Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
DEVICES AND METHODS FOR TRACKING, LOCATING AND PROVIDING
PROTECTION TO INDIVIDUALS
BACKGROUND OF THE INVENTION
[0001] Methods are needed to further protect individuals from becoming lost or
abducted, and to track and locate children who are lost or abducted.
SUMMARY OF THE INVENTION
[0002] In one aspect are methods for tracking and locating an individual, and
for
providing protection to such an individual. In another aspect are devices for
tracking and
locating an individual, and for providing protection to such an individual. In
certain
embodiments, the methods and devices incorporate a tag. In further
embodiments, the
tag is an RFID tag. In further embodiments, the tag includes a microchip
connected to an
antenna. In further embodiments, the methods and devices incorporate an RFID
reader.
In further embodiments, the methods and devices incorporate a device for data
processing. In further embodiments, the tag is incorporated into clothing. In
further
embodiments the methods and devices are used to track, locate, and/or provide
protection
to children, the elderly, the injured, the sick and other individuals in need
of protection.
BRIEF DESCRIPTION OF THE DRAWINGS
[0003] A better understanding of the features and advantages of the present
invention
will be obtained by reference to the following detailed description that sets
forth
illustrative embodiments, in which the principles of the invention are
utilized, and the
accompanying drawings of which:
[0004] FIG. 1 provides one embodiment of the devices and methods described
herein for
tracking, locating, and/or providing protection to individuals.
[0005] FIG. 2 provides non-limiting illustrative embodiments of Unique Smart
Tags
with embedded microchips.
[0006] FIG. 3 provides non-limiting illustrative embodiments of apparel
incorporating
the RFID tags described herein.
[0007] FIG. 4 provides non-limiting illustrative embodiments of apparel
incorporating
the RFID tags described herein.
[0008] FIG. 5 provides a non-limiting illustrative embodiment of a method for
obtaining
subscribers for a subscriber network described herein.
[0009] FIG. 6 provides a non-liiniting illustrative embodiment of a subscriber
network
described herein.
-1-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
C0'01-0] FIG. 7-provitleg a non-limiting illustrative embodiment of the use of
the RFID
tags described herein.
[0011] FIG. 8 provides a non-limiting illustrative embodiment of the use of
the RFID
tags described herein.
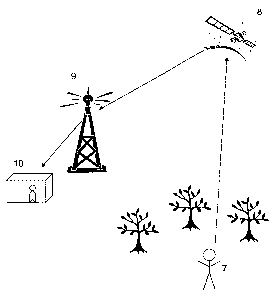
[0012] FIG. 9 provides a non-limiting illustrative embodiment of the use of
the RFID
tags described herein.
DETAILED DESCRIPTION OF THE INVENTION
Overview of RFID Technology
[0013] Inside an RFID tag is a microchip connected to an antenna. The
microchip can
store modest amounts of information, up to about 2k bits. RFID tags are often
used to
store a simple identification number. In more sophisticated systems the tag
can function
as a portable traveling database for the item to which it is attaclied. Tags
come in a
variety of form factors and can be attached to basically anything
[0014] An RFID Reader controls the wireless reading and writing of information
stored
on an RFID tag. The RFID reader generates an RF field around its antenna. The
RF field
energizes the tag and a means to transfer data to the reader. The tag
modulates the
reader's RF field and the reader can detect this. Similarly, the reader turns
the RF field on
and off in the right sequence in order to write the tag.
Circuit Components:
[0015] The tag is one component of the circuitry. The tag is basically an
integrated
circuit deposited on a small silicon chip that has an integrated small,
flexible antenna.
This composite circuit creates a tag which by design is capable of processing
a variety of
frequency ranges and may be passive or active. The passive RFID works by
magnetic
induction. The integrated circuit provides data storage to record and store
information.
[0016] The Reader: A reader sends a signal to the tag. The tag absorbs some of
the RF
energy from the reader signal and then reflects the RF energy as a return
radio signal
containing information from its memory. The reader device generates an
alternating
magnetic field from a coil of wire. A tag also has a coil of wire that induces
current from
the magnetic field. This current provides power to the passive tag. The tag
then sends
back its own varying magnetic field which is read by the reader device.
