Note: Descriptions are shown in the official language in which they were submitted.
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
Title
Secure Wireless Networks For Vehicle Assigning Authority
(TL-001C4W0)
Technical Field
[0001] The present invention generally relates to wireless networks for
vehicles.
Background Art
[0002] The prior art discusses various techniques for wireless
networks for
vehicles.
[0003] U.S. Patent Number 9215590 for Authentication Using Vehicle
Data
Pairing discloses the wireless pairing of a portable device with an on-board
computer of a vehicle for authenticating a transaction with a third party.
[0004] General definitions for terms utilized in the pertinent art
are set forth
below.
[0005] BLUETOOTH technology is a standard short range radio link
that
operates in the unlicensed 2.4 gigaHertz band.
[0006] FTP or File Transfer Protocol is a protocol for moving files
over the
Internet from one computer to another.
[0007] Media Access Control (MAC) Address is a unique identifier
assigned
to the network interface by the manufacturer.
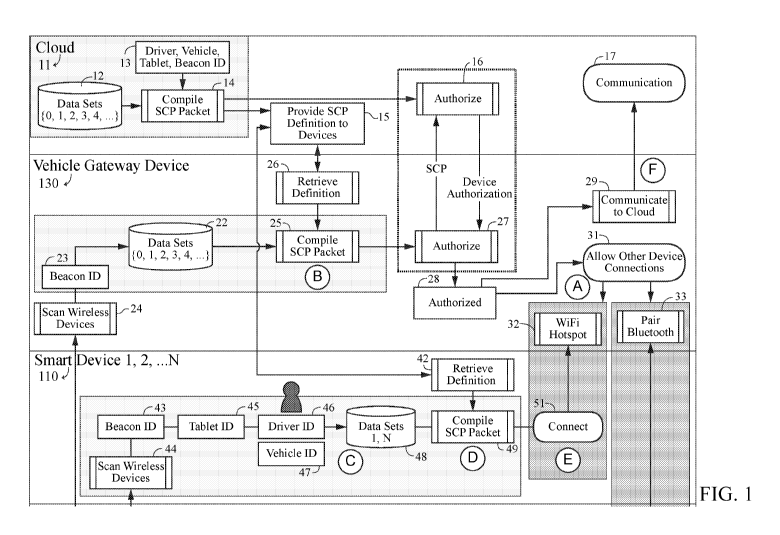
[0008] Memory generally includes any type of integrated circuit or storage
device configured for storing digital data including without limitation ROM,
PROM, EEPROM, DRAM, SDRAM, SRAM, flash memory, and the like.
[0009] Processor generally includes all types of processors
including without
limitation microprocessors, general purpose processors, gate arrays, array
processors, application specific integrated circuits (ASICs) and digital
signal
processors.
[00010] SCP (Secure Connection Packet) is used to provide authentication
between multiple devices or a local party and remote host to allow for secure
communication or the transfer of computer files.
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
2
[00011] SSID (Service Set Identifier) is a 1 to 32 byte string that
uniquely
names a wireless local area network.
[00012] There is a need for securely connecting a device to a single access
point in a vehicle, while preventing malicious users from detecting and
connecting to a wireless network published on a vehicle.
Summary Of The Invention
[00013] The present invention provides a system and method of securely and
accurately connecting mobile devices to wireless networks in vehicles by
using encrypted wireless network configurations based on vehicle specific
data.
[00014] One aspect of the present invention is a method for a secure
connection
to a wireless network of a vehicle. The method includes generating, at a
server, definitions for a SCP packet for assigning authority for a vehicle.
The
method also includes transmitting the definitions for the SCP packet from the
server to a CVD and a mobile device. The method also includes compiling the
SCP packet at the CVD to generate a CVD compiled SCP. The method also
includes transmitting the CVD compiled SCP to the server for authorization.
The method also includes transmitting authorization for the CVD compiled
SCP from the server to the CVD for creation of a validated SCP. The method
also includes generating a dataset at the mobile device to compile a mobile
device compiled SCP. The method also includes broadcasting at a CVD a
wireless network with a hidden and hashed SSID unique to the vehicle, the
hidden and hashed SSID generated from the validated SCP packet. The
method also includes generating at the mobile device the hashed SSID and a
passphrase from the dataset, which allows the mobile device connect to the
wireless network. The method also includes searching at a mobile device for a
vehicle having the CVD broadcasting the wireless network in a hidden mode.
