Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
MERCHANT TENANT RISK MONITORING METHOD, DEVICE, COMPUTER
EQUIPMENT AND STORAGE MEDIUM
BACKGROUND OF THE INVENTION
Technical Field
[0001] The present application relates to the field of computer data
processing technology, and
more particularly to a merchant tenant risk monitoring method, and
corresponding device,
computer equipment and storage medium.
Description of Related Art
[0002] With the rapid development of the e-commerce field, more and more
transactions are
carried out online over the internet. At present, quality check of to-be-
settled merchant
tenants for applications to settle on platforms (also referred to as e-
commerce platforms)
appears particularly important, as this is closely related to the normal
operation and risk
control of the platforms.
[0003] For quite a long time, risk control at the level of merchant tenants is
invariably highly
dependent on human investigation and human check and analysis no matter
whether it is
in the banking industry, in the science and technology industry or in the
financial industry.
Such a mode of over-dependence on manual collection of data and subjective
judgment
requires the consumption of lot of time and is not high in accuracy.
SUMMARY OF THE INVENTION
[0004] In view of the above technical problems, there is an urgent need to
provide a merchant
tenant risk monitoring method, and corresponding device, computer equipment
and
1
Date Recue/Date Received 2022-06-01
storage medium that are accurate and time-saving.
[0005] There is provided a merchant tenant risk monitoring method that
comprises:
[0006] obtaining risk assessment values before settlement to which plural
target merchant tenants
respectively correspond, and platform record data formed by platform
operations carried
out by the various target merchant tenants within a buffer period after
settlement;
[0007] performing feature extraction on the platform record data of the
various target merchant
tenants respectively, and obtaining feature vectors after settlement to which
the various
target merchant tenants correspond;
[0008] employing an abnormality detection model to perform abnormality
detection processing
on a feature matrix constituted by the feature vectors after settlement to
which the plural
target merchant tenants correspond, and obtaining risk assessment values after
settlement
to which the various target merchant tenants correspond; and
[0009] calculating comprehensive risk values to which the various target
merchant tenants
correspond according to the risk assessment values before and after settlement
to which
the various target merchant tenants correspond.
[0010] In one of the embodiments, the method further comprises:
[0011] obtaining basic information data of a to-be-settled merchant tenant
applying for
settlement on the platform;
[0012] performing feature extraction on the basic information data, and
obtaining a feature vector
before settlement of the to-be-settled merchant tenant;
[0013] performing similarity matching calculation on the feature vector before
settlement of the
to-be-settled merchant tenant with a feature vector to which each of plural
risky merchant
tenants corresponds, and obtaining similarity values between the to-be-settled
merchant
tenant and the various risky merchant tenants;
[0014] calculating to obtain a risk assessment value before settlement of the
to-be-settled
merchant tenant according to the similarity values between the to-be-settled
merchant
tenant and the various risky merchant tenants; and
2
Date Recue/Date Received 2022-06-01
[0015] determining the to-be-settled merchant tenant as a target merchant
tenant when the risk
assessment value before settlement of the to-be-settled merchant tenant is not
greater than
a preset first risk assessment threshold.
[0016] In one of the embodiments, the method further comprises:
[0017] sending check prompt information to a terminal for prompting to further
assess a risk of
the to-be-settled merchant tenant when the risk assessment value before
settlement of the
to-be-settled merchant tenant is greater than the first risk assessment
threshold and is not
greater than a preset second risk assessment threshold; and
[0018] intercepting an application for settlement on the platform of the to-be-
settled merchant
tenant when the risk assessment value before settlement of the to-be-settled
merchant
tenant is greater than the second risk assessment threshold.
[0019] In one of the embodiments, the method is characterized in that:
[0020] the basic information data includes registration record information and
external transfer
information of the to-be-settled merchant tenant; and that
[0021] the platform record data includes a merchant business poi __________
tiait, transaction flow data, and
order record data of the target merchant tenant within the buffer period after
settlement.
[0022] In one of the embodiments, the various risky merchant tenants are
subordinate to clusters
corresponding thereto, and the step of calculating to obtain a risk assessment
value before
settlement of the to-be-settled merchant tenant according to the similarity
values includes:
[0023] calculating to obtain a risk assessment value before settlement of the
to-be-settled
merchant tenant according to the following formula:
In4A5 AtoS .................. S MAn
r=1
Rm C k
[0024]
[0025] where Rm c k expresses the risk assessment value before settlement of
the to-be-settled
merchant tenant, k expresses the number of clusters, Sm]Sw2 ...............
Smy, 1 expresses
3
Date Recue/Date Received 2022-06-01
products between n i number of similarity values obtained after performing
similarity
matching calculation on the feature vector before settlement of the to-be-
settled merchant
tenant with feature vectors to which n i number of risky merchant tenants in
the ith
cluster correspond, and n i expresses the total number of risky merchant
tenants
subordinate to the ith cluster.
[0026] In one of the embodiments, the abnormality detection model is an
isolation forest model,
and the step of employing an abnormality detection model to perform
abnormality
detection processing on a feature matrix constituted by the feature vectors
after settlement
to which the plural target merchant tenants correspond, and obtaining risk
assessment
values after settlement to which the various target merchant tenants
correspond includes:
[0027] inputting the feature matrix into the isolation forest model,
outputting abnormality scores
to which the various target merchant tenants correspond, numerically
transforming the
abnormality scores of the various target merchant tenants, and obtaining risk
assessment
values after settlement of the various target merchant tenants, wherein the
risk assessment
values after settlement are valuated in the range of being not smaller than 0
and not greater
than 1.
[0028] In one of the embodiments, the step of calculating comprehensive risk
values to which
the various target merchant tenants correspond according to the risk
assessment values
before and after settlement to which the various target merchant tenants
correspond
includes:
[0029] respectively weighting and thereafter summating the risk assessment
values before and
after settlement to which the various target merchant tenants correspond, and
obtaining
the comprehensive risk values to which the various target merchant tenants
correspond.
[0030] There is provided a computer equipment that comprises a memory, a
processor and a
computer program stored on the memory and operable on the processor, and the
following
4
Date Recue/Date Received 2022-06-01
steps are realized when the processor executes the computer program:
[0031] obtaining risk assessment values before settlement to which plural
target merchant tenants
respectively correspond, and platform record data formed by platform
operations carried
out by the various target merchant tenants within a buffer period after
settlement;
[0032] performing feature extraction on the platform record data of the
various target merchant
tenants respectively, and obtaining feature vectors after settlement to which
the various
target merchant tenants correspond;
[0033] employing an abnormality detection model to perform abnormality
detection processing
on a feature matrix constituted by the feature vectors after settlement to
which the plural
target merchant tenants correspond, and obtaining risk assessment values after
settlement
to which the various target merchant tenants correspond; and
[0034] calculating comprehensive risk values to which the various target
merchant tenants
correspond according to the risk assessment values before and after settlement
to which
the various target merchant tenants correspond.
