Note: Descriptions are shown in the official language in which they were submitted.
CARD VERIFICATION SYSTEM
Technical Field
[0001] The present invention relates to a card verification system.
Background
[0002] In recent years, card settlements using credit cards, electronic money
cards, debit cards,
etc. have increased. With the increase of card settlements, however, damage
caused by skimming
has also increased. Particularly, in the case of credit cards, since credit
approval is given, damage
is less likely to be detected unless the credit limit has been exceeded. The
damage may be often
found only after the credit card statement, sent after the fact, is checked.
Prior Art Documents
[0003] Patent Documents
[0004] Patent Document 1: Japanese Unexamined Patent Application Publication
(Translation
of PCT Application) No. 2002-508550
[0005] Patent Document 1: Japanese Unexamined Patent Application Publication
(Translation
of PCT Application) No. 2002-537619
Summary
[0006] If skimming damage is noticed at the time of statement checking and if
the damage is
reported to the police thereafter, there is some period of time between the
use of a fraudulent card
and the start of investigation. Accordingly, a salesperson subject to the
fraud may not be able to
recount events fully, and/or security camera footage may be often erased.
Therefore, more
effective investigation methods are currently required in order to reduce
skimming crimes. Even
though card information is skimmed, if a fraudulent card created based on the
skimmed card
information can be made unavailable, the card company or the cardholder will
not sustain any
actual damage. Accordingly, an authentication method other than a PIN number,
or other
authentication methods vulnerable to skimming, is required.
[0007] The present invention has been made in view of such a situation, and a
purpose thereof
is to provide a technique for reducing damage caused by card skimming.
1
Date recue/Received Date 2020-04-06
[0008] One aspect of the card verification system of the present invention
includes: a
card/mobile terminal relation information storage unit for storing
associations between settlement-
use card information and mobile terminal device information; an authentication
request receiving
unit for receiving an authentication request from a settlement system that has
received a settlement
request from a card reading terminal device; a mobile terminal information
retrieval unit for, based
on the card information included in the authentication request, retrieving
information of the mobile
terminal device associated with the card information from the card/mobile
terminal relation
information storage unit; a check request notification unit for notifying the
mobile terminal device
of the check request based on the retrieved information of the mobile terminal
device; a check
result receiving unit for receiving, based on a user operation on the mobile
terminal device, a check
result including approval or non-approval of settlement from the mobile
terminal device; an
authentication unit for determining, based on the received check result,
whether to authenticate the
settlement for which the authentication request was received; and an
authentication result
notification unit for notifying the settlement system of the authentication
result from the
authentication unit.
[0009] Another aspect of the present invention is also a card verification
system. This card
verification system includes a fraud detection-use card information storage
unit for storing card
information whose next use will be regarded as an illegal use; and an illegal
use information
notification unit for notifying a predetermined information system with card
illegal use
information including a usage location of a fraudulent card when the card
information referenced
by the settlement system that received the settlement request from the card
reading terminal device
matches the card information registered in the fraud detection-use card
information storage unit.
[0010] Optional combinations of the aforementioned constituting elements, and
implementations of the present invention in the form of methods, apparatuses,
systems, recording
media, and computer programs may also be practiced as additional modes of the
present invention.
[0011] According to the present invention, it is possible to reduce the damage
caused by card
skimming.
Brief Description of the Drawings
[0012] Fig. 1 is a block diagram that shows a configuration of a card
settlement system according
to a first embodiment of the present invention;
2
Date recue/Received Date 2020-04-06
[0013] Fig. 2 is a block diagram that shows a configuration of a card reading
terminal device
shown in Fig. 1;
[0014] Fig. 3 is a block diagram that shows a configuration of a settlement
system shown in Fig.
1;
[0015] Fig. 4 is a block diagram that shows a configuration of a card
verification system shown
in Fig. 1;
[0016] Fig. 5 is a view of an example of card information/mobile terminal
information
association table configured in the card/mobile terminal association
information storage unit;
[0017] Fig. 6 is a block diagram that shows a configuration of a mobile
terminal device shown
in Fig. 1;
[0018] Fig. 7 is a view of a settlement check screen displayed on the mobile
terminal device;
[0019] Fig. 8 is a flowchart that shows a procedure of processing performed in
the card
settlement system according to the embodiment;
[0020] Fig. 9 is a view of an example of a card/mobile terminal information
relation table
configured in the card/mobile terminal relation information storage unit
according to modification
example 1 of the first embodiment;
[0021] Fig. 10 is a view of an example of card/mobile terminal information
relation table
configured in the card/mobile terminal relation information storage unit
according to modification
example 2 of the first embodiment;
[0022] Fig.11 is a block diagram that shows a configuration of a card
settlement system
according to a second embodiment of the present invention;
[0023] Fig. 12 is a block diagram that shows a configuration of a settlement
system according
to the second embodiment;
[0024] Fig. 13 is a view of an example of an affiliated shop information table
provided in an
affiliated shop information storage unit of the settlement system according to
the second
embodiment;
[0025] Fig. 14 is a block diagram that shows a configuration of the card
verification system
according to the second embodiment;
[0026] Fig. 15 is a diagram that shows an example of a detection information
table provided in
a detection-use card information storage unit of the card verification system
according to the
second embodiment;
3
Date recue/Received Date 2020-04-06
[0027] Figs. 16(a)-(d) are diagrams that each show an example of a message
displayed on a
display unit of the card reading terminal device;
[0028] Fig. 17 is a flowchart that shows a procedure of processing performed
in the card
settlement system according to an embodiment; and
[0029] Fig. 18 is a block diagram that shows a configuration of a card
verification system
dedicated to criminal investigation using a fraudulence detection card.
Detailed Description
[0030] In recent years, damage to credit cards caused by skimming has become
widespread.
[0031] Because the card is in hand. the victim notices the skimming damage
only after receiving
a credit card statement. Unlike pickpocketing or robbery skimming is noticed
after a period of
time. causing delay. Also, it is extremely difficult for the victim to
identify the place where the
damage occurred.
[0032] Major methods of skimming crimes are as follows: installing a skimming
device on an
automatic teller machine 15 (ATM) to read card information and stealing its
password or pin using
a miniature camera or a dummy numeric keypad; and having a staff member of a
business, such
as a restaurant or a hotel, illegally steal card information while the staff
member handles the card.