The method also includes connecting the mobile device with the CVD. The
CVD comprises a processor, a WiFi radio, a BLUETOOTH ("BT") radio, a
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
3
memory, and a connector for mating with a connector plug of a vehicle. The
mobile device comprises a graphical user interface, a BT radio, a processor, a
WiFi radio and a cellular network interface.
[00015] Another aspect of the present invention is a system for vehicle to
mobile device secure wireless communications. The system comprises a
vehicle, a CVD, a mobile device and a passive communication device. The
vehicle comprises an on-board computer with a memory having a vehicle
identification number (VIN), a connector plug, and an motorized engine. The
CVD comprises a processor, a WiFi radio, a BT radio, a memory, and a
connector for mating with the connector plug of the vehicle. The mobile
device comprises a graphical user interface, a mobile application, a
processor,
a WiFi radio, and a cellular network interface. The passive communication
device operates on a BT communication protocol. The server is configured to
generate a plurality of definitions for a SCP packet for assigning authority
for
the vehicle. The server is configured to transmit the plurality of definitions
for
the SCP packet from the server to the CVD and the mobile device. The CVD
is configured to compile the SCP packet to generate a CVD compiled SCP.
The CVD is configured to transmit the CVD compiled SCP to the server for
authorization. The server is configured to transmit authorization for the CVD
compiled SCP to the CVD for creation of a validated SCP. The mobile device
is configured to generating a dataset to compile a mobile device compiled
SCP. The CVD is configured to broadcast a wireless network with a hidden
and hashed SSID unique to the vehicle, the hidden and hashed SSID generated
from the validated SCP packet. The mobile device is configured to generate
the hashed S SID and a passphrase from the dataset, which allows the mobile
device connect to the wireless network. The mobile device is configured to
search for a vehicle having the CVD broadcasting the wireless network in a
hidden mode. The mobile device is configured to connect to the CVD over the
wireless network.
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
4
[00016] Yet another aspect of the present invention is a method for a secure
connection to a wireless network of a vehicle. The method includes
transmitting a plurality of definitions for a SCP packet from a server to a
CVD
and a mobile device. The method also includes receiving at the server a CVD
compiled SCP packet for authorization. The method also includes transmitting
authorization for the CVD compiled SCP packet from the server to the CVD
for creation of a validated SCP. The method also includes generating a dataset
at the mobile device to compile a mobile device compiled SCP. The method
also includes broadcasting at a CVD a wireless network with a hidden and
hashed SSID unique to the vehicle, the hidden and hashed SSID generated
from the validated SCP. The method also includes generating at the mobile
device the hashed SSID and a passphrase from the dataset, which allows the
mobile device connect to the wireless network. The method also includes
connecting the mobile device with the CVD over the wireless network.
[00017] Yet another of the present invention is a method for a secure
connection to a wireless network of a vehicle for a predetermined work
assignment. The method includes broadcasting a wireless network having a
service set identifier (SSID) from a CVD physically connected to an on-board
computer of an assigned vehicle of a plurality of vehicles at a facility. The
SSID of the wireless network is not published. The method also includes
connecting the CVD with a mobile device for the predetermined work
assignment, the CVD using an encrypted password, the CVD of the assigned
vehicle broadcasting the wireless network with the unpublished SSID, and the
CVD previously paired with the mobile device according to at least one of a
driver, a vehicle with a known identification, and a mobile device with a
known identification. The vehicle comprises the on-board computer with a
memory having a vehicle identification number (VIN), a connector plug, and
an motorized engine. The CVD comprises a processor, a WiFi radio, a BT
radio, a memory, and a connector for pairing with the connector plug of the
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
vehicle. The mobile device comprises a graphical user interface, a processor,
a
WiFi radio, a BT radio, and a cellular network interface.
[00018] Yet another aspect of the present invention is a system for a secure
connection to a wireless network of a vehicle for a predetermined work
5 assignment. The system comprises a vehicle, a CVD, and a mobile
device.