[0035] There is provided a computer-readable storage medium storing a computer
program
thereon, and the following steps are realized when the computer program is
executed by
a processor:
[0036] obtaining risk assessment values before settlement to which plural
target merchant tenants
respectively correspond, and platform record data formed by platform
operations carried
out by the various target merchant tenants within a buffer period after
settlement;
[0037] performing feature extraction on the platform record data of the
various target merchant
tenants respectively, and obtaining feature vectors after settlement to which
the various
target merchant tenants correspond;
[0038] employing an abnormality detection model to perform abnormality
detection processing
on a feature matrix constituted by the feature vectors after settlement to
which the plural
target merchant tenants correspond, and obtaining risk assessment values after
settlement
to which the various target merchant tenants correspond; and
[0039] calculating comprehensive risk values to which the various target
merchant tenants
Date Recue/Date Received 2022-06-01
correspond according to the risk assessment values before and after settlement
to which
the various target merchant tenants correspond.
[0040] In the aforementioned merchant tenant risk monitoring method, device,
computer
equipment and storage medium, by a series of such steps as performing feature
extraction
on the platform record data of the target merchant tenants in the buffer
period after
settlement, constructing a feature matrix, and detecting abnormality, risk
assessment
values after settlement are obtained, and it is made possible, in combination
with risk
assessment values before settlement, to determine comprehensive risk values of
the target
merchant tenants at the end of the buffer period after settlement, to timely
monitor
merchant tenant risks, and to obtain accurate monitoring results.
BRIEF DESCRIPTION OF THE DRAWINGS
[0041] Fig. 1 is a view illustrating the application environment for the
merchant tenant risk
monitoring method in an embodiment;
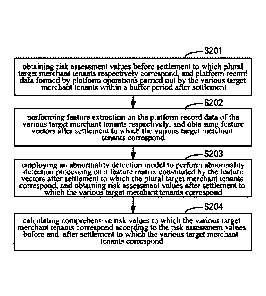
[0042] Fig. 2 is a flowchart schematically illustrating the merchant tenant
risk monitoring
method in an embodiment;
[0043] Fig. 3 is a flowchart schematically illustrating the step of judging
the size of a risk
assessment value before settlement involved in an embodiment;
[0044] Fig. 4 is a block diagram illustrating the structure of the merchant
tenant risk monitoring
device in an embodiment;
[0045] Fig. 5 is a block diagram illustrating the structure of the risk
assessment value calculating
module before settlement involved in an embodiment; and
6
Date Recue/Date Received 2022-06-01
[0046] Fig. 6 is a view illustrating the internal structure of the computer
equipment in an
embodiment.
DETAILED DESCRIPTION OF THE INVENTION
[0047] To make more lucid and clear the objectives, technical solutions and
advantages of the
present application, the present application is described in greater detail
below with
reference to accompanying drawings and embodiments. As should be understood,
the
specific embodiments described here are merely meant to explain the present
application,
rather than to restrict the present application.
[0048] The merchant tenant risk monitoring method provided by the present
application is
applicable to the application environment as shown in Fig. 1, in which server
101 can
communicate with terminal 102 through network, for instance, after having
calculated the
compressive risk value of a target merchant tenant, server 101 can send the
compressive
risk value to terminal 102 for display by terminal 102, at this time, the
checking personnel
at the platform can learn of the risk situation of the target merchant tenant
through the
compressive risk value displayed by terminal 102. Server 101 can be embodied
as an
independent server or a server cluster consisting of a plurality of servers,
and terminal
102 can be, but is not limited to be, any of various personal computers,
notebook
computers, smart mobile phones, panel computers, and portable wearable
devices.
[0049] In one embodiment, as shown in Fig. 2, there is provided a merchant
tenant risk
monitoring method, and the method is explained with an example of its being
applied to
server 101 in Fig. 1, to comprise the following steps:
[0050] Step S201 - obtaining risk assessment values before settlement to which
plural target
merchant tenants respectively correspond, and platform record data formed by
platform
operations carried out by the various target merchant tenants within a buffer
period after
settlement;
7
Date Recue/Date Received 2022-06-01
[0051] Step S202 - performing feature extraction on the platform record data
of the various target
merchant tenants respectively, and obtaining feature vectors after settlement
to which the
various target merchant tenants correspond;
[0052] Step S203 - employing an abnormality detection model to perform
abnormality detection
processing on a feature matrix constituted by the feature vectors after
settlement to which
the plural target merchant tenants correspond, and obtaining risk assessment
values after
settlement to which the various target merchant tenants correspond; and
[0053] Step S204 - calculating comprehensive risk values to which the various
target merchant
tenants correspond according to the risk assessment values before and after
settlement to
which the various target merchant tenants correspond.
[0054] When a merchant tenant is not settled on the platform, this merchant
tenant can be referred
to as a to-be-settled merchant tenant, after an application of the merchant
tenant to settle
on the platform has been ratified, the merchant tenant can be referred to as a
target
merchant tenant. In the above steps, after target merchant tenants have
settled on the
platform, a buffer period after settlement should be undergone, under certain
more
specific circumstances, if after the buffer period after settlement ends, the
comprehensive
risk values of these target merchant tenants are within a reasonable range,
then the target
merchant tenants will be allowed to retain the settled status.
[0055] As should be noted, in step S201, in obtaining the two different types
of data as the risk
assessment values before settlement and the platform record data of specific
target
merchant tenants, it is possible to firstly obtain one type of data and then
obtain another
type of data, and it is also possible to simultaneously obtain the two
different types of
data.
[0056] The risk assessment values before settlement of the target merchant
tenants can be
determined according to the relevant data of to-be-settled merchant tenants
when they are
not settled. The specific obtaining mode will be described later in this
paper.
8
Date Recue/Date Received 2022-06-01
[0057] The platform record data of the target merchant tenants at least
includes data, such as
order information or transaction flow information, etc., generated through
commercial
activities carried out by the target merchant tenants through the platform
after settlement
on the platform. However, under some specific circumstances, the platform
record data
can further include other data, and these data can be formed before settlement
of to-be-
settled merchant tenants on the platform, such as places of registration of
enterprises to
which the target merchant tenants correspond.
