Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
1
ROBUST METHOD AND APPARATUS FOR PROCESSING
CABLE MODEM CONFIGURATION FILES
FIELD OF THE INVENTION
The present invention is related generally to cable modems, and more
specifically to a method and apparatus for robust processing of cable modem
configuration files where the file is formatted as simple network management
protocol (SNMP) objects.
1 o BACKGROUND OF THE INVENTION
Internet access via a telephone modem is available today at speeds up to 56
Kbps. The telephone-based modem modulates and demodulates data signals for
transmission over the voice band telephony network. By contrast, a cable modem
provides Internet access via the cable television system, which offers a
higher bandwidth
15 and therefore operates at higher data rates than the telephone system. The
cable modem
provides connectivity between the user's computer or other communications
device and
the cable system headend, from which access is available to the Internet or
other external
network, via, for example Tl transmission line. In a cable network, data
transmitted
from the network headend to the user or subscriber is referred to as
downstream data;
2 o data transmitted from the user to the network headend is referred to as
upstream data.
An exemplary prior art two-way cable system is illustrated in block diagram
form in FIG. 1. The prior art cable system includes headend equipment 101, a
hybrid
fiber coaxial (HFC) cable plant 103, a plurality of cable modems 105 and 106
(only
two shown), and a corresponding plurality of subscriber communications devices
107
a5 and 108 (only two shown) coupled to the cable modems 105 and 106 via
corresponding communications links 116 and 117. Exemplary communications
devices 107 and 108 include a computer, a television or a telephone. As is
well
known in the are, the headend equipment 101 includes processors, routers,
switches, a
broadband downstream transmitter, upstream receivers, splitters, combiners,
3 o subscriber databases, network management stations, dynamic host
configuration
protocol (DHCP) servers and trivial file transfer protocol (TFTP) servers,
call agents,
media gateways, and billing systems . The HFC cable plant 103 includes fiber
optic
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
2
cables, coaxial cables, fiber/coax nodes, amplifiers, filters and taps, which
support
transmissions from the headend equipment 101 to the cable modems 105 and 106
over
a shared downstream channel 110 and transmissions from the cable modems 105
and
106 to the headend equipment 101 over a shared upstream channel 112. Program
s signals are input to the headend equipment 101 as shown for broadcast to the
cable
subscribers, as discussed hereinbelow.
Each channel 110 and 112 may utilize a different transmission protocol to
communicate information. Typically, the modulation used to convey information
over
the downstream channel 110 (e.g., 64-ary quadrature amplitude modulation
(QAM)) is
of a higher order than the modulation used to convey information over the
upstream
channel 112 (e.g., differential quaternary phase shift keying (DQPSI~) or 16-
ary
QAM), resulting in higher speed downstream transmissions than upstream
transmissions. Cable systems in which upstream transmission speeds are less
than
downstream transmission speeds are typically referred to as "asymmetric"
systems.
Cable systems in which upstream transmission speeds are substantially
equivalent to
downstream transmission speeds are typically referred to as "symmetric"
systems.
In addition to the particular type of modulation used on each channel 110 and
112, the shared nature of each channel 110 and 112 introduces other protocol
requirements. For example, since the downstream channel 110 is shared, the
ao downstream protocol includes address information and each cable modem 105
and
106 monitors the downstream channel 110 for information packets addressed to
it.
Only information packets addressed to a particular cable modem 105 or 106 (or
the
attached communications devices 107 or 108) or addressed to all (i.e.,
broadcast
messages) cable modems 105 or 106 (or the attached communications devices 107
or
108) are processed by the cable modems 105 and 106 and forwarded to the
associated
subscriber communications device 107 and 108 as appropriate. Since the
upstream
channel 112 is shared, the upstream channel access protocol is designed to
reduce the
likelihood of collisions of communicated information emanating from the cable
modems 105 and 106. A number of multiple access protocols exist to define
upstream
3 o channel access, including well-known protocols such as ALOHA, slotted-
ALOHA,
code division multiple access (CDMA), time division multiple access (TDMA),
TDMA-with collision detect, and caxrier sense multiple access (CSMA).