The vehicle comprises an on-board computer with a memory having a vehicle
identification number (VIN), a connector plug, and an motorized engine. The
CVD comprises a processor, a WiFi radio, a BT radio, a memory, and a
connector for pairing with the connector plug of the vehicle. The mobile
device comprises a graphical user interface, a processor, a WiFi radio, a BT
radio, and a cellular network interface. The predetermined work assignment is
assigned through a pairing event. The mobile device has been previously
paired with the CVD and has been provided the SSID and an encrypted
password. The CVD is configured to broadcast a WiFi network having a
service set identifier (SSID), wherein the SSID is not published. The mobile
device is configured to search for the vehicle having the CVD broadcasting
the WiFi network with the SSID. The mobile device is configured to connect
with the CVD using the encrypted password.
Brief Description Of the Drawings
[00019] FIG. 1 is a block diagram of system for a secure communication
protocol for connecting a wireless device to a single access point in a
vehicle.
[00020] FIG. 1A is a continuation of the block diagram of FIG. 1.
[00021] FIG. 2 is a flow chart of a method for a secure connection to a
wireless
network of a vehicle.
[00022] FIG. 3 is an illustration of a driver identifying a vehicle through
connection of a tablet computer to an unpublished network.
[00023] FIG. 4 is an isolated view of general components of a mobile device.
[00024] FIG. 5 is an isolated view of general components of a server.
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
6
[00025] FIG. 6 is a flow chart of method for securely connecting a wireless
device to a single access point in a vehicle.
[00026] FIG. 7 is an illustration of a system for securely connecting a
wireless
device to a single access point in a vehicle.
[00027] FIG. 8 is an illustration of a driver identifying a vehicle through
connection of a tablet computer to an unpublished network.
[00028] FIG. 9 is a block diagram of system for securely connecting a wireless
device to a single access point in a vehicle
[00029] FIG. 10 is a block diagram of system for securely connecting a
wireless device to a single access point in a vehicle.
Best Mode(s) For Carrying Out The Invention
[00030] A system 10 for securely connecting a wireless device to a single
access point in a vehicle for a predetermined work assignment is set for the
FIGS. 1 and 1A. The system 10 preferably comprises a remote server (cloud)
11, a vehicle gateway device 130, a smart device 110 and a passive device 61.
The vehicle gateway device 130 is preferably a connected vehicle device
("CVD").
[00031] The server/cloud 11 accesses dataset 12 and obtains driver
information. Vehicle information, mobile device information (MAC address),
passive device information (beacon ID) and other information to compile a
SCP packet 14. At block 15, the server 11 provides SCP definitions to the
vehicle gateway device 130 and the mobile device 110. At block 16 the
server/cloud 11 authorizes the SCP. At block 17, the server/cloud 11
communicates with the vehicle gateway device 130.
[00032] The vehicle gateway device 130 uses datasets 22, with the beacon ID
23, a scan of wireless devices 24 along with the SCP definitions 26 received
from the server/cloud 11 to compile a CVD compiled SCP packet 25. The
CVD compiled SCP packet is sent to the cloud/server 11 at block 16 and
authorization/validation of the CVD compiled SCP packet is received at block
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
7
27. At block 28 the SCP is authorized for broadcasting at the vehicle gateway
device 130 a wireless network with a hidden and hashed SSID unique to the
vehicle, the hidden and hashed SSID generated from the validated SCP packet.
At block 29, the vehicle gateway device 130 communicates the broadcast with
the server/cloud 11. At block 31, the vehicle gateway device 130
communicates with other devices, namely the smart device 110 over
preferably a WiFi hotspot 32 and the passive device 61 by pairing using a BT
communication protocol at block 33.
[00033] At block 49, the smart device (mobile device) 110 compiles a
complied mobile device SCP packet from the SCP definitions 42, the data sets
48, the beacon ID 43, the Tablet ID 45, a driver ID 46, a vehicle ID 47 and
scan of wireless devices 44. The mobile device 110 generates the hashed
SSID and a passphrase from the complied mobile device SCP packet. At block
51, the mobile device 110 connects to the WiFi hotspot 32 of the vehicle
device gateway 130.
[00034] The passive device 61 broadcast a unique ID at block 62 which is
received by the mobile device 110 and the vehicle gateway device 130. At
block 63, if a BT device, it broadcasts a BT advertisement at block 64.
[00035] The SCP is defined by an assigning authority in the server/cloud 11.