[0017] Data Processing: Once the data is received from the reader the signal
will be
processed to trigger an alarm alert device, this may be in the form of a
repeating audible
resonance, flashing light, or a similar alert type device.
-2-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
Mock Diagram of a typical RFID system. (Flow Chart)
Smart Tag sewn in children's night clothes>>>>>>>>>>Radio waves emitted from
tag , Received by Antenna and to Reader>>>>to Audible
sound or Device.
Signal >>>>>>
Child's >>>>>>> receive >>>>>>>>>> >>>>>>
Apparel by
with Antenna
Smart Signal from Alarm
to
Tag Sntarl Tag Process ir fo. or
sewn in to Reader Reader Sent to alarm Device
Application of RFID technology
Method foY Incorporating Iden.tifying Tag into Apparel
[0018] The devices and methods described herein utilize an RFID tag called a
Unique
Smart Tag configured as described herein and integrated into a wearable item.
[0019] In order for the Unique Smart Tag to be integrated into an item of
clothing, it
must be resistant to wear and tear from laundering, folding, and daily use of
the clothing
itself. It must be resistant to a certain amount of heat from sources such as
outdoor
teniperatures, body heat, and clothes dryers. It must be resistant to water
and chemicals
such as laundry detergent, chlorine, dry cleaning procedures, and the like.
[0020] The Unique Smart Tag is a microchip that is attached to a small,
flexible antenna
or antennae. The microchip is composed of an integrated circuit deposited on a
small
silicon chip. The critical component of the Unique Smart Tag is this microchip
since any
damage to its circuitry could render the device useless. However, the
microchip must be
attached to the antenna or antennae in order for the signal to reach the
microchip.
[0021] The antenna is attached to the microchip by means that are known in the
prior art.
The microchip portion of the Unique Smart Tag is embedded in a material that
is
impervious to physical abuse, heat, water, and chemical damage. FIG. 2
displays an
array of Unique Smart Tags with embedded microchips. The embedding "material"
may
be a resin or laminate. By way of example, the resin may be melamine resin,
epoxy
resin, polyurethane resin, polyurea elastomer resin, alkyl resin, casein, or
mixtures
thereof.
[0022] The method of manufacture for embedding the Unique Smart Tag in resin
or
laminate involves placing a predetermined amount of the resin or laminate on a
substrate,
allowing the resin or laminate to gel or soften and then placing the Unique
Smart Tag on
the resin or laminate with the microchip component centered on the resin or
laminate
drop. After placement of the Unique Smart Tag, another predetermined amount of
resin
-3-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
or Urh'friate'19 pladbd ot4 too 'o'f the microchip component before the first
gelled layer of
resin or laminate is allowed to fully cure. This method seals the microchip in
the resin or
laminate completely.
[0023] A Unique Smart Tag that is ruggedized and therefore protected from
physical
abuse, heat and chemical damage can be integrated into various wearable items.
Practically every wearable item is capable of having a Unique Smart Tag
integrated into
it during manufacture. Outerwear, sleepwear, clothing, underwear, and even
footwear
and accessories have locations where a Unique Smart Tag may be attached or
carried.
[0024] Although the Unique Smart Tag may be attached to virtually any surface
via an
adhesive backing or other means of attachment, the preferred embodiment for
attaching it
to an individual's clothing is one in which the Unique Smart Tag is
"incorporated" into a
"concealed area" and therefore hidden from plain sight while the individual is
wearing
the clothing. In this way, an abductor may not be aware of, and cannot remove
the
Unique Smart Tag from the individual. Additionally, hiding the Unique Smart
Tag
protects the tag from further wear and tear, therefore extending the life of
the tag.
Furthermore, concealment of the Unique Smart Tag protects the individual from
irritation, either from physical friction with the tag or conditions such as
allergies or
contact dermatitis.
[0025] A "wearable" item into or onto which the Unique Smart Tag may be
incorporated
comprises apparel, jewelry, accessories, patches, tags, or any other means by
which
something may be attached to or carried on an individual. In one embodiment,
the
wearable item can be "apparel" such as clothes, footwear, underwear,
outerwear,
sleepwear, and accessories. The wearable item comprises clothing patches,
zippers,
strings, collars, pockets, or any other item that can be sewn, ironed onto,
tied, or
otherwise attached to an item of apparel.
