Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 02805539 2016-12-08
PPH
SYSTEM AND METHOD FOR SECURE REMOTE ACCESS
FIELD OF THE INVENTION
The invention relates to the field of computer authentication and
authorization. More
particularly, the invention relates to a system and method for secure remote
connection to
computing services.
BACKGROUND OF THE INVENTION
Authentication is the mechanism for securely identifying users, typically
through user ID
and password. These credentials are vulnerable to malware attacks, such as key
logging. In order
to access local resources on a computer, conventional authentication methods
employing user ID
(Identity Document) and password are adequate. When a remote service is
activated, it is
unprotected and open to hacking.
Accordingly, it would be beneficial to provide an improved approach for
providing a
secure access to remote computing services, which would avoid or mitigate the
shortcomings of
the existing prior art.
SUMMARY OF THE INVENTION
There is an object of the present invention to provide a system, method and
apparatus for
secure remote connection to computing services.
According to one aspect of the invention, there is provided a method for
remote secure
access of a user to a service on a server computer, the method comprising:
(a) at a client device, obtaining, from the server computer or a third party
server
computer, an authorization software and an input information to the
authorization software;
(b) separating authentication and authorization processes, comprising
excluding service
access privileges from the authenticating process and transferring the
privileges to the
authorization process, comprising:
(i) authenticating at least one of:
1
CA 02805539 2016-12-08
PPH
a user;
or the user and the client device, comprising: verifying identity thereof,
without providing
the access of the user to the service;
(ii) upon successful authenticating, authorizing access of the user to the
service,
comprising:
(ii-1) establishing an authorization connection between the client device and
the
server computer;
(ii-2) at the server computer, detecting the authorization connection, and
creating a
blocking process to block access of the user to the service on the server
computer;
(ii-3) executing the authorization software on the client device and the
server
computer or the third party server computer with the input information
obtained in the step (a);
and
(ii-4) provided an output from the authorization software on the client device
and the
server computer or the third party server computer is the same, terminating
the blocking process
on the server computer, thereby allowing the access of the user to the service
on the service
computer.
In the method described above, the authorization software is configured to
perform a One-
Time-Authorization (OTA).
In the method described above, the OTA is performed using a one-way function.
In the method described above, the OTA is performed using a dynamic connection
information for the authorization connection as the input information.
In the method describe above, the establishing the authorization connection
comprises
establishing a remote desktop connection.
In the method describe above, the creating the blocking process further
comprises creating
a blocking window on a desktop of the server computer.
2
CA 02805539 2016-12-08
PPH
In the method describe above, the creating the blocking window further
comprises creating
a modal dialog window.
The method further comprises:
providing a quick response (QR) code including a dynamic connection
information for the
authorization connection in a blocking window on the server computer; and
at the client device, obtaining the dynamic connection information from the QR
code.
The method further comprises one or more of the following:
sharing the output from the authorization software on the client device and
the server
computer or the third party server computer via a shared clipboard; or
sending the output from the authorization software on the client device to the
server
computer or the third party server computer via a secure channel; or
copying the output from the authorization software on the client device to a
clipboard, and
pasting said output into a secure shell executing the blocking process.
The method further comprises:
using the service; and
closing the authorization connection on the server computer.
In the method describe above, the using the service further comprise:
automatically signing into the service in a remote desktop window on the
client device
using user account credentials; and
the user signing out of the service in the remote desktop window on the client
device.
According to another aspect of the invention, there is provided a system for
remote secure access
of a user to a service on a server computer, the system comprising:
a client device having a processor;
a server computer; and
3
CA 02805539 2016-12-08
PPH
computer readable instructions stored in a memory of the client device and the
server
computer, causing:
(a) the client device to obtain, from the server computer or a third party
server computer,
an authorization software and an input information to the authorization
software;
(b) the server computer and the client device to separate authentication and
authorization
processes, comprising excluding service access privileges from the
authenticating process and
transferring the privileges to the authorization process, comprising:
(i) authenticating at least one of:
a user;
or the user and the client device, comprising:
verifying identity thereof, without providing the access of the user to the
service;
(ii) upon successful authenticating, authorizing access of the user to the
service,
comprising:
(ii-1) establishing an authorization connection between the client device and
the server computer;
(ii-2) at the server computer, detecting the authorization connection, and
creating a blocking process to block access of the user to the service on the
server computer;
(ii-3) executing the authorization software on the client device and the
server
computer or the third party server computer with the input information
obtained in the step (a); and
(ii-4) provided an output from the authorization software on the client device
and the server computer or the third party server computer is the same,
terminating the blocking process on the server computer, thereby allowing the
access of the user to the service on the service computer.
