Note: Descriptions are shown in the official language in which they were submitted.
CACHE SYSTEM HOTSPOT DATA ACCESS METHOD, APPARUTUS, COMPUTER
DEVICE AND STORAGE MEDIUM
Field
[0001] The present disclosure relates to the field of computer technology,
particularly to a
cache system hotspot data access method, an apparatus, a computer device, and
a storage
medium.
Background
[0002] Redis is a currently widely used distributed K-V ( key-value pairs)
cache system, when
accessing to this system, calculating a fragmentation according to a key's
hash (hash function)
to store and obtain this K-V, however, in the actual application, during some
rush hours, there
are many requests accessing to the same key (may correspond to some promotion
goods,
hotspot news, hotspot comments, etc.), this key can be referred as the hotspot
key, according
to the hash of this hotspot key, all the access requests will fall in the same
fragmentation and
severely increase the load of this fragmentation, then resulting in a long
response time and low
access efficiency.
Invention Content
[0003] Based on this, it is necessary to provide a cache system hotspot data
access method,
an apparatus, a computer device, and a storage medium to tackle the above-
mentioned technical
problems, wherein the method can disperse the hotspot key's traffic on the
fragmentation and
achieve hotspot key's evenly access and improve cache system access
efficiency.
[0004] A cache system hotspot data access method comprises:
[0005] Receiving an access request from a cache system, the access request
carries a to be
accessed data identity;
1
Date Recue/Date Received 2021-10-18
[0006] Obtaining a pre-set route scheduling rule when to be accessed data
corresponding to
the to be accessed data identity is in a candidate hotspot data list;
[0007] Routing the access request to the target fragmentation according to the
pre-set route
scheduling rule, responding the access request through the target
fragmentation, obtaining an
access result corresponding to the to be accessed data identity, wherein the
target fragmentation
is not specifically used to process the access request corresponding to the to
be accessed data
identity.
[0008] In an implementation, before receiving the access request of the cache
system,
comprising: obtaining candidate hotspot data, wherein the candidate hotspot
data includes
correspondingly hotspot data identity; obtaining candidate fragmentation set,
wherein the
candidate fragmentation set includes at least one candidate fragmentation;
traversing each
candidate fragmentation, so that the candidate fragmentation loads the
candidate hotspot data;
generating a candidate hotspot data list according to the candidate hotspot
data.
[0009] In an implementation, the cache system hotspot data access method also
comprises:
obtaining pre-set expiration time corresponding to each candidate hotspot
data; removing the
correspondingly candidate hotspot data from the candidate hotspot data list
when reaching the
pre-set expiration time, obtaining the updated candidate hotspot data list.
[0010] In an implementation, after receiving the access request of the cache
system, also
comprising: obtaining a pre-set counter; responding the access request through
the pre-set
counter, obtaining current access times corresponding to the to be accessed
data identity; if the
current access times does not reach an access times threshold, determining of
whether to be
accessed data corresponding to the to be accessed data identity is in the
candidate hotspot data
list; if determining of to be accessed data corresponding to the to be
accessed data identity is
in the candidate hotspot data list, entering step of obtaining the pre-set
route scheduling rule.
2
Date Recue/Date Received 2021-10-18
[0011] In an implementation, the cache system hotspot data access method also
comprises:
if the current access times reaches the access times threshold, obtaining a
candidate
fragmentation set, wherein the candidate fragmentation set includes at least
one candidate
fragmentation; traversing each candidate fragmentation, loading the to be
accessed data
through each candidate fragmentation; obtaining current counter status
corresponding to the
pre-set counter; setting the current counter status to current expiration
status, determining of
the pre-set counter is no longer counting.
[0012] In an implementation, when to be accessed data corresponding to the to
be accessed
data identity is in a candidate hotspot data list, comprising: obtaining a
candidate hotspot data
list, wherein the candidate hotspot list includes each candidate hotspot data,
each candidate
hotspot data includes correspondingly candidate hotspot data identity; if
existing the same
candidate hotspot data identity as the to be accessed data identity,
determining of to be accessed
data corresponding to the to be accessed data identity is in the candidate
hotspot data list.
[0013] In an implementation, the cache system hotspot data access method also
comprises:
if to be accessed data corresponding to the to be accessed data identity is
not in the candidate
hotspot data list, determining the correspondingly default fragmentation
according to the to be
accessed data identity, wherein the default fragmentation is specifically used
to process the
access request corresponding to the to be accessed data identity; responding
the access request
through the default fragmentation, obtaining access result corresponding to
the to be accessed
data identity.
[0014] A cache system hotspot data access's apparatus comprises:
[0015] An access request receiving module configured to receive an access
request of a cache
system, wherein the access request carries a to be accessed data identity;
[0016] A route rule obtaining module configured to obtain a pre-set route
scheduling rule
when to be accessed data corresponding to the to be accessed data identity is
in a candidate
3
Date Recue/Date Received 2021-10-18
hotspot data list;
[0017] An access result generation module configured to route the access
request to the target
fragmentation according to the pre-set route scheduling rule, responding the
access request
through the target fragmentation, obtaining an access result corresponding to
the to be accessed
data identity, wherein the target fragmentation is not specifically used to
process the access
request corresponding to the to be accessed data identity.
[0018] A computer device, including a memory, a processor and a computer
program stored
in the memory and ran on the processor configured to achieve the following
steps when the
processor executes the computer program:
[0019] Receiving an access request from a cache system, the access request
carries a to be
accessed data identity;
[0020] Obtaining a pre-set route scheduling rule when to be accessed data
corresponding to
the to be accessed data identity is in a candidate hotspot data list;
[0021] Routing the access request to the target fragmentation according to the
pre-set route
scheduling rule, responding the access request through the target
fragmentation, obtaining an
access result corresponding to the to be accessed data identity, wherein the
target fragmentation
is not specifically used to process the access request corresponding to the to
be accessed data
identity.
