
wireless
communications network; the computer server receiving a fourth set of signal
data from the
first transceiver, the fourth set of signal data comprising data about the
properties of the fourth
set of wireless signals, the property data being generated as part of ordinary
operation of the
first transceiver on the communication network; and in the determining step,
the computer
server determining whether a human is present within the detection area based
at least in part
on a comparison of the wireless signal properties in the received fourth set
of wireless signal
data to the second baseline signal profile.
4
7615577
Date Recue/Date Received 2022-07-04
[011] In another embodiment of the method, the determining step applies
statistical methods
to the second set of wireless signal data to determine the presence of a
human.
[012] In another embodiment of the method, the method further comprises: the
computer
server continuously determining the presence or absence of a human within the
detection area,
the determination based at least in part on a comparison of the baseline
signal profile to signal
data comprising data about the properties of the first set of wireless signals
received
continuously at the computer server from the first transceiver; and the
computer continuously
updating the baseline signal profile based on the continuously received signal
data when the
continuously received signal data indicates the absence of a human in the
detection area.
[013] In another embodiment of the method, the method further comprises: the
computer
server determining the number of humans is present within the detection area,
the determination
based at least in part on a comparison of the received second set of signal
properties to the
baseline signal profile.
[014] In another embodiment of the method, the method further comprises: the
computer
server determining the location of one or more humans within the detection
area, the
determination based at least in part on a comparison of the received second
set of signal
properties to the baseline signal profile.
[015] In another embodiment of the method, the method further comprises: the
computer
server being operatively coupled to a second system; and only after the
computer server detects
the presence of a human in the detection area, the computer operates the
second system.
[016] In another embodiment of the method, the detection network and the
second system are
configured to communicate using the same communication protocol.
[017] In another embodiment of the method, the second system is an electrical
system.
[018] In another embodiment of the method, the second system is a lighting
system.
7615577
Date Recue/Date Received 2022-07-04
[019] In another embodiment of the method, the second system is a heating,
venting, and
cooling (HVAC) system.
[020] In another embodiment of the method, the second system is a security
system.
[021] In another embodiment of the method, the second system is an industrial
automation
system.
[022] In another embodiment of the method, the wireless communication protocol
is selected
from the group consisting of: BluetoothTM, BluetoothTM Low Energy, ANT, ANT+,
WiFi,
Zigbee, Thread, and Z-Wave.
[023] In another embodiment of the method, the wireless communication network
has a
carrier frequency in the range of 850 MHz and 17.5 GHz inclusive.
[024] In another embodiment of the method, the determination whether a human
is present
within the detection area is adjusted based on machine learning comprising:
determining a first
sample location of a human having a fiducial element in the detection area,
the first sample
location being determined based upon detecting the fiducial element;
determining a second
sample location of the human in the detection area, the second sample location
being
determined based at least in part on a comparison of the received second set
of signal data to
the baseline signal profile not utilizing the fiducial element; comparing the
first sample location
and the second sample location; and adjusting the determination step based on
non-fiducial
element location to improve the location calculating capabilities of the
system, the adjusting
based upon the comparing step.
[025] In another embodiment of the method, the determination whether a human
is present
within the detection area is adjusted based on machine learning comprising:
determining based
on user input or action that a human was present in an area when the sample
signal properties
correspond at least in part with baseline signal properties of an empty space,
modifying, at least
in part, the baseline signal properties for an empty space; modifying, at
least in part, the signal
6
7615577
Date Recue/Date Received 2022-07-04
properties associated with an occupied space; and adjusting the method for
comparing sample
signal properties to the baseline and other comparative signal properties to
improve the
accuracy of the system over time.
[026] In an embodiment of the system, the user input or action which provides
presence data
is provided directly to the system in some form including, but not limited to,
physical switches,
smartphone input, or auditory cues.
[027] In an embodiment of the system, the user input or action which provides
presence data
is provided indirectly to the system in some form, such as deliberately
changing the signal
profile to counteract a decision being taken by the system, such as providing
such a change
during a dimming phase in a lighting system.
[028] In another embodiment of the method, the method further comprises: the
computer
server storing a plurality of historical data records indicative of whether a
human was present
in the detection area over a period of time, each of the historical data
records comprising an
indication of the number of humans detected in the detected area and the date
and time of when
the number of humans was detected in the detection area; and the computer
server making the
historical data records available to one or more external computer systems via
an interface.
[029] Also described herein, among other things, is a method for detecting the
presence of a
human comprising: providing a first transceiver disposed at a first position
within a detection
area; providing a second transceiver disposed at a second location within the
detection area;
providing a computer server communicably coupled to the first transceiver;
providing a first
external system operatively coupled to the computer server; providing a second
external system
operatively coupled to the computer server; the computer server receiving from
the first
transceiver a set of baseline signal data comprising property data about the
signal properties of
a first set of wireless signals received by the first transceiver from the
second transceiver when
no human is present in the detection area, the property data being generated
by the first
7
7615577
Date Recue/Date Received 2022-07-04
transceiver as part of ordinary operation of the first transceiver on the
communication network;
the computer server creating a baseline signal profile for communications from
the second
transceiver to the first transceiver when no human is present in the detection
area, the baseline
signal profile being based at least in part on the property data representing
characteristics of
wireless transmissions from the second transceiver to the first transceiver
when no human is
present in the detection area; the computer server receiving from the first
transceiver a first set
of sample baseline signal data comprising property data about the signal
properties of a second
set of wireless signals received by the first transceiver from the second
transceiver when a
human is present in the detection area, the property data being generated by
the first transceiver
as part of ordinary operation of the first transceiver on the communication
network; the
computer server creating a first sample baseline signal profile for
communications from the
second transceiver to the first transceiver when a human is present in the
detection area, the
first sample baseline signal profile being based at least in part on the
property data in the first
set of sample baseline signal data, representing characteristics of wireless
transmissions from
the second transceiver to the first transceiver when a human is present in the
detection area; the
computer server receiving from the first transceiver a second set of sample
baseline signal data
comprising property data about the signal properties of a third set of
wireless signals received
by the first transceiver from the second transceiver when a human is present
in the detection
area, the property data being generated by the first transceiver as part of
ordinary operation of
the first transceiver on the communication network; the computer server
creating a second
sample baseline signal profile for communications from the second transceiver
to the first
transceiver when a human is present in the detection area, the second sample
baseline signal
profile being based at least in part on the property data in the second set of
sample baseline
signal data, representing characteristics of wireless transmissions from the
second transceiver
to the first transceiver when a human is present in the detection area; the
computer server
8
7615577
Date Recue/Date Received 2022-07-04
receiving from the first transceiver a third set of sample baseline signal
data comprising
property data about the signal properties of a fourth set of wireless signals
received by the first
transceiver from the second transceiver when a human is present in the
detection area, the
property data being generated by the first transceiver as part of ordinary
operation of the first
transceiver on the communication network; the computer server determining to
operate the first
external system based upon the computer server determining that the property
data in the third
set of sample baseline signal data corresponds to the first sample baseline
signal profile; the
computer server determining not to operate the second external system based
upon the
computer server determining that the property data in the third set of sample
baseline signal
data does not correspond to the second sample baseline signal profile.
[030] In an embodiment of the method, the determination to operate the first
external system
and the determination not to operate the second external system is adjusted
based on machine
learning comprising: determining a first sample location of a human having a
fiducial element
in the detection area, the first sample location being determined based upon
detecting the
fiducial element; determining a second sample location of the human in the
detection area, the
second sample location being determined based at least in part on a comparison
of the received
second set of signal data to the baseline signal profile not utilizing the
fiducial element;
comparing the first sample location and the second sample location; and
adjusting the
determination steps based on non-fiducial element location to improve the
location calculating
capabilities of the system, the adjusting based upon the comparing step.
[031] In another embodiment of the method, the determination to operate the
first external
system and the determination not to operate the second external system is
adjusted based on
machine learning comprising: determining a first sample location of a human in
the detection
area using inference, the first sample location being determined based upon
detecting the
human interacting with the system in some known way; determining a second
sample location
9
7615577
Date Recue/Date Received 2022-07-04
of the human in the detection area, the second sample location being
determined based at least
in part on a comparison of the received second set of signal data to the
baseline signal profile
not utilizing the inferred location; comparing the first sample location and
the second sample
location; and adjusting the determination steps based on inferred location to
improve the
location calculating capabilities of the system, the adjusting based upon the
comparing step.
[032] In another embodiment of the method, the property data about the
wireless signals
comprises data about signal properties selected from the group consisting of:
received signal
strength, latency, and bit error rate.
[033] In another embodiment of the method, the computer server creates the
first sample
baseline signal profile by applying statistical methods to the first set of
sample baseline signal
data, and the computer server creates the second sample baseline signal
profile by applying
statistical methods to the second set of sample baseline signal data.
[034] In another embodiment of the method, the method further comprises: the
computer
server receiving from the first transceiver additional sets of baseline signal
data comprising
property data about the signal properties of a second set of wireless signals
received by the first
transceiver from the second transceiver, the property data being generated by
the first
transceiver as part of ordinary operation of the first transceiver on the
communication network
and the computer server updating the baseline signal profile based on the
continuously received
additional sets of baseline signal data when the continuously received sets of
baseline signal
data indicate the absence of a human in the detection area.
[035] In another embodiment of the method, the method further comprises: the
computer
server receiving from the first transceiver a set of signal data comprising
property data about
the signal properties of a second set of wireless signals received by the
first transceiver from
the second transceiver when one or more humans are present in the detection
area, the property
data being generated by the first transceiver as part of ordinary operation of
the first transceiver
7615577
Date Recue/Date Received 2022-07-04
on the communication network; the computer server determining the quantity of
humans
present in the detection area based at least in part on a comparison of the
set of signal data to
the baseline signal profile.
[036] In another embodiment of the method, the method further comprises: the
computer
server determining a location of each of the one or more humans present in the
detection area,
the detemiination based at least in part on a comparison of the set of signal
data to the baseline
signal profile.
[037] In another embodiment of the method, when a human is present in the
detection area,
the computer server determines that a human is present in the detection area
and operates the
first external system even if the property data in the third set of sample
baseline signal data
corresponds to the second sample baseline signal profile.
[038] In another embodiment of the method, when a human is present in the
detection area,
the computer server determines that a human is present in the detection area
and operates the
second external system only if the property data in the third set of sample
baseline signal data
corresponds to the second sample baseline signal profile.
[039] In another embodiment of the method, the wireless communication network
has a
carrier frequency in the range of 850 MHz and 17.5 GHz inclusive.
[040] In another embodiment of the method, the method further comprises: the
computer
server storing a plurality of historical data records indicative of whether a
human was present
in the detection area over a period of time, each of the historical data
records comprising an
indication of the number of humans detected in the detected area and the date
and time of when
the number of humans was detected in the detection area; and the computer
server making the
historical data records available to one or more external computer systems via
an interface.
11
7615577
Date Recue/Date Received 2022-07-04
BRIEF DESCRIPTION OF THE DRAWINGS
[041] FIG. 1 is a schematic diagram of an embodiment of a system according to
the present
disclosure.
[042] FIG. 2 is a flow chart of an embodiment of a method according to the
present disclosure.
[043] FIG. 3A depicts a schematic diagram of a system for change detection in
a detection
network over time according to the present disclosure.
[044] FIG. 3B depicts a schematic diagram of a system for detecting changes in
locations of
humans in a detection network over time according to the present disclosure.
12
7615577
Date Recue/Date Received 2022-07-04
DESCRIPTION OF THE PREFERRED EMBODIMENT
[045] The following detailed description and disclosure illustrates by way of
example and not
by way of limitation. This description will clearly enable one skilled in the
art to make and use
the disclosed systems and methods, and describes several embodiments,
adaptations,
variations, alternatives and uses of the disclosed systems and methods. As
various changes
could be made in the above constructions without departing from the scope of
the disclosures,
it is intended that all matter contained in the description or shown in the
accompanying
drawings shall be interpreted as illustrative and not in a limiting sense.
[046] Generally speaking, described herein, among other things, are systems
and methods for
detecting the presence of a body in a network without fiducial elements.