In the system describe above, the authorization software is configured to
perform a One-
Time-Authorization (OTA).
In the system describe above, the OTA uses a one-way function.
4
CA 02805539 2016-12-08
PPH
In the system describe above, the OTA uses a dynamic connection information
for the
authorization connection as the input information.
In the system describe above, the the authorization connection comprises a
remote
desktop connection.
In the system describe above, the blocking comprises a blocking window on a
desktop of
the server computer.
In the system describe above, the blocking window comprises a modal dialog
window.
In the system describe above, the computer readable instructions further cause
the server
computer to form a quick response (QR) code including a dynamic connection
information for
the authorization connection in a blocking window on the server computer, and
the client device
to obtain the dynamic connection information from the QR code.
In the system describe above, the computer readable instructions further cause
the server
computer and the client device to perform one or more of the following:
to share the output from the authorization software on the client device and
the server
computer or the third party server computer via a shared clipboard; or
to send the output from the authorization software on the client device to the
server
computer or the third party server computer via a secure channel; or
to copy the output from the authorization software on the client device to a
clipboard, and to
paste said output into a secure shell executing the blocking process.
In the system describe above, the computer readable instructions further cause
the server
computer to close the authorization connection upon the user using the
service.
In the system describe above, the computer readable instructions further cause
the client
5
CA 02805539 2016-12-08
PPH
device to automatically sign into the service in a remote desktop window using
user account
credentials.
Thus, an improved system and method for secure remote connection to computing
services have been provided.
BRIEF DESCRIPTION OF THE DRAWINGS
Further features and advantages of the invention will be apparent from the
following
description of the embodiment, which is described by way of example only and
with reference to
the accompanying drawings, in which:
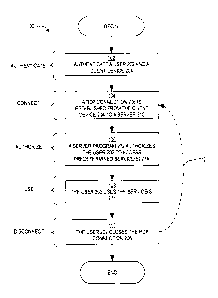
Fig. 1 shows a top level flowchart of a method in accordance with a first
embodiment of the
present invention;
Fig. 2 shows an overview block diagram of a system in accordance with the
first embodiment of
the present invention with elements referenced in the flowchart of Fig. 1;
Figs. 3A and 3B show a flowchart of a method of an authentication process in
the flowchart
shown in Fig. 1;
Figs. 4A and 4B show detailed block diagrams of the system shown in Fig. 2
with elements
referenced in the flowcharts of Figs. 3A and 3B;
Figs. 5 shows a flowchart of a method of a connection process in the flowchart
shown in Fig. 1;
Figs. 6 shows a detailed block diagram of the system shown in Fig. 2 with
elements referenced in
the flowchart of Fig. 5;
Figs. 7 shows a flowchart of a method of an authorization process in the
flowchart shown in Fig.
1;
Figs. 8 shows a detailed block diagram of the system shown in Fig. 2 with
elements referenced in
the flowchart of Fig. 7;
Figs. 9 shows a flowchart of a method of a Using Services process in the
flowchart shown in Fig.
1;
Figs. 10 shows a detailed block diagram of the system shown in Fig. 2 with
elements referenced
in the flowchart of Fig. 9;
6
CA 02805539 2016-12-08
PPH
Fig. 11 shows a top level flowchart of a method in accordance with a second
embodiment of the
present invention;
Fig. 12 shows an overview block diagram of a system in accordance with the
second
embodiment of the present invention with elements referenced in the flowchart
of Fig.
11;
Figs. 13 shows a flowchart of a method of a connection process in the
flowchart shown in Fig.
11;
Figs. 14 shows a detailed block diagram of the system shown in Fig. 2 with
elements referenced
in the flowchart of Fig. 13;
Figs. 15 shows a flowchart of a method of an authorization process in the
flowchart shown in
Fig. 11;
Figs. 16 shows a detailed block diagram of the system shown in Fig. 12 with
elements referenced
in the flowchart of Fig. 15;
Figs. 17 shows a flowchart of a method of a Using Services process in the
flowchart shown in
Fig. 11;
Figs. 18 shows a detailed block diagram of the system shown in Fig. 12 with
elements referenced
in the flowchart of Fig. 17;
Fig. 19 shows a top level flowchart of a method in accordance with a third
embodiment of the
present invention;
Fig. 20 shows an overview block diagram of a system in accordance with the
third embodiment
of the present invention with elements referenced in the flowchart of Fig.19;
Figs. 21 shows a flowchart of a method of a connection process in the
flowchart shown in Fig.