[0022] A computer readable storage medium stored with a computer program
configured to
achieve the following steps when the processor executes the computer program:
[0023] Receiving an access request from a cache system, the access request
carries a to be
accessed data identity;
4
Date Recue/Date Received 2021-10-18
[0024] Obtaining a pre-set route scheduling rule when to be accessed data
corresponding to
the to be accessed data identity is in a candidate hotspot data list;
[0025] Routing the access request to the target fragmentation according to the
pre-set route
scheduling rule, responding the access request through the target
fragmentation, obtaining an
access result corresponding to the to be accessed data identity, wherein the
target fragmentation
is not specifically used to process the access request corresponding to the to
be accessed data
identity.
[0026] The above-mentioned cache system hotspot data access method, apparatus,
computer
device and storage medium, receiving an access request from a cache system,
the access request
carries a to be accessed data identity; obtaining a pre-set route scheduling
rule when to be
accessed data corresponding to the to be accessed data identity is in a
candidate hotspot data
list; and routing the access request to the target fragmentation according to
the pre-set route
scheduling rule, responding the access request through the target
fragmentation, obtaining an
access result corresponding to the to be accessed data identity, wherein the
target fragmentation
is not specifically used to process the access request corresponding to the to
be accessed data
identity. Therefore, the target fragmentation can be specifically used to
process the access
requests corresponding to the other access data identities, wherein the access
data
corresponding to the other access data identities may not be hotspot data, so
according to the
route scheduling rule, the access request corresponding to the hotspot data
can be routed to the
fragmentation corresponding to non-hotspot data, the fragmentation traffic
corresponding to
the hotspot data can be shared by the fragmentation corresponding to the non-
hotspot data, so
as to achieve the evenly access to the hotspot data.
Drawing Description
[0027] Figure 1 is an application environment diagram of the cache system
hotspot data
access method in an implementation;
Date Recue/Date Received 2021-10-18
[0028] Figure 2 is a process diagram of the cache system hotspot data access
method in an
implementation;
[0029] Figure 3 is a process diagram of the cache system hotspot data access
method in an
implementation;
[0030] Figure 4 is a process diagram of the cache system hotspot data access
method in
another implementation;
[0031] Figure 5 is a process diagram of the cache system hotspot data access
method in an
implementation;
[0032] Figure 6 is a process diagram of the cache system hotspot data access
method in an
implementation;
[0033] Figure 7 is a process diagram of the candidate hotspot data list's
matching step in an
implementation;
[0034] Figure 8 is a process diagram of the cache system hotspot data access
method in an
implementation;
[0035] Figure 9 is a structural diagram of the cache system hotspot data
access apparatus in
an implementation;
[0036] Figure 10 is an internal structure of a computer device in an
implementation;
[0037] Figure 11 is an internal structure of a computer device in an
implementation.
6
Date Recue/Date Received 2021-10-18
Specific implementation methods
[0038] In order to make clearer application purposes, technical solutions, and
advantages, the
present disclosure is further explained in detail with a particular embodiment
thereof, and with
reference to the drawings. It shall be appreciated that these descriptions are
only intended to be
illustrative, but not to limit the scope of the disclosure thereto.
[0039] The cache system hotspot data access method provided by the present
application can
be applied in the application environment as shown in Figure 1. Wherein,
terminal 102
communicates with server 104 through the network. Among them, the terminal 102
can be used
but not limit to a variety of personal computers, laptops, smart phones,
tablets and portable
wearable devices, the server 104 can be achieved by an independent server or a
server cluster
composed of plural servers.
[0040] Specifically, the terminal 120 obtains the access request from the
cache system, the
access request carries the to be accessed data identity and the access request
is sent to server
104 through the network connection, after the server 104 receives the cache
system access
request, obtaining a pre-set route scheduling rule when to be accessed data
corresponding to
the to be accessed data identity is in a candidate hotspot data list, routing
the access request to
the target fragmentation according to the pre-set route scheduling rule,
responding the access
request through the target fragmentation, obtaining an access result
corresponding to the to be
accessed data identity, wherein the target fragmentation is not specifically
used to process the
access request corresponding to the to be accessed data identity.
[0041] In another implementation, the server 104 receives the access request
from the cache
system, the access request carries the to be accessed data identity, obtaining
a pre-set route
scheduling rule when to be accessed data corresponding to the to be accessed
data identity is
in a candidate hotspot data list, routing the access request to the target
fragmentation according
to the pre-set route scheduling rule, responding the access request through
the target
fragmentation, obtaining an access result corresponding to the to be accessed
data identity,
wherein the target fragmentation is not specifically used to process the
access request
7
Date Recue/Date Received 2021-10-18
corresponding to the to be accessed data identity.
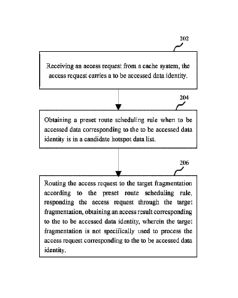
[0042] In an implementation, as shown in Figure 2, a cache system hotspot
access method is
provided, this method is applied in the terminal or the server in Figure 1 as
an illustration,
comprising following steps:
[0043] Step 202, receiving an access request from a cache system, the access
request carries
a to be accessed data identity;
[0044] Wherein, cache system (Redis) is the current enterprise widely used
distributed K-V
(key-value pairs) cache system, in a distributed system, the cache plays an
important role and
acts as hotpot cache or full cache, during the process of using the cache,
usually many
fragmentations are used which can not only increase the cache capacity, but
also disperse the
server's pressure where the cache system is located, so that the better
support capability for the
cache system service is provided.
