Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
g~
20365-2694
BACKGRO~ND OF THE INVENTION
The invention is Airected to a method and apparatus
for modifying configurations of a data processing system,
particularly a system comprising a control mechanism in a
modular system architecture, whereby function modules are
combined into individual configurations, each of which is used
for processing a procedure.
In a data processing system, individual operational
sequences are executed with the assistance of a respectively
defined configuration of system parts. These system parts can
lnclude periphery apparatus, speclflc memory elements and the
like, but can also include program archives, sub-programs and
common data regions with information stored therein such as,
for example, access authorizations. In the following, such
parts are referred to as function modules. When a modification
is undertaken at one of these function modules, the
modification can be signiflcant for the other function modules
of the configurations to which the modified function module
belong~. This modiflcatlon must, therefore, not be executed
arbitrarily and in an uncoordinated fashion. In general, a re-
start of the data processing system is required for that
pUrpose, with the modified function module being accepted
together with all other function modules of the configuration.
SUHHARY OF THE INVENTION
The object underlying the present invention is to
enable the modification of a configuration, without
interrupting the operation of the data processing system.
According to a broad aspect of the invention there is
provided a method for modifying configurations of a data
processing system comprising a control means which is composed
of at least one sub-controller and modular system architecture,
B 2
~274917
20365-2694
whereby function modules are combined to form individual
configurations which are each utilized for specific operational
sequences of the data processing system, configuration-specific
parameters entered in a configuration memory being assigned to
these function modules and modified accordingly with a
configuration modification in the configuration memory, the
control means identifying the function modules which are
affected by the configuration modification by interrogation of
the configuration memory and supplying modification information
to these function modules, characterized in that a
conf~guration data number is allocated as a logical address to
every configuration, that before every access of the
configuration memory the configuratlon data number is converted
by means of an address converting memory into a configuration
data address as a physical address of the corresponding
configuration in the configuration memory, that every sub-
control~er is assigned its own configuration memory for the
function modules with which it can combine and the request of
modification information in the respective configuration
memories of the other sub-controllers is recorded by every sub-
controller for required configurations from other configuration
memories.
In accord with this method, not only every
modification at a function module itself can be accommodated,
but also an expansion of the data processing system, by
technical improvements or adaptation of the performance
capability, can be implemented at any time. ~ach function
module has its relevant configuration data stored, and each is
informed of the modification. The reliability and availability
of the data processing system are increased in that the outage
of a function module is also entered in the configuration
~Z'749J~
20365-2694
memory, and so no access to the malfunctioning or non-extant
function module is initiated, which could otherwise result in a
blocking of the overall data processing system. The message
traffic of ~he control means is relieved in this method, in
that only the necessary modification messages are carried out
and differing from the previous method, all function modules
are not continuously supplied ~ith configuration data. The
modification of configurations is possible with relatively
little cost, and constant monitoring of the composition of the
lndividual configurations, and the informing of all function
modules of a given modificatlon, can be eliminated.
A configuration modiflcation is achieved by the
emission of the modification information, initiated by the
write-ln of the new confiyuration data lnto the configuration
memory by the control means. When a function module makes only
rare use of specific configurations, then it is advantageous
that the relevant configuration data are interrogated from the
configuration memory, as needed, to simpllfy case of a function
module that does not contaln any modification information from
a conflguration. The unnecessary entry of modification
information is thereby avolded and the data processing system
is further
3a
" ~ L~ U ;~ L ~ . . t . y .
i2749~
~elleved of super~luou~ ~es3age t~fflc, In or~er to quarantee a
reliable handllng of later con~lguration modiflcationg,
particularly in s~rvlce ins~ncs~ ~nd for new connectlons, a
request of the modification lniormation by the funotlon module is
ente~ed ln the ~onf~gurstion me~ory by emltting a modlflc~tion
parameter.