[0026] The Unique Smart Tag is small enough that it can be placed on fabric
and sewn
into a hem, waistband, collar or seam. In one embodiment, on outerwear such as
shown
in FIG. 3, the Unique Smart Tag is sewn into a collar as in A, a seam as in B,
or a
waistband as in C. In another embodiment such as the pair ofjeans shown in
FIG. 3, the
Unique Smart Tag is sewn into a waistband as in D or a side seam as in E. In
one
embodiment, the Unique Smart Tag is sewn into clothing when an elastic
waistband is
incorporated into the article. In another embodiment, the Unique Smart Tag is
sewn into
a pocket. In yet another embodiment, the Unique Smart Tag is part of the heel,
insole,
midsole, or upper portion of footwear as show in FIG. 4.
-4-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
[002,7] TlYd'6P6ratY'uiial'd69igf1 and use of SmartWear is specifically
designed for is
individual safety and security, anti-kidnapping circumstance and or similar
abduction
situations. The devices and methods described herein utilize a Unique Smart
Tag
(Transponder) configured as described herein and sewn the individual's
apparel.
[0028] The Unique Smart Tag may also be used for more temporary purposes. In
one
embodiment, it may be incorporated into a patch that has an adhesive to be
attached to a
person either by placing it directly on the slcin or by placing it on the
person's clothing.
A patch with a Unique Smart Tag may be used to attach information about a
patient
directly on his person. This may be useful particularly in triage during a
large event
where many people are injured, medical charts are not available, and patients
may be
moved frequently.
[0029] The Unique Smart Tag is incorporated into the patch by the existence of
two
layers. The first layer has an adhesive backing and the second layer is a
covering layer.
A resin-encapsulated or lanzinate-covered Unique Smart Tag is located between
these
two layers. In one embodiment, the Unique Smart Tag is manufactured using one
of the
layers as a substrate and the top layer is fused on top using an adhesive. The
layers may
be made of paper, fabric, foam, or other sheet-like material. In one
embodiment the
material may be naturally-derived, such as cotton. In another embodiment the
material
may by synthetic such as plastic. In another embodiment the layers are a
combination of
natural and synthetic materials. The adhesive is similar to those used on
medical
bandages, is skin-friendly, and readily removable.
Busitaess Method
[0030] A consumer purchases or otherwise acquires said RFID tag-enabled
product. At
this stage, the point-of-sale, the consumer has the option to enter a
subscription
agreement and activate said RFID tag. To activate the RFID tag, a unique code
is
programmed into the tag using an RFID tag encoding device and assigned to the
consumer, now subscriber. In another embodiment, the unique identification
code which
has been previously embedded on the RFID tag is read by an RFID tag reader and
given
to the consumer. This code is then entered into a subscriber network database
by the
retailer or consumer, along with identifying personal information of the
subscriber.
[0031] A "subscriber" is a primary purchaser or consumer of the RFID tagged
product as
well as the purchaser or consumer's family members such as the purchaser's
spouse,
children or dependents. In another embodiment, an RFID-tagged product may be
bought
as a gift for a third party and the RFID tag may be activated by the third
party, now
subscriber, at the retailer at a later time. In another embodiment, an RFID-
tagged product
-5-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
may b&"purcTl~f~ed'"ag'a-'gifC''lb-r a third party and the RFID tag unique
identification code is
provided for the third party, who is now the subscriber. The subscriber has
the option of
returning to the point-of-sale after the purchase of an RFID tag-enabled
product has been
made to subscribe to the network.
[0032] In one embodiment, the RFID tag has no information embedded in it. In
another
embodiment, the RFID tag is already programmed with an SKU number for the
purposes
of inventory tracking. This number is removed from the RFID tag at point of
sale. The
SKU number is overwritten with the subscriber code in the event the customer
subscribes
to the network.