19;
Figs. 22 shows a detailed block diagram of the system shown in Fig. 2 with
elements referenced
in the flowchart of Fig. 21;
Figs. 23 shows a flowchart of a method of an authorization process in the
flowchart shown in
Fig. 19;
Figs. 24 shows a detailed block diagram of the system shown in Fig. 12 with
elements referenced
in the flowchart of Fig. 23;
7
CA 02805539 2016-12-08
PPH
Figs. 25 shows a flowchart of a method of a Using Services process in the
flowchart shown in
Fig. 19; and
Figs. 26 shows a detailed block diagram of the system shown in Fig. 12 with
elements referenced
in the flowchart of Fig. 25.
The accompanying drawings are included to provide a further understanding of
the
present invention and are incorporated in and constitute a part of this
specification. The drawings
illustrate some embodiments of the present invention and together with the
description serve to
explain the principles of the invention. Other embodiments of the present
invention and many of
the intended advantages of the present invention will be readily appreciated
as they become
better understood by reference to the following detailed description. The
elements of the
drawings are not necessarily to scale relative to each other. Like reference
numerals designate
corresponding similar parts.
DETAILED DESCRIPTION OF EMBODIMENTS OF THE INVENTION
Embodiments of the present invention address deficiencies in conventional
authentication
and authorization processes when remote connections are used to access
computing services. The
process of authorization is distinct from that of authentication. Whereas
authentication is the
process of verifying that "you are who you say you are", authorization is the
process of verifying
that "you are permitted to do what you are trying to do". Authorization thus
presupposes
authentication.
Various embodiments of the present invention will be described in general
using
summary flowcharts and block diagrams with each general description followed
by detailed
flowcharts and block diagrams.
Referring to Fig. 1 there is shown a summary flowchart of a method 100 of a
first =
embodiment of the present invention; and in Fig. 2 there is shown a block
diagram 200 of a
system including elements referred to in the flowchart 100 in Fig. 1.
8
CA 02805539 2016-12-08
PPH
Firstly, a user 202 and a user device 204, or a client device 204, the two
terms to be used
interchangeably in this application, are authenticated 102. The user device
204 may be, for
example, a personal computer, tablet computer, a smart phone, or any other
device suitable for
the user 202 to remotely access desired services.
Next, a remote desktop connection 206 is established 104 from the client
device 204 to a
server computer 210. The remote desktop connection 206 may be made through a
network such
as, for example, the Internet 208, a LAN (local area network), WAN (wide area
network), or the
like. The remote desktop connection 206 may be based on conventional protocols
such as RDP
(Remote Desktop Protocol) or VNC (Virtual Network Computing) protocols or the
like. The
server computer 210 may be, for example, be a computing system within a bank,
on-line retailer
or any other like institution offering one or more predetermined on-line
service(s) 214. In
general, the server computer 210 may be, for example, a computer having a
processor configured
to execute instructions stared in a memory (not shown). For clarity, the
predetermined services
214 comprise computer readable instructions stored in the memory of the server
computer 210.
As well, the server program comprises computer readable instructions stored in
the memory of
the server computer 210.
All modules or blocks shown inside the client device 204 and the server
computer 210
comprise computer readable instructions stored in a non-transitory computer
readable storage
medium, such as computer memory, CD-ROM, DVD or similar, for retrieval and/or
execution by
a processor.
Next, a server program 212 executing on the server computer 210 authorizes 106
the user
202 to access and use the predetermined services 214 on the server computer
210 that are
available to the authenticated user 202 and authenticated client device 204.
Next, the user 202 uses 108 the predetermined services 214 in a conventional
manner.
When the user 202 is finished using the predetermined services 214, the user
202 closes
110 the RDP connection 206. Optionally, the user 202 may repeat 112 the
connection 104 to
closing 110 processes as many times as desired without repeating the
authentication 102 process.