Generally speaking,
the systems and methods described herein use signal absorption, and signal
forward scatter and
reflected backscatter of the RF communication caused by the presence of a
biological mass in
a communications network, generally a mesh network.
[047] Throughout this disclosure, the term "computer" describes hardware which
generally
implements functionality provided by digital computing technology,
particularly computing
functionality associated with microprocessors. The term "computer" is not
intended to be
limited to any specific type of computing device, but it is intended to be
inclusive of all
computational devices including, but not limited to: processing devices,
microprocessors,
personal computers, desktop computers, laptop computers, workstations,
terminals, servers,
clients, portable computers, handheld computers, smart phones, tablet
computers, mobile
devices, server farms, hardware appliances, minicomputers, mainframe
computers, video game
consoles, handheld video game products, and wearable computing devices
including but not
limited to eyewear, wrist-wear, pendants, and clip-on devices.
[048] As used herein, a "computer" is necessarily an abstraction of the
functionality provided
by a single computer device outfitted with the hardware and accessories
typical of computers
13
7615577
Date Recue/Date Received 2022-07-04
in a particular role. By way of example and not limitation, the term
"computer" in reference to
a laptop computer would be understood by one of ordinary skill in the art to
include the
functionality provided by pointer-based input devices, such as a mouse or
track pad, whereas
the term "computer" used in reference to an enterprise-class server would be
understood by
one of ordinary skill in the art to include the functionality provided by
redundant systems, such
as RAID drives and dual power supplies.
[049] It is also well known to those of ordinary skill in the art that the
functionality of a single
computer may be distributed across a number of individual machines. This
distribution may be
functional, as where specific machines perform specific tasks; or, balanced,
as where each
machine is capable of performing most or all functions of any other machine
and is assigned
tasks based on its available resources at a point in time. Thus, the term
"computer" as used
herein, can refer to a single, standalone, self-contained device or to a
plurality of machines
working together or independently, including without limitation: a network
server farm,
"cloud" computing system, software-as-a-service, or other distributed or
collaborative
computer networks.
[050] Those of ordinary skill in the art also appreciate that some devices
which are not
conventionally thought of as "computers" nevertheless exhibit the
characteristics of a
"computer" in certain contexts. Where such a device is performing the
functions of a
"computer" as described herein, the term "computer" includes such devices to
that extent.
Devices of this type include but are not limited to: network hardware, print
servers, file servers,
NAS and SAN, load balancers, and any other hardware capable of interacting
with the systems
and methods described herein in the matter of a conventional "computer."
[051] Throughout this disclosure, the term "software" refers to code objects,
program logic,
command structures, data structures and definitions, source code, executable
and/or binary
files, machine code, object code, compiled libraries, implementations,
algorithms, libraries, or
14
7615577
Date Recue/Date Received 2022-07-04
any instruction or set of instructions capable of being executed by a computer
processor, or
capable of being converted into a form capable of being executed by a computer
processor,
including without limitation virtual processors, or by the use of run-time
environments, virtual
machines, and/or interpreters. Those of ordinary skill in the art recognize
that software can be
wired or embedded into hardware, including without limitation onto a
microchip, and still be
considered "software" within the meaning of this disclosure. For purposes of
this disclosure,
software includes without limitation: instructions stored or storable in RAM,
ROM, flash
memory BIOS, CMOS, mother and daughter board circuitry, hardware controllers,
USB
controllers or hosts, peripheral devices and controllers, video cards, audio
controllers, network
cards, BluetoothTM and other wireless communication devices, virtual memory,
storage devices
and associated controllers, firmware, and device drivers. The systems and
methods described
here are contemplated to use computers and computer software typically stored
in a computer-
or machine-readable storage medium or memory.
[052] Throughout this disclosure, terms used herein to describe or reference
media holding
software, including without limitation terms such as "media," "storage media,"
and "memory,"
may include or exclude transitory media such as signals and carrier waves.
[053] Throughout this disclosure, the term "network" generally refers to a
voice, data, or other
telecommunications network over which computers communicate with each other.
The term
"server" generally refers to a computer providing a service over a network,
and a "client"
generally refers to a computer accessing or using a service provided by a
server over a network.
Those having ordinary skill in the art will appreciate that the terms "server"
and "client" may
refer to hardware, software, and/or a combination of hardware and software,
depending on
context. Those having ordinary skill in the art will further appreciate that
the teinis "server"
and "client" may refer to endpoints of a network communication or network
connection,
including but not necessarily limited to a network socket connection. Those
having ordinary
7615577
Date Recue/Date Received 2022-07-04
skill in the art will further appreciate that a "server" may comprise a
plurality of software and/or
hardware servers delivering a service or set of services. Those having
ordinary skill in the art
will further appreciate that the term "host" may, in noun form, refer to an
endpoint of a network
communication or network (e.g., "a remote host"), or may, in verb form, refer
to a server
providing a service over a network ("hosts a website"), or an access point for
a service over a
network.
[054] Throughout this disclosure, the term "real time" refers to software
operating within
operational deadlines for a given event to commence or complete, or for a
given module,
software, or system to respond, and generally invokes that the response or
performance time
is, in ordinary user perception and considered the technological context,
effectively generally
cotemporaneous with a reference event. Those of ordinary skill in the art
understand that "real
time" does not literally mean the system processes input and/or responds
instantaneously, but
rather that the system processes and/or responds rapidly enough that the
processing or response
time is within the general human perception of the passage of real time in the
operational
context of the program. Those of ordinary skill in the art understand that,
where the operational
context is a graphical user interface, "real time" normally implies a response
time of no more
than one second of actual time, with milliseconds or microseconds being
preferable. However,
those of ordinary skill in the art also understand that, under other
operational contexts, a system
operating in "real time" may exhibit delays longer than one second,
particularly where network
operations are involved.
[055] Throughout this disclosure, the term "transmitter" refers to equipment,
or a set of
equipment, having the hardware, circuitry, and/or software to generate and
transmit
electromagnetic waves carrying messages, signals, data, or other information.
A transmitter
may also comprise the componentry to receive electric signals containing such
messages,
signals, data, or other information, and convert them to such electromagnetic
waves. The term
16
7615577
Date Recue/Date Received 2022-07-04
"receiver" refers to equipment, or a set of equipment, having the hardware,
circuitry, and/or
software to receive such transmitted electromagnetic waves and convert them
into signals,
usually electrical, from which the message, signal, data, or other information
may be extracted.
The term "transceiver" generally refers to a device or system that comprises
both a transmitter
and receiver, such as, but not necessarily limited to, a two-way radio, or
wireless networking
router or access point. For purposes of this disclosure, all three temis
should be understood as
interchangeable unless otherwise indicated; for example, the term
"transmitter" should be
understood to imply the presence of a receiver, and the twit "receiver" should
be understood
to imply the presence of a transmitter.
[056] Throughout this disclosure, the term "detection network" refers to a
wireless network
used in the systems and methods of the present disclosure to detect the
presence of biological
mass interposed within the communications area of the network. A detection
network may use
general networking protocols and standards and may be, but is not necessarily,
a special-
purpose network. That is, while the nodes in the network could be deployed for
the specific
purpose of setting up a wireless detection network according to the present
invention, they need
not be and generally will not be. Ordinary wireless networks established for
other purposes
may be used to implement the systems and methods described herein. In the
preferred
embodiment, the detection network uses a plurality of BluetoothTM Low Energy
nodes, but the
present disclosure is not limited to such nodes. Each node acts as a computer
with an
appropriate transmitter and receiver for communicating over the network. Each
of the
computers provides a unique identifier within the network whenever
transmitting a message
such that a receiving computer is capable of discerning from where the message
originated.
Such message origination information will usually be critical to the
functioning of the invention
as described in this detailed description. The receiving computer then
analyzes the incoming
signal properties, including but not limited to, signal strength, bit error
rate, and message delay.
17
7615577
Date Recue/Date Received 2022-07-04
The detection network may be a mesh network, which means a network topology in
which each
node relays data from the network.
[057] Throughout this disclosure, the term "node" refers to a start point or
endpoint for a
network communication, generally a device having a wireless transceiver and
being a part of a
detection network. Nodes are generally standalone, self-contained networking
devices, such as
wireless routers, wireless access points, short-range beacons, and so forth. A
node may be a
general-purpose device or a special-purpose device configured for use in a
detection network
as described herein. By way of example and not limitation, a node may be a
device having the
wireless transmission capabilities of an off-the-shelf wireless networking
device with the
addition of specialized hardware, circuitry, componentry, or programming for
implementing
the systems and methods described herein; that is, for detecting significant
changes to signal
properties, including but not limited to, signal strength, bit error rate, and
message delay.
Within a detection network, each node can act as both a transmitter of signal
to the network, as
well as a receiver for other nodes to push information. In the preferred
embodiment, the nodes
utilize BluetoothTM Low Energy (BLE) as a wireless networking system.
[058] Throughout this disclosure, the term "continuous" refers to something
happening at an
ongoing basis over time, whether such events are mathematically continuous or
discontinuous.
The generally accepted mathematical definition of "continuous function"
describes a function
which is without holes or jumps, generally described by two-sided limits. The
technology
described herein is based upon disturbances to a telecommunications system, in
which the
transceivers transmit at discrete intervals, and the received raw data is
taken discretely, i.e. at
discrete time intervals. The resulting data is itself may be discrete in that
it captures the
characteristic of the system during a particular observation window (i.e., the
time interval). In
a physical or mathematical sense, this mechanism is essentially a set of
discrete data points in
time, implying a discontinuous function. However, in the context of the
technology, one of
18
7615577
Date Recue/Date Received 2022-07-04
ordinary skill in the art would understand a system exhibiting this type of
behavior to be
"continuous" given that such measurements are taken at an ongoing basis over
time.
[059] The measurable energy density signature of RF signals is impacted by
environmental
absorbers and reflectors. Many biological masses, such as humans, are mostly
water and act as
significant energy absorbers. Other attributes of people such as clothing,
jewelry, internal
organs, etc. all further impact the measurable RF energy density. This is
particularly true where
RF communication devices are transmitting over relatively short distances
(e.g., less than 50
meters), such as BluetoothTM, WiFiTM, 802.15.4 (Zigbee, Thread), and Z-Wave
transceivers. A
human who passes through the physical space of the network will cause signal
absorption and
disruption. Due to relative uniformity in size, density, and mass composition,
human bodies
can cause characteristic signal absorption, scattering, and measurable
reflection. Changes in
signal behavior and/or characteristics are generally referred to herein as
"Artifacts." Such
phenomena are particularly useful in the Industrial, Scientific, and Medical
(ISM) bands of the
RF spectrum, but are generally observable in bands beyond these.
[060] In an RF communication system comprising a transmitter and receiver
separated in
space, signals received by the receiver from a given transmitter are made up
of energy from the
original transmitted message which has arrived at the receiver. Objects
generally in the
transmission path will affect the characteristics of ultimate signal which
arrives at the receiver.
[061] Communication systems are generally designed to handle such issues and
still faithfully
reproduce the message from the transmitter. Since humans generally exist, as
far as RF
communications are impacted, as a mass of water, one such observable
difference between
human presence and absence in a detection network is signal absorption by the
human.
Generally, the closer to the transmitter or receiver, the more significant the
absorption is likely
to be.
19
7615577
Date Recue/Date Received 2022-07-04
[062] Generally, it is envisioned that humans will produce artifacts in a
detection network in
a somewhat predictable manner, which can be detected or identified
programmatically by
detection algorithms. Further, artifacts may be cross correlated across the
network to determine
an estimated position of the object causing the artifact. The accuracy of this
estimation may
vary with the algorithms chosen/constructed, and with the equipment used in
the individual
system.
[063] For each given algorithm which is chosen/constructed, the system may
build such
detections as a combination of a baseline signal profile with no human present
in the detection
area and sample baseline signal data with a human present in the detection
area. New incoming
sample baseline signal data may be compared against both the known sample
baseline signal
data and the baseline signal profile to determine the presence or absence of
humans in a space.