[0033] The subscriber "network" is a secured computer network that contains a
database
of all unique identifiers assigned to the RFID tags and the accompanying
information
assigned to each code. A "unique identifier" is an entry within the database,
associated
with a subscriber's information. In one embodiment, each RFID tag-enabled
product
contains a unique identifier that is unique from all other RFID tag-enabled
products. In
another einbodiment, the unique identifier is used for any number of RFID tag-
enabled
products. In this embodiment, a unique identifier belonging to a subscriber is
unique
from all other subscribers and the subscriber keeps a record of his/her unique
identifier to
encode all the RFID tag-enabled products which the subscriber owns. The
subscriber
provides his/her code when the RFID tag is activated at the point-of-sale.
[0034] The subscriber has the option at any time to add additional relevant
information to
the database entry corresponding to said code. The subscriber has the option
at any time
to remove any or all information correlating to his/her code from the
database, thereby
ending his/her affiliation with the code. Removal of information from the
database
requires the subscriber to access to the database as an authorized user.
[0035] The quantity and content of the information a subscriber may add is
entirely at the
discretion of the subscriber. This information is likely to be at least one of
the following:
(1) name of the subscriber (and dependents), (2) date of birth, (3) address,
(4) telephone
number, (5) emergency contact information, (6) next of kin, (7) medical
conditions or
requirements, (8) social security number, (9) physical description, (10)
photograph, (11)
any other information the subscriber deems relevant.
[0036] In one embodiment, relevant subscriber information is provided at the
point of
sale by a means determined by the method of sale. In another embodiment,
relevant
subscriber information is provided post-sale by one or more of the following
methods: (1)
telephoning the network provider customer service, (2) via the internet, (3)
by mail, (4)
by speaking to a network representative in person.
-6-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
[0037] In one em'Uotiin'1'ent"tht subscriber can add or remove relevant
subscriber
information at any time through one or more of the following methods: (1)
telephoning
the network provider customer service, (2) via the internet, (3) by mail, (4)
by speaking to
a network representative in person.
[0038] Access to the subscriber network will be highly secured and limited
only to
authorized persons. Access will be by a usemame and password system unique to
all
authorized persons and all access will be logged by username, date, time and
information
accessed.
[0039] The subscriber will have access to personal information only as
pertains to the
subscriber's own subscription. The subscriber maintains control over access
privileges to
each individual item of the subscriber's information within the network.
[0040] Full access will be available only to "authorized persons" defined as
(1) certain
employees of the network provider company and their affiliates, (2) emergency
services
personnel such as fire, police, ambulance, emergency medical personnel,
physicians,
Coast Guard, and National Guard, (3) other authorized personnel as required on
a case by
case basis and authorized by subscriber.
[0041] Authorized users will be able to access and view the subscriber's
information
using the code assigned to the RFID tag. The code assigned to the RFID tag can
be
associated with identifying information in the network via (1) telephone, (2)
internet, (3)
by speaking to a network representative, or (4) other secure means of routing
information
from a network in a fast and reliable manner.
Subscriber Network
[0042] In one embodiment as shown in FIG. 5, a retailer offers for sale an
RFID tag-
enabled product. In one embodiment, the product is sold in a retail
establishment or store.
In another embodiment, the product is sold through a website or via the
internet. In
another embodiment the product is sold through a catalogue and mail order
process.
[0043] A consumer purchases or otherwise acquires said RFID tag-enabled
product. At
this stage, the point-of-sale, the consumer has the option to enter a
subscription
agreement and activate said RFID tag. To activate the RFID tag, a unique code
is
programmed into the tag using an RFID tag encoding device and assigned to the
consumer, now subscriber. In another embodiment, the unique identirication
code which
has been previously embedded on the RFID tag is read by an RFID tag reader and
given
to the consumer. This code is then entered into a subscriber network database
by the
retailer or consumer, along with identifying personal information of the
subscriber.
-7-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
[004-4] A MbScrYlYet" As a"prYYnary purchaser or consumer of the RFID tagged
product as
well as the purchaser or consumer's family members such as the purchaser's
spouse,
children or dependents. In another embodiment, an RFID-tagged product may be
bought
as a gift for a third party and the RFID tag may be activated by the third
party, now
subscriber, at the retailer at a later time. In another embodiment, an RFID-
tagged product
may be purchased as a gift for a third party and the RFID tag unique
identification code is
provided for the third party, who is now the subscriber. The subscriber has
the option of
returning to the point-of-sale after the purchase of an RFID tag-enabled
product has been
made to subscribe to the network.