[0058] As regards the buffer period after settlement, it is a time period
whose corresponding time
duration can be set according to practical requirement, such as 10 days, half
a month, or
a full month, etc. The buffer period after settlement can be counted from the
time point
at which an application submitted by a to-be-settled merchant tenant to the
platform for
settlement on the platform is ratified, and can also be counted from a certain
time point
after settlement (for instance, from the time at which the first transaction
occurs after the
target merchant tenant has settled on the platform), to which no particular
restriction is
made in this context. The significance of setting up a buffer period after
settlement lies in
the facilitation to timely carry out risk surveillance after the target
merchant tenant has
settled on the platform, in the collection of relevant data corresponding to
this stage, and
in the facilitation to more accurately obtain the monitoring result (such as
the
comprehensive risk value) in conjunction with data of the to-be-settled
merchant tenant
before settlement on the platform.
[0059] As regards feature extraction, since it is needed to monitor the risks
of various target
merchant tenants, it is therefore required to process the platform record data
of the various
target merchant tenants before the monitoring, and the specific mode is the
feature
extraction. After feature extraction has been performed on the platform record
data of
each target merchant tenant, a feature vector after settlement corresponding
to each target
merchant tenant can be obtained. Feature extraction can be embodied as a
currently
9
Date Recue/Date Received 2022-06-01
available feature engineering algorithm, to which not much restriction is made
in this
context.
[0060] As regards the abnormality detection model, it is usually embodied as
an unsupervised
learning model, such as an isolation forest model, a KNN (K Nearest Neighbors)
model,
or an LOF (Local Outlier Factor) model, etc. The objective of abnormality
processing
rests mainly in differentiating data that is inconsistent with normal samples,
to thereby
determine any target merchant tenant who possesses abnormal behavior/property.
With
respect to plural target merchant tenants that settle on a platform during a
certain time
period, the feature vector after settlement of each target merchant tenant is
obtained to
construct a feature matrix, and abnormality detection processing is performed
on the
feature matrix, whereby an abnormality score of each target merchant tenant
can be
obtained, and sizes of the abnormality scores reflect the levels of risks of
behaviors of the
target merchant tenants during the buffer period after settlement. Under some
circumstances, the abnormality scores can be directly taken to serve as risk
assessment
values after settlement; under other circumstances, it is also possible to
transform the
abnormality scores to obtain risk assessment values after settlement
possessing mapping
relations to the abnormality scores.
[0061] The comprehensive risk values in step S204 are one piece of data that
reflects
comprehensive risks of target merchant tenants at the end of the buffer period
after
settlement. It is generally possible to respectively weight the risk
assessment values
before and after settlement and thereafter summate the two values, and then
take the
numerical values of such summation as comprehensive risk values. However, the
use of
other calculating modes to obtain the comprehensive risk values is not
excluded, it is
required at this time to provide the risk assessment values before settlement
and the
comprehensive risk values with correlation, and to simultaneously provide the
risk
assessment values after settlement and the comprehensive risk values also with
correlation, such correlations can be positive correlations, moreover, such
correlations
Date Recue/Date Received 2022-06-01
can be proportional correlations.
[0062] In the aforementioned merchant tenant risk monitoring method, by a
series of such steps
as performing feature extraction on the platform record data of the target
merchant tenants
within the buffer period after settlement, constructing a feature matrix, and
detecting
abnormality, risk assessment values after settlement are obtained, and it is
made possible,
in combination with risk assessment values before settlement, to determine
comprehensive risk values of the target merchant tenants at the end of the
buffer period
after settlement. Data generated within the time interval of the buffer period
after
settlement is utilized to perform risk surveillance, whereby risk results of
merchant
tenants after settlement on the platform can be timely obtained, risk
assessment values
after settlement and risk assessment values before settlement are processed,
risks
reflected by properties or behaviors of merchant tenants before settlement on
the platform
are not only considered, but risks reflected by properties or behaviors of
merchant tenants
after settlement on the platform are also considered, the comprehensive risk
values
obtained thereby can reflect comprehensive risk levels of target merchant
tenants from an
overall perspective, thus facilitating to enhance accuracy of risk monitoring
results of
merchant tenants. As should be noted, the risk monitoring results, or
monitoring results,
as mentioned in this paper mainly stand for data descriptive of risk levels of
merchant
tenants (including target merchant tenants) directly or indirectly obtained by
the merchant
tenant risk monitoring method, the directly obtained data can be compressive
risk values,
risk assessment values before settlement, or assessment values after
settlement, and the
indirectly obtained data can be obtained by mapping processing of the directly
obtained
data, for instance, the directly obtained data can be mapping-processed to
obtain
corresponding risk levels, and the risk levels can as well be regarded as
monitoring results
at this time.
[0063] In some embodiments, as shown in Fig. 3, the merchant tenant risk
monitoring method
further comprises:
11
Date Recue/Date Received 2022-06-01
[0064] Step S301 - obtaining basic information data of a to-be-settled
merchant tenant applying
for settlement on the platform;
[0065] Step S302 - performing feature extraction on the basic information
data, and obtaining a
feature vector before settlement of the to-be-settled merchant tenant;
[0066] Step S303 - performing similarity matching calculation on the feature
vector before
settlement of the to-be-settled merchant tenant with a feature vector to which
each of
plural risky merchant tenants corresponds, and obtaining similarity values
between the
to-be-settled merchant tenant and the various risky merchant tenants;
[0067] Step S304 - calculating to obtain a risk assessment value before
settlement of the to-be-
settled merchant tenant according to the similarity values between the to-be-
settled
merchant tenant and the various risky merchant tenants; and
[0068] Step S305 - determining the to-be-settled merchant tenant as a target
merchant tenant
when the risk assessment value before settlement of the to-be-settled merchant
tenant is
not greater than a preset first risk assessment threshold.
[0069] As regards server 101, there will be the circumstance in which
applications for settlement
on the platform will be incessantly received. In this case, when the risk
assessment value
before settlement is not greater than a first risk assessment threshold, the
to-be-settled
merchant tenant to which the risk assessment value before settlement
corresponds can be
determined as a target merchant tenant by the execution of steps S301-S305,
and risk
evaluation is performed once again at the end of the buffer period after
settlement of the
target merchant tenant by the execution of steps S201-S204, to obtain the
comprehensive
risk value. It is thusly not only ensured that the merchant tenant being
settled on the
platform has relatively low risk, but also made possible to carry out further
risk
surveillance to the merchant tenant being settled on the platform.
