Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
A METHOD AND APPARATUS FOR DETERMINING WHETHER A FEE IS TO BE CHARGED TO A
PARTY
INITIATING A TELEPHONE CALL
S
TECHNICAL FIELD OF THE INVENT10N
The present invention relates to communications and, more particularly, to a
method and apparatus for determining whether a party making a telephone call
or
1o sending an email message is to be charged a fee. More particularly, the
method and
apparatus of the present invention provide for determining whether a patty
initiating a
telephone call or email communication is authorized by the party who is the
target of
the telephone cal( or email message. It the initiating party making the
telephone call or
sending the email message is not authorized by the target party, the
initiating party may
1, be charged a fee in return for being allowed to communicate with the target
party.
BACKGROUND OF THE INVENTION
Many businesses utilize telemarketing as a means of soliciting customers in
order to promote or sell the company's products and/or services. Telephone
2U solicitations have become such an annoyance to many telephone subscribers
that at
least one State, namely Georgia, has enacted legislation intended to prevent
companies
or individuals from contacting telephone subscribers who have been placed on a
list,
referred to as the "No Call List", maintained by the Georgia Public Service
Department. A fee is charged to any telephone subscriber wanting to be
registered on
2s the list. Telephone solicitors are required to obtain the list and
quarterly updates of
registrants to the list and to pay an annual fee. if a telephone solicitor
places a
telephone call to anyone on the list, the telephone solicitor can be subjected
to a fine.
One of the disadvantages of using the "No Call List" is that subscribers must
pay a fee to be placed on the list in order to prevent telemarketers from
contacting
_so them. Currently, this fee is $5.00 per telephone number. Therefore, a
financial burden
is placed on the telephone subscriber in order for the telephone subscriber to
avoid
being bothered by unwanted telephone calls.
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
A service known as Caller-ID is now available which allows a party receiving a
telephone call to visually review the telephone number and/or the identity of
the calling
party before deciding whether to accept the telephone call. However, Caller-ID
has
several disadvantages. First of all, when the subscriber receives a telephone
call, the
subscriber must visually review the caller's identity and/or the telephone
number on the
display of the Caller-ID device to determine whether he or she wishes to
accept the
telephone call. Therefore, the telephone rings regardless of whether or not
the
subscriber is interested in accepting the call, which interrupts the
subscriber. Although
the Caller-ID service does provide the subscriber with the option of blocking
telephone
m calls, it does not provide for billing the calling party a fee in order to
connect the
calling part with the subscriber.
Secondly, many telephone calls show up on the Caller-ID display as
"unknown" or "private'' numbers, thereby preventing the subscriber from
ascertaining
the telephone number and/or identity of the calling party. Therefore, the
subscriber
> > often feels compelled to accept the call when this message is displayed
even though the
subscriber does not know the telephone number and/or the identity of the
calling party.
Recently, a service known as "Privacy Manager", developed by Ameritech
Corporation, solves some of the shortcomings of Caller-ID related to "unknown"
and
"private" numbers. Privacy Manager implements software which intercepts calls
from
2~~ "unknown", "private", ''unavailable", "out-of area" and "blocked" numbers
which are
directed to persons subscribing to the "Privacy Manager" service. The software
then
causes the caller to be asked to record his or her name and then provides that
information to the subscriber. The subscriber then decides whether he or she
wishes to
accept the call. Therefore, the caller is not connected to the subscriber
until the
2a subscriber has indicated that he or she will accept the call. If the caller
does not
provide the caller's name, the software causes the call to be disconnected.
One of the disadvantages of Privacy Manager is that the telephone rings and
the subscriber must then decide whether to accept the call. Therefore, even if
the
subscriber decides not to accept the call, the subscriber has been
inconvenienced by the
3o call.
2
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
Accordingly, a need exists for a method and apparatus that allows a subscriber
to authorize certain callers to be connected to the subscriber and, on the
other hand,
which allows a subscriber to effectively block calls from unauthorized parties
and/or
selectively accept the unauthorized calls in exchange for some pecuniary
benefit
a charged to the party initiating the call. In this way, a financial burden is
not placed on
the subscriber, but rather, is placed on the unauthorized caller. Furthermore,
if the
subscriber decides to accept an unauthorized call, the subscriber can,
depending on
how the fees are allocated, receive a portion of the fee charged to the
telemarketer in
return for being connected to the subscriber.
to With respect to email communications, many companies and individuals are
currently using email to solicit business. The receiving party often has never
even
spoken with the person sending the email message and has not even expressed an
interest in doing business with the party sending the email message.
Currently, when a
subscriber of an Internet Service Provider (ISP) wants to check his or her
electronic
1 ~ mail, the subscriber connects to the subscriber's ISP and any new mail is
downloaded
to the subscriber's computer, or data terminal equipment (DTE), via the
subscriber's
data communication equipment (DCE), e.g., a modem, which is coupled to the
DTE.
