Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 02798626 2012-12-10
FIELD OF THE INVENTION
[0001] The current invention relates to the fields of biometric security,
automated banking
machines, fraud prevention, retailing industry, hospitality industry, and the
financial banking
industry in general. The present invention relates to authenticating a user
based on their unique
biometric physical characteristics.
BACKGROUND OF THE INVENTION
[0002] In today's society automated teller machines have become ubiquitous
around the globe.
The financial industry has invested heavily and as a result profited greatly
from the continual rise
in demand for ATM terminals. Accordingly, fraud has also increased as a result
and begun to
flourish. Nevertheless, in the past several years there have been significant
advancements in
banking securities. With the increase of digital technologies on the rise,
criminals are also
adapting and using new sophisticated measures to defraud consumers. One such
measure has
been called 'cloning' or 'skimming'. Traditionally, swipe-card and smart-card
security features
have proven to be fairly effective at combating many forms of fraud. However,
criminal
organizations are now employing sophisticated card 'cloning' devices to copy a
user's
swipe/smart-card information. Furthermore, they have implemented complex
systems and means
for capturing an individual's PIN and later fraudulently draining their
financial account of funds
with the cloned card. These instances of financial terrorism often occur at
the ATM apparatus's
themselves but also occur at point of sale terminals. Check fraud and identity
theft are also
growing rampant. Financial institutions, as well as government agencies have
an immutable
obligation to consumers and the general public to help impede this growth in
crime. Banks and
other institutions are currently working diligently to innovate and implement
new advancements
to hinder this continual proliferation in fraud. Adopting new and robust
security measures are
imperative for combating this injustice. The growth in the field of biometrics
has provided a
solution and a glimpse into the future of financial security in general.
SUMMARY OF THE INVENTION
[0003] The following presents a simplified summary and a plurality of
embodiments in order to
provide basic understanding of the current invention. It is readily understood
by one skilled in
the art, that this summary is intended to provide general concepts and
embodiments. This
summary is not an extensive overview, neither is it intended to identify
critical or key elements
of all contemplated embodiments, and neither to limit the scope of the
invention. The purpose of
the summary is to provide a plurality of concepts and embodiments in a
simplified form as a
prelude to the more detailed description that is presented later.
[0004] The current invention has been developed in response to security
concerns related to the
art. In particular, in response to the problems of increased debit, credit,
check, banking, and
automated teller machine fraud. The security needs in the art have not been
met with the current
mechanisms in place and fraud is continually on the rise. Accordingly, the
present invention has
CA 02798626 2012-12-10
been developed to provide an apparatus, system, and method to overcome the
shortcomings in
the current art. Embodiments of the present invention address the above-
discussed needs by
providing an automated teller machine with a biometric fingerprint scanner,
and/or a biometric
vascular vein pattern scanner. Embodiments of the present invention also
address the above-
discussed needs by equipping a point of sale terminal (POS) with a biometric
fingerprint and/or
biometric vein scanning module. The biometric scanning modules may be
'contact', and/or
`contactless'. In this evolution in the art, there is a great need of readily
verifying whether
obtained biological information is derived from a living biological origin or
a non-living non-
biological origin. The disclosed invention answers and solves these needs.
[0005] Herein for the purpose of brevity automated teller machines equipped
with advanced
biometric fingerprint and/or vascular vein pattern technology may be referred
to in some
instances as `biometric banking machines' (BBM) '5 and/or `biometric teller
machines' (BTM)'s.
This referral is not intended in any way to limit the scope of any embodiment.
Its sole purpose is
to advance the ideology, and terminology in the art, and by no means delineate
the scope of the
invention.
[0006] In an embodiment of the invention, BBM terminals include a plurality of
transaction
capabilities, functions, systems, modules, and devices. Some function devices
include, but not
limited to, a card reader, a biometric imaging device, a keypad, a printer, a
PIN (Personal
Identification Number) reader, a cash dispenser, a display terminal, a cash
acceptor, a check
acceptor, a security camera, an alarm system, a code reader, user interface,
processing device,
and a biometric finger and vein scanning module.
[0007] BBM / BTM terminals utilize state of the art high tech security
systems, programs,
sensors, algorithms, logic, encryption, devices, and modules. Some security
sensors include, but
not limited to, magnetic, and seismic.
[0008] Biometric banking machine apparatuses utilize a plurality of biometric
authenticating
modules. Including, but not limited to, an input module, a verification
module, an encryption
module, a decryption module, a duress module, a memory module, and a storage
module.
[0009] Moreover in the implementation of the claimed embodiment, BBM terminals
operate on
multiple automated systems and methods responsive to recognizing and
authenticating a person
based on unique distinguishable human fingerprint attributes.
[0010] Furthermore in the implementation of the claimed embodiment, BBM
terminals operate
on multiple systems and methods responsive to recognizing a person based on
unique vascular
human vein pattern attributes.
[0011] In one embodiment of the invention, the apparatus includes an input
terminal that
conducts and receives a biometric scan and verification sequence by a user
activating a biometric
imaging reader.