[0033] Credit card authentication is generally performed by allowing the user
to sign or to enter
a password. However, the signature or password is often stolen concurrently
with the skimming
of card information. The crime of skimming is difficult to detect and hence is
a crime where the
criminal is difficult to track down and arrest. The type of such a criminal
group is called a "hit-
and-run" type. and the criminal group operates while moving from place to
place; accordingly,
even if damage can be promptly detected, finding and arresting the criminal
will be difficult. Also,
such a criminal group forms a hierarchy with the leader at the top; the role
of stealing card
information, and the role of actually using a fraudulent card, performed by
withdrawers. is at the
bottom of the hierarchy. As such, even if a withdrawer can be caught, it will
be difficult to reach
the leader of the group. Therefore, through conventional police stakeouts or
prompt detection of
skimming devices, it is difficult to eliminate skimming crimes. As follows, a
card settlement
system 1 for enabling a new investigation method effective for detection of
skimming crimes is
described as an embodiment.
4
Date recue/Received Date 2020-04-06
[0034] Fig. 1 is a block diagram that shows a configuration of a card
settlement system 1
according to an embodiment of the present invention. In the card settlement
system 1 according to
an embodiment. a settlement system 20, a card verification system 10, a card
reading terminal
device 30, and a mobile terminal device 40 are used. Also, the card settlement
system 1 works in
cooperation with a police information system 50. Further, the card settlement
system 1 works in
cooperation with a security camera 60 installed in an affiliated shop, as
needed. The card
verification system 10, card reading terminal device 30, and mobile terminal
device 40 are
connected to one another via a network 2. The network 2 represents a
communication channel, and
the communication medium or protocol thereof is not limited; however, a high-
security
communication protocol, such as SSL communication, should be desirably used.
[0035] The card reading terminal device 30 is a terminal device provided with
a function to read
information of a card 3 presented or inserted by a cardholder. For example,
the card reading
terminal device 30 may be a cash register connected to a card reader, an ATM,
a handy terminal,
or a tablet terminal with a card reader provided externally. In the
description of the embodiment.
it is mainly assumed to be a cash register connected to a card reader. With
this type of the card
reading terminal device 30, a salesperson receives a card 3 from a customer
and inserts the card 3
into the card reader, so that the card information is transferred into the
cash register.
[0036] Fig. 2 is a block diagram that shows a configuration of the card
reading terminal device
30 shown in Fig. 1. The card reading terminal device 30 comprises a 20 control
unit 31, a memory
unit 32, a communication unit 33, a display unit 34, an operation unit 35, a
card reading unit 36,
and a printing unit 37. Card information read by the card reading unit 3 6
from a card 3 is output
to the control unit 31 . The control unit 31 connects to the network 2 via the
communication unit
33 and notifies the settlement system 20 of a settlement request. The control
unit 31 conveys the
settlement request at least including the card information read by the card
reading unit 36 and
affiliated shop information retrieved from the memory unit 32.
[0037] Fig. 3 is a block diagram that shows a configuration of the settlement
system 20 shown
in Fig. 1. The settlement system 20 is provided in a data center of a card
company or of a system
operation company commissioned by a card company. The settlement system 20
generally consists
of multiple servers. Also, the settlement system 20 may be constituted by
servers installed in
multiple locations connected by cloud computing.
Date recue/Received Date 2020-04-06
[0038] The settlement system 20 comprises a control unit 21, a memory unit 22,
a
communication unit 23, a display unit 24, an operation unit 25, and an issuing
unit 26. The 15
control unit 21 includes a settlement request receiving unit 211, a card
validity judgment unit 212,
an authentication request notification unit 213, an authentication result
receiving unit 214, a
settlement judgment result notification unit 215, a detection-use card
information generating unit
20 216, a detection-use card information notification unit 217, an affiliated
shop information
notification unit 218, and an instruction transfer unit 219. Fig. 3 only shows
the functional blocks
of the control unit 21 related to the processes featured in the embodiment.
The functions of the
control unit 21 can be implemented by cooperation between hardware resources
and software
resources or only by hardware resources. As hardware resources, processors,
ROMs, RAMs, LSIs,
or the likes can be employed. As software resources. operating systems,
applications, and other
programs can be employed. The memory unit 22 may be constituted by an HDD or
SSD, for
example, and includes a card information storage unit 221 and an affiliated
shop information
storage unit 222. Fig. 3 also only shows the functional blocks of the memory
unit 22 related to the
processes featured in the embodiment.
[0039] Fig. 4 is a block diagram that shows a 10 configuration of the card
verification system
shown in Fig. 1. The card verification system 10 may be possessed by another
entity instead of
a card company or by a card company itself. The card verification system 10 is
also provided in a
data center of the owner or of a system operation company commissioned by the
owner. The card
verification system 10 generally consists of multiple servers. Also, the
settlement system 20 and
card verification system 10 may be unified and integrally operated.
[0040] The card verification system 10 comprises a control unit 11, a memory
unit 12, a
communication unit 13, a display unit 14, and an operation unit 15. The
control unit 11 includes
an authentication request receiving unit 111, a mobile terminal information
retrieval unit 112, a
check request notification unit 113, a check result receiving unit 25 114, an
authentication unit
115, an authentication result notification unit 116, a detection-use card
information receiving unit
117, a detection-use card information comparison unit 118, an affiliated shop
information
acquisition unit 119, an illegal use information notification unit 1110, a
card preservation
instruction issuing unit 1111, a message generating unit 1112, a message
display instruction
issuing unit 1113, and a video preservation instruction issuing unit 1114.
Fig. 4 also only shows
the functional blocks of the control unit 11 related to the processes featured
in the embodiment.
6
Date recue/Received Date 2020-04-06
The functions of the control unit 11 can be implemented by cooperation between
hardware
resources and software resources or only by hardware resources. The memory
unit 12 may be
constituted by an HDD or SSD, for example, and includes a card/mobile terminal
relation
information storage unit 121 and a detection-use card information storage unit
122. Fig. 4 also
only shows the functional blocks of the memory unit 12 related to the
processes featured in the
embodiment.