The subscriber may have to dial in to the ISP in order for these events to
occur or the
subscriber may be connected to a server that periodically connects with the
ISP or that
2U has a ''nailed up" connection to the ISP to enable email for the subscriber
to be
downloaded to the server.
In each of these cases, email intended for the subscriber is ultimately
downloaded from the ISP and displayed on a monitor comprised by the
subscriber's
DTE when the user checks to see whether he or she has received mail. The user
2> normally must read the message in order to determine that the message is an
unreduested and/or undesired message.
Oftentimes, people solicit business over the Lnternet by sending out email
messages, which may be, for example, advertisements, to large numbers of
people.
The recipients of these messages often are not interested in receiving these
messages.
so Sometimes these messages contain a large quantity of data and may take
quite a bit of
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
time to download. Furthermore, some of these messages contain data such as
computer viruses that can adversely affect the subscriber's computer.
Accordingly, a need exists for a method and apparatus that allow unwelcome
or unsolicited email messages to be screened out so that they are not
downloaded to
a the subscriber, or to allow the messages to be provided to the subscriber in
return for
charging a fee to the sender.
SUMMARY OF THE INVENTION
The present invention provides a method and apparatus for allowing a
m telephone subscriber or ISP subscriber to selectively control which parties
are allowed
to communicate with the subscriber by either telephone or electronic mail
(email).
When a party makes a telephone call or sends an email message to a target
party, a
determination is made as to whether the initiating party is an authorized
party. If so,
the initiating party is allowed to communicate with the subscriber in the
normal
t ~ manner. If not, the initiating party may be charged a fee in return for
being allowed to
communicate with the target party.
The determination as to whether a party is an authorized party preferably can
be accomplished in a many different ways. In accordance with one embodiment,
an
authorization list associated with the target party is checked to determine
whether the
2o initiating party is an authorized party. Therefore, if the telephone number
or email
address of the initiating party, depending on which mode of communications is
used, is
on an authorization list associated with the target party, the initiating
party is allowed
to communicate with the target party in the normal manner. if not, the
initiating party
may either be blocked from communicating with the target party or may be
charged a
2a fee in return for being allowed to communicate with t:he target party.
In accordance with an alternative embodiment, the communication being
attempted by the initiating party may include an identifier indicating that
the calling
party is not an authorized party. For example, the identifier could indicate
that the
Callrng party is a telemarketer or a person soliciting business via email.
This could be
,o the case where the state and/or federal government have required, by
statute or
=t
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
otherwise, that parties soliciting business via telephone or email be required
to append
the identifier to communications directed to target parties. In this case, the
target
party's authorization list could simply indicate whether or not the target
party is willing
to accept communications associated with the identifier. The identifier could
be part
a or all of the initiating party's telephone number or email address or it
could be a
separate identifier. For example, a telemarketer initiating a telephone call
could be
required by law to dial a particular code when dialing a target party's
telephone
number. The telephone network would then identify the party as a telemarketer
and
then check to see whether the target party has authorized communications from
m telemarketers. If not, the initiating party could simply be blocked from
communicating
with the target party or could be charged a fee in return for being allowed to
communicate with the target party.
These and other features and advantages of the present invention will become
apparent from the following description, drawings and claims.
is
BRIEF DESCRIPTION OF THE DRAWINGS
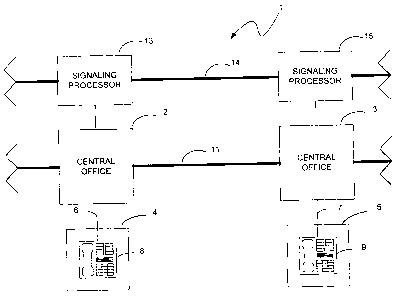
Fig. l is a block diagram of a typical telephone network implementing
common-channel signaling, commonly referred to as signaling system 7 (SS7).
Fig. 2 is a block diagram illustrating the components of the central office
shown
2u in Fig. 1.
Fig. 3 is a flow chart functionally demonstrating the method of the present
invention in accordance with a first embodiment.
Fig. 4 is a tlow chart functionally demonstrating the method of the present
invention in accordance with a second embodiment.
2s Fig. 5 is a block diagram of the switching module shown in Fig. 2.
Fig. 6 is a block diagram of the software and data stored in the switch memory
of the switching module shown in Fig. 5.
Fig. 7 is a flow chart showing the process performed by the switching module
of Fig. .5 in determining whether a feature is to be activated or whether a
call is to be
3u routed.
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
Fig. 8 is a flow chart illustrating the method of the present invention for
modifying an existing authorization list in accordance with the present
invention.
