Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 03166981 2022-07-05
PERMISSION ABNORMALITY DETECTING METHOD, DEVICE, COMPUTER
EQUIPMENT AND STORAGE MEDIUM
BACKGROUND OF THE INVENTION
Technical Field
[0001] The present application relates to the field of computer technology,
and more particularly
to a permission abnormality detecting method, and corresponding device,
computer
equipment and storage medium.
Description of Related Art
[0002] With the development of the computer technology, mobile intelligent
platforms have been
vigorously progressing in both the aspects of hardware and software, the types
of various
sensors applicable to intelligent equipment are even more abundant and
advanced, being
capable of acquiring various user data and other information, the Android
system is much
favored by manufacturers and users alike by virtue of its open-source and free
of charge
qualities, and has become now the No.1 operating system of intelligent
equipment, but
the ensuing hidden risks to safety have also been becoming gradually
prominent, as a
great deal of events occurred over the recent years in which privacy data of
users was
leaked. However, currently available detections on the leakage of users'
privacy data put
complicated configuration requirements on operations, and the operation times
are
unduly long, so the detection efficiency is rendered low.
SUMMARY OF THE INVENTION
[0003] In view of the aforementioned technical problems, there is an urgent
need to provide a
permission abnormality detecting method, and corresponding device, computer
1
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
equipment and storage medium enabling quick detection of any anormal use
permission.
[0004] There is provided a permission abnormality detecting method that
comprises:
[0005] obtaining a source code to be detected;
[0006] detecting whether the source code to be detected has any matching
target analysis
keyword according to an association relation;
[0007] obtaining, when a matching target analysis keyword is present in the
source code to be
detected, a target permission that corresponds to the target analysis keyword;
[0008] detecting whether an original application manifest configuration file
has any target use
permission node that corresponds to the target permission; and
[0009] determining, when there is no target use permission node corresponding
to the target
permission, a permission to which the source code to be detected corresponds
as an
abnormal use permission.
[0010] In one of the embodiments, the method further comprises: obtaining an
original
application manifest configuration file to which an engineering project to be
detected
corresponds, wherein the original application manifest configuration file
includes use
permission nodes to which the engineering project to be detected corresponds;
extracting
the use permission nodes from the original application manifest configuration
file, and
obtaining a permission node list file, wherein the permission node list
includes a first use
permission; deleting permission content to which the use permission nodes
correspond in
the original application manifest configuration file, and obtaining an
intermediate
application manifest configuration file; detecting the intermediate
application manifest
configuration file, and obtaining a permission detection result list, wherein
the permission
detection result includes a second use permission; determining any abnormal
use
permission according to the permission node list file and the permission
detection result
list; and generating a permission abnormality detection report according to
the abnormal
use permission.
2
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0011] In one of the embodiments, the step of obtaining an original
application manifest
configuration file to which an engineering project to be detected corresponds
includes:
obtaining a system operation instruction; obtaining, when the system operation
instruction is operative for the first time, a system source code to which a
system in which
the engineering project to be detected resides corresponds; analyzing the
system source
code, and obtaining a development environment to which the system source code
corresponds; and obtaining, when the development environment is determined as
a
development environment supported by the system, an original application
manifest
configuration file to which the engineering project to be detected
corresponds.
[0012] In one of the embodiments, the step of determining any abnormal use
permission
according to the permission node list file and the permission detection result
list includes:
obtaining a current use permission; and determining the current use permission
as an
abnormal use permission if the current use permission is only present in the
permission
node list file or only present in the permission detection result list.
[0013] In one of the embodiments, the permission abnormality detecting method
further
comprises: obtaining a system source code to which the system in which the
engineering
project to be detected resides corresponds; analyzing the system source code,
and
obtaining a target permission in the system source code; obtaining an analysis
keyword
to which the target permission corresponds, and searching for matching source
code
content in the system source code according to the analysis keyword; and
creating a
corresponding association relation of the analysis keyword with the
corresponding source
code content.
[0014] In one of the embodiments, the step of obtaining an analysis keyword to
which the target
permission corresponds, and searching for matching source code content in the
system
source code according to the analysis keyword includes: traversing each row of
source
codes of the system source code; obtaining a current row of source codes, and
judging
3
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
whether the current row of source codes contains the analysis keyword; and
determining,
when the current row of source codes contains the analysis keyword, the
current row of
source codes as the source code content to which the analysis keyword
corresponds.