A conflguratlon data number 19 allocat~d as a loglcal
address to every conflguration entered in the conflguratlon
memory. ~his ig lndependent of, and dlfferent fro~ the actual
me~ory addreRs. This lncrea~e6 the rellablllty o~ acce~s to the
configuration ~e~ory ~nce, dlfferlnq rom th~ prevlous practice,
the accesg addreq~ need not be calculated. There is, therefore,
no occa~lon for any malfunctio~-caused mlscalculation of the
acces~ addre~s. An addltional protectlon of the data of the
configuration memory agalnst unauthorlzed access and destructlon
Is achleved, ln that the conflguratlon memory ls acce~sed with
the configuration data number ~la an addre~ convertlng msmory,
whereby the conflguratlon data number 1~ converted lnto a
conf iguratlon data addresR a~ a new add~es~ of the corre~pondlng
con~iguratlon ln the conflguratlon memory.
In order to formally,aheck the storod parameter~ of
every conflguratlon, and ln order to be able to mAp the
conflg~ratlon memory, the numb~r of parameters ~tored ln the
con~lguratlon data ~emory for a config~ratlon i-Q recorded by a
confl~uratlon data formst.
In order to lmpr~ve the performance oapablllty of the
da~a proce~sing gystem, a plurality of sub-controlle~s
correspon~lng to a control devlce end t.o esch sub~cont~oller is
assigned it~ own con~lgur~tion memory fo~ the ~unctlon modules
with whieh lt comblnes, and the reque~t o~ the modlflcation ln
the re~pectlve conflguratlon ~emorles o~ the othe~r sub-
controllers ls recorded by every sub-oontroller for re~uired
configuratlons rom other eonfl~uratlon memor~e~. Wlth tha
~2~4~
arrangement of the dlvlded controllers, each sub-controllor is
asslgned specific ~oba. To t~l~ end, 1~ autonomously admini~ters
the conflguratlon9 of the ~unctlon module~ a~signea to it, and
surveyable unlts are thereby created. Thio method nables syst~m
e~panslons, by attachlng urther da~a proce~Ylng block~
comprising sub-oontroller~ and conflguratlon memories, to be
carried out r~latlvely easlly. Since, however, the sub-
controllers also handle shared procedures, the communicatiOn of
the modlficatlon of a confl~uratlon thereby requlr~d 18 protect~d
ln that the paramcters of th~ affeeted ~ub-controller~ in the
respective conflguratlon are ente~ed ln the conflguratton
me~ory. With ~ub-controlle~ havihg ldentical ~obs, the
configuratlon memories are held to ldentlcal contents and the
modlicatlon of a conflguratlon 1~ entered ln every one of the~e
conflgura~lon memorle~.
I~ ls advantageous for the implementat~on of the method
of the invention that oach o~ the functlon module~ contaln~ a
communicatlon memory whlch 18 o~nnected to the contral means or
the receptlon o~ modlflcatlon ln~ormatlon. Th~ ~unotlon module
is connected to the conflgurat~on memory and the confl~uratlon
memory 1~ connected to the control means. ~he control mean~ and
the functlon module~ are connected to the conflgurstion memory
via the address oonvertlng ~emory. A~ a result, the
conflguratlon m-mory can be arbitrarlly arranged and modified in
other msmory area~ without having to modlfy the acca~OE ~n tho
control moans and the f~nctlon modules. ~he protectlon cf the
stored data ls lncroase~ ln th~t the conflguratlon memory 1~ no
longer dlrectly accessed.
In order to incre~4e tho porformanc- cap4blllty of the
everall systom, ~ho control means ls composed o~ a plurallty of
sub-controllerY and every sub-~ontroller ls conneoted to lts own
configuration memo~y. Partlculsrly wlth ldentical s~b-
controllers, it ls advantageou~ that a supervl30ry controll~r ls
i2749~7
present for at least one conflguratian memory in order to
interrogate and/or modlfy the ~onf~gurat~on data, and ln erder to
output the modlflcatlon lnformation. It i~ the~eby guaranteed
that the content of the configuratlon memories remaln~ ldentical,
since the modlflcation of a conflgur~tlon ls entered lnto every
one of the~e conf iguratlon memorles .