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
3
Some two-way cable systems abide by and use the upstream and downstream
channel protocols defined in the recently published standard entitled, Data-
Over-Cable
System Interface Specification (DOCSIS) Version 1Ø The upstream protocol
defined
by the DOCSIS standard is a TDMA approach where timing is controlled by the
s headend equipment 101 (referred to as the "cable modem termination station"
(CMTS) in the DOCSIS standard) and communicated to the cable modems 105, 106
via time stamp synchronization messages transmitted over the downstream
channel
110. Thus, for upstream communication to occur in an orderly, high quality
manner, a
time reference in each cable modem 105 and 106 must be substantially
synchronized
to with a similar time reference in the headend equipment 101, before the
modems 105
and 106 begin transmitting information provided by the subscriber
communication
devices 107 and 108. Absent proper synchronization, a transmission from one
modem
105 may collide with a transmission from another modem 106.
The headend equipment 101 is typically coupled via an appropriate
15 communication link 119, such as a fiber-distributed data interface (FDDI)
link or a
100 baser Ethernet link, to an external network 114, such as the public
switched
telephone network (PSTI~ or a wide area packetized network, such as the
Internet.
Thus, the two-way cable system provides communication connectivity between the
subscriber communication devices 107 and 108 (and other similar devices not
shown
z o in Figure 1 ), and Internet servers, computer networks, and so forth on
the external
network 114.
Figure 2 is a block diagram of the cable components at a user or subscriber
site, including the cable modem 105. At the subscriber's premises, a splitter
I34
splits the incoming signal so that a program signal is displayed on a
television 140
under control of a set top box 138. The second output terminal from the
splitter 134
provides connectivity to the cable modem 105. Downstream signals from the HFC
cable plant 103 are supplied to an RF (Radio Frequency) turner 142, which is
tuned to
a frequency allocated to the cable modem 105 during the modem's start-up
phase.
The downstream signal is demodulated in a demodulator 144 and the output
therefrom
3 o is input to a media access controller 26. The signal from the media access
controller
146 is input to a data and control logic unit 148 that controls overall
operation of the
cable modem 1 OS and further provides data contz-ol and collection functions.
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
4
The communication device 108 is connected to the data and control logic unit
148 of the cable modem 105 for receiving data sent in the downstream direction
from
the HFC cable plant 103 and for transmitting data in the upstream direction,
typically
with an ultimate destination of the external network 114. The outgoing data
from the
communication device 108 passes through the data and control logic unit 28,
through
the media access controller 26 and finally is modulated by a modulator 150.
The
upstream data then passes through the splitter 134 for transmission to the HFC
cable
plant 103.
Returning to Figure I, the headend equipment 10I also receives program
1 o signals (via satellite downlink, terrestrial microwaves or landlines) for
broadcast to the
communication devices 107 and 108 via the cable modem lOS and 106,
respectively.
The program signals are carried over a 6 MHz segment of the downstream channel
110, which is the spectrum bandwidth allocated to a cable television channel
for the
broadcast of program signals to all subscribers. (The International spectral
bandwidth
is 8 MHz.) At the subscriber's location, the program signal is received by the
set top
box 138, while the downstream data is separately received by the cable modem l
OS or
106. The number of upstream and downstream data channels in a given cable
modem
system is engineered based on the service area, the number of users, the data
rate
allocated to each user and the available spectrum.
a o When the cable modem 1 OS or 106 is powered up, a connection is created to
the headend equipment 101 using the Internet protocol (IP) so that IP-
formatted data
from the external network 114 can be forwarded downstream to the cable modem l
OS
or 106. After power-up, the cable modems l OS and 106 receive a channel
assignment
from the headend equipment 101. The cable modems 105 and 106 also contact a
dynamic host configuration protocol (DHCP) sever to download the name of the
modem conf guration file. Using this configuration file name, the cable modems
I OS
and 106 contact the appropriate trivial file transfer protocol (TFTP) server
where the
configuration file is stored. Finally, the configuration file is downloaded
from the
TFTP server to the cable modems lOS and 106. Information in the configuration
file
3 o allows the cable modems l OS and 106 to identify the applicable cable
modem
operating software and the location from which that operating software can be
downloaded to the cable modems lOS and 106.
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
A network manager executes network management functions that monitor and
control the various network elements. Exemplary network elements include, the
cable
modems 105 and 106, hosts, gateways, terminals and servers. Each network
element
includes a management agent for performing the network management functions as
s requested by the network manager. The SNMP (simple network management
protocol) protocol is used to communicate the network management information
between the network management station and the agents within each network
element.
The SNMP protocol defines the scope of management information, the format for
representing that management information, the operations amenable to
management
1 o control and, the format and interpretation of data exchanges between the
management
entities, i.e., the network management station and the management agents. The
cable
modems 105 and 106 can be configured to block access by non-authorized
management stations.