[0015] There is provided a permission abnormality detecting device that
comprises:
[0016] a first obtaining module, for obtaining a source code to be detected;
[0017] an analysis keyword matching module, for detecting whether the source
code to be
detected has any matching target analysis keyword according to an association
relation;
[0018] a second obtaining module, for obtaining, when a matching target
analysis keyword is
present in the source code to be detected, a target permission that
corresponds to the target
analysis keyword;
[0019] a permission node detecting module, for detecting whether an original
application
manifest configuration file has any target use permission node that
corresponds to the
target permission; and
[0020] an abnormal use permission determining module, for determining, when
there is no target
use permission node corresponding to the target permission, a permission to
which the
source code to be detected corresponds as an abnormal use permission.
[0021] There is provided a computer equipment that comprises a memory, a
processor and a
computer program stored on the memory and operable on the processor, and the
following
steps are realized when the processor executes the computer program:
[0022] obtaining a source code to be detected;
[0023] detecting whether the source code to be detected has any matching
target analysis
keyword according to an association relation;
[0024] obtaining, when a matching target analysis keyword is present in the
source code to be
detected, a target permission that corresponds to the target analysis keyword;
[0025] detecting whether an original application manifest configuration file
has any target use
permission node that corresponds to the target permission; and
[0026] determining, when there is no target use permission node corresponding
to the target
4
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
permission, a permission to which the source code to be detected corresponds
as an
abnormal use permission.
[0027] There is provided a computer-readable storage medium storing a computer
program
thereon, and the following steps are realized when the computer program is
executed by
a processor:
[0028] obtaining a source code to be detected;
[0029] detecting whether the source code to be detected has any matching
target analysis
keyword according to an association relation;
[0030] obtaining, when a matching target analysis keyword is present in the
source code to be
detected, a target permission that corresponds to the target analysis keyword;
[0031] detecting whether an original application manifest configuration file
has any target use
permission node that corresponds to the target permission; and
[0032] determining, when there is no target use permission node corresponding
to the target
permission, a permission to which the source code to be detected corresponds
as an
abnormal use permission.
[0033] In the aforementioned permission abnormality detecting method,
corresponding device,
computer equipment and storage medium, a source code to be detected is
obtained, it is
detected whether the source code to be detected has any matching target
analysis keyword
according to an association relation, when a matching target analysis keyword
is present
in the source code to be detected, a target permission that corresponds to the
target
analysis keyword is obtained, it is detected whether an original application
manifest
configuration file has any target use permission node that corresponds to the
target
permission, and when there is no target use permission node corresponding to
the target
permission, it is determined that a permission to which the source code to be
detected
corresponds is an abnormal use permission. By means of this method, through
the
association relation an analysis keyword that corresponds to the source code
to be
detected can be obtained, an original application manifest configuration file
can be
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
obtained, and it can be determined whether the permission to which the source
code to be
detected corresponds is an abnormal use permission by detecting whether the
original
application manifest configuration file has any target use permission node
that
corresponds to the target permission, not any configuration is required, and
the efficiency
in detecting abnormal use permissions is enhanced.
BRIEF DESCRIPTION OF THE DRAWINGS
[0034] Fig. 1 is a view illustrating the application environment for a
permission abnormality
detecting method in an embodiment;
[0035] Fig. 2 is a flowchart schematically illustrating a permission
abnormality detecting method
in an embodiment;
[0036] Fig. 3 is a flowchart schematically illustrating a permission
abnormality detecting method
in another embodiment;
[0037] Fig. 4 is a flowchart schematically illustrating a step of obtaining an
original application
manifest configuration file in an embodiment;
[0038] Fig. 5 is a flowchart schematically illustrating a step of determining
an abnormal use
permission in an embodiment;
[0039] Fig. 6 is a flowchart schematically illustrating a permission
abnormality detecting method
in another embodiment;
[0040] Fig. 7 is a flowchart schematically illustrating a step of searching
for source code content
in an embodiment;
6
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0041] Fig. 8 is a block diagram illustrating the structure of a permission
abnormality detecting
device in an embodiment;
[0042] Fig. 9 is a block diagram illustrating the structure of a permission
abnormality detecting
device in another embodiment;
[0043] Fig. 10 is a block diagram illustrating the structure of a manifest
configuration file
obtaining module in an embodiment;
[0044] Fig. 11 is a block diagram illustrating the structure of a permission
abnormality detecting
device in another embodiment; and
[0045] Fig. 12 is a block diagram illustrating the internal structure of a
computer equipment in
an embodiment.