9
CA 02805539 2016-12-08
PPH
The authentication 102 process will now be described in more detail with
reference to the
flowchart shown in Figs. 3A and 3B; and the block diagrams shown in Figs. 4A
and 4B. For
clarity, a layout guide 302 shows an arrangement of Figs. 3A and 3B.
First, the client device 204 establishes 304 a secure connection 402 with the
server
computer 210. The secure connection 402 may be based on any secure protocol
known in the art
such as SSL (Secure Sockets Layer), TLS (Transport Layer Security), or the
like.
Then server program 212 sends 306 an invitation in including a URL (Uniform
Resource
Location) for downloading 312 a client program 408 from, for example, a
download site on the
Internet 208. The invitation may optionally include a registration code (not
shown). The
invitation 404 may be sent via email or any other conventional message system.
The client
program 408, after downloading 312, comprises computer readable instructions
stored in a
memory (not shown) of the client device 204.
Having received the invitation 404 the user decides 308 to accept the
invitation 404 or
not. If the user 202 does not accept the invitation 404 the authentication
process 102 fails and the
authentication process stops 310.
If the user 202 accepts the invitation, the user 202 downloads 312 the client
program 408
using the provided URL 406 to the client device 204 and initiates execution of
the client program
408 on the client device 204.
The user 202 enters 314 a predetermined user PIN (Personal Identification
Number) 410
to the client program 408. The predetermined PIN 410 may be, for example, a
secret number
known only to the user 202, or biometric information entered using
conventional hardware (not
shown) included in the client device 204.
The client program 408 sends 316 the user PIN 410, a client device ID 413,
and,
optionally, the registration code 404 to the server program 212. The client
device ID 413 is a
copy made by the client program 408 when the client program 408 is initially
executed 312 of a
static dev ID 412 unique to the client device 404 that is determined at time
of manufacture.
CA 02805539 2016-12-08
PPH
Beneficially, at any time after the authentication process 102, the client
program 408 may
compare the copy of the client device ID 413 with the static device ID 412 for
increased security.
The server program 212 generates a random number for providing 318 a secret
key 414.
The random number may be generated by any process known in the art.
The server program 212 encrypts 320 the secret key 414 using the user PIN 410
and the
client device ID 413 as keys to provide an encrypted secret key 416. The
secret key 414 may be
encrypted, for example, using any suitable algorithm known in the art such as
AES (Advanced
Encryption Standard) or the like.
The server program 212 sends 322 the encrypted secret key 416 to the client
program 408
over the secure connection 402.
The client program 408 decrypts 324 the encrypted secret key 416 using the
user PIN 410
and the client device id 413 as keys.
The user 202 enters 326 user account credentials 418 into the client program
408.
Optionally, the server program 212 encrypts 328 the user account credentials
418 with the
secret key 414. The server program 212 sends 330 the encrypted user account
credentials (not
shown) to the client program 408. The client program 408 decrypts 332 the
encrypted user
account credentials.
The client program 408 closes 324 the secure connection 402.
Fig 4B shows the system 200 after completion of the authentication process
102. The user
202 and the client device 204 are now authenticated since the user 202 and the
client device
share the predetermined user PIN; and the client program 408 and server
program 212 share the
secret key 414. After the authentication process 102 the client device 204 is
what is known in the
art as a trusted device.
11
CA 02805539 2016-12-08
PPH
Figs. 5 shows a flowchart of a method of the connection process 104 in the
flowchart
shown in Fig. 1; and Fig. 6 shows a detailed block diagram of the system 200
shown in Fig. 2
with elements referenced in the flowchart of Fig. 5.
The user 202 enters 502 a PIN 602 into the client program 408. The entered
user PIN 602
is compared 504 with the predetermined user PIN 410. If the entered user PIN
602 and the
predetermined user PIN 410 do no match, the connection process 104 is stopped
506. If the
entered user PIN 602 and the predetermined user PIN 410 do match then the
connection process
104 continues.
The client program 408 establishes 508 a remote desktop connection 206 from
the client
device 204 to the server computer 210. The remote desktop connection may be a
RDP (Remote
Desktop Protocol) or VNC (Virtual Network Computing) connection or the like.