[0045] In one embodiment, the RFID tag has no information einbedded in it. In
another
embodiment, the RFID tag is already programmed with an SKU number for the
purposes
of inventory tracking. This number is removed from the RFID tag at point of
sale. The
SKU number is overwritten with the subscriber code in the event the customer
subscribes
to the network.
[0046] An RFID Tag Reader controls the wireless reading and writing of
information
stored on an RFID tag. The RFID reader generates an RF field around its
antenna. The
RF field energizes the tag and a means to transfer data to the reader. The tag
modulates
the reader's RF field and the reader can detect this. Similarly, the reader
turns the RF
field on and off in the right sequence in order to write the tag.
[0047] The subscriber "network" is a secured computer network that contains a
database
of all unique identifiers assigned to the RFID tags and the accompanying
information
assigned to each code. A "unique identifier" is an entry within the database,
associated
with a subscriber's information. In one embodiment, each RFID tag-enabled
product
contains a unique identifier that is unique from all other RFID tag-enabled
products. In
another embodiment, the unique identifier is used for any number of RFID tag-
enabled
products. In this embodiment, a unique identifier belonging to a subscriber is
unique
from all other subscribers and the subscriber keeps a record of his/her unique
identifier to
encode all the RFID tag-enabled products which the subscriber owns. The
subscriber
provides his/her code when the RFID tag is activated at the point-of-sale.
[0048] The subscriber has the option at any time to add additional relevant
information to
the database entry corresponding to said code. The subscriber has the option
at any time
to remove any or all information correlating to his/her code from the
database, thereby
ending his/her affiliation with the code. Removal of information from the
database
requires the subscriber to access to the database as an authorized user.
-8-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
[0'049] This',qu'antPty; athd ewYtent of the information a subscriber may add
or remove is
entirely at the discretion of the subscriber. FIG. 6 outlines possible
discrete information
fields that a subscriber may want to add content to. These fields all linlc to
the main
subscriber profile and consist of sub-fields of information that fall under
the unbrella of
the parent field. These fields are descibed fitrther below.
[0050] In one embodiment, the medication profile field contain the following
set of sub-
fields for each medication being taken. Name of Medication; Condition being
treated;
Strength; Units; Form (Liquid, Pill, etc); Frequency; Duration; Directions;
Start Date;
Currently Taking (Yes/No); Prescribing Doctor.
[0051] In one embodiment, the Doctor/Hospital Profile field contains the
following set of
sub-fields for each of the subscriber's doctors: First Name; Last Name; Title;
Clinic or
Hospital; Address 1; Address 2; City; State; Postal Code; Office Phone; Mobile
Phone;
Home Phone; Email.
[0052] In one embodiment the Allergy Profile field contains the following set
of sub-
fields for each allergy indicated: Allergic to; Allergic Reaction; Other
Reaction;
Treatment; Doctor;
[0053] In one emboidment, the condition/illness profile field contains the
following sub-
fields for each set of condition/illness: Condition or illness; Active(active,
inactive,
resolved); Date of onset; Date of diagnosis; Date of resolution; Method of
treatment;
Doctor;
[0054] In one embodiment, the immunizations profile contains the following set
of sub-
fields for each immunization performed: Immunized for; Date of immunization;
Doctor;
[0055] In one embodiment, the family member profile field contains the
following set of
sub-fields for each family member listed: Prefix; First Name; Last Name;
Suffix; Date of
birth; Gender; Race; Primary Language; Height; Weight; Eye color; Blood type;
Photo 1
(Head Shot); Photo 2 (Profile); Instructions in event of emergency; Medical
Authorization; Medical Authorization digital signature; Smartwear Digital ID;
Date
Added; User ID; Subscriber ID.