The server/cloud 11 sends the SCP definition and any other required data in
datasets to the CVD 130 and the mobile device 110. The CVD 130 adds the
contextual data from local datasets to the sever-sent data to compile its SCP
based definition. The local datasets include data wirelessly scanned from
passive devices, preferably transmitting a BT beacon. Other local datasets
include information from the vehicle. The CVD 130 sends its compiled SCP
packet to the server 11 for authorization. The server 11 verifies the CVD
compiled SCP packet, and if valid, the server 11 transmits a
validation/approval signal to the CVD 130. The CVD then generates an access
point SSID/passphrase with SCP. Likewise, the mobile device 110 utilizes
contextual data from local datasets to compile its SCP based on the
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
8
definitions. The mobile device 110 connects to the access point of the CVD
130 using the SCP. The CVD 130 and the mobile device 110 also connect to
the passive device 61 since it is part of the SCP definition.
[00036] A predetermined work assignment is a temporal event with a fixed
start and completion based on assignable boundary conditions. The assignable
boundary condition is at least one of a predetermined time period, a
geographical destination, and a set route. Alternatively, the assignable
boundary condition is any feature with a beginning and a termination. The
assigning authority is performed by a person or persons, who have the
appropriate authority and mechanisms to assign specific tasks and assets to a
specific vehicle and vehicle operator or custodian, and to assign workflow
assignments to same. The predetermined work assignment is assigned to a
known person or entity that has its own primary networked device accessible
through a password protected user interface, a specific name and password
that auto-populates or otherwise automatically satisfies a plurality of
credentials requirements, wherein the plurality of credential requirements are
automatically available or revoked based on the assignable boundary condition
identified in a pairing event.
[00037] The CVD 130 broadcasts a Wifi wireless network with a hidden and
hashed SSID unique to the host vehicle and protected by a unique,
dynamically generated and hashed passphrase. The vehicle ID is entered into
an application on the tablet that is then converted to the same hashed SSID
and passphrase, which allows the tablet to attempt to connect to the
corresponding CVD Wifi network and begin communication.
[00038] A method 900 for a secure connection to a wireless network of a
vehicle is shown in FIG. 2. At block 901, a server generates definitions for a
SCP packet for assigning authority for a vehicle. At block 902 the server
transmits the definitions for the SCP packet to a CVD and a mobile device. At
block 903, the CVD compiles the SCP packet to generate a CVD compiled
SCP. At block 904, the CVD transmits the CVD compiled SCP to the server
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
9
for authorization. At block 905, the server transmits authorization for the
CVD
compiled SCP from to the CVD for creation of a validated SCP. At block 906,
the mobile device generates a dataset to compile a mobile device compiled
SCP. At block 907, the CVD broadcasts at a wireless network with a hidden
and hashed SSID unique to the vehicle. The hidden and hashed SSID is
generated from the validated SCP packet. At block 908, the mobile device
generates the hashed SSID and a passphrase from the dataset, which allows
the mobile device connect to the wireless network. At block 909, the mobile
device searches for a vehicle having the CVD broadcasting the wireless
network in a hidden mode. At block 910, the mobile device securely connects
with the CVD.
[00039] One embodiment is a system for vehicle to mobile device secure
wireless communications. The system comprises a vehicle 210, a CVD 130, a
mobile device 110 and a passive communication device 61. The vehicle 210
comprises an on-board computer with a memory having a vehicle
identification number (VIN), a connector plug, and an motorized engine. The
CVD 130 comprises a processor, a WiFi radio, a BT radio, a memory, and a
connector for mating with the connector plug of the vehicle. The mobile
device 110 comprises a graphical user interface, a mobile application, a
processor, a WiFi radio, and a cellular network interface. The passive
communication device 61 operates on a BT communication protocol. The
server 11 is configured to generate a plurality of definitions for a SCP
packet
for assigning authority for the vehicle. The server 11 is configured to
transmit
the plurality of definitions for the SCP packet from the server to the CVD 130
and the mobile device 110. The CVD 130 is configured to compile the SCP
packet to generate a CVD compiled SCP. The CVD 130 is configured to
transmit the CVD compiled SCP to the server 11 for authorization. The server
11 is configured to transmit authorization for the CVD compiled SCP to the
CVD 130 for creation of a validated SCP. The mobile device 110 is
configured to generating a dataset to compile a mobile device compiled SCP.