[0045] Wherein, the access request of the cache system is used to request
access to the cache
system, which can be generated through performing trigger operations on the
access control
set by the relevant business access application, the operation can be but not
limited to click
operation, voice operation, timing events and so on. Among them, the access
request carries
the to be accessed data identity, the to be accessed data identity is used to
uniquely identify the
to be accessed data, and correspondingly access result can be obtained
according to the to be
accessed data identity.
[0046] Step 204, obtaining a pre-set route scheduling rule when to be accessed
data
corresponding to the to be accessed data identity is in a candidate hotspot
data list.
[0047] Wherein, in an actual application, during some rush hours, there will
be many requests
frequently accessing to the same data, such as accessing to the same key,
wherein, the key can
correspond to some promotion products, hotspot news, hotspot comments and so
on in an
8
Date Recue/Date Received 2021-10-18
application, and these requests will be instantly gathered in a fragmentation,
which will affect
the request and the response time on this fragmentation, but for those
fragmentations with less
access request data, the traffic of the cache request will be less.
[0048] Therefore, after receiving the access request, judging whether the to
be accessed data
corresponding to the to be accessed data identity is the hotspot data, if the
to be accessed data
is hotspot data, to avoid the failure response due to the massive access
requests, the access
request corresponding to the hotspot data can be dispersed to each
fragmentation to achieve
hotspot data's evenly access.
[0049] Specifically, after receiving the access request from the cache system,
obtaining the
candidate hotspot data list, wherein the candidate hotspot data list includes
at least one
candidate hotspot data, determining of whether the to be accessed data
corresponding to the to
be accessed data identity is hotspot data in the access request by matching
with the candidate
hotspot data list, if the to be accessed data corresponding to the to be
accessed data identity is
in the candidate hotspot data list, which means the to be accessed data is
hotspot data that needs
to be evenly accessed, obtaining pre-set route scheduling rule, wherein the
pre-set route
scheduling rule here is pre-set for evenly accessing that can be determined
and obtained based
on service requirements, actual application scenarios or product requirements.
[0050] In another implementation, if to be accessed data corresponding to the
to be accessed
data identity is not in the candidate hotspot data list, which means the to be
accessed data is not
hotspot data without much capacities, this access request can be processed
just through the
default fragmentation corresponding to the to be accessed data identity,
therefore, determining
the matched default fragmentation according to the to be accessed data
identity, responding the
access request through this default fragmentation, obtaining the
correspondingly access result.
Wherein the default fragmentation is specifically used to process the access
request
corresponding to the to be accessed data identity, the access requests
corresponding to the
different access data identities can be processed by different default
fragmentations.
9
Date Recue/Date Received 2021-10-18
[0051] Step 206, routing the access request to the target fragmentation
according to the pre-
set route scheduling rule, responding the access request through the target
fragmentation,
obtaining an access result corresponding to the to be accessed data identity,
wherein the target
fragmentation is not specifically used to process the access request
corresponding to the to be
accessed data identity.
[0052] Wherein the target fragmentation here is used to process this access
request's
fragmentation through the pre-set route scheduling rule, which means the
target fragmentation
is not specifically used to process the access request corresponding to the to
be accessed data
identity, the target fragmentation can be specifically used to process the
access requests
corresponding to other access data identities, the access data corresponding
to this other access
data identities may not be the hotspot data, therefore, so according to the
route scheduling rule,
the access request corresponding to the hotspot data can be routed to the
fragmentation
corresponding to non-hotspot data, the fragmentation traffic corresponding to
the hotspot data
can be shared by the fragmentation corresponding to the non-hotspot data, so
as to achieve the
evenly access to the hotspot data.
[0053] Specifically, after obtaining the pre-set route scheduling rule, the
access request can
be routed to the target fragmentation according to the pre-set route
scheduling rule, the target
fragmentation here can pre-load each hotspot data, when the access request
corresponding to
the to be accessed data identity is routed to this target fragmentation, the
target fragmentation
responds this access request directly and obtains the access result
corresponding to the to be
accessed data identity.
[0054] In another implementation, the target fragmentation does not pre-load
each hotspot
data but records the access times of the access request corresponding to the
to be accessed data
identity through the pre-set counter, when the access times reaches the pre-
set access times
threshold, then loading each hotspot data through the target fragmentation,
when the target
fragmentation completes the loading of hotspot data, the access request
corresponding to the
to be accessed data identity can be routed to the target fragmentation
according to the pre-set
Date Recue/Date Received 2021-10-18
route scheduling rule, the target fragmentation responds this access request
directly and obtains
the access result corresponding to the to be accessed data identity.
[0055] When the access times does not reach the pre-set access times
threshold, determining
of whether the to be accessed data corresponding to the to be accessed data
identity is in the
candidate hotspot data list, if determining of to be accessed data
corresponding to the to be
accessed data identity is in the candidate hotspot data list, entering step of
obtaining the pre-
set route scheduling rule.
[0056] In a specific implementation, assuming a distributed system composed of
10 groups
of candidate fragmentations (1-10), a hotspot key will only be routed to the
candidate
fragmentation 1 according to the default HASH rule, if there are 10000 access
requests
concurrently accessing to this hotspot key, the candidate fragmentation 1 will
instantly have
10000 access requests, but through the present application's cache system
hotspot access
method, the 10 groups of candidate fragmentations will all temporarily load
this hotspot key,
if there are 10000 access requests concurrently accessing to this hotspot key,
the concurrent
access requests will be dispersed to the 10 groups of fragmentations according
to the pre-set
route scheduling rule, basically each group of candidate fragmentations only
has 1000 access
requests, therefore, the candidate fragmentation will only has 1/10 of the
original traffic.
