Note: Descriptions are shown in the official language in which they were submitted.
METHOD AND SYSTEM FOR MESSAGE RESPECIATION
FIELD OF THE DISCLOSURE
[0001] The present disclosure is related to monitoring of electronic messages,
and in
particular relates to extracting information from electronic messages created
using
message templates.
BACKGROUND
[0002] Extracted information from messages can be used in a variety of
situations. For
example, an electronic commerce platform may allow those with accounts on the
platform to connect their email accounts. Some or all of the emails arriving
at these
email accounts can then be monitored by the electronic commerce platform to
provide
value-added services such as tracking purchases, shipments and deliveries for
the
account holder.
[0003] In order to extract the information, an email extractor may be used.
SUMMARY
[0004] High accuracy and precision email extractors are typically created to
parse only
one specific email template each. Therefore, a sophisticated email extracting
system,
such as one built to interpret e-commerce emails from buyers' inboxes, may
require
thousands or hundreds of thousands of email extractors, each created to
identify
specific relevant information from a single distinct email template.
[0005] Information from messages generated utilizing a template can be
extracted by
utilizing a message extractor specialized for such template. However, for
systems
requiring thousands or hundreds of thousands of email extractors, the reuse of
extractors for templates bearing similarities saves resources.
1
Date Regue/Date Received 2022-07-07
[0006] Specifically, when parsing a growing stream of em ails whose formats
change
unpredictably over time, a solution that will improve scalability (e.g.
through automation)
would be beneficial.
[0007] The subject-matter of the present application relates to the
identification of a
similar cluster of one or more templates and the creation of grouped clusters
that can
use a single extractor for messages falling within the grouped cluster.
[0008] In one aspect, a computer-implemented method may be provided. The
method
may include applying a mapping function to a received message to create a
characteristic value, wherein the mapping function is adapted to map similar
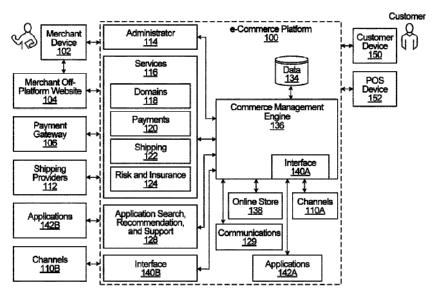
messages
to similar characteristic values. The method may further include comparing the
characteristic value to values associated with message clusters and
determining that
the characteristic value matches a cluster characteristic value associated
with at least
two message clusters. Responsive to determining that the characteristic value
matches
the cluster characteristic value associated with the at least two message
clusters, the
method may include linking the at least two message clusters into a combined
message
cluster, assigning a message extractor to the combined message cluster, the
message
extractor being selected from amongst message extractors associated with the
at least
two message clusters, and using the assigned message extractor to extract
information
from the received message.
[0009] In some embodiments the message extractor may be assigned based on
quality
scores for information extracted by message extractors associated with the at
least two
message clusters.
[0010] In some embodiments the at least two message clusters may include at
least one
previously combined message cluster.
2
Date Regue/Date Received 2022-07-07
[0011] In some embodiments the received message may comprise an email message
and wherein the mapping function may map Hypertext Markup Language (HTML)
elements from the email message extracted using XPaths.
[0012] In some embodiments the characteristic value may comprise an array of
values
created by using a minhash of the XPaths.
[0013] In some embodiments the characteristic value may match when a threshold
number of elements in the array is the same as a number of elements indicated
by the
value associated with at least one message cluster.
[0014] In some embodiments the method may further comprise checking
information
extracted against known information field values to verify the assigned
message
extractor is correctly extracting information.
[0015] In some embodiments the received message may be an electronic commerce
transaction message and wherein the computer system is an electronic commerce
platform.
[0016] In some embodiments messages associated with the at least two message
clusters that match the message may be from a first vendor and differ based on
a
number of products in the messages.
[0017] In one aspect, a computing device comprising a processor and
communications
subsystem may be provided. The computing device may be configured to apply a
mapping function to a received message to create a characteristic value,
wherein the
mapping function is adapted to map similar messages to similar characteristic
values.
The computing device may be further configured to compare the characteristic
value to
values associated with message clusters and determine that the characteristic
value
matches a cluster characteristic value associated with at least two message
clusters.
Responsive to determining that the characteristic value matches the cluster
3
Date Regue/Date Received 2022-07-07
characteristic value associated with the at least two message clusters, the
computing
device may be further configured to link the at least two message clusters
into a
combined message cluster, assign a message extractor to the combined message
cluster, the message extractor being selected from amongst message extractors
associated with the at least two message clusters, and use the assigned
message
extractor to extract information from the received message.
[0018] In some embodiments the message extractor may be assigned based on
quality
scores for information extracted by message extractors associated with the at
least two
message clusters.
[0019] In some embodiments the at least two message clusters may include at
least one
previously combined message cluster.
[0020] In some embodiments the received message may comprise an email message
and wherein the mapping function may map Hypertext Markup Language (HTML)
elements from the email message extracted using XPaths.
[0021] In some embodiments the characteristic value may comprise an array of
values
created by using a minhash of the XPaths.
[0022] In some embodiments the characteristic value may match when a threshold
number of elements in the array is the same as a number of elements indicated
by the
value associated with at least one message cluster.
[0023] In some embodiments the computing device may further be configured to
check
information extracted against known information field values to verify the
assigned
message extractor is correctly extracting information.
4
Date Regue/Date Received 2022-07-07
[0024] In some embodiments, the received message may be an electronic commerce
transaction message and wherein the computer system is an electronic commerce
platform.
[0025] In some embodiments messages associated with the at least two message
clusters that match the message may be from a first vendor and differ based on
a
number of products in the messages.
[0026] In a further aspect, a non-transitory computer readable medium for
storing
instruction code may be provided. The instruction code, when executed by a
processor
of a computing device, may cause the computing device to apply a mapping
function to
a received message to create a characteristic value, wherein the mapping
function is
adapted to map similar messages to similar characteristic values. The
instruction code,
when executed by a processor of a computing device, may further cause the
computing
device to compare the characteristic value to values associated with message
clusters
and determine that the characteristic value matches a cluster characteristic
value
associated with at least two message clusters. The instruction code, when
executed by
a processor of a computing device, may further cause the computing device to,
responsive to determining that the characteristic value matches the cluster
characteristic value associated with the at least two message clusters, link
the at least
two message clusters into a combined message cluster, assign a message
extractor to
the combined message cluster, the message extractor being selected from
amongst
message extractors associated with the at least two message clusters, and use
the
assigned message extractor to extract information from the received message.
[0027] In some embodiments, the message extractor may be assigned based on
quality
scores for information extracted by message extractors associated with the at
least two
message clusters.
Date Recue/Date Received 2022-07-07
BRIEF DESCRIPTION OF THE DRAWINGS
[0028] The present disclosure will be better understood with reference to the
drawings,
in which:
[0029] Figure 1 is a block diagram showing an example e-commerce system
capable of
implementing the embodiments of the present disclosure.
[0030] Figure 2 is a block diagram showing an example interface for a merchant
using
the e-commerce platform of Figure 1.
[0031] Figure 3 is a block diagram showing a first example message created
from a
template with information embedded therein.
[0032] Figure 4 is a block diagram showing a second example message created
from a
template with information embedded therein.
[0033] Figure 5 is a process diagram showing a process for assigning a value
to a
cluster.
[0034] Figure 6 is a block diagram showing two clusters and a threshold area
for
similarity scores in order to fall into each cluster.
[0035] Figure 7 is a block diagram showing three clusters, each with a
threshold area
for similarity scores in order to fall into the cluster, where a third cluster
falls into the
threshold area for two other clusters.
[0036] Figure 8 is a block diagram showing two combined clusters, where a
further
cluster falls into the threshold area for the two combined clusters.
[0037] Figure 9 is a process diagram showing a process for the assignment and
grouping of clusters based on received messages.
6
Date Regue/Date Received 2022-07-07
[0038] Figure 10 is a process diagram showing a process for retiring message
extractors.
[0039] Figure 11 is a block diagram of a simplified computer device capable of
being
used with embodiments of the present disclosure.
DETAILED DESCRIPTION
[0040] The present disclosure will now be described in detail by describing
various
illustrative, non-limiting embodiments thereof with reference to the
accompanying
drawings and exhibits. The disclosure may, however, be embodied in many
different
forms and should not be construed as being limited to the illustrative
embodiments set
forth herein. Rather, the embodiments are provided so that this disclosure
will be
thorough and will fully convey the concept of the disclosure to those skilled
in the art.
[0041] In accordance with the embodiments of the present disclosure, a
computer
system such as an e-commerce platform, may monitor a user's email box or other
messaging system for particular types of messages. Such messages are typically
computer generated and form part of the e-commerce transaction, and can
include
messages that an order has been placed, that an order has been shipped, that
the
order has been delivered, among other options. Typically, such message is
formed
utilizing a template. The e-commerce platform may include message extractors
for
known templates or groups of templates, where the message extractor can
successfully
extract information from such messages. While the use of message extractors
for use in
an electronic commerce setting are described below, the methods and systems of
the
present disclosure can equally be used in other systems to extract information
from
messages, and the use of an electronic commerce platform is therefore not
limiting and
provided for illustration only.
[0042] When a template changes (e.g., when a particular sender changes the
template
they are using for sending some or all of their messages), such as if a
merchant tweaks
7
Date Regue/Date Received 2022-07-07
or completely changes the layout of an email such as an Order Confirmation
email, a
new message extractor may need to be used to extract information from a
message
utilizing such new template. In other cases, the container for the template
may
completely change, such as a merchant moving from email notification to Short
Message Service (SMS) notifications. Further, in some cases the SMS
notifications
may have their own template.
[0043] An e-commerce platform serving thousands of vendors may have thousands
or
hundreds of thousands of message extractors based on known templates.
Therefore, in
some cases a new email extractor may need to be found or created for the new
template. Methods and systems for handling template changes were for example
described in U.S. Patent Application Serial Number 17/390,162, filed July 30,
2021, the
contents of which are incorporated herein by reference.
[0044] Systems and methods are provided below for applying a mapping function
to a
received message to create a characteristic value, also sometimes referred to
as a
fingerprint, wherein the mapping function is adapted to map similar messages
to similar
characteristic values. Emails with similar characteristic values may be
clustered
together.