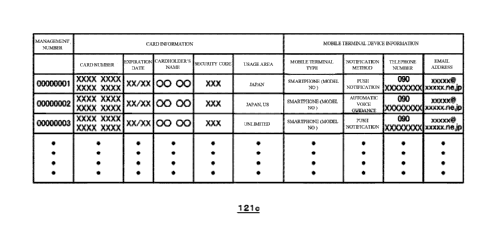
[0041] Fig 5. is a view of an example of card information/mobile terminal
information relation
table configured in the card/mobile terminal relation information storage
unit. A detailed
explanation is provided in later section.
[0042] Fig. 5 is a block diagram that shows a configuration of the mobile
terminal device 40
shown in Fig. 1. The mobile terminal device 40 is a terminal device carried by
a holder of a card
3. For the mobile terminal device 40, a smartphone, a feature phone, a tablet,
a portable music
player, or a portable game device may be used, for example. Since a
communication function is
required in the embodiment, when a tablet, a portable music player, or a
portable game device is
used, such a device needs to be used with a SIM card inserted thereto or while
being connected to
an access point of a wireless LAN.
[0043] The mobile terminal device 40 comprises a control unit 41, a memory
unit 42, a
communication unit 43, an antenna 43a, a display unit 44, an operation unit
45, an imaging unit
46, and a GPS receiving unit 47. The following describes the processing of
embodiment 1 with
reference to Figs. 1 to 6.
[0044] The settlement request receiving unit 211 of the settlement system 20
receives a
settlement request from the card reading terminal device 30 via the network 2.
The card validity
judgment unit 212 determines whether the card information included in the
settlement request is
valid (S20). Specifically, the card information of the used card 3 is read
from the card information
storage unit 221, and the card validity judgment unit 212 checks whether or
not the expiration date
of the used card 3 has passed, and the like. When the used card 3 is not
valid, the settlement
judgment result notification unit 215 notifies the card reading terminal
device 30 of settlement
refusal. When the used card 3 is valid, the authentication request
notification unit 213 notifies the
card verification system 10 of the authentication request concerning the
received settlement
request via the network 2. The authentication request includes at least the
card information
included in the settlement request received from the card reading terminal
device 30.
7
Date recue/Received Date 2020-04-06
[0045] The authentication request receiving unit 111 of the card verification
system 10 receives
the authentication request from the settlement system 20. Based on the card
information included
in the authentication request, the mobile terminal information retrieval unit
112 reads the
information of the mobile terminal device 4 associated with the card
information from the
card/mobile terminal relation information storage unit 121.
[0046] The card/mobile terminal relation information storage unit 121 holds
the information of
the card 3 and the information of the mobile terminal device 40 in association
with each other. In
the example shown in FIG. 5, the card number, expiration date, cardholder's
name, and security
code are stored as the information of the card 3. These pieces of card
information are provided in
advance by a card company that uses the service provided by the card
verification system 10.
[0047] In the example shown in FIG. 5, mobile terminal type, notification
method, telephone
number, and email address are stored as the information of the mobile terminal
device 40. These
pieces of mobile terminal information are provided in advance by a card
company that uses the
service provided by the card verification system 10. When a contract with a
card user is agreed,
the card company registers mobile terminal information to be used for
authentication. The card
company may make authentication using a mobile terminal device 40 mandatory or
make it
optional.
[0048] Many card users will select a smartphone or feature phone as the mobile
terminal device
40 to register. Methods of notifying the mobile terminal device 40 at the time
of authentication
include email, SMS (Short Message Service), and voice guidance. In the case of
email or SMS,
the push notification service provided by the telecommunications carrier or OS
vendor is used.
With the push notification service, even when the relevant application has not
been launched on
the mobile terminal device 40, provided that the mobile terminal device 40 is
powered on, the
settlement check screen can be displayed on the display unit 44.
[0049] People who are not accustomed to handling a mobile terminal device 40
can use voice
guidance. In the case of voice guidance, a call is made to the mobile terminal
device 40 at the time
of authentication, and the user selects the numbers on the operation unit 45
according to the
automatic voice guidance.
[0050] The check request notification unit 113 of the card verification system
10 notifies the
mobile terminal device 40 of the check request based on the information of the
mobile terminal
device 40 read by the mobile terminal information retrieval unit 112. For
example, the telephone
8
Date recue/Received Date 2020-04-06
number of the mobile terminal device 40 is sent to the server of the OS
vendor, and a push
notification to the mobile terminal device 40 is requested. Upon receiving a
check request
concerning a card settlement from the card verification system 10, the control
unit 41 of the mobile
terminal device 40 displays a settlement check screen.
[0051] Fig. 7 is a view of a settlement check screen 44a displayed on the
mobile terminal device.
On the settlement check screen 44a shown in Fig 7, a product name, a
settlement amount, an OK
key 44b, and a NO key 44c are displayed. When the user hands the card 3 to the
shop worker to
pay at the cash register, the settlement check screen 44a is displayed on the
mobile terminal device
40 held by the user. The user checks the content of the settlement check
screen 44a and presses
the OK key 44b or the NO key 44c. In this example, use of a touch panel
display in which the
display unit 44 and the operation unit 45 are integrated is assumed. In the
case of a feature phone,
the intention of the user as to whether to approve or reject is input using
physical keys provided
on the operation unit 45.
[0052] Based on the user operation performed on the operation unit 45, the
control unit 41
notifies the card verification system 10 of the check result including an
approval or non-approval
of the settlement by the user via the network 2. The check result receiving
unit 114 of the settlement
system 20 receives the check result from the mobile terminal device 40. Based
on the received
check result, the authentication unit 115 determines whether to authenticate
the settlement for
which the authentication request was received. In the simplest design, when
the check result from
the portable terminal device 40 is an approval, the authentication is
determined to have been
successful, and when the check result is rejected, the authentication is
determined to have failed.
The authentication result notification unit 116 notifies the settlement system
20 of the
authentication result.
[0053] The authentication result receiving unit 214 of the card verification
system 20 receives
the authentication result from the settlement system 10. The settlement
judgment result notification
unit 215 notifies the card reading terminal device 30 of the authentication
result received from the
card verification system 10 via the network 2. The control unit 31 of the card
reading terminal
device 30 causes the display unit 34 to display the authentication result.
[0054] Fig. 8 is a flowchart showing the flow of processing of the card
settlement system 1
according to the first embodiment. The card reading unit 36 of the card
reading terminal device 30
9
Date recue/Received Date 2020-04-06
reads the card information when the card 3 is inserted (S30), and the control
unit 31 passes the
settlement request including the retrieved card information to the settlement
system 20 (S31).