[0057] In the above-mentioned cache system hotspot data access method,
receiving an access
request from a cache system, the access request carries a to be accessed data
identity; obtaining
a pre-set route scheduling rule when to be accessed data corresponding to the
to be accessed
data identity is in a candidate hotspot data list; routing the access request
to the target
fragmentation according to the pre-set route scheduling rule, responding the
access request
through the target fragmentation, obtaining an access result corresponding to
the to be accessed
data identity, wherein the target fragmentation is not specifically used to
process the access
request corresponding to the to be accessed data identity. Therefore, the
target fragmentation
can be specifically used to process the access requests corresponding to the
other access data
identities, wherein the access data corresponding to the other access data
identities may not be
11
Date Recue/Date Received 2021-10-18
hotspot data, so according to the route scheduling rule, the access request
corresponding to the
hotspot data can be routed to the fragmentation corresponding to non-hotspot
data, the
fragmentation traffic corresponding to the hotspot data can be shared by the
fragmentation
corresponding to the non-hotspot data, so as to achieve the evenly access to
the hotspot data.
[0058] In an implementation, as shown in Figure 3, before receiving the access
request of the
cache system, comprising:
[0059] Step 302, obtaining candidate hotspot data, wherein the candidate
hotspot data
includes correspondingly hotspot data identity.
[0060] Step 304, obtaining candidate fragmentation set, wherein the candidate
fragmentation
set includes at least one candidate fragmentation.
[0061] Step
306, traversing each candidate fragmentation, so that the candidate
fragmentation loads the candidate hotspot data.
[0062] Step 308, generating a candidate hotspot data list according to the
candidate hotspot
data.
[0063] Among them, before receiving the access request of the cache system,
all the
candidate fragmentations can collect all candidate hotpot data, then pre-
loading all candidate
hotspot data and combining all successfully loaded candidate hotspot data to a
candidate
hotspot data list, when receiving the access request of the cache system,
judging whether the
to be accessed data corresponding to the to be accessed data identity included
in the access
request is in the candidate hotspot data list, if yes, determining the target
fragmentation from
the candidate fragmentations according to the pre-set route scheduling rule,
responding to this
access request through the target fragmentation and obtaining the access
result.
[0064] Specifically, obtaining candidate hotspot data, the candidate hotspot
data includes
12
Date Recue/Date Received 2021-10-18
correspondingly candidate hotspot data identity, wherein the obtaining of the
candidate hotspot
data can be through massive web crawling, data crawling or access records of
various popular
websites, and the candidate hotspot data includes correspondingly candidate
hotspot data
identity, the different candidate hotspot data correspond to the different
candidate hotspot data
identity.
[0065]
Furthermore, obtaining all candidate fragmentations, then all candidate
fragmentations form a candidate fragmentation set, traversing all candidate
fragmentations,
each fragmentation loads the candidate hotspot data, when each candidate
fragmentation
successfully loads the candidate hotspot data, a candidate hotspot data list
is composed of the
candidate hotspot data, which means the candidate hotspot data joins the
candidate hotpot data
list.
[0066] In an implementation, as shown in Figure 4, the cache system hotspot
data access
method also comprises:
[0067] Step 402, obtaining pre-set expiration time corresponding to each
candidate hotspot
data.
[0068] Step 404, removing the correspondingly candidate hotspot data from the
candidate
hotspot data list when reaching the pre-set expiration time, obtaining the
updated candidate
hotspot data list.
[0069] When loading the candidate hotspot data in each candidate
fragmentation, meanwhile,
the pre-set expiration time corresponding to candidate hotspot data needs to
be set, generally
the pre-set expiration time is not very long and just can pass the peak access
period. Wherein
the pre-set expiration time corresponding to each candidate hotspot data can
be obtained
according to business requirements, actual application scenarios, product
requirements and so
on, the pre-set expiration time corresponding to each candidate hotspot data
can be the same
and can be different. To avoid wasting resources, when reaching the pre-set
expiration time,
13
Date Recue/Date Received 2021-10-18
removing the candidate hotspot data corresponding to the reached pre-set
expiration time from
the candidate hotspot data list, updating the candidate hotspot data list and
obtaining the
updated candidate hotspot data list.
[0070] In a specific implementation, before receiving the access request of
the cache system,
collecting the hotspot key in advance, cyclically traversing all the candidate
fragmentations,
each candidate fragmentation loads the hotspot key once, meanwhile, the pre-
set expiration
time is set, generally the pre-set expiration time is not very long and just
can pass the peak
access period. When the scheduler completes the loading action, the hotspot
key will be
updated to the candidate hotpot data list.
[0071] Furthermore, when the cache system access is in process, the business
system needs
to access the hotspot key to obtain the pre-set route scheduling rule. Due to
the pre-loading of
the hotspot key, the candidate hotpot data list is already updated, therefore,
the access request
is routed to the other target fragmentations by using pre-set route scheduling
rules such as
random, polling, or the most recently non-used route scheduling rules. If the
hotspot key is
expired, the candidate hotspot data list will also remove this hotspot key.
[0072] In an implementation, as shown in Figure 5, after receiving the access
request of the
cache system, also comprising:
[0073] Step 502, obtaining a pre-set counter.
[0074] Step 504, responding the access request through the pre-set counter,
obtaining current
access times corresponding to the to be accessed data identity.
[0075] Step 506, if the current access times does not reach an access times
threshold,
determining of whether to be accessed data corresponding to the to be accessed
data identity is
in the candidate hotspot data list.
14
Date Recue/Date Received 2021-10-18
[0076] Step 508, if determining of to be accessed data corresponding to the to
be accessed
data identity is in the candidate hotspot data list, entering step of
obtaining the pre-set route
scheduling rule.
[0077] Wherein, if each candidate fragmentation does not pre-load each hotspot
data before
receiving the access request of the cache system, but with the increase of
some hotspot data
access, when triggering a pre-set threshold, then each fragmentation completes
loading to
hotpot data. Specifically, obtaining the pre-set counter, wherein the pre-set
counter is used to
record the times of the access times of the hotspot data, for example, the pre-
set counter here
is used to record the access times of the access request corresponding to the
to be accessed data
identity, responding to the access request through the pre-set counter, then
obtaining the current
access times corresponding to the to be accessed data identity.