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
The CVD 130 is configured to broadcast a wireless network with a hidden and
hashed SSID unique to the vehicle, the hidden and hashed SSID generated
from the validated SCP packet. The mobile device 110 is configured to
generate the hashed SSID and a passphrase from the dataset, which allows the
5 mobile device connect to the wireless network. The mobile device 110
is
configured to search for a vehicle having the CVD broadcasting the wireless
network in a hidden mode. The mobile device 110 is configured to connect to
the CVD 130 over the wireless network.
[00040] The dataset preferably comprises at least one of a plurality of
10 definitions for the SCP packet, a tablet ID, a driver ID, a vehicle
ID, a beacon
ID, identified or defined entity/participant to the transaction, descriptions,
actions, or states of thing, characteristics of identifiable devices, when
present
in a certain proximity and/or context.
[00041] Optionally, the mobile device 110 connects to a passive device, the
passive device operating on a BT communication protocol. The passive device
61 is preferably a BT enabled device advertising a unique ID as a beacon or a
complex system (speaker, computer, etc.) that emits BT enabled device
advertising a unique ID as a beacon. The mobile device 110 preferably
receives input from a driver of the vehicle, and/or the server 11 contains the
assigning authority that generates the SCP definitions.
[00042] The passive device 61 is preferably an internal device in the vehicle
or
an external device posted on a gate to a facility and generating a beacon. The
beacon from the passive device is preferably a mechanism to ensure that the
connection between the mobile device 110 and the CVD 130 occurs at a
specific physical location dictated by the assigning authority through the
server 11. Preferably, the automatic connection between the mobile device
110 and the CVD occurs because the assigning authority, through the server,
has dictated that it occur.
[00043] As shown in FIG. 3, each of a multitude of trucks 210a-210d broadcast
a wireless signal for a truck specific network, with one truck 210c
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
11
broadcasting a wireless signal 225. However, the SSID is not published so
unless a driver is already in possession of the SSID, the driver will not be
able
to pair the tablet computer 110 with the CVD 130 of the truck 210 to which
the driver is assigned. So even though the wireless signals are being
"broadcast", they will not appear on a driver's tablet computer 110 (or other
mobile device) unless the tablet computer 110 has already been paired with
the CVD 130 of the vehicle 210. A driver 205 in possession of a tablet
computer 110 pairs, using a signal 230, the tablet computer 110 with the
wireless network 225 of the CVD of the truck 210c, and thus the driver locates
the specific truck 210c he is assigned to in a parking lot full of identical
looking trucks 210a-d.
[00044] The mobile communication device 110, or mobile device, is preferably
selected from mobile phones, smartphones, tablet computers, PDAs and the
like. Examples of smartphones and the device vendors include the IPHONE
smartphone from Apple, Inc., the DROID smartphone from Motorola
Mobility Inc., GALAXY S smartphones from Samsung Electronics Co.,
Ltd., and many more. Examples of tablet computing devices include the
IPAD tablet computer from Apple Inc., and the XOOMTm tablet computer
from Motorola Mobility Inc.
[00045] BLUETOOTHTm technology operates in the unlicensed 2.4 GHz band
of the radio-frequency spectrum, and in a preferred embodiment the secondary
device 30 and/or primary device 25 is capable of receiving and transmitting
signals using BT technology. LTE Frequency Bands include 698-798MHz
(Band 12, 13, 14, 17); 791-960MHz (Band 5, 6, 8, 18,19,20); 1710-2170MHz
(Band 1, 2, 3, 4, 9, 10, 23, 25, 33, 34, 35, 36, 37, 39); 1427-1660.5MH (Band
11, 21, 24); 2300-2700MHz (Band 7, 38, 40, 41); 3400-3800MHz (Band 22,
42, 43), and in a preferred embodiment the secondary device 30 and/or the
primary device 25 is capable of receiving and transmitting signals using one
or
more of the LTE frequency bands. WiFi preferably operates using 802.11a,
802.11b, 802.11g, 802.11n communication formats as set for the by the IEEE,
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
12
and in in a preferred embodiment the secondary device 30 and/or the primary
device 25 is capable of receiving and transmitting signals using one or more
of
the 802.11 communication formats. Near-field communications (NFC) may
also be utilized.