Fig. 9 is a flow chart illustrating the method of the present invention in
accordance with one embodiment for creating a new subscriber authorization
list.
s Fig. I 0 is a flow chart illustrating the method of the present invention
for
allowing the subscriber to automatically add the telephone number of the most
recent
unauthorized calling party to the subscriber's authorization list and/or which
allows the
fee that was charged to the caller to be deleted from the billing records.
Fig. 1 I is a block diagram of an Internet network with which the present
to invention can be implemented.
Fig. I 2 is a flow chart functionally demonstrating the method of the present
invention in accordance with the preferred embodiment.
DETAILED DESCRIPTION OF THE INVENTION
ns Fig. 1 illustrates a block diagram of a telephone system 1 in which the
method
and apparatus of the present invention may be implemented. For ease of
illustration,
only two customer premises 4 and 5 and the central ofFices 2 and 3 to which
they are
connected are shown in Fig. I. Central o~ces ? and 3 provide the switching
operations for connecting a calling party located at a customer premises 5
with a
2o subscriber located at another customer premises 4 A twisted, or copper,
pair 6
connects the central office 2 to a telephone 8 located at the customer
premises 4. The
central office 2 is connected to central office 3 via a cable trunk I 1. The
central office
3 is connected to a telephone 9 located at customer premises 5 via a twisted,
or
copper, pair 7. Voice information is transmitted over trunk 1 I between
central offices
2, 2 and 3.
Preferably, call signaling is accomplished in accordance with the common-
channel signaling protocol, which is well known in the communications industry
and
commonly referred to as signaling system 7 (SS7). The common-channel signaling
protocol utilizes a separate dedicated data channel to carry signaling
information in the
form of short packets of data. Ln accordance with this protocol, the packets
of data
G
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
contain call signaling information as well as the identification and/or
telephone number
of the calling party. These packets are transmitted between the signaling
processors 13
and 1 > via cable trunk 14. The signaling processors 13 and 15 determine the
switching
of the customer circuits to be performed by switching modules (not shown)
located at
a the central offices 2 and 3 to cause the calling party located at customer
premises 5 to
ultimately be connected to the subscriber located at customer premises 4.
Fig. 2 is a block diagram which illustrates the central offices 2 and 3 in
more
detail. Each of the central offices comprise an administrative module and a
plurality of
switching modules. The functions of these components will be described with
respect
m to central office 2. The administrative module 18 receives the call
signaling
information from the signaling processor 13 and causes the switching modules
20 to be
switched to set up call sessions for telephones 21. The administrative module
18 also
handles all billing tasks for the central office 2 and creates billing files
that are
ultimately dumped to a location designated by the telephone company where they
are
to used to generate customers' bills. The administrative module comprises a
computer
(not shown) running software for performing all of these tasks. The
administrative
module 18 also comprises a memory device (not shown) in communication with the
computer with for storing any files used by or generated by the computer and
any
other software needed by the computer for performing all of its tasks.
2o The switching modules 20 perform the switching of the customer circuits.
Preferably, the method of the present invention is implemented in part by the
switching
modules 20 and in part by the administrative module 18. Each of the switching
modules comprises a computer for performing the switching functions. This
computer
preferably is utilized in accordance with the present invention to determine
whether the
25 identity and/or telephone number of the calling party is on a list of
parties authorized
by the called parties. Each switching module 20 contains a list which
corresponds to
each of the called parties serviced by that particular switching module. Once
this
determination is made by the switching module 20, the switching module 20
takes the
appropriate action. The administrative module 18 calculates all billing
information
>u relating to the fee to be charged to and collected from the calling party.
7
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
This method of the present invention is shown in detail in Fig. 3 in
accordance
with a first embodiment. When a calling party initiates a telephone call, the
call
signaling information is decoded in the manner discussed above, as indicated
at block
32. It will be understood by those skilled in the art that the method and
apparatus of
the present invention apply to all types of communications devices which
utilize the
telephone network including, but not limited to, for example, analog
telephones, digital
telephones, cordless telephones, hand-held devices, facsimile machines,
pagers, cellular
telephones, etc. It will be understood by those skilled in the art the manner
in which
the method and apparatus of the present invention apply to all such devices.
to The information decoded at block 32 will include the calling party's
telephone
number, as well as the subscriber's telephone number. This information may
also
contain the identity of the calling party. Preferably, the subscriber's
telephone number
is used to generate a memory address, or a block of addresses, at which the
subscriber's list of authorized calling parties is stored. The computer of the
switching
module 20 then compares the calling party's telephone number with the
telephone
numbers contained in the list, as indicated at blocks 33 and 34 and makes a
determination as to whether the calling party's telephone number is contained
on the
list of authorized calling parties.