DETAILED DESCRIPTION OF THE INVENTION
[0046] To make more lucid and clear the objectives, technical solutions and
advantages of the
present application, the present application is described in greater detail
below with
reference to accompanying drawings and embodiments. As should be understood,
the
specific embodiments described here are merely meant to explain the present
application,
rather than to restrict the present application.
[0047] The permission abnormality detecting method provided by the present
application is
applicable to the application environment as shown in Fig. 1, in which
terminal 102
communicates with server 104 through network. Terminal 102 can be, but is not
limited
to be, any of various personal computers, notebook computers, smart mobile
phones,
panel computers, and portable wearable devices, and server 104 can be embodied
as an
independent server or a server cluster consisting of a plurality of servers.
7
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0048] Specifically, terminal 102 can obtain a source code to be detected, and
send the obtained
source code to be detected to server 104; upon reception of the source code to
be detected,
server 104 detects whether the source code to be detected has any matching
target analysis
keyword according to an association relation, when a matching target analysis
keyword
is present in the source code to be detected, obtains a target permission that
corresponds
to the target analysis keyword, detects whether an original application
manifest
configuration file has any target use permission node that corresponds to the
target
permission, and, when there is no target use permission node corresponding to
the target
permission, determines that a permission to which the source code to be
detected
corresponds is an abnormal use permission. Further, server 104 can send the
abnormal
use permission to terminal 102 for check by the developer of terminal 102.
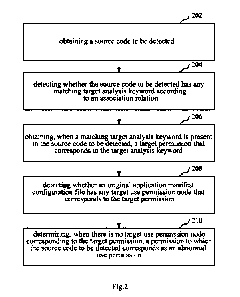
[0049] In one embodiment, as shown in Fig. 2, there is provided a permission
abnormality
detecting method, and the method is explained with an example of its being
applied to
the terminal or server in Fig. 1, to comprise the following steps.
[0050] Step 202 - obtaining a source code to be detected.
[0051] Step 204 - detecting whether the source code to be detected has any
matching target
analysis keyword according to an association relation.
[0052] Step 206 - obtaining, when a matching target analysis keyword is
present in the source
code to be detected, a target permission that corresponds to the target
analysis keyword.
[0053] The source code to be detected here indicates a candidate source code
for detection, it can
be either a source code to which an engineering project to be detected
corresponds, or a
source code to which the system in which the engineering project resides
corresponds.
Specifically, previously created association relations are obtained, since the
association
8
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
relations are relations between the source code content and analysis keywords,
it is
therefore possible to detect according to the association relations whether
there is any
matching target analysis keyword in the source code to be detected, namely to
match and
obtain a target analysis keyword to which the source code to be detected
corresponds
according to the association relations, and the process can specifically be to
detect
whether there is source code content identical with the source code to be
detected in the
association relations, if there is, to take the analysis keyword to which the
source code
content corresponds as an analysis keyword matching the source code to be
detected, and
to further obtain a target permission to which the target analysis keyword
corresponds, if
there is no, to discard the source code to be detected.
[0054] Step 208 ¨ detecting whether an original application manifest
configuration file has any
target use permission node that corresponds to the target permission.
[0055] Step 210¨ determining, when there is no target use permission node
corresponding to the
target permission, a permission to which the source code to be detected
corresponds as
an abnormal use permission.
[0056] Specifically, all use permission nodes in the original application
manifest configuration
file are obtained, the various use permission nodes include their respective
corresponding
use permissions, and it is detected whether the use permissions to which the
use
permission nodes correspond include a target permission, in other words, it is
detected
whether the original application manifest configuration file contains any
target
permission. When it is detected that the use permissions to which the use
permission
nodes correspond in the original application manifest configuration file
include a target
permission, this indicates that the target permission has been declared in the
original
application manifest configuration file, then it can be determined as a normal
use
permission. To the contrary, when it is detected that the use permissions to
which the use
permission nodes correspond in the original application manifest configuration
file do not
9
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
include any target permission, this indicates that no target permission has
been declared
in the original application manifest configuration file, then there might be
the missing of
use permission, and it is then determined that the permission to which the
source code to
be detected corresponds is an abnormal use permission.