According to the SNMP protocol, the network management information is
represented in the ASN.1 language (Abstract Syntax Notation, Version 1). The
SNMP protocol defines the various network management operations as alterations
to
or inspections of variables in a TLV (type-length-value) data string that is
stored
within each network device agent. Thus the network agent of a hardware device
using
the SNMP protocol interacts with the management station to retrieve (get) or
alter
(set) variables in the data string. Use of the TLV format limits the number of
management functions that can be implemented by the management station to two:
one operation assigns a value to a specified configuration or parameter data
string and
the other operation retrieves a value. The configurations or parameters that
can be
managed by the network manager are set forth in a management information base
z s (MIB) within each network device agent.
The simple network management protocol is the most common protocol used
by network management software applications to query or control a network
agent. A
network agent is software that executes on network devices, such as a work
station or
a muter, and has the ability to gather information about device operation,
which in
3 o turn can be retrieved by the network management station. The network
management
station gathers and stores this data. Both the network manager and the network
agent
execute network management software that enables data interchange between the
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
6
network manager and the controlled network agents. Also, the network
management
station runs network management software that enables it to perform network
management functions, as is well known to those skilled in the art. The
Internet
protocol version of SNMP is used by most network management software
s applications. The SNMP protocol operates on top of the Internet protocol.
The management information base (MIB) describes the data that is retrievable
or modifiable over a network by a network management station. Through the
management information base, the network management station knows what
information the network agent has and the aspects of the device that are
controllable.
io The control functions executed by the network manager include those related
to the
device's interaction with the network and operation of the device itself.
The management information base on the network agent is a repository of
characters that identify certain operational parameters of the network device,
such as a
network interface card, hub, switch or router. By modifying these parameters,
the
15 network manager controls the network device. In addition to controlling the
network
device with which it is associated, the network agent gathers statistics and
responds to
queries from the network manager in a manner specified by the applicable
protocol.
As mentioned above, a DOCSIS certificated cable modem is configured by
downloading a configuration file from a TFTP server. The configuration file
can
2 o include parameters formatted as SNMP type-length value words. The type
field of the
type-length-value format is a single byte identifier defining the
configuration
parameter set forth in the value field. The length field is also a single byte
field
identifying the length of the immediately subsequently value field. The value
field
can range from one to 254 bytes and contains the specific values of the
configuration
25 parameter. The cable modems 105 and 106 must process all the SNMP TLV's in
the
file, but ignore improperly formatted or unknown TLV's. Once an error in a
file type
is detected, no further TLV's of that type are processed. Therefore, a need
exists for
more efficient processing of the TLV's, allowing the corrupted or unknown
TLV's to
be ignored, while allowing processing of the valid TLV's.
3 o The cable modems 1 OS and 106 each include a network management agent
and its associated MIB's. The DOCSIS specification identifies those MIB's that
must
be supported by the network management agent of the cable modem. Each MIB
refers
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
7
to one or more attributes or features of the device, where each such attribute
or feature
is designated by an object identifier, also referred to as an OID. Each OID is
a multi-
digit number with the digits separated by periods. For example,
1.3.5.7.8.10.12.3 is
an OID. The OID's for configurable or settable device attributes also are
associated
s with a value for that attribute, e.g., speed, time, temperature. Non-
configurable device
attributes simply provide information and thus the OID is not associated with
a
configurable element.
One technique for configuring the cable modem places the OID in the
configuration file and requires the cable modem to treat the OID's as if they
were
1 o being set by a .network management station. As an example, there are
certain OID's
that determine which network managers are allowed access to a cable modem.
Someone familiar with the detailed operation of a cable modem could power
cycle the
modem and thereby enable several features (by setting certain objects via the
object
identifiers) and then further set other objects to block access to the cable
modem by
15 other network managers. With access blocked, the obj ects cannot be read or
reset by a
network management station associated with the cable system. To prevent such
an
occurrence, appropriate information is contained in the configuration file
that sets the
security features when the cable modem is powered up. Once the security
features are
set, only network management stations as identified in the security settings
can access
20 and write or set the cable modem objects. In this way, the cable system
operator
ensures that only qualified network management stations can access the cable
modem
network agent.
BRIEF DESCRIPTION OF THE DRAWINGS
25 The present invention can be more easily understood and the further
advantages and uses thereof more readily apparent when considered in view of
the
description of the preferred embodiments and the following figures in which:
Figures l and 2 are electrical block diagram of a typical prior-art two-way
cable communications system;
3 o Figure 2 illustrates a data packet unit in accordance with the teachings
of the
present invention; and
Figure 3 is a process flow chart implementing the teachings of the present
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
8
invention.
DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS
Before describing in detail the particular method and apparatus for processing
s the simple management protocol-type-length-value words in accordance with
the
present invention, it should be observed that the present invention resides
primarily in
a novel combination of steps and apparatus elements. Accordingly the hardware
components and the method steps have been represented by conventional elements
in
the drawings, showing only those specific details that are pertinent to the
present
to invention so as not to obscure the disclosure with structural details that
will be readily
apparent to those skilled in the art having the benefit of the description
herein.
Under the SNMP standard, each object identifier is a numeric value that
represents some aspect or feature of a managed device, such as the cable
modems lOS
and 106. Object identifiers (or OID's) are used to identify a particular
object or a
s5 column in a table, and each consists of a series of numbers. The MIB
defines the
series of numbers such .that both the network agent and the network management
station are able to interpret the numbers.
Upon receipt of the configuration file at modem start-up, the modems l OS and
106 receive a plurality of TLV's for processing. The cable modems lOS and 106
2 o segregate the TLV words into a plurality of packet-data units based on the
type field.
The OID's represent one type of the TLV words, and thus all OID's are grouped
into
one packet data unit for processing. The OID number strings are the values in
the
TLV format. A prior art SNMP agent, according to the applicable standards, for
processing TLV's, processes all the OID's as a single group until an error is
detected.
25 Once an error is detected, no further OID's in the packet data unit are
processed.
Failure to process the erred and the remaining OID's can create configuration
errors or
limit the ability of the network manager to control and monitor the network
agent.
In accordance with the teachings of the present invention, in the cable modems
lOS and 106, the Oll~'s are first sorted by lexicographical ordering by the
network
3 o agent. That is, based on the number of digits in the OID. For example, all
six digit
OID's are grouped together; all seven digit OID's are grouped together, etc.
In
addition to or in lieu of the lexicographical ordering, the OID's are sorted
into scalar
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
9
(i.e., a single object value) and tabular object values. A tabular object
value is one in
which multiple objects are contained within a single row. Rather than
processing all
the O)D's as a group, the present invention groups the OJD's into multiple
packet data
units. In one embodiment, all scalar values are packaged in a single packet
data unit
s and then processed. All tabular objects are also packaged into a single
packet data
unit for processing or all the O)D's for a single tabular row are grouped into
a packet
data unit. In another embodiment, all same-digit O)D's are packaged into a
single
packet data unit.
The following examples are intended to clarify the teachings of the present
so invention. Scalar values, which always terminate in a "0", such as the two
set forth
below, are grouped together.
1.3.6.1.2.1.1.4.0 sysContact
1.3.6.1.2.1.1.5.0 sysName
The O>D digits 1.3.6.1.2.1.1 identifies a systems group for a network agent.
Two
is objects are identified above, one identified by the ".4" digit and the
other object
identified by the ".5" digit. Both obj ect identifiers terminate with a zero,
indicating
that they are scaler values. According to the definitions for these objects,
both provide
read/write access by the network management station. The "sysContact" object
is the
textual identification of the contact person for this managed node, together
with
zo information on how to contact that person. The "sysName" object is an
administratively-assigned name for the managed node. By convention, this is
the
node's fully-qualified domain name.
The following three obj ects are tabular values taken from the same table and
are accordingly grouped together. The final (7) indicates that these objects
are from
25 the seventh row in the table. The penultimate digits (2, 3 and 4) identify
the second,
third, and fourth columns of the seventh row. Tabular OID's never end in a
zero;
instead, they terminate with the row number. Note further that according to
the
present invention, these objects are segregated from the two objects set forth
above
due to the different number of digits in the OJD.
3 0 1.3.6.1.2.1.1.9.1.2.7 sysORm
1.3.6.1.2.1.1.9.1.3.7 sysORDESCR
1.3.6.1.2.1.1.9.1.4.7 sysORUptimeNODE
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
The following three objects are also grouped together and because they are
located in
the fifteenth row of the table, identifying columns two, three and four.
1.3.6.1.2.1.2.2.1.2.15 ifDEFCR
1.3.6.1.2.1.2.2.1.3.15 ifTYPE
s 1.3.6.1.2.1.2.2.1.4.15 ifMTU
As explained above, objects that are defined in the same MIB share all the
same OID digits up to the point where unique OID's axe needed to identify a
different
obj ect as defined by the MIB.