The conflgurat~on memory 18 dlvlded i~to a plurallty of
configuration memory srea~ ln order to achleve deslgn
~lexlbillty, and in order to b~ able to modify the memory ln a
sim~le way. A free de~ign of ~he memory arrangement 1Y thereby
also enabled.
B~IEF DEsCRIpTIoN 0~ THE DRAWINGS
The inventlon shall be set forth ln greater detail with
reference to exemplary embodiments ln drawlngs. Shown are:
Flg. 1 ~hows a first exemplary embodlment ln a schematlc
lllustratlon:
Flg. 2 .~how~ a second exemplary embodiment ln a
schematic lllu~tratlon,
Fig. 3 shows a first example of the organiza~lon of a
conflguratlon m~mory; and
Flg, 4 ~howg a second example oi the organlzatlon of a
conf lguratlon memory.
DESCRIPTION OF THE PREFERRED EME~ODIMENTS
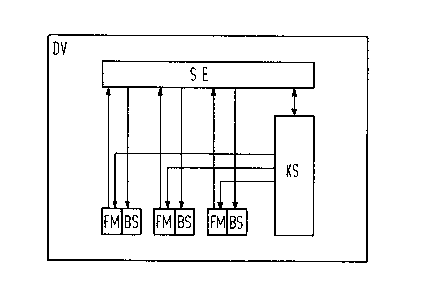
A data processlng sys~em DV shown ln Flg. 1, cantalns a
control mean~ SE and a plurality of funetlon modules FM. The
control means SE 18, for example, a central pro~essor unlt and
the functlon modules FM are memory area~, programs, or the
like. The ad~inlstratlon of the conilguratlonY required for
individual operation~ proceduras 1~ c~rrled out by a
configuratlon memory ~S. ~he parameters of the functlon modules
F~ belonging to every configuratlon are stored in thc
--6--
~L2~4917
conflguratlon memory KS; it is fashloned a~ a random-access
memory ( RAM) . When a conflg~ration is then modlfled from the
outslde by an operator, for exa~ple by attachin~ or disconnecting
a functlon module FM, then the correspondi~g parameter in the
memory KS ie modifie~ with the ~ssistance of the control means
SE. ~his wrlte lnstructlon initlateR the emlssion of a
modlflcation lnformation, whlch the ContrOl means S~ writes into
the communicatlon memory BS of the affected function mod~les
FM. A~ a result, the relevant conflgur~tion data can be directly
~tored by the function module FM, which i~ belng particul~rly
~dvantageoug when the con~l~uratlon data are frequently requir~d
but ~re rarely modified. The communlcatlon memories ~S are
random-acee~ memorle~ (RAMs). A protection mesns ( not shown )
can reglster the outage of a function mod~le FM ln the
conflguratlon memory, and may al80 store the re~son for the
o~ta~e.
I~ iB thereb~ ~ssured thst a configu~ation mod1flcation
~s not un~ertaken in an uncoordinated fa~hlon. With the
a~sLstance of the modl~lcation lnformation ln the communio~tion
memory ~S of tho funetlon module FM, the control of the acccs~ to
the modifië~ function module FM 19 corrected and adapted to the
sctual condltion~. In lnstances ln whlch conflguration d~ta ar~
frequently modlfled but are only r~rely used, thls unnecessary
message trafflo ls svoided when ~he function module~ FM ~an also
read the parameterg of a configuration dlrectlY o~t of the
oonflguratlon memory KS. Thl~ read instruction makes it possible
or the func~lon module FM to dlrectly enter a reque~t for
modlficatlon information in the configuration memory ~S by
speciying A modlfic~tion p~rametez.
~ erminals such as video terminals or personal computers
msy repre~ent functlon mod~les FM o~ the dats proces~ln~ ~y~tem
DV. For example, the employment o~ "intelligent" terminals
ensble~ the d~rect dsta exchange between ~wo ~uch termlnal~, vla
--7--
. . ..