[0045] Each cluster may be assigned one or more extractors. Typically, each
extractor
is created, designed, constructed, trained and/or instructed, manually and can
therefore
be time consuming to create. The extractor is used to retrieve values within
the
message that may be of interest to the system. Specifically, email messages
are, in
many cases, auto-generated using templates, and such templates will map to
similar
identifiers. For example, as provided above, an email extractor may extract a
Tracking
Identifier, Order Date, Ship Date, Carrier, and Products, or other
information, related to
an order from a buyer's shipping notification email received from a merchant
with whom
they recently placed an order. The email extractor may use XPaths within the
message
to find the information in some cases. However other options are possible.
8
Date Regue/Date Received 2022-07-07
[0046] Characteristic values can then be compared to a value associated with
each of a
plurality of clusters. When an incoming email is entered into the extracting
system, the
system identifies a relevant extractor or extractors to assign to it.
Typically, this is done
by using a clustering algorithm to identify and cluster distinct groups of
emails together.
For example, store ABC Order Confirmation cluster, store ABC Shipping Update
cluster.
The groups of em ails in these clusters may be across multiple vendors who use
the
same templates, and the clusters are not necessarily tagged explicitly.
[0047] When classifying a new email message, the new email message may overlap
with two separate clusters. This may indicate that there is a similarity
between the new
email message and the two clusters that it overlaps with. For example, in one
case, an
email confirmation from a particular vendor for a single product may be put
into a first
cluster. An email confirmation from the same vendor for an order with three
products
may be put into a second cluster. In some cases, the minhash values or
similarity
indexes for the first and second cluster may not overlap. However, when a
third email
message is received from the same vendor for an order with two products, when
classifying that message, it may be discovered that it is similar to both the
first cluster
and the second cluster. This may indicate a relationship between the first
cluster,
second cluster, and the new email message.
[0048] In this case, the clusters may be grouped to form a combined cluster
and a single
extractor or group of extractors may be assigned to the combined cluster, as
described
below.
[0049] While the examples in the present disclosure are for an email
processing system
that is part of an ecommerce platform, this is merely provided for
illustration. The
embodiments of the present disclosure could equally be used with any email
processing
system.
9
Date Regue/Date Received 2022-07-07
[0050] An example e-commerce platform
[0051] Although integration with a commerce platform is not required, in some
embodiments, the methods disclosed herein may be performed on or in
association with
a commerce platform such as an e-commerce platform. Therefore, an example of a
commerce platform will be described.
[0052] FIG. 1 illustrates an example e-commerce platform 100, according to one
embodiment. The e-commerce platform 100 may be used to provide merchant
products
and services to customers. While the disclosure contemplates using the
apparatus,
system, and process to purchase products and services, for simplicity the
description
herein will refer to products. All references to products throughout this
disclosure should
also be understood to be references to products and/or services, including,
for example,
physical products, digital content (e.g., music, videos, games), software,
tickets,
subscriptions, services to be provided, and the like.
[0053] While the disclosure throughout contemplates that a 'merchant' and a
'customer'
may be more than individuals, for simplicity the description herein may
generally refer to
merchants and customers as such. All references to merchants and customers
throughout this disclosure should also be understood to be references to
groups of
individuals, companies, corporations, computing entities, and the like, and
may
represent for-profit or not-for-profit exchange of products. Further, while
the disclosure
throughout refers to 'merchants' and 'customers', and describes their roles as
such, the
e-commerce platform 100 should be understood to more generally support users
in an
e-commerce environment, and all references to merchants and customers
throughout
this disclosure should also be understood to be references to users, such as
where a
user is a merchant-user (e.g., a seller, retailer, wholesaler, or provider of
products), a
customer-user (e.g., a buyer, purchase agent, consumer, or user of products),
a
prospective user (e.g., a user browsing and not yet committed to a purchase, a
user
evaluating the e-commerce platform 100 for potential use in marketing and
selling
products, and the like), a service provider user (e.g., a shipping provider
112, a financial
provider, and the like), a company or corporate user (e.g., a company
representative for
Date Recue/Date Received 2022-07-07
purchase, sales, or use of products; an enterprise user; a customer relations
or
customer management agent, and the like), an information technology user, a
computing entity user (e.g., a computing bot for purchase, sales, or use of
products),
and the like. Furthermore, it may be recognized that while a given user may
act in a
given role (e.g., as a merchant) and their associated device may be referred
to
accordingly (e.g., as a merchant device) in one context, that same individual
may act in
a different role in another context (e.g., as a customer) and that same or
another
associated device may be referred to accordingly (e.g., as a customer device).
For
example, an individual may be a merchant for one type of product (e.g.,
shoes), and a
customer/consumer of other types of products (e.g., groceries). In another
example, an
individual may be both a consumer and a merchant of the same type of product.
In a
particular example, a merchant that trades in a particular category of goods
may act as
a customer for that same category of goods when they order from a wholesaler
(the
wholesaler acting as merchant).
[0054] The e-commerce platform 100 provides merchants with online
services/facilities
to manage their business. The facilities described herein are shown
implemented as
part of the platform 100 but could also be configured separately from the
platform 100,
in whole or in part, as stand-alone services. Furthermore, such facilities
may, in some
embodiments, may, additionally or alternatively, be provided by one or more
providers/entities.
[0055] In the example of FIG. 1, the facilities are deployed through a
machine, service
or engine that executes computer software, modules, program codes, and/or
instructions on one or more processors which, as noted above, may be part of
or
external to the platform 100. Merchants may utilize the e-commerce platform
100 for
enabling or managing commerce with customers, such as by implementing an e-
commerce experience with customers through an online store 138, applications
142A-
B, channels 110A-B, and/or through point of sale (POS) devices 152 in physical
locations (e.g., a physical storefront or other location such as through a
kiosk, terminal,
reader, printer, 3D printer, and the like). A merchant may utilize the e-
commerce
11
Date Recue/Date Received 2022-07-07
platform 100 as a sole commerce presence with customers, or in conjunction
with other
merchant commerce facilities, such as through a physical store (e.g., 'brick-
and-mortar
retail stores), a merchant off-platform website 104 (e.g., a commerce Internet
website or
other internet or web property or asset supported by or on behalf of the
merchant
separately from the e-commerce platform 100), an application 142B, and the
like.
However, even these 'other' merchant commerce facilities may be incorporated
into or
communicate with the e-commerce platform 100, such as where POS devices 152 in
a
physical store of a merchant are linked into the e-commerce platform 100,
where a
merchant off-platform website 104 is tied into the e-commerce platform 100,
such as, for
example, through 'buy buttons' that link content from the merchant off
platform website
104 to the online store 138, or the like.
[0056] The online store 138 may represent a multi-tenant facility comprising a
plurality of
virtual storefronts. In embodiments, merchants may configure and/or manage one
or
more storefronts in the online store 138, such as, for example, through a
merchant
device 102 (e.g., computer, laptop computer, mobile computing device, and the
like),
and offer products to customers through a number of different channels 110A-B
(e.g.,
an online store 138; an application 142A-B; a physical storefront through a
POS device
152; an electronic marketplace, such, for example, through an electronic buy
button
integrated into a website or social media channel such as on a social network,
social
media page, social media messaging system; and/or the like). A merchant may
sell
across channels 110A-B and then manage their sales through the e-commerce
platform
100, where channels 110A may be provided as a facility or service internal or
external
to the e-commerce platform 100. A merchant may, additionally or alternatively,
sell in
their physical retail store, at pop ups, through wholesale, over the phone,
and the like,
and then manage their sales through the e-commerce platform 100. A merchant
may
employ all or any combination of these operational modalities. Notably, it may
be that by
employing a variety of and/or a particular combination of modalities, a
merchant may
improve the probability and/or volume of sales. Throughout this disclosure the
terms
online store 138 and storefront may be used synonymously to refer to a
merchant's
online e-commerce service offering through the e-commerce platform 100, where
an
12
Date Regue/Date Received 2022-07-07
online store 138 may refer either to a collection of storefronts supported by
the e-
commerce platform 100 (e.g., for one or a plurality of merchants) or to an
individual
merchant's storefront (e.g., a merchant's online store).
[0057] In some embodiments, a customer may interact with the platform 100
through a
customer device 150 (e.g., computer, laptop computer, mobile computing device,
or the
like), a POS device 152 (e.g., retail device, kiosk, automated (self-service)
checkout
system, or the like), and/or any other commerce interface device known in the
art. The
e-commerce platform 100 may enable merchants to reach customers through the
online
store 138, through applications 142A-B, through POS devices 152 in physical
locations
(e.g., a merchant's storefront or elsewhere), to communicate with customers
via
electronic communication facility 129, and/or the like so as to provide a
system for
reaching customers and facilitating merchant services for the real or virtual
pathways
available for reaching and interacting with customers.
[0058] In some embodiments, and as described further herein, the e-commerce
platform
100 may be implemented through a processing facility. Such a processing
facility may
include a processor and a memory. The processor may be a hardware processor.
The
memory may be and/or may include a non-transitory computer-readable medium.
The
memory may be and/or may include random access memory (RAM) and/or persisted
storage (e.g., magnetic storage). The processing facility may store a set of
instructions
(e.g., in the memory) that, when executed, cause the e-commerce platform 100
to
perform the e-commerce and support functions as described herein. The
processing
facility may be or may be a part of one or more of a server, client, network
infrastructure, mobile computing platform, cloud computing platform,
stationary
computing platform, and/or some other computing platform, and may provide
electronic
connectivity and communications between and amongst the components of the e-
commerce platform 100, merchant devices 102, payment gateways 106,
applications
142A-B, channels 110A-B, shipping providers 112, customer devices 150, point
of sale
devices 152, etc.. In some implementations, the processing facility may be or
may
include one or more such computing devices acting in concert. For example, it
may be
13
Date Regue/Date Received 2022-07-07
that a plurality of co-operating computing devices serves as/to provide the
processing
facility. The e-commerce platform 100 may be implemented as or using one or
more of
a cloud computing service, software as a service (SaaS), infrastructure as a
service
(laaS), platform as a service (PaaS), desktop as a service (DaaS), managed
software
as a service (MSaaS), mobile backend as a service (MBaaS), information
technology
management as a service (ITMaaS), and/or the like. For example, it may be that
the
underlying software implementing the facilities described herein (e.g., the
online store
138) is provided as a service, and is centrally hosted (e.g., and then
accessed by users
via a web browser or other application, and/or through customer devices 150,
POS
devices 152, and/or the like). In some embodiments, elements of the e-commerce
platform 100 may be implemented to operate and/or integrate with various other
platforms and operating systems.