[064] Short-range low power communication networks typically operate using
signals in the
2.4GHz frequency band, which is notable for being well-within the energy
frequencies humans
have been observed to absorb. As indicated, a human body physically interposed
in a detection
network absorbs and/or reflects at least some of the signals transmitted
between and among
nodes. However, other effects may also take place, such as forward and
backward scattering.
Utilizing the collection of data in a detection network without a human
present to establish a
baseline, and examining future elements of said data for statistically
significant differences
typically exhibited by the physical presence of one or more humans, whether or
not the one or
more humans is moving, the detection network makes the determination as to the
presence or
absence of humans within the network.
[065] Depending on the communication network itself, hardware used, and the
human, those
changes may register within the network in different ways and produce
different results;
however, such changes are detectable. This differs from radar technologies in
that detection of
the object does not necessarily rely or depend upon only signal reflection,
but often rather the
7615577
Date Recue/Date Received 2022-07-04
opposite principle ¨ signal absorption ¨ which is detected via measurable
changes in signal
characteristics between a transmitter and receiver in different physical
locations.
[066] By analyzing the change in signal characteristics between nodes within
the network,
the position of a disruptor and ¨ e.g., a human body ¨ can be calculated
relative to the network.
Because the mere presence of the body is sufficient, this system does not
necessarily include a
fiducial element, and it need not rely on motion or movement. Because no
fiducial element is
required, the systems and methods described herein may provide an anonymous
location data
reporting service, allowing for the collection of data concerning traffic,
travel routes, and
occupancy without requiring additional components or devices to be associated
with the bodies
being tracked. Generally speaking, the systems and methods described herein
operate in real
time.
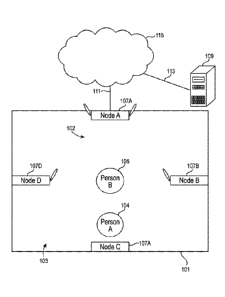
[067] FIG. 1 is a schematic diagram of a system and method according to the
present
disclosure. In the depicted embodiment (101) of FIG. 1, a detection network
(103) comprising
a plurality of nodes (107) is disposed within a physical space (102), such as
a room, corridor,
hallway, or doorway. In the depicted embodiment of FIG. 1, an indoor space
(102) is used, but
the systems and methods described herein are operable in external environments
as well. In the
depicted embodiment, a node (107A) is communicably coupled (111) to a
telecommunications
network (115), such as an intranet, an internet, or the Internet. A server
computer (109) may
also be communicably coupled (113) to the telecommunications network (115) and
thereby
with the connected node (107A). The depicted server (109) comprises
programming
instructions for implementing the systems described herein, and carrying out
the method steps
described herein. However, in an embodiment, the functions performed by the
server may be
performed by one or more nodes (107) having the appropriate
software/programming
instructions, or being appropriately modified.
21
7615577
Date Recue/Date Received 2022-07-04
[068] In the depicted embodiment of FIG. 1, each of the nodes (107) is
communicably
connected with at least one other node (107) in the detection network (103),
and may be
communicably connected to two or more, or all of the other nodes (107) in the
detection
network (103). For example, in a typical wireless network deployment strategy,
a plurality of
wireless access points is placed throughout the physical space (102),
generally to ensure that a
high-quality signal is available everywhere. These nodes (107) collectively
form a detection
network (103) and may transmit data to one another, or may transmit only to a
router or set of
routers. In the depicted embodiment of FIG. 1, node (107A) is a wireless
router, and the other
nodes (107B), (107C) and (107D) are wireless access points. However, this is
just one possible
configuration. Further, it is not necessary that any given node (107) be a
particular type of
wireless device. Any number of nodes (107) may comprise a router, access
point, beacon, or
other type of wireless transceiver. Further, any number of nodes (107) may be
present in an
embodiment, though a minimum of two is preferred. More nodes (107) in a space
(102)
increases the amount of data collected (as described elsewhere herein), thus
improving the
chance that a human is generally interposed between at least two nodes (107),
improving the
location resolution.
[069] In the ordinary course of operation, the nodes (107) frequently send and
receive wireless
transmissions. For example, when a wireless router (107A) receives a data
packet, the wireless
router (107A) typically broadcasts a wireless transmission containing the
packet. This means
that any receivers within the broadcast radius of the router (107A) can
receive the signal,
whether or not intended for them. Likewise, when an access point receives
local data, such data
is likewise broadcast and can be detected by other access points, and the
router. Even when no
user data is actively transmitted on the network, other data is frequently
transmitted. These
other transmissions may include status data, service scans, and data exchange
for functions of
the low-level layers of the network stack.
22
7615577
Date Recue/Date Received 2022-07-04
[070] Thus, each node (107) in a typical detection network (103) receives
transmissions on a
consistent basis and, in a busy network, this effectively may be a continuous
basis. The
detection network (103) may thus be used to calculate the existence and/or
position of a
biological mass (104) or (105) physically interposed within the transmission
range of the
network (103). Because the presence of a human body impacts the
characteristics of signals
transmitted between or among nodes (107) within the network (103), such
presence can be
detected by monitoring for changes in such characteristics. This detection may
also be
performed while the data in the data packets being transmitted and received is
still being
transmitted and received; that is, the detection is incident to ordinary data
exchange between
or among two or more nodes, which continues regardless of the detection.
Specifically, the
wireless network may operate to transfer data between nodes, while
simultaneously using
characteristics of how the data packets incorporating that data have been
impacted by the
presence of an object in the transmission path, to detect and locate the
object.
[071] In the depicted embodiment of FIG. 1, at least one node (107) monitors
the
communication signatures between itself (107) and at least one other node
(107) for statistically
significant changes in signal characteristics even while it awaits, receives,
and/or transmits
communications between itself and other nodes (107). The particular geometry
of the physical
space (102), including the presence and location of fixtures in the physical
environment,
generally does not impact the system because the monitoring is for
statistically significant
change in signal characteristics indicating or evidencing the characteristics
of a human. That
is, a change in signal characteristics is attributable to a change in
absorbers or reflectors, like
human bodies, in the physical environment or communication space covered by
the detection
network (103). The detection of the presence of a human within the detection
network (103)
may be done using statistical analysis methods on the signal, such as using
sensing algorithms,
as described elsewhere herein. Again, this does not require the human to be
associated with a
23
7615577
Date Recue/Date Received 2022-07-04
fiducial element, or in motion. Instead, the detection network (103) detects
that characteristics
of the network communication have changed because a new object (which is
generally a human
object) has been introduced in the communication space and the presence of
that object has
caused a change to the characteristics of the network communications,
typically data packets,
between nodes (107).
[072] To detect a change, generally a baseline of signal characteristics is
developed against
which recently transmitted signals are compared. These characteristics are
derived from typical
wireless communication network diagnostic information. This baseline of signal
characteristics
between nodes (107) is generally established prior to the use of the detection
network (103) as
a detector. This may be done by operating the detection network (103) under
typical or normal
circumstances, that is with the detection network (103) communicating data
packets, with no
significant biological mass interposed in the physical broadcast space of the
detection network
(103). For an amount of time during such operation, signal characteristics
between and/or
among nodes (107) are monitored and collected and stored in a database. In an
embodiment,
the server (109) will receive and store such data, but in an embodiment, one
or more nodes
(107) may comprise hardware systems configured to receive and/or store such
data.
[073] For example, where a node (107) contains special purpose hardware and
programming
for use according to the present disclosure, such node (107) may store its own
signal
characteristic data. Such signal characteristic data may be data relating to
the received energy
characteristic of signals received by a particular node (107) from one or more
other nodes (107).
The baseline data establishes for each node (107) a signature characteristic
profile, which is
essentially a collection of data defining the typical and/or general
characteristics of signals
received by the node (107) under ordinary operating circumstances where there
is no significant
biological mass interposed in the detection network (103). The node (107) may
have one or
more of such profiles for each other node (107) from which it receives data.
24
7615577
Date Recue/Date Received 2022-07-04
[074] In an embodiment, after the baseline signatures have been detected and
collected, the
detection network (103) will generally continue to operate in the same or
similar fashion, but
is now able to detect the presence of a biological mass. This is done by
detecting and collecting
additional signal characteristics, generally in real-time, as the detection
network (103) operates
in a normal mode of transmitting and receiving data packets. These newly
generated real-time
signal characteristic profiles are also generally characteristics of signals
between two particular
nodes (107) in the detection network (103), and thus can be compared to a
corresponding
baseline signal characteristic profile for the same two particular nodes
(107). A statistically
significant difference in certain characteristics between the two profiles may
then be interpreted
as being caused by the presence of a significant biological mass, such as a
human.
[075] The comparison operations may be performed by appropriate hardware in a
given node
(107), or the real-time signal characteristic profiles may be transmitted to a
server (109) for
processing and comparison. In a further embodiment, both are done so that a
copy of the real-
time data is also stored and accessible via the server, effectively providing
a history of signal
characteristic profiles.
[076] This is because, as described herein, a biological mass interposed
within the network
will generally cause at least some signal characteristics between at least two
nodes to change
when a data packet is transmitted which intercepts and/or generally interacts
with the biological
mass. The degree and nature of the change generally will be related to the
nature of the
particular biological mass interposed (e.g., the size, shape, and
composition), and its location
in the network (103). For example, where a housefly flies through the
detection network (103),
the amount of signal change may be so minor as to be indistinguishable from
natural
fluctuations in signal characteristics. However, a larger mass, such as a
human, may cause more
substantial and statistically significant changes in signal characteristics.
7615577
Date Recue/Date Received 2022-07-04
[077] Such changes may not necessarily manifest in all signal characteristic
profiles for the
detection network (103). For example, where the mass is interposed at the edge
of the detection
network (103), the nodes (107) nearest that edge are likely to experience
statistically significant
signal characteristic changes, whereas nodes on the opposing side of the
detection network
(103) (whose signals to each other do not pass through or around the
biological mass), are
likely to experience few or no statistically significant changes. Thus, if the
physical locations
of the nodes (107) are also known, the system can determine not only that a
biological mass is
present in the detection network (103), but calculate an estimate of where it
is located, by
determining which nodes (107) are experiencing changes and calculating the
magnitude of
those changes.
[078] This can be seen in the depicted embodiment of FIG. 1. In FIG. 1,
assuming the
presence of only one human ¨ either A (104) or B (105) ¨ is present at a time
for simplicity, A
(104) would generally have a greater impact on the signal characteristics
between nodes (107C)
and (107A) than between nodes (107A) and (107C). Further, A (104) would also
generally
have a small bidirectional effect on the signal characteristics between nodes
(107B) and
(107D). By contrast, B (105) would have a bidirectional impact on the signal
characteristics
between nodes (107A) and (107C), as well as on the signal characteristics
between nodes
(107B) and (107D).
[079] While all nodes may be communicating with one another, the effects of A
(104) and B
(105) will generally be more negligible on communications where A (104) and/or
B (105) are
not generally in line with the communications path between nodes. For example,
neither person
(104) or (105) is likely to seriously impact transmission between nodes (107A)
and (107B)
because neither person (104) or (105) is in the transmission path between
those nodes.
However, A (104) may have an impact on transmissions between nodes (107C) and
(107D).
26
7615577
Date Recue/Date Received 2022-07-04
[080] It should be noted that the presence or absence of a biological mass
within the
communication area of the detection network (103) will not necessarily result
in any change in
data communication. It is expected that the detection network (103) will
utilize its standard
existing protocols, means, and methods (including all forms of retransmission
and error
checking) to make sure that the data in the data packets being transmitted is
correctly received,
processed and acted upon. In effect, the detection process of the detection
network (103) is
performed in addition to the standard data communication of the detection
network.
[081] It should be recognized from this that the data in the data packets
being communicated
by the nodes (107) in the detection network (103) generally will not be
directly used to detect
the biological mass within the communication area of the detection network
(103). Instead, the
data will simply be data being communicated via the detection network (103)
for any reason
and will often have nothing to do with detection of the biological mass.
Further, while this
disclosure generally contemplates packetized communication in the form of data
packets, in an
alternative embodiment, the data may be continuously communicated in a non-
packetized
form.