[0055] The card validity judgment unit 212 determines whether the card
information included
in the settlement request is valid (S20). When the used card 3 is not valid (N
in S20), the settlement
judgment result notification unit 215 notifies the card reading terminal
device 30 of settlement
refusal. When it is valid (Y in S20), the authentication request notification
unit 213 notifies the
card verification system 10 of the authentication request (S21).
[0056] The mobile terminal information retrieval unit 112 of the card
verification system 10
reads the information of the mobile information associated with the card
information relating to
the authentication request from the card/mobile terminal relation information
storage unit 121
(S10). The check request notification unit 113 notifies the registered mobile
terminal device 40 of
the check request based on the mobile terminal device information.
[0057] Upon receiving the check request, the control unit 41 of the mobile
terminal device 40
displays the settlement check screen (S40). The control unit 41 of the mobile
terminal device 40
receives an operation of approving or rejecting settlement from the user via
the operation unit 45
(S41) and notifies the card verification system 10 of the check result
reflecting the operation of the
user (S42).
[0058] The authentication result notification unit 116 of the card
verification system 10 notifies
the settlement system 20 of the authentication result based on the check
result. When
authentication is successful (Y in S22), the settlement judgment result
notification unit 215 of the
settlement system 20 notifies the card reading terminal device 30 of
settlement approval (S23).
When authentication fails (N in S22), the settlement result notification unit
215 notifies the card
reading terminal device 30 of settlement refusal (S24).
[0059] As described above, according to the first embodiment, even if card
information is
skimmed, illegal use can be prevented if the registered mobile terminal device
40 itself is not
stolen. In the event that the email address or telephone number is disclosed
but the registered
mobile terminal device 40 is still in the hands of the legitimate cardholder,
he or she will notice
the illegal use at the point when illegal use of the skimmed card information
is attempted.
Accordingly, damage due to skimming can be reduced.
[0060] Since users commonly carry around their mobile terminal device 40, this
does not
significantly reduce the convenience of the card user. Rather, in comparison
to signing or entering
Date recue/Received Date 2020-04-06
a PIN number, the burden on the user is reduced (one touch of the screen in
sufficient). Moreover,
if the authentication method according to Embodiment 1 is adopted, a reduction
in losses due to
skimming damage can be anticipated and thus the fees paid by the card company
to the insurance
company may be reduced. The card company can return these savings to the
cardholder in the form
of points. Thus, cardholders can be given the incentive of a higher point
return rate if they employ
this authentication method. As such, cardholders can be expected to actively
adopt this
authentication method.
[0061] A modification example of the first embodiment is described below. In
the above
description, it is assumed that the cardholder and the owner of the registered
mobile terminal
device 40 are the same person, but this need not be the case. For example, the
owner of the
cardholder may be a wife and the owner of the mobile terminal device 40 may be
a husband.
Alternatively, these roles may be reversed. Further, the cardholder may be an
elderly person or
minor, and the owner of the mobile terminal device 40 may be a carer (i.e.
child, parent or
guardian). Moreover, information of a plurality of mobile terminal devices 40
may be linked to
the information of a single card 3.
[0062] Fig. 9 is a is a view of an example of a card/mobile terminal
information relation table
121b configured in the card/mobile terminal relation information storage unit
121 according to
modification example 1 of the first embodiment. For the data of management
number 00000001
in the card/mobile terminal information relation table 121b shown in FIG. 9,
the information of
two mobile terminal devices 40 is associated with the information of one card
3.
[0063] In the modification example 1, when the information of card 3 included
in the
authentication request from the settlement system 20 is associated with the
information of a
plurality of mobile terminal devices 40, the check request notification unit
113 of the card
verification system 10 notifies each of the mobile terminal devices 40 of the
check request. The
authentication unit 115 determines that the authentication is successful when
the check result
receiving unit 114 has received check results of approval from all of the
plurality of mobile
terminal devices 40, and determines that the authentication has failed if a
check result of non-
approval is received from any one or more of the plurality of mobile terminal
devices 40.
[0064] According to the modification example 1, illegal use of the card 3 can
be prevented as
long as the registered plurality of mobile terminal devices 40 are not all
stolen. Thus, security can
11
Date recue/Received Date 2020-04-06
be further enhanced. It is also possible to flexibly incorporate rules for the
handling of cards within
a family into the system.
[0065] Fig. 10 is a is a view of an example of a card/mobile terminal
information relation table
121c configured in the card/mobile terminal relation information storage unit
121 according to
modification example 2 of the first embodiment. In modification example 2, the
card information
includes a usage area for card 3. Since card information is electronic data,
it can easily be spread
all over the world via the Internet. Thus, it is often the case that the
country where the skimming
occurred, and the country of illegal use are different. The cardholder can
register the country in
which the card 3 is to be used with the card company in advance. Note also
that the usage area is
not limited to specific countries. A wider area, such as the EU, or a narrow
area, such the Tokyo
metropolitan area, may also be set.
[0066] In modification example 2, the authentication unit 115 of the card
verification system 10
compares the usage area of the card 3 included in the authentication request
received from the
settlement system 20 with the usage area the card registered in the
card/mobile terminal relation
information storage unit 121. If the usage area is different, the
authentication fails. In the
modification example 2, it is preferable that the check request notification
unit 113 notifies the
mobile terminal device 40 with a check request including the area where the
card 3 was used.
[0067] Thus, according to the modification example 2, it is possible to reduce
the risk of
skimmed card information being illegally used overseas. Other usage method are
possible, such as
restricting the area where a child uses the card 3 to the area where the child
lives.
[0068] In modification example 3, whether or not to use this authentication
method is determined
according to the settlement amount. The authentication request notification
unit 213 of the
settlement system 20 notifies the card verification system 10 of the
authentication request when
the settlement amount included in the settlement request from the card reading
terminal device 30
is equal to or more than a set amount (for example, 10,000 yen). When the
settlement amount is
less than the set amount, notification of the authentication request is not
performed. When the
settlement amount is less than the set amount, authentication in the
conventional way with a
signature or pin number, or no authentication is selected.
[0069] With modification example 3, it is possible to achieve a balance
between security and
convenience. Particularly, in modification example 1, since multiple user
approvals are required,
it possible to imagine cases where card payment is not possible due to the
user being unable to
12
Date recue/Received Date 2020-04-06
obtain all the approvals in short time. By contrast, modification example 3
ensures convenience
by employing conventional authentication methods in the case of the payment of
small amounts.