If so, the calling party is connected to the subscriber by the switching
module
2o without a fee being charged to the calling party's account, as indicated at
block 35. if
not, the calling party is charged a fee and the calling party is connected
with the
subscriber, as indicated at block 36. The calling party's billing account is
then
updated, as indicated at block 37. The administrative module 18 then
calculates the
percentage of the collected fee to be added to the subscriber's account, as
indicated at
2, block 38. The administrative module then updates the subscriber's billing
account, as
indicated at block 39.
It will be understood by those skilled in the art that the order in which
steps 3 5
through 39 are performed is not critical to the present invention. For
example, the
operations occurring at block 37 may be performed prior to the calling party
actually
3e being connected to the subscriber. Similarly, the subscriber's account
could be
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
updated before the calling party's account is updated. Also, other
determinations may
also be made, such as, for example, whether the calling party's billing
account is
current, i.e., whether or not the calling party has been delinquent in paying
its
telephone bill or its toll fee bill. It should also be noted that it is not
necessary that
steps 39 and 40 be performed at all.
Fig. 4 illustrates an alternative embodiment of the present invention which is
similar to the embodiment shown in Fig. 3 except that, prior to billing the
fee to the
calling party's account, a determination is made as t.o whether the calling
party has
authorized these types of fees to be billed to its account, as indicated at
step 45. This
m feature of the present invention is intended to prevent calling parties from
being billed
without their knowledge or consent. A determination is made at step 43 as to
whether
the calling party is on the list of authorized calling parties. If so, the
calling party is
connected with the subscriber without the fee being charged, as indicated at
block 44.
If the calling party is not on the list of authorized calling parties, a
determination is
t > made as to whether the calling party has authorized billings for these
types of fees to
be charged to its account, as indicated at block 45. If not, the calling party
is informed
that it has not authorized these types of billings, as indicated at block 47.
If the calling party has authorized such billings, the fee is charged to the
calling
party's billing account and the calling party is connected with the
subscriber, as
2ca indicated at block 46. The calling party's billing account is then
updated, as indicated
at block 48. The percentage of the fee to be added to the subscriber's account
is then
calculated, as indicated at block 49, and the subscriber's billing account is
updated, as
indicated at block S I . However, it should be noted that steps 49 and 51 are
optional.
Whatever percentage of the fee that is not added to the subscriber's account
may be
z~ retained by the telephone company or may be paid to some other entity. As
indicated
above, the manner in which the fee is allocated is not critical to the present
invention.
It should also be noted that the methods of the present invention described
above can also be used with facsimile machines since these also make use of
the
telephone network and since the telephone number of the calling facsimile
machine is
;u contained in the common-channel signaling information. In this case, the
steps
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
performed in Figs. 3 and 4 will also be performed for facsimile communications
using
the telephone number of the facsimile initiating the communication.
It should be noted that the fee may be charged to the calling party regardless
of
whether or not the called party actually answers the telephone. In this case,
the fee
would be charged when the central office connects the calling party's line
with the
called party's line, regardless of whether or not the called party answers the
telephone.
As stated above, rather than comparing the calling party's telephone number or
identity to a list of authorized calling parties, an identifier associated
with the calling
party could be analyzed to determine whether or not the calling party is an
authorized
calling party. For example, telemarketers could have an identifier associated
with
them, such as a particular sequence of telephone digits, which identify them
as
telemarketers. The telephone network could be configured to detect this
identifier.
The identifier could be detected at any one of many suitable locations within
the
telephone network, as will be understood by those skilled in the art. A
determination
would then be made as to whether or not the called party has authorized the
receipt of
communications from telemarketers. If so, the telemarketer will be allowed to
communicate with the called party in the normal manner. If not, the
telemarketer may
be blocked from communicating with the called party or may be charged a fee in
return
for being connected with, or being allowed to communicate with, the called
party.
2o In the case where an identifier is used to identify the type of party that
is
initiating the communication, the telephone subscriber's authorization list
would not
contain a list of authorized telephone numbers, but instead would simply
indicate
whether the subscriber has authorized calls from parties associated with the
identifier.
Therefore, a determination would not have to made as to whether any entry of
the
2a subscriber's list matches the identifier. Rather, a single determination
would be made
as to whether or not the subscriber has authorized communications associated
with the
identifier.
Those skilled in the art will understand that this embodiment of the present
invention could be accomplished in many ways. One of the advantages of this
so embodiment is that it is not necessary for a list of authorized telephone
numbers to be
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
generated for each subscriber. Rather, a single entry in a database could be
used to
determine whether or not the subscriber is willing to freely accept
communications
from the party initiating the call. Of course, calling partys such as
telemarketers may
not freely identify themselves. Therefore, they may be required by law to do
so. As
a evidenced from the promulgation of statutes such as those relating to the
Georgia "No
Call List", requiring partys to comply with such statutes is feasible. Another
advatage
to this embodiment is that the telephone network could easily and quickly
determine
whether a calling party is an authorized calling party, thereby reducing the
amount of
processing overhead that is associated with implementing the present invention
in the
telephone network.
