Note: Descriptions are shown in the official language in which they were submitted.
CA 03162736 2022-05-24
DATA TRANSMISSION METHOD AND DEVICE BASED ON CONSORTIUM
BLOCKCHAIN
BACKGROUND OF THE INVENTION
Technical Field
[0001] The present invention relates to the field of blockchain technology,
and more particularly
to a data transmission method and device based on consortium blockchain.
Description of Related Art
[0002] Blockchain is a novel application pattern that merges together such
computer techniques
as distributed data storage, point-to-point transmission, consensus mechanism,
and
encryption algorithm, etc. In accordance with differences in the extents of
centralization
of the blockchain network, the following three types of blockchains are
subdivided under
different application scenarios:
[0003] 1. the blockchain, which is made public to the entire network without
any user
authorization mechanism, is referred to as a public chain;
[0004] 2. the blockchain that allows authorized nodes to access the network,
in which
information can be checked according to permission, and which is usually used
between
organizations, is referred to as consortium blockchain;
[0005] 3. the blockchain, all nodes in whose network are controlled by a
single organization, is
referred to as a private chain.
[0006] Currently speaking, consortium blockchain exhibits more practical
significance and
brighter commercial prospect. The consortium blockchain can better exert the
functions
of interconnection and intercommunication, and sharing of information of the
internet.
However, with the gradual abundance of application scenarios for the
consortium
1
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
blockchain, higher and higher demands are being put on the safety and privacy
of data
transmission.
[0007] At present, data transmission within the alliance channel mainly
employs the technology
of bulk encryption and transmission of messages, and specific techniques
involved
therein include symmetric encryption, asymmetric encryption, and digital
signature
verification, of which:
[0008] by the symmetric encryption technique, the same secret key is used for
encryption and
decryption;
[0009] by the asymmetric encryption technique, a pair of secret keys is
created, of which the
secret key not made public is called a private key, and the secret key made
public is called
a public key; the public key encrypts data, while the corresponding private
key decrypts
data;
[0010] by the digital signature verification technique, the asymmetric key
encryption technique
is combined for use with the digital digest technique; a pair of secret keys
is created, of
which the private key performs digital signature on digital digest, while the
corresponding
public key verifies the same.
[0011] However, the aforementioned methods are problematic as specified below:
on the one
hand, by the bulk encryption and decryption of data, the receiving party can
view only
the whole message after receiving the secret key, as it is impossible for the
transmitting
party to control fine granularity, for example, to allow the receiving party
to view only
designated sections; on the other hand, although symmetric encryption is
advantageous
in terms of quick speed and high efficiency, the safety for transmitting
secret keys over
the network is not so high, whereas asymmetric encryption has the advantage of
high
safety, but the speed of encryption and decryption is relatively low.
SUMMARY OF THE INVENTION
2
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0012] In order to address the problems pending in the state of the art,
embodiments of the
present invention provide a data transmission method and device based on
consortium
blockchain, so as to overcome such prior-art problems as by the bulk
encryption and
decryption, the receiving party can view only the whole message after
receiving the secret
key, as it is impossible for the transmitting party to control fine
granularity (for example,
to allow the receiving party to view only designated sections), safety for
transmitting
secret keys over the network in the symmetric encryption technique is not so
high, and
the speed of encryption and decryption in the asymmetric encryption technique
is low.
[0013] In order to solve the above technical problems, the present invention
employs the
following technical solutions.
[0014] According to the first aspect, there is a data transmission method
based on consortium
blockchain, and the method is applied to a first node on a blockchain and
comprises the
following steps:
[0015] splitting data into plural data blocks, employing different symmetric
keys to
correspondingly encrypt the plural data blocks, generating plural data block
cyphertexts,
numbering the same and uploading the same to the blockchain;
[0016] employing a public key of the first node to encrypt the symmetric keys,
generating a first
secret key cyphertext and uploading the same to the blockchain;
[0017] employing a private key of the first node to decrypt a numbered
cyphertext coming from
the blockchain, and obtaining a number of a to-be-enquired data block
cyphertext of a
second node, wherein the numbered cyphertext is generated by the second node
employing the public key of the first node to encrypt the number of the to-be-
enquired
data block cyphertext; and
[0018] employing, when the second node is allowed to enquire, a public key of
the second node
to encrypt a corresponding symmetric key, generating a second secret key
cyphertext, and
transmitting the same to the second node through the blockchain, so that the
second node
employs its own private key to decrypt the second secret key cyphertext and
obtain the
3
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
corresponding symmetric key.