[0012] In a specific embodiment, BBMs allow a user to input a PIN in
conjunction with a
successful biometric scan to gain access to financial transactions.
[0013] In yet another embodiment, account access is granted upon successful
biometric
fingerprint and/or vascular vein pattern authentication without the need of a
PIN.
[0014] A plurality of communication interface, systems and networks are
utilized for
verification and authenticating biometric data. Also a plurality of
programming environments are
utilized by the disclosed apparatus.
CA 02798626 2012-12-10
[0015] Also in one embodiment, a user inserts their plastic debit/credit card
with a magnetic
stripe, or debit/credit smart-card with chip technology containing unique card
number and
security features, into the card reader to commence the authentication
process. Authentication is
then initiated by the user placing their fingerprint on the biometric
fingerprint scanner, and/or
placing hand over biometric vein scanner. Moreover in the embodiment, the
user's unique
biometric fingerprint and vascular vein pattern is scanned, captured, and
digitally matched
against the current biometric data stored on file for that specific biometric
account.
[0016] In an exemplary embodiment, a point of sale terminal (POS) is equipped
with a
biometric fingerprint and/or vascular vein scanning device.
[0017] In another exemplary embodiment, a bank teller service transaction
window is equipped
with a biometric fingerprint and/or vascular vein scanning device.
[0018] Check fraud has grown to be an expensive and unsightly burden on both
consumers as
well as the financial industry in general. For purposes of greatly improving
industry security and
standards, the disclosed invention must be implemented nationwide. Employing a
biometric
fingerprint reader to a bank teller service window greatly reduces the
capability of falsification.
Moreover, incorporating a biometric vascular vein scanning device is virtually
impossible to
replicate due to the fact that it requires hemoglobin of a living human being
and the internal scan
of subcutaneous systems.
[0019] In one embodiment, a token such as a swipe/smart card is used to
initiate the
authentication process.
[0020] In one embodiment, token-less access is engaged by successful biometric
vein pattern
scan and/or fmgerprint scan bypassing the use of swipe-card or smart-card.
[0021] In the specification of some exemplary embodiments, the expression
"vein pattern"
and/or "vascular vein pattern" is deemed to include the pattern of a plurality
of subcutaneous
systems and not limited to any specific type of arteries, veins, capillaries,
or blood vessels.
BRIEF DESCRIPTION OF THE DRAWINGS
[0022] Preferred embodiments of the current invention will now be illustrated
in the appended
drawings. Moreover, one of ordinary skill in the art will readily understand
the exemplary
renditions and illustrations of the disclosed invention. Further understanding
that these drawings
depict only some preferred embodiments, and in no way to be considered
limiting to the scope of
the invention. It should be noted that the illustrated components and features
are not necessarily
drawn to scale.
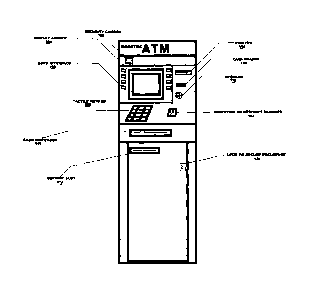
[0023] FIG. 1 is an illustration of a preferred embodiment in which an ATM is
provided that
has been equipped with a biometric fingerprint scanner.
[0024] FIG. 2 is an illustrated embodiment in which an ABM is provided that
has been
equipped with a biometric fingerprint scanner.
[0025] FIG. 3 is an illustration of a preferred embodiment in which a BBM is
shown that is
equipped with a biometric fingerprint scanner.
[0026] FIG. 4 is an illustration of a preferred embodiment in which a BBM is
shown that is
CA 02798626 2012-12-10
equipped with a biometric vascular vein scanner.
[0027] FIG. 5 is an illustration of a preferred embodiment in which a BBM
apparatus is shown
that has been equipped with both a biometric fingerprint scanner and a
biometric vascular vein
scanner.
[0028] FIG. 6 is an illustration of a preferred embodiment in which a bank
teller service
transaction window is shown that is equipped with a biometric fingerprint
scanner.
.[0029] FIG. 7 is an illustration of a preferred embodiment in which a bank
teller service
transaction window is shown that is equipped with both a biometric fingerprint
scanner and a
biometric vascular vein scanner.
[0030] FIG. 8 is an illustration of a preferred embodiment in which a back
teller service
transaction window is shown that is equipped with a singular device that scans
biometric
fingerprint as well as biometric vascular vein pattern.
[0031] FIG. 9 is an illustration of a preferred embodiment in which a POS
terminal is shown
that has been equipped with a biometric fingerprint scanner.
[0032] FIG. 10 is an illustration of a preferred embodiment in which a POS
terminal is shown
that has been equipped with a biometric fingerprint scanner and a contactless
card reader.
[0033] FIG. 11 is an illustration of a preferred embodiment in which a POS
terminal is shown
that has been equipped with a biometric vascular vein scanner.