~!749~7
the data proce~qlng system D~. For thls appllcatlon, the
relevant co~fi~uratlon is form~d by the existing data
transmlssion equlpment, and the communication-caPablo terminal~,
whlCh ~erve afi functlon modulea FM. These ter~inals have access
to an informing m~mory BS in whlch the current ~oster of
avallable communlcations partners i~ llated under an iden~ifler
of the fun~tlon ~da~a transml~sion to t~rminals". In case of an
alternatlon in thls roater, for example due to ~he Qddition of a
new termlnal or a chan~e ln the communleatlon capabillty of the
function module FM, ~uch as an added printer, telecopler,
tel~printer or the llke, the new function module FM communicates
a corre~pondlng me~a~e to the control mean~ SE. ~h~ l~tter
modlfle~ or augment6 the ldentlfler~ ln the communlcatlon memory
KS for the a~ected configuratlon~. It ~unctlons as a common or
shared data ~a~e of tho function module6 ~M. The in f orming
memories BS of th~ termlnals are sub~equontly corrected or
u~dated, A6 a re~ult thereof, tha ~tate of po~6ible
communication~ partners ls updated wlthout havln~ to undertake
modif$catlons ln the operatlng pro~ramy of the functlon ùnlts.
It ls also unneceggary to check for the presence of the
communlcatlons partner before evory data transmlY~lon, and thus
loading the bus ~ystems of the data transmlsslon equipment
betw0en the ~ontroller~. ~he increase ln the c~paclty of the
data procesalng 4y4tem FM ls therefore not at~onded by an out-of-
proportlon rlsQ in the messaqe traffic.
Flg. 2 ~hows the second exemplary embodiment, a
¢o~puter-controll-d telephone ywltehing 6y~tem. In p~lnclplo, it
corre~pondQ to the data proceaslng ~y6tem DV of tho flrst
exomplary embodlment; howover, the control m~an~ SE 1Y
composed o~ a plurality of sub-oontrollers TS, ~n order to
lnorea~e call-handllng C4p~city and in order to prod~ce a ~ob
dlvl~ion. Glven a re-~tart followlng modifiCation of a functlon
module FM, 8 purt~cularly great guantity of conflguration dat~
_~_
~274917
would h~ve to b~ 3tored, and the handling of conflguration
modificat~ons in ~ccord with the lnventlon i~ there~ore lent
~peclal slgn~ficance slnce onl~ the modiflcatiOn information
actually r~qulred are then to b~ forwarded. The nece~qary
message traffic ls urther reduCed ~ince every sub-controller TS
admlnlsters the configurations of the function modules FM
a~lgned to lt and predomln~ntly u~ed by lt.
The handlln~ of the conflguration modifications ~or
every ~ub-controller TS is assumed by a separate supervl~ory
control VS. For protection of the con~lguratlon data, every
conflguratlon memory KS is accessed vla an addre3s converting
memory AUS. Every conflgurstion corresponds to a confi~uration
d~ta num~er ~DN ( Flg. 3 ) . It 19 deflned a~ a loglcal addresy.
When the hou~ekeeptng supervl~ory control VS acce~ses the
conflguration memory KS, then the conflguration data nu~ber KDN
1Y converted lnto the corresponding memory loca~lon addre~s of
the conflguratlon memory KS, by means of the addre~s convertin~
memory AUS. When the p~rameter~ o~ a conflguration are ~tored at
8 d~fferent sub-controller TS, then the number thereof 18 entered
ln the addres~ convertlng memory A~S, under tho conflguration
dat~ number KDN, and the acce~s i~ forwarded to the control VS of
the co~reQpondlng 8ub-oontroller TS. In c~se a functlon mod~le
FM of a different sub-controller TS is a component pa~t of a
conflguratlon, the eorresponding supervlsory control VS ls
entered in the conflg~ratlon memory KS a~ 8 parameter, znd
modlflcatlon information i~ then ~ent via it to the communicatlon
memory BS.