[0056] In one embodiment the emergency contact profile field contains the
following set
of subfields for each contact listed: Prefix; First Name; Last Name; Address
1; Address 2;
City; State; Postal Code; Relationship; Day phone; Evening phone; Mobile
phone; Email
address
[0057] In one embodiment the surgery & procedures profile field contains the
following
set of subfields for each surgery or procedure: Procedure; Date; Result;
Doctor;
-9-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
C~0'058] 1'mone embotYirderlt,'tPle subscriber profile field contains the
following sub-fields:
User name; Password; First name; Last name; Email; Work phone; Mobile phone;
Important information; Date joined; Status; Billing code.
[0059] In one embodiment the biometric profile field contains the following
sub-fields:
Finger print scans; Iris Scan; DNA profile;
[0060] In one embodiment, each field has a number of sub-fields common to each
field,
these include: Comments; Date updated; User ID; Access level where access
levels
allows subscribers to predetermine who will be able to access each discrete
field. For
example, a subscriber could allow a school or similar agency to access only
the contact
information, allow doctors and hospitals to access medications and allergies
and allow
law enforcement agencies to access eveiy field.
[0061] In one embodiment, each information field is stored on a separate
server in
separate locations to facilitate greater security, faster access, improved
reliability and
flexibility in data control and access.
[0062] Full automatic and unrestricted access will be available only to
certain individuals
as indicated in the subscription agreement and may include (1) certain
employees of the
network provider company and their affiliates, (2) emergency services
personnel such as
fire, police, ambulance, emergency medical personnel and physicians, coast
guard,
National Guard, (3) other authorized personnel as required on a case by case
basis and
authorized by subscriber.
[0063] Authorized personnel will be assigned a usemame and password that will
allow
them access to the network at their access level (doctor, school, law
enforcement etc) and
will be able to access and view the subscriber's information using the code
assigned to
the RFID tag(s). The code assigned to the RFID tag can be associated with
identifying
information in the network via one or more of the following (1) telephone, (2)
internet,
(3) by speaking to a network representative, or (4) other secure means of
routing
information from a network in a fast and reliable manner.
Early Warning Systein and Locator Device
[0064] Also described herein is a method for the tracking of individuals as
they enter and
exit a certain predefined area. In effect, this embodiment creates an
invisible electronic
fence around a home or building such that when an individual comes in close
proximity
of an exit portal, an audible or visible alarm will be triggered. This
monitoring system is
useful to prevent the abduction of individuals from homes and schools, or the
departure
of a sleepwalker, mentally disabled, or elderly person from a house or
building. Such a
-10-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
rnonizarhig sysiem c'an be"Y'h~ifiluable in which only one or a few
individuals need to be
monitored such that the system is not triggered by pets, full-capacity adults,
or guests.
[0065] The illustration of FIG. 7 provides an overview of the components of
one
embodiment of the early warning system and locator device. In general, the
system of
the present enibodiment collects data from an RFID device attached to a child
1 via one
or more remote RFID readers which are located in a entryway or exit 2 and 4 or
a
window 3.
[0066] The predefined area is a locality such as a house, apartment,
condominium, or
other dwelling. The locality can be a building such as a day care facility or
school. In
anther embodiment, the locality comprises a geographic area such as a
neighborhood,
amusement park, nature preserve, campsite, sports arena, department store,
shopping
mall, ski resort, etc. The geographic area could be defined by sphere of
activity or
physical boundaries.
[0067] The monitoring system is small in size and can be integrated into a new
or
existing home alarm system. In this way, the system is unobtrusive, and cannot
be
tampered with easily. Furthermore, the system may be such that a home alarm
system is
installed with it concurrently, in the same areas of the home, and can be
turned on or off
with the same action. The alarm device is also adoptable with cell phone
technology.
[0068] The monitoring system of the present invention includes an RFID reader
which
controls the wireless reading and writing of information stored on an RFID
tag. The
RFID reader generates an RF field around its antenna. The RF field energizes
the tag and
a means to transfer data to the reader. The tag modulates the reader's RF
field and the
reader can detect this. Similarly, the reader turns the RF field on and off in
the right
sequence in order to write the tag.
[0069] The RFID tag is integrated into a child or individual's sleepwear,
apparel, or
footwear, or can be otherwise worn or carried on the person as a wristband,
bandage, or
accessory.
[0070] The RFID tag is activated by programming a unique code into the tag
using an
RFID reader. The unique code can be a simple alphanumerical code.