[0078] Furthermore, determining of whether the to be accessed data
corresponding to the to
be accessed data identity has triggered a pre-set threshold, which can
specifically be obtaining
the access times threshold, determining of whether the to be accessed data has
triggered the
pre-set threshold according to the access times threshold and the current
access times, if the
current access times does not reach the access threshold, which means the
access times of this
to be accessed data does not reach the pre-set threshold and there are not
many access times,
then determining of whether the to be accessed data corresponding to the to be
accessed data
identity is in the candidate hotspot data list, if determining of the to be
accessed data
corresponding to the to be accessed data identity is in the candidate hotspot
data list, entering
the step of obtaining pre-set route scheduling rule.
[0079] In an implementation, as shown in Figure 6, the cache system hotspot
data access
method also comprises:
[0080] Step 602, if the current access times reaches the access times
threshold, obtaining a
candidate fragmentation set, wherein the candidate fragmentation set includes
at least one
candidate fragmentation.
Date Recue/Date Received 2021-10-18
[0081] Step 604, traversing each candidate fragmentation, loading the to be
accessed data
through each candidate fragmentation.
[0082] Step 606, obtaining current counter status corresponding to the pre-set
counter.
[0083] Step 608, setting the current counter status to current expiration
status, determining
of the pre-set counter is no longer counting.
[0084] If the current access times reaches the access times threshold, which
means the access
times of the to be accessed data reaches the access times threshold and there
are many access
times, therefore, obtaining all the fragmentations, then all candidate
fragmentations form a
candidate fragmentation set, traversing all candidate fragmentations, each
fragmentation loads
the candidate hotspot data and obtains the current counter status
corresponding to the pre-set
counter, when each candidate fragmentation successfully loads the candidate
hotspot data,
setting the current counter status to be current expiration status, when
setting the pre-set counter
to be expiration status, then the counter is no longer counting.
[0085] In a specific implementation, before the access of the cache system,
the hotspot key
is not pre-loaded. When the cache system access is in process, the hotspot key
needs to be
accessed, because the hotspot key does not exist in the candidate hotspot data
list, the cache
system routes the request to the matched candidate fragmentation 1 according
to the hotspot
key, wherein the candidate fragmentation 1 is specifically used to process
this hotspot key.
Among them, whenever accessing this hotspot key, the pre-set counter will
increase one count
in the memory, the pre-set counter is effective in the initial stage, when the
pre-set counter
reaches or exceeds the pre-set threshold, the counter will trigger all
candidate fragmentations
to complete this dynamic loading of the hotspot KEY.
[0086] When completing the dynamic loading of the hotspot KEY, then setting
the counter
of this hotspot KEY to be expiration status, the counter is no longer
counting, and adding the
16
Date Recue/Date Received 2021-10-18
hotspot KEY to the candidate hotspot data list, at this time, the candidate
hotspot data list is
already updated, therefore, using the pre-set route scheduling rules such as
random, polling, or
the most recently non-used route scheduling rules, routing the hotspot key to
the target
fragmentation.
[0087] In an implementation, as shown in Figure 7, when to be accessed data
corresponding
to the to be accessed data identity is in a candidate hotspot data list,
comprising:
[0088] Step 702, obtaining a candidate hotspot data list, wherein the
candidate hotspot list
includes each candidate hotspot data, each candidate hotspot data includes
correspondingly
candidate hotspot data identity.
[0089] Step 704, if existing the same candidate hotspot data identity as the
to be accessed
data identity, determining of to be accessed data corresponding to the to be
accessed data
identity is in the candidate hotspot data list.
[0090] According to whether the to be accessed data corresponding to the to be
accessed data
identity is in the candidate hotspot data list, judging whether the to be
accessed data is the
hotspot data, if to be accessed data is the hotspot data, to avoid the failure
response due to the
massive access requests, the access request corresponding to the hotspot data
can be dispersed
to each fragmentation to achieve hotspot data's evenly access.
[0091] Specifically, after receiving the access request from the cache system,
obtaining the
candidate hotspot data list, wherein the candidate hotspot data list includes
at least one
candidate hotspot data, determining of whether the to be accessed data
corresponding to the to
be accessed data identity is hotspot data in the access request by matching
with the candidate
hotspot data list, if the to be accessed data corresponding to the to be
accessed data identity is
in the candidate hotspot data list, which means the to be accessed data is
hotspot data that needs
to be evenly accessed.
17
Date Recue/Date Received 2021-10-18
[0092] Wherein, determining whether the to be accessed data is in the
candidate hotspot data
list according to whether the candidate hotspot data identity is the same as
the to be accessed
data identity, if existing the same candidate hotspot data identity as the to
be accessed data
identity, which means existing the same candidate hotspot data as to be
accessed data in the
candidate hotspot data list, determining of the to be accessed data
corresponding to the to be
accessed data identity is in the candidate hotspot data list, which means the
to be accessed data
corresponding to the to be accessed data identity is hotspot data, to avoid
the failure accesses,
therefore, hotspot data's evenly access is needed.
[0093] In an implementation, as shown in Figure 8, the cache system hotspot
data access
method also comprises:
[0094] Step 802, if to be accessed data corresponding to the to be accessed
data identity is
not in the candidate hotspot data list, determining the correspondingly
default fragmentation
according to the to be accessed data identity, wherein the default
fragmentation is specifically
used to process the access request corresponding to the to be accessed data
identity.
[0095] Step 804, responding the access request through the default
fragmentation, obtaining
access result corresponding to the to be accessed data identity.