[00046] As shown in FIG. 4, a typical mobile communication device 110
preferably includes an accelerometer 301, I/0 (input/output) 302, a
microphone 303, a speaker 304, a GPS chipset 305, a BT component 306, a
Wi-Fi component 307, a 3G/4G component 308, RAM memory 309, a main
processor 310, an OS (operating system) 311, applications/software 312, a
Flash memory 313, SIM card 314, LCD display 315, a camera 316, a power
management circuit 317, a battery 318 or power source, a magnetometer 319,
and a gyroscope 320.
[00047] Each of the interface descriptions preferably discloses use of at
least
one communication protocol to establish handshaking or bi-directional
communications. These protocols preferably include but are not limited to
XML, HTTP, TCP/IP, Serial, UDP, FTP, Web Services, WAP, SMTP, SMPP,
DTS, Stored Procedures, Import/Export, Global Positioning Triangulation,
IM, SMS, MMS, GPRS and Flash. Databases that may be used with the
system preferably include but are not limited to MS SQL, Access, My SQL,
Progress, Oracle, DB2, Open Source DBs and others. Operating system used
with the system preferably include Microsoft 2010, XP, Vista, 200o Server,
2003 Server, 2008 Server, Windows Mobile, Linux, Android, Unix, I series,
AS 400 and Apple OS.The underlying protocol at the cloud server 11, is
preferably Internet Protocol Suite (Transfer Control Protocol/Internet
Protocol
("TCP/IP")), and the transmission protocol to receive a file is preferably a
file
transfer protocol ("FTP"), Hypertext Transfer Protocol ("HTTP"), Secure
Hypertext Transfer Protocol ("HTTPS") or other similar protocols. The
transmission protocol ranges from SIP to MGCP to FTP and beyond. The
protocol at the authentication server 40 is most preferably HTTPS. Wireless
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
13
standards include 802.11a, 802.11b, 802.11g, AX.25, 3G, CDPD, CDMA,
GSM, GPRS, radio, microwave, laser, Bluetooth, 802.15, 802.16, and IrDA.
[00048] Components of a cloud computing server 40 of the system, as shown in
FIG. 5, preferably includes a CPU component 401, a graphics component 402,
PCl/PCI Express 403, memory 404, non-removable storage 407, removable
storage 408, Network Interface 409, including one or more connections to a
fixed network, and SQL database(s) 45a-45d, which includes the venue's
CRM. Included in the memory 404, is an operating system 405, a SQL server
406 or other database engine, and computer programs/software 410. The
server 40 also preferably includes at least one computer program configured to
receive data uploads and store the data uploads in the SQL database.
Alternatively, the SQL server can be installed in a separate server from the
server 40.
[00049] A flow chart for an alternative method 600 for a secure connection to
a
wireless network of a vehicle is shown in FIG. 6. At block 601, the CVD
broadcasts an encrypted, blind SSID based on specific vehicle data. At block
602, leveraging the known vehicle data and the encryption algorithm a mobile
device searches for a vehicle having a CVD broadcasting the wireless
network. At block 603, the mobile device is connected with the CVD.
[00050] A system for a secure connection to a wireless network of a vehicle is
shown in FIG. 7. A truck 210a. Those skilled in the pertinent art will
recognize that the truck 210a may be replaced by any type of vehicle (such as
a bus, sedan, pick-up, sport utility vehicle, limousine, sports car, delivery
truck, van, mini-van, motorcycle, and the like) without departing from the
scope of spirit of the present invention. The truck 210a preferably comprises
a
motorized engine 234, a vehicle identification number ("VIN"), an on-board
computer 232 with a memory 231 and a connector plug 235. The on-board
computer 232 preferably has a digital copy of the VIN in the memory 231.
The on-board computer 232 is preferably in communication with the
motorized engine 234. The truck 210a may also have a GPS component for
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
14
location and navigation purposes, a satellite radio such as SIRIUS satellite
radio, a driver graphical interface display, a battery, a source of fuel and
other
components found in a conventional long distance truck. Also in the truck
210a is a CVD 130 comprising a processor, a WiFi radio, a BT radio, a
memory and a connector to connect to the connector plug of the on-board
computer 232. A driver 205 preferably has a mobile communication device
such as a tablet computer 110 in order to pair with a wireless network
generated by the CVD 130 of the truck 210a. The tablet computer 110
preferably comprises a graphical user interface 335, a processor 310, a WiFi
radio 307, a BT radio 306, and a cellular network interface 308.