[0070] In modification example 4, when a payment is made on the operation unit
45 of the
mobile terminal device 40, position information generated by the GPS receiving
unit 47 is used in
addition to the user operation to determine whether or not to approve
settlement. The GPS
receiving unit 47 receives radio waves from a plurality of satellites,
specifies the latitude and
longitude at which the mobile terminal device 40 is located and generates
position information.
The control unit 41 notifies the card verification system 10 of the position
information generated
by the GPS receiving unit 47 in addition to the check result including the
approval or non-approval
of the settlement by the user.
[0071] The authentication unit 115 of the card verification system 10
determines whether or not
the position information of the affiliated shop in which the card 3 is used
substantially matches the
position information received from the mobile terminal device 40. If the check
result by the user
is approval and the position information substantially matches, the decision
is successful
authentication. In any other case, the decision is authentication failure. In
modification example 4,
the affiliated shop information including the position information of the
affiliated shop is included
in the authentication request from the settlement system 20.
[0072] As described above, according to modification example 4, security is
further enhanced
by preventing someone from achieving authentication by stealing the email
address of the mobile
terminal device 40 and intercepting the check email. Note also that an
arrangement is possible
whereby authentication can be achieved when there is substantial agreement
between the position
information of the affiliated shop and the position information of the mobile
terminal device 40
without requiring the user to approve or reject settlement. Since no operation
by the user is needed,
this arrangement improves convenience. It is particularly effective as an
authentication method for
the settlement of small amounts. When the settlement amount is equal to or
more than the set
amount (for example, 10, 000 yen), the settlement check by the above-described
user operation
may be selected, and when it is less than the set amount, the check by
matching of the above-
described position information may be selected.
[0073] Next, a second embodiment will be described. In the first embodiment,
the main purpose
is to block illegal use based on skimmed card information. In the second
embodiment, however,
the main purpose is to detect skimming crime and thereby reduce the incidence
skimming crime
13
Date recue/Received Date 2020-04-06
itself. Skimming is difficult to detect and hence is a crime where the
criminal is difficult to track
down and arrest. Such criminal groups are called a "hit-and-run" groups, and
tend to operate while
moving from place to place. Thus, even if damage can be promptly detected,
finding and arresting
the criminal is difficult. Also, such a criminal group forms a hierarchy with
the leader at the top;
the role of stealing card information, and the role of actually using a
fraudulent card, performed
by withdrawers, is at the bottom of the hierarchy. As such, even if a
withdrawer can be caught, it
will be difficult to reach the leader of the group Therefore, it is difficult
to eliminate skimming
crimes through conventional police stakeouts or prompt detection of skimming
devices. In the
second embodiment, a card settlement system 1 for realizing a new
investigation method that is
effective for exposing skimming crime will be explained.
[0074] Fig. 11 is a flowchart showing the configuration of the card settlement
system 1
according to the second embodiment of the present invention. The card
settlement system 1
according to the second embodiment further cooperates with the police
information system 50.
Also, if necessary, it cooperates with the security camera 60 installed in the
affiliated shop.
[0075] Fig. 12 is a flowchart showing the configuration of the settlement
system 20 according
to the second embodiment. The control unit 21 of the settlement system 20
according to the second
embodiment additionally includes, in the functional block of the control unit
21 of the settlement
system 20 according to the first embodiment shown in Fig. 3, a detection-use
card information
generating unit 216, a detection-use card information notification unit 217,
an affiliated shop
information notification unit 218 and an instruction transfer unit 219.
[0076] Fig. 13 is a view of an example of an affiliated shop information table
222a provided in
an affiliated shop information storage unit 222 of the settlement system 20
according to the second
embodiment. A detailed explanation will be given in a later section.
[0077] Fig. 14 is a flowchart showing the configuration of the card
verification system 10
according to the second embodiment. The control unit 11 of the card
verification system 10
according to the second embodiment additionally includes, in the functional
block of the control
unit 11 of the card verification system 10 according to the first embodiment
shown in Fig. 5, a
detection-use card information receiving unit 117, a detection-use card
information comparison
unit 118, an affiliated shop information acquisition unit 119, a card
preservation instruction issuing
unit 1111, a message generating unit 1113 and a video preservation instruction
issuing unit 1114.
The memory unit 12 card verification system 10 according to the second
embodiment additionally
14
Date recue/Received Date 2020-04-06
includes, in the functional block of the memory unit 12 of the card
verification system 10 according
to the first embodiment shown in Fig. 5, a detection-use card information
storage unit 122.
[0078] Fig. 15 is a view of an example of detection -use information table
122a provided in
detection-use card information storage unit 122 of the card verification
system 10 according to the
second embodiment. A detailed explanation will be given in a later section.
Hereinafter, the
processing according to the second embodiment will be described with reference
to Figs. 11 to 15.
Note that descriptions common to the first embodiment will be omitted as
appropriate.
[0079] The investigative authorities request a card company to issue a card
used to detect fraud.
Accordingly, the card company creates, for example, a card of which the first
use is regarded as
normal use and of which the second or subsequent use is regarded as illegal
use (hereinafter, such
a card will be referred to as a one-time card). The one-time card has the same
appearance as a
normal card but contains different card information. The detection-use card
information generating
unit 216 of the settlement system 20 generates card information for fraud
detection according to
the request from the investigative authorities and transmits the card
information to the issuing unit
26. Accordingly, the issuing unit 26 issues a fraud detection card containing
the card information.
In the card information storage unit 221, information of a fraud detection-use
card having the same
data structure as information of a normal card is registered. The detection-
use card information
notification unit 217 then notifies the card verification system 10 of the
information of the fraud
detection-use card.
[0080] [0060]
[0081] The detection-use card information receiving unit 117 of the card
verification system 10
receives the card information from the settlement system 20 and registers the
card information in
the detection-use card information storage unit 122. As shown in Fig. 15, the
detection-use card
information includes a valid flag in addition to the items of normal card
information. The valid
flag is set to "0 (non- active)" when the detection-use card is in a normal
use mode and is set to "1
(active)" when the detection-use card is in a detection mode. In the state
where a card has not been
used since the issuance of the card, the valid flag is set to "0". Once a one-
time card is used, the
valid flag is changed from "0" to "1". Card information in which the valid
flag is "1" is information
indicating that the next use of the card will be regarded as illegal use.
