Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
25-1t-99; 9:47 ;Patents & FETHERSTONHAUGH ;+4t 32 724 96 62 # 2/ 21
Method and system to provide objects to users of a telecommunications
network
The present invention concerns a method and a system to
provide objects, especially documents, multimedia objects, software
applications andlor processes, to users of a telecommunications network.
The present invention specifically concerns a method to provide objects to
nomad users of a network in which the users identify themselves with an
identification module, for example with a personal chip card. especially a
SIM card.
Telecommunications systems to provide data and objects to other
users are already known. in these systems, also known as pull systems,
various providers can file various objects and data at various nodes of a
telecommunications system where they can be sought at the users'
initiative. The Internet is a well-known example of such a system.
t5 Users are usually connected to an ISP (Internet Service Provider)
via the public telephone network. Generally, the users are not identified
personally by the provider of the telephone network; merely the used
terminals are identified, regardless of the user, for billing of the
telecommunication charges. The ISP generally request a password for
identification purposes but a large number of ISP do not require an
absolutely reliable identification. The Internet can therefore also be used
by anonymous and unreliably identified users. Furthermore, the
identification of users is, as a rule, not passed on by the ISP to further
information providers.
As the identification of the Internet users is not reliable, it cannot
be used to check the authorization of said users to access objecrts of a
confidential nature such as private or corporate documents. Providers vn
the Internet of confidential objects and documents, or of objects and
documents that are not free of charge, as a rule require the users to
identify themselves with a password before being able to access protected
storage areas. In this case the users are directly identified by the provider
CA 02292530 1999-11-30
25-11-99; 9:47 ;Patents & FETHERSTONHAUGH ;+41 32 724 96 62 # 3/ 21
2
and receive a first bill from the telephone network provider for the
connection to the 15P, a second bill from the ISP for access to the intemet
and a third bill from the provider of objects or documents for access to the
sought objects. This billing arrangement is rather inconvenient for the user.
Also known are mobile radio networks and other networks in
which the users, often called subscribers, identify themselves with an
identification module, often called SIM (Subscriber Identification Module)
card in the form of a chip card. In these networks, the identification of the
_
users by the network provider is very reliable and independent of the used
terminal. The GSM mobile radio network is an example of such a network.
The GSM network was developed primarily for voice
communicafiivn between mobile users. The interface between GSM
networks and other networks, for example the Internet, is however also
known and was among others described in patent application
EP-A1-0841788 among others. Thus, subscribers to a mobile radio network
can also access data filed by another provider at a host In the Internet and
receive these data for example on mobile terminals, for example mobile
telephones or palmtops. A protocol for data transfer and for applications
within a mobile radio network was specified among others in the WAP
(Wireless Application Protocol) forum.
Subscribers to mobile radio networks who access the Internet
with their mobile terminals in said fashion are identified only within the
mobile radio network. This secure identification method by means of the
users' chip card cannot however be used by object providers in the intemet
to check access authorization of said users to protected objects.
t=urthermore, these providers cannot easily bill the access to users.
It is therefore an aim of this invention to propose a method and
a system to provide objects to users of a mobile telecommunications
network, wherein users identify themselves with an identification module
and wherein identification is also used by various providers to verify access
authorization to various objects.
CA 02292530 1999-11-30
CA 02292530 2004-02-05
3
Another aim of the invention is to propose a method and a
system that can also be utilized by nomad users who are not linked to a fixed
node in the telecommunications network. Nomad users are defined in this text
as users who can log in from various nodes in a telecommunications network
and whose identification is not dependent on their geographical location. As
an example of nomad users one could cite subscribers in a digital mobile
radio network, users of a fixed and PLC (Power Line Communication) network
who let themselves be identified personally and regardless of the used
terminal through an identification module in the network.
Another aim of the invention is to propose a method and a
system wherein the providers of objects let themselves be identified through
an identification module. Thus they can be identified reliably in order to
enable
them to administer the access authorization to filed data themselves.