Fig. 5 is a block diagram illustrating the components of the switching module
shown in Fig. 2. The switching module comprises line units 78 which comprise
circuitry (not shown) which terminates the telephone lines connected to the
telephones
21. A time slot interchanger (TSI) 74, also commonly referred to as the
switching
t ~ fabric, controls the multiplexing and demultiplexing of the telephones 21
communicating with the switching module 20. The TS1 74 is in communication
with a
dual tone multifrequency (DTMF)/dial pulse decoder 76 which decodes the
frequencies
entered on the keypads of the telephones 21. The DTMF 76 then provides digit
reports corresponding to the decoded frequencies to a core processor 70 of the
20 switching module 20. The core processor receives the digit reports and
determines
whether a call is to be routed or whether a feature is to be activated. The
core
processor 70 runs software and other data stored in switch memory device 72.
In
accordance with the present invention, the core processor 70 generates the
subscriber
authorization lists and updates, or modifies, the authorization lists, which
preferably
2a are stored in switch memory device 72. The core processor 70 also performs
the tasks
of determining whether a caller is an authorized or unauthorized caller, as
discussed
above with respect to Figs. 3 and 4.
The authorization lists may be generated in a plurality of manners. In
accordance with a first embodiment of the present invention, the subscriber
may simply
call the local telephone company and orally provide the local telephone
company with
n
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/I8I83
a list of authorized callers. Preferably, the list is maintained by the
subscriber's local
telephone company because the method and apparatus of the present invention
are
preferably implemented at the central office, which is typically owned and
operated by
the local telephone companies. However, those skilled in the art will
understand that
the present invention is not limited with respect to the location in the
telephone
network at which the present invention is implemented and thus is not limited
with
respect to the entity which maintains the authorization list. For example, the
authorization list could be maintained by a long distance carrier.
In accordance with the first embodiment of the present invention, whenever the
m list is to be updated, i.e., whenever a telephone number is to be removed or
added to
the list, the subscriber simply calls the Local telephone company (or other
entity
maintaining the list) and orally updates the list. A person at the local
telephone
company edits the list on a computer in accordance with the subscriber's
requests and
the modified list is then saved in switch memory device 72. In the case where
one or
i a more identifiers are used to identify the types of parties, the person
would simply tell
an appropriate person at the telephone company that they want to block, or do
not
want to freely accept (i.e., without charging the calling party a fee),
telephone calls
from calling parties associated with the identifiers.
Also, if a caller was charged in return for being connected to the subscriber
and
2u the subscriber now wants to add the caller to the authorization list and/or
delete the
charge, the subscriber can orally request that the caller be added to the list
and/or that
the charge to the caller be deleted. Once the modifications to the list have
been made,
the list with the updates is re-saved in the switch memory device 72. The
charges
associated with any unauthorized calls are also saved in one or more files in
the switch
2~ memory device 72 and these files are eventually downloaded to the
administrative
module 18 so that appropriate billing records can be updated and/or generated.
Fig. 6 is a block diagram illustrating the software modules and the database
stored in switch memory device 72 which are utilized by the core processor 70
to
generate and update the subscriber authorization lists. The core processor 70
runs a
,u digit analysis software module 79 which analyzes the digit reports received
by the core
l2
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
processor 70 from the DTMF decoder 76 to identify the digits that have been
pressed
or dialed. Information relating to the identified digits is then utilized by a
call
processing software module 80 executed by the core processor 70. The call
processing software module 80 determines whether the digits represent a call
to be
routed or whether they represent a feature to be activated. In accordance with
the
present invention, the feature to be activated is a request to generate or
update a
subscriber authorization list.
Fig. 7 is a flow chart functionally illustrating the operations performed by
the
DTNLF decoder 76 and by the core processor 70 executing the digit analysis and
call
1( processing software modules 79 and 80, respectively. As stated above, the
DTMF
decoder 76 generates digit reports which are output to the core processor 70,
as
indicated by block 88. The digit analysis software module 79 being executed by
the
core processor 70 then analyzes the digit reports to determine which digits
were
entered by the subscriber and this information is passed to the call
processing module
1 ~ 80, as indicated by block 89. The call processing module 80 then
determines whether
a call is to be routed or whether a feature is to be activated, as indicated
by block 91.