A plurality of sub-controllers TS ~or handllng ldentlcal
Jobs can bo util~zod in the telephone swltchlng system o~ Fig.
2. In this case, the re8pectlve configur~tlon memorles KS mu8t
have the same oontent~. A oonflguratlon modlflcatlon i9
therefore un~ertaken in all of the~e configuration memorie~ ~S.
To this end, a fiepara~e controller for conflguratlon data
_g_
~2749~
admln~ stra~lon ce~n alE~ be utll lzed . This es~abllsheS re~le~ts
of modlficatlon mes~a~es in the lndividual conflguratlon memories
KS ~o that, given configuratic~n modiflcatlons in the domain o~
one of the sub-cont~oller~ TS, the rema~nlng, identical sub-
controller~ TS are lnformed via the conflguratlon data
admini~tratlon. Such a mDdiflcat.ion information ls handled with
prlorlty,
Fig. 3 ghows an exemplary structure of the addr~ess
conv~rtlng memory AUS and of the a~sociated configuratlon memory
KS . The conf lç~uration data number KDN is converted into the
conflguratlon da~a address KDA, to whlch a con~lguratlon data
format KDF is also a~signed. ~h~ configuratlon data format KDF
~pecifleY the type ~nd number of parameter~ belonglng to the
configurfltlon data number KDN. On the basls of the format check,
lt is also possible for the funetion module~ FM to check the
formal correctnes~ of ~ stored configuratlon, and tc dlscover
lncorrectly handled modlfications. Glven conflguratlon data
numbers KDN, who~e data are ~tored ln the domaln o~ dlfferent
~ub-controllers 5~S, the number ther~of is l~keWlSe ~tored ln the
address converting memory AUS. The configur~tlon memory KS 18
constr~cte~ matrlx-llke in whlch every row corresponds to one
confl~urutlon. The parameters of the lndlvldual functlon modules
FM are entered ~ucc0s~ively.
Flg. 4 show~ a further embodiment of ~he fitructure of
the ~onfiguratlon me~ory KS. ~he parameters of every
config~ratlon are entered colum~-by-column ln ~helr own
conflguratlon memory area~ KSl through KS4. ~hls ~nable~ a more
flexlble deslgn of the configuration memory KS and particul~rly
facllitates a pos~lble later expan~lon by slmple attech~nt of
new conflguratlon memory areas, and an optimlza~lon of the access
speed to the ln~ivldual p~rameters.
~ he functlon "c~ll setup" of the telephone swltchlng
~ystem FVA requireQ, for exa~ple, the followlng functlon module6
--10-
1~49~7
: a dial tone yenera~or, a pushbutton re~eiver, an
authorization check and a ~witchlng matrlx network COntroller,
all of whlch are listed under th~ correspondlng confi~uration
dat~ number. Whon a ~ubscrlber then plcks up hi~ telephone
receiver, then th~ ~sociated ~ub-controller Ts no longer ha6 to
lndividually ~he~k for the presence of the ~unctlon ~oduleY FM
whlch are requlred for call setup. With reference to the
oorrespondlng conflg~ration data number KDN, the managemont
control VS dlrectly supplles the current ~ta~us of these functlon
modules FM, from the configuration memory KS vla the address
convertlng memory. ~he ldentifier of each of the ~our functlon
modules FM 1~ entered by a blt or a byte under the corresponding
~onfi~uratlon data addres~ KDA. If, for example, the d~al tone
generato~ were to be m~lfunctionlng, thQn elther the ldentlfier
of another dlal tone generato~ or the non-availabillty of the
dlal tone ~enerator ls reliably entered. In the former ca~e, the
~ub-controller TS can lmmediately connect the functional dial
tone generator to the subscrlber statlon, ln the ~econd ca~e, no
oall BetUp ~ Y ~tarted. The need for dialo~ue between the
functlon modules FM and the sub-controller ~S i8 ellmlnated.