[082] In an embodiment, in order to allow the detection network (103) to
detect the presence
or absence of a particular biological mass, the system includes a training
aspect or step. This
aspect may comprise, after the baseline is established, one or more humans are
deliberately
interposed in the network at one or more locations in the network, and one or
more additional
sets of baseline data are collected and stored. This second baseline may be
used for comparison
purposes to improve accuracy in detecting the size, shape, and/or other
characteristics of a
biological mass interposed in the network, and/or for improving the accuracy
of location
determination. Such training may use supervised or unsupervised learning,
and/or may utilize
techniques known to one skilled in the art of machine learning.
27
7615577
Date Recue/Date Received 2022-07-04
[083] In an embodiment, a detection network (103) may use a specialized
protocol comprising
a controlled messaging structure and/or format, which can be controlled from
one node (107)
to another (107), making it simpler and easier to determine from which node
(107) a message
originated, and allowing for control of aspects such as the composition of the
signal sent,
transmitted signal strength, and signal duration. Such control further
facilitates certain
improvements in processing, and facilitates receivers identifying and using
certain signal
qualities and/or characteristics particular to the detection aspects of the
network (103), which
may differ from general networking aspects sharing the same network (103).
With control of
the message sent and received on the opposing sides of the mass being located,
it is not
necessary to send a signal as a scan, nor to sweep a region in space, as such
functions tend to
require significantly more expensive equipment than is needed for typical
broadcast or
directional transmission between nodes (107). Messages are generally
constructed in such a
way as to best produce usable data for detection algorithms which would be
constructed to
function best with the communication network they are being used within.
Generally, such
constructions still avoid the need for waveform level analysis of the signals
sent by the network.
[084] In the depicted embodiment, each node (107) generally is able to
determine the origin
node (107) of packets received by such node (107). Such message origination
information is
typically encoded within the message itself, as would be known to one skilled
in
communications networks. By way of example and not limitation, this may be
done by
examining data embedded in established protocols in the networking stack, or
by examining
data transmitted by the sending node (107) for the specific purpose of
implementing the
systems and methods described herein. Typically, each node (107) has
appropriate hardware
and processing capability for analyzing the messages received. While many
different
topologies and messaging protocols would allow for the functionality described
herein,
28
7615577
Date Recue/Date Received 2022-07-04
generally mesh networking topologies and communication methods will produce
usable
results.
[085] FIG. 2 depicts an embodiment (201) of a method according to the present
disclosure
and should be understood in conjunction with the system of FIG. 1. In the
depicted
embodiment, the method begins (203) with the establishment (203) of a
detection network
(103) comprising a plurality of communication nodes (107) according to the
present disclosure.
As would be known to one skilled in the art of setting up communication
systems, there are
many different approaches to the setup of such a network (103) and many
different network
(103) topologies may prove viable within this framework.
[086] Next, a digital map in memory may be generated (205) indicating the
detection
network's (103) physical node (107) geometry. The detection algorithms
described herein
generally use information about where in the physical environment (102) the
nodes (107) are
deployed. Data about such physical location of the nodes (107) may be supplied
manually to
an accurate diagram of the physical network environment (102), and/or software
could be used
to automatically generate a relational position map of one or more nodes (107)
within the
detection network (103), facilitating easier placement of the nodes (107) into
such an
environment map or diagram.
[087] Alternatively, nodes (107) may be placed on a blank or empty map or
diagram using
relational (as opposed to absolute) distances for detection. In such a
dimensionless system,
messages could still be generated from the algorithms related to the detection
of humans in the
system (101), and additional manual processing may be included, such as user
input concerning
which messages are sent related to the presence and/or movement of humans
within the
network (103).
[088] In an embodiment with automatic node (107) location detection, node
(107) locations
are detected algorithmically and/or programmatically by one or more nodes
(107) and/or a
29
7615577
Date Recue/Date Received 2022-07-04
computer server (109), based upon factors such as, but not necessarily limited
to: detection
network (103) setup and configuration, including physical location of specific
hardware
components such as nodes (107) and each node's (107) location relative to one
or more other
nodes (107); signal strength indicators; and, transmission delay. In the
depicted embodiment,
this step (205) further comprises overlaying the generated map on a digital
map of the physical
space (102) or environment (referred to herein as an "environment map") the
detection network
(103) occupies, such as floor plan of a building. This step (205) may further
and optionally
comprise a scaling element to align the scales of the generated map to the
environment map,
as well as user-manipulated and/or modifiable input elements for making
adjustments to fine-
tune the generated map so that it more closely conforms to the actual node
(107) deployment
geometry, as would be understood by one of ordinary skill in the art. In an
alternative
embodiment, each node (107) may be manually placed in its appropriate location
on the
environment map without using a relative location algorithm.
[089] Either way, this step (205) establishes the physical locations of the
nodes (107) in the
detection network (103), which will facilitate determination of the location
of interposed
biological masses attributable to the presence of humans within the detection
network (103).
By placing the nodes (107) on a map (either through manual or automatic
means), the nodes
(107) can track the presence of a human in the network (103) based on how the
baseline signal
affects communication between various nodes (107). The system (101) then
utilizes
information collected about the signals which arrive at the receivers, given a
transmitted set of
information known to the data processing algorithm. The data processing
algorithm is what
ultimately determines whether a human is present within the network (103)
and/or where within
the network (103) that human is located.
[090] Next, messages are constructed and exchanged (207) in a format, and
according to a
protocol, determined to be suitable for detecting the presence of a biological
mass within the
7615577
Date Recue/Date Received 2022-07-04
network (103). While this may be done using general purpose networking
protocols known in
the art, such as protocols in the OSI network model, or special-purpose
protocols which replace,
or supplement, such general-purpose protocols.
[091] Generally, it preferred that this step further comprise controlling
and/or modifying
(207) messages passed within the detection network (103) for the specific
purpose of detecting
human presence and facilitating simplified statistical analysis. By
controlling (207) message
exchange, the system (101) can adjust for a common content being sent through
the detection
network (103) while also facilitating adjustment of parameters including, but
not necessarily
limited to: transmission intervals; transmission power; message length and/or
content; and,
intended message recipient(s). Again, the system does not necessarily rely on
waveform level
analysis, allowing operation within the confines of wireless communication
standards.
[092] Controlling (207) such parameters facilitates the development of
statistics and/or
analytics, which may be based at least in part on pre-defined or anticipated
message content or
characteristics. Such content and/or characteristics may include, without
limitation,
transmission timestamp and/or transmission power level. By controlling and
modifying (207)
these aspects, one may overcome hardware limitations, including hardware
features which
cause unwanted consequences when used in a detection network (103) according
to the
presence disclosure, such as but not necessarily limited to automatic gain
control (AGC)
circuits, which may be integrated into certain receiver hardware in a node
(107).
[093] Next in the depicted embodiment (201), the space (102) is cleared (209)
of significant
biological mass - notably humans (205). Then, a statistical baseline of signal
strength is
developed (211) locally by each node (107). Again, by placing the nodes (107)
on a map in
step (205), whether through manual and/or automatic means, the nodes (107) can
track the
presence of a human in the network (103) based on how the baseline signal is
affected for
communication between nodes (107).
31
7615577
Date Recue/Date Received 2022-07-04
[094] Next, a biological mass enters (213) the detection network (103),
causing signal
absorption and other distortions, which manifest in changes in signal
characteristics between
nodes (107). These changes are detected (215) and analyzed (217) to determine
whether the
changes are indicative of the presence of a human, or of another type of
biological mass the
detection network (103) is configured to detect. Such detections are further
localized at least to
an area between nodes, such as within an interior area between three nodes on
the network, but
possibly with greater accuracy depending on the algorithms and hardware being
in use at the
time.
[095] Generally, this is done using detection algorithms executed either by
one or more nodes
(107) or by a server computer (109). The nodes (107) and/or server (109) use
software to
estimate the location of the detected biological mass in the detection network
(103) using one
or more detection algorithms. Such algorithms generally compare the baseline
profile to newly
detected signals, and may also use or be based upon various data and other
aspects, such as,
without limitation: detection network (103) setup and configuration, including
physical
location of specific hardware components such as nodes (107) and each node's
(107) location
relative to one or more other nodes (107); signal strength indicators; and,
transmission delay.
[096] Generally speaking, as described elsewhere herein, these algorithms
include comparing
newly gathered signal characteristic profiles (215) to baseline signal
characteristic profiles
(211) to identify a change and determine whether, based on the nature of the
change, the change
is indicative of the presence of a human. This determination may be done at
least in part using
training data developed through machine learning as described elsewhere
herein.
[097] In an embodiment, the detection algorithms may further comprise the use
of observed
signal characteristic change(s) between one or more pairs of nodes (107) in
the detection
network (103), correlated in time and relative effect. These factors
facilitate the identification
of a physical location in the detection network (103) where such a signal
change took place,
32
7615577
Date Recue/Date Received 2022-07-04
allowing for an estimate of the physical location of the human causing such
signal characteristic
change(s), which in turn may be used to estimate a physical location in the
detection network
(103) environment where the biological mass is interposed. Such physical
location may be
provided as simple x, y, z coordinates according to a coordinate system, or
may be visually
indicated, such as on the map.
[098] Where multiple humans are present in the detection network (103),
separating out the
impact of the various individuals from one another is more difficult, and
accuracy will
generally improve with the addition of more nodes (107). In an embodiment,
techniques such
as advanced filtering and predictive path algorithms may be used to separately
determine
location of individuals within the network (103). Although movement of the
human in the
network (103) is not required for the systems and methods to operate properly,
movement, or
lack of movement, may be used to improve detection accuracy, such as by
predicting the path
of a single individual. This can help identify instances where an individual
has, statistically,
"disappeared" from the detection network (103) but the system has sufficient
data to estimate
that the individual is still present in the network (103).
[099] For example, where an individual's movement path has been predicted, and
terminates
next to another detected individual, the system (101) may determine that the
two individuals
are too close together for signal characteristic profile changes to separately
identify them, but
since the individual's movement path was not determined to have taken the
individual out of
the network's (103) detection range, the algorithm determines that the
individual is present,
and not moving, in close proximity to another detected human. Thus, when one
of the two
proximate, stationary humans moves, the algorithms may again separately
identify each one,
and resume predicting path based on observed signal characteristic profile
changes.
[0100] In this way, the systems and methods according to the present
disclosure can track one
or more individual humans within a network (103), whether or not moving, and
whether or not
33
7615577
Date Recue/Date Received 2022-07-04
any such humans are associated with a fiducial element. Identifying specific
individuals may
further be done using other path prediction and sensing algorithms, such as
but not necessarily
limited to those used in the robotics industry for human-following technology,
in order to
estimate which human was which. It should be noted that individuals may impart
specific and
unique effects on various signal characteristics, allowing for the
identification of a specific
individual, and further allowing for one specific individual to be
distinguished from others.
Such effects may be used to further determine the location of specific
individuals within the
detection network.
[0101] The detection algorithm(s) are generally constructed to take advantage
of the
characteristics of communication signals, considering factors such as, but not
necessarily
limited to, frequency of the signal(s) and the transmitted power levels of the
signal(s). In an
embodiment, the algorithms detect human presence using data-driven methods for
determining
the effect of the presence of a human on signal characteristics in the RF
environment within
the communication network, and then identifying when that effect is later
observed.
[0102] For example, in an embodiment, a signal characteristic which varies
with the presence
of a human body is the signal strength registered between nodes (107). This is
particularly the
case within a BLE network, and the statistics related to signal strength over
time may indicate
the presence of a human within the network. These artifacts may be used by the
detection
algorithm(s) to provide information about the physical location of the object
causing the
artifact. That is, by combining various statistics about artifacts captured
across the network
(103), the system determines where in physical space (102) the artifact is
located, and thus
where a human is in the network (103).
[0103] In the simplest use case, the algorithms may simply identify changes in
signal
characteristics which are similar to changes known (e.g., from training) to be
caused by the
presence of a human, and simply trigger a detection event (219) whenever such
changes relative
34
7615577
Date Recue/Date Received 2022-07-04
to a baseline are detected. This may appear like an adjustment of mean,
standard deviation,
skewness, or variance in the signal strength depending on the system (101)
used. When the
detected signal characteristic profile returns to a profile similar to the
baseline, it can be inferred
that the physical environment (102) has returned to an empty state with
respect to whether a
human is present.