If a call is to be routed, the core processor 70 sets up the path for the
call. If a feature
is to be activated, the call processing module determines which feature is to
be
activated, as indicated by block 93, and then causes the selected feature to
be
2o activated, as indicated by block 94.
When the call processing software module 80 determines at block 93 that the
digits correspond to a request to automatically update a subscriber
authorization list,
the call processing module 80 retrieves the list associated with the
subscriber from the
database 82 stored in the switch memory device 72, as indicated by block 99 in
Fig. 8.
2> The core processor 70 then modifies the file corresponding to the
subscriber's
authorization list in accordance with the digit reports received by the core
processor 70
from the DTMF decoder 76, as indicated by block 100. These digit reports
correspond to entries made by the subscriber on his or her telephone 21 which,
in turn,
correspond to telephone numbers to be added to or deleted from the list. Once
the list
3o has been modified, the list is re-saved in the database 82 contained in the
switch
13
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
memory device 72, as indicated by block 101.
The same code or different codes can be assigned to the tasks of updating an
existing list and of generating a new list. For example, the code "*62" could
be
assigned to the task of generating a new list and the code "*63" could be
assigned to
s the task of updating an existing list. If different codes are used for these
tasks, the
core processor 70 will simply perform as instructed by the software of the
call
processing software module in accordance with the code received from the DTMF
decoder 76. In this case, the routines executed by the core processor 70 will
vary
depending on which code was received.
to If the same code is used for both of these tasks, the core processor 70
will
cause a prerecorded announcement to be played back by the announcement unit 77
to
the subscriber that tells the subscriber to enter a particular digit if the
subscriber wants
to update an existing list and to enter a different digit if the subscriber
wants to create a
new list. The announcement unit 77 may be comprised in what is commonly
referred
t a to as a global digital service unit (not shown) which contains a variety
of prerecorded
announcements that serve subscribers. In this case, the recorded announcement
might
state, for example: "If you wish to update an existing list, press 1. If you
wish to
create a new list, press 2".
In this example, if a 1 was entered by the subscriber, the next recorded
2e announcement might state: "lf you wish to add a new number to your list,
please press
1. If you wish to delete a number from your list, please press 2." In this
example, if a
l was entered by the subscriber in response to this announcement, the next
announcement might state: "Please enter each number to be added to your list,
starting with the area code. After each number has been entered, press the
star key.
2, Once you have completed entering all of the numbers, press the pound key,
or simply
hang up."
if the subscriber is generating a new list, the core processor 70 may cause
similar announcements might be played back to the subscriber by the
announcement
unit 77 to assist the subscriber in creating the list. Those skilled in the
art will
3o understand the manner in which this task and the announcements, if any, can
be
m
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
customized to facilitate the tasks of creating new lists or modifying old
lists. It should
also be noted that announcements are not necessary at all. The subscriber who
has
subscribed to the service of the present invention rnay be provided with
instruction
literature which obviates the need for recorded announcements. However,
preferably
s announcements are used to facilitate this process and to make the process of
updating
and creating lists easy for the subscriber.
Fig. 8 is a flow chart generally illustrating the method of the present
invention
in accordance with one embodiment which enables a subscriber to create a new
subscriber authorization list. When the subscriber picks up the telephone to
get a dial
t o tone, the subscriber enters a code which the core processor 70 recognizes
as a request
to update a subscriber authorization list. The core processor 70 then causes a
prerecorded announcement to be played back to the subscriber which tells the
subscriber how to enter the information to be placed in the authorization
list, as
indicated by block 105. The announcement might say, for example: "Enter each
telephone number to be placed in your list, starting with the area code. After
each
telephone number has been entered, press the star key. Once you have finished
entering all of the telephone numbers, press the pound key. You may start
entering the
telephone numbers to be placed in your list now."
In this example, the call processing module 80 being executed by the core
2o processor 70 will control the generation of the list, as indicated by block
107, and, at
the same time, will wait for the pound key to be pressed, as indicated by
block 106.
Once the pound key has been depressed, the core processor 70 will save the new
list
along with an indication of the subscriber (e.g., his or her telephone number)
with
which the list is associated, as indicated by block 108.
Z> One feature of the present invention is that the subscriber is provided
with a
way to prevent callers who are not currently listed on the subscriber's
authorization list
from being charged a fee in return for being connected to the subscriber's
telephone.
Preferably, immediately after the subscriber has finished speaking or
otherwise
communicating with the unauthorized caller that the subscriber wishes to add
to the
30 list, the subscriber hangs up the telephone, thereby causing it to go "on-
hook", and
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
then immediately picks up the telephone, thereby causing it to go "ofd=hook".
The
subscriber then enters a particular code, such as, for example, "*71", which
preferably
is different from the codes) assigned to the tasks of updating and generating
authorization lists. This code indicates to the core processor.70 that the
last caller that
a was connected with the subscriber is to be added to the subscriber's
authorization list
and/or that the fee that was charged to the caller is to be deleted from the
billing
records.