[0034] FIG. 12 is an illustration of a preferred embodiment in which a POS
terminal is shown
that has been equipped with a singular device that scans biometric fingerprint
and biometric
vascular vein pattern.
[0035] FIG. 13 is an illustration of a preferred embodiment in which a POS
terminal is shown
that has been equipped with a device that scans both biometric fingerprint and
biometric vascular
vein pattern, as well as a contactless card reading device.
[0036] FIG. 14 is a flowchart that shows an exemplary set of user registration
and
authentication steps.
[0037] FIG. 15 is a flowchart that depicts an exemplary set of user access and
authentication
steps.
DETAILED DESCRIPTION
[0038] A plurality of embodiments for the present invention will hereinafter
be described in
further detail. Various descriptions of a plethora of materials, techniques,
devices, and equipment
are in some instances omitted so as not to obscure the invention or limit the
scope thereof
Various additions, substitutions, re-arrangements, and/or modifications within
the same scope
and/or complimentary scope of the current invention will become apparent to
one of ordinary
skill in the art. Exemplified configurations of the current invention will at
times be described
with reference to the drawings. These configurations and embodiments depict
only some
preferred embodiments, and in no way to be considered limiting to the scope of
the invention.
[0039] FIG. 1 is a preferred embodiment in which an exemplary ATM terminal is
provided that
has been innovated and equipped with a biometric fingerprint scanner. FIG. 2
is in essence the
CA 02798626 2012-12-10
same as FIG. 1 wherein the only difference is in the understood terminology.
In FIG. 2 the
apparatus is understood to be named ABM instead of ATM. This illustration in
the contrast in
nomenclature of the two embodiments is done because globally banking machines
are often
referred to as automated banking machines (ABM)'s and automated teller
machines (ATM)'s.
FIG. 1 and FIG. 2 are embodied in one sense to satisfy the globally accepted
nomenclature.
FIG. 3 is in essence the same apparatus as FIG. 1 and FIG. 2, the only
difference being the
apparatus given the name BBM standing for biometric banking machine wherein
the term
'automated' is understood to silently come before the word biometric, to
further advance the
exemplary nomenclature in the art. This nomenclature by no means limits the
scope of the
current invention, but instead is understood to showcase the advancement in
ideology and
terminology in the art.
[0040] FIG. 4 is a preferred embodiment of a BBM apparatus that is equipped
with a biometric
vascular vein pattern scanner. FIG. 5 is a preferred embodiment in which a BBM
apparatus is
equipped with both a biometric fingerprint scanner and a biometric vascular
vein pattern scanner.
In FIG. 5 it is also understood, by one of ordinary skill in the art, that the
biometric fingerprint
scanner and vascular vein scanner can either be one singular scanning device
or two separate
scanning devices. In the specification of some exemplary embodiments, the
expression "vein
pattern" and/or "vascular vein pattern" is deemed to include the pattern of a
plurality of
subcutaneous systems including, and not limited to, any type of arteries,
veins, capillaries, and
blood vessels.
[0041] FIG. 6 is a preferred embodiment of a bank teller service transaction
window that has
been equipped with a biometric fingerprint scanner. This illustration is
understood to be an
exemplary model of a typical bank teller window innovated with the capability
for biometric
authentication. FIG. 7 is a preferred embodiment of a bank teller service
transaction window that
has been equipped with a biometric vascular vein pattern scanner. FIG. 8 is an
illustrated
embodiment of a bank teller service transaction window that has been equipped
with a singular
scanning device that scans both biometric fingerprint and vascular vein
pattern.
[0042] It should be noted that when the terms "biometric fingerprint scanner"
and "biometric
vascular vein pattern scanner" are used, they are understood by one of
ordinary skill in the art, to
refer to a scanning apparatus that conducts either a 'contact' scan or
`contactless' scan. Indeed, a
'contact' scan is understood to be conducted by physical contact with the
apparatus scanning
module. A `contactless' scan is understood to be conducted without the need of
physical contact
with the apparatus. In an exemplary embodiment of a `contactless' scan, a user
holds their hand
over a biometric fingerprint and/or vascular vein pattern reader and the scan
is conducted without
physical contact. In an exemplary embodiment of a 'contact' scan, a user
places their hand
directly in contact with the apparatus scanning module and the scan is
conducted via physical
contact.
[0043] FIG. 9 is an illustration of a preferred embodiment in which a POS
terminal is shown
that has been equipped with a biometric fingerprint scanner. The POS terminal
is understood by
one of ordinary skill in the art, to exemplify and embody any place where a
user can access their
financial account to pay for goods and services and/or any other financial
transaction. FIG. 10 is
an illustrated embodiment of a POS terminal equipped with a biometric
fingerprint scanner as
well as a `contactless' card reading device. Many financial service providers
are providing their
clients with 'quick pay' or sometimes called 'pay-pass' token capability. This
capability is
exemplified in some of the illustrated embodiments that are equipped with
`contactless' reading
CA 02798626 2012-12-10
devices. The scope of the `contactless' card reading device is understood by
one of ordinary skill
to be in no way limited to 'quick pay' and/or 'pay-pass' functionality. FIG.