[0070] The feature extraction in step S302 can be carried out by a currently
available feature
engineering algorithm mentioned before, to which not much restriction is made
in this
context.
12
Date Recue/Date Received 2022-06-01
[0071] The risky merchant tenants in step S303 mainly indicate suspect or
abnormal merchant
tenant samples currently in grasp, as regards the risky merchant tenants, it
is also possible
to employ the mode of feature extraction to obtain feature vectors
corresponding to the
risky merchant tenants. When the number of risky merchant tenants is
relatively large,
the risky merchant tenants can be marked, risky merchant tenants with the same
mark are
considered to be one cluster, and such marks can be designated with
correspondences
with such behaviors/properties as operation anomaly,
pornography/gambling/drugging,
click farming, and cashing, etc. Performing similarity matching calculation on
the feature
vector before settlement of the to-be-settled merchant tenant with a feature
vector to
which each of plural risky merchant tenants corresponds can mainly include the
following
two modes:
[0072] (1) Similarity calculation is performed on the feature vector before
settlement with feature
vectors of risky merchant tenants in one cluster, to obtain similarity values
corresponding
to this cluster; in accordance with this mode, similarity values of the
feature vector before
settlement with respect to plural clusters can be obtained, generally
speaking, how many
clusters there are, that many similarity values can be obtained; on the basis
thereof, the
plural similarity values are averaged to finally obtain an average value, and
this average
value can be regarded as the similarity value between the to-be-settled
merchant tenant
and the various risky merchant tenants.
[0073] (2) Calculation is performed not in accordance with the cluster mode,
whereas uniform
similarity calculation is directly performed on the feature vector before
settlement and
the feature vectors of all risky merchant tenants, and similarity values
between the to-be-
settled merchant tenant and the various risky merchant tenants are directly
obtained.
[0074] Determining the to-be-settled merchant tenant as a target merchant
tenant in step S305
can be either automatically executed by server 101, or triggered by server 101
according
to an instruction input by the platform checking personnel and sent by
terminal 102. It is
specifically possible to add the settled merchant tenant from a list of
settlement check to
13
Date Recue/Date Received 2022-06-01
a list of check approval. Alternatively, the mark of application for
settlement of the to-be-
settled merchant tenant is changed to a mark corresponding to the platform
settled.
[0075] In some embodiments, as shown in Fig. 3, the merchant tenant risk
monitoring method
further comprises:
[0076] Step S306 - sending check prompt information to terminal 102 for
prompting to further
assess a risk of the to-be-settled merchant tenant when the risk assessment
value before
settlement of the to-be-settled merchant tenant is greater than the first risk
assessment
threshold and is not greater than a preset second risk assessment threshold;
and
[0077] Step S307 - intercepting an application for settlement on the platform
of the to-be-settled
merchant tenant when the risk assessment value before settlement of the to-be-
settled
merchant tenant is greater than the second risk assessment threshold.
[0078] The first risk assessment threshold and the second risk assessment
threshold in Fig. 3 can
be designed according to practical requirement, and no particular restriction
is made
thereto. The check prompt information functions mainly to notify the platform
checking
personnel to assess the risk of the to-be-settled merchant tenant. Moreover,
terminal 102
can detect a feedback instruction of the platform checking personnel, and
sends the
feedback instruction to server 101; if the feedback instruction is for
instructing server 101
to determine the to-be-settled merchant tenant as a target merchant tenant,
server 101
executes the processing steps to determine the to-be-settled merchant tenant
as a target
merchant tenant; if the feedback instruction is for instructing server 101 to
intercept an
application for settlement on the platform of the to-be-settled merchant
tenant, server 101
executes the interception processing step. Thusly, it is facilitated to make
more accurate
judgment on the risk of the to-be-settled merchant tenant.
[0079] When the risk assessment value before settlement of the to-be-settled
merchant tenant is
greater than the second risk assessment threshold, the application for
settlement on the
platform of the to-be-settled merchant tenant is intercepted, indicating that
the risk of the
14
Date Recue/Date Received 2022-06-01
to-be-settled merchant tenant is relatively high, at this time it is not
required for the
platform checking personnel to check, as it is possible for server 101 to make
the
intercepting process on its own initiative. The intercepting process is a
process to not
allow settlement of the application for settlement on the platform, whereby
the to-be-
settled merchant tenant cannot be settled on the platform at least within a
period of time.
With respect to such intercepting process, server 101 can generate first
interception
prompt information and send the same terminal 102, so as to let the platform
checking
personnel learn of the event.
[0080] In some embodiments, the basic information data includes registration
record information
and external transfer information of the to-be-settled merchant tenant, and
the platform
record data includes a merchant business poi ______________________________ ti
aft, transaction flow data, and order record
data of the target merchant tenant within the buffer period after settlement.
[0081] Generally speaking, since the dimensions of the obtainable data are
limited before the to-
be-settled merchant tenant is settled on the platform, the basic information
data at this
time can include registration record information, region information, and
legal person
qualification information of the to-be-settled merchant tenant. Further, the
registration
record information includes, but is not limited to, registered mailbox
information,
registered telephone information, and registration time information. The basic
information data can further include external transfer information, and the
external
transfer information includes, but is not limited to, transfer frequency
information, actual
controller transfer information, and transfer bank information. However, the
platform
record data is different, as it is mainly derived from commercial behavior
data of target
merchant tenants recorded by the server to which the platform corresponds,
such as
customer transactions, transfer information, and deposit and withdrawal
information, etc.
As should be noted, in addition to the data generated or formed within the
buffer period
after settlement, the platform record data can further include data generated
or formed
before settlement on the platform. Under some specific circumstances, the
merchant
Date Recue/Date Received 2022-06-01
business poi ______________________________________________________________ Li
aft includes, but is not limited to, customer type (corporate-oriented type,
privately oriented type, etc.) data, registered capital data, data reflecting
whether the
account of a target merchant tenant exists and whether the registered mobile
phone region
and registered account region do not conform to each other, and data
reflecting whether
the registered region of the target merchant tenant originates from a highly
risky region.
