Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
CREDIT CARD WITH BUILT-IN SENSOR FOR FRAUD DETECTION
CROSS-REFERENCE TO RELATED APPLICATIONS
100011 This application claims the benefit of the following United States
non-
provisional application, which is hereby incorporated by reference in its
entirety: United
States Non-Provisional Application Number 14/505,254, filed October 2, 2014.
BACKGROUND
100021 The present disclosure relates to a credit card system and method,
and
more particularly, to a credit card system and method with reduced potential
of credit card
number miSilsC.
100031 The development of retail electronic commerce has been relatively
slow
in spite of the perceived demand for such trade. One great deterrent to the
expansion of
retail electronic commerce is the potential for fraud. This potential for
fraud has been a
major concern for the credit card companies and financial institutions, as
well as the
customers and the providers of the goods and services.
100041 Credit card companies have an efficient credit card system, which
operates well for face-to-face transactions, i.e., "card present" transactions
where the credit
card is physically presented to a trader, so that the trader can obtain the
credit card number
and compare signatures before accepting a particular credit card.
100051 There are also particular personal concerns for the consumer in that
the
fraudulent use of the credit card number may not become apparent for some
time. This can
happen even if the card is still in the authorized cardholder's possession.
Further, when
fraud does occur, the consumer has the task of persuading the credit card
provider that
fraud by another did indeed occur.
100061 There is also the additional fear of being overcharged on a credit
card.
There are thus particular risks for those credit cardholders who have
relatively high
spending limits, in that if fraud should occur, it may be some considerable
time before it is
detected. One particular form of fraud, referred to as "skimming," is
particularly difficult to
control. What happens is that the cardholder proffers his or her card at an
establishment to
-1-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
make a transaction, the relevant information is electronically and/or
physically copied from
the card, and the card is subsequently reproduced. This can be a particular
problem with
travelers, particularly during an extensive period of travel, as the
fraudulent card may turn
up in other places, and it may be some considerable time before the fraud is
detected.
100071 For remote credit card use, the credit cardholder has to provide
details of
name, credit card number, expiration date, Card Verification Value (CVV)
number, and
often many other pieces of information for verification, such as address,
password, date-of-
birth and/or various password-verifying information. The storing and updating
of the
information is expensive but necessary. This in and of itself is a
considerable security risk,
as one will appreciate that this information could be used to fraudulently
charge goods and
services to the cardholder's account or to obtain unauthorized access other
accounts or
resources of the user that may use the same types of information. Such
fraudulent use is not
limited to those people to whom the credit card information has been given
legitimately, but
extends to anybody who can illegitimately obtain such details. A major problem
in relation
to this form of fraud is that the credit card may still be in the possession
of the legitimate
holder as these fraudulent transactions are taking place. This is often
referred to as
"compromised numbers" fraud. Indeed, this fraud requires only one dishonest or
negligent
staff member, for example in a shop, hotel or restaurant, to record or
accidentally transmit
the credit card number. It is thus a distinct problem from theft of the
physical card.
100081 Certain current approaches to the limiting of credit card fraud rely
on the
theft of a card being reported and elaborate verification systems, whereby
altered patterns
of use initiate some inquiry from the credit card company. Many authorized
credit
cardholders receive telephone calls, or even have their legitimate use of a
card suspended,
when their use of the card has been exceptional or otherwise unusual in the
eyes of the
organization that provides the verification services. In cases of valid card
use, these
interruptions can be invasive and quite frustrating to consumers.
100091 Thus, there have been many developments in an effort to overcome
this
fundamental problem. of fraud, both in the general area of fraud for ordinary
use of credit
cards and for the particular problems associated with such remote use. A need
exists for
improved methods and systems for detecting and preventing fraud, while
avoiding the
difficulties in current methods.
-2-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
SUMMARY
100101 A card according to one disclosed non-limiting embodiment of the
present disclosure includes a sensor, which may include an imaging system
and/or a system
for recording audio. The sensor may include a video camera, a still camera, an
audio
recorder, or other facility for recording images and/or sounds in the
environment of the
card. References throughout this disclosure to a camera, a video camera, an
imaging
system, or a recording system should be understood to encompass all of these
embodiments
of recording of images and/or audio, except where context may prevent.