[0104] Elaborating on the simplest use case, the baseline profile in this case
comprises some
or all baseline profiles which exist when a space does not contain any humans,
and may vary
depending on physical adjustments to that space. Simpler algorithms, which may
account for
the changes associated with a newly detected human change relative to a recent
baseline, can
be used to address such situations; however, in the event that the baseline
has changed, it is
preferred that the system accurately determine whether one or more current
signal profiles
matches an empty baseline profile, or matches a profile one that represents
some degree of
occupancy. Such determinations may be made in response to movement, but it is
preferred that
they be not made in response to movement, but rather based on whether the
characteristics of
such a signal can be correlated with one or more of the empty baselines or one
or more of the
presence signal profiles.
[0105] Compared to other technologies used for such determinations (typically
the Passive
Infrared (PIR) Sensor), which require motion to function, the systems and
methods described
herein are capable of detecting the presence of a static human within a space
(102), whether or
not in motion, and more precisely, detecting when a human is no longer in the
space (102). For
applications such as security and occupancy sensing, this system would be more
difficult to
trick. Some examples of tricks that may fool PIR and other similar motion
based technologies
include holding a sheet in front of a person while they enter a space, moving
very slowly, or
remaining generally motionless in an area after entering. Another benefit is
that the system
does not necessarily require additional hardware beyond that used in ordinary
network
7615577
Date Recue/Date Received 2022-07-04
communications. This is because the additional software and processing
capability may be
provided via external components or modifications to existing hardware, such
as by
implementing the appropriate software as a System On a Chip (SOC) attached to
off-the-shelf
communications modules. If additional processing power is required, additional
processing
node(s) may be added to analyze the signals propagated between nodes (107), or
the workload
may be transmitted to and handled by a dedicated server machine (109).
[0106] Making determinations of human presence and/or location may be related
to the
particulars of the signal type being analyzed, and controlling the signal sent
between nodes
(107) on the network (103) to best achieve those detections. By sending
controlled
communication pulses through the network (103) where the original signal is
known and the
transmitted power can be modulated, it is possible to develop exemplary data
related to signal
absorption, reflection, backscatter, etc. due to additional humans between the
nodes (107).
Since it is generally assumed that a baseline system can be configured without
the presence of
a human and that such a baseline would look statistically different than with
a human present,
it can further be assumed that signal characteristic changes would be due to
the presence of a
human in the network. By allowing for the input of timers and generally
configuring the system
to refine the baseline definition when a space (102) is empty, the system may
recalibrate itself
periodically to achieve improved accuracy. Generally speaking, tracking
algorithms make use
of the best available triangulation calculations combined with statistical
methods, as would be
known to one skilled in the art of location technologies, coupled with the
detection algorithms
for detecting humans within the network (103).
[0107] The present disclosure does not require a fiducial element associated
with the human
detected, nor does it require that the human be carrying any device capable of
communicating
with the network; however, such technology would take advantage of such
elements should
they be deployed within the system. The addition of such elements may ease the
calculation
36
7615577
Date Recue/Date Received 2022-07-04
burden on the system and allow for increased accuracy. The systems and methods
described
herein do not preclude such additional functionality, and could be enhanced by
it. Augmenting
detection with an inference engine adds to the ability of the sensing hardware
to recover from
a false alarm situation or other edge case, thereby making the system more
robust. Such an
inference engine may further feed information into a machine learning system,
which may
further modify the one or more baseline signal profiles or the one or more
presence signal
profiles to improve the performance of the system.
[0108] In an embodiment, a detection network (103) implementing the systems
and methods
described herein may further comprise elements for taking action (219) based
on the detected
presence and/or location of a human. This may be done, for example, by sending
control signals
over the network using the computers to first determine the presence and/or
location of a human
on the network, and then to determine an action to take based on the presence
and/or location
of a human on the network, and to send a message over that network to take
that action. Since
the communication network and the network performing the detection may be the
same
network, the invention described herein extends the traditional functionality
of a
communication network to include human detection and/or location sensing
without requiring
additional sensing hardware.
[0109] The computer elements on the network necessarily perform additional
calculations and
may craft communication signals. This may ease the calculation burden on the
computers;
however, the network may still function as a command and control network,
independently of
the network as a detection network.
[0110] The system as a whole can be used for a wide variety of applications,
ranging from
occupancy sensing, as might be used for lighting control and/or security, to
counting the
number of people in a space as might be needed for a heat and/or traffic map,
to a system that
tracks individual humans moving through a space. The technology may be
integrated into the
37
7615577
Date Recue/Date Received 2022-07-04
network nodes themselves, or may be a combination of nodes transmitting
information to a
processing element (either directly on the network or in the cloud) to perfoun
the calculations
to determine the desired information. The final integrated product suite may
be customized for
an application, and could be used in a variety of different ways.
[0111] No additional sensor is required (though, in an embodiment, one may be
present), and
the detections are effectively made through calculating statistics from the
traditional RF
communication stack. Such a system prevents the collection of personal data
from the people
walking through the space as the system only knows that an approximately human-
sized mass
of water, organs, clothing, etc. has passed through, and does not require any
separate device to
act as a fiducial element. As such, the technology represents a significant
departure from
traditional methods for tracking humans moving through a space.
[0112] A logical extension of the systems and methods described herein
comprises
dynamically handling functional network messages within the statistical
analysis so as to avoid
or reduce additional messaging overhead for the system. It is also
contemplated that, in an
embodiment, the systems and methods described herein are extended to comprise
dynamic
adjustments to network and/or message structure, configuration, and/or
operating parameters
based at least in part on functional messages transmitted within the network.
[0113] Further, because the tracking is based on signals being affected by
what is generally a
human mass, the system is not reliant on the human moving around for
detections. By not
relying on movement, many of the shortfalls with traditional presence sensing
technologies,
such as passive infrared and ultrasonic sensing technology, are overcome.
[0114] The utilization of a communication network's signals between nodes to
detect the
presence of humans in the network where the human does not carry a fiducial
element is a
radical departure from current non-fiducial element detection methods and
makes use of
communication networks to perfolin presence sensing in an entirely new way.
The combination
38
7615577
Date Recue/Date Received 2022-07-04
of detection techniques and utilization of network nodes as transmitter
receiver combinations
for the purposes of performing human presence detection presented herein
constitute a new
type of human presence detection system which does not require additional
equipment beyond
that which is required to form the communication network itself.
[0115] The systems and methods described herein may be implemented in a
communication
network without influencing the operation of the network itself for purposes
of ordinary
communication. The network continues to operate as a communications network as
its primary
function, but some of the communications are used in this case to calculate
the position of a
human existing in the network. Because the systems and methods described
herein utilize basic
operations of a network, a human within the network additionally carrying a
transceiver device
known to the network may be detected and located with increased accuracy. Such
a transceiver
device, which may comprise, for example, a mobile computing device having a
wireless
transceiver, such as a cell phone, mobile phone, smart phone, tablet computer,
wearable
computer technology, and so forth, may connect to the network and be locatable
by the network
using traditional triangulation methods known to one skilled in the art.
Machine learning
algorithms may also be applied when a person carries such a transceiver, which
may in turn
further improve performance.
[0116] The location calculation of a known transceiver device may be compared
with the
location of the person as determined by the non-transceiver aspects described
herein. With the
communications network reporting both the location of the fiducial element as
well as the
human within the network, the locations of those two can be compared. Since it
is generally
the case that the detected location of a fiducial element has a higher degree
of fidelity than the
estimated location of the human based on network communications alone, the
location
calculations for the position of the human within the network can be adjusted
using machine
39
7615577
Date Recue/Date Received 2022-07-04
learning algorithms so as to improve the location calculation capabilities of
the system for the
next human entering the network.
[0117] Using machine learning algorithms, the system can improve the accuracy
of location
predicting algorithms based on the known location from the transceiver. This
may allow for
verification of prior determinations, and refining of future determinations.
For example, if it is
found that prior determinations are consistently off by about the same amount,
that amount
may be applied to future determinations as an adjustment. In this way, the
system can continue
to improve and train itself to better locate the humans within the network.
Similarly, machine
learning can continue to improve the detection and false alarm rate. By way of
example and
not limitation, data concerning prior traffic patterns at a facility can be
used to establish
defaults, presumptions, or expectations concerning the range of times or days
during which a
particular facility is generally occupied or generally empty. Such data can be
used by the system
to improve its performance.
[0118] Additionally, the system is configured to make or draw inferences, such
as based upon
physical interactions with network elements; that is, devices or components
attached to or
communicating with the network that are operable by or operate based upon the
presence of a
human, such as network-operable electrical switches, doors, motion sensors,
infrared sensors,
and the like. Such physical interactions may be considered fiducial elements
at the point in
time that they are interacted with for the purposes of the system. As an
example, if a light
switch that is part of the network is actuated, the system may infer that a
human was present at
or near the physical location of the switch at the time the switch was
actuated. As such, the
system could use that information as a known data point (i.e., examining
signal characteristics
of the various network devices at that point of time with the inferred
knowledge that those
characteristics reflect a human at a particular location near the switch) to
which it could apply
machine learning to better make predictions of human presence in the future.
Additionally,
7615577
Date Recue/Date Received 2022-07-04
such events could serve as presence triggers for other purposes such as
security alerts. As an
example, say that the system is in a security mode and someone has found a way
to mask their
presence but still interacts with a switch, then the system would be able to
determine that
someone was present and send an alert based on the interaction with the
switch. Generally
speaking, interactions with the system would be defined both physically and
logically where
logical interaction would include typical usage patterns based on time,
outside inputs, etc. Such
a system serves as backup to the RF presence sensing and provides additional
machine learning
capabilities to the system.
[0119] Additionally, the system can estimate whether a mobile transceiver in
the network is
actually being carried by a human or not, such as where a human leaves a
device in a location
in the network. Because the system can detect the human as a biomass through
changes in
signal characteristics, the system can detect whether a transceiver is present
in the network
while a human biomass is not. This inhibits false training of the system and
facilitates the
avoidance of baseline and presence signal profiles being corrupted by data not
correlated with
such profiles.
[0120] In an embodiment, as a further input to the inference engine, if some
indication of the
system changes states, and a human within the detection area behaves in such a
manner as to
correct the system state, the system may infer that it should adjust its
baseline and presence
profiles to better reflect user preferences. By way of example, if the lights
in a space were to
turn off with a human in the space, said human may engage in behavior to
reflect presence,
such as physically moving, waving arms, and so forth, or simply looking for or
walking towards
a wall switch. This movement may be detected within some reasonable amount of
time, and
the system may determine that it incorrectly determined that the space was
absent, and adjust
its baseline and presence profiles accordingly. Such activities may be
referred to as inferring
the presence of one or more humans in a space.
41
7615577
Date Recue/Date Received 2022-07-04
[0121] As a side effect of collecting various signal characteristics and being
capable of running
them through various algorithms, the system is capable of running multiple
detection
calculations simultaneously to achieve different performance criteria with the
same system. As
an example, the same communication network can be used for detections
associated with
lighting and security; however, the gathered statistics can be processed
differently, but
simultaneously, for the two applications. In this way, the lighting
application can still provide
for a shorter time to detect, but with a potentially higher false alarm rate,
while a security
application can trade a slightly longer time to detect while reducing the
false alarm rate. The
signal characteristics to be processed by the system may vary by application,
but all are
captured from the communication network and can be processed in multiple ways
simultaneously. Such processing methods may be encapsulated in multiple sets
of different
sample baseline signal data for determining detections relative to a baseline
signal profile.
[0122] In an embodiment of a system according to the present disclosure, the
system comprises
a communication system which is capable of determining the presence of one or
more humans
from information about the wireless signals between two or more computers on
the network
where each computer consists of: a transceiver for communication; and a
computing element
for performing calculations, where each computer sends signals to one or more
other computers
on the network where the signal includes a unique identifier of the computer
sending the signal;
where each computer processes the signals received for the purposes of
determining the
presence of one or more humans; and where the one or more humans are not
required to have
on their person any device capable of communicating with the network.