[0059] In some embodiments, the facilities of the e-commerce platform 100
(e.g., the
online store 138) may serve content to a customer device 150 (using data 134)
such as,
for example, through a network connected to the e-commerce platform 100. For
example, the online store 138 may serve or send content in response to
requests for
data 134 from the customer device 150, where a browser (or other application)
connects to the online store 138 through a network using a network
communication
protocol (e.g., an internet protocol). The content may be written in machine
readable
language and may include Hypertext Markup Language (HTML), template language,
JavaScript, and the like, and/or any combination thereof.
[0060] In some embodiments, online store 138 may be or may include service
instances
that serve content to customer devices and allow customers to browse and
purchase
the various products available (e.g., add them to a cart, purchase through a
buy-button,
and the like). Merchants may also customize the look and feel of their website
through
a theme system, such as, for example, a theme system where merchants can
select
and change the look and feel of their online store 138 by changing their theme
while
having the same underlying product and business data shown within the online
store's
product information. It may be that themes can be further customized through a
theme
14
Date Recue/Date Received 2022-07-07
editor, a design interface that enables users to customize their website's
design with
flexibility. Additionally or alternatively, it may be that themes can,
additionally or
alternatively, be customized using theme-specific settings such as, for
example, settings
as may change aspects of a given theme, such as, for example, specific colors,
fonts,
and pre-built layout schemes. In some implementations, the online store may
implement
a content management system for website content. Merchants may employ such a
content management system in authoring blog posts or static pages and publish
them to
their online store 138, such as through blogs, articles, landing pages, and
the like, as
well as configure navigation menus. Merchants may upload images (e.g., for
products),
video, content, data, and the like to the e-commerce platform 100, such as for
storage
by the system (e.g., as data 134). In some embodiments, the e-commerce
platform 100
may provide functions for manipulating such images and content such as, for
example,
functions for resizing images, associating an image with a product, adding and
associating text with an image, adding an image for a new product variant,
protecting
images, and the like.
[0061] As described herein, the e-commerce platform 100 may provide merchants
with
sales and marketing services for products through a number of different
channels 110A-
B, including, for example, the online store 138, applications 142A-B, as well
as through
physical POS devices 152 as described herein. The e-commerce platform 100 may,
additionally or alternatively, include business support services 116, an
administrator
114, a warehouse management system, and the like associated with running an on-
line
business, such as, for example, one or more of providing a domain registration
service
118 associated with their online store, payment services 120 for facilitating
transactions
with a customer, shipping services 122 for providing customer shipping options
for
purchased products, fulfillment services for managing inventory, risk and
insurance
services 124 associated with product protection and liability, merchant
billing, and the
like. Services 116 may be provided via the e-commerce platform 100 or in
association
with external facilities, such as through a payment gateway 106 for payment
processing,
shipping providers 112 for expediting the shipment of products, and the like.
Date Regue/Date Received 2022-07-07
[0062] In some embodiments, the e-commerce platform 100 may be configured with
shipping services 122 (e.g., through an e-commerce platform shipping facility
or through
a third-party shipping carrier), to provide various shipping-related
information to
merchants and/or their customers such as, for example, shipping label or rate
information, real-time delivery updates, tracking, and/or the like.
[0063] FIG. 2 depicts a non-limiting embodiment for a home page of an
administrator
114. The administrator 114 may be referred to as an administrative console
and/or an
administrator console. The administrator 114 may show information about daily
tasks, a
store's recent activity, and the next steps a merchant can take to build their
business. In
some embodiments, a merchant may log in to the administrator 114 via a
merchant
device 102 (e.g., a desktop computer or mobile device), and manage aspects of
their
online store 138, such as, for example, viewing the online store's 138 recent
visit or
order activity, updating the online store's 138 catalog, managing orders,
and/or the like.
In some embodiments, the merchant may be able to access the different sections
of the
administrator 114 by using a sidebar, such as the one shown on FIG. 2.
Sections of the
administrator 114 may include various interfaces for accessing and managing
core
aspects of a merchant's business, including orders, products, customers,
available
reports and discounts. The administrator 114 may, additionally or
alternatively, include
interfaces for managing sales channels for a store including the online store
138, mobile
application(s) made available to customers for accessing the store (Mobile
App), POS
devices, and/or a buy button. The administrator 114 may, additionally or
alternatively,
include interfaces for managing applications (apps) installed on the
merchant's account;
and settings applied to a merchant's online store 138 and account. A merchant
may use
a search bar to find products, pages, or other information in their store.
[0064] More detailed information about commerce and visitors to a merchant's
online
store 138 may be viewed through reports or metrics. Reports may include, for
example,
acquisition reports, behavior reports, customer reports, finance reports,
marketing
reports, sales reports, product reports, and custom reports. The merchant may
be able
to view sales data for different channels 110A-B from different periods of
time (e.g.,
16
Date Regue/Date Received 2022-07-07
days, weeks, months, and the like), such as by using drop-down menus. An
overview
dashboard may also be provided for a merchant who wants a more detailed view
of the
store's sales and engagement data. An activity feed in the home metrics
section may be
provided to illustrate an overview of the activity on the merchant's account.
For
example, by clicking on a 'view all recent activity' dashboard button, the
merchant may
be able to see a longer feed of recent activity on their account. A home page
may show
notifications about the merchant's online store 138, such as based on account
status,
growth, recent customer activity, order updates, and the like. Notifications
may be
provided to assist a merchant with navigating through workflows configured for
the
online store 138, such as, for example, a payment workflow, an order
fulfillment
workflow, an order archiving workflow, a return workflow, and the like.
[0065] The e-commerce platform 100 may provide for a communications facility
129 and
associated merchant interface for providing electronic communications and
marketing,
such as utilizing an electronic messaging facility for collecting and
analyzing
communication interactions between merchants, customers, merchant devices 102,
customer devices 150, POS devices 152, and the like, to aggregate and analyze
the
communications, such as for increasing sale conversions, and the like. For
instance, a
customer may have a question related to a product, which may produce a dialog
between the customer and the merchant (or an automated processor-based
agent/chatbot representing the merchant), where the communications facility
129 is
configured to provide automated responses to customer requests and/or provide
recommendations to the merchant on how to respond such as, for example, to
improve
the probability of a sale.
[0066] The e-commerce platform 100 may provide a financial facility 120 for
secure
financial transactions with customers, such as through a secure card server
environment. The e-commerce platform 100 may store credit card information,
such as
in payment card industry data (PCI) environments (e.g., a card server), to
reconcile
financials, bill merchants, perform automated clearing house (ACH) transfers
between
the e-commerce platform 100 and a merchant's bank account, and the like. The
17
Date Recue/Date Received 2022-07-07
financial facility 120 may also provide merchants and buyers with financial
support, such
as through the lending of capital (e.g., lending funds, cash advances, and the
like) and
provision of insurance. In some embodiments, online store 138 may support a
number
of independently administered storefronts and process a large volume of
transactional
data on a daily basis for a variety of products and services. Transactional
data may
include any customer information indicative of a customer, a customer account
or
transactions carried out by a customer such as. for example, contact
information, billing
information, shipping information, returns/refund information, discount/offer
information,
payment information, or online store events or information such as page views,
product
search information (search keywords, click-through events), product reviews,
abandoned carts, and/or other transactional information associated with
business
through the e-commerce platform 100. In some embodiments, the e-commerce
platform
100 may store this data in a data facility 134. Referring again to FIG. 1, in
some
embodiments the e-commerce platform 100 may include a commerce management
engine 136 such as may be configured to perform various workflows for task
automation
or content management related to products, inventory, customers, orders,
suppliers,
reports, financials, risk and fraud, and the like. In some embodiments,
additional
functionality may, additionally or alternatively, be provided through
applications 142A-B
to enable greater flexibility and customization required for accommodating an
ever-
growing variety of online stores, POS devices, products, and/or services.
Applications
142A may be components of the e-commerce platform 100 whereas applications
142B
may be provided or hosted as a third-party service external to e-commerce
platform
100. The commerce management engine 136 may accommodate store-specific
workflows and in some embodiments, may incorporate the administrator 114
and/or the
online store 138.
[0067] Implementing functions as applications 142A-B may enable the commerce
management engine 136 to remain responsive and reduce or avoid service
degradation
or more serious infrastructure failures, and the like.
18
Date Regue/Date Received 2022-07-07
[0068] Although isolating online store data can be important to maintaining
data privacy
between online stores 138 and merchants, there may be reasons for collecting
and
using cross-store data, such as, for example, with an order risk assessment
system or a
platform payment facility, both of which require information from multiple
online stores
138 to perform well. In some embodiments, it may be preferable to move these
components out of the commerce management engine 136 and into their own
infrastructure within the e-commerce platform 100.
[0069] Platform payment facility 120 is an example of a component that
utilizes data
from the commerce management engine 136 but is implemented as a separate
component or service. The platform payment facility 120 may allow customers
interacting with online stores 138 to have their payment information stored
safely by the
commerce management engine 136 such that they only have to enter it once. When
a
customer visits a different online store 138, even if they have never been
there before,
the platform payment facility 120 may recall their information to enable a
more rapid
and/or potentially less-error prone (e.g., through avoidance of possible mis-
keying of
their information if they needed to instead re-enter it) checkout. This may
provide a
cross-platform network effect, where the e-commerce platform 100 becomes more
useful to its merchants and buyers as more merchants and buyers join, such as
because there are more customers who checkout more often because of the ease
of
use with respect to customer purchases. To maximize the effect of this
network,
payment information for a given customer may be retrievable and made available
globally across multiple online stores 138.