11 is an illustration
of a preferred embodiment in which a POS terminal is shown that has been
equipped with a
biometric vascular vein scanner. FIG. 12 is an illustration of a preferred
embodiment in which a
POS terminal is shown that has been equipped with a singular device that scans
both biometric
fingerprint and/or biometric vascular vein pattern. FIG. 13 is an illustration
of a preferred
embodiment in which a POS terminal is shown that has been equipped with a
device that scans
both biometric fingerprint and biometric vascular vein pattern, as well as a
`contactless' card
reading device.
[0044] FIG. 14 is a flowchart that shows an exemplary set of user registration
and
authentication steps. This flowchart is intended to be an exemplary
illustration of a general
embodiment of a user registration sequence and procedure. It is understood by
one of ordinary
skill in the art, that this flowchart is a general example and by no means
limiting to the scope of
the invention. It is also understood that additional sequences, events,
substitutions, and steps may
be made within the scope of the invention without departing from the spirit of
the current
invention thereof, and that the invention includes all such sequences, events,
substitutions, and
steps. FIG. 15 is a flowchart that depicts an exemplary set of user access and
authentication
steps. This flowchart is intended to illustrate an exemplary embodiment in
which a user initiates,
authenticates, and ultimately is granted or denied access to their biometric
financial account.
This flowchart, similar to the previous flowchart, is intended to be an
exemplary illustration of a
general embodiment of a user access sequence and procedure. It is understood
by one of ordinary
skill in the art, that this flowchart is a general example and by no means
limiting to the scope of
the invention. It is also understood that additional sequences, events,
substitutions, and steps may
be made within the scope of the invention without departing from the spirit of
the current
invention thereof, and that the invention includes all such sequences, events,
substitutions, and
steps.
[0045] In the embodiment of the present invention, various biometric imaging
modules and
procedures are implemented to capture biometric image data from fingerprint
and/or vascular
vein pattern. The embodied apparatus is functional to capturing additional
forms of biometric
image/data comprising, but not limited to, retina, iris, hand geometry,
signature, and voice
analysis. Furthermore, the step by step workings are readily understood by one
of ordinary skill
in the art.
[0046] A biometric information authenticating module is implemented in some
embodiments,
comprising a means for efficient communication between apparatus and user's
financial
institution. This module is facilitated by predetermined set of device
protocols. Furthermore, the
step by step workings are readily understood by one of ordinary skill in the
art.
[0047] A biometric data input/output module is implemented in some specific
embodiments,
comprising of inputting a user's biometric data, generating an encryption
algorithm, and
transmitting said exemplary data. Additionally comprising of a verification
protocol as well as
decrypting the received data.
[0048] A biometric feedback module is embodied to provide audio and/or visual
feedback to
apparatus user. Furthermore, the embodied feedback module is facilitated to
provide real-time
feedback to apparatus manufacturer and/or maintenance technician, as well as
user's financial
institution. Furthermore, the step by step workings are readily understood by
one of ordinary
skill in the art.
CA 02798626 2012-12-10
[0049] A biometric storage module is embodied to comprise a means for
biometric data to be
securely encrypted and stored within apparatus. This module further comprises
an inhibiting
protocol for inhibiting any unverified attempt to gain access to said
encrypted data. In some
embodiments this storage module is only a temporary-storage module and the
biometric data
captured is deleted upon successful and/or unsuccessful verification sequence.
Furthermore, the
modular workings and mechanical implementations are readily understood by one
of ordinary
skill in the art.
[0050] A biometric communication module is embodied to comprise a means for
facilitating
communication between apparatus and preferred networks. Some networks
comprising, but not
limited to, the apparatus service/monitoring network, and various financial
institutions secure
network. Additionally in the exemplary embodiment, pluralities of
communication interfaces are
utilized to help facilitate communication. Furthermore, the modular workings
and mechanical
aspects are readily understood by one of ordinary skill in the art.
[0051] In the embodiment of the present invention, a biometric fingerprint
scanner is
implemented to conduct and scan a user's unique biometric fingerprint.
Furthermore in the
embodiment, the biometric fingerprint scanning device is equipped with an anti-
falsification
module that interprets if the scanned data was obtained in 2-D or 3-D. The
exemplary scan is
rejected if it is suspected to be a 2-Dimention falsification. The exemplary
scan is processed if it
is interpreted to be a real-time 3-Dimention scan of the user's biometric
data. Furthermore, one
of ordinary skill in the art will readily understand the mechanical workings
and technical
peripherals.
[0052] In the embodiment of the present invention, a biometric vascular vein
scanner is
implemented to scan and verify a user's unique subcutaneous patterns.
Furthermore, pluralities
of scanning methods are implemented to obtain biometric data by utilizing
various aspects and
qualities of the infrared and near-infrared spectrum. Furthermore, one of
ordinary skill in the art
will readily understand the mechanical workings and technical aspects.