[00051] As shown in FIG. 8, each of a multitude of trucks 210a-210k broadcast
a wireless signal 224a-k for a truck specific network, with one truck 210f
broadcasting a wireless signal 225. However, all of the wireless signal 224a-
224k and 225 do not publish their respective SSID so that a mobile device 110
must already be paired with the CVD 130 of the truck 210 in order to connect
to the truck based wireless network 224a-224k or 225 of each of the CVDs
130 of each of the trucks 210a-210k. A driver 205 in possession of a tablet
computer 110 pairs with the specific truck wireless network 225 of the CVD
130 of the truck 210f, and thus the driver locates the specific truck 210f he
is
assigned to in a parking lot full of identical looking trucks 210a-210k.
[00052] FIGS. 9 and 10 illustrate a pairing process for a system 100 for
securely connecting a wireless device to a single access point in a vehicle
for a
predetermined work assignment. The predetermined work assignment is a
temporal event with a fixed start and completion based on assignable
boundary conditions. The assignable boundary condition is at least one of a
predetermined time period, a geographical destination, and a set route.
Alternatively, the assignable boundary condition is any feature with a
beginning and a termination. The assigning authority is performed by a person
or persons, who have the appropriate authority and mechanisms to assign
specific tasks and assets to a specific vehicle and vehicle operator or
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
custodian, and to assign workflow assignments to same. The predetermined
work assignment is assigned to a known person or entity that has its own
primary networked device accessible through a password protected user
interface, a specific name and password that auto-populates or otherwise
5 automatically satisfies a plurality of credentials requirements,
wherein the
plurality of credential requirements are automatically available or revoked
based on the assignable boundary condition identified in a pairing event.
[00053] The secure connection is preferably established between a
tablet
computer 110 and connected vehicle device ("CVD") 130. The CVD 130 is
10 preferably physically connected to an on-board computer of a vehicle.
The
vehicle is preferably a delivery truck or a long-haul semi-truck. The CVD 130
does not broadcast a S SID, and thus the wireless network is unpublished. The
tablet computer 110, having previously paired with the CVD 130, is used to
"find" or re-pair with the wireless network of the CVD 130 since WiFi
15 settings are retained in a memory of the tablet computer 130. At block
111,
the installation begins for the tablet computer 110. At block 112, a setup
screen having an ESN, a power unit identification and a tablet computer serial
number is displayed. At block 112a the device of the known person or known
entity uses at least one of a password protected user interface, a specific
name
and password that auto-populates or otherwise automatically satisfies
credentials requirements for the pairing event. At block 113, the
identifications are inputted, and at block 121 they are validated. At block
114,
it finds the default SSID plus the password. At block 115, the processing
occurs including the processing of the tablet computer setup and the
verification of the power unit identification. At block 116, it connects with
the
default settings to the CVD 130 pairing with the default settings 131 of the
CVD 130. At block 117, the tablet computer sends configuration data to the
CVD 130. At block 132, the CVD 130 updates the WiFi settings and at block
133 validates the power unit to the VIN. At block 140, the CVD 130 is
registered with a cloud computing service 140, and at block 142, the tablet
Date Recue/Date Received 2021-11-18
CA 03141293 2021-11-18
WO 2020/236452
PCT/US2020/032389
16
computer is registered with the cloud computing service 140. At block 118,
the tablet computer 110 sets the configured SSID and password from the CVD
130. At block 119, the tablet computer 110 reconnects with the configured
WiFi settings. At block 134 on the CVD 130, the configured WiFi settings
include the SSID, encrypted, the WPA2 PSK: encrypt (power unit
identification salt) and the SSID is not broadcasted. At block 122, the
settings
are validated on the tablet computer 110. Block 120 is a critical error screen
in which the tablet WIFI setup failed or the power unit identification was not
verified. At block 123, a confirmation screen is shown on the tablet computer
110. At block 124, the setup is complete. At block 125, a tablet WiFi setup re-
pairing screen is shown.
Date Recue/Date Received 2021-11-18