[0070] For functions that are not included within the commerce management
engine
136, applications 142A-B provide a way to add features to the e-commerce
platform
100 or individual online stores 138. For example, applications 142A-B may be
able to
access and modify data on a merchant's online store 138, perform tasks through
the
administrator 114, implement new flows for a merchant through a user interface
(e.g.,
that is surfaced through extensions / API), and the like. Merchants may be
enabled to
discover and install applications 142A-B through application search,
recommendations,
19
Date Regue/Date Received 2022-07-07
and support 128. In some embodiments, the commerce management engine 136,
applications 142A-B, and the administrator 114 may be developed to work
together. For
instance, application extension points may be built inside the commerce
management
engine 136, accessed by applications 142A and 142B through the interfaces 140B
and
140A to deliver additional functionality, and surfaced to the merchant in the
user
interface of the administrator 114.
[0071] In some embodiments, applications 142A-B may deliver functionality to a
merchant through the interface 140A-B, such as where an application 142A-B is
able to
surface transaction data to a merchant (e.g., App: "Engine, surface my app
data in the
Mobile App or administrator 114"), and/or where the commerce management engine
136 is able to ask the application to perform work on demand (Engine: "App,
give me a
local tax calculation for this checkout").
[0072] Applications 142A-B may be connected to the commerce management engine
136 through an interface 140A-B (e.g., through REST (REpresentational State
Transfer)
and/or GraphQL APIs) to expose the functionality and/or data available through
and
within the commerce management engine 136 to the functionality of
applications. For
instance, the e-commerce platform 100 may provide API interfaces 140A-B to
applications 142A-B which may connect to products and services external to the
platform 100. The flexibility offered through use of applications and APIs
(e.g., as
offered for application development) enable the e-commerce platform 100 to
better
accommodate new and unique needs of merchants or to address specific use cases
without requiring constant change to the commerce management engine 136. For
instance, shipping services 122 may be integrated with the commerce management
engine 136 through a shipping or carrier service API, thus enabling the e-
commerce
platform 100 to provide shipping service functionality without directly
impacting code
running in the commerce management engine 136.
[0073] Depending on the implementation, applications 142A-B may utilize APIs
to pull
data on demand (e.g., customer creation events, product change events, or
order
Date Regue/Date Received 2022-07-07
cancelation events, etc.) or have the data pushed when updates occur. A
subscription
model may be used to provide applications 142A-B with events as they occur or
to
provide updates with respect to a changed state of the commerce management
engine
136. In some embodiments, when a change related to an update event
subscription
occurs, the commerce management engine 136 may post a request, such as to a
predefined callback URL. The body of this request may contain a new state of
the object
and a description of the action or event. Update event subscriptions may be
created
manually, in the administrator facility 114, or automatically (e.g., via the
API 140A-B). In
some embodiments, update events may be queued and processed asynchronously
from a state change that triggered them, which may produce an update event
notification that is not distributed in real-time or near-real time.
[0074] In some embodiments, the e-commerce platform 100 may provide one or
more of
application search, recommendation and support 128. Application search,
recommendation and support 128 may include developer products and tools to aid
in
the development of applications, an application dashboard (e.g., to provide
developers
with a development interface, to administrators for management of
applications, to
merchants for customization of applications, and the like), facilities for
installing and
providing permissions with respect to providing access to an application 142A-
B (e.g.,
for public access, such as where criteria must be met before being installed,
or for
private use by a merchant), application searching to make it easy for a
merchant to
search for applications 142A-B that satisfy a need for their online store 138,
application
recommendations to provide merchants with suggestions on how they can improve
the
user experience through their online store 138, and the like. In some
embodiments,
applications 142A-B may be assigned an application identifier (ID), such as
for linking to
an application (e.g., through an API), searching for an application, making
application
recommendations, and the like.
[0075] Applications 142A-B may be grouped roughly into three categories:
customer-
facing applications, merchant-facing applications, integration applications,
and the like.
Customer-facing applications 142A-B may include an online store 138 or
channels
21
Date Regue/Date Received 2022-07-07
110A-B that are places where merchants can list products and have them
purchased
(e.g., the online store, applications for flash sales (e.g., merchant products
or from
opportunistic sales opportunities from third-party sources), a mobile store
application, a
social media channel, an application for providing wholesale purchasing, and
the like).
Merchant-facing applications 142A-B may include applications that allow the
merchant
to administer their online store 138 (e.g., through applications related to
the web or
website or to mobile devices), run their business (e.g., through applications
related to
POS devices), to grow their business (e.g., through applications related to
shipping
(e.g., drop shipping), use of automated agents, use of process flow
development and
improvements), and the like. Integration applications may include applications
that
provide useful integrations that participate in the running of a business,
such as
shipping providers 112 and payment gateways 106.
[0076] As such, the e-commerce platform 100 can be configured to provide an
online
shopping experience through a flexible system architecture that enables
merchants to
connect with customers in a flexible and transparent manner. A typical
customer
experience may be better understood through an embodiment example purchase
workflow, where the customer browses the merchant's products on a channel 110A-
B,
adds what they intend to buy to their cart, proceeds to checkout, and pays for
the
content of their cart resulting in the creation of an order for the merchant.
The merchant
may then review and fulfill (or cancel) the order. The product is then
delivered to the
customer. If the customer is not satisfied, they might return the products to
the
merchant.
[0077] In an example embodiment, a customer may browse a merchant's products
through a number of different channels 110A-B such as, for example, the
merchant's
online store 138, a physical storefront through a POS device 152; an
electronic
marketplace, through an electronic buy button integrated into a website or a
social
media channel). In some cases, channels 110A-B may be modeled as applications
142A-B. A merchandising component in the commerce management engine 136 may
be configured for creating, and managing product listings (using product data
objects or
22
Date Recue/Date Received 2022-07-07
models for example) to allow merchants to describe what they want to sell and
where
they sell it. The association between a product listing and a channel may be
modeled as
a product publication and accessed by channel applications, such as via a
product
listing API. A product may have many attributes and/or characteristics, like
size and
color, and many variants that expand the available options into specific
combinations of
all the attributes, like a variant that is size extra-small and green, or a
variant that is size
large and blue. Products may have at least one variant (e.g., a "default
variant") created
for a product without any options. To facilitate browsing and management,
products
may be grouped into collections, provided product identifiers (e.g., stock
keeping unit
(SKU)) and the like. Collections of products may be built by either manually
categorizing
products into one (e.g., a custom collection), by building rulesets for
automatic
classification (e.g., a smart collection), and the like. Product listings may
include 2D
images, 3D images or models, which may be viewed through a virtual or
augmented
reality interface, and the like.
[0078] In some embodiments, a shopping cart object is used to store or keep
track of
the products that the customer intends to buy. The shopping cart object may be
channel
specific and can be composed of multiple cart line items, where each cart line
item
tracks the quantity for a particular product variant. Since adding a product
to a cart does
not imply any commitment from the customer or the merchant, and the expected
lifespan of a cart may be in the order of minutes (not days), cart
objects/data
representing a cart may be persisted to an ephemeral data store.
[0079] The customer then proceeds to checkout. A checkout object or page
generated
by the commerce management engine 136 may be configured to receive customer
information to complete the order such as the customer's contact information,
billing
information and/or shipping details. If the customer inputs their contact
information but
does not proceed to payment, the e-commerce platform 100 may (e.g., via an
abandoned checkout component) transmit a message to the customer device 150 to
encourage the customer to complete the checkout. For those reasons, checkout
objects
can have much longer lifespans than cart objects (hours or even days) and may
23
Date Regue/Date Received 2022-07-07
therefore be persisted. Customers then pay for the content of their cart
resulting in the
creation of an order for the merchant. In some embodiments, the commerce
management engine 136 may be configured to communicate with various payment
gateways and services 106 (e.g., online payment systems, mobile payment
systems,
digital wallets, credit card gateways) via a payment processing component. The
actual
interactions with the payment gateways 106 may be provided through a card
server
environment. At the end of the checkout process, an order is created. An order
is a
contract of sale between the merchant and the customer where the merchant
agrees to
provide the goods and services listed on the order (e.g., order line items,
shipping line
items, and the like) and the customer agrees to provide payment (including
taxes).
Once an order is created, an order confirmation notification may be sent to
the customer
and an order placed notification sent to the merchant via a notification
component.
Inventory may be reserved when a payment processing job starts to avoid over-
selling
(e.g., merchants may control this behavior using an inventory policy or
configuration for
each variant). Inventory reservation may have a short time span (minutes) and
may
need to be fast and scalable to support flash sales or "drops", which are
events during
which a discount, promotion or limited inventory of a product may be offered
for sale for
buyers in a particular location and/or for a particular (usually short) time.
The
reservation is released if the payment fails. When the payment succeeds, and
an order
is created, the reservation is converted into a permanent (long-term)
inventory
commitment allocated to a specific location. An inventory component of the
commerce
management engine 136 may record where variants are stocked, and may track
quantities for variants that have inventory tracking enabled. It may decouple
product
variants (a customer-facing concept representing the template of a product
listing) from
inventory items (a merchant-facing concept that represents an item whose
quantity and
location is managed). An inventory level component may keep track of
quantities that
are available for sale, committed to an order or incoming from an inventory
transfer
component (e.g., from a vendor).
[0080] The merchant may then review and fulfill (or cancel) the order. A
review
component of the commerce management engine 136 may implement a business
24
Date Recue/Date Received 2022-07-07
process merchant's use to ensure orders are suitable for fulfillment before
actually
fulfilling them. Orders may be fraudulent, require verification (e.g., ID
checking), have a
payment method which requires the merchant to wait to make sure they will
receive
their funds, and the like. Risks and recommendations may be persisted in an
order risk
model. Order risks may be generated from a fraud detection tool, submitted by
a
third-party through an order risk API, and the like. Before proceeding to
fulfillment, the
merchant may need to capture the payment information (e.g., credit card
information) or
wait to receive it (e.g., via a bank transfer, check, and the like) before it
marks the order
as paid. The merchant may now prepare the products for delivery. In some
embodiments, this business process may be implemented by a fulfillment
component of
the commerce management engine 136. The fulfillment component may group the
line
items of the order into a logical fulfillment unit of work based on an
inventory location
and fulfillment service. The merchant may review, adjust the unit of work, and
trigger the
relevant fulfillment services, such as through a manual fulfillment service
(e.g., at
merchant managed locations) used when the merchant picks and packs the
products in
a box, purchase a shipping label and input its tracking number, or just mark
the item as
fulfilled. Alternatively, an API fulfillment service may trigger a third-party
application or
service to create a fulfillment record for a third-party fulfillment service.