[0123] In an embodiment of such a system, the algorithms use statistical
methods to determine
the presence of one or more humans. In a further embodiment of such a system,
the statistical
methods determine the number of people present. In another further embodiment
of such a
system, the system is capable of determining the physical location of the one
or more humans
42
7615577
Date Recue/Date Received 2022-07-04
on the network. In a still further embodiment of such a system, the system is
capable of tracking
the physical location of the one or more humans over time. In another further
embodiment of
such a system, the system uses information about the presence of one or more
humans to control
devices on the network. In an embodiment, the network is a mesh network.
[0124] In an embodiment, the computers determine their relative physical
locations and further
determine the relative physical location of the one or more humans on the
network. In a further
embodiment, statistical methods are applied to a measure of signal strength to
determine the
presence of a human. In a further embodiment, the transmitted signal is
controlled for making
detecting human presence easier. In a further embodiment, the power level of
the transmitted
signal is controlled for making human presence easier. In a further
embodiment, the system
functions as an occupancy sensing system. In a further embodiment, the
occupancy sensing
system controls a lighting system. In a further embodiment, the network for
controlling the
lighting system and the network used for occupancy sensing utilize the same
communications
technology and hardware. In a further embodiment, the communications
technology employed
by the computers is chosen from the list of: BluetoothTM Low Energy, WiFi,
Zigbee, Thread,
and Z-Wave.
[0125] In a further embodiment, the system functions as a sensing system for a
security
application. In a further embodiment, the security sensing system controls the
security system.
In a further embodiment, the network for controlling the security system and
the network used
for security sensing utilize the same communications technology and hardware.
In a further
embodiment, the system functions as a human detector for robotic systems. In a
further
embodiment, the robotic systems have computers which locate various elements
of the robotic
system relative to one another dynamically. In a further embodiment, the
network for
controlling the robotic systems and the network for functioning as the human
detector for the
system utilize the same communications technology and hardware.
43
7615577
Date Recue/Date Received 2022-07-04
[0126] In a further embodiment, the system functions as a sensing system for a
HVAC
application. In a further embodiment, the HVAC sensing system controls the
HVAC system.
In a further embodiment, the network for controlling the HVAC system and the
network used
for HVAC sensing utilize the same communications technology and hardware.
[0127] In another embodiment, the system uses machine learning to improve its
detection
capabilities where humans which have a fiducial element on their person train
the system
through: (1) using known location techniques to determine the location of the
fiducial element;
(2) using the system described above to locate the person; (3) comparing the
location calculated
by the method of (1) of this paragraph to the method of (2) of this paragraph;
(4) adjusting the
location determining methods using machine learning algorithms to improve the
location
calculating capabilities of the system.
[0128] In another embodiment, the system may infer the presence of humans in
the network
based on those humans interacting in some way with one or more of the
computers on the
network. In a further embodiment, the system may use the inferred presence of
a human as an
input for machine learning to improve its detection capabilities.
[0129] In an embodiment of a system according to the present disclosure, the
system comprises
a communication system which is capable of determining the presence, both
static and moving,
of one or more humans from information about the signals between two or more
computers on
the network where each computer consists of: a transceiver for communication;
and a
computing element for performing calculations, where each computer sends
signals to one or
more other computers on the network where the signal includes a unique
identifier of the
computer sending the signal; where each computer processes the signals
received for the
purposes of determining the presence of one or more humans; where the one or
more humans
are not required to have on their person any device capable of communicating
with the network.
44
7615577
Date Recue/Date Received 2022-07-04
[0130] In an embodiment, the algorithms use statistical methods to determine
the presence of
one or more humans. In another embodiment, the statistical methods determine
the number of
people present. In another embodiment, the system is capable of determining
the physical
location of the one or more humans on the network. In another embodiment, the
system is
capable of tracking the physical location of the one or more humans over time.
In another
embodiment, the system uses information about the presence of one or more
humans to control
devices on the network. In another embodiment, the information about the
presence of one or
more humans is made available to one or more systems not directly involved in
the
determination of presence. In another embodiment, the system has the ability
to perform self-
optimization to achieve a given performance according to one or more preset
criteria.
[0131] In another embodiment, the communications protocols or network is
generally defined
by a standards committee including but not limited to protocols such as
BluetoothTM Low
Energy, WiFi, Zigbee, Thread, and Z-Wave. In another embodiment, statistical
methods are
applied to a measure of received signal strength to determine the presence of
a human. In
another embodiment, the transmitting and receiving devices on the network may
be selected
and actuated by the system for the purpose of making human detection easier.
In another
embodiment, the power level of the transmitted signal may be controlled for
making human
presence easier. In another embodiment, the system functions as an occupancy
sensing system
for a lighting system. In another embodiment, the occupancy sensing system
controls a lighting
system. In another embodiment, the network for controlling the lighting system
and the
network used for occupancy sensing utilize the same communications technology
and
hardware.
[0132] In another embodiment, the system functions as a sensing system for a
security
application. In another embodiment, the security sensing system controls the
security system.
In another embodiment, the network for controlling the security system and the
network used
7615577
Date Recue/Date Received 2022-07-04
for security sensing utilize the same communications technology and hardware.
In another
embodiment, the system functions as an occupancy sensor for a Heating,
Venting, and Cooling
(HVAC) system. In another embodiment, the occupancy sensing system controls
the HVAC
system. In another embodiment, the network for controlling the HVAC system and
the network
used for occupancy sensing utilize the same communications technology and
hardware.
[0133] In another embodiment, the system uses machine learning to improve its
detection
capabilities where humans which have a fiducial element on their person train
the system
through: (1) using known location techniques to determine the location of the
fiducial element;
(2) using the system to locate the person; (3) comparing the location
calculated by (1) of this
paragraph to (2) of this paragraph; (4) adjusting the location determining
methods using
machine learning algorithms to improve the location calculating capabilities
of the system.
[0134] In another embodiment, the system may infer the presence of humans in
the network
based on those humans interacting in some way with one of the computers on the
network. Said
interactions may be direct physical interactions or indirect interaction in
response to some
change of state in the system (e.g., waving arms in response to lights turning
off). In another
embodiment, the system may use the inferred presence of a human as an input
for machine
learning to improve its detection capabilities.
[0135] Also described herein is a communication system which is capable of
determining the
presence, both static and moving, of one or more humans in a detection network
based on
information about the signals between two or more computers on the network
where each
computer consists of: a transceiver for communication; and, a computing
element for
performing calculations, where each computer sends signals to one or more
other computers
on the network where the signal includes a unique identifier of the computer
sending the signal;
where each computer will process the signals received for the purposes of
determining the
presence of one or more humans in two or more ways to achieve different
performance criteria
46
7615577
Date Recue/Date Received 2022-07-04
as required to function for two or more purposes simultaneously; where the one
or more
humans are not required to have on their person any device capable of
communicating with the
network.
[0136] In an embodiment, the algorithms use two or more statistical methods to
determine the
presence of one or more humans according to two or more sets of performance
criteria. In
another embodiment, the system has the ability to perform self-optimization to
achieve a set of
two or more performances according to two or more preset criteria. In another
embodiment,
the communications protocols or network is generally defined by a standards
committee
including but not limited to protocols such as BluetoothTM Low Energy, WiFi,
Zigbee, Thread,
and Z-Wave. In another embodiment, two or more statistical methods are applied
to a measure
of received signal strength to determine the presence of a human according to
two or more sets
of perfoi mance criteria. In another embodiment, the system uses machine
learning to improve
the detection capabilities of the two or more methods for determining presence
where humans
which have a fiducial element on their person train the system through: (1)
using known
location techniques to determine the location of the fiducial element; (2)
using the system to
locate the person; (3) comparing the location calculated by (1) of this
paragraph to (2) of this
paragraph; (4) adjusting the location determining methods using machine
learning algorithms
to improve the location calculating capabilities of the system.
[0137] In an embodiment, the systems and methods described herein include
change detection.
By way of example and not limitation, change detection may use or utilize a
rolling baseline
approach. In such an embodiment, a first baseline is established and compared
with a second
baseline, and any differences between the first and second baselines caused by
the presence of
a human in the detection network may be recognized by the system. This may be
done by
programming software to receive sets of wireless signal characteristic data
from one or more
nodes in the detection network and, based on such data, detecting changes in
the RF
47
7615577
Date Recue/Date Received 2022-07-04
environment caused by a human being present in a different position when the
first baseline is
established as compared to the second baseline. Such methods may be utilized
when a system
is first setup in a location to establish a minimal performance level without
requiring a space
be empty upon startup. Such systems with change detection may improve overtime
to a state
between change and presence where limited aspects of presence detection may be
present in
such a system.
[0138] An exemplary illustration of change detection is depicted in FIG. 3A.
In the depicted
embodiment of FIG. 3A, the RF environment of FIG. 1 is shown with a human
(301) present
in the environment (103) at a discreet position (303). As described elsewhere
in this disclosure,
the characteristics of wireless signal transmissions among the nodes (107A) to
(107D) is
influenced by the presence of the human (301). In this particular example,
transmissions
between node A (107A) and node D (107D) are influenced by the presence of the
human (301).
Thus, when the baseline is established (211) as shown in the method of FIG. 2,
the baseline
represents the wireless signal characteristics while the human (301) is
present at the discreet
position (303). If the human (301) moves to a new position (305), as can be
seen if FIG. 3A,
the characteristics of wireless signals among the nodes (107A) to (107D) will
change.
[0139] In this particular exemplary embodiment, there will be little
interference between nodes
A (107A) and D (107D) when the human is at position (305). However, there will
be greater
interference between nodes B (107B) and C (107C), because the position (305)
is disposed
between those two nodes. Thus, when the differences are detected (205) as
shown in FIG. 2,
the change in position of the human can be detected.
[0140] This is less difficult to implement than presence sensing because the
need to establish
baselines in the detection network (103) without a human present is reduced.
Such a system
may detect changes within the detection network (103) based primarily on when
a human
changes positions, and updating the operative baseline profile on a rolling
basis. That is, the
48
7615577
Date Recue/Date Received 2022-07-04
baseline (211) is updated in this embodiment to be equal to the baseline when
the human (301)
is at position (305). Thus, when the human (301) moves to a third position
(307), the differences
detected (215) are as between the second baseline taken at position (305) and
the wireless signal
characteristics of detection network (103) when the human is at position
(307). Likewise, the
baseline (211) has been updated to be equal to the baseline in position (307),
which can then
be used to detect further changes in the position of a human (201). This
detection method uses
changes in the wireless signal baselines caused by changes in the position of
a human (301) in
the detection network (103). This system has many advantages over prior art
motion detection
technologies, such as passive infrared, in that this system is not obscured by
objects and can
detect slow or gradual changes in position, which may be overlooked by prior
art systems. In
an embodiment using this methodology, the baselines may be continuously
updated.
[0141] In another embodiment, the system or method comprises making a
confidence
determination. This aspect may determine a degree of confidence that a third
baseline
corresponds to either a first or second set of baselines. The confidence
determination may use
any number of techniques, including techniques known in the art, such as
supervised training
or the use of statistical methods to determine a degree of similarity or
difference between data
sets. The confidence may increase or decrease over time, allowing for
decisions to be
automatically made with respect to baseline differences that are minimally
different, but may
still indicate the presence of a human in the detection network (103).
Confidence in a
determination of presence or absence of a human in the detection network (103)
may be
determined based on how similar a third baseline is to a first or second
baseline. For example,
if a third baseline is known to indicate the present of a mass whose impact on
signal
characteristics is known, comparing the first or second baseline to the third
may improve (or
decrease) the confidence level that the identified mass is the same as the
mass identified in the
third baseline. Based on confidence, the system can be configured to use
different confidence
49
7615577
Date Recue/Date Received 2022-07-04
thresholds in different operational contexts (e.g., HVAC, security, lighting,
safety, etc.). A
system or method including a confidence determination may operate across a
plurality of
systems using a common communication system, wherein the systems can include
disparate
nodes in communication with one another. A given node may operate in a
plurality of detection
networks (103), allowing for better system scaling when deploying the systems
and methods
to multiple adjacent detection networks (103).