[0019] Moreover, the step of splitting data into plural data blocks, employing
different symmetric
keys to respectively and correspondingly encrypt the data blocks, generating
plural data
block cyphertexts, numbering the same and uploading the same to the blockchain
specifically includes:
[0020] splitting data into plural data blocks according to types of
information in the data;
[0021] generating one symmetric key corresponding to each data block; and
[0022] employing the symmetric keys respectively to encrypt corresponding data
blocks,
generating data block cyphertexts, numbering the same and uploading the same
to the
blockchain.
[0023] Moreover, before the step of employing a public key of the first node
to encrypt the
symmetric keys, the method further comprises:
[0024] locally generating a public key and a private key of the first node,
and uploading the
public key of the first node to the blockchain.
[0025] Moreover, the step of employing, when the second node is allowed to
enquire, a public
key of the second node to encrypt a corresponding symmetric key, generating a
second
secret key cyphertext, and transmitting the same to the second node through
the
blockchain specifically includes:
[0026] employing the private key of the first node to decrypt the first secret
key cyphertext
obtained from the blockchain, and obtaining the symmetric key;
[0027] obtaining a symmetric key to which the to-be-enquired data block
cyphertext corresponds
from the symmetric key;
[0028] employing the public key of the second node to encrypt the symmetric
key to which the
to-be-enquired data block cyphertext corresponds, and generating a second
secret key
cyphertext; and
[0029] transmitting the second secret key cyphertext to the second node
through the blockchain.
4
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0030] Moreover, when the second node is not allowed to enquire, an enquiry
rejecting message
is generated and transmitted to the second node through the blockchain.
[0031] According to the second aspect, there is a data transmission method
based on consortium
blockchain, and the method is applied to a second node on a blockchain and
comprises
the following steps:
[0032] when the second node is not allowed to enquire, an enquiry rejecting
message is generated
and transmitted to the second node through the blockchain (sic).
[0033] Moreover, before the step of obtaining a symmetric key to which the to-
be-enquired data
block cyphertext corresponds from the blockchain, the method further
comprises:
[0034] locally generating a public key and a private key of a second node, and
transmitting the
public key of the second node to the blockchain.
[0035] Moreover, the step of obtaining a symmetric key to which the to-be-
enquired data block
cyphertext corresponds from the blockchain, decrypting the to-be-enquired data
block
cyphertext, and obtaining a data block as required specifically includes:
[0036] obtaining a second secret key cyphertext from the blockchain, wherein
the second secret
key cyphertext is generated by the first node employing the public key of the
second node
to encrypt the symmetric key to which the to-be-enquired data block cyphertext
corresponds;
[0037] employing the private key of the second node to decrypt the second
secret key cyphertext,
and obtaining a corresponding symmetric key; and
[0038] employing the corresponding symmetric key to decrypt the to-be-enquired
data block
cyphertext, and obtaining a data block required to be enquired.
[0039] According to the third aspect, there is a data transmission device
based on consortium
blockchain, and the device is applied to a first node on a blockchain and at
least comprises:
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0040] a data splitting module, for splitting data into plural data blocks;
[0041] a first encrypting module, for employing different symmetric keys to
respectively and
correspondingly encrypt the plural data blocks, generating plural data block
cyphertexts,
numbering the same and uploading the same to the blockchain;
[0042] wherein the first encrypting module is further employed for employing a
public key of
the first node to encrypt the symmetric keys, generating a first secret key
cyphertext and
uploading the same to the blockchain;
[0043] a first decrypting module, for employing a private key of the first
node to decrypt a
numbered cyphertext coming from the blockchain, and obtaining a number of a to-
be-
enquired data block cyphertext of a second node, wherein the numbered
cyphertext is
generated by the second node employing the public key of the first node to
encrypt the
number of the to-be-enquired data block cyphertext;
[0044] wherein the first encrypting module is further employed for employing a
public key of
the second node to encrypt a corresponding symmetric key, and generating a
second secret
key cyphertext; and
[0045] a transmitting module, for transmitting the second secret key
cyphertext to the second
node through the blockchain.
[0046] Moreover, the device further comprises:
[0047] a first generating module, for generating one symmetric key
corresponding to each data
block.