[0053] In the embodiment of the current invention a card reader is equipped to
the apparatus.
This card reader is understood to read, scan, interpret, and communicate with
the apparatus CPU
and user's financial institution. It is understood by one of ordinary skill,
that the card reader
device is functional to read and interact with a plurality of card-types. Card
types including, but
not limited to, credit cards with magnetic stripe and/or chip technology, and
debit cards with
magnetic stripe and/or chip technology. It is also understood that the card
reading device is
capable of reading `contactless' cards and `contactless' mobile devices.
Furthermore, the step by
step workings are readily understood by one of ordinary skill in the art.
[0054] Furthermore in the embodiment of the current invention, a keypad is
equipped to the
apparatus. This exemplary keypad is implemented in a plurality of ways. Some
implementations
comprising, but not limited to, tactile integrated braille, numeric
functionality, alphanumeric
functionality, touch-screen functionality, and a means of `contactless'
functionality. These
implementations are understood to be general aspects and in no way limiting to
the scope of the
invention. Furthermore, the step by step workings are readily understood by
one of ordinary skill
in the art.
[0055] Moreover in the embodiment of the present invention, a PIN reader
module is
implemented by the disclosed apparatus. A user enters their PIN on the earlier
described keypad,
their PIN is then processed and authenticated. The PIN reader is a separate
module with sensors
CA 02798626 2012-12-10
for detecting suspicious anomalies. One of the methods by which criminals
steal a person's PIN
is by placing a false keypad over an apparatuses real keypad. The PIN
information is then
recorded and later used to defraud the account holder. This PIN reading module
implements
sensors that aid in detecting any tampering. Such sensors include, but not
limited to, a weight
sensor for detecting any added weight to any apparatus compartment that should
not be present
and also is not a result of normal operational use.
[0056] In the embodiment of the present invention, a printer is equipped to
the apparatus. The
printer is functional to provide a printed copy of various transactions.
Transactions including, but
not limited to, passbook update, balances, and account activity. Furthermore,
the step by step
workings are readily understood by one of ordinary skill in the art.
[0057] In the embodiment of the current invention a secure enclosure for a
plurality of financial
instruments is implemented. This enclosure is only capable of being accessed
by authorized
apparatus service technicians, through the use of secure locks, sealing volts,
and mechanisms.
Furthermore, the step by step workings are readily understood by one of
ordinary skill in the art.
[0058] In the embodiment of the current invention, a cash dispenser is
implemented by the
disclosed apparatus. The cash dispenser is functional to dispense cash to
authenticated user's.
The apparatus CPU is functional to interpret currency conversions and dispense
the correct
quantity of funds to the requesting user. Furthermore, the step by step
workings are readily
understood by one of ordinary skill in the art.
[0059] In the embodiment of the present invention, a display terminal is
implemented by the
disclosed apparatus. The display terminal is functional to provide visual
instructions, inputs, and
cues to the apparatus user. These instructions, inputs, and visual cues may be
done via a plurality
of methods. Some methods comprise of, but not limited to, a means for touch-
screen interaction.
A means for visual assistance to those that may be differently-abled is also
implemented by the
disclosed apparatus. Furthermore, the step by step technological workings are
readily understood
by one of ordinary skill in the art.
[0060] In the embodiment of the present invention, a cash acceptor is
implemented and utilized.
The disclosed cash acceptor is functional to accept cash into the apparatus
and hold it securely
for later processing. Furthermore, the step by step technological workings of
the cash acceptor
are readily understood by one of ordinary skill in the art.
[0061] In the embodiment of the present invention, a check acceptor is
implemented and
utilized. The disclosed check acceptor is functional to accept various forms
of checks into the
apparatus and hold it securely for later processing. Furthermore, the step by
step technological
workings of the check acceptor are readily understood by one of ordinary skill
in the art.
[0062] In the embodiment of the present invention, a plurality of security
cameras and detectors
are implemented by the disclosed apparatus. The security cameras are
functional to capture
images and/or video in instances of suspicious activity. Some detectors and
sensors comprise of,
but not limited to, thermal, magnetic, and seismic. Furthermore, the step by
step mechanical
workings are readily understood by one of ordinary skill in the art.
[0063] In the embodiment of the present invention, a code reader is equipped
to the disclosed
apparatus. This code reader is functional to read and interpret secure codes
on such 'contact'
devices as tokens, and also `contactless' devices. Furthermore, the step by
step operational
workings are readily understood by one of ordinary skill in the art.
CA 02798626 2012-12-10
[0064] In the embodiment of the present invention, an encryption module is
equipped to the
disclosed apparatus. This module contains pluralities of algorithms for
encrypting sensitive
information and communicating it between both the biometric banking apparatus,
and the
apparatus user's financial institution. In one exemplary embodiment asymmetric
encryption is
employed. Nonetheless, it is understood by one of ordinary skill that a
plurality of suitable
encryption methods are capable of being employed.