[0082] After the card is used in multiple card reading terminal devices 30 to
be investigated, the
mode may be switched from the normal use mode to the detection mode. When a
card reading
Date recue/Received Date 2020-04-06
terminal device 30 assumed to be used for skimming cannot be identified, a
trap may be set by
allowing a number of card reading terminal devices 30 to read card information
of a detection-use
card. In this case, after the card information is read by multiple card
reading terminal devices 30,
the mode may be switched from the normal use mode to the detection mode.
[0083] In the following, it will be assumed as an example that a different one-
time card is used
for each card reading terminal device 30 to be investigated. In this case, the
place where skimming
occurred can be uniquely identified. The issued one-time cards are distributed
to investigators of
the investigative authorities. By identifying a shop or an ATM used by
multiple skimming victims,
the investigative authorities can identify a candidate of shops and ATMs with
a strong possibility
of being used for skimming. There is also a case where a candidate of shops
and ATMs with a
strong possibility of being used for skimming can be identified based on
information provided by
a citizen or an insider.
[0084] An investigator uses a one-time card at a shop or an ATM with a strong
possibility of
being used for skimming. Specifically, the investigator allows the card
reading terminal device 30
that is to be investigated to read the card information of the one-time card.
The settlement request
receiving unit 211 of the settlement system 20 receives from the card reading
terminal device 30a
settlement request including the card 20 information of the one-time card. The
card validity
judgment unit 212 then judges the validity of the card information included in
the settlement
request. In the card information storage unit 221, card information of a one-
time card is also
registered in a data structure same as that of normal card information.
Accordingly, the card
validity judgment unit 212 judges the card information of the one-time card to
be valid.
[0085] The authentication request notification unit 213 notifies the card
verification system 10
of an authentication request including the card information of the one-time
card. Accordingly, the
authentication request receiving unit 111 of the card verification system 10
receives the
authentication request from the settlement system 20. The detection-use card
information
comparison unit 118 then compares the card information with detection-use card
information
stored in the detection-use card information storage unit 122. When it is card
information of a one-
time card, there is card information identical therewith in the detection-use
card information
storage unit 122.
[0086] Accordingly, the detection-use card information comparison unit 118
retrieves the
identical detection-use card information from the detection-use card
information storage unit 122
16
Date recue/Received Date 2020-04-06
and checks the valid flag therein. When the valid flag is "0", the flag is
changed to "1" and the
information in the detection-use card information storage unit 122 is
overwritten accordingly.
After the valid flag is changed to "1", normal authentication processing is
performed for the
authentication request. When the valid flag is "1", in order to acquire
detailed information of the
affiliated shop, the affiliated shop information acquisition unit 119 notifies
the settlement system
20 of an acquisition request for acquiring the affiliated shop information.
[0087] Accordingly, the affiliated shop information notification unit 218 of
the settlement
system 20 retrieves the requested affiliated shop information from the
affiliated shop information
storage unit 222 and notifies the card verification system 10 thereof. In the
second embodiment,
as affiliated shop information, investigation information for facilitating
detection of illegal use is
also registered, in addition to the basic information including an address and
a telephone number.
In the example shown in Fig. 7, the type of the reader, whether or not a card
return rejection
function is provided, whether or not a message display function is provided,
whether or not a
security camera is installed, whether or not the security camera is connected
to the network, and
the investigative cooperation level are registered as the investigation
information.
[0088] Readers can be broadly classified as being either user-operated manned
machines on the
side providing the product or service, or unattended machines operated by the
cardholder
himself/herself. A typical example of an unattended machine is an ATM. Where
the credit card
has a cashing function, it is possible to borrow up to a limit amount from the
card company by
inserting the credit card into the ATM of a financial institution. Therefore,
if the credit card
information and PIN number are stolen, there is a risk that money will be
withdrawn.
[0089] The card return refusal function is a function that is sometimes
provided in reading units
that receive either the whole or a large portion of the card into an internal
portion. For example,
some ATMs implement a function whereby if an unauthorized card such as a
counterfeit card is
inserted, the card is held internally and is not returned. It is to be noted
that the card return refusal
function is not implemented in general swipe-type reading units.
[0090] The message display function is a function for displaying information
to the user on the
side providing the product or service, on the display unit 34 of the card
reading terminal device
30. This function is basically supposed to show the shop worker a message
requesting cooperation
with an investigation.
17
Date recue/Received Date 2020-04-06
[0091] The presence or absence of a monitoring camera 60 imaging the card
reading terminal
device 30 is registered. It is also registered whether the monitoring camera
60 is connected to the
network 2 so that it can be operated remotely, or whether it is operating as a
stand-alone device.
[0092] The investigation cooperation level is the level to which an affiliated
shop will cooperate
with the card company or investigative authorities and is agreed by card
company and investigative
authorities and the affiliated shop is advance. In the description of
Embodiment 2, there are 5
levels, "5" being the highest investigation cooperation level and "1" being
the lowest. Affiliated
shops that actively cooperate in the investigation by, for example, extending
the time that a
fraudulent card user is present at the cash register or restraining the
fraudulent card user select "5"
while shops that wish to be involved to the minimum possible extent in the
investigation select
[0093] The affiliated shop information acquisition unit 119 of the settlement
system 20 acquires
the affiliated shop information from the card verification system 10. The
illegal use information
notification unit 1110 notifies, via the network 2, the police information
system 50 of the card
illegal user information including the location where the illegal card was
used, which is included
in the affiliated shop information. For example, it may notify the police
information system 50 of
the country in which the fraudulent card was used. When the police information
system 50 receives
the card illegal use information from the card verification system 10 a
request for investigation is
issued to an investigator near the location where the illegal card was used.
For example, the
investigation office with jurisdiction over the location where the fraudulent
card was used may
inform the investigators that a fraudulent card was used using police radio.
[0094] In some countries, special organizations other than police may have the
authority to
investigate card crime. In that case, card illegal use information is sent to
the organization's
information system. In addition, card illegal use information may be sent to
the information system
of a mass media organization such as a newspaper company or a television
station. Having the
mass media cover skimming crime can be anticipated to increase public interest
in it.