Alternatively, the
unique code can be identifying data such as a name, address, phone number, or
even a
photo.
[0071] RFID readers are embedded in certain strategic locations such as window
frames,
door frames, driveways, fences, or water sources. Water sources comprise
swimming
pools, spas, jacuzzis, hot tubs, water gardens, ponds, lakes, streams, or
rivers. FIG. 8 is
-11-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
ail illtistraribn-bf-one ernl7odYi'nent in which the RFID reader 5 is located
adjacent to a
door frame and the RFID device is attached to a child's clothing 6.
[0072] When an encoded RFID device passes in close proximity of an RFID
reader, the
system compares the stored ID with those stored in the system and triggers an
audible
and/or visible alarm if the ID matches any within the system. Alternatively,
in the event
the individual is physically moved outside a specified distance or range, as
defined by
specification, a detection notification in the form of an audible alarm or
flashing lights
will be activated. The alarm may be audible or visible either at the source of
the
triggering event, at another location such as a base station within the home
or a parent's
bedroom, or at multiple locations throughout the system. Since the system is
wireless,
once activated, deactivation by an intruder is virtually impossible.
[0073] In one embodiment, the identification tags are semi-passive devices. A
semi-
passive RFID tag is able to use an attached power source, but the power source
is not
continually transmitting information. An RFID reader is able to read and write
data to a
semi-passive RFID tag at a greater speed and distance than that of a passive
RFID tag.
[0074] It is one object of the methods and devices described herein to create
a small,
efficient sensor which is capable of detecting a specific encoded RFID device
when it
traverses a predefined area. In one application, this predefined area is an
entrance to a
house or residential building.
[0075] It is a further object of the methods and devices described herein to
provide
detailed information regarding the location of an individual, should the
individual leave
the predefined area and need to be tracked in a larger environment.
[0076] The devices and methods described herein provide a constant monitoring
system
that is wireless and able to be placed in an undetectable part of the
individual's apparel.
Moreover it has the ability to penetrate room walls, and similar obstacles
normally
encountered in the home or other similar environments. The Unique Smart Tag is
highly
reliable and can withstand severe environments and hot/cold temperature
extremes.
GPS Devices arad Lofag Rayage Passive/Active Tags
[0077] Also described herein is the use of a GPS device with long range
passive/active
tags to locate an individual. New technology allows GPS-enabled devices to be
incorporated into wearable objects, including clothing (using the principles
described for
RFID-enabled tags described elsewhere herein).
[0078] In one embodiment, the identification tags are compliant with longer
range
detectors. The GPS-enabled device which is worn or attached to the person or
child is
such that it is not only capable of communicating with a short-range RFID
reader, but
-12-
CA 02599363 2007-08-27
WO 2006/122041 PCT/US2006/017753
al'so is'-capa151'o 'of l,'ralhsi'nitt4ng data to a GPS network such that
location information
within a larger area can be communicated via a satellite network.
[0079] In one embodiment, such as illustrated in FIG. 9, a lost or abducted
person 7 who
is in an open environment may be located via a signal given by the GPS-enabled
device
(which also has RFID capability) to a GPS satellite 8. The signal received by
the GPS
satellite is transmitted to a GPS receiver 9 and retransmitted to a person or
persons 10
with specific information on the location of the lost or abducted person.
[0080] In one embodiment, the identification tags are active devices. An
active GPS-
enabled device system consists of the same features and functionality as a
passive system
with the addition of a power source associated with the tag. This power source
enables
reading and writing of the GPS-enabled device (which also has RFID capability)
at a
greater speed and distance and permits the tag to transmit information to a
RFID reader.
If an active identification tag is used, the active RFID system can be
integrated with
permanent structures such cellular telephone towers.
[0081] While embodiments of the present invention have been shown and
described
herein, it will be obvious to those skilled in the art that such embodiments
are provided
by way of example only. Numerous variations, changes, and substitutions will
now occur
to those skilled in the art without departing from the invention. It should be
understood
that various alternatives to the embodiments of the invention described herein
may be
employed in practicing the invention. It is intended that the following claims
define the
scope of the invention and that methods and structures within the scope of
these claims
and their equivalents be covered thereby.
-13-