Currently, typical switching modules keep track of the last call that was
connected to the subscriber's line. The well known "call back" feature
provided by
1o telephone companies uses this information. Also, when a telephone goes
"ot~=hook",
typical switching modules know the telephone number associated with the
telephone
that is "off hook". Therefore, all the subscriber has to do in order for the
last caller to
be added to the list and/or for the charge to be removed is to enter this
code, which
preferably is common to all subscribers who subscribe to the feature of the
present
1 ~ invention. An exemplary embodiment of this feature of the present
invention is shown
in Fig. 10. When the subscriber finishes speaking with someone whom the
subscriber
wants to have added to the list, the subscriber will simply hang up the
telephone, wait
to hear the dial tone, and then press the code, e.g., "*71". The call
processing
software module 80 being executed by the core processor 70 detects the entry
of the
2u code "*71 ", as indicated by block I 1 s, and then causes the last caller's
telephone
number to be added to the subscriber's list, as indicated by block 115. This
may also
cause the charge to the caller to be removed from the billing file stored in
the switch
memory device, as indicated by block l 17. This feature of the present
invention allows
the subscriber to easily update the list and to easily delete charges to
callers whom the
2 > subscriber does not want to be charged.
It should be noted that the same or different <;odes can be assigned to the
tasks
of adding the last caller to the list and of modifying the file containing fee
information
in order to delete the charge to the last caller. If the same code is used for
these tasks,
then a prerecorded announcement might be played to the subscriber when the
core
3t> processor detects the code which states: "If you would like to add the
caller to your
lG
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
list and you would like to have the fees charged to the caller removed, press
I . If you
would like to have the fees charged to the caller removed, but do not wish to
have the
caller added to your list, press 2. If you would like to have the caller added
to your
list, but do not wish to have the fee removed, please press 0."
Due to the high volume of traffic that may result from playing back
announcements to subscribers and from the keypad entries made by the
subscribers in
response to the announcements, it may be desirable to utilize a trunk unit
(not shown)
which connects the switching module 20 to one or more processors (not shown)
that
are dedicated to controlling the playback of the prerecorded announcements by
one or
l0 more announcement units to the subscribers, as well as the handling of the
keypad
entries made by the subscribers. These additional processors may use the
decoder 76
of the switching module to decode the entries made by the subscribers in
response to
the announcements, or they may use one or more separate decoders (not shown)
which
are dedicated to this task. Those skilled in the art will understand the
manner in which
this additional equipment could be implemented in accordance with the present
invention to handle these tasks.
Fig. 1 1 is a block diagram of the preferred embodiment of the present
invention
wherein the present invention is implemented as part of an ISP system. End
users
having data terminal equipment (DTEs) 121 and 128, such as personal computers,
are
2~~ connected to the network 124, which preferably is thE: Internet, via ISl's
122 and 126,
repsectively. The DTEs 121 and 128 are connected to the ISPs 122 and 126 via
data
communication equipment (not shown}, such as modems or terminal adapters. The
ISPs 122 and 126 typically comprise one or more servers and several modems, or
data
communications equipment devices, for interfacing with the network 124.
2a In accordance with the present invention, when a sending party represented
by
DTE 121 sends an email message to an intended receiving party represented by
DTE
128, the intended receiving party's ISP 126 determines whether the source
address
associated with the email communication is a source address authorized by the
intended receiving party. In order to perform this task, a computer (not
shown)
ao located at the ISP 126 compares the source address with a list of source
addresses
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
associated with the destination address to determine whether the source
address is an
authorized source address. If so, the computer stores the message at the
location in
the ISP database corresponding to the mail box associated with the destination
address, i.e., the intended recipient's mail box. If not, the computer either
causes the
message to be discarded or charges a fee to the sending party associated with
the
source address and stores the message in the intended recipient's mail box.
As stated above, the present invention can be used with all types of networks,
including private networks, such as local area networks (LANs) and wide area
networks (WAN s). The present invention is also not limited with respect to
the
location at which the method and/or apparatus are located in the
communications
network. Preferably, the present invention is implemented at the intended
receiving
party's ISP. Alternatively, the present invention could be implemented at, for
example,
routers of the network or at the sending party's ISP.
Preferably, the communications protocol that is used with the present
invention
t> is TCP/IP. When using TCP/IP, the destination address of the intended
receiving party
and the source address the sending panty are contained in the IP message, or
datagram.
However, many other types of communications protocols also transmit an
indication of
the source of the message to the intended recipient. including communications
protocols that do and do not comply with the Open Systems Interconnect (OSI)
tea model. Other types of public and private communications protocols can also
be used
with the present invention, including proprietary protocols, as will be
understood by
those skilled in the art.