[0057] In the aforementioned permission abnormality detecting method, a source
code to be
detected is obtained, it is detected whether the source code to be detected
has any
matching target analysis keyword according to an association relation, when a
matching
target analysis keyword is present in the source code to be detected, a target
permission
that corresponds to the target analysis keyword is obtained, it is detected
whether an
original application manifest configuration file has any target use permission
node that
corresponds to the target permission, and when there is no target use
permission node
corresponding to the target permission, it is determined that a permission to
which the
source code to be detected corresponds is an abnormal use permission. By means
of this
method, through the association relation an analysis keyword that corresponds
to the
source code to be detected can be obtained, an original application manifest
configuration
file can be obtained, and it can be determined whether the permission to which
the source
code to be detected corresponds is an abnormal use permission by detecting
whether the
original application manifest configuration file has any target use permission
node that
corresponds to the target permission, not any configuration is required, and
the efficiency
in detecting abnormal use permissions is enhanced.
[0058] In one embodiment, as shown in Fig. 3, the permission abnormality
detecting method
further comprises the following steps.
[0059] Step 302 - obtaining an original application manifest configuration
file to which an
engineering project to be detected corresponds, wherein the original
application manifest
configuration file includes use permission nodes to which the engineering
project to be
detected corresponds.
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0060] The application manifest configuration file is an information
description file of the
engineering project, the application manifest configuration file includes, but
is not limited
to include, various pieces of component information to which the engineering
project to
be detected corresponds, and the various components can be Activity, Service,
Content
provider, and BroadcastReceiver. The application manifest configuration file
can be
AndroidManifest.xml that defines the information of the components Activity,
Service,
Content provider, and BroadcastReceiver contained in the engineering project
to be
detected. Each engineering project must contain an AndroidManifest.xml file
under the
root directory, and the filename thereof cannot be modified.
[0061] The application manifest configuration file includes use permission
nodes to which the
engineering project to be detected corresponds, the use permission nodes here
are
employed to declare permissions of the engineering project to be detected, the
use
permission nodes can be use-permission nodes that are employed to declare
corresponding permissions of the engineering project to be detected, and all
use
permission nodes have corresponding permission contents. The original
application
manifest configuration file to which the engineering project corresponds
includes at least
one use permission node.
[0062] Step 304 - extracting the use permission nodes from the original
application manifest
configuration file, and obtaining a permission node list file, wherein the
permission node
list includes a first use permission.
[0063] The first use permission here is a use permission declared by the
various use permission
nodes in the permission node list. The original application manifest
configuration file to
which the engineering project corresponds includes at least one use permission
node, all
use permission nodes in the original application manifest configuration file
are entirely
extracted out to form a permission node list file. Since the permission node
is employed
11
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
to declare the corresponding permission, the extracted permission nodes
include
corresponding use permissions, then the permission node list includes the
first use
permission. That is, the permission node list file only includes the use
permission nodes
in the original application manifest configuration file, while the use
permission nodes are
employed to declare corresponding permissions, so the permission node list
further
includes the first use permission to which the use permission nodes
correspond.
[0064] In one embodiment, for instance, the original application manifest
configuration file
AndroidManifest.xml in the engineering project to be detected is marked as
file A. All
use permission nodes <use-permission> in file A are saved in a list file C. A
is the original
application manifest configuration file, and C is the permission node list
file.
[0065] Step 306 - deleting permission content to which the use permission
nodes correspond in
the original application manifest configuration file, and obtaining an
intermediate
application manifest configuration file.
[0066] Specifically, after the permission node list file has been obtained,
permission contents to
which the use permission nodes correspond in the original application manifest
configuration file are deleted, and a new intermediate application manifest
configuration
file is obtained. The process can specifically be to obtain permission
contents to which
the various use permission nodes correspond in the original application
manifest
configuration file, to delete the permission contents to which the various use
permission
nodes correspond, and to obtain the intermediate application manifest
configuration file;
the intermediate application manifest configuration file does not include the
permission
contents to which the use permission nodes correspond at this time, but the
intermediate
application manifest configuration file still includes permission contents to
which other
nodes correspond.