The access authorization granted by the providers can be
nominal or issued to the holder of a token. In the former case only users
whose names or identification are on a list drawn up by the provider may
access the objects in question. In the latter case, the users must obtain a
transferable token to access these objects. These tokens contain for example
an electronic key for the documents in question and can be sold or traded.
Thus the copyright to a document, for example to a text or a multimedia
document, may also be sold.
The present invention will be better understood from reading
the description given by way of example and illustrated by the sole figure
representing a block diagram that shows the most important components of a
telecommunications system according to an embodiment of the invention.
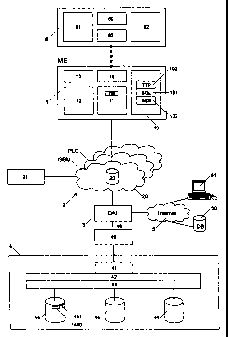
Figure 1 represents in a schematic way a terminal 1 that can
be used in a telecommunications network 2. The terminal can be for example
a digital mobile radio apparatus, for example a mobile radio telephone or
CA 02292530 2004-02-05
4
a laptop/palmtop that can be used for example in a GSM network 20 or a UMTST""
network. The terminal 1 can however also be a PLC (Power Line Communication)
terminal that can be linked to other terminals over a current network 2. In
one
variation terminal 1 is comprised of a normal terminal in a fixed network, for
example a telephone, a fax machine, a television, radio or DAB receiver or a
PC
with modem that is equipped with a chip-card reader.
The terminal in this example comprises an identification module 10 (to
be explained below), data processing means 11 (for example a processor with
corresponding storage means), input means 12, for example a keyboard, a
microphone, an input pen and/or a mouse, as well as output means 13, for
example a LCD and/or a loudspeaker. Preferably the terminal 1 additionally
includes a contact free interface 14 which enables it to communicate with
other
apparatus 6 in the same room. The contact free 15 interface 14 can be for
example an infrared interface, for example according to the IrdA protocol, or
preferably a radio interface according to the Bluetooth specification. The
other unit
6 can for example serve to extend the input, replay or storage possibilities
of the
usually portable terminal 1. The apparatus 6 can be for example a PC that
offers
more storage and processing means or a display unit, for example a monitor, a
projector, a television set or a printer, or else a receiver, for example a PC
with
Internet connection, a DAB receiver etc. The transfer of data between terminal
1
and the external unit 6 is preferably bi-dimensional.
The processing means 11 preferably consist of hardware components
as well as software modules, for example a WAP (Wireless Application Protocol)
module to send and receive data according to the WAP protocol.
Other components in terminal 1 could also include for example a GPS
(Global Positioning System) receiver (not shown) or a similar location
determining
device through which the geographical location of the terminal can be
established.
CA 02292530 2004-02-05
The user of terminal 1 is identified in the network through an
identification module 10, for example with a chip card 10 inserted in the
terminal.
Such identification cards are already common among others in GSM mobile radio
telephones and are also used in PAY-TV control units and in various computer
networks. The identification card 10 comprises preferably a processor (not
shown),
for example a microprocessor with integrated memory as well as contact
surfaces
(not shown) to link the card with the terminal.
An identity indication 102 that clearly identifies the user in the 10
telecommunications network 10 is stored in a protected part of the card 10.
Such
information is known for example in GSM networks as IMSI (International Mode
Subscriber Identity). As described below, this identification according to the
1 S invention is also used for the identification of the users in database
system 4
In one form of the invention, an applet, for example a JAVAT"" applet in
a JAVAT"" compatible chip card, containing for example GSM functions, can be
used as a means of identil7cation. In this way, the method according to the
invention can also be carried out with a JAVAT"" card.
The identification card 10 also comprises preferably encryption 20 and
signature means 100 for signing and encoding messages as well as checking the
authenticity of messages through network 2. For this purpose preferably the
TTP
(Trusted Third Party) process is used, which is described in patent
application
W098/37524 in the name of the applicant. Thus can confidentiality,
authenticity,
the non-deniability of the origin, the integrity of the data as well as the
authenticity
of the sender in question be ensured.