[0048] Moreover, the device further comprises:
[0049] a second generating module, for locally generating a public key and a
private key of the
first node, and uploading the public key of the first node to the blockchain.
[0050] According to the fourth aspect, there is a data transmission device
based on consortium
blockchain, and the device is applied to a second node on a blockchain and at
least
comprises:
6
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0051] a second encrypting module, for employing a public key of a first node
obtained from a
blockchain to encrypt a number of a to-be-enquired data block cyphertext, and
generating
a numbered cyphertext;
[0052] a signing module, for signing the numbered cyphertext and transmitting
the same to the
blockchain;
[0053] an obtaining module, for obtaining a symmetric key to which the to-be-
enquired data
block cyphertext corresponds from the blockchain; and
[0054] a second decrypting module, for decrypting the to-be-enquired data
block cyphertext, and
obtaining a data block as required.
[0055] Moreover, the device further comprises:
[0056] a third generating module, for locally generating a public key and a
private key of a
second node, and transmitting the public key of the second node to the
blockchain.
[0057] The technical solutions provided by the embodiments of the present
invention bring about
the following advantageous effects.
[0058] 1. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, the first node on the
blockchain
of the data sharing system can self-define the block encryption strategy.
Through the
block encryption method, the first node can flexibly control the message
accessing
strategy to control fine granularity, for instance, to allow only the second
node to view
designated sections, and authorization from the first node is required for the
second node
to view certain blocks in the message, whereby controllability of data is
guaranteed.
[0059] 2. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, block encryption is
performed on
the message by means of a symmetric encryption algorithm, and symmetric keys
are
encrypted by means of an asymmetric encryption algorithm, whereby efficiency
of
7
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
encryption and decryption is enhanced as far as possible while data safety is
guaranteed.
[0060] 3. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, data is encrypted and
thereafter
stored on the blockchain, unless authorization is made, it is impossible for
other persons
to decrypt the data; moreover, when data blocks are encrypted and thereafter
transmitted,
what is stored on the blockchain is all the encrypted data, so that safety and
privacy of
the data are guaranteed.
[0061] 4. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, all symmetric keys are
temporarily
generated and stored on the blockchain, as long as the local asymmetric
private key is not
lost, decryption can be made again from the blockchain very conveniently, so
that
restorability of data is guaranteed.
BRIEF DESCRIPTION OF THE DRAWINGS
[0062] To more clearly describe the technical solutions in the embodiments of
the present
invention, drawings required to be used in the description of the embodiments
will be
briefly introduced below. Apparently, the drawings introduced below are merely
directed
to some embodiments of the present invention, while it is possible for persons
ordinarily
skilled in the art to acquire other drawings based on these drawings without
spending
creative effort in the process.
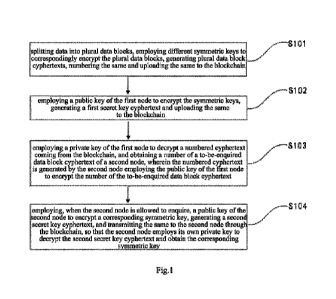
[0063] Fig. 1 is a flowchart of the data transmission method based on
consortium blockchain
according to an exemplary embodiment;
[0064] Fig. 2 is a flowchart illustrating the process of splitting data into
plural data blocks,
employing different symmetric keys to correspondingly encrypt the data blocks,
8
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
generating plural data block cyphertexts, numbering the same and uploading the
same to
the blockchain according to an exemplary embodiment;
[0065] Fig. 3 is a flowchart illustrating the process of employing, when the
second node is
allowed to enquire, a public key of the second node to encrypt a corresponding
symmetric
key, generating a second secret key cyphertext, and transmitting the same to
the second
node through the blockchain according to an exemplary embodiment;
[0066] Fig. 4 is a flowchart of the data transmission method based on
consortium blockchain
according to an exemplary embodiment;
[0067] Fig. 5 is a flowchart illustrating the process of obtaining a symmetric
key to which the to-
be-enquired data block cyphertext corresponds from the blockchain, decrypting
the to-
be-enquired data block cyphertext, and obtaining a data block as required
according to an
exemplary embodiment;
[0068] Fig. 6 is a view schematically illustrating the structure of the data
transmission device
based on consortium blockchain according to an exemplary embodiment; and
[0069] Fig. 7 is a view schematically illustrating the structure of the data
transmission device
based on consortium blockchain according to an exemplary embodiment.