[0065] In the embodiment of the present invention, a decryption module is
equipped to the
disclosed apparatus. This module is functional to decrypting encrypted data
sent from apparatus
and/or users financial institution. Furthermore, in-depth operational workings
are readily
understood by one of ordinary skill in the art.
[0066] In the embodiment of the present invention, a plurality of processing
devices are utilized
by the disclosed apparatus. These processing devices comprise, but not limited
to, a central
processing unit, a microcontroller, a control circuit, and a microprocessor.
The functionality of
these components is readily understood by one of ordinary skill in the art.
[0067] In the embodiment of the current invention, a control module is
equipped to the
disclosed apparatus. The control module is functional to control access to
various networks and
communication procedures within the apparatus.
[0068] In the embodiment of the present invention, a wireless communication
module is
equipped to the disclosed apparatus. This module includes a receiver for
receiving wireless
signals from a plurality of networks. Some networks comprising, though not
limited to, mobile,
and Bluetooth networks.
[0069] In the embodiment of the present invention, an audio module is equipped
to the
apparatus. This audio module consists of a speaker operative to give audio
signals as well as cues
to apparatus user. This module is also operative to assist differently-abled
user's to interact with
the apparatus via audio aids.
[0070] In the embodiment of the present invention, a plurality of downstream
ports are
implemented. These ports are in data communication with a multiport hub. These
ports are
functional to the exchange of authorization codes and authorizing
communication access. The
functionality of these ports is readily understood by one of ordinary skill in
the art.
[0071] In the embodiment of the current invention, a manufacture access module
is equipped to
the apparatus. This module is operative to enable authorized apparatus
personnel with access to
apparatus inner mechanisms.
[0072] In the embodiment of the present invention, a central processing unit
(CPU) is
implemented by the disclosed apparatus. This CPU is functional to communicate
control all the
processes within the apparatus. The functionality of the CPU is readily
understood by one of
ordinary skill in the art.
[0073] In the embodiment of the present invention, a secure crypto-processor
is implemented
by the apparatus. This secure crypto-processor is functional by employing
multiple levels of
physical and software/firmware security. The crypto-processor encrypts,
decrypts, and executes
instructions within the apparatus ergo maintaining a secure environment.
[0074] In the embodiment of the present invention, a cryptographic module is
implemented by
the apparatus. This module utilizes cryptographic logic, cryptographic
algorithms, and
cryptographic processes to help sustain a high level of apparatus security.
The functionality of
CA 02798626 2012-12-10
the cryptographic module is readily understood by one of ordinary skill in the
art.
[0075] In an embodiment of the present invention, a capacitive sensor is
implemented by the
disclosed apparatus. This sensor utilizes human body capacitance as an input.
The body
capacitance is then utilized in some instances to operate touch devices on the
apparatus.
[0076] In the embodiment of the present invention, a user interface module is
implemented by
the apparatus. This module enables user communication with apparatus as well
as functionality
of the apparatus. Functionality is actuated by a plurality of means, not
limited to, touch screen,
tactile buttons, keypad, and audio and video cues. The general operation of
the module is readily
understood by one of ordinary skill in the art.
[0077] In the embodiment of the present invention, a backup power device is
equipped to the
apparatus. This backup power device provides backup power to the apparatus in
the event of loss
of power. Distress signal is then communicated to apparatus monitoring network
informing them
of the loss of power. A surge protection device is also implemented to prevent
apparatus damage
in event of power surge.
[0078] In one aspect of the present invention, a memory management system is
utilized. This
system is functional to record and interact between the central processing
unit and all apparatus
functionality. An auxiliary memory management unit is also utilized by the
disclosed invention
to behave as a temporary-memory system. This auxiliary version of the memory
management
system is functional to execute predetermined instructions on what types of
data to record and
how long to store or erase such data. This system is responsive to reduce
communication wait-
time during any apparatus functionality and/or authentication sequence. The
general workings
and operation of this system is readily understood by one of ordinary skill in
the art.
[0079] In the embodiment of the present invention, a token-based system is
utilized. This token-
based system is functional to allow and/or disallow the use and/or
communication of tokens.
This system is operational to receive, authenticate, transmit, and execute
commands from
apparatus central processing unit. This system is responsive to allow and/or
disallow access to a
user's financial account by the initial stage of authenticating their
contact/contactless token, and
verifying/authenticating the account protocols and security features. In one
exemplary
embodiment a token may be in reference to a debit card and/or credit card,
and/or any other
contact device. In another exemplary embodiment a token may be a contactless
device such as a
mobile device, debit/credit card, and/or any other external contactless
apparatus. The
functionality of this system is readily understood by one of ordinary skill in
the art.
[0080] In one embodiment of the present invention, a token-less system is
utilized. This token-
less system is responsive to communicate and retrieve user account profile and
data without the
use of a token. In the functionality of this system neither a contact token or
contactless token is
needed or utilized to initiate apparatus interaction and/or communication. In
an exemplary
enactment of this disclosed system a user approaches the apparatus and then
simply places
his/her hand directly on, or hold over, the biometric fingerprint and/or vein
pattern scanner of the
apparatus. This system then communicates the scanned biometric data and
retrieves, populates,
and initiates authentication sequence. The functionality of this system is
readily understood by
one of ordinary skill in the art.