The server
program 212 detects 510 the remote desktop connection 206 and creates a
blocking window 606
on a server desktop 608. The blocking window may be for example a modal dialog
box. Such a
dialog box, as understood in the art, blocks all other user access until
certain inputs or actions are
provided. In this case the action is the authorization of the user 202 as
describe herein below. In
general, any type of process or program that blocks the user 202 from
accessing any services on
the server computer 210 until the user 204 is authorized is within the scope
of the invention.
Figs. 7 shows a flowchart of a method of the authorization process 106 in the
flowchart
shown in Fig. 1 and Figs. 8 shows a detailed block diagram of the system 200
shown in Fig. 2
with elements referenced in the flowchart of Fig. 7.
First, the client program 408 creates 702 a client OTA code 802 by combining
dynamic
connection information 804 with the secret key 414. The dynamic connection
information 804
may be, for example, an IP (Internet Protocol) address, port number, time
stamp or any
combination thereof. The dynamic connection information 804, secret key 414,
and dynamic
connection information 804 are combined using a one-way function such as
exclusive OR, or
any other one-way function known in the art.
12
CA 02805539 2016-12-08
PPH
Next, the client program 408 copies 704 the client OTA code 802 to a shared
clipboard
806.
Next, the server program 212 detects 706 the client OTA code on the shared
clipboard
806. The server program 212 creates 708 a server OTA code 810 by combing the
dynamic
connection information 808 with the secret key 414. The dynamic connection
information 808
may be, for example, an IP (Internet Protocol) address, port number, time
stamp or any
combination thereof. The dynamic connection information 804 is the same as the
dynamic
connection information 808 on the server computer 210. The dynamic connection
information
808 and secret key 414 are combined using the same one-way function as in
creating the client
OTA code 802 described herein above.
Next, the server program 212 compares 710 the server OTA code 810 with the
client OTA
code 802. If the server OTA code 810 does not match the client OTA code 802,
then the blocking
window 606 remains 714 and the authorization process 106 is stopped.
If the server OTA code 810 does match the client OTA code 802, then the server
program
212 removes 716 blocking window 606 from the server desktop 608.
Figs. 9 shows a flowchart of a method of the Using Services 108 process in the
flowchart
shown in Fig. I; and Fig. 10 shows a detailed block diagram of the system 200
shown in Fig. 2
with elements referenced in the flowchart of Fig. 9.
First, preferably the client program 408 automatically signs into 902 the
service 214
using the user account credentials 418, or alternatively the user 202 manually
signs into the
service 214. Then the user 202 uses 904 the service 214 in a conventional
manner from the client
device 204 such as bank accounts or online retail services. After the user 202
is finished, the user
202 signs out 906 of service 214.
Lastly, the user closes 110 the RDP connection 206 in a conventional manner.
Referring now to Fig. 11, there is shown a summary flowchart of a method 1110
in
accordance with a second embodiment of the present invention; and Fig. 12
shows an overview
13
CA 02805539 2016-12-08
PPH
block diagram of a system 1200 in accordance with the second embodiment of the
present
invention with elements referenced in the flowchart of Fig. 11.
Firstly, a user 202 and a user device 204 are authenticated 102. The
authentication
process 102 of the second embodiment is identical to the authentication
process of the first
embodiment 102 as described herein above. The user device 204 is preferably
mobile device
such as a smart phone, PDA (Personal Digital Assistant) or the like having a
camera with QR
(Quick Response) code reading capability as is common in the art.
Next, a remote desktop connection 206 is established 104 from a client
terminal 1202 to
the server computer 210.
Next, a server program 212 authorizes 1106 the user 202 from the client
terminal 1202 to
access and use the predetermined services 214 on the server computer 210 that
are available to
the authenticated user 202 and authenticated client device 204. The client
terminal may be, for
example, a public shared computer in a cafe or library not previously
authenticated.
Next, the user 202 uses 108 the predetermined services 214 in a conventional
manner.
When the user 202 is finished using the predetermined services 214, the user
202 closes
110 the RDP connection 206. Optionally, the user 202 may repeat 1112 the
connection 104 to
closing 110 processes as many times as desired without repeating the
authentication 102 process.
Figs. 13 shows a flowchart of a method of the connection process 1100 in the
flowchart
shown in Fig. 11; and Figs. 14 shows a detailed block diagram of the system
shown in Fig. 2
with elements referenced in the flowchart of Fig. 13.
First, the user 202 establishes 1302 a remote desktop connection 206 from the
client
terminal 1202 to the server computer 210.