DETAILED DESCRIPTION OF THE INVENTION
[0070] In order to make clearer the objectives, technical solutions and
advantages of the present
invention, the technical solutions in the embodiments of the present invention
will be
more clearly and comprehensively described below with reference to the
accompanying
drawings in the embodiments of the present invention. Apparently, the
embodiments as
described are merely partial, rather than the entire, embodiments of the
present invention.
9
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
All other embodiments obtainable by persons ordinarily skilled in the art on
the basis of
the embodiments in the present invention without spending creative effort
shall all fall
within the protection scope of the present invention.
[0071] Fig. 1 is a flowchart of the data transmission method based on
consortium blockchain
according to an exemplary embodiment. The method is applied to a first node on
a
blockchain, and with reference to Fig. 1, the method comprises the following
steps.
[0072] S101 - splitting data into plural data blocks, employing different
symmetric keys to
correspondingly encrypt the plural data blocks, generating plural data block
cyphertexts,
numbering the same and uploading the same to the blockchain.
[0073] Specifically, the first node (namely a data transmitting party) can
split data (namely a
plaintext message) into plural data blocks according to business requirement,
temporarily
generate symmetric keys, employ the symmetric keys to encrypt the data blocks
to
generate plural first encrypted data blocks, wherein each data block
corresponds to one
symmetric key, and all symmetric keys are different from one another;
thereafter, after
the plural first encrypted data blocks have been sequentially numbered, these
first
encrypted data blocks and their numbers are uploaded to the blockchain for
storage. As
should be noted here, the same and single symmetric key can also be used to
encrypt the
data blocks.
[0074] S102 - employing a public key of the first node to encrypt the
symmetric keys, generating
a first secret key cyphertext and uploading the same to the blockchain.
[0075] Further, before the public key of the first node is employed to encrypt
the symmetric keys,
the first node locally generates the public key and the private key of the
first node, and
uploads the public key of the first node to the blockchain.
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0076] Specifically, the first node firstly employs the public key of the
first node to encrypt the
symmetric keys to generate a first secret key cyphertext, and then uploads the
first secret
key cyphertext to the blockchain for storage. Since all symmetric keys are
temporarily
generated, and stored on the blockchain after having been encrypted by means
of the
public key of the first node, as long as the local asymmetric private key is
not lost,
decryption can be made again from the blockchain very conveniently, so that
restorability
of data is guaranteed. Moreover, the symmetric keys are encrypted and
thereafter stored
on the blockchain, whereby loss of the symmetric keys due to invalidation of
the local
node can be avoided. In addition, the public key of the first node is uploaded
to the
blockchain, whereby it can be conveniently shared with other users in the
blockchain.
[0077] S103 - employing a private key of the first node to decrypt a numbered
cyphertext coming
from the blockchain, and obtaining a number of a to-be-enquired data block
cyphertext
of a second node, wherein the numbered cyphertext is generated by the second
node
employing the public key of the first node to encrypt the number of the to-be-
enquired
data block cyphertext.
[0078] Specifically, the first node (namely the data transmitting party)
monitors the data in the
blockchain, when the signed numbered cyphertext is received, it firstly
employs its own
private key to decrypt the cyphertext, and obtains the number of the data
block cyphertext
(namely the number of the to-be-enquired data block cyphertext) desired to be
enquired
by the second node (namely the data receiving party).
[0079] S104 - employing, when the second node is allowed to enquire, a public
key of the second
node to encrypt a corresponding symmetric key, generating a second secret key
cyphertext, and transmitting the same to the second node through the
blockchain, so that
the second node employs its own private key to decrypt the second secret key
cyphertext
and obtain the corresponding symmetric key.
11
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0080] Specifically, if the first node agrees the second node to enquire the
to-be-enquired data
block cyphertext, the symmetric key used for encrypting the to-be-enquired
data block
cyphertext is uploaded to the blockchain, before such uploading, a public key
of a second
node obtained from the blockchain is employed to encrypt the corresponding
symmetric
key, and a second secret key cyphertext is generated and thereafter uploaded
to the
blockchain.
[0081] Fig. 2 is a flowchart illustrating the process of splitting data into
plural data blocks,
employing different symmetric keys to correspondingly encrypt the data blocks,
generating plural data block cyphertexts, numbering the same and uploading the
same to
the blockchain according to an exemplary embodiment, and with reference to
Fig. 2, the
process includes the following steps.
[0082] S101.1 ¨ splitting data into plural data blocks according to types of
information in the
data.