A SQL client 101 is furthermore preferably integrated in card 10 as a
software application. The company Centura already offers SQL clients
integrated
in a card. Thus a call according the SQL protocol can be made between the SQL
client on the card and an external SQL database server in the
telecommunications
network, as will be explained further below. Other
25-11-99; 9:47 ;Patents & FETHERSTONHAUGH ;+41 32 724 96 62 # 7/ 21
6
database query languages can also be used instead of or in addition to SQL
in the frame of the invention.
Card 10 preferably supports java and the SQL client is preferably
a SQL JDBC (SQL Java DBC).
Terminal 1 with the identification module 10 can log into a
nomad network 2, for example in a mobile radio network 20, to -
communicate with other terminals in this network. Network 2 comprises _
preferably a home location register (HLR) 22 in which user specific
information, among others the billing address as well as the present ;
l0 location of the terminal in the network, is stored. When the user switches
=_
on his terminal or connects it to fihe network, he is identified by HLR 22
through user identity indication 102. The connections that the user makes
through the network 2 or use of other VAS (Value Added Service) in the
network are then billed by a Billing Server 21, either by charging an
account (not shown) in card 10 (Prepaid) or by later billing the user with a
monthly bill (Postpaid).
Preferably the user can also log in with the terminal into
networks run by other network providers. Known roaming methods are
used for this purpose. Preferably the user can also log in with his
2o identification card 1o into another type of network, for example with the
same card and suitable terminals either in a GSM network with 900, 1800 or
1900 MHz or also in a PLC (Power Line Communication) network. The user
is, however, always billed by the billing center of his home network.
Through the appropriate interface DIA (Direct intemet Access) 3
the network 2 is linked to the Internet 5_ This interface allows the bi-
directional transmission of messages between the nomad network 2 and
the Internet. In this manner, the user why is logged in network 2 can, with
his terminal 10, also prepare, send and receive emails or download data
from web server 51 or database 50 in the Internet. For that purpose the
WAP (Wireless Application Protocol) is preferably used.
CA 02292530 1999-11-30
CA 02292530 2004-02-05
7
In Internet 5 the nomad user remains anonymous or is identified at
most by an easily forged email address. Access to protected or expensive
applications or objects in the Internet is therefore only possible through
additional end-to-end encryption methods. The billing of these applications is
in this case generally done by the service provider 50, 51, for example
through the querying users giving their credit card number. The user is billed
individually for each required service, which is rather awkward especially if
many small amounts from various providers are being billed. Furthermore, in
most cases the users and the object providers do not know each other so
that the latter are hardly in any position to check the users' solvency.
According to the invention, the network 2 is also linked to a
database system 4 that is being administrated for example by the provider of
network 2 and/or one or several organizations associated with the provider.
The link between network 2 and database system 4 is effected preferably by
the mentioned DIA3 and a link 49, for example a TCP/IP, ATM or XDSL link
and an optional firewall device 40. The TCP/IP link and the firewall device
are preferably administrated by the provider of network 2 and/or of system 4;
the connection is therefore not established via the public Internet 5.
The database system consists of one or preferably several
distributed databases 44 (Hosts) that can be located in various geographical
locations. A conventional database administrator 42 operates the whole
database, among others the filing of the objects (Document Hosting) and if
necessary also the replication rights. The database administrator can include
for example a conventional SQL server, preferably a JAVA DBC server. A
user administrator 43 consisting preferably of a software module, operates
the rights of the various users.