[0142] In another embodiment, baseline differences may be used to count or
estimate the
number of humans present in the detection network. In an embodiment, this may
be done by
estimating the amount of human mass in the detection network, and dividing by
an average
mass per person. This may be done by establishing a first, empty baseline when
there are no
humans in the detection network (103), and establishing a second, occupied
baseline when
some known number of humans are present in the detection network (103). Next,
a third
baseline is taken and compared to the first empty baseline and the second
occupied baseline.
The system software then interprets where the third baseline wireless signal
characteristics fit
on a spectrum of profiles between the first empty baseline and the second
occupied baseline,
and from that determination estimate the total amount of human mass in the
detection network
(103). This estimation may be based upon the total mass of humans in the
detection network
when the second occupied baseline was established.
[0143] By way of example and not limitation, if the signal distortion in the
third baseline is
moderate as compared to the first empty baseline, the system may estimate that
the amount of
human mass present is relatively low. However, if the amount of signal
distortion is closer to
that shown in the second occupied baseline, the system may determine that the
estimated
amount of human mass present in the detection network (103) is closer to the
amount that was
present when the second baseline was taken. Similarly, if the amount of
distortion is determined
to be even more extreme than that reflected in the second baseline, the system
may determine
7615577
Date Recue/Date Received 2022-07-04
that the total amount of human mass present when the third baseline was taken
exceeds the
amount present when the second baseline was taken. The estimation of human
mass may be
based broadly upon the algorithms and methods described herein, and adjusted
to estimate a
number of humans in a space as generally described above.
[0144] In another embodiment, a system uses entrance and exit signatures in
network
diagnostic information to estimate the number of humans present in a space
based upon such
signatures.
[0145] In such a method, an entrance profile is established by a human
entering a space, an
exit profile is established by a human leaving the same space, and another
later-captured profile
is compared to the entrance and exit profiles to determine whether a human has
entered or
exited the space. Entrance and exit profiles are learned through normal system
operation, based
upon estimation from the presence detection technology and its determination
following a state
change. By way of example and not limitation, if a system detects a change and
presence goes
from not being detected to being detected, such an event may be classified as
an entrance.
Similarly, by way of example and not limitation, if the system detects a
change and determines
that a space has gone from occupied to unoccupied, such an event may be
classified as an exit.
The difference between entrance count and exit count may be used to estimate
the number of
humans present in the space.
[0146] In another embodiment, a system uses entrance and exit signatures in
network
diagnostic information in combination with people count estimates derived from
comparing a
sample profile against presence profiles of varying people counts.
[0147] Each of these methods may be used in conjunction with one or more
counting methods
to enhance the accuracy.
51
7615577
Date Recue/Date Received 2022-07-04
[0148] In an embodiment, the count or estimate of humans present in the
detection network
(103) may be used to operate another system, such as, but not necessarily
limited to, a HVAC
system.
[0149] In an embodiment, the location or position of a human in the detection
network is
estimated. This may be done by estimating the range between various devices to
determine the
location of a human, examining subset detection areas constructed from higher
numbers of
nodes, using various location baselines, and further extending the function of
a location system
to analyze locations over time to estimate speed and direction of a human in
the detection
network. In one embodiment of such a method, the system may use various node
pairs,
estimating the position of a human between those pairs based on baseline
information, using
overlapping estimates within the node pairs, then determining a highest
probability position for
a human in the detection network based on those overlapping estimates to
determine the actual
location of the human.
[0150] In another embodiment, systems with larger number of nodes can use more
subset
detection areas, generally each with three or more nodes, to determine the
presence or absence
of a human in each space, and estimate location based on overlapping occupied
areas wherein
the common occupied space might be assumed to be the most specific location of
a human in
the detection network. By way of example and not limitation, a set of four
nodes may be
subdivided into four sets of three nodes, where location may be determined
based upon which
subsets of three nodes presence is detected within. This sub-area creation
allows for detections
within subareas where such sub-shapes are defined by overlapping areas created
with sets of
three or more nodes. Alternatively, a plurality of baselines for humans in
different locations
within a detection network may be established, with subsequent baselines
compared against
said baselines to determine the location within the detection network of a
human. By way of
example and not limitation, a detection profile may be created for various
locations within a
52
7615577
Date Recue/Date Received 2022-07-04
detection area where a given detection profile corresponds with a human in a
given position
within the network, a sample profile is compared against a set of detection
profiles
corresponding to different positions, the system determines which detection
profiles correlate
most with the sample profile, and the system makes a determination of the
location of the
human based on the location of the detection profiles deemed most similar to
the sample profile.
[0151] Additionally, based on detected changes in locations of humans in the
detection
network over time, a human's travel speed and direction in the detection
network may be
estimated. This may be done, for example, through the use of interpolation and
dead reckoning,
or direct reconnaissance. An exemplary embodiment of such a system and method
is depicted
in FIG. 3B. In the depicted embodiment, a human is located in a detection
network (103) at
position (401) at Timeo. At a subsequent point in Timei, the Human is detected
at a different
position (403). Because position (401) and position (403) are known, a
Distancei between them
can be calculated. Additionally, the amount of time elapsed from Timeo to
Timei can be
determined or is known. Given that distance equals rate times time, the rate
of movement of
the human from position (401) to position (403) can be determined.
Additionally, a Vector
could be determined representing the movement of the human, embodying both
direction and
magnitude (speed).
[0152] Having only two sample points, however, raises the possibility of a
high error rate, and
more than two sample points is desired. For example, in the depicted
embodiment, a third
profile taken at Time2 places the human at position (405). Again, the
Distance2 from position
(403) to position (405) can be determined, and a rate of speed between these
positions may also
be determined. Ti the depicted embodiment, these positions are generally
linear, suggesting
that the human is moving in a more or less straight line in a given direction,
defined by Vector.
The system may thus further estimate the future or expected position of the
human based on
this data. That is, at Time3 an estimated position (407) of the human may be
determined based
53
7615577
Date Recue/Date Received 2022-07-04
on the prior detected locations. This estimate may place the human outside of
the detection
network (103), and may be further used to estimate the arrival or departure of
a human in or
from the detection network (103). Additionally, this information may be used
to alert another
segment of the detection network, or another detection network entirely, of a
potentially soon
to be arriving human. This may be done, for example, by communications using
the computer
server (109) via the network (115).
[0153] Continuing the exemplary embodiment above, in the depicted embodiment,
the
human's detected change in position from Timeo to Timei is 0.8 meters in one
second, for a
speed of .8 meters per second. The detected change in distance from Timei to
Time2 is 1.2
meters, with one additional elapsed second, or, 2.0 total meters over two
total elapsed seconds,
for an average speed of one meter per second. Thus, at Time3, one second
later, an additional
one meter of movement may be anticipated, making the estimated future position
(407) one
meter further along Vector than position (405).
[0154] In an embodiment, the systems and methods use machine learning to
further train the
system over time. By way of example and not limitation, a system may
accumulate data from
one or more of the above-described change detection techniques using a
combination of known
feedback and/or feedback from third party systems such as but not limited to
interactions with
other smart devices (thermostats, voice recognition systems, etc.), and/or use
inference over
time to improve operation based on expected or anticipated system behavior.
Such inferences
may be based upon ordinary behavior in a space, direct human interaction with
elements of the
system, or sample profile changes from human reactions to system decisions. By
way of
example and not limitation, in a system implementing change detection to
operate lighting or
HVAC systems, user feedback may be provided to the system as supervised
training data,
indicating whether a given operation was correct (i.e., whether a change in
the lighting or
HVAC system should have been made or not).
54
7615577
Date Recue/Date Received 2022-07-04
[0155] Similarly, in a system implementing presence detection, a user may
force change
detection to trigger while within a detection network, providing the system an
automated means
to establish a baseline practice for the occupied space based upon the time
that change
triggering events occur and, facilitating times far removed from change
triggering events to be
detected as generally empty. When combined with inferring occupancy based on
room type,
such a method may facilitate the system training itself, improving
functionality over time from
change detection to presence detection level functionality. Effectively, by
using the system
based on change detection, the system may infer presence and absence, allowing
it to establish
baseline profiles for when no human is present and detection profiles based on
when there is a
human present. In such a way, the system would be capable of training itself
to move from
operating as a change detection system into one operating as a true presence
detection system.
[0156] In an embodiment implementing counting, combinations of change
detection and
presence detection may determine an estimated count of humans within a
detection network,
estimating such counting baseline profiles and improving them over time. Such
a system may
facilitate the system training itself over time to count the number of humans
within the
detection network.
[0157] In an embodiment implementing locating people, combinations of change
detection,
presence detection, and counting people may be utilized to determine estimates
of location
based on overlapping areas and occupancy counts, eventually establishing more
accurate
baseline estimates, allowing the system over time to improve locating humans
within a
detection network. Such a system may comprise an inference engine, such as
computer
software running on the server, and/or build an estimation of expected system
operation from
normal operations, and may adjust operational parameters in accordance with
expected
behavior. For example, if a detection area is typically empty from 10:00am
until 3:00pm, and
occupied from 3:00pm until 6:00pm, parameters may be adjusted to expect
emptiness from
7615577
Date Recue/Date Received 2022-07-04
10:00am-3:00pm and to expect presence from 3:00pm until 6:00pm). Such
inferences may be
developed over time and may improve performance at those times, while
maintaining overall
flexibility.
[0158] Nodes may be disposed in various location combinations to improve
system operation.
A system may operate with nodes located on walls, ceilings, fixed nodes,
mobile nodes, and/or
in mixed configurations. Because spaces are three-dimensional, detection areas
may be defined
by nodes on different floors of a building. Nodes may be placed on walls in
positions such as
switches and outlets. The broadcast range generally defines the perimeter of a
detection area,
and the system may be configured to examine network diagnostics assuming
humans are within
said perimeter.
[0159] In an embodiment, one or more nodes may be placed on a ceiling. By way
of example
and not limitation, this might occur when nodes are integrated into fixtures
and/or lighting
systems. In such an embodiment, nodes may radiate generally downward into the
detection
area, and a system may be configured to examine network diagnostics based on
different
radiation and multi-path patterns than might be seen from a switch and outlet
based system. In
such an embodiment, nodes generate communications in a generally downward
direction where
reflections from walls, objects, and floors generally ensure that the RF
energy reaches other
nodes via multipath. The multipath also generally provides for coverage of the
detection area.
Such coverage due to multipath means that ceiling mounted nodes function
similarly to wall
mounted nodes with regards to the impact of a human on network diagnostic
information.
[0160] Other fixed nodes are also contemplated, such as, without limitation:
televisions;
monitors; and, smart home hubs. Such nodes may be installed on a wall,
ceiling, or at a fixed
location. Still other nodes, such as smartphones, tablets, and laptop
computers, may be used in
a detection network as a mobile node. However, in such an embodiment, a mobile
node may
56
7615577
Date Recue/Date Received 2022-07-04
first locate itself relative to fixed nodes in the system. Having its location
established within
the network may further enhance the accuracy of the system.
[0161] In an embodiment, combinations of nodes may be used in a detection
area. When
combining larger number of nodes, the system may determine the optimal nodes
for operation.
Optimal nodes may be determined by, among other things, determining the most
efficient nodes
for a chosen level of functionality. As node count increases, accuracy of
determination
generally increases, as does level of functionality.
[0162] In an embodiment, one or more nodes may operate in a plurality of
detection areas. This
facilitates improved system scaling, particularly for adjacent detection
areas. Such scaling may
additionally result in inference within a larger network of nodes including
the plurality of
detection areas, further facilitating the tracking of human detections from
one detection area to
the next. For example, nodes may be shared between detection areas. A given
node in a first
detection network may have network diagnostic information based on
communications within
said first detection area, and may also be part of a second detection network
and have network
diagnostic information based on communications within said second detection
network. The
system can make independent decisions on how to operate third party systems in
each of the
two detection areas. Examining inference across detection areas can improve
the determination
of the presence or absence of humans within the detection areas, particularly
where a person
leaves one detection area and enters another. Detected changes in signal
characteristics can be
used to determine the presence or absence of a human in the individual areas,
based on
information shared between the first and second detection area.