All or a portion of any fee charged may be paid to the intended receiving
party.
A portion of the fee may be applied, for example, to the intended receiving
party's ISP
2, service account to reduce the intended receiving party's ISP service bill.
Preferably,
the service provided by the present invention is optional and can be enabled
or disabled
at the receiving party's ISP depending on whether the receiving party has
subscribed to
the service.
Fig. l2 illustrates the method of the present invention in accordance with a
>c> preferred embodiment wherein a determination is made as to whether an e-
mail
18
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
message has originated from an authorized e-mail source address. The computer
at the
ISP decodes the datagram and obtains the source and destination addresses, as
indicated at block 131. The computer then compares the source address with a
list of
source addresses associated with the destination address and makes a
determination as
to whether the source address is on a list of authorized source addresses, as
indicated
at blocks 133 and 135. Thus, the destination address is used to determine
which list is
associated with the intended receiving party.
If a determination is made that the source address is on the list of
authorized e
mail addresses, then the e-mail message is saved in a location in a database
associated
m with the e-mail address of the receiving party so that the receiving party
can access the
e-mail message, as indicated at block 137. In this case, a fee is not charged
to the
sending party. If the sending party's e-mail address is not on the list of
authorized e-
mail addresses, then a determination is made as to whether the sending party
has
authorized the ISP to bill it for these types of fees, as indicated at block
138. If not,
1 ~ the sending party is notified by an e-mail message that it has not
authorized fee billing,
as indicated at block 141. 1t should be noted that the steps illustrated at
blocks 138
and 141 are optional. Alternatively, the process could proceed directly from
decision
block 135 to either block 137 or 141, depending on the results of the
comparison.
If the sending party has authorized billing for the fees, then the fee is
charged to
2o the sending party's billing account and the e-mail message is saved in the
receiving
party's mailbox, as indicated at block 139. The sending party's billing
account is then
updated, as indicated at block 14 3. The percentage of the fee to be added to
the
receiving party's billing account is then calculated, as indicated at block
145. The
receiving party's billing account is then update, as indicated at block 147.
2, The order in which the steps corresponding to blocks 137 through 147 are
performed is not limited to any particular order. It will be understood by
those skilled
in the art that the order of these steps can be rearranged and performed in
any suitable
order. It should also be noted that steps 143, 145 and l47 are also optional.
Rather
than updating the sending party's account, as presented by block 143, the
sending
3o party could simply be sent a bill. The steps represented by blocks 145 and
147 could
19
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
be eliminated altogether, since the present invention is not limited with
respect to the
manner in which the fees are allocated.
As stated above, rather than comparing the sending party's email address to a
list of authorized email addresses, an identifier identifying the nature of
the
s communication could be appended to or included in the message. For example,
parties
that solicit business over the Internet could be required by law to identify
messages
that are sent for the purpose of soliciting business with a particular
identifier. The
receiving party's ISP would then simply determine whether the receiving party
has
authorized these types of communications. If not, the ISP could simply block
the
m transmission, e.g., not save it the intended receiving party's mailbox, or
could charge
the sending party a fee in return for providing the communication to the
intended
recipient. Those skilled in the art will understand the manner in which this
embodiment
could be accomplished.
It should also be noted that the step represented by block 14I in Fig. 12
could
to be utilized as a billing tool. For example, when the sending party is not
authorized, the
ISP could cause a message to be sent to the sending party that states that the
sending
party is not authorized, but that the communication will be provided to the
intended
recipient if the sending party agrees to pay a fee. The sending party could
then reply
by authorizing the fee to be charged or could decline to pay the fee. 'The
message sent
2c> by the could request that the party enter card number
ISP sending a credit of an
account which the fee will be The sending could then
to charged. party reply by
authorizingpayment to be made fromdesignated Alternatively,
the account. the
sending party could simply authorize the charge and make payment at a later
date.
It should be noted that the present invention has been described with respect
to
2s particular embodiments, but that the present invention is not limited to
these
embodiments. It will also be understood by those skilled in the art that the
manner in
which an unauthorized sending party is billed with a fee and the manner in
which the
billing account of the receiving party is updated is not limited to any
particular method.
Also, the location at which the billing of the fee and the updating of any
accounts is
;o performed is not limited to any particular location. The billing and
updating of
CA 02340260 2001-02-09
WO 00/10318 PCT/US99/18183
accounts for unauthorized e-mail addresses can be performed at the ISP
location or at
some other location in communication with the receiving party's ISP. It will
be
understood by those skilled in the art that other modifications and variations
to the
embodiments of the present invention discussed above; can be made which are in
the
s scope and spirit of the present invention.
21