[0095] In the cases that the affiliated shop is described as having a card
return refusal function,
the card preservation instruction issuing unit 1111 issues a fraudulent card
preservation instruction
for instructing the card reading unit 36 of the card reading terminal device
30 to hold the inserted
card therein. The fraudulent card preservation instruction is sent to the
settlement system 20, and
the instruction transfer unit 219 notifies the card reading terminal device 30
of the fraudulent card
18
Date recue/Received Date 2020-04-06
preservation instruction. If the card reading terminal device 30 cannot be
controlled directly from
the card reading terminal device 30, the information processing system of the
financial institution
in which the card reading terminal device 30 is installed requests
preservation of the card 3 inserted
into the card reading unit 36 . Since there is a possibility that the
fraudulently used card 3 may
have fingerprints of the criminal group, such as the withdrawer etc., adhered
thereon, the fraudulent
card is retained as evidence.
[0096] When it is described in the affiliated shop information that security
cameras and a
security camera network are present, the video preservation instruction
issuing unit 1114 issues a
video preservation instruction instructing that video data captured by the
video camera 60 is to be
preserved. The video card preservation instruction is sent to the settlement
system 20, and the
instruction transfer unit 219 of the settlement system 20 notifies the control
system of the security
camera 60 of the video preservation instruction. Since the video from the
security camera 60 is
conventionally erased when a storage period expires, a request is made to
preserve at least the
images from the date and time of the illegal use. The video preservation
instruction may also
include a message requesting that the video showing the fraudulent user be
provided to the
investigative body.
[0097] If the security camera 60 is of a type that permit adjustment of the
aspects of image
quality such as the resolution and frame rates through settings, the video
preservation instruction
issuing unit 1114 may instruct the control system of the security camera 60 to
increase the image
quality of the security camera 60.
[0098] If the affiliated shop information indicates the presence of a message
display function,
the message generating unit 1112 generates a message to cause display on the
display unit 34 of
the card reading terminal device 30. The message generating unit 1112
generates a message based
on the investigative cooperation level, presence/absence of a security camera
60, presence/absence
of a security camera network connection, and the police investigation policy.
[0099] Figs. 16(a) to 16(d) are diagrams showing examples of messages
displayed on the display
unit 34 of the card reading terminal device 30. Fig. 16 (a) is an example of
the message displayed
when the investigative cooperation level is "5" and a trained security guard
or the like is employed
in the shop. On the other hand, when a standalone security camera 60 is
installed, a warning
message such as "Please do not erase the video from the camera" may be added.
In order to
conserve memory, the standalone security camera 60 overwrites images stored in
the memory after
19
Date recue/Received Date 2020-04-06
a short period of time (for example, one day). Accordingly, it is desirable to
display a warning
message indicating that the video from the security camera should be kept.
[0100] Fig. 16(b) is an example of the message displayed when the
investigative cooperation
level is "4" or "5". When no trained security guard employed, the message of
16(b) is displayed
rather than the message of 16(a), even if the investigative cooperation level
is "5". The shop worker
who sees the message of Fig. 16(b) will seek to prolong the cardholder's stay
by requesting the
entry of personal information on a form. During this time, an investigator can
approach the shop.
[0101] Note also, that rather than restraining the withdrawer, the
investigative policy might be
to follow the withdrawer and establish contact with higher-ranking members of
the organization.
In the case that such a policy is used, the message of Fig. 16(b) will be
selected over that of Fig.
16(a) even if the investigative cooperation level is "5" and a trained guard
is employed in the shop.
A particularly effective investigation method is to prearrange the presence of
an investigator in the
shop.
[0102] Fig. 16(b) is an example of the message displayed when the
investigative cooperation
level is "2" or "3". The message requests that the police are notified without
placing a significant
burden on the shop worker. At the point that the withdrawer leaves the shop,
the shop worker who
handled the transaction will clearly remember things like the facial features,
clothes, direction of
escape etc. of the withdrawer. Also, as result of the message being displayed,
the shop worker will
observe the customer more carefully. The investigating authorities can obtain
accurate and timely
information about the withdrawer and make use of it in the initial
investigation.
[0103] Fig. 16(d) is an example of the message displayed when the
investigative cooperation
level is "1" or "2". In affiliated shops that are reluctant to cooperate with
an investigation, the
transaction is handled by refusing settlement when a fraudulent card is used.
When the
investigative cooperation level is "2" and a standalone security camera 60 is
installed, a request
not to erase footage from the security camera 60 may be made.
[0104] The message display instruction issuing unit 1113 of the card
verification system 10
issues a message display instruction for instructing the display unit 34 of
the card reading terminal
device 30 to display the message generated by the message generating unit
1112. The message
display instruction is sent to the settlement system 20, and the instruction
transfer unit 219 of the
settlement system 20 passes the message display instruction to the card
reading terminal device
30.
Date recue/Received Date 2020-04-06
[0105] Fig. 17 is a flowchart showing the flow of processing of the card
payment system 1
according to the second embodiment. The card reading unit 36 of the card
reading terminal device
30 reads the card information when the card 3 for fraud-detection is inserted
(S30), and the control
unit 31 passes the settlement request including the retrieved card information
to the settlement
system 20 (S31).
[0106] The card validity judgment unit 212 determines whether the card
information included
in the settlement request is valid (S20). When the card is invalid (N in S20),
the process proceeds
to step S24 in Fig. 8. When it is valid (Y in S20), the authentication request
notification unit 213
notifies the card verification system 10 of the authentication request (S21).
[0107] The fraudulent card information comparison unit 118 of the card
verification system 10
checks whether the card information received in response to authentication
request from the
settlement system 20 matches any of the card information registered in the
detection-use card
information storage unit 122 (S13). If no matching card information exists (N
in S13), the process
proceeds to step S10 in Fig. 8. If matching card information exists (Y in
S13), the validity flag of
the matching card information is verified (S14). When the validity flag is "0"
(N in S14), the
fraudulent card information comparison unit 118 changes the validity flat from
"0" to "1" (S15).
Thereafter the process proceeds to step S10 of Fig. 8.
[0108] When the validity flag is "1" (Y in S14), the affiliated shop
information acquisition unit
119 passes an acquisition request for affiliated shop information to the
settlement system 20. Upon
receiving the acquisition request, the affiliated shop information
notification unit 218 of the
settlement system 20 reads the corresponding affiliated shop information from
the affiliated shop
information storage unit 222 and notifies the card verification system 10
(S25). The affiliated shop
information acquisition unit 119 of the settlement system 10 acquires the
affiliated shop
information sent from the settlement system 20.