[0081] In one aspect of the present invention, a response system for duress
identification is
utilized. This system is functional to respond to any detection of duress
identification. During the
user authentication process this system detects if any security parameters are
breached. This
CA 02798626 2012-12-10
system is not simply utilized to process an instance of unsuccessful
verification, but instead to
detect any suspicious anomalies trying to falsify themselves as successful
indicators during the
identification process. In an exemplary embodiment of this system, a fake
token is inserted into
apparatus and detected as being a falsification attempt by this system.
Apparatus authorities are
them alerted of the instance of this action. Furthermore in this exemplary
embodiment of this
system, a fake model or sample is presented to the apparatus in the form of a
fake fmgerprint
replica and/or vein pattern replica and is detected by this system as being a
fraudulent
authorization attempt. One such exemplary way in which the apparatus utilizes
this system is,
although not limited by, detecting hemoglobin in living human blood as an
indicator that this
individual requesting authorization is both a human and as well as being a
living person. The
functionality of this system is readily understood by one of ordinary skill in
the art.
[0082] In the embodiment of the present invention, a plurality of security
systems are utilized.
These systems comprise of imaging systems as well as sensors. Some of these
systems and
sensors have previously been discussed in this disclosure. These systems
comprise of both
software, firmware, and hardware. All apparatus security means and systems
share the intrinsic
characteristic that they provide an alert indication once any condition and/or
protocol has been
met. Any alteration, or attempted alteration, of the disclosed apparatus is
alerted to apparatus
security authority. Tamper-detection software is also utilized by these
systems to alert apparatus
authorities in event of any confirmed apparatus tampering and/or suspicious
indicators of
possible and/or attempted tampering. The functionality of the disclosed
systems is readily
understood by one of ordinary skill in the art.
[0083] In one aspect of the disclosed invention, a zeroisation system is
utilized. This system is
functional to erase sensitive parameters from the apparatus in event of
possible apparatus theft.
This system is responsive to insure sensitive data is not captured or
disclosed to unauthorized
person/persons in event of apparatus theft and/or tampering. The zeroisation
system is in direct
communication with apparatus memory management system as well as cryptographic
processes.
The functionality of the disclosed system is readily understood by one of
ordinary skill in the art.
[0084] In one aspect of the current invention, an event recorder system is
utilized. This system
is functional to record and log all events and interactions conducted and/or
received by
apparatus. This system operates by parameters set by the apparatus memory
management and
cryptographic systems. The functionality of the disclosed system is readily
understood by one of
ordinary skill in the art.
[0085] In one embodiment of the present invention, an encryption system is
utilized. An
encryption module has previously been discussed above. This system is
associated with the
above-discussed module and is functional to execute encryption keys
communicating within a
cryptographic module. This system is functional to both encrypt as well as
decrypt data. This
system is responsive to decrypt, encrypt, transmit, and verify secure keys and
parameters within
apparatus data sensitivity protocols. The functionality of the disclosed
system is readily
understood by one of ordinary skill in the art.
[0086] In one aspect of the disclosed invention, a feedback system is
utilized. A feedback
module has been previously discussed above. This system is directly associated
with the above-
discussed module and is functional to transmit feedback via electronic means,
audio means,
and/or visual means. This system communicated in real-time with apparatus
authorities to
provide data and execute functionality. The general functionality of the
disclosed system is
readily understood by one of ordinary skill in the art.
CA 02798626 2012-12-10
[0087] In one embodiment of the present invention, a dispatch communication
system is
utilized. This system is functional to communicate with apparatus authorities
as well as
dispatched maintenance personnel. This system has secure protocols and
parameters to allow or
disallow access to various secure enclosures. In one exemplary embodiment an
apparatus
controller schedules a secure cash re-fill. This system logs and verifies this
data with the
indicators and access keys provided by apparatus technician to determine if
this is an authorized
and/or previously confirmed scheduled interaction. The general functionality
of the disclosed
system is readily understood by one of ordinary skill in the art.
[0088] In one aspect of the present invention, a troubleshoot system is
utilized. This system is
responsive to perform routine schedule apparatus software and hardware checks,
and to
communicate this data with an apparatus authorized controller. This system is
function to
troubleshoot minor glitches itself while forwarding details of the occurrence
to be simultaneously
reviewed, as well as requesting an authorized apparatus technician to either
remotely trouble
shoot the problem or dispatch a service technician. The general functionality
of the disclosed
system is readily understood by one of ordinary skill in the art.
[0089] In one embodiment of the present invention, a user validating system is
utilized. This
system is functional to validate an authorized account holder based on
specific predetermined
parameters. In an exemplary embodiment this system is utilized in instances
wherein a user
requests additional security measures added to his/her account from financial
service institution.