Other
possibilities exist for fulfilling an order. If the customer is not satisfied,
they may be able
to return the product(s) to the merchant. The business process merchants may
go
through to "un-sell" an item may be implemented by a return component. Returns
may
consist of a variety of different actions, such as a restock, where the
product that was
sold actually comes back into the business and is sellable again; a refund,
where the
money that was collected from the customer is partially or fully returned; an
accounting
adjustment noting how much money was refunded (e.g., including if there was
any
restocking fees or goods that weren't returned and remain in the customer's
hands); and
the like. A return may represent a change to the contract of sale (e.g., the
order), and
where the e-commerce platform 100 may make the merchant aware of compliance
issues with respect to legal obligations (e.g., with respect to taxes). In
some
embodiments, the e-commerce platform 100 may enable merchants to keep track of
changes to the contract of sales over time, such as implemented through a
sales model
Date Regue/Date Received 2022-07-07
component (e.g., an append-only date-based ledger that records sale-related
events
that happened to an item).
[0081] Message Templates
[0082] As provided above, the embodiments of the present disclosure could be
implemented on any email processing system. For example, an electronic
commerce
platform such as that described with regards to Figure 1, may allow those with
accounts
on the platform to (with appropriate disclosure and consent, as required, for
example, by
applicable law or practice) connect their messaging accounts to the system to
allow
messages from those accounts to be retrieved and/or accessed. Messaging
accounts
may include email accounts, text message accounts, or any other type of
account in
which a merchant may send messages to a customer. The present disclosure is
described with regards to email accounts for illustration. However, this is
not limiting,
and the same principles could be applied to other types of messaging accounts.
[0083] Some or all of the messages arriving at these email accounts can then
be
monitored by the electronic commerce platform to provide value-added services
such as
tracking purchases, shipments and deliveries for the account holder.
[0084] Typically, such messages will be computer generated using a template. A
template is indicative of a structure or layout of a message. For example,
reference is
made to Figure 3.
[0085] In the example of Figure 3, a message 300 may be received by an account
holder within a message processing system. The account holder has subscribed
to the
message processing system to monitor transactions and in this regard, the
message
300 may be analyzed by the message processing system.
[0086] Message 300 is from a vendor who uses a first template. For example,
message
300 is a shipping notification to indicate that a product has shipped or will
soon ship.
Various fields within the message are filled in by the computer generating the
message
26
Date Regue/Date Received 2022-07-07
and the remainder of the template remains the same between messages. For
example,
the template for message 300 includes a name field 310, a shipping date 312,
an
address shipped to block 314, as well as a URL for the shipping number shown
with
URL 316 for a shipper 318.
[0087] Referring to Figure 4, another example email received by an account
holder for
an e-commerce platform is provided. In the example of Figure 4, a message 400
is
again a shipping notification indicating that an order has been shipped.
Message 400 is
from a different vendor and uses a different template than that of Figure 3,
and has
various fields such as an order number 410, a delivery date 412, a block or
button 414
having a unique URL behind such button, a shipping destination 416, an order
price
420, a shipper 422, and a tracking number 424.
[0088] When comparing the embodiments of the templates shown in Figures 3 and
4,
the structure of the templates is completely different. Each email has a
unique layout,
HyperText Markup Language (HTML) and/or eXtensible Markup Language (XML)
structure, where elements can be found using different XML Paths (XPath)
expressions.
In particular, an XPath is a syntax or language for selecting one or more
elements in an
XML document.
[0089] Further, while the embodiments of Figures 3 and 4 show shipping
notifications,
other messages from a vendor may include an order confirmation message, an
order
processed notification, a delivery pending shortly notification, a delivery
notification,
among others. Each may have a different template assigned thereto.
[0090] Further, vendors may use different notification templates depending on
other
factors such as country or region of a customer, a type of product or service
involved
with a particular transaction, based on the recipient of the message, among
other
options. For example, if the product is being shipped to a customer in Canada
the
notification message may be in both English and French, whereas a notification
to a
customer in the United States may be in English only, or in English and
Spanish in
27
Date Regue/Date Received 2022-07-07
some cases. If the customer is a member of a loyalty program the template used
may
include fields and wording around loyalty rewards for the transaction. Other
factors are
possible. Each may therefore use a different template.
[0091] In some cases, the template may look different if a different number of
products
are being reported in the message. For example, a purchase notification from a
vendor
for a single product may look similar to a purchase notification for two or
more products,
but with additional fields for the second and subsequent products. To a
message
extractor, messages having different numbers of products in them may be
considered
different templates.
[0092] In some cases, rather than an ecommerce platform and messages relating
to
vendors, the message processing system may be used for other purposes. For
example, a scheduling manager may receive messages that use various templates
and
the message processing system may group those messages and extract
information.
Other examples are possible.
[0093] The structure of a template may be used for assigning templates into
groups,
called clusters, and assigning one or more values to such cluster based on the
message templates in that cluster.
[0094] Clusters and Cluster Values
[0095] In some cases, the same templates may be used by different vendors. In
other
cases, related companies may use the same notification templates. Other
options for
the reuse of templates are also possible.
[0096] In this regard, the templates may be assigned into a logical group
referred to
herein as a cluster. Each template has a characteristic value, and a cluster
can have
one or more templates. Therefore, values associated with message clusters may
for
example, be characteristic values associated with templates that are
associated with the
message cluster.
28
Date Recue/Date Received 2022-07-07
[0097] A group of emails utilizing the same template may be grouped or
categorized into
a cluster, and one or more email extractors as defined below may be assigned
to such
cluster. In some cases, a further group of emails using a second template may
also be
grouped into this cluster, and a second characteristic value may be associated
with the
cluster based on the second template.
[0098] Thuse, characteristic values are values corresponding to templates.
[0099] Each cluster may have one or more values assigned thereto.
Specifically,
reference is made to Figure 5, which shows a process for assigning a value to
a
cluster. Such value may be, for example, a hex of a minhash for the template
that was
first seen for the cluster.
[0100] The process of Figure 5 starts at block 510 and proceeds to block 520
in which
characteristics are extracted from a message.
[0101] Based on the characteristics extracted at block 520, a check can be
made at
block 522 to determine whether a cluster is known for the message
characteristics. If
yes, the process proceeds to block 530 and ends.
[0102] Conversely, if a cluster is not known then the process proceeds to
block 540 in
which a cluster may be created. The process then proceeds to block 542 in
which a
value is assigned to the cluster. The value may be assigned in various ways.
[0103] In one embodiment, the value may be a hash of the elements in a
template. For
example, utilizing the template for the message of Figure 3, the XPaths of the
template
specified using XPath expressions are:
[
'/html',
29
Date Recue/Date Received 2022-07-07
'/htm I/body',
'/htm I/body/font',
'/html/body/font/br[1]',
'/html/body/font/br[2]',
'/html/body/font/br[3]',
'/html/body/font/br[4]',
'/html/body/font/br[5]',
'/html/body/font/br[6]',
'/html/body/font/b[1]',
'/html/body/font/br[7]',
'/html/body/font/br[8]',
'/html/body/font/br[9]',
'/html/body/font/br[10]',
'/html/body/font/b[2]',
'/htm I/body/font/a',
'/html/body/font/br[11]',
'/html/body/font/br[12]'
l
Table 1: Example XPaths for aTemplate
[0104] In one embodiment, the value for the cluster may therefore be based on
a
minhash of the XPaths for the primary email template used for that cluster. A
minhash
is an algorithm for estimating how similar two sets are and may in some cases
produce
a fixed length array of values for a given input. For example, the XPaths in
Table 1 can
be used in a minhash function where the output is defined to have a fixed
sized array of
values, for example 128 values. This is however not limiting and other lengths
are
possible. The output of such minhash function may be:
[4138275, 58467968, 361694150, 60789464, 245961614, 7841238,
90464114, 57044459, 354535158, 194189851, 140056852, 60798928,
194284999, 45838352, 151698913, 36481736, 27197609, 332341639,
Date Recue/Date Received 2022-07-07
70279226, 349082816, 185879925, 186146414, 89945648, 276059490,
38312470, 133999309, 23856165, 277015002, 572091941, 92895461,
80811224, 214262812, 545873223, 9395008, 10930505, 227986709,
20629749, 31596960,466741011, 51216863, 551949416, 295030646,
677315696, 42131191, 107637808, 63825010, 246814026, 49316811,
325148032, 213424747, 249791222, 29511745, 69035818, 28622995,
512800234, 139457788, 313654355, 36857204, 55603873, 275578986,
363485812, 153524886, 123565663, 61487864, 13420203, 28292728,
14478851, 64900169, 7373373, 425451853, 294656222, 6716086,
320325391, 495924302, 407123249, 363237260, 189620341, 243627538,
133233712, 165993244, 543186247, 189101443, 366586677, 242145588,
53910115, 220089639, 47608692, 279398352, 465508506, 120219978,
606245647, 448302536, 250528084, 920785849, 156799164, 131690695,
381496397, 181417001, 137386063, 223089022, 616125108, 278446605,
797038136,163450663, 72773915, 460478840, 34887879, 15320297,
2666089, 21835911, 9738635, 82448666,421678353, 129315830,
24403591, 900464338, 103312975, 159061420, 198902214, 144899528,
77265193, 221203133, 2817520, 74641430, 144255143, 102180984,
73413794, 137281749]
Table 2: Example minhash of XPaths of Table 1
[0105] The array of Table 2 may therefore be the value assigned at block 542
to the
cluster containing the template for the email message of Figure 3, and be
considered
the characteristic value for the template.
[0106] The use of a minhash to calculate the value at block 542 is however
merely an
example. In other cases, values could be generated using other techniques. For
example, an encoder using a natural language processing machine learning (ML)
model
could be used. Such encoder may be trained on millions of raw emails to gain
its own
understandings of emails and structures. Such encoder could assign a value to
the
31
Date Recue/Date Received 2022-07-07
template, and subsequently a cosine similarity could be used to match a value
for an
incoming email to a centroid.
[0107] In other cases, other value assigning processes could be used.
[0108] Once the value is assigned at block 542 the process proceeds to block
530 and
ends.
[0109] The process of Figure 5 could, for example, be used whenever a new
cluster is
created. If a value needs to be assigned to more than one cluster in a system,
the
process of Figure 5 could be repeated for each cluster.
[0110] Similar Clusters
[0111] Utilizing the process of Figure 5, two email messages with the
different
templates may be used to create two separate clusters. For example, reference
is now
made to Figure 6.