The transaction flow data can be transaction flow slice information, which
mainly
involves money flow and flow time slice information of the target merchant
tenant within
the buffer period after settlement, such as balance information of associated
accounts at
each time point within half a month after settlement on the platform; the
transaction flow
slice information can also include information representing flowing in and out
of great
amount of capital, abrupt change in account balance, unduly much orders in
abnormal
transaction times, unduly much transfer of orders with similar amounts of
money, unduly
much amount of transfer across the border or across provinces, or frequent
cash
withdrawal/transfer of corporate accounts, etc. The order record data mainly
includes
online/offline order record information of the target merchant tenant after
settlement on
the platform, focusing principally on portrait information of transactions,
including, but
not limited to, transaction frequency information, machine fingerprint
information, order
amount of money information, and buyer qualification record information.
[0082] In some embodiments, when the number of clusters to which risky
merchant tenants
correspond is k, Ci [m,õm] can be employed to represent a set of all risky
merchant tenants in the ith cluster, where 1 i<k , mo represents the first
risky
merchant tenant in the ith cluster, by the same token, m,õ 1 represents the n
ith risky
merchant tenant in the ith cluster, and n i represents the number of risky
merchant
tenants in this cluster. At this time, with respect to a certain to-be-settled
merchant tenant
(represented by M), feature extraction can be performed on its basic
information data, to
obtain d dimension of a feature vector before settlement (represented by f, ),
16
Date Recue/Date Received 2022-06-01
fM = (t,õ/õt ); with respect to a certain risky merchant tenant (represented
by
min ), feature extraction can be performed on the basic information data of
this risky
merchant tenant, to obtain d dimension of a feature vector to which this risky
merchant
tenant corresponds, represented by fm ,,j, fm,,=
[0083] To facilitate further understanding, explanation is made with a
circumstance in which the
number of clusters is 2, in one of which cluster the number of risky merchant
tenants is
2, and in another one of which cluster the number of risky merchant tenants is
3. At this
time, k is 2, with respect to the first cluster, i is valuated as 1, n = n 1 =
2, the set
of risky merchant tenants in the first cluster is
m1,2] , where rn11 represents the
first risky merchant tenant in the first cluster, and mu represents the second
risky
merchant tenant in the first cluster. With respect to the second cluster, i is
valued as 2,
n i = n 2= 3 , the set of risky merchant tenants in the second cluster is
C2[11/2,/, m2,2, m2,3] m21 represents the first risky merchant tenant in the
second cluster,
M2,2 represents the second risky merchant tenant in the second cluster, and
m23
represents the third risky merchant tenant in the second cluster. Suppose d=6,
then as
regards rn11 (the first risky merchant tenant in the first cluster), its
corresponding feature
vector is , = (tinny
mll; the feature vectors to which other
risky merchant tenants correspond can be represented in accordance with the
similar
principle, to which no repetition is made in this context.
[0084] Performing similarity matching calculation on the feature vector before
settlement of a
certain to-be-settled merchant tenant (represented by M) with a feature vector
of a certain
risky merchant tenant (represented by in,n ) can be to calculate their cosine
similarity
value. The calculation formula of the cosine similarity value can be inferred
from the
17
Date Recue/Date Received 2022-06-01
following formula (1).
[0085] Consine similarity(a = b) ¨ a b (1)
MaMMbM
[0086] In formula (1), a and b respectively represent two pieces of data of
the cosine similarity
value to be calculated, specifically, they can respectively represent the
feature vector
before settlement and the feature vector of the risky merchant tenant.
Consine similarity(a = b) represents the cosine similarity value of the
feature vector
before settlement and the feature vector of the risky merchant tenant.
[0087] Thus, with respect to a certain cluster Ci[mi,õ ,
the similarity values of the
feature vector fm before settlement of a certain to-be-settled merchant tenant
and the
feature vectors of risky merchant tenants in this cluster can be represented
as
(Smo õSmo, , where Smo represents the similarity value (such as a cosine
similarity value) of fm with the feature vector of the first risky merchant
tenant in this
cluster obtained after similarity matching calculation, by the same token, Smo
represents the similarity value of fm with the feature vector of the n ith
risky merchant
tenant in this cluster obtained after similarity matching calculation.
[0088] In some embodiments, the various risky merchant tenants are subordinate
to clusters
corresponding thereto, and step S304 includes calculating to obtain a risk
assessment
value before settlement of the to-be-settled merchant tenant according to
formula (2):
In4r5At]SAu2 ................. S Mn r
[0089] Rm c k = __ 1=1 (2)
18
Date Recue/Date Received 2022-06-01
[0090] where Rm õ expresses the risk assessment value before settlement of the
to-be-settled
merchant tenant, it is also a comprehensive similarity value of the feature
vector before
settlement of the to-be-settled merchant tenant with the feature vectors to
which the risky
merchant tenants of k number of clusters, k expresses the number of clusters,
..........................................................................
Sm,õ 1 expresses products between n i number of similarity values
obtained after performing similarity matching calculation on the feature
vector before
settlement of the to-be-settled merchant tenant with feature vectors to which
n i
number of risky merchant tenants in the ith cluster correspond, and n i
expresses the
total number of risky merchant tenants subordinate to the ith cluster.
[0091] To facilitate comprehension, an example is provided here. In this
example, k=2. Suppose
when i=1, n i=n 1= 2; suppose when i=2, n i=n 2= 3 .
[0092] Then there is R
m C k All] All' +mziSm22Sm2,3
2
[0093] Seen as such, JS 1S. S _________________________________________ 1
min represents a geometrical average similarity value of
................................ õ
fm with plural similarity values of feature vectors of the risky merchant
tenants in the
cluster, moreover, Rm k represents a compressive similarity value obtained
after
employing an arithmetic averaging calculation on plural geometrical average
similarity
values.
[0094] In some embodiments, Rm k can be regarded as a risk assessment value
before
settlement, its valuation range lies between 0 and 1, the higher this value
is, the higher
will be the risk level of the to-be-settled merchant tenant.
19
Date Recue/Date Received 2022-06-01
[0095] In some embodiments, the abnormality detection model is an isolation
forest model, and
step S203 includes: inputting the feature matrix into the isolation forest
model, outputting
abnormality scores to which the various target merchant tenants correspond,
numerically
transforming the abnormality scores of the various target merchant tenants,
and obtaining
risk assessment values after settlement of the various target merchant
tenants, wherein
the risk assessment values after settlement are valuated in the range of being
not smaller
than 0 and not greater than 1.
[0096] Specifically, a currently available isolation forest model can be used,
for example, an
Isolation Forest function in python is used to serve as the function to which
the isolation
forest model corresponds, at which time the feature matrix is substituted in
the function,
and abnormality scores in the valuation range of -1 to 1 will be obtained.