[0083] Specifically, the first node (namely the data transmitting party) can
flexibly split data
(namely a message) into plural data blocks according to business requirement.
For
instance, a message contains three types of information, namely username,
mobile phone
number, and mail address, and the transmitting terminal can split this message
into three
blocks.
[0084] S101.2 - generating one symmetric key corresponding to each data block.
[0085] Specifically, the first node traverses the plural data blocks, and one
symmetric key is
generated corresponding to each data block, in other words, the symmetric keys
can be
temporarily generated.
[0086] S101.3 - employing the symmetric keys respectively to encrypt
corresponding data blocks,
12
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
generating data block cyphertexts, numbering the same and thereafter uploading
the same
to the blockchain.
[0087] Specifically, different symmetric keys are respectively employed to
encrypt
corresponding data blocks to generate first encrypted data blocks, and the
first encrypted
data blocks are sequentially numbered and thereafter uploaded together with
their
numbers to the blockchain for storage, i.e., symmetric keys used by different
data blocks
are also different.
[0088] Fig. 3 is a flowchart illustrating the process of employing, when the
second node is
allowed to enquire, a public key of the second node to encrypt a corresponding
symmetric
key, generating a second secret key cyphertext, and transmitting the same to
the second
node through the blockchain according to an exemplary embodiment, and with
reference
to Fig. 3, the process includes the following steps.
[0089] S104.1 ¨ employing the private key of the first node to decrypt the
first secret key
cyphertext obtained from the blockchain, and obtaining the symmetric keys.
[0090] Specifically, if the first node agrees with the enquiring request of
the second node, the
first node firstly obtains the first secret key cyphertext from the
blockchain, employs its
own private key to decrypt the cyphertext, and obtains all symmetric keys.
[0091] S104.2 - obtaining a symmetric key to which the to-be-enquired data
block cyphertext
corresponds from the symmetric keys.
[0092] Specifically, the first node can enquire the symmetric keys according
to the number of
the to-be-enquired data block cyphertext or by any other means to obtain
therefrom the
symmetric key corresponding to the to-be-enquired data block cyphertext.
13
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0093] S104.3 - employing the public key of the second node to encrypt the
symmetric key to
which the to-be-enquired data block cyphertext corresponds, and generating a
second
secret key cyphertext.
[0094] Specifically, the first node obtains from the blockchain a public key
of the second node
shared by the second node, and then employs the public key of the second node
to encrypt
the symmetric key to which the to-be-enquired data block cyphertext
corresponds to
generate a second secret key cyphertext.
[0095] S104.4 - transmitting the second secret key cyphertext to the second
node through the
blockchain.
[0096] Specifically, the second node monitors the data in the blockchain, when
the first node
uploads the second secret key cyphertext to the blockchain, the second node
obtains the
second secret key cyphertext from the blockchain.
[0097] In another exemplary embodiment of the present invention, the method
further comprises:
[0098] generating an enquiry rejecting message when the second node is not
allowed to enquire,
and transmitting the same to the second node through the blockchain.
[0099] Specifically, the rejecting message does not contain the symmetric key
used for
encrypting the to-be-enquired data block cyphertext, so the second node cannot
obtain
the data block required to be enquired.
[0100] Fig. 4 is a flowchart of a data transmission method based on consortium
blockchain
according to an exemplary embodiment, and with reference to Fig. 4, the method
comprises the following steps.
[0101] S201 - employing a public key of a first node obtained from a
blockchain to encrypt a
14
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
number of a to-be-enquired data block cyphertext, generating a numbered
cyphertext,
signing the numbered cyphertext and transmitting the same to the blockchain.
[0102] Specifically, the second node (namely the data receiving party)
monitors data in the
blockchain. When a data block cyphertext is received and it is desired to
enquire certain
data blocks therein, the second node employs the public key of the first node
obtained
from the blockchain to encrypt the number of the to-be-enquired data block
cyphertext,
generates a numbered cyphertext, signs the numbered cyphertext and thereafter
transmits
the same to the blockchain. As should be noted here, it is the number of the
to-be-enquired
data block cyphertext that is encrypted and thereafter transmitted to the
blockchain, rather
than that the to-be-enquired data block cyphertext is encrypted and thereafter
transmitted
to the blockchain, whereby the load of data transmission can be reduced on the
one hand,
while on the other hand, it is made possible to keep secret the data block(s)
desired to be
enquired by the second node, and to prevent other nodes in the blockchain from
obtaining
the information. Additionally, signing the numbered cyphertext can facilitate
the first
node to make identification authentication on the second node, and to judge
whether to
consent to the enquiring request of the second node on the corresponding data
block(s).