[0112] In the embodiment of Figure 6, a first cluster 610 has a cluster
characteristic
value assigned thereto. Specifically, in some cases, each template may be
identified by
a fixed-length hash (e.g. a minhash), where all emails considered to be in
that cluster
have a fixed-length hash that is within a certain threshold of difference from
the cluster's
identification hash. This may be referred to as a similarity index. Using the
"minhash"
example, the array of hash values found for the email message can be compared
with
an array associated with each template. If an element in the two arrays
matches, this
can be used to increase the similarity index. One or more extractors
associated with
the cluster having the template with the highest similarity index can then be
used to try
to extract information from the email message.
[0113] Messages that are received within the computing system that have a
characteristic value within a similarity threshold 612 of at least one cluster
characteristic
value would be grouped into the cluster 610. In the example below, only a
cluster 610 is
32
Date Regue/Date Received 2022-07-07
assumed to have a single template associated therewith for simplicity. This is
however
not limiting and could be expanded to cases where the cluster is associated
with
multiple templates.
[0114] For example, the similarity threshold may indicate that the Jaccard
similarity is
within 80% of the value. However, such similarity threshold is provided merely
for
illustration purposes and the value of the similarity threshold may be any
threshold set
for the system. Further, the value of the similarity threshold may depend on
the type of
similarity being assessed.
[0115] A second message or group of messages may be received by the system and
the characteristic value found for these messages may create a second cluster
620.
Again, cluster 620 is assumed to have only a single template in this example
for
simplicity. However, cluster 620 could, in other cases, have multiple
templates
associated therewith. Messages that are received within the computing system
that are
within a similarity threshold 622 of a cluster characteristic value for
cluster 620 would be
grouped into cluster 620.
[0116] In the embodiment of Figure 6, the cluster characteristic value of
cluster 610 is
outside of the similarity threshold 622, and the cluster characteristic value
of cluster 620
is outside of similarity threshold 612, and therefore these are two separate
clusters in
the system.
[0117] However, if a third message or group of messages is received that has a
characteristic value with a similarity threshold that captures the values both
cluster 610
and cluster 620 (i.e. a characteristic value for this message is within both
similarity
threshold 612 and similarity threshold 622), this may indicate that there is a
similarity
between the clusters and potentially a single extractor (or a single set of
extractors) may
be used on a combined cluster.
33
Date Regue/Date Received 2022-07-07
[0118] Specifically, reference is now made to Figure 7. In the embodiment of
Figure 7,
a first cluster 710 has a cluster characteristic value assigned thereto.
Messages that
are received within the computing system that are within a similarity
threshold 712 of
this cluster characteristic value would be grouped into the cluster 710. For
example, the
similarity threshold may indicate that the Jaccard similarity is within 85% of
the value.
[0119] A second message or group of messages may be received by the system and
the characteristic value found for these messages may create a second cluster
720.
Messages that are received within the computing system that are within a
similarity
threshold 722 of the cluster characteristic value for cluster 720 would be
grouped into
cluster 720.
[0120] In the embodiment of Figure 7, the cluster characteristic value for
cluster 710 is
outside of the similarity threshold 722, and the cluster characteristic value
of cluster 720
is outside of similarity threshold 712, and therefore these are two separate
clusters in
the system.
[0121] In the example of Figure 7, a third message or group of messages is
received
that would ordinarily cause a cluster 730 with a characteristic value to be
created. If
cluster 720 did not exist in the system, the value for cluster 730 would fall
within the
similarity threshold 712 and therefore be grouped with cluster 710. Similarly,
if cluster
710 did not exist in the system, the characteristic value for cluster 730
would fall within
the similarity threshold 722 and therefore be grouped with cluster 720. Thus
this third
group of messages is based a single template that, once processed by the
mapping
function, results a characteristic value that fall within both threshold 712
and threshold
722.
[0122] Since the characteristic value for the message falls within similarity
threshold 712
and similarity threshold 722, this may indicate that a relationship may exist
between the
messages forming cluster 710, the messages forming cluster 720, and the
messages
forming cluster 730. Put another way, the messages that would normally create
cluster
34
Date Regue/Date Received 2022-07-07
730 would have a characteristic value with a similarity index 732 that would
capture the
cluster characteristic values of both cluster 710 and cluster 720, indicating
a similarity
between the two clusters.
[0123] In this case, a link may be created between cluster 710 and cluster
720, as
shown with line 740 in the embodiment of Figure 7. Based on this link, a
single
message extractor or single set of message extractors may be assigned to the
combined message cluster, as described below. Such single message extractor or
set
of message extractors may then be used to extract information from messages
received
having a characteristic value that is within a similarity threshold of the
combined
message cluster.
[0124] In the embodiment of Figure 7, two clusters, namely cluster 710 and
cluster 720,
may be grouped into a combined cluster based on a message received that
overlaps
both clusters. In some cases, clusters may already be grouped, and a new
message
received may be used to group previously combined clusters with other clusters
or other
groups of clusters. Thus, the embodiments of the present disclosure are not
meant to
be limited to grouping only standalone clusters, but can be used to group
previously
combined clusters with either standalone clusters or other combined clusters.
[0125] For example, reference is now made to Figure 8. In the embodiment of
Figure 8,
a first combined cluster 810 may have been created, for example, as indicated
above
with regard to Figure 7. Similarly, a second combined cluster 820 may have
been
created, for example as indicated above with regard to Figure 7. However,
combined
cluster 810 and combined cluster 820 are initially considered to be separate
combined
clusters since the similarity thresholds for the clusters in each combined
cluster do not
overlap the cluster characteristic value of any clusters within the other of
the combined
clusters.
[0126] In this regard, if a new message is received with a characteristic
values shown
with reference numeral 830 that is within the similarity thresholds of two
combined
Date Regue/Date Received 2022-07-07
clusters, this may indicate that the two combined clusters may also be similar
and thus
may be grouped into a single larger combined cluster.
[0127] In further embodiments, a cluster may be grouped with a previously
combined
cluster. Other options are possible.
[0128] In this case, a link 840 may be created between combined cluster 810
and
combined cluster 820. Based on this link, a single message extractor or a
single set of
message extractors may be assigned to the larger combined message cluster, as
described below. Such single message extractor may then be used to extract
information from messages received having a characteristic value that is
within a
similarity threshold of the larger combined message cluster.
[0129] Further, while the embodiments of Figures 7 and 8 show the combining of
two
clusters or groups of clusters, in some cases more than two clusters may be
combined.
For example, if a message has a characteristic value that would fall within
the similarity
threshold of three or more clusters or groups of clusters, then such three or
more
clusters or groups of clusters may be combined in some embodiments.
[0130] Message Extractor
[0131] A message extractor is an algorithm, code segment or program that is
used to
find information from a message. The message extractor may be customized or
programmed specifically for a template to allow the program to quickly and
accurately
find the information elements desired by a computer system such as an e-
commerce
platform.
[0132] The information elements extracted by a message extractor could be
configured
based on the type of message being received and the type of information within
that
message. Further, certain information may be relevant for the e-commerce
platform or
computer system while other information may be irrelevant, and therefore the
message
extractor may be customized to obtain only the relevant information in some
cases.
36
Date Regue/Date Received 2022-07-07
[0133] Utilizing the example message from Figure 3, one simplified description
of a
message extractor is illustrated with regard to Table 3.
{
"tracking_num be r": "xpath[/html/body/font/a/text()]",
"carrier": null,
"tracking_urI": "xpathVhtml/body/font/a/@hrefr
1
Table 3: Example of a simplified message extractor
[0134] As seen in the example of Table 3, the information sought from the
message of
Figure 3 by a computer system such as an e-commerce platform includes the
tracking
number, and tracking URL. The location of these elements is provided as an
XPath to
one or more elements of the message. However, this is merely an example and
the
identification of the information desired within a message template could be
done in
other ways, such as relative positions, based on tags within the message,
among other
options.
[0135] Further, in the example of Table 3, information about a carrier may
also be
desired by an e-commerce platform. However, in this case the type of message
associated with the message extractor does not include such information and
therefore
the value is assigned as a null value in accordance with the example of Table
3. In other
cases, information that is not available may simply be ignored by the message
extractor. Other options are possible.
[0136] Based on the simplified message extractor of Table 3, the information
extracted
from the message of Figure 3 is provided in Table 4 below.
{
"carrier": null,
37
Date Regue/Date Received 2022-07-07
"tracking_number": "94555555555555555555 ",
"tracking_urI":
"https://tools.usps.com/go/TrackConfirmAction.action?tLabels=945555555555555555
55"
1
Table 4: Information from the message extractor of Table 3
[0137] While the example extractor of Table 3 and results of Table 4 provide
for the
tracking number and tracking URL. In other examples the computer system or e-
commerce platform may desire to check a shipping address against a registered
shipping address for a client and therefore may extract the shipping address
314 from
message 300. In other cases, the date 312 may be extracted. In some cases,
more
sophisticated algorithms may be applied to the data and more or fewer data
fields may
need to be extracted. Therefore, the example of Table 3 is provided merely for
illustration purposes.
[0138] In further embodiments, rather than a single message extractor, a set
of
message extractors may be utilized. Specifically, a first message extractor
may be used
to extract a first piece of information or specific information elements. A
second
message extractor may be used to extract a different piece of information or
set of
message elements. In this way, multiple extractors may be used, and the set of
message extractors may be unique to a cluster.
[0139] As seen from the example of Table 3, the message extractor is a program
that
can be run quickly on messages as they are received at the system and the
message
extractor is tailored to the template by utilizing the positions of the
information within the
message for extraction. This ensures that computing resources are utilized
efficiently
when processing thousands or hundreds of thousands of messages in a short time
period.
38
Date Recue/Date Received 2022-07-07
[0140] For this reason, high accuracy and precision email extractors are
typically only
applicable to a few specific email templates each. Therefore, a sophisticated
email
extracting system, such as one built to interpret e-commerce emails from
buyers'
inboxes, may require thousands or hundreds of thousands of email extractors,
each
trained to identify specific relevant information from a single distinct email
template.
[0141] Creating Combined Clusters
[0142] In accordance with the embodiments of the present disclosure, when a
new
message is received then clusters or combined clusters may be created.
Reference is
now made to Figure 9.