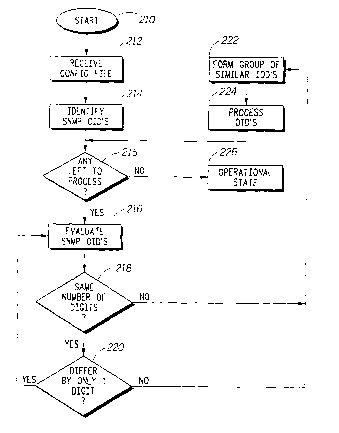
Figure 4 illustrates the process for processing the obj ects in accordance
with
Z o the teachings of the present invention. Figure 4 begins at start step 210
and proceeds
to a step 212 where the configuration file is received by the cable modem 105
or 106.
Although the configuration file is used as an example to which the teachings
of the
present invention can be applied, those skilled in the art recognize that the
teachings
can be applied to any network management file that employs TLV and SNMP
parameters in OID form. At a step 214 the SNMP objects within the
configuration
file are identified. Recall that the configuration file includes multiple
parameters for
setting up and configuring the cable modem; many of the these parameters are
not
related to the network management aspects associated with the SNMP protocol.
At a
decision step 215, a determination is made whether there are any OID's left to
2 o process. If there are none, processing moves to an operational state 226.
If there are O~'s remaining to be processed, processing moves to a step 216
where OID's are evaluated. Essentially, the OID's are segregated into groups
having
the same number of digits and differing by only one digit value from other
OID's in
the group. To implement this grouping arrangement, at the step 216, the number
of
~ 5 digits in the OID is counted. Processing then moves to a decision step 218
for
comparing the number of digits in the currently processed OID with the number
of
digits in the most previous OID. For the first pass through the decision step
218, the
result is affirmative, since there is no previous value for comparison. With
an
affirmative answer from the decision step 218, processing moves to a decision
step
3 0 220 for comparing the individual digit values of each OID. Recall that alI
OID's for a
given object differ by only one digit. For the first pass through the decision
step 220,
the answer is affirmative and processing then returns to the step 216 to
retrieve and
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
22
evaluate the next OID. Now processing moves to the decision step 218 for
evaluating
the next OID. If the first and second OID's have the same number of digits,
then the
result from the decision step 218 is affirmative and processing moves to the
decision
step 220. Here, the individual digits of the OID's are examined and if they
differ by
s only one digit value, processing returns to the step 216. In this way, as
the steps 216,
218, and 220 are executed, a group of similar (defined as having the same
number of
digits and differing by only one digit value) is formed. This group is closed
(see a
step 222) when either of the decision steps 218 or 220 generates a negative
response.
Once a group of similar OID's is formed, referred to as a packet data unit,
they are
1 o processed at a step 224. As discussed above, the group is referred to as a
packet data
unit. Processing of the 0117's involves determining whether there are any
errors or
corrupted bits and setting the object to which the OID refers to the value
associated
with the OID. Further, in accordance with the teachings of the present
invention, all
scaler OlD's are separated from tabular OID's and tabular OID's from the same
table
15 now are grouped together into one packet data unit.
Thus, in accordance with the teachings of the present invention, individual
corrupted or unreadable objects within a packet data unit do not cause all
OTD's in the
configuration file to be ignored. Instead, since each packet data unit
includes only
related OID's, if a single OID within the packet is corrupted, and therefore
the whole
packet is discarded, OID's in other packets are not affected and can therefore
be
operative to establish or set device features or aspects. This technique
ensures
maximum use of the various SNMP objects and therefore, provides maximum
network manageability via the network/manager agent relationship. In the prior
art
multiple objects in a packet data unit are ignored when only a single object
is
~5 corrupted or unreadable, thus limiting the network management
functionality.
While the invention has been described with reference to a preferred
embodiment, it will be understood by those skilled in the art that various
changes may
be made and equivalent elements may be substituted for elements thereof
without
departing from the scope of the present invention. In addition, modifications
may be
3 o made to adapt a particular situation more material to the teachings of the
present
invention without departing from the essential scope thereof. Therefore, it is
intended
that the invention not be limited to the particular embodiment disclosed as
the best
CA 02428464 2003-05-09
WO 02/42882 PCT/USO1/47184
12
mode contemplated for carrying out this invention, but that this invention
will include
all embodiments falling within the scope of the appended claims.