[0103] S202 - obtaining a symmetric key to which the to-be-enquired data block
cyphertext
corresponds from the blockchain, decrypting the to-be-enquired data block
cyphertext,
and obtaining a data block as required.
[0104] Moreover, before the symmetric key to which the to-be-enquired data
block cyphertext
corresponds is obtained from the blockchain, a public key and a private key of
the second
node are locally generated, and the public key of the second node is
transmitted to the
blockchain.
[0105] Fig. 5 is a flowchart illustrating the process of obtaining a symmetric
key to which the to-
be-enquired data block cyphertext corresponds from the blockchain, decrypting
the to-
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
be-enquired data block cyphertext, and obtaining a data block as required
according to an
exemplary embodiment, and with reference to Fig. 5, the process includes the
following
steps.
[0106] S202.1 - obtaining a second secret key cyphertext from the blockchain,
wherein the
second secret key cyphertext is generated by the first node employing the
public key of
the second node to encrypt the symmetric key to which the to-be-enquired data
block
cyphertext corresponds.
[0107] Specifically, the second node monitors data on the blockchain, when the
first node
employs the public key of the second node to encrypt the symmetric key to
which the to-
be-enquired data block cyphertext corresponds, generates the second secret key
cyphertext and transmits the same to the blockchain, the second node obtains
the second
secret key cyphertext from the blockchain.
[0108] S202.2 - employing the private key of the second node to decrypt the
second secret key
cyphertext, and obtaining a corresponding symmetric key.
[0109] Specifically, the second node employs the private key that matches the
public key of the
second node to decrypt the second secret key cyphertext, and obtains the
symmetric key
used when the to-be-enquired data block cyphertext is encrypted.
[0110] S202.3 - employing the corresponding symmetric key to decrypt the to-be-
enquired data
block cyphertext, and obtaining a data block required to be enquired.
[0111] Specifically, the second node employs the corresponding symmetric key
to decrypt the
to-be-enquired data block cyphertext, and finally obtains the data block
required thereby,
thus facilitating enquiring by itself.
16
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0112] An exemplary example is taken below to help understand the specific
data transmitting
process of the data transmission method based on consortium blockchain
provided by the
embodiments of the present invention.
[0113] Suppose there are one data transmitting party S (namely a first node),
and two data
receiving parties A and B (namely a second node and a third node). Data
transmitting
party S, data receiving party A and data receiving party B employ an RSA
algorithm to
each generate a pair of public and private keys locally.
[0114] Data transmitting party S firstly splits a plaintext message Plain
(namely data) into n
blocks according to specific business requirement, i.e.,
Plain=Plain[1,2,...n]. Each data
block is then encrypted and numbered. The Plain array is cyclically traversed,
and an
AES KEY (namely a symmetric key) is temporarily generated by means of an AES
algorithm for each Plain element, i.e., Ci=AES encrypt(Pi, AES KEY). The AES
KEY
is employed to perform symmetric encryption on the element to obtain a
cyphertext
(namely a data block cyphertext), the cyphertext is numbered and then added to
a
cyphertext array, i.e., Cipher=[C1,C2...Cn]. Moreover, data transmitting party
S employs
its own public key RSA to encrypt the n number of AES KEYs to generate a first
secret
key cyphertext Ck=RSA encrypt(AES KEY, Pub S). Finally, the data block
cyphertext
Cipher and its number, and the first secret key cyphertext Ck are all uploaded
to the
blockchain for storage.
[0115] On receiving the data block cyphertext Cipher and its number, data
receiving party A
desires to know certain blocks therein, which are supposed to be the xth and
the yth blocks
here (x and y are both smaller than or equal to n). Data receiving party A
firstly employs
the public key of data transmitting party S to subject the numbers (namely x
and y) of the
xth and yth data block cyphertexts to RSA encryption, generates a numbered
cyphertext,
signs the same and thereafter stores the same in the blockchain, namely stores
ReqA=RSA encrypt(x,y),Pub S) in the blockchain.