[0096] Specifically, if to be accessed data corresponding to the to be
accessed data identity
is not in the candidate hotspot data list, which means the to be accessed data
is not hotspot data
without much capacities, this access request can be processed just through the
default
fragmentation corresponding to the to be accessed data identity, therefore,
determining the
matched default fragmentation according to the to be accessed data identity,
responding the
access request through this default fragmentation, obtaining the
correspondingly access result.
Wherein the default fragmentation is specifically used to process the access
request
corresponding to the to be accessed data identity, the access requests
corresponding to the
different access data identities can be processed by different default
fragmentations.
18
Date Recue/Date Received 2021-10-18
[0097] In a specific implementation, a cache system hotspot data access method
is provided,
specifically comprising as following steps:
[0098] 1. Obtaining candidate hotspot data, wherein the candidate hotspot data
includes
correspondingly hotspot data identity.
[0099] 2. Obtaining candidate fragmentation set, wherein the candidate
fragmentation set
includes at least one candidate fragmentation.
[0100] 3. Traversing each candidate fragmentation, so that the candidate
fragmentation loads
the candidate hotspot data.
[0101] 4. Generating a candidate hotspot data list according to the candidate
hotspot data.
[0102] 5. Obtaining pre-set expiration time corresponding to each candidate
hotspot data.
[0103] 6. Removing the correspondingly candidate hotspot data from the
candidate hotspot
data list when reaching the pre-set expiration time, obtaining the updated
candidate hotspot
data list.
[0104] 7. Receiving the access request of the cache system, the access request
carries the to
be accessed data identity.
[0105] 8. Obtaining a pre-set counter.
[0106] 9. Responding the access request through the pre-set counter, obtaining
current access
times corresponding to the to be accessed data identity.
[0107] 10. If the current access times does not reach an access times
threshold, determining
of whether to be accessed data corresponding to the to be accessed data
identity is in the
19
Date Recue/Date Received 2021-10-18
candidate hotspot data list.
[0108] 11. If determining of to be accessed data corresponding to the to be
accessed data
identity is in the candidate hotspot data list, obtaining the pre-set route
scheduling rule.
[0109] 11-1. Obtaining candidate hotspot data list, if to be accessed data
corresponding to
the to be accessed data identity is in a candidate hotspot data list, wherein
the candidate hotspot
list includes each candidate hotspot data, each candidate hotspot data
includes correspondingly
candidate hotspot data identity.
[0110] 11-2. If existing the same candidate hotspot data identity as the to be
accessed data
identity, determining of to be accessed data corresponding to the to be
accessed data identity
is in the candidate hotspot data list.
[0111] 12. Routing the access request to the target fragmentation according to
the pre-set
route scheduling rule, responding the access request through the target
fragmentation, obtaining
an access result corresponding to the to be accessed data identity, wherein
the target
fragmentation is not specifically used to process the access request
corresponding to the to be
accessed data identity.
[0112] 13.
If the current access times reaches the access times threshold, obtaining a
candidate fragmentation set, wherein the candidate fragmentation set includes
at least one
candidate fragmentation.
[0113] 14. Traversing each candidate fragmentation, loading the to be accessed
data through
each candidate fragmentation.
[0114] 15. Obtaining current counter status corresponding to the pre-set
counter.
[0115] 16. Setting the current counter status to current expiration status,
determining of the
pre-set counter is no longer counting.
Date Recue/Date Received 2021-10-18
[0116] 17. If to be accessed data corresponding to the to be accessed data
identity is not in
the candidate hotspot data list, determining the correspondingly default
fragmentation
according to the to be accessed data identity, wherein the default
fragmentation is specifically
used to process the access request corresponding to the to be accessed data
identity.
[0117] 18. Responding the access request through the default fragmentation,
obtaining access
result corresponding to the to be accessed data identity.
[0118] Although the above-mentioned steps in the flowchart are shown in
sequence as
indicated by the arrows, these steps are not necessarily executed in the order
indicated by the
arrows. Unless explicitly instruction in this article, there is no strict
order in which these steps
can be performed, and they can be performed in any other orders. In addition,
at least parts of
the appended drawings in the steps can include more sub steps or multiple
stages, these sub
steps or stages are not necessarily completed at the same time but can be
executed in different
time, the execution order of these sub steps or stages is also not necessarily
in sequence order
but can be performed alternately with the other steps or sub steps of other
steps or at least one
part of the other stages.
[0119] In an implementation, as shown in Figure 9, a cache system hotspot data
access
apparatus 900 is provided, comprising: access request receiving module 902,
roue rule
obtaining module 904, and access result generation module 906, wherein:
[0120] An access request receiving module 902 configured to receive an access
request of a
cache system, wherein the access request carries a to be accessed data
identity.
[0121] A route rule obtaining module 904 configured to obtain a pre-set route
scheduling rule
when to be accessed data corresponding to the to be accessed data identity is
in a candidate
hotspot data list.
21
Date Recue/Date Received 2021-10-18
[0122] An access result generation module 906 configured to route the access
request to the
target fragmentation according to the pre-set route scheduling rule,
responding the access
request through the target fragmentation, obtaining an access result
corresponding to the to be
accessed data identity, wherein the target fragmentation is not specifically
used to process the
access request corresponding to the to be accessed data identity.
[0123] In an implementation, the cache system hotspot data access apparatus
900 is also used
for obtaining candidate hotspot data, wherein the candidate hotspot data
includes
correspondingly hotspot data identity, obtaining candidate fragmentation set,
wherein the
candidate fragmentation set includes at least one candidate fragmentation,
traversing each
candidate fragmentation, so that the candidate fragmentation loads the
candidate hotspot data,
generating a candidate hotspot data list according to the candidate hotspot
data.