Next, the server program 212 detects 1304 the remote desktop connection 206
and creates
a blocking window 606 on the server desktop 608.
14
CA 02805539 2016-12-08
PPH
Next, the server program 212 provides 1306 a QR code 1402 including the
dynamic
connection information 808 in the blocking window 606.
Next, the user 202 enters 1308 a user pin 602 into the client program 408. The
entered
PIN 602 is compared 1310 with the predetermined user PIN 410. If the entered
user PIN 602 and
the predetermined user PIN 410 do no match, the connection process 1104 is
stopped 1312. If the
entered user PIN 602 and the predetermined user PIN 410 do match then the
connection process
1104 continues.
Next, the user 202 holds the client device 204 in a position for the client
program 408 to
read 1314 the QR code 1402 and provide the dynamic connection information 808
to the client
program 408.
Figs. 15 shows a flowchart of a method of the authorization process 1104 in
the flowchart
shown in Fig. 11; and Fig. 16 shows a detailed block diagram of the system
1200 shown in Fig.
12 with elements referenced in the flowchart of Fig. 15.
First, the client program 408 creates 1502 a client OTA code 802 by combining
the
dynamic connection information 806 with the secret key 414.
Then the client program 408 sends 1506 the client OTA code 802 to the server
program
212 on an authorization channel 1602. The authorization channel 1602 may be
based on any
secure protocol known in the art such as SSL (Secure Sockets Layer), TLS
(Transport Layer
Security), or the like.
Then the server program 212 creates 1508 a server OTA code by combing the
dynamic
connection information 808 with the secret key 414.
Then the server program 212 compares 1510 the server OTA code 810 with the
client
OTA code 802. If the server OTA code 810 does not match the client OTA code
802, then the
blocking window 606 remains 1514 and the authorization process 106 is stopped.
If the server OTA code 810 does match the client OTA code 802, then the server
program
212 removes '516 blocking window 606 from the server desktop 608.
CA 02805539 2016-12-08
PPH
Figs. 17 shows a flowchart of a method of a Using Services process in the
flowchart
shown in Fig. 11; and Figs. 18 shows a detailed block diagram of the system
shown in Fig. 12
with elements referenced in the flowchart of Fig. 17.
The user 202 signs 1702 into the service 214 with the user account credentials
418 in the
remote desktop 610 on the client terminal 1202. The user 202 uses 704 the
service 214 in a
conventional manner from the client terminal 1202. The user 202 signs out 1706
of service 214
Lastly, the user 202 closes 1110 the RDP connection 206 in a conventional
manner.
Fig. 19 shows a summary flowchart of a method 1900 in accordance with a third
embodiment of the present invention; and Fig. 20 shows an overview block
diagram of a system
2000 in accordance with the third embodiment of the present invention with
elements referenced
in the flowchart of Fig.19.
Firstly, a user 202 and a user device 204 are authenticated 102 using a
process identical to
the process 102 described in the first embodiment
Next, a SSH (secure shell) connection 2002 is established 1904 from the client
device
204 to the server computer 210.
Next, a server program 212 authorizes 1906 the user 202 to access and use the
predetermined services 214 on the server computer 210 that are available to
the authenticated
user 202 and authenticated client device 204.
Next, the user 202 uses 1908 the predetermined services 214 in a conventional
manner.
When the user 202 is finished using the predetermined services 214, the user
202 closes
110 the SSH connection 2002. Optionally, the user 202 may repeat 1912 the
connection 1904 to
closing 1910 processes as many times as desired without repeating the
authentication 102
process.
16
CA 02805539 2016-12-08
PPH
Figs. 21 shows a flowchart of a method of the connection process 1904 in the
flowchart
shown in Fig. 19; and Figs. 22 shows a detailed block diagram of the system
shown in Fig. 20
with elements referenced in the flowchart of Fig. 21.
First, the user 202 enters 2102 a PIN 602 into the client program 408. The
entered user
PIN 602 is compared 2104 with the predetermined user PIN 410. If the entered
user PIN 602 and
the predetermined user PIN 410 do no match, the connection process 1904 is
stopped 2106. If the
entered user PIN 602 and the predetermined user PIN 410 do match then the
connection process
1904 continues.
Next, the client program 408 establishes 2108 a secure shell connection 2002
from the
client device 204 to the server computer 210. The server program 212 detects
2110 the secure
shell connection 2002 and a blocking program 2204 in the secure shell 2202.