17
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0116] On receiving the ReqA, data transmitting party S decrypts the same with
its own private
key, and obtains numbers x, y. If data transmitting party S consents to the
request of data
receiving party A to view Plain x, Plain y, corresponding secret keys AES
KEYx,
AES KEYy are stored in the blockchain. The specific process is as follows:
[0117] Ck is enquired from the blockchain, and decryption is made with its own
private key to
obtain all symmetric keys: AES KEY=RSA decrypt(Ck, Priv S). The xth and yth
AES KEYs are extracted from the AES KEYs, and the public key of data receiving
party
A is subsequently employed to encrypt the same to a second secret key
cyphertext RespA,
in which RespA = RSA encrypt(AES KEYx, AES KEYy), Pub A).
[0118] On receiving the RespA, data receiving party A firstly employs its
private key to decrypt
the same, and obtains AES KEYx, AES KEYy , namely: (AES KEYx, AES KEYy) =
RSA decrypt(RespA, Priv A). Subsequently, data receiving party A decrypts the
cyphertext according to the secret key as obtained, and obtains the required
message
blocks, namely:
[0119] Plainx=AES decrypt(Cx, AES KEYx)
[0120] Plainy=AES decrypt(Cy, AES KEYy)
[0121] In addition, on receiving the Cipher, data receiving party B desires to
know a certain
block therein, which is supposed to be the zth block (z is smaller than or
equal to n). Data
receiving party B employs the public key of data transmitting party S to
subject z to RSA
encryption, signs the same and thereafter stores the same in the blockchain,
namely
ReqB=RSA encrypt((z),Pub S).
[0122] On receiving the ReqB, data transmitting party S decrypts the same with
its own private
key, and obtains the number z. If data transmitting party S does not consent
to the request
of B, a response message is stored in the blockchain. The response message
obtained by
data receiving party B does not contain AES KEYz, in other words, data
receiving party
18
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
B cannot obtain any required message block.
[0123] Fig. 6 is a view schematically illustrating the structure of the data
transmission device
based on consortium blockchain according to an exemplary embodiment, and the
device
is applied to a first node on a blockchain, which does not belong to the
structure of the
device and is hence framed by dotted lines. With reference to Fig. 6, the
device at least
comprises:
[0124] a data splitting module, for splitting data into plural data blocks;
[0125] a first encrypting module, for employing different symmetric keys to
respectively and
correspondingly encrypt the plural data blocks, generating plural data block
cyphertexts,
numbering the same and uploading the same to the blockchain;
[0126] wherein the first encrypting module is further employed for employing a
public key of
the first node to encrypt the symmetric keys, generating a first secret key
cyphertext and
uploading the same to the blockchain;
[0127] a first decrypting module, for employing a private key of the first
node to decrypt a
numbered cyphertext coming from the blockchain, and obtaining a number of a to-
be-
enquired data block cyphertext of a second node, wherein the numbered
cyphertext is
generated by the second node employing the public key of the first node to
encrypt the
number of the to-be-enquired data block cyphertext;
[0128] wherein the first encrypting module is further employed for employing a
public key of
the second node to encrypt a corresponding symmetric key, and generating a
second secret
key cyphertext; and
[0129] a transmitting module, for transmitting the second secret key
cyphertext to the second
node through the blockchain.
[0130] Moreover, the device further comprises:
[0131] a first generating module, for generating one symmetric key
corresponding to each data
block.
19
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
[0132] Moreover, the device further comprises:
[0133] a second generating module, for locally generating a public key and a
private key of the
first node, and uploading the public key of the first node to the blockchain.
[0134] In another exemplary embodiment of the present invention, the first
decrypting module
is further employed for employing the private key of the first node to decrypt
the first
secret key cyphertext obtained from the blockchain, and obtaining the
symmetric keys.
[0135] The first encrypting module is further employed for employing a public
key of the second
node to encrypt the symmetric key to which the to-be-enquired data block
cyphertext
corresponds, and generating a second secret key cyphertext.
[0136] The transmitting module is further employed for generating an enquiry
rejecting message
when the second node is now allowed to enquire, and transmitting the same to
the second
node through the blockchain.
[0137] The device can further comprise:
[0138] an enquiring module, for obtaining a symmetric key to which the to-be-
enquired data
block cyphertext corresponds from the symmetric keys.