A f~rther example ls the functlon of "mailbox call-
ln". The con1guratlon for the executlon o thlo function
employ~ the followlng function module~ FM: an ~ccess
authorlzatlon snd a storagQ dl~k unit. If a ~tor~go disk unlt
wero to fall, then, for example, an em~rgency program can c3ncel
the avall~billty o~ the functlon module FM stora~e dlsk unit in
all configurat~ons or, in the case of redundant avallablllty of
the ~torage diQk unlt, can enter the new ldent1fle~. The new
connection of the ~torage aisk unit c~n tak~ plaoe durlng the
operatlon of the telephone swltohin~ ~ystem FVA. A restart i8
not necessary slnce only the identlfler of the new Ytor~ge dl~k
unlt ha~ to be entorod ln the conflguratlon memory KS. Th~ 8
4~17
oc~urs by trangmittlng a modlfy para~eter frem the ~torage dl~k
unlt to the management controller Vs. The up~tlng of the
informlng memory 3S of the affecte~ function module ~M is
l~kewl~e und-rtaken by the msnagement controller vS. When a
~torage dlsk unit is temporarily dlsconn~cted for ~alntenance
purpo~es, then lts ldenti~ler merely haQ to be deleted ~ro~ the
configuratlon me~ory KS. The modiflcatlon of an acces~
authorizatlon take~ place in the ~ame way. The reduction in
outlay 1~ particularly slgnficant in prl~ate branch exchanges
~nce ~uch modiflcatlon~ ~re frequently und~rtaken thereln.
Without informfng memory BS and conflguration memory KS, the
lnterrogation of the wcess authorization in every mailbox C~
ln, via a different ~ub-controller T~, would re~ult in a
unreasonable load on the data transmisslon lines of the telephon~
~wltahlng 8yBtem FVA.
In addltion to the h~rd~are-orlentQd ~nd ~oftwsre-
orlented structure of the system, on the basls of the
identlficatlon of the function modules FM, the opsratlng statu~
1~ al~o sntered ln the confi~atlon memory KS. ~he ln~entlon
al~o facllltate~ equipment re-lnltlallzation a~ter an ou~age,
~lnco modly parameters are transm~ted from the functlon modules
FM to the management controller VS. The distrtbutlOn of the
conflguration dAta 1Y accompllshed automstlc~
A~ the exemplary embodlment~ show, the method of the
lnv~ntlon for moalfylng con$1gur~tions, with the a~sistance of
configuratlon d~ta number~ KDN, allows ~n especially efflcient
exploltatlon of data pro~esRlng ~ystems DV having modulflr sygtem
archltecture. Modifications of ind~vldual conflguratlong are
also pos~lble during o~erations; emlsslon of damage reports by
the unctlon modules FM enables thc dat~ proCoSBing sys~em DV to
react to unfore~een occurenceR. AC a result thereof, the
operatlonal reliabil~ty 1~ further enhanced. The employment of
the conflguratlon ~ata number~ KDN enables the free ds~lgn of the
i274917
strUcture of the memory sreas of the data proce~slng system DV.
Since the control device SE and the ~unctlon modulefi FM access
the confl~uratlon memory KS only w1th a con~iguratlon da~a number
KDN, lt la of no ~lgnlf~cance for them where th$s conflguration
memory KS is ac~ual~y sltuated, and how the data proce~sing
~ystem DF i~ actually cnnstruct~d. Vnits whlch are surveyable
for ~ystem malntenance and modlflcation are thus created, whereby
operating cost~ are reduced and a ~e~hnological impro~emen~ of
already existin~ data processing sy~tem~ DV i6 realized.
It will be apparont that varlous modlflcation~ and
addltlonB may be made ln the apparatus and method of the present
lnvantion w$thout de~artlng from the essentla1 ~eatures of
novelty th~roof, Which are lntended ~o be deflnod ~nd secured by
the appended claim~.
-13-