[0124] In an implementation, the cache system hotspot data access apparatus
900 is also used
for obtaining pre-set expiration time corresponding to each candidate hotspot
data, removing
the correspondingly candidate hotspot data from the candidate hotspot data
list when reaching
the pre-set expiration time, obtaining the updated candidate hotspot data
list.
[0125] In an implementation, the cache system hotspot data access apparatus
900 is also used
for obtaining a pre-set counter, responding the access request through the pre-
set counter,
obtaining current access times corresponding to the to be accessed data
identity, if the current
access times does not reach an access times threshold, determining of whether
to be accessed
data corresponding to the to be accessed data identity is in the candidate
hotspot data list; if
determining of to be accessed data corresponding to the to be accessed data
identity is in the
candidate hotspot data list, entering step of obtaining the pre-set route
scheduling rule.
[0126] In an implementation, the cache system hotspot data access apparatus
900 is also used
for obtaining a candidate fragmentation set if the current access times
reaches the access times
threshold, wherein the candidate fragmentation set includes at least one
candidate
22
Date Recue/Date Received 2021-10-18
fragmentation, traversing each candidate fragmentation, loading the to be
accessed data
through each candidate fragmentation, obtaining current counter status
corresponding to the
pre-set counter, setting the current counter status to current expiration
status, determining of
the pre-set counter is no longer counting.
[0127] In an implementation, route rule obtaining module 904 is also used for
obtaining a
candidate hotspot data list, wherein the candidate hotspot list includes each
candidate hotspot
data, each candidate hotspot data includes correspondingly candidate hotspot
data identity, if
existing the same candidate hotspot data identity as the to be accessed data
identity,
determining of to be accessed data corresponding to the to be accessed data
identity is in the
candidate hotspot data list.
[0128] In an implementation, the cache system hotspot data access apparatus
900 is also used
if the to be accessed data corresponding to the to be accessed data identity
is not in the candidate
hotspot data list, determining the correspondingly default fragmentation
according to the to be
accessed data identity, wherein the default fragmentation is specifically used
to process the
access request corresponding to the to be accessed data identity, responding
the access request
through the default fragmentation, obtaining access result corresponding to
the to be accessed
data identity.
[0129] For the specific limitation of the cache system hotspot data access
apparatus can refer
to the above-mentioned the cache system hotspot data access method, which will
not be
repeated here. Each module of the above data cache apparatus can be achieved
fully or partly
by software, hardware, and their combinations. The above modules can be
embedded in the
processor or independent of the processor in computer device and can store in
the memory of
computer device in form of software, so that the processor can call and
execute the operations
corresponding to the above modules.
[0130] In an implementation, a computer device is provided to be a server and
whose internal
structure diagram is shown in Figure 10. The computer device includes a
processor, a memory,
23
Date Recue/Date Received 2021-10-18
a network interface, and a database connected through a system bus. The
processor of the
computer device is configured to provide calculation and control capabilities.
The memory of
computer device includes non-volatile storage medium and internal memory. The
memory of
non-volatile storage medium has operation system, computer programs and
database. The
internal memory provides an environment for the operation system and computer
program
running in a non-volatile storage medium. The network interface of the
computer device is
used to communicate with an external terminal through a network connection.
The computer
program is executed by the processor to implement a cache system hotspot data
access method.
[0131] In an implementation, a computer device is provided to be a server and
whose internal
structure diagram is shown in Figure 11. The computer device includes a
processor, a memory,
a network interface, and a database connected through a system bus. The
processor of the
computer device is configured to provide calculation and control capabilities.
The memory of
computer device includes non-volatile storage medium and internal memory. The
memory of
non-volatile storage medium has operation system, computer programs and
database. The
internal memory provides an environment for the operation system and computer
program
running in a non-volatile storage medium. The network interface of the
computer device is
used to communicate with an external terminal through a network connection.
The computer
program is executed by the processor to implement a cache system hotspot data
access method.
The computer device's display monitor can be LCD monitor or electronic ink
display monitor,
the input apparatus of the computer device can be the touch layer on the
display monitor, also
can be button, trackball, or touchpad, and can be the external keyboard,
touchpad, or mouse,
etc.
[0133] The skilled in the art can understand that the structure shown in
Figure 10 and Figure
11 is only partial structural diagram related this application solution and
not constitute
limitation to the computer device applied on the current application solution,
the specific
computer device can include more or less components than what is shown in the
figure, or
combinations of some components or different components to what is shown in
the figure.
24
Date Recue/Date Received 2021-10-18
[0134] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining candidate hotspot data, wherein the candidate
hotspot data
includes correspondingly hotspot data identity, obtaining candidate
fragmentation set, wherein
the candidate fragmentation set includes at least one candidate fragmentation,
traversing each
candidate fragmentation, so that the candidate fragmentation loads the
candidate hotspot data,
generating a candidate hotspot data list according to the candidate hotspot
data.
[0135] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining pre-set expiration time corresponding to each
candidate hotspot
data, removing the correspondingly candidate hotspot data from the candidate
hotspot data list
when reaching the pre-set expiration time, obtaining the updated candidate
hotspot data list.
[0136] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining a pre-set counter, responding the access request
through the pre-
set counter, obtaining current access times corresponding to the to be
accessed data identity, if
the current access times does not reach an access times threshold, determining
of whether to
be accessed data corresponding to the to be accessed data identity is in the
candidate hotspot
data list; if determining of to be accessed data corresponding to the to be
accessed data identity
is in the candidate hotspot data list, entering step of obtaining the pre-set
route scheduling rule.
[0137] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining a candidate fragmentation set if the current
access times reaches
the access times threshold, wherein the candidate fragmentation set includes
at least one
candidate fragmentation, traversing each candidate fragmentation, loading the
to be accessed
data through each candidate fragmentation, obtaining current counter status
corresponding to
the pre-set counter, setting the current counter status to current expiration
status, determining
of the pre-set counter is no longer counting.