[0143] The process of Figure 9 starts at block 910 and proceeds to block 920
in which a
mapping function may be applied to a received message to create characteristic
values.
For example, the mapping function may be the minhash function applied to a
message's
tree of XML elements described above with regard to Table 2. In other cases,
the
mapping function may be a natural language processing algorithms applied to a
message. In other cases, other types of mapping functions could also be used.
[0144] The mapping function creates a characteristic value as its output which
can then
be used to identify a template and corresponding message extractor or
extractors. In
particular, from block 920 the process proceeds to block 930 to check whether
the
characteristic value matches any extractor values. This may be done, for
example, by
checking the array of values of the minhash for the message with arrays of
values for
the clusters and the extractors associated therewith. The comparison may not
need an
exact match, but in some cases the match may need to be close enough according
to a
specified threshold.
[0145] For example, utilizing the minhash example above, the minhash will
produce 128
values in an array. Therefore, if the characteristic value for the message is
an array of
128 values and the value associated with a cluster is an array of 128 values,
each value
can be compared against the value in the corresponding position in the other
array. If a
39
Date Recue/Date Received 2022-07-07
threshold number of values matches, this may indicate that the characteristic
value
matches the extractor values.
[0146] Similarly, natural language processing may create a value which can
then be
compared on a cosine similarity basis to the value for each of the extractors
to find if a
match exists. The match may exist, in this case, if the characteristic value,
when the
cosine similarity function is applied, is above a threshold.
[0147] Other techniques for determining whether the characteristic value
matches a
value for an extractor at block 930 are also possible.
[0148] If it is determined at block 930 that the characteristic value does not
match any
extractor values, either based on the individual message or the cluster, the
process
proceeds from block 930 to block 932 in which at least one message extractor
may be
found or created. For example, in one case a flag may be provided that an
extractor for
the template needs to be created, and this may be provided to a developer or
group of
developers.
[0149] In other cases, existing extractors within a computing system may be
reviewed to
identify whether such existing extractors could be used with the message
received.
Specifically, as no message extractors have currently been assigned to the
received
message or new cluster, the system needs to either identify an existing
extractor which
will work or to create a new message extractor. However, computationally it
would be a
very long process to run all of the message extractors in a system against the
received
message to determine whether the information needed was successfully
extracted.
Given the volume of messages received at a typical e-commerce platform, such
processing could result in significant delays, dropped messages, or an
expenditure of
significant resources to provide for the processing power needed, among other
difficulties. Rather, a more focused search for message extractors may be
performed.
Date Recue/Date Received 2022-07-07
[0150] Specifically, in some cases, the characteristic value obtained for the
received
message can be compared with the values associated with existing message
extractors
to identify a subset of message extractors that could be attempted to be used.
[0151] In one embodiment, the message extractors could be identified by
finding
message extractors which exceed a similarity index. Using the minhash example
again,
a comparison between the array for the characteristic values and the array for
a plurality
of message extractors could be made. If the number of matches between the two
arrays
exceeds a similarity index, such message extractor could be attempted.
[0152] In other cases, a cosine similarity value could be used.
[0153] In other cases, Jaccard similarity could be used. Other similarity
comparisons
could also be made.
[0154] The identification at block 932 could identify one or more message
extractors.
For example, if the similarity index is matched by a plurality of message
extractors, in
some cases each of the message extractors above the similarity index could be
tried. In
other cases, if the number of message extractors above the similarity index is
too high,
then a subset of the identified message extractors could be attempted.
[0155] Further, secondary factors may also be used to help identify the
message
extractor. For example, if a sudden increase in the volume of one cluster is
noticed
(which may correspond with a decrease in another cluster), this may indicate
that a
template for emails from the decreased cluster may have been changed. In some
cases the old extractor may still be able to parse parts of the messages using
the new
template (for example if the new template builds on the old template), and in
this case
the extractor for the decreased cluster may be added to the one or more
extractors
identified.
41
Date Regue/Date Received 2022-07-07
[0156] In other cases, evidence such as a name of a merchant, subject line,
sender
email address, product names, lengths and numbers of shipping identifiers,
among
others, could be used to add to the one or more extractors identified. In some
cases,
such evidence could be collected from evidence outside of an extractor, such
as
message metadata, among other options.
[0157] In some cases, generic or catch-all extractors, and or automated
extractors,
could be added to the one or more extractors identified as well. For example,
a generic
extractor may involve finding regulator expressions for application to raw
message html
in some cases. Other options are possible.
[0158] Once the one or more extractors has been identified, they can be used
to extract
information from the message as shown at block 936. For example, an extractor
may in
some cases be bound to the received message or cluster for the received
message.
This binding may be temporary in some cases, until a better message extractor
is
found, for example.
[0159] The extracted information may also optionally be given a "quality
score" based on
various factors. For example, if X values are expected to be extracted, but
only X-Y
values are found using the extractor, this can lower the quality index. Each
expected
field may be given a weight in some cases, and the quality score may be
affected by the
weight of the missing fields.
[0160] Extrinsic evidence, such as known formats for data from a particular
merchant,
can also be used in finding the quality score.
[0161] In some cases, a comparison between the values obtained from a
plurality of
extractors can also be used.
[0162] If the quality score from one extractor in some cases, or from values
from a
plurality of extractors in other cases, exceeds a threshold, a new extractor
may be
42
Date Recue/Date Received 2022-07-07
assigned for the message identifier, and the new extractor can immediately
begin
parsing such messages.
[0163] In some cases, the new extractor may be a combination of two or more
previous
extractors, or parts thereof, to find the expected values fields. Thus, a new
message
extractor may be created based on a plurality of previously known message
extractors,
where parts of such previously known message extractors producing desired data
may
be combined.
[0164] In some cases, the new extractor may be created based on a modification
of
existing extractors and further based on information regarding the calculated
difference
between the original extractor template and new template. Specifically,
information
about the differences between the old and new templates may be used to modify
the
extractors. For example, the root of the XPaths can be changed to the updated
structure
and the new extractor can then be tried on the new template. Other examples
are
possible.
[0165] This optional quality check is shown as block 934 in the embodiment of
Figure 9,
where the use of the identified at least one message extractor at block 936 is
only
performed if the quality check exceeds a threshold. If not, more message
extractors
can be identified at block 932.
[0166] Further, in some cases the quality can be increased by using other
sources of
information, such as an operator for the merchant platform identifying
information
elements, or crowdsourcing to verify information elements. For example, when a
new
cluster is identified, a request to an operator at the e-commerce platform may
be made
to verify that the extractor is working correctly. In other cases, the
recipient of the
original message may be queried to determine whether information identified is
correct
within the message. In other cases, crowd sourcing through a blog or quality
control
website may be done requesting verification. Other options are possible. This
could
43
Date Recue/Date Received 2022-07-07
therefore be used to create a new message extractor based on previous message
extractors.
[0167] The urgency of the request to the other sources of information may be
correlated
to the volume of email messages having the same identifier within the computer
system
in some cases.
[0168] From block 936 the process proceeds to block 940 and ends.
[0169] Referring again to block 930, if the characteristic value does match
with that of
one or more templates of at least one cluster, the process proceeds from block
930 to
block 950. At block 950, a check is made to determine whether the
characteristic value
matches with that of one or more templates of two or more clusters.
Specifically, using
the example Figure 7 above, a message creating a new cluster 730 would overlap
with
existing clusters 710 and 720, and therefore, the check at block 950 of Figure
9 would
find that the characteristic value matches two or more clusters.
[0170] From block 950, if only one cluster is matched, the process proceeds to
block
952 in which the matched message extractor or set of message extractors is
used to
extract information from the received message. From block 952 the process
proceeds to
block 940 and ends.
[0171] Conversely, from block 950, if the characteristic value matches two or
more
clusters or combined clusters, the process proceeds to block 960 in which the
two or
more clusters or combined clusters ("parents") are combined into a new
combined
cluster.
[0172] The process then proceeds to block 962 in which a message extractor may
be
assigned to the new combined cluster. Specifically, in some cases the message
extractor from one of the parent clusters or combined clusters may be
attempted to be
used with the new combined cluster.
44
Date Recue/Date Received 2022-07-07
[0173] In some cases, the message extractors from each of the parent clusters
or
combined clusters may be attempted with the new combined cluster.
[0174] In each case, an optional quality check, as shown at block 964, may be
used to
determine whether the quality of the extractor exceeds a threshold. The
quality check
performed at block 964 can be similar to the quality check performed at block
934, as
described above.
[0175] If the quality check at block 964 is not passed, the process may
proceed back to
block 962 in which a new message extractor is assigned to the new combined
cluster.
[0176] Conversely, if the quality check is passed, the process may proceed
from block
964 to block 966 in which the assigned message extractor may be used to
extract
information from messages falling within the new combined cluster.
[0177] From block 966, the process proceeds to block 940 and ends.
[0178] In this way, related clusters can be found to create combined clusters
which
utilize a single message extractor or set of message extractors. The use of a
single
message extractor or set of message extractors for a larger combined cluster
can save
and/or reduce consumption of system resources by not requiring the creation
and
storing of as many extractors within the computing system.
[0179] While the above utilizes a similarity threshold as the sole determining
factor to
combine clusters, in some cases, other factors may also be utilized. For
example, a
complexity score may be needed to create combined clusters. Specifically, in
some
cases, if the HTML elements within a message are too simple, this may cause
the
comparison for the similarity threshold to return a false positive. Therefore,
in some
embodiments, a complexity score may be utilized in addition to the similarity
threshold
to determine whether to create the combined cluster.
Date Regue/Date Received 2022-07-07
[0180] As used herein, a complexity score may indicate whether the elements
within the
message are complex enough to consider grouping or combining the clusters. The
complexity score may relate to a shape of the HTML tree, a number of elements
within
the message, among other factors. Therefore, at block 950, an additional check
may be
made to determine whether the complexity score also matches the threshold in
order to
link two or more message clusters or combined clusters together.
[0181] Retiring Extractors
[0182] In the case where a message template changes and a new message
extractor is
created or assigned, or in the case where clusters or combined clusters are
grouped,
old message extractors may still exist that are no longer being used. For
example, this
may occur if a merchant swaps data paths within a template, changes email
templates,
among other options, as well as with the combining of the clusters.
[0183] In some cases, such unused message extractors may be kept for potential
future
use if a new template is introduced.