In order for a user to provide objects to other users of the
telecommunications network, the user must first reserve a domain 440 in
database system 4. To this effect he has to log into network 2 and send a
message to the database system, for example through the WAP protocol
25-11-99; 9:47 ;Patents & FETHEFSTaNHAUGH ;+41 32 724 96 62 # 9/ 21
andlor a SQL protocol. According to the invention the user is identified by
the user administrator 43 through the transmitted identity indication 102
from the identification module i0. In the case of a GSM network 20, the
IM51 or any other identification contained in an applet stored in the SIM
card 10 is communicated through network 2 and the safe channel 3, 49, 40
to the database system. The user can then store data and objects in this
reserved domain 440.
Reserved memory areas are preferably rented to the user by the
database system. The amount billed depends for example on the reserved
or actually used memory area and of the length of usage. Other
parameters, for example a certain requin~d quality of service, can also
effect the amount billed. Preferably the details of the billed amounts are
established by the user administrator 43, embedded in a message and
assigned through link 49 and the home network of the user to the billing
center 21. To this end methods can for example be used that are already in
use for the transmission of CDR (Call Detail Records) in a roaming process
between two mobile radio networks . Applets, for example JAVA applets,
can also be used to allow for a billing in different networks 2. The charge
for use of the database is then simply billed to the providing user with the
ZO normal bill for use of the network or is billed separately or is debited to
an
account in his card.
The providing user can allot various access authorizations 441 to
the stored objects. For example, certain objects can be private, in which
case only he has got access to these objects. In this private area he can
store
for example objects and documents for which there is no space on his
identification card 10. He can also use this area of the card for example to
backup certain parts of his card, for example to copy the stored telephone
numbers and user specific parameters in database system 4. He can store
objects in said private area as well as his card or his terminal 1.
Other objects may for example only be accessible for certain
other users (Closed User Group). These objects can encompass for example
internal company documents and applications. The authorized users can
CA 02292530 1999-11-30
CA 02292530 2004-02-05
9
either be mentioned by name - in this case only the users listed by the
provider have access to said objects - or they can be holder of certain
transmittable tokens - in which case only the users who have first acquired
the
appropriate token can access said objects once. The tokens can include for
example an electronic key that is necessary to read the objects. After a
successful access to the relevant objects, the corresponding tokens is erased.
In this way objects, for example text documents, computer programs or
multimedia objects, can be sold.
Other objects can of course also be made public and generally
accessible; in this case, every user without any specific authorization can
access said objects.
A user wanting to access objects stored in database system 4 first
has to connect to this system. For this purpose he uses a terminal 1 with an
identification module 10, preferably a WAP supporting terminal andlor module.
He is identified in network 2 and database 4 through his identity indication
stored in his identification module. Preferably his identity is also checked
by a
UP server 41 that checks his electronic signature generated by the encryption
system 100. This electronic signature can be required either for every use or
only for access to certain objects, for example only if the objects provider
demands it. A password can also be required by the user administrator, by a
provider or by a suitable program in his identification module for example to
access certain objects or address areas of the database.
The querying user can then send a query to database system 4.
The query in the easiest case can be only the address of a sought document
in the database system, or it may be a more complex query, for example a
SQL query generated by the SQL client 101, that is understood and
interpreted by the SQL server. The SQL server then determines the answer to
the query, which can for example consist of a list with one or several objects
440 in the database system, and verifies whether the already identified user
is
allowed to access these objects. To this end, it verifies the authorizations
allotted to these objects by the provider.
CA 02292530 2004-02-05
If the querying user's access authorization is granted, the database
system sends a reply to him, said reply already containing for example a copy
of
the sought object. The required object can then be seen, saved or listened to
on
the terminal 1 of the user or it can be transferred via an infrared or
Bluetooth
interface to another unit 6. If the user has no access to these objects, he
receives
preferably a message or is asked to enter another identification, for example
in
the form of a password. Preferably the number of tries is limited to n, for
example
10 n = 3; after n unsuccessful tries, access is then denied.
The providers can preferably allocate an expiration date for their
objects. In this case the database system allows access to these objects only
up
to the indicated date, which can be useful for example to distribute tariffs
or other
time dependent information. In one form of the invention it is also possible
to
provide a time window indicating the beginning and end of the period of
validity.