[0109] The illegal use information notification unit 1110 sends the police
information system 50
the card illegal use information including the address, which is included in
the acquired affiliated
shop information. The instruction issuing unit issues an instruction to
execute a process to be
executed on the affiliated shop side at the time of fraud detection (S19), and
the instruction transfer
unit 219 of the settlement system 20 sends the issued instruction to at least
one of the card reading
terminal device 30, the shop information system, and the control system of the
security camera 60
(S26).
21
Date recue/Received Date 2020-04-06
[0110] In the above-described second embodiment, when a one-time card with the
valid flag in
the active state is used, it can be deemed that a fraudulent use of the card
was intentionally made.
A withdrawer who is aware of the circumstances can be arrested as the
principal perpetrator. If
someone unaware of the circumstances has been requested to use the card, the
person responsible
for making the request can be arrested as the indirect perpetrator.
Conventionally, when a
withdrawer used a fraudulent card, victims would not generally be aware that
they had been
skimmed and would not make a report of the fraud. Therefore, even if the
behavior of a withdrawer
seemed suspicious, under the law, it was difficult to arrest him or her as a
principal perpetrator.
[0111] The one-time card looks the same as a normal card and can be used in
the normal way
when the valid flag thereof is non-active. Accordingly, a person who illegally
obtains the card
information and PIN number of the one-time card will use them without noticing
that they are for
fraud detection.
[0112] According to the second embodiment, the investigation can be started
promptly when
illegal use occurs, and so evidence can be preserved, and the memories of any
witnesses will be
fresh. Also, if the withdrawer can be tracked, it may be possible to reach
higher-ranking members
of the criminal group.
[0113] Also, as such investigation methods become more widely known, it can be
anticipated
that people will be deterred from using fraudulent cards. There have been an
increasing number of
cases in which people conspiring to use fraudulent cards purchase skimmed card
information and
PINs on the Internet to make fraudulent cards. In this case, the shallow
nature of the connection
between the person who did the skimming and the person using the fraudulent
card makes arrest
of both difficult.
[0114] However, if the people considering use of a fraudulent card begin to
feel at risk of being
arrested when they do so, they are more likely to have second thoughts about
committing the crime.
Accordingly, it can be anticipated that demand for skimmed card information
will decrease and
sales by sellers of skimmed card information will fall. Based on this
mechanism, a gradual decrease
in the skimming crime can be expected.
[0115] The present invention has been described with reference to the
embodiments. The
embodiments are merely illustrative, and it will be obvious to those skilled
in the art that various
modifications can be made to the combinations of constituting elements and
processes and that
any such modifications also fall within the scope of the present invention.
22
Date recue/Received Date 2020-04-06
[0116] In the second embodiment, a card settlement system 1 for realizing both
an authentication
method used with a mobile terminal device and a criminal investigation using
the card fraud-
detection card 3 were described. However, a card settlement system 1 dedicated
to criminal
investigations using a fraud detection card 3 can also be configured.
[0117] Fig. 18 is a block diagram showing the configuration of a card
verification system 10
dedicated to criminal investigations using the fraud detection-use card 3. In
the card verification
system 10 shown in Fig. 18, the mobile terminal information retrieval unit
112, the check request
notification unit 113, the check result receiving unit 114, and the
authentication unit 115 in the
card verification system 10 shown in Fig. 14 are no longer necessary. Further,
rather than making
the authentication request, the settlement system 20 makes an inquiry request
as to whether or not
the card information is that of a detection-use card. Thus, in place of the
authentication request
receiving unit 111 and the authentication result notification unit 116, an
inquiry request receiving
unit 111a and an inquiry result notification unit 116a are provided.
[0118] In the above description, the card 3 is assumed to be a credit card,
but the invention is
also applicable to a bank cash card, an electronic money card, or a debit
card. In particular, by
applying the card payment system 1 according to the first embodiment to the
cash card and setting
up the system so that the settlement verification notification is sent to an
adult child's mobile
terminal device 40, it is possible to prevent bank transfer fraud aimed at
elderly parents.
[0119] Description of the reference numerals
[0120] 1 Card settlement system 20, 2 Network, 3 Card, 10 Card verification
system, 11 Control
unit, 111 Authentication request receiving unit, 111a Inquiry request
receiving unit, 112 Mobile
terminal information retrieval unit, 113 Check request notification unit, 114
Check result receiving
unit, 115 Authentication unit, 116 Authentication result notification unit,
116a Inquiry result
notification unit, 117 Detection-use card information receiving unit, 118
Detection-use card
information comparison unit, 119 Affiliated shop information acquisition unit,
1110 Illegal use
information notification unit, 1111 Card preservation instruction issuing
unit, 1112 Message
generating unit, 1113 Message display instruction issuing unit, 1114 Video
preservation
instruction issuing unit, 12 Memory unit, 121 Card/mobile terminal relation
information storage
unit, 122 Detection-use card information storage unit, 23 Communication unit,
24 Display unit, 21
Control unit, 20 Settlement system, 21 Control unit, 211 Settlement request
receiving unit, 212
Card validity judgment unit, 213 Authentication request notification unit, 214
Authentication
23
Date recue/Received Date 2020-04-06
result receiving unit, 215 Settlement judgment result notification unit, 216
Detection-use card
information generating unit, 217 Detection-use card information notification
unit, 218 Affiliated
shop information notification unit, 219 Instruction transfer unit, 22 storage
unit, 221 Card
information storage unit, 222 Affiliated shop information storage unit, 23
Communication unit, 24
Display unit, 25 Operation unit, 26 Issuing unit, 30 Card reading terminal
device, 31 Control unit,
32 Memory unit, 33 Communication unit, 34 Display unit, 35 Operation unit, 36
Card reading
unit, 37 Printing unit, 40 Mobile terminal device, 41 Control unit, 42 Memory
unit, 43
Communication unit, 43a Antenna, 44 Display unit, 45 Operation unit, 46
Imaging unit, 47 GPS
receiving unit, 50 Police information system, 60 Security camera.
[0121] Industrial applicability
[0122] The present invention can be applied in the field of credit card
settlement.
24
Date recue/Received Date 2020-04-06