[0067] In one embodiment, for instance, the original application manifest
configuration file
12
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
AndroidManifest.xml in the engineering project to be detected is marked as
file A. All
use permission nodes <use-permission> in file A are saved in a list file C. A
is the original
application manifest configuration file, and C is the permission node list
file. Further,
permission contents to which permission nodes <use-permission> in file A
correspond
are entirely deleted, and a new application manifest configuration file D is
obtained.
[0068] Step 308 - detecting the intermediate application manifest
configuration file, and
obtaining a permission detection result list, wherein the permission detection
result
includes a second use permission.
[0069] Specifically, after the intermediate application manifest configuration
file has been
obtained, the intermediate application manifest configuration file is
detected, a
DroidPrivacyChecker detecting system can be specifically employed to
automatically
detect the intermediate application manifest configuration file, the
DroidPrivacyChecker
detecting system is open-sourced, the detecting system can directly perform an
analyzing
process on the intermediate application manifest configuration file, and the
detecting
system abides by a certain rule to detect during the detecting process, so as
to obtain a
detection result, which is precisely the permission detection result list. The
rule here can
be self-defined, and such self-definition can be determined according to
practical business
requirement or specific application scenario.
[0070] The permission detection result here includes a second use permission,
the second use
permission here is a use permission to which the intermediate application
manifest
configuration file corresponds, although the intermediate application manifest
configuration file does not include any use permission node, the intermediate
application
manifest configuration file still includes self-defined use permission nodes,
and the
second use permission here is a permission to which a self-defined use
permission node
corresponds. Use permission nodes and self-defined use permission nodes are
different
in meanings, as the use permission nodes are employed by the engineering
project to be
13
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
detected to declare corresponding permissions during installation, and can be
use-
permission, whereas the self-defined use permission nodes are employed by the
engineering project to be detected to self-define to declare corresponding
permissions
according to practical requirement or the business scenario, and can be
permission.
[0071] Step 310 - determining any abnormal use permission according to the
permission node
list file and the permission detection result list.
[0072] Specifically, after the permission detection result list has been
obtained, any abnormal
use permission can be determined according to the permission node list file
and the
permission detection result list. Determination of any abnormal use permission
can be to
take the permission node list file as a standard, to compare the permission
node list file
with the permission detection result list, and to determine any missing use
permission and
redundant use permission in the permission detection result list as abnormal
use
permissions. Specifically, a current use permission is obtained, the current
use permission
can be a use permission randomly determined in the permission node list file
to serve as
the current use permission, it is alternatively also possible to base on
priorities of various
use permissions in the permission node list file to sequentially take the
various use
permissions to serve as the current use permission according to the
priorities, when the
current use permission is only present in the permission node list file or
only present in
the permission detection result list, the current use permission is determined
as an
abnormal use permission.
[0073] When the current use permission is only present in the permission node
list file, this
indicates that a redundant permission declaration on the current use
permission is present
in the engineering project to be detected, this current use permission is not
required in the
engineering project to be detected, but it has been declared in the
application manifest
configuration file, so it might be illegally used by other malicious
application programs
in the future, thereby causing leakage of users' privacy data.
14
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0074] When the current use permission is only present in the permission
detection result list,
this indicates that the current use permission may be present in the
engineering project to
be detected, while a crash of application program generated by the engineering
project to
be detected would be caused when the engineering project to be detected runs
to the point
of requiring the current use permission. Accordingly, when the current use
permission is
only present in the permission node list file or only present in the
permission detection
result list, the current use permission is determined as an abnormal use
permission.
[0075] Step 312 - generating a permission abnormality detection report
according to the
abnormal use permission.
[0076] Specifically, after the abnormal use permission has been obtained, the
abnormal use
permission can be presented to the developing personnel for check thereby in
the form of
a permission abnormality detection report. The developing personnel may make
modification according to the permission abnormality detection report, to
avoid leakage
of users' privacy data, to thereby avoid unnecessary financial loss to the
company and the
users.