Figs. 23 shows a flowchart of a method of an authorization process in the
flowchart
shown in Fig. 19; and Figs. 24 shows a detailed block diagram of the system
shown in Fig. 20
with elements referenced in the flowchart of Fig. 23.
The authorization process for the third embodiment 1906 is substantially the
same as the
first embodiment 106 except that the server program 212 removes 2118 the
blocking program
2204 from the secure shell 2202.
Figs. 25 shows a flowchart of a method of the Using Services process in the
flowchart
shown in Fig. 19; and Figs. 26 shows a detailed block diagram of the system
shown in Fig. 20
with elements referenced in the flowchart of Fig. 25.
First, the user 202 signs into 2502 service 214 in the remote shell 2206. The
user 202
uses 2504 the service 214. The user 202 signs out 2506 of service 214.
Therefore embodiments of the present invention expand a shared environment
between
the client and the server elements, which require the following:
Separating the authentication process from the authorization process;
17
CA 02805539 2016-12-08
PPH
Reversing a conventional sequence of access and connection processes by
establishing a
connection first, so that dynamic connection link information can be used as
an input for
generating stronger, more secure OTA codes that are uniquely associated with
the connection.
This authorization process authorizes the user for a specific run-time
connection that has been
established, since the dynamic connection information forms part of the OTA
code.
Embodiments of the present invention provide an improved authorization process
for
securely accessing remote computing services, such as data centers and various
services based on
cloud computing models, for example. Furthermore, embodiments of the present
invention
provide a real-time method for generating and verifying a One-Time
Authorization (OTA) code.
This method is based on the client program and server program sharing the
static and dynamic
information for generating and verifying OTA codes:
Accordingly, it is to be understood that the embodiments of the invention
herein
described are merely illustrative of the application of the principles of the
invention. Reference
herein to details of the illustrated embodiments is not intended to limit the
scope of the claims,
which themselves recite those features regarded as essential to the invention.
TABLE OF ELEMENTS
100 Flowchart of a first embodiment
102 to 112 Processes of flowchart 100
200 System block diagram of the first embodiment
202 User
204 Client Device
206 RDP Connection
208 Internet
210 Server Computer
18
CA 02805539 2016-12-08
PPH
212 Server Program
214 Service(s)
302 Layout guide to Figs. 3A and 3B
304 to 324 Processes of Authentication 102 shown in Fig. 1
402 Secure Connection
404 Invitation
406 Download URL
408 Client Program
410 Predetermined User Pin
412 Static Client Device ID
413 Client device ID (copy)
414 Secret Key
416 Encrypted Secret Key
418 User Account Credentials
502 to 510 Processes of Connection 104 shown in Fig. 1
602 Entered User PIN
604 Static Connection Information
606 Blocking Window
608 Server Desktop
19
CA 02805539 2016-12-08
PPH
610 Remote Desktop
702 to 718 Processes of Authorization 106 shown in Fig. 1
802 Client OTA Code
804 Client Dynamic Connection Information
806 Shared Clipboard
808 Server Dynamic Connection Information
810 Server OTA Code
902 to 906 Processes of Using Services 108 shown in Fig. 1
1100 Flowchart of a second embodiment
102, 1104 to 1112 Processes of flowchart 1100
1200 System block diagram of the second embodiment
1202 Client terminal
1302 to 1314 Processes of connection 1104 shown in Fig. 11
1402 QR code
1502 to 1516 Processes of authorization 1106 shown in Fig. 11
1602 Authorization channel
1702 to 1706 Processes of Using Services 1108 shown in Fig. 11
1900 Flowchart of a third embodiment
102, 1904 to 1912 Processes of flowchart 1900
CA 02805539 2016-12-08
PPH
2000 System block diagram of the third embodiment
2002 Secure shell connection
2102 to 2110 Processes of connection 1904 shown in Fig.
19
2202 Shell
2204 Blocking program
2206 Remote shell
2302 to 2318 Processes of authorization 1906 shown in
Fig. 19
2502 to 2506 Processes of using 1908 show in Fig. 19
Thus, an improved system, method and apparatus for secure remote connection to
computing services have been provided.
Although the embodiments of the invention have been described in detail, it
will be
apparent to one skilled in the art that variations and modifications to the
embodiment may be
made within the scope of the following claims.
21