[0139] Fig. 7 is a view schematically illustrating the structure of the data
transmission device
based on consortium blockchain according to an exemplary embodiment, and the
device
is applied to a second node on a blockchain, which does not belong to the
structure of the
device and is hence framed by dotted lines. With reference to Fig. 7, the
device at least
comprises:
[0140] a second encrypting module, for employing a public key of a first node
obtained from a
blockchain to encrypt a number of a to-be-enquired data block cyphertext, and
generating
a numbered cyphertext;
[0141] a signing module, for signing the numbered cyphertext and transmitting
the same to the
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
blockchain;
[0142] an obtaining module, for obtaining a symmetric key to which the to-be-
enquired data
block cyphertext corresponds from the blockchain; and
[0143] a second decrypting module, for decrypting the to-be-enquired data
block cyphertext, and
obtaining a data block as required.
[0144] Moreover, the device further comprises:
[0145] a third generating module, for locally generating a public key and a
private key of a
second node, and transmitting the public key of the second node to the
blockchain.
[0146] In another exemplary embodiment of the present invention, the device
can further
comprise:
[0147] a receiving module, for obtaining a second secret key cyphertext from
the blockchain,
wherein the second secret key cyphertext is generated by the first node
employing the
public key of the second node to encrypt the symmetric key to which the to-be-
enquired
data block cyphertext corresponds.
[0148] The second decrypting module is further employed for employing the
private key of the
second node to decrypt the second secret key cyphertext, and obtaining
corresponding
symmetric keys.
[0149] In summary, the technical solutions provided by the embodiments of the
present invention
bring about the following advantageous effects.
[0150] 1. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, the first node on the
blockchain
of the data sharing system can self-define the block encryption strategy,
through the block
encryption method, the first node can flexibly control the message accessing
strategy to
control fine granularity, for instance, to allow the second node to view
designated sections
21
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
only, and authorization from the first node is required for the second node to
view certain
blocks in the message, whereby controllability of data is guaranteed.
[0151] 2. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, block encryption is
performed on
the message by means of a symmetric encryption algorithm, and symmetric keys
are
encrypted by means of an asymmetric encryption algorithm, whereby efficiency
of
encryption and decryption is enhanced as far as possible while data safety is
guaranteed.
[0152] 3. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, data is encrypted and
thereafter
stored on the blockchain, unless authorization is made, it is impossible for
other persons
to decrypt the data; moreover, when data blocks are encrypted and thereafter
transmitted,
what is stored on the blockchain is all the encrypted data, so that safety and
privacy of
the data are guaranteed.
[0153] 4. In the data transmission method and device based on consortium
blockchain as
provided by the embodiments of the present invention, all symmetric keys are
temporarily
generated and stored on the blockchain, as long as the local asymmetric
private key is not
lost, decryption can be made again from the blockchain very conveniently, so
that
restorability of data is guaranteed.
[0154] All the above optional technical solutions are randomly combinable to
form selectable
embodiments of the present invention, and these are not redundantly described
in a one-
by-one basis.
[0155] As should be noted, when the data transmission device based on
consortium blockchain
applied to a first node and a second node on a blockchain as provided by the
aforementioned embodiments triggers a data transmission business, the division
into the
22
Date Recue/Date Received 2022-05-24
CA 03162736 2022-05-24
aforementioned various functional modules is merely by way of example, while
it is
possible, in actual application, to base on requirements to assign the
functions to different
functional modules for completion, that is to say, to divide the internal
structure of the
device into different functional modules to complete the entire or partial
functions
described above. In addition, the data transmission device based on consortium
blockchain applied to a first node on a blockchain provided by the
aforementioned
embodiment pertains to the same conception as the data transmission method
based on
consortium blockchain provided by the method embodiment, and the data
transmission
device based on consortium blockchain applied to a second node on a blockchain
pertains
to the same conception as the data transmission method based on consortium
blockchain
provided by the method embodiment ¨ see the corresponding method embodiments
for
their specific realization processes, while no repetition will be made in this
context.
[0156] As understandable by persons ordinarily skilled in the art, realization
of the entire or
partial steps of the aforementioned embodiments can be completed by hardware,
or by a
program to instruct relevant hardware. The program can be stored in a computer-
readable
storage medium, and the storage medium can be a read-only memory, a magnetic
disk, or
an optical disk, etc.
[0157] What the above describes is merely directed to preferred embodiments of
the present
invention, and is not meant to restrict the present invention. Any amendment,
equivalent
replacement or improvement makeable within the spirit and principle of the
present
invention shall all be covered by the protection scope of the present
invention.
23
Date Recue/Date Received 2022-05-24