[0077] In one embodiment, for instance, the original application manifest
configuration file
AndroidManifest.xml in the engineering project to be detected is marked as
file A, which
is simultaneously backed up and marked as file B. All use permission nodes
<use-
permission> in file A are saved in a list file C. A is the original
application manifest
configuration file, and C is the permission node list file.
[0078] Moreover, the permission contents to which the permission nodes <use-
permission> in
file A are entirely deleted, and a new application manifest configuration file
a is obtained.
It is stored and completely placed back in the directory in which the original
application
manifest configuration file AndroidManifest.xml resides in the corresponding
directory
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
of the engineering project to be detected, under the condition the filename of
file A is not
modified, to cover the original file, and the DroidPrivacyChecker detecting
system
automatically invokes a lint command "lint¨check MissingPermission myproject"
to
perform dedicated detection of the abnormal use permission Missing-Permission
on the
engineering project to be detected, in which my project is the name of the
engineering
project to be detected.
[0079] Furthermore, after the command has been executed to completion, the
detection is parsed
to generate and obtain a permission detection result list result.xml, namely
to obtain the
permission detection result list D. Thereafter, each use permission is
compared in the
permission detection result list D and the permission node list file C, if a
certain use
permission (marked as E) is only present in C, this indicates that a redundant
permission
declaration on E is present in the engineering project to be detected, this
permission is
not required in the engineering project to be detected but declared for use,
so it would be
much possibly illegally used by other malicious application programs, thereby
causing
leakage of users' information. If a certain use permission (marked as F) is
only present in
D, this indicates that declaration on permission F may be present in the
engineering
project to be detected, while a crash of application program generated by the
engineering
project to be detected would be caused when the program runs to the point of
requiring
permission F.
[0080] Finally, a permission abnormality detection report is generated
according to the abnormal
use permission generated above, after generation the backed-up file B is
placed back to
cover file A to restore to the original file status of the engineering project
to be detected,
and to prevent the detecting procedure from affecting the engineering project
to be
detected.
[0081] In the aforementioned permission abnormality detecting method, an
original application
manifest configuration file to which the engineering project to be detected
corresponds is
16
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
obtained, the original application manifest configuration file includes use
permission
nodes and a corresponding first use permission, and the permission contents to
which the
use permission nodes correspond in the original application manifest
configuration file
are then deleted to obtain an intermediate application manifest configuration
file. The
intermediate application manifest configuration file is then detected to
obtain a
permission detection result list that includes a second use permission, and
the abnormal
use permission is finally determined according to the permission node list
file and the
permission detection result list, to thereby generate a permission abnormality
detection
report. Through this method, the abnormal use permission can be detected only
by
obtaining the original application manifest configuration file of the
engineering project
to be detected, not any configuration is required, and the efficiency in
detecting abnormal
use permissions is enhanced.
[0082] In one embodiment, as shown in Fig. 4, the step of obtaining an
original application
manifest configuration file to which an engineering project to be detected
corresponds
includes the following.
[0083] Step 402 - obtaining a system operation instruction.
[0084] Step 404 - obtaining, when the system operation instruction is
operative for the first time,
a system source code to which a system in which the engineering project to be
detected
resides corresponds.
[0085] The system operation instruction is used to instruct operation of the
system in which the
project to be detected resides, if a terminal serves as the executing subject,
the terminal
is installed with an application relevant to permission abnormality detection,
the system
operation instruction can be generated by triggering through the application,
and it is
specifically possible to trigger to generate the system operation instruction
through a
clicking operation or a voicing operation acting on a presentation interface
of the
17
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
application. In one embodiment, if a server serves as the executing subject,
after the
terminal has triggered to generate the system operation instruction, the
system operation
instruction is sent to the server through network connection. Alternatively,
the server can
directly obtain the system operation instruction, and it is not required to
obtain the system
operation instruction through the terminal, for instance, the system operation
instruction
is triggered through a timed event.
[0086] Specifically, after the system operation instruction has been obtained,
it is required to
detect whether the system operation instruction is operative for the first
time, when it is
detected that the system operation instruction is operative for the first
time, the system
source code to which the system in which the engineering project to be
detected resides
corresponds is obtained. The so-called system source code is a source code
related to the
system, for instance, the Android system source code can be the system source
code.