[0097] Numerically transforming the abnormality scores of the target merchant
tenants aims to
correspond the valuation range of the risk assessment value after settlement
to the
valuation range of the risk assessment value before settlement, and the two
valuation
ranges both lie within 0 and 1, so as to facilitate subsequent calculation of
the
comprehensive risk value.
[0098] Suppose that n number of merchant tenants in a group of to-be-settled
merchant tenants
is ratified for settlement, that is to say, there are n target merchant
tenants now, and these
target merchant tenants can be represented by M1, M,õ Mn , in which Mi
represents
the first target merchant tenant, so on and so forth, and Mn represents the
nth target
merchant tenant. Feature extraction is performed on the platform record data
of these
target merchant tenants respectively, whereby feature vectors after settlement
of n number
of target merchant tenants can be obtained, suppose that the dimension of each
feature
vector after settlement is p, a matrix is constructed out of the feature
vectors after
settlement of the n number of target merchant tenants, and a feature matrix
can be
obtained (represented by X),
Date Recue/Date Received 2022-06-01
X11 = = = Xlp
X= = = .
= = = x
[0099] X1 nP /
[0100] Element xnp of X represents the pth feature value of the nth target
merchant tenant
(namely Ma).
[0101] X is input in the abnormality detection model, and abnormality scores
of n number of
target merchant tenants can be output, with respect to a certain target
merchant tenant
(represented by M , 1<j<n ), its abnormality score is t, , since -1 ti ,
so
numerical transformation can be performed according to formula (3).
V-(1 -1)
[0102] P ¨ (2)
2
[0103] where Pi represents a risk assessment value after settlement
corresponding to M1, and
its valuation range lies between 0 to 1.
[0104] In some embodiments, step S204 includes: respectively weighting and
thereafter
summating the risk assessment values before and after settlement to which the
various
target merchant tenants correspond, and obtaining the comprehensive risk
values to which
the various target merchant tenants correspond. More specifically, under some
circumstances, the comprehensive risk value to which M corresponds is
represented
by RiskScore MJ, which can be calculated and obtained according to formula
(4).
[0105] RiskScore MJ =a = Rm k+ (1-a )=P (4)
¨
[0106] where a represents a weight to which Rm, k corresponds, at this time,
Rm, k
21
Date Recue/Date Received 2022-06-01
represents the risk assessment value before settlement to which Mi
corresponds, and
(1- a) represents a weight to which Pj corresponds.
[0107] In some embodiments, with respect to a certain target merchant tenant,
when its
corresponding comprehensive risk value is greater than a preset comprehensive
risk
threshold, server 101 sends second interception information (the second
interception
information is used to prompt that the risk of the target merchant tenant is
relatively high)
to terminal 102, and performs an intercepting process of the target merchant
tenant after
settlement on the platform, for instance, to intercept the corresponding
online shop of the
target merchant tenant or put the corresponding commodities of the target
merchant tenant
off the shelf. If the comprehensive risk value is not greater than the preset
comprehensive
risk threshold, it is possible to update the platform record data again after
a designated
time duration, and to calculate again the comprehensive risk value of the
target merchant
tenant, when the updated comprehensive risk value is greater than the preset
comprehensive risk threshold, server 101 performs an intercepting process on
the target
merchant tenant after settlement on the platform.
[0108] As should be understood, although the various steps in the flowcharts
of Figs. 2 and 3 are
sequentially displayed as indicated by arrows, these steps are not necessarily
executed in
the sequences indicated by arrows. Unless otherwise explicitly noted in this
paper,
execution of these steps is not restricted by any sequence, as these steps can
also be
executed in other sequences (than those indicated in the drawings). Moreover,
at least
partial steps in the flowcharts of Figs. 2 and 3 may include plural sub-steps
or multi-
phases, these sub-steps or phases are not necessarily completed at the same
timing, but
can be executed at different timings, and these sub-steps or phases are also
not necessarily
sequentially performed, but can be performed in turns or alternately with
other steps or
with at least some of sub-steps or phases of other steps.
22
Date Recue/Date Received 2022-06-01
[0109] In one embodiment, as shown in Fig. 4, there is provided a merchant
tenant risk
monitoring device 400 that comprises:
[0110] a data obtaining module 401, for obtaining risk assessment values
before settlement to
which plural target merchant tenants respectively correspond, and platform
record data
formed by platform operations carried out by the various target merchant
tenants within
a buffer period after settlement;
[0111] a feature extracting module 402, for performing feature extraction on
the platform record
data of the various target merchant tenants respectively, and obtaining
feature vectors
after settlement to which the various target merchant tenants correspond;
[0112] an abnormality detecting module 403, for employing an abnormality
detection model to
perform abnormality detection processing on a feature matrix constituted by
the feature
vectors after settlement to which the plural target merchant tenants
correspond, and
obtaining risk assessment values after settlement to which the various target
merchant
tenants correspond; and
[0113] a risk calculating module 404, for calculating comprehensive risk
values to which the
various target merchant tenants correspond according to the risk assessment
values before
and after settlement to which the various target merchant tenants correspond.
[0114] In one embodiment, as shown in Fig. 5, the merchant tenant risk
monitoring device 400
further comprises:
[0115] a basic information data obtaining module 501, for obtaining basic
information data of a
to-be-settled merchant tenant applying for settlement on the platform;
[0116] a feature vector before settlement obtaining module 502, for performing
feature
extraction on the basic information data, and obtaining a feature vector
before settlement
of the to-be-settled merchant tenant;
[0117] a similarity matching and calculating module 503, for performing
similarity matching
calculation on the feature vector before settlement of the to-be-settled
merchant tenant
with a feature vector to which each of plural risky merchant tenants
corresponds, and
obtaining similarity values between the to-be-settled merchant tenant and the
various
23
Date Recue/Date Received 2022-06-01
risky merchant tenants;
[0118] a risk assessment value before settlement calculating module 504, for
calculating to
obtain a risk assessment value before settlement of the to-be-settled merchant
tenant
according to the similarity values between the to-be-settled merchant tenant
and the
various risky merchant tenants; and
[0119] a target merchant tenant determining module 505, for determining the to-
be-settled
merchant tenant as a target merchant tenant when the risk assessment value
before
settlement of the to-be-settled merchant tenant is not greater than a preset
first risk
assessment threshold.