100111 A credit card system according to one disclosed non-limiting
embodiment of the present disclosure includes a first surface and a second
surface. The
first surface may include an account number and at least one of the first
surface and the
second surface may include an sensor system, such as a video camera. The card
system may
include a control module in communication with the sensor system and a
communication
system in communication with the control module.
100121 A method of credit card fraud detection according to another
disclosed
non-limiting embodiment of the present disclosure includes flagging suspicious
activity on
a credit card and prompting a user to take a self-image or to record the
user's voice via the
camera of the credit card.
100131 The foregoing features and elements may be combined in various
combinations without exclusivity, unless expressly indicated otherwise. These
features and
elements as well as the operation thereof will become more apparent in light
of the
following description and the accompanying drawings. It should be understood,
however,
the following description and drawings are intended to be exemplary in nature
and non-
limiting.
BRIEF DESCRIPTION OF THE DRAWINGS
100141 Various features will become apparent to those skilled in the art
from the
following detailed description of the disclosed non-limiting embodiment. The
drawings
that accompany the detailed description can be briefly described as follows:
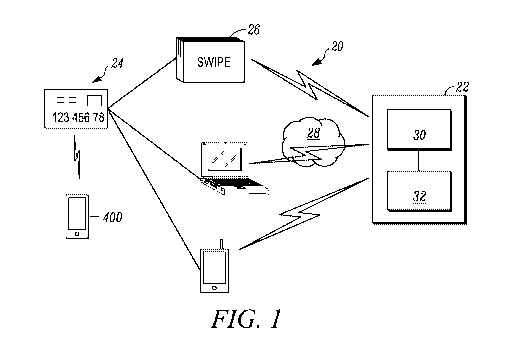
100151 Figure 1 is a schematic view of a credit card system;
100161 Figure 2 is a schematic view of a credit card with a camera
according to
one disclosed non-limiting embodiment; and
-3-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
100171 Figure 3 is a flow chart illustrating a method of credit card fraud
detection according to another disclosed non-limiting embodiment of the
present disclosure.
DETAILED DESCRIPTION
[00181 Figure I schematically illustrates a credit card system 20. The
system 20
generally includes a transactional processing system 22, which, accordingly to
exemplary
embodiments, may be operated by a host, such as the credit card provider or a
third party
processor on behalf of the credit card provider. Generally, this transactional
processing
system 22 receives and processes credit card transactions that are generated
at retail locations
or at locations remote from the card. The credit card transactions can
originate from a
merchant in the conventional manner, e.g., by swiping a credit card 24 through
a card swipe
unit 26. Alternatively, the credit card transaction requests can originate
from any device,
such as an electronic device (e.g., a personal computer, laptop, mobile phone,
tablet, or other
consumer device). The device can interface with the transactional processing
system. 22
through any type of network, including any type of public or propriety
network, or some
combination thereof, for instance, via the Internet 28. The transactional
processing system 22
can also interface with other types of devices, such as wireless (e.g.,
cellular telephone)
devices.
100191 The transactional processing system 22 may include a processing
facility, such as a processing system 30, that may interface with a data
storage facility, such
as a database system 32 that stores information regarding customers' accounts,
such as
information regarding various conditions that apply to each customer's
account. The
processing facility 30 can internally perform the approval and denial of
credit card
transaction requests by making reference to credit history information and
other
information in the conventional manner. Alternatively, this function can be
delegated to a
separate clearance processing facility as well as to a distributed
transactional processing
system. It should be understood that the transactional processing system 22,
the processing
system 30, and the database system 32 may be distributed across multiple
locations as
might be understood by one of skill in the art.
100201 With reference to Figure 2, the credit card 24, as generally
understood,
typically includes an account number 100 on one surface 102 of the credit card
24 and a
magnetic strip 104 on the opposite surface 106 of the credit card 24. In the
case of smart
cards, the card may include a chip in addition to, or as an alternative to,
the magnetic strip.
-4-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
The size of a typical credit card is typically about 3 3/8 x 2 1/8 in (85.60 x
53.98 mm),
conforming to the ISO/IEC 7810 ID-1 standard. Credit cards have an account
number 100
complying with the ISO/IEC 7812 numbering standard. Both of these standards
are
maintained and further developed by ISO/IEC JTC 1/SC 17/WO I.
100211 The account number 100 refers herein to the account number allocated
by the provider to the authorized card user for his or her account. The
account number 100
is typically raised from the surface 102 of the credit card 24. The magnetic
strip 104 may
often commonly be referred to as a swipe card or magstripe read by swiping
past a
magnetic reading head typical of the card swipe unit 26. In another disclosed
non-limiting
embodiment, the credit card 24 may be dynamic and provide for multiple cared
numbers
100 representative of multiple credit cards such that the single credit card
may essentially
function as many credit cards.
100221 In this specification, except where context prevents, the term
"credit
card" should be understood to encompass credit cards (MaterCard RTM, Visa.RTM,
etc.),
charge cards (e.g., American Express RTM, etc), debit cards such as those
usable at ATMs
and many other locations or that are associated with a particular account,
identification
cards (such as a driver's license, student ID, library card, and the like),
and various hybrids
thereof that are often carried by a person to purchase goods and services or
to allow access
to the same, as well as provide identification. The identification card, which
may be used
to verify aspects of a person's personal identity issued in the form of a
relatively small,
mostly standard-sized card is usually called an identity card or ID.
100231 The credit card 24 generally includes a control module 200 with a
processor 202, a memory 204, and an interface 206. The processor 202 may be
any type of
microprocessor or processors having desired performance characteristics. The
memory 204
may include any type of computer readable medium that stores the data and
control
algorithms 220 described herein below. Other operational software for the
processor 202
may also be stored in the memory 204. The interface 206 facilitates
communication with
other systems such as a sensor 208, a communication system 210, a geo-location
system
212, a display system 214, and/or an input/output device 216. It should be
appreciated that
although particular subsystems are separately defined, each or any of the
subsystems may
be combined or segregated via hardware and/or software of the system.
-5-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
100241 Examples of the sensor 208 include, but are not limited to, video
cameras, digital cameras, imaging systems, charge coupled devices, audio
recording
systems, forward looking infrared, thermal systems and/or other imaging
sensors and
combinations thereof. The foregoing may have various optical elements,
including lenses,
micro-lenses, CMOS sensors and the like. It should be appreciated that other
sensors, in
addition, or alternatively to the image sensors such as a microphone will also
benefit
herefrom. That is, the sensor 208 may essentially take an image of the user's
face or voice
to provide authorization.
100251 Examples of the communication system 210 include, but are not
limited
to, a wireless communication interface such as a wireless LAN (Wi-Fi)
interface, cellular
network interface, or other communication interface that ultimately permits
communication
with the transactional processing system 22 through any type of communication
interface
including any type of public or propriety networks, or some combination
thereof, for
instance, via the Internet 28 (Figure 1).
100261 Examples of the geo-location system 212 include, but are not limited
to,
Global Positioning Systems, radio navigation, and others.
100271 Examples of the display system 214 include, but are not limited to,
a
liquid crystal display, light emitting diode (LED) displays, video display, HD
display, text
display, speakers, or other communication element that provides visual or
audible
communication with the cardholder.
100281 Examples of the input/output device 216 include, but are not limited
to, a
button that triggers the sensor 208. It should be appreciated that the
input/output device
216 may alternatively or additionally be displayed by the display system 214
and need not
be a physical button. In embodiments, the sensor 208 may be triggered
remotely, such as to
record images and/or audio in the environment of the card, such as to record a
party that
may have stolen the card or to verify images and/or sounds in the environment
of the card,
such as to indicate or confirm the location of the card in a particular
environment.
100291 Examples of the power source 218 include, but are not limited to, a
battery, fuel cell, or other active power source. Alternatively, a passive
power source such
a device that generates power from movement may be provided. Alternatively
still, the
power source 218 may derive power from an external source such as the action
of swiping
the credit card in the card reader or a placing the card in a chip reader.
-6-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
100301 With reference to Figure 3, in one disclosed non-limiting
embodiment,
an algorithm for operation of the credit card 24 is schematically illustrated.
The functions
of the algorithm 220 are disclosed in terms of fimctional block diagrams and
it should be
appreciated by those skilled in the art with the benefit of this disclosure
that these functions
may be enacted in either dedicated hardware circuitry or programmed software
routines as a
computer readable storage medium capable of execution as instructions in a
microprocessor-based electronics control embodiment such as the control module
200.
That is, the memory 204 is an example computer storage media having embodied
thereon
computer-useable instructions such as the algorithms 220 that, when executed,
performs a
method 300 of credit card fraud detection.
10031.1 The method 300, effectuated by the algorithm 220, may be initiated
by
credit card fraud detection algorithms of the transactional processing system
22 (Figure 1)
that have flagged suspicious activity on the credit card 24 (step 302). That
is, in response to
the use of the credit card 24, the credit card fraud detection algorithms off
board of the
credit card 24 may "flag" the transaction for suspicious activity. It should
be appreciated
that the algorithm 220 may be performed on board the credit card 24 such as
via the control
module 200, off board the credit card 24 such as via the remote processing
center 22, or
combinations thereof as well as in a distributed or cloud based system.
100321 In response to "flagging" of a transaction for suspicious activity,
the
remote processing center 22 will prompt the user to take an image of
themselves (step 304)
via the imaging system 208. That is, the cardholder must take an image of
himself or
herself that would be sufficient to, for example, be processed by facial
recognition
software. Further, the initial card authorization process may require the user
to take an
image sufficient to provide a baseline on file for later facial recognition
matching in an
automated manner.
100331 In one disclosed non-limiting embodiment, the prompt may be
communicated via a transaction interface, such as shopping cart, during an
Internet
purchase. That is, the website checkout may require the cardholder to take a
self-picture
prior to completion of the transaction. Alternatively, or in addition, the
prompt may be
provided on the credit card 24 such as, via a message on the display system
214, or a
flashing light. Alternatively, or in addition, the prompt may be provided to a
device 400 of
the authorized cardholder, such as via text message to a mobile phone.
Alternatively, the
-7-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
prompt may be provided by a device at a retailer, such as the card reading
system at a point
of sale system of the retailer.
100341 In another disclosed non-limiting embodiment, the transactional
processing system 22 will initiate selective operation of the imaging system
208 without
user initiation (step 306). Such selective operation may be initiated upon the
credit card 24
being separated from. the device 400 (Figure 1) by a predetermined distance
determined via
the geo-location system 212, or movement of the credit card 24 to a location
not typical of
the authorized cardholder.
In one disclosed non-limiting embodiment, the image is then transmitted to the
transactional processing system 22 (step 306), where the image is matched with
the
authorized cardholder's image that is on file (step 308). Matching may be
based on facial
recognition technology. Facial recognition may be accomplished by any of a
variety of
known techniques, including geometric techniques that look at distinguishing
facial features,
such as size, relative size, distances, and angles among recognizable
elements, such as eyes,
nose, mouth, chin, and the like, and including photometric or statistical
approaches that
reduce elements (e.g., pixels) or regions of image into values that are
compared with
templates to identify the extent of variances. Any technique known to one of
ordinary skill in
the art is intended to be encompassed herein, including linear discriminate
analysis, principal
component analysis using Eigen faces, hidden Markov models, elastic bunch
graph matching
(e.g., using the Fisherface algorithm), and learning models (e.g., multi-
linear subspace
learning using tensor representations and neuronal motivated dynamic link
matching).
Matching may also be based on voice recognition technology, also known as
speaker
recognition or verification technology. This may include various approaches
known to those
of skill in the art, including techniques that use acoustical features that
emerge from the
anatomy of the user and behavioral techniques that relate to pitch, frequency,
or patterns of
speaking by an individual. If the match is determined (e.g., if a match
percentage is above a
certain threshold in a statistical technique), then the transaction
transactional processing
system. 22 can ascertain that the person who has the card is the authorized
cardholder and the
block or flag on suspicious activity can be lifted. If the match percentage is
below the
threshold, a further 'flag' is placed on the transaction as potentially
fraudulent and a full hold
may be put on the credit card 24 until the authorized cardholder contacts the
remote
processing center 22 to resolve the issue.
-8-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
100351 In another disclosed non-limiting embodiment, the image of the user
captured by the sensor 208 during a transaction may be processed on the credit
card 24
itself to confirm that the image is matched with the authorized cardholder's
image, such as
comparing to an image that is stored in the memory 204 during the initial card
authorization
process. In this non-limiting embodiment, no communication with the
transaction
transactional processing system 22 need be performed unless, for example, the
match
percentage or other indicator of facial or voice recognition is below the
threshold and the
authorized cardholder must contact the remote processing center 22 to resolve
the issue.
100361 The credit card 24 disclosed herein envisions a further way to
ascertain
that the credit card is in the hands of the authorized cardholder through an
automated image
matching mechanism. Of course this does not apply when the physical card
itself is in the
possession of the cardholder but the account number has been compromised.
Also,
leveraging a card built-in camera for fraud detection would be an additional
deterrent to
theft of physical credit cards.
100371 The methods and systems described herein may be deployed in part or
in
whole through a machine that executes computer software, program codes, and/or
instructions on a processor. The processor may be part of a server, client,
network
infrastructure, mobile computing platform, stationary computing platform, or
other
computing platform. A processor may be any kind of computational or processing
device
capable of executing program instructions, codes, binary instructions and the
like. The
processor may be or include a signal processor, digital processor, embedded
processor,
microprocessor or any variant such as a co-processor (math co-processor,
graphic co-
processor, communication co-processor and the like) and the like that may
directly or
indirectly facilitate execution of program code or program instructions stored
thereon. In
addition, the processor may enable execution of multiple programs, threads,
and codes. The
threads may be executed simultaneously to enhance the performance of the
processor and to
facilitate simultaneous operations of the application. By way of
implementation, methods,
program codes, program instructions and the like described herein may be
implemented in
one or more thread. The thread may spawn other threads that may have assigned
priorities
associated with them; the processor may execute these threads based on
priority or any
other order based on instructions provided in the program code. The processor
may include
memory that stores methods, codes, instructions and programs as described
herein and
-9-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
elsewhere. The processor may access a storage medium through an interface that
may store
methods, codes, and instructions as described herein and elsewhere. The
storage medium
associated with the processor for storing methods, programs, codes, program
instructions or
other type of instructions capable of being executed by the computing or
processing device
may include but may not be limited to one or more of a CD-ROM, DVD, memory,
hard
disk, flash drive, RAM, ROM, cache and the like.
100381 A processor may include one or more cores that may enhance speed and
performance of a multiprocessor. In embodiments, the process may be a dual
core
processor, quad core processors, other chip-level multiprocessor and the like
that combine
two or more independent cores (called a die).
100391 The methods and systems described herein may be deployed in part or
in
whole through a machine that executes computer software on a server, client,
firewall,
gateway, hub, router, or other such computer and/or networking hardware. The
software
program may be associated with a server that may include a file server, print
server, domain
server, intemet server, intranet server and other variants such as secondary
server, host
server, distributed server and the like. The server may include one or more of
memories,
processors, computer readable media, storage media, ports (physical and
virtual),
communication devices, and interfaces capable of accessing other servers,
clients,
machines, and devices through a wired or a wireless medium, and the like. The
methods,
programs or codes as described herein and elsewhere may be executed by the
server. In
addition, other devices required for execution of methods as described in this
application
may be considered as a part of the infrastructure associated with the server.
100401 The server may provide an interface to other devices including,
without
limitation, clients, other servers, printers, database servers, print servers,
file servers,
communication servers, distributed servers and the like. Additionally, this
coupling and/or
connection may facilitate remote execution of program across the network. The
networking
of some or all of these devices may facilitate parallel processing of a
program or method at
one or more location without deviating from the scope of the invention. In
addition, all the
devices attached to the server through an interface may include at least one
storage medium
capable of storing methods, programs, code and/or instructions. A central
repository may
provide program instructions to be executed on different devices. In this
implementation,
-10-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
the remote repository may act as a storage medium for program code,
instructions, and
programs.
100411 The software program may be associated with a client that may
include a
file client, print client, domain client, internet client, intranet client and
other variants such
as secondary client, host client, distributed client and the like. The client
may include one
or more of memories, processors, computer readable media, storage media, ports
(physical
and virtual), communication devices, and interfaces capable of accessing other
clients,
servers, machines, and devices through a wired or a wireless medium, and the
like. The
methods, programs or codes as described herein and elsewhere may be executed
by the
client. In addition, other devices required for execution of methods as
described in this
application may be considered as a part of the infrastructure associated with
the client.
100421 The client may provide an interface to other devices including,
without
limitation, servers, other clients, printers, database servers, print servers,
file servers,
communication servers, distributed servers and the like. Additionally, this
coupling and/or
connection may facilitate remote execution of program across the network. The
networking
of some or all of these devices may facilitate parallel processing of a
program or method at
one or more location without deviating from the scope of the invention. In
addition, all the
devices attached to the client through an interface may include at least one
storage medium
capable of storing methods, programs, applications, code and/or instructions.
A central
repository may provide program instructions to be executed on different
devices. In this
implementation, the remote repository may act as a storage medium for program
code,
instructions, and programs.
100431 The methods and systems described herein may be deployed in part or
in
whole through network infrastructures. The network infrastructure may include
elements
such as computing devices, servers, routers, hubs, firewalls, clients,
personal computers,
communication devices, routing devices and other active and passive devices,
modules
and/or components as known in the art. The computing and/or non-computing
device(s)
associated with the network infrastructure may include, apart from other
components, a
storage medium such as flash memory, buffer, stack, RAM, ROM and the like. The
processes, methods, program codes, instructions described herein and elsewhere
may be
executed by one or more of the network infrastnictural elements.
- I 1-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
100441 The methods, program codes, and instructions described herein and
elsewhere may be implemented on a cellular network having multiple cells. The
cellular
network may either be frequency division multiple access (FDMA) network or
code
division multiple access (CDMA) network. The cellular network may include
mobile
devices, cell sites, base stations, repeaters, antennas, towers, and the like.
100451 The methods, programs codes, and instructions described herein and
elsewhere may be implemented on or through mobile devices. The mobile devices
may
include navigation devices, cell phones, mobile phones, mobile personal
digital assistants,
laptops, palmtops, netbooks, pagers, electronic books readers, music players
and the like.
These devices may include, apart from other components, a storage medium such
as a flash
memory, buffer, RAM, ROM and one or more computing devices. The computing
devices
associated with mobile devices may be enabled to execute program codes,
methods, and
instructions stored thereon. Alternatively, the mobile devices may be
configured to execute
instructions in collaboration with other devices. The mobile devices may
communicate with
base stations interfaced with servers and configured to execute program codes.
The mobile
devices may communicate on a peer to peer network, mesh network, or other
communications network. The program code may be stored on the storage medium
associated with the server and executed by a computing device embedded within
the server.
The base station may include a computing device and a storage medium. The
storage device
may store program codes and instructions executed by the computing devices
associated
with the base station.
100461 The computer software, program codes, and/or instructions may be
stored and/or accessed on machine readable media that may include: computer
components,
devices, and recording media that retain digital data used for computing for
some interval
of time; semiconductor storage known as random access memory (RAM); mass
storage
typically for more permanent storage, such as optical discs, forms of magnetic
storage like
hard disks, tapes, drums, cards and other types; processor registers, cache
memory, volatile
memory, non-volatile memory; optical storage such as CD, DVD; removable media
such as
flash memory (e.g. USB sticks or keys), floppy disks, magnetic tape, paper
tape, punch
cards, standalone RAM disks, Zip drives, removable mass storage, off-line, and
the like;
other computer memory such as dynamic memory, static memory, read/write
storage,
mutable storage, read only, random access, sequential access, location
addressable, file
-12-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
addressable, content addressable, network attached storage, storage area
network, bar
codes, magnetic ink, and the like.
100471 The methods and system.s described herein may transform physical
and/or or intangible items from one state to another. The methods and systems
described
herein may also transform data representing physical and/or intangible items
from one state
to another.
100481 The elements described and depicted herein, including in flow charts
and
block diagrams throughout the figures, imply logical boundaries between the
elements.
However, according to software or hardware engineering practices, the depicted
elements
and the functions thereof may be implemented on machines through computer
executable
media having a processor capable of executing program instructions stored
thereon as a
monolithic software structure, as standalone software modules, or as modules
that employ
external routines, code, services, and so forth, or any combination of these,
and all such
implementations may be within the scope of the present disclosure. Examples of
such
machines may include, but may not be limited to, personal digital assistants,
laptops,
personal computers, mobile phones, other handheld computing devices, medical
equipment,
wired or wireless communication devices, transducers, chips, calculators,
satellites, tablet
PCs, electronic books, gadgets, electronic devices, devices having artificial
intelligence,
computing devices, networking equipments, servers, routers and the like.
Furthermore, the
elements depicted in the flow chart and block diagrams or any other logical
component may
be implemented on a machine capable of executing program instructions. Thus,
while the
foregoing drawings and descriptions set forth functional aspects of the
disclosed systems,
no particular arrangement of software for implementing these functional
aspects should be
inferred from these descriptions unless explicitly stated or otherwise clear
from the context.
Similarly, it will be appreciated that the various steps identified and
described above may
be varied, and that the order of steps may be adapted to particular
applications of the
techniques disclosed herein. All such variations and modifications are
intended to fall
within the scope of this disclosure. A.s such, the depiction and/or
description of an order for
various steps should not be understood to require a particular order of
execution for those
steps, unless required by a particular application, or explicitly stated or
otherwise clear from
the context.
-13-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
100491 The methods and/or processes described above, and steps thereof, may
be realized in hardware, software or any combination of hardware and software
suitable for
a particular application. The hardware may include a dedicated computing
device or
specific computing device or particular aspect or component of a specific
computing
device. The processes may be realized in one or more microprocessors,
microcontrollers,
embedded microcontrollers, programmable digital signal processors or other
programmable
device, along with internal and/or external memory. The processes may also, or
instead, be
embodied in an application specific integrated circuit, a programmable gate
array,
programmable array logic, or any other device or combination of devices that
may be
configured to process electronic signals. It will further be appreciated that
one or more of
the processes may be realized as a computer executable code capable of being
executed on
a machine readable medium.
100501 The computer executable code may be created using a structured
programming language such as C, an object oriented programming language such
as C++,
or any other high-level or low-level programming language (including assembly
languages,
hardware description languages, and database programming languages and
technologies)
that may be stored, compiled or interpreted to run on one of the above
devices, as well as
heterogeneous combinations of processors, processor architectures, or
combinations of
different hardware and software, or any other machine capable of executing
program
instructions.
100511 Thus, in one aspect, each method described above and combinations
thereof may be embodied in computer executable code that, when executing on
one or more
computing devices, performs the steps thereof. In another aspect, the methods
may be
embodied in systems that perform the steps thereof, and may be distributed
across devices
in a number of ways, or all of the functionality may be integrated into a
dedicated,
standalone device or other hardware. In another aspect, the means for
performing the steps
associated with the processes described above may include any of the hardware
and/or
software described above. All such permutations and combinations are intended
to fall
within the scope of the present disclosure.
100521 While the invention has been disclosed in connection with the
preferred
embodiments shown and described in detail, various modifications and
improvements
thereon will become readily apparent to those skilled in the art. Accordingly,
the spirit and
-14-
CA 02961017 2017-03-10
WO 2016/053605 PCT/US2015/049999
scope of the present invention is not to be limited by the foregoing examples,
but is to be
understood in the broadest sense allowable by law.
100531 Except where context indicates otherwise, the terms "cardholder,"
"consumer," "customer," "end user" and "user" are used interchangeably to
refer to an
entity, e.g., an individual, that has been rightfully issued a
credit/debit/charge card number,
e.g., through a contractual arrangement, or that has been authorized to use
such card by
such entity or a representative of such entity.
100541 The use of the terms "a," "an," "the," and similar references in the
context of description (especially in the context of the following claims) are
to be construed
to cover both the singular and the plural, unless otherwise indicated herein
or specifically
contradicted by context. The modifier "about" used in connection with a
quantity is
inclusive of the stated value and has the meaning dictated by the context
(e.g., it includes
the degree of error associated with measurement of the particular quantity).
All ranges
disclosed herein are inclusive of the endpoints, and the endpoints are
independently
combinable with each other.
100551 Although the different non-limiting embodiments have specific
illustrated components, the embodiments of this invention are not limited to
those particular
combinations. It is possible to use some of the components or features from
any of the non-
limiting embodiments in combination with features or components from any of
the other
non-limiting embodiments.
100561 it should be appreciated that like reference numerals identify
corresponding or similar elements throughout the several drawings. It should
also be
appreciated that although a particular component arrangement is disclosed in
the illustrated
embodiment, other arrangements will benefit herefrom.
100571 Although particular step sequences are shown, described, and
claimed, it
should be understood that steps may be performed in any order, separated or
combined
unless otherwise indicated and will still benefit from the present disclosure.
100581 All documents referenced herein are hereby incorporated by
reference.
100591 The foregoing description is exemplary rather than defined by the
limitations within. Various non-limiting embodiments are disclosed herein,
however, one
of ordinary skill in the art would recognize that various modifications and
variations in light
of the above teachings will fall within the scope of the appended claims. It
is therefore to
-15-
CA 02961017 2017-03-10
WO 2016/053605
PCT/US2015/049999
be understood that within the scope of the appended claims, the disclosure may
be practiced
other than as specifically described. For that reason the appended claims
should be studied
to determine true scope and content.
-16-