[0087] Step 406 - analyzing the system source code, and obtaining a
development environment
to which the system source code corresponds.
[0088] Step 408 - obtaining, when the development environment is determined as
a development
environment supported by the system, an original application manifest
configuration file
to which the engineering project to be detected corresponds.
[0089] Specifically, after the system source code to which the system in which
the engineering
project to be detected resides corresponds has been obtained, the system
source code is
analyzed, and the development environment in which the engineering project to
be
detected resides can be obtained from the system source code. It is
specifically possible
to analyze the system source code with the help of the DroidPrivacyChecker
detecting
system, and to analyze the meaning to which each row of codes in the system
source code
corresponds to obtain the corresponding development environment. Further, it
is then
detected whether the development environment obtained by analysis is a
development
18
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
environment supported by the system in which the engineering project to be
detected
resides, and it is specifically possible to obtain a development environment
supported by
the system, and to detect whether the development environment supported by the
system
matches the development environment to which the system source code
corresponds,
when the two match, it can then be determined that the development environment
to
which the system source code corresponds is a development environment
supported by
the system, to the contrary, if the two do not match, it can then be
determined that the
development environment to which the system source code corresponds is not a
development environment supported by the system.
[0090] Finally, after the development environment to which the system source
code corresponds
has been determined to be a development environment supported by the system,
the
original application manifest configuration file to which the engineering
project to be
detected corresponds is obtained.
[0091] In one embodiment, as shown in Fig. 5, the step of determining any
abnormal use
permission according to the permission node list file and the permission
detection result
list includes:
[0092] Step 502 - obtaining a current use permission; and
[0093] Step 504 - determining the current use permission as an abnormal use
permission if the
current use permission is only present in the permission node list file or
only present in
the permission detection result list.
[0094] The current use permission here is a use permission currently being
used for processing,
it is possible to randomly select a use permission from the first use
permissions in the
permission node list file to serve as the current use permission, or to
sequentially take the
first use permissions according to their priorities in the permission node
list file to serve
as the current use permission. The current use permission can also be selected
from the
use permissions in the permission detection result list to serve as the
current use
19
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
permission, likewise, it is possible to randomly select a use permission from
the second
use permissions in the permission detection result list to serve as the
current use
permission, or to sequentially take the second use permissions according to
their priorities
in the permission detection result list to serve as the current use
permission.
[0095] Moreover, it is detected whether the current use permission is
simultaneously present in
the permission node list file and the permission detection result list, when
it is detected
that the current use permission is only present in the permission node list
file or only
present in the permission detection result list, the current use permission is
determined as
an abnormal use permission. The circumstance in which the current use
permission is
only present in the permission node list file or only present in the
permission detection
result list can be that the current use permission is present in the
permission node list file
and is not present in the permission detection result list, or that the
current use permission
is present in the permission detection result list and is not present in the
permission node
list file.
[0096] When the current use permission is only present in the permission node
list file, this
indicates that a redundant permission declaration on the current use
permission is present
in the engineering project to be detected, this current use permission is not
required in the
engineering project to be detected, but it has been declared in the
application manifest
configuration file, so it might be illegally used by other malicious
application programs
in the future, thereby causing leakage of users' privacy data.
[0097] When the current use permission is only present in the permission
detection result list,
this indicates that the current use permission may be present in the
engineering project to
be detected, while a crash of application program generated by the engineering
project to
be detected would be caused when the engineering project to be detected runs
to the point
of requiring the current use permission.
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0098] Accordingly, to sum it up, when the current use permission is only
present in the
permission node list file or only present in the permission detection result
list, the current
use permission can be determined as an abnormal use permission.
[0099] In one embodiment, as shown in Fig. 6, the permission abnormality
detecting method
further comprises the following steps.
[0100] Step 602 - obtaining a system source code to which the system in which
the engineering
project to be detected resides corresponds.
[0101] Step 604 - analyzing the system source code, and obtaining a target
permission in the
system source code.
[0102] The system source code here is a source code related to the system, for
instance, the
Android system source code can be the system source code. Specifically, the
system
source code to which the system in which the engineering project to be
detected resides
corresponds is obtained, because the permission of the system can be