[0120] In one embodiment, as shown in Fig. 5, the merchant tenant risk
monitoring device 400
further comprises:
[0121] a check prompt information sending module 506, for sending check prompt
information
to a terminal for prompting to further assess a risk of the to-be-settled
merchant tenant
when the risk assessment value before settlement of the to-be-settled merchant
tenant is
greater than the first risk assessment threshold and is not greater than a
preset second risk
assessment threshold; and
[0122] an interception processing module 507, for intercepting an application
for settlement on
the platform of the to-be-settled merchant tenant when the risk assessment
value before
settlement of the to-be-settled merchant tenant is greater than the second
risk assessment
threshold.
[0123] In one embodiment, the risk assessment value before settlement
calculating module
calculates to obtain the risk assessment value before settlement of the to-be-
settled
merchant tenant according to formula (2).
[0124] In one embodiment, the abnormality detection model is an isolation
forest model, and the
abnormality detecting module 403 inputs the feature matrix in the isolation
forest model,
outputs abnormality scores to which the various target merchant tenants
correspond,
24
Date Recue/Date Received 2022-06-01
numerically transforms the abnormality scores of the various target merchant
tenants, and
obtains risk assessment values after settlement of the various target merchant
tenants,
wherein the risk assessment values after settlement are valuated in the range
of being not
smaller than 0 and not greater than 1.
[0125] In one embodiment, the risk calculating module 404 respectively weights
and thereafter
summates the risk assessment values before and after settlement to which the
various
target merchant tenants correspond, and obtains the comprehensive risk values
to which
the various target merchant tenants correspond.
[0126] Specific definitions relevant to the merchant tenant risk monitoring
device may be
inferred from the aforementioned definitions to the merchant tenant risk
monitoring
method, while no repetition is made in this context. The various modules in
the
aforementioned merchant tenant risk monitoring device can be wholly or partly
realized
via software, hardware, and a combination of software with hardware. The
various
modules can be embedded in the form of hardware in a processor in a computer
equipment or independent of any computer equipment, and can also be stored in
the form
of software in a memory in a computer equipment, so as to facilitate the
processor to
invoke and perform operations corresponding to the aforementioned various
modules.
[0127] In one embodiment, a computer equipment is provided, the computer
equipment can be
a server, and its internal structure can be as shown in Fig. 6. The computer
equipment
comprises a processor, a memory, and a network interface connected to each
other via a
system bus. The processor of the computer equipment is employed to provide
computing
and controlling capabilities. The memory of the computer equipment includes a
nonvolatile storage medium and an internal memory. The nonvolatile storage
medium
stores therein an operating system, and a computer program. The internal
memory
provides environment for the running of the operating system and the computer
program
in the nonvolatile storage medium. The network interface of the computer
equipment is
Date Recue/Date Received 2022-06-01
employed to connect to an external terminal via network for communication. The
computer program realizes a merchant tenant monitoring method when it is
executed by
a processor.
[0128] As understandable to persons skilled in the art, the structure
illustrated in Fig. 6 is merely
a block diagram of partial structure relevant to the solution of the present
application, and
does not constitute any restriction to the computer equipment on which the
solution of
the present application is applied, as the specific computer equipment may
comprise
component parts that are more than or less than those illustrated in Fig. 6,
or may combine
certain component parts, or may have different layout of component parts.
[0129] In one embodiment, there is provided a computer equipment that
comprises a memory, a
processor and a computer program stored on the memory and operable on the
processor,
and the following steps are realized when the processor executes the computer
program:
obtaining risk assessment values before settlement to which plural target
merchant tenants
respectively correspond, and platform record data formed by platform
operations carried
out by the various target merchant tenants within a buffer period after
settlement;
performing feature extraction on the platform record data of the various
target merchant
tenants respectively, and obtaining feature vectors after settlement to which
the various
target merchant tenants correspond; employing an abnormality detection model
to
perform abnormality detection processing on a feature matrix constituted by
the feature
vectors after settlement to which the plural target merchant tenants
correspond, and
obtaining risk assessment values after settlement to which the various target
merchant
tenants correspond; and calculating comprehensive risk values to which the
various target
merchant tenants correspond according to the risk assessment values before and
after
settlement to which the various target merchant tenants correspond.
[0130] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: obtaining basic information data of a to-be-
settled merchant
26
Date Recue/Date Received 2022-06-01
tenant applying for settlement on the platform; performing feature extraction
on the basic
information data, and obtaining a feature vector before settlement of the to-
be-settled
merchant tenant; performing similarity matching calculation on the feature
vector before
settlement of the to-be-settled merchant tenant with a feature vector to which
each of
plural risky merchant tenants corresponds, and obtaining similarity values
between the
to-be-settled merchant tenant and the various risky merchant tenants;
calculating to obtain
a risk assessment value before settlement of the to-be-settled merchant tenant
according
to the similarity values between the to-be-settled merchant tenant and the
various risky
merchant tenants; and determining the to-be-settled merchant tenant as a
target merchant
tenant when the risk assessment value before settlement of the to-be-settled
merchant
tenant is not greater than a preset first risk assessment threshold.
[0131] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: sending check prompt information to a terminal for
prompting
to further assess a risk of the to-be-settled merchant tenant when the risk
assessment value
before settlement of the to-be-settled merchant tenant is greater than the
first risk
assessment threshold and is not greater than a preset second risk assessment
threshold;
and intercepting an application for settlement on the platform of the to-be-
settled
merchant tenant when the risk assessment value before settlement of the to-be-
settled
merchant tenant is greater than the second risk assessment threshold.
[0132] In one embodiment, the various risky merchant tenants are subordinate
to clusters
corresponding thereto, and the step of calculating to obtain a risk assessment
value before
settlement of the to-be-settled merchant tenant according to the similarity
values is
realized when the processor executes the computer program includes:
calculating to
obtain a risk assessment value before settlement of the to-be-settled merchant
tenant
according to the formula (2).
[0133] In one embodiment, the abnormality detection model is an isolation
forest model, and the
27
Date Recue/Date Received 2022-06-01
step of employing an abnormality detection model to perform abnormality
detection
processing on a feature matrix constituted by the feature vectors after
settlement to which
the plural target merchant tenants correspond, and obtaining risk assessment
values after
settlement to which the various target merchant tenants correspond is realized
when the
processor executes the computer program includes: inputting the feature matrix
into the
isolation forest model, outputting abnormality scores to which the various
target merchant
tenants correspond, numerically transforming the abnormality scores of the
various target
merchant tenants, and obtaining risk assessment values after settlement of the
various
target merchant tenants, wherein the risk assessment values after settlement
are valuated
in the range of being not smaller than 0 and not greater than 1.