[0138] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining a candidate hotspot data list, wherein the
candidate hotspot list
Date Recue/Date Received 2021-10-18
includes each candidate hotspot data, each candidate hotspot data includes
correspondingly
candidate hotspot data identity, if existing the same candidate hotspot data
identity as the to be
accessed data identity, determining of to be accessed data corresponding to
the to be accessed
data identity is in the candidate hotspot data list.
[0139] In an implementation, the processor performs the following steps when
executing the
computer program: if the to be accessed data corresponding to the to be
accessed data identity
is not in the candidate hotspot data list, determining the correspondingly
default fragmentation
according to the to be accessed data identity, wherein the default
fragmentation is specifically
used to process the access request corresponding to the to be accessed data
identity, responding
the access request through the default fragmentation, obtaining access result
corresponding to
the to be accessed data identity.
[0140] In an implementation, a computer readable storage medium stored with a
computer
program configured to achieve the following steps when the processor executes
the computer
program: receiving an access request from a cache system, the access request
carries a to be
accessed data identity; obtaining a pre-set route scheduling rule when to be
accessed data
corresponding to the to be accessed data identity is in a candidate hotspot
data list; routing the
access request to the target fragmentation according to the pre-set route
scheduling rule,
responding the access request through the target fragmentation, obtaining an
access result
corresponding to the to be accessed data identity, wherein the target
fragmentation is not
specifically used to process the access request corresponding to the to be
accessed data identity.
[0141] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining candidate hotspot data, wherein the candidate
hotspot data
includes correspondingly hotspot data identity, obtaining candidate
fragmentation set, wherein
the candidate fragmentation set includes at least one candidate fragmentation,
traversing each
candidate fragmentation, so that the candidate fragmentation loads the
candidate hotspot data,
generating a candidate hotspot data list according to the candidate hotspot
data.
26
Date Recue/Date Received 2021-10-18
[0142] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining pre-set expiration time corresponding to each
candidate hotspot
data, removing the correspondingly candidate hotspot data from the candidate
hotspot data list
when reaching the pre-set expiration time, obtaining the updated candidate
hotspot data list.
[0143] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining a pre-set counter, responding the access request
through the pre-
set counter, obtaining current access times corresponding to the to be
accessed data identity, if
the current access times does not reach an access times threshold, determining
of whether to
be accessed data corresponding to the to be accessed data identity is in the
candidate hotspot
data list; if determining of to be accessed data corresponding to the to be
accessed data identity
is in the candidate hotspot data list, entering step of obtaining the pre-set
route scheduling rule.
[0144] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining a candidate fragmentation set if the current
access times reaches
the access times threshold, wherein the candidate fragmentation set includes
at least one
candidate fragmentation, traversing each candidate fragmentation, loading the
to be accessed
data through each candidate fragmentation, obtaining current counter status
corresponding to
the pre-set counter, setting the current counter status to current expiration
status, determining
of the pre-set counter is no longer counting.
[0145] In an implementation, the processor performs the following steps when
executing the
computer program: obtaining a candidate hotspot data list, wherein the
candidate hotspot list
includes each candidate hotspot data, each candidate hotspot data includes
correspondingly
candidate hotspot data identity, if existing the same candidate hotspot data
identity as the to be
accessed data identity, determining of to be accessed data corresponding to
the to be accessed
data identity is in the candidate hotspot data list.
[0146] In an implementation, the processor performs the following steps when
executing the
computer program: if the to be accessed data corresponding to the to be
accessed data identity
27
Date Recue/Date Received 2021-10-18
is not in the candidate hotspot data list, determining the correspondingly
default fragmentation
according to the to be accessed data identity, wherein the default
fragmentation is specifically
used to process the access request corresponding to the to be accessed data
identity, responding
the access request through the default fragmentation, obtaining access result
corresponding to
the to be accessed data identity.
[0147] The skilled in the art can understand that all or partial of procedures
from the above-
mentioned methods can be performed by computer program instructions through
related
hardware, the mentioned computer program can be stored in a non-volatile
material computer
readable storage medium, this computer can include various implementation
procedures from
the abovementioned methods when execution. Any reference to the memory, the
storage, the
database, or the other media used in each implementation provided in current
application can
include non-volatile and/or volatile memory. Non-volatile memory can include
read-only
memory (ROM), programable ROM (PROM), electrically programmable ROM (EPRPMD),
electrically erasable programmable ROM (EEPROM) or flash memory. Volatile
memory can
include random access memory (RAM) or external cache memory. As an instruction
but not
limited to, RAM is available in many forms such as static RAM (SRAM), dynamic
RAM
(DRAMD), synchronous DRAM (SDRAM), dual data rate SDRAM (DDRSDRAM),
enhanced SRAM (ESDRAM), synchronal link (Synchlink) DRAM (SLDRAM), memory bus
(Rambus), direct RAM (RDRAM), direct memory bus dynamic RAM (DRDRAM), and
memory bus dynamic RAM (RDRAM), etc.
[0148] The technical features of the above-mentioned implementations can be
randomly
combined, for concisely statement, not all possible combinations of technical
features in the
abovementioned implementations are described. However, if there are no
conflicts in the
combinations of these technical features, it shall be within the scope of this
descriptions.
[0149] The above-mentioned implementations are only several implementations in
this
disclosure and the description is more specific and detailed but cannot be
understood as the
28
Date Recue/Date Received 2021-10-18
limitation of the scope of the invention patent. Evidently those ordinary
skilled in the art can
make various modifications and variations to the disclosure without departing
from the spirit
and scope of the disclosure. Therefore, the appended claims are intended to be
construed as
encompassing the described embodiment and all the modifications and variations
coming into
the scope of the disclosure.
29
Date Recue/Date Received 2021-10-18