An example of an additional security request could be adding a password to the
account. Another
example of a specific security request could be a user requesting that only
the fingerprint of a
specific finger be deemed a successful authentication, or only a specific hand
or body part
deemed a successful vein pattern scan. This added security may be added in the
event of any
forced authentication wherein a user is forced by someone else to withdraw
from an ATM. This
system would immediately alert authorities that the user had activated his pre-
set security alert
measure and to review security systems and possibly contact and/or dispatch
law enforcement.
The general functionality of the disclosed system is readily understood by one
of ordinary skill in
the art.
[0090] In one aspect of the present invention, a system to authenticate a
user's PIN is utilized.
This system is functional to communicate and verify account data to allow or
disallow access to
further authentication steps and/or general account access.
[0091] In one embodiment of the present invention, a system for capturing a
user's biometric
image data is utilized. Aspects of this system have previously been discussed
in general above.
This system is functional to interpret the scanned biometric image, transform
it into secure
encrypted data, and communicated it with apparatus CPU and user's financial
institution. The
general functionality of the disclosed system is readily understood by one of
ordinary skill in the
art.
[0092] In one aspect of the current invention, an angular displacement system
is utilized. This
system is functional to determine the precise angle of each biometric scan and
correct the
displacement data in correlation with authenticated data. In an exemplary
embodiment, a user
places their fingerprint on fingerprint reader to be scanned. The angle that
the user places their
fingerprint in this example is off by thirty degrees. The angular displacement
system corrects this
angle in the data and then processes it alongside the correct angle of user's
authentic scan on file.
The general functionality of the disclosed system is readily understood by one
of ordinary skill in
the art.
CA 02798626 2012-12-10
[0093] In one embodiment of the present invention, a plurality of computer
operating systems
are functional to be utilized. Systems such as MICROSOFT WINDOWS, LINUX,
and/or any
other dedicated operating systems designed specifically for the disclosed
apparatus.
[0094] In one aspect of the present invention, a currency conversion system is
utilized. This
system provides the apparatus with the capability to interpret and communicate
foreign exchange
rates to apparatus user. The exemplary user then can decide to proceed with
transaction if the
rate provided is acceptable or decline the transaction. The disclosed
biometric apparatus may or
may not charge a fee for doing currency conversions and/or authenticating
transactions with
foreign financial institutions.
[0095] In one aspect of the present invention, a global positioning system is
utilized. This
system allows the disclosed biometric apparatus to emit its coordinates and
communicate with
authorized apparatus control personnel. The functionality of the disclosed
system is readily
understood by one of ordinary skill in the art.
[0096] In one embodiment of the present invention, a software repository is
utilized. This
repository is functional to store authorized software packages and deploy a
package management
system. These systems allow functionality to install, upgrade, troubleshoot,
and/or remove some
specific aspects of various apparatus software packages.
[0097] In one aspect of the present invention, a 3D rendering system is
utilized. This system is
responsive to determine that biometric scanned data is of an actual 3D user
bodily section and
not a 2D falsification or attempted falsification.
[0098] In one aspect of the disclosed invention, biometric imaging systems are
utilized. These
systems comprise capturing, transforming, and communicating biometric
fingerprint and vein
pattern data for authentication. Aspects of these systems have previously been
discussed above.
[0099] In the embodiment of the disclosed invention a plurality of methods are
employed.
These methods comprising, but not limited to, a plurality of steps. A
registration step wherein a
user registers with a financial institution to open a biometric account. In
this exemplary
registration step the user selects the exact type of biometric account and
transaction capabilities
needed to address their needs. Furthermore, in this registration step if a
user already has an
account with a financial institution it can be transitioned into a biometric
account. An input step
wherein a user provides their Identification to be verified and recorder by
financial institution. A
sampling step wherein a user provides their biometric properties to be
sampled, captured, and
recorder by financial institution. A token step wherein a token based aid is
added to user's
biometric account. This token comprising of, but not limited to, a
debit/credit smart-card and/or
swipe-card. This token is also capable of being a 'contact' and/or
`contactless' device. A
secondary input step further comprising of a user has the option to select a
secure PIN to be
synced to their biometric account and token. A protocol step further
comprising account limits
and transaction protocols agreed upon by users and their financial
institutions. Some exemplary
protocols could be withdrawal limits from biometric apparatus, and POS
terminal purchase
limits. A closing step further comprising a user and their financial
institution agree upon
confidentiality matters and account is activated. Within this closing step all
the terms of
agreement are discussed and accepted. An initiation step further comprising a
user inserting their
token to be read by a biometric banking machine. This exemplary initiation
comprises a first
CA 02798626 2012-12-10
initiation wherein a user upon activating account can initiate access to their
account and perform
any requests or changes. An identification step comprising a user placing
their finger and/or hand
on biometric fingerprint and/or vascular vein scanner to be read. A
communication step wherein
the captured biometric data is communicated to financial institution database
and authenticated.
An access step wherein, depending successful authentication, access is either
granted or denied.