[0163] In an embodiment, the systems and methods may operate through the use
of a mass
identification technique. In such an embodiment, a "mass" is identified and
tracked. A unique
identity may be assigned to the mass by the computer systems, and tracked
based on changes
to wireless signal characteristics. By way of example, and not limitation, if
a mass is first
57
7615577
Date Recue/Date Received 2022-07-04
detected near the center of a room, and next detected at a location several
feet away from the
center of the room, but the system has not detected any other masses as
entering the room, the
system may infer that the second detected mass is the same mass as the first
detected mass, but
has relocated to a new position. Based on the difference in signal
characteristics caused by the
interference of the mass in the network, the system may infer, for example,
that other masses
exhibiting similar movement would have similar effects on the signal
characteristics. In this
way, the system can "learn" how to identify a mass, and track it.
[0164] Although each human mass in the system causes different interference
characteristics
when disposed at any location, for most indoor locations, the total set of
humans likely to be
present in a room is generally finite. That is, most indoor spaces are, for
any appreciable length
of time, occupied by the same basic set of people most of the time, with only
minor and
infrequent variations. For example, the same set of people generally show up
each day to a
workplace, or a school, or even a public location such as a restaurant.
Because most indoor
spaces can only be entered from a limited number of points of entry, such as
doorways, the
system can detect a person entering at the point of ingress, and determine the
specific
interference pattern caused by the presence of that particular human upon
entering the space.
Based on the signal characteristics (interference) and the way that those
characteristics change
compared to other humans in the space, it can be determined where and how each
human mass
moves through the room.
[0165] It is contemplated that a system may automate various aspects of setup,
particularly
with regards to grouping nodes into detection areas and building levels of
functionality
nominally based on the machine learning methods described herein. A system
which
determines nearest nodes and estimates detection areas through inference
requires no setup by
a user. Based upon best estimates, a user may simply place nodes throughout a
building, and
the nodes automatically group into detection areas using unsupervised machine
learning,
58
7615577
Date Recue/Date Received 2022-07-04
ultimately resulting in a building system learning how to detect occupants.
Occupancy can then
be related to actions taken by occupants, developing an automation system
which reduces or
eliminates the need for human input for normal system operation.
[0166] In an embodiment, the method is a method for detecting the presence of
a human
comprising: providing a first transceiver disposed at a first location within
a detection area;
providing a second transceiver disposed at a second location within said
detection area; a
computer server communicably coupled to said first transceiver; said first
transceiver receiving
a first set of wireless signals from said second transceiver; said computer
server: receiving a
first set of signal data from said first transceiver, said first set of signal
data comprising data
about properties of said first set of wireless signals; inferring that said
first set of signal data is
indicative of the presence of a human in said detection area; creating a
detection signal profile
for wireless communications from said second transceiver to said first
transceiver based at least
in part on said properties of said first set of wireless signals in said first
set of signal data when
a human is inferred present in said detection area; said first transceiver
receiving a second set
of wireless signals from said second transceiver; said computer server:
receiving a second set
of signal data from said first transceiver, said second set of signal data
comprising data about
properties of said second set of wireless signals; inferring that said second
set of signal data is
indicative of the absence of any humans in said detection area; creating a
baseline signal profile
for wireless communications from said second transceiver to said first
transceiver based at least
in part on said properties of said second set of wireless signals in said
second set of signal data
when the absence of any humans in in said detection area is inferred; said
first transceiver
receiving a third set of wireless signals from said second transceiver; said
computer server
receiving a third set of signal data from said first transceiver, said third
set of signal data
comprising data about properties of said third set of wireless signals;
determining whether said
third set of signal data is indicative of the presence of a human, or absence
of any humans, in
59
7615577
Date Recue/Date Received 2022-07-04
said detection area, said determining based at least in part a comparison of
said third set of
signal data to said detection signal profile and said baseline signal profile.
[0167] In a further embodiment, the method comprises: in said inferring that
said first set of
signal data is indicative of the presence of a human in said detection area,
said inferring is based
at least in part on additional signal data sets for signals received by said
first transceiver from
other transceivers in the detection area; and in said inferring that said
second set of signal data
is indicative of the absence of any humans in said detection area, said
inferring is based at least
in part on additional signal data sets for signals received by said first
transceiver from other
transceivers in the detection area.
[0168] In a further embodiment, the method comprises: said computer server
storing a plurality
of historical data records indicative of whether a human was determined to be
present in said
detection area over a period of time, each of said historical data records
comprising an
indication of a number of humans determined to be present in said detection
area and a date
and time when each of said number of humans was determined to be present in
said detection
area; and said computer server making at least some of said plurality of
historical data records
available to one or more external computer systems via an interface.
[0169] In a further embodiment, the method comprises: said computer server is
operatively
coupled to a second system; and only after said computer server determines a
human is present
in said detection area, said computer server operates said second system.
[0170] In a further embodiment, the method comprises: said first transceiver
and said second
system are configured to communicate using an identical communication
protocol.
[0171] In a further embodiment, the method comprises: said second system is
selected from
the group consisting of: an electrical system; a lighting system; a heating,
venting, and cooling
(HVAC) system; a security system; and, an industrial automation system.an
electrical system.
7615577
Date Recue/Date Received 2022-07-04
[0172] In a further embodiment, the method comprises: said wireless
communication utilizes
a protocol selected from the group consisting of: BluetoothTM, BluetoothTM Low
Energy, ANT,
ANT+, WiFi, Zigbee, Thread, and Z-Wave.
[0173] In a further embodiment, the method comprises: said wireless
communications from
said second transceiver to said first transceiver have a carrier frequency in
the range of 850
MHz and 17.5 GHz inclusive.
[0174] In a further embodiment, the method comprises: said computer server
determining
whether said third set of signal data is indicative of the presence of a human
includes a
confidence metric.
[0175] In a further embodiment, the method comprises: said first transceiver
and said second
transceiver are configured to calculate their relative positions within said
detection area
automatically.
[0176] In another embodiment, the method comprises a method for estimating the
number of
humans present in an area comprising: providing a first transceiver disposed
at a first location
within a detection area; providing a second transceiver disposed at a second
location within
said detection area; a computer server communicably coupled to said first
transceiver; said first
transceiver receiving a first set of wireless signals from said second
transceiver when no
humans are present within said detection area; said computer server receiving
a first set of
signal data from said first transceiver, said first set of signal data
comprising data about
properties of said first set of wireless signals; said computer server
creating a baseline signal
profile for wireless communications from said second transceiver to said first
transceiver, said
baseline signal profile being based at least in part on said properties of
said first set of wireless
signals in said first set of signal data when no humans are present in said
detection area; said
first transceiver receiving a second set of wireless signals from said second
transceiver when a
first plurality of humans is present in said detection area, said first
plurality of humans having
61
7615577
Date Recue/Date Received 2022-07-04
a total mass; said computer server receiving a second set of signal data from
said first
transceiver, said second set of signal data comprising data about properties
of said second set
of wireless signals; said computer server creating a second baseline signal
profile for wireless
communications from said second transceiver to said first transceiver, said
second baseline
signal profile being based at least in part on said properties of said second
set of wireless signals
in said second set of signal data when said first plurality of humans is
present in said detection
area; said first transceiver receiving a third set of wireless signals from
said second transceiver
when a second plurality of humans is present within said detection area; said
computer server
receiving a third set of signal data from said first transceiver, said third
set of signal data
comprising data about properties of said third set of wireless signals; said
computer server
estimating the total mass of said second plurality of humans, said estimating
based at least in
part on a comparison of said properties of said third set of wireless signals
in said third set of
wireless signal data to said baseline signal profile and to said baseline
signal profile; said
computer server estimating the total number of humans in said plurality of
humans based at
least in part on dividing said estimated total mass of said plurality of
humans by an average
mass per human.
[0177] In a further embodiment, the method comprises: said computer server
estimating the
total mass of said second plurality of humans is further based at least in
part on a comparison
of said properties of said third set of wireless signals in said third set of
wireless signal data to
said properties of said second set of wireless signals in said second set of
wireless signal data.
[0178] In a further embodiment, the method comprises: said properties of said
first set of
wireless signals, said second set of wireless signals, and said third set of
wireless signals
comprise wireless network signal protocol properties deteunined by said first
transceiver.
62
7615577
Date Recue/Date Received 2022-07-04
[0179] In a further embodiment, the method comprises: each of said wireless
network signal
protocol properties is selected from the group consisting of: received signal
strength, latency,
and bit error rate.
[0180] In a further embodiment, the method comprises: said computer server
estimating
comprises interpolating the total mass of humans in said second plurality of
humans.
[0181] In a further embodiment, the method comprises: said interpolating uses
an assumed
mass of zero for said baseline signal profile and said total mass of humans in
said first
plurality of humans for said second baseline signal profile.
[0182] In a further embodiment, the method comprises: said total mass is a
discrete user-
supplied quantity.
[0183] T In a further embodiment, the method comprises: said average mass per
human is a
discrete user-supplied quantity.
[0184] In a further embodiment, the method comprises: said computer server
storing a plurality
of historical data records indicative of whether a human was present in the
detection area over
a period of time, each of said historical data records comprising an
indication of a number of
humans detected in said detection area and a date and time when each of said
number of humans
was detected in said detection area; and said computer server making at least
some of said
plurality of historical data records available to one or more external
computer systems via an
interface.
[0185] In a further embodiment, the method comprises: said computer server
estimating the
total mass of said second plurality of humans is adjusted based on machine
learning comprises:
determining a first sample total mass of a plurality of humans having a
fiducial element in said
detection area, said first sample mass being deteimined based upon detecting
said fiducial
element; determining a second sample total mass of said plurality of humans in
said detection
area, said second sample mass being determined based at least in part on a
comparison of said
63
7615577
Date Recue/Date Received 2022-07-04
received second set of signal data to said baseline signal profile; comparing
said first sample
mass and said second sample mass; and adjusting said estimation of said total
mass of said
second plurality of humans based upon said comparing.
[0186] In a further embodiment, the method comprises: said computer server
estimating the
total mass of said second plurality of humans is adjusted based on machine
learning comprises:
determining a first sample total mass of a plurality of humans based on
inferences in said
detection area; determining a second sample total mass of a plurality of
humans in said
detection area, said second sample mass being determined based at least in
part on a comparison
of said received second set of signal data to said baseline signal profile;
comparing said first
sample mass and said second sample mass; and adjusting said determination of
said second
sample mass based upon said comparing.
[0187] In a further embodiment, the method comprises: said determining a first
sample location
of a human based on inference in said detection area comprises said computer
server infening
from a detected operation of a network element in said detection area that a
human is present
in said detection area near said network element.
[0188] In a further embodiment, the method comprises: said network component
is a
component of an electrical system, a lighting system, a heating, venting, and
cooling (HVAC)
system, a security system, or an industrial automation system.
[0189] In a further embodiment, the method comprises: n said estimating the
total number of
humans in said plurality of humans includes a confidence metric.
[0190] In a further embodiment, the method comprises: said first transceiver
and said second
transceiver are configured to calculate their relative positions within said
detection area
automatically.
64
7615577
Date Recue/Date Received 2022-07-04
[0191] In a further embodiment, the method comprises: said wireless
communication utilizes
a protocol selected from the group consisting of: BluetoothTM, BluetoothTM Low
Energy,
ANT, ANT+, WiFi, Zigbee, Thread, and Z-Wave.
[0192] In a further embodiment, the method comprises: said wireless
communications from
said second transceiver to said first transceiver have a carrier frequency in
the range of 850
MHz and 17.5 GHz inclusive.
[0193] While the invention has been disclosed in conjunction with a
description of certain
embodiments, including those that are currently believed to be preferred
embodiments, the
detailed description is intended to be illustrative and should not be
understood to limit the scope
of the present disclosure. As would be understood by one of ordinary skill in
the art,
embodiments other than those described in detail herein are encompassed by the
present
invention. Modifications and variations of the described embodiments may be
made without
departing from the spirit and scope of the invention.
7615577
Date Recue/Date Received 2022-07-04