[0184] However, in other cases such unused extractors may be retired from the
system.
[0185] In other cases, the quality of the information produced by an extractor
may not
meet or may no longer meet a threshold quality score. In this case, it may be
cheaper to
retire such extractor and create a new extractor to then deal with tickets
regarding the
problems with the quality of the information extracted by such extractor.
[0186] Reference is now made to Figure 10. In the embodiment of Figure 10, the
process starts at block 1010 and proceeds to block 1020 in which a check is
made to
see whether the extractor is still being used. For example, if the extractor
has been
replaced by a new extractor, if the extractor is no longer being used because
a different
extractor is used for a combined cluster, among other options, then the check
at block
1020 will find that the extractor is no longer being used.
46
Date Recue/Date Received 2022-07-07
[0187] The process then proceeds to block 1030 in which the unused extractor
may be
retired.
[0188] From block 1030, the process proceeds to block 1040 and ends.
[0189] However, in other cases, the extractor may still be used, but may be
producing
poor quality results. Specifically, if a vendor has changed the position of
data within a
template, the value for the corresponding template may still be the same (e.g.
because
the same tree of XML elements is used), but the extracted information may not
be
providing the correct results. Therefore, in the embodiment of Figure 10, if
an extractor
is still being used, the process proceeds from block 1020 to block 1050 in
which a check
is made to determine whether the quality of the results meet a threshold.
[0190] Various thresholds may exist for the check at block 1050. For example,
a check
may be made to determine whether the use rate of the extractor exceeds a
threshold.
For example, equation 1 below may be used to determine a use value that can be
compared with a threshold value:
times used (1)
use rate = . __________________________________
times picked
[0191] In equation 1, the times used value may indicate the times that the
extractor has
been used to extract one or more pieces of information from a message. The
times
picked value may indicate the times that the extractor was picked to test
whether it
could extract information from a message. Therefore, equation one provides a
ratio of
whether the information was used when the extractor was picked to obtain
information
and therefore provides an indication of whether junk data or true data was
returned.
[0192] In addition, or instead, the threshold may utilize equation 2 below.
47
Date Recue/Date Received 2022-07-07
live trackers yielded (2)
active rate =
total trackers yielded
[0193] Equation 2 may be applicable when the data being extracted is the
shipping
tracker number. The tracking number can be compared with the shipping
company's
website to determine whether the tracker is live or not. Therefore, equation 2
may yield
whether the tracking number that is being extracted from the messages is a
live tracking
number or not. In some cases, equation 2 may need to be used several days
after the
package has been shipped and the message has been received, in order to allow
for
the shipping company to update the relevant database record made available to
the
public or to third party partners.
[0194] While equations 1 and 2 provide examples of thresholds, they are meant
for
illustration and other types of thresholds or signals could be used in the
determination of
block 1050. For example, other signals such as a tracking URL instead of a
tracking
number, feedback from users, tickets opened for incorrect data, machine
learning
validation models, among other signals that the information is being extracted
incorrectly, could be used in the determination at block 1050.
[0195] In some cases, the values for the information being extracted could be
compared
with historical data to make a determination of whether the quality of the
information
being extracted meets the threshold.
[0196] In some cases, the quality threshold may be determined based on
crowdsourcing
(e.g. of the actual results of the extractors) or certain reviewers.
[0197] Other options for finding the quality are possible.
[0198] If the quality meets a threshold, as determined at block 1050, the
process
proceeds to block 1040 and ends.
48
Date Recue/Date Received 2022-07-07
[0199] Conversely, if the quality does not meet the threshold, the process
proceeds from
block 1050 to block 1030 in which the extractor may be retired or depreciated.
[0200] Specifically, in some cases, multiple extractors may be used for a
single cluster.
This set of extractors may be used in conjunction with each other. In some
cases, one
out of the set of multiple extractors may be producing erroneous results, in
this case,
other extractors may be given a priority over the extractor providing poor
quality results,
thereby depreciating the poor quality extractor. In other cases, the poor
quality extractor
may be blocked. In other cases, the poor quality extractor may be retired
meaning that
the property extractor may be deleted or archived in the system. Other options
are
possible.
[0201] In other cases, if multiple extractors are being used, then each field
being
extracted may be separately compared in block 1050 to ensure the quality meets
a
threshold. In this case, the extractors providing better quality results may
be given a
higher quality score than those providing less accurate results, and the
depreciation of
block 1030 may lower quality scores as feedback is received.
[0202] Therefore, a weight may be assigned for each extractor per field.
[0203] In some cases, certain fields may be considered to be more important
than other
fields. For example, a tracking number may be considered a more important
piece of
information then a "shipped from" address. In this case, an extractor that
provides high
quality tracking number extraction but poor quality "shipped from" information
may be
prioritized over an extractor that provides high quality "shipped from"
information but low
quality tracking number extraction. Again, such depreciation may be
implemented at
block 1030.
[0204] From block 1030, the process proceeds to block 1040 and ends.
49
Date Recue/Date Received 2022-07-07
[0205] The above-discussed methods are computer-implemented methods and
require
a computer for their implementation/use. Such computer system could be
implemented
on any type of, or combination of, network elements or computing devices. For
example, one simplified computing device that may perform all or parts the
embodiments described herein is provided with regard to Figure 11.
[0206] In Figure 11, computing device 1011 includes a processor 1120 and a
communications subsystem 1130, where the processor 1120 and communications
subsystem 1130 cooperate to perform the methods of the embodiments described
herein.
[0207] The processor 1120 is configured to execute programmable logic, which
may be
stored, along with data, on the computing device 1110, and is shown in the
example of
Figure 11 as memory 1140. The memory 1140 can be any tangible, non-transitory
computer readable storage medium, such as DRAM, Flash, optical (e.g., CD, DVD,
etc.), magnetic (e.g., tape), flash drive, hard drive, or other memory known
in the art. In
one embodiment, processor 1120 may also be implemented entirely in hardware
and
not require any stored program to execute logic functions. Memory 1140 can
store
instruction code, which, when executed by processor 1120 cause the computing
device
1010 to perform the embodiments of the present disclosure.
[0208] Alternatively, or in addition to the memory 1140, the computing device
1110 may
access data or programmable logic from an external storage medium, for example
through the communications subsystem 1130.
[0209] The communications subsystem 1130 allows the computing device 1110 to
communicate with other devices or network elements. In some embodiments,
communications subsystem 1130 includes receivers or transceivers, including,
but not
limited to, ethernet, fiber, Universal Serial Bus (USB), cellular radio
transceiver, a VVi-Fi
transceiver, a Bluetooth transceiver, a Bluetooth low energy transceiver, a
GPS
receiver, a satellite transceiver, an IrDA transceiver, among others. As will
be
Date Regue/Date Received 2022-07-07
appreciated by those in the art, the design of the communications subsystem
1130 will
depend on the type of communications that the transaction device is expected
to
participate in.
[0210] Communications between the various elements of the computing device
1110
may be through an internal bus 1160 in one embodiment. However, other forms of
communication are possible.
[0211] The elements described and depicted herein, including in flow charts
and block
diagrams throughout the figures, imply logical boundaries between the
elements.
However, according to software or hardware engineering practices, the depicted
elements and the functions thereof may be implemented on machines through
computer
executable media having a processor capable of executing program instructions
stored
thereon as a monolithic software structure, as standalone software modules, or
as
modules that employ external routines, code, services, and so forth, or any
combination
of these, and all such implementations may be within the scope of the present
disclosure. Examples of such machines may include, but may not be limited to,
personal
digital assistants, laptops, personal computers, mobile phones, other handheld
computing devices, medical equipment, wired or wireless communication devices,
transducers, chips, calculators, satellites, tablet PCs, electronic books,
gadgets,
electronic devices, devices having artificial intelligence, computing devices,
networking
equipment, servers, routers and the like. Furthermore, the elements depicted
in the flow
chart and block diagrams or any other logical component may be implemented on
a
machine capable of executing program instructions. Thus, while the foregoing
drawings
and descriptions set forth functional aspects of the disclosed systems, no
particular
arrangement of software for implementing these functional aspects should be
inferred
from these descriptions unless explicitly stated or otherwise clear from the
context.
Similarly, it will be appreciated that the various steps identified and
described above
may be varied, and that the order of steps may be adapted to particular
applications of
the techniques disclosed herein. All such variations and modifications are
intended to
fall within the scope of this disclosure. As such, the depiction and/or
description of an
51
Date Regue/Date Received 2022-07-07
order for various steps should not be understood to require a particular order
of
execution for those steps, unless required by a particular application, or
explicitly stated
or otherwise clear from the context.
[0212] The methods and/or processes described above, and steps thereof, may be
realized in hardware, software or any combination of hardware and software
suitable for
a particular application. The hardware may include a general-purpose computer
and/or
dedicated computing device or specific computing device or particular aspect
or
component of a specific computing device. The processes may be realized in one
or
more microprocessors, microcontrollers, embedded microcontrollers,
programmable
digital signal processors or other programmable device, along with internal
and/or
external memory. The processes may also, or instead, be embodied in an
application
specific integrated circuit, a programmable gate array, programmable array
logic, or any
other device or combination of devices that may be configured to process
electronic
signals. It will further be appreciated that one or more of the processes may
be realized
as a computer executable code capable of being executed on a machine readable
medium.
[0213] The computer executable code may be created using a structured
programming
language such as C, an object oriented programming language such as C++, or
any
other high-level or low-level programming language (including assembly
languages,
hardware description languages, and database programming languages and
technologies) that may be stored, compiled or interpreted to run on one of the
above
devices, as well as heterogeneous combinations of processors, processor
architectures,
or combinations of different hardware and software, or any other machine
capable of
executing program instructions.
[0214] Thus, in one aspect, each method described above, and combinations
thereof
may be embodied in computer executable code that, when executing on one or
more
computing devices, performs the steps thereof. In another aspect, the methods
may be
embodied in systems that perform the steps thereof and may be distributed
across
52
Date Recue/Date Received 2022-07-07
devices in a number of ways, or all of the functionality may be integrated
into a
dedicated, standalone device or other hardware. In another aspect, the means
for
performing the steps associated with the processes described above may include
any of
the hardware and/or software described above. All such permutations and
combinations
are intended to fall within the scope of the present disclosure.
53
Date Recue/Date Received 2022-07-07