As mentioned above, the providers can store for example documents
or objects in any storage format whatsoever, for example text documents, still
or
moving pictures, sound sequences etc. They can also, however, store
applications or computer programs that can be downloaded and run by other
users; the providers can either allow a single use or an unlimited number of
uses.
Preferably users can also store objects as well as process applications that
can
be implemented in the database system. For example, search engines be stored
that allow users to search for other objects in the database system 4 or to
carry
out other services. Applications may also be stored in the database system,
for
example personal agents, to which various parameters can be applied by
querying users to implement certain functions.
The user administrator 43 preferably examines whether the querying
user's terminal is technically able to access the sought objects. It would for
example be purposeless to send a document consisting of picture data only to a
user whose terminal does not allow the display of pictures. For this purpose
the
JINIT"" standard known for other applications in GSM
25-11-99; 9:47 ;Patents & FETHERSTflNHAUGH ;+41 32 724 96 62 # 12/ 21
11
networks is preferably used to ensure technical compatibility between the
user's terminal and the sought object.
The directory hierarchy in database 44 is not essential to the
invention but it has to allow for fast searches for stored objects. Each
stored object has preferably its own address; certain parts of the address
are allotted by the database administrator whereas other parts are defined
by the providing user. Search engines that are supplied by the database
administrator 42 and/or the user help users to find objects by indexing or
cataloguing other objects. Users can preferably also save as bookmarks the
address of important documents or other standard queries in their
identifiication modules.
A user profile is preferably stored in the database system and
operated by the user administrator. User specific details are stored in the
user profile, for example the identification, the preferred language, the
preferred terminal etc., or also the preferred bookmarks. Preferably the
user profile also contains a required Quality of Service (QoS). In that way,
various users can have access of differing quality to the objects, which may
be billed differently. The Qo5 can indicate for example the objects'
bandwidth, reaction time, availability, preferred transmission channel (for
example SMS, USSR or speechldata channel in the case of a GSM mobile
radio network ) etc.
Also, users who store and provide objects in database system 4
allocate various Quality of Service values to said objects. For example,
providers can indicate that every user with the maximal bandwidth can
access certain objecrts. Providers can also request, for example, that their
objects be stored in better, for example faster or more secure, server if the
database system is spread over several servers.
A fee tan be charged for access to the sought objects in database
system 4. It has already been mentioned that certain objects can only be
accessed when the querying user has first acquired a token, and said tokens
can also be sold or traded. The administrator of the database system 4 can
CA 02292530 1999-11-30
25-11-99; 9:47 ;Patents & FETHERSTONHAUGH ;+41 32 724 96 62 # 13/ 21
12
also .request a fee which can then be directly billed to the user by the above
mentioned mechanism through account center 21. The charged fee
depends on various parameters, for example on the siae of the object (in
kilobytes), on the type of the object, on the required quality of service, on
the complexity of the query etc. Furthermore, the administrator of the
database system as well as the provider of nefinrork 2 (if they are two
separate entities) can demand a fee for the transfer of the object to the
user's terminal. The fee requested by the account center 21 can either be
deducted from a prepaid account in the users identification module or it
can be billed with the user's bill for use of the telecommunications
network.
The provider can, with the same mechanism, also charge a fee for
access to the objects he provides. The requested fee is at the earliest
allocated when certain objects or classes of objects are stored. If a user
later
accesses these objects the fee is determined by the database administrator,
then communicated to the account center 21, billed to the querying user
together with a fee from the database system administrator and credited
to the provider.
Users can preferably access database system 4 from the intemet,
either to reserve memory areas in which to store objects, or to access stored
objects. In this case a point to-point encryption and signing method
between the users 5i from the Internet and the database system a is
preferably used so as to guarantee reliable identification of the users from
the Internet. The TTP method for example can be used to this end. The
users from the Internet cannot however access costly objects in the
database system 4, or can only do so with another billing mechanism, far
example a credit card.
CA 02292530 1999-11-30