[0134] In one embodiment, the step of calculating comprehensive risk values to
which the
various target merchant tenants correspond according to the risk assessment
values before
and after settlement to which the various target merchant tenants correspond
is realized
when the processor executes the computer program includes: respectively
weighting and
thereafter summating the risk assessment values before and after settlement to
which the
various target merchant tenants correspond, and obtaining the comprehensive
risk values
to which the various target merchant tenants correspond.
[0135] In one embodiment, there is provided a computer-readable storage medium
storing
thereon a computer program, and the following steps are realized when the
computer
program is executed by a processor: obtaining risk assessment values before
settlement
to which plural target merchant tenants respectively correspond, and platform
record data
formed by platform operations carried out by the various target merchant
tenants within
a buffer period after settlement; performing feature extraction on the
platform record data
of the various target merchant tenants respectively, and obtaining feature
vectors after
settlement to which the various target merchant tenants correspond; employing
an
abnormality detection model to perform abnormality detection processing on a
feature
matrix constituted by the feature vectors after settlement to which the plural
target
28
Date Recue/Date Received 2022-06-01
merchant tenants correspond, and obtaining risk assessment values after
settlement to
which the various target merchant tenants correspond; and calculating
comprehensive
risk values to which the various target merchant tenants correspond according
to the risk
assessment values before and after settlement to which the various target
merchant tenants
correspond.
[0136] In one embodiment, when the computer program is executed by a
processor, the following
steps are further realized: obtaining basic information data of a to-be-
settled merchant
tenant applying for settlement on the platform; performing feature extraction
on the basic
information data, and obtaining a feature vector before settlement of the to-
be-settled
merchant tenant; performing similarity matching calculation on the feature
vector before
settlement of the to-be-settled merchant tenant with a feature vector to which
each of
plural risky merchant tenants corresponds, and obtaining similarity values
between the
to-be-settled merchant tenant and the various risky merchant tenants;
calculating to obtain
a risk assessment value before settlement of the to-be-settled merchant tenant
according
to the similarity values between the to-be-settled merchant tenant and the
various risky
merchant tenants; and determining the to-be-settled merchant tenant as a
target merchant
tenant when the risk assessment value before settlement of the to-be-settled
merchant
tenant is not greater than a preset first risk assessment threshold.
[0137] In one embodiment, when the computer program is executed by a
processor, the following
steps are further realized: sending check prompt information to a terminal for
prompting
to further assess a risk of the to-be-settled merchant tenant when the risk
assessment value
before settlement of the to-be-settled merchant tenant is greater than the
first risk
assessment threshold and is not greater than a preset second risk assessment
threshold;
and intercepting an application for settlement on the platform of the to-be-
settled
merchant tenant when the risk assessment value before settlement of the to-be-
settled
merchant tenant is greater than the second risk assessment threshold.
29
Date Recue/Date Received 2022-06-01
[0138] In one embodiment, the various risky merchant tenants are subordinate
to clusters
corresponding thereto, and the step of calculating to obtain a risk assessment
value before
settlement of the to-be-settled merchant tenant according to the similarity
values is
realized when the computer program is executed by a processor includes
calculating to
obtain a risk assessment value before settlement of the to-be-settled merchant
tenant
according to the formula (2).
[0139] In one embodiment, the abnormality detection model is an isolation
forest model, and the
step of employing an abnormality detection model to perform abnormality
detection
processing on a feature matrix constituted by the feature vectors after
settlement to which
the plural target merchant tenants correspond, and obtaining risk assessment
values after
settlement to which the various target merchant tenants correspond is realized
when the
computer program is executed by a processor includes: inputting the feature
matrix into
the isolation forest model, outputting abnormality scores to which the various
target
merchant tenants correspond, numerically transforming the abnormality scores
of the
various target merchant tenants, and obtaining risk assessment values after
settlement of
the various target merchant tenants, wherein the risk assessment values after
settlement
are valuated in the range of being not smaller than 0 and not greater than 1.
[0140] In one embodiment, the step of calculating comprehensive risk values to
which the
various target merchant tenants correspond according to the risk assessment
values before
and after settlement to which the various target merchant tenants correspond
is realized
when the computer program is executed by a processor includes: respectively
weighting
and thereafter summating the risk assessment values before and after
settlement to which
the various target merchant tenants correspond, and obtaining the
comprehensive risk
values to which the various target merchant tenants correspond.
[0141] As comprehensible to persons ordinarily skilled in the art, the entire
or partial flows in
the methods according to the aforementioned embodiments can be completed via a
Date Recue/Date Received 2022-06-01
computer program instructing relevant hardware, the computer program can be
stored in
a nonvolatile computer-readable storage medium, and the computer program can
include
the flows as embodied in the aforementioned various methods when executed. Any
reference to the memory, storage, database or other media used in the various
embodiments provided by the present application can all include nonvolatile
and/or
volatile memory/memories. The nonvolatile memory can include a read-only
memory
(ROM), a programmable ROM (PROM), an electrically programmable ROM (EPROM),
an electrically erasable and programmable ROM (EEPROM) or a flash memory. The
volatile memory can include a random access memory (RAM) or an external cache
memory. To serve as explanation rather than restriction, the RAM is obtainable
in many
forms, such as static RAM (SRAM), dynamic RAM (DRAM), synchronous DRAM
(SDRAM), dual data rate SDRAM (DDRSDRAM), enhanced SDRAM (ESDRAM),
synchronous link (Synchlink) DRAM (SLDRAM), memory bus (Rambus) direct RAM
(RDRAM), direct Rambus dynamic RAM (DRDRAM), and Rambus dynamic RAM
(RDRAM), etc.
[0142] Technical features of the aforementioned embodiments are randomly
combinable, while
all possible combinations of the technical features in the aforementioned
embodiments
are not exhausted for the sake of brevity, but all these should be considered
to fall within
the scope recorded in the Description as long as such combinations of the
technical
features are not mutually contradictory.
[0143] The foregoing embodiments are merely directed to several modes of
execution of the
present application, and their descriptions are relatively specific and
detailed, but they
should not be hence misunderstood as restrictions to the inventive patent
scope. As should
be pointed out, persons with ordinary skill in the art may further make
various
modifications and improvements without departing from the conception of the
present
application, and all these should pertain to the protection scope of the
present application.
Accordingly, the patent protection scope of the present application shall be
based on the
31
Date Recue/Date Received 2022-06-01
attached Claims.
32
Date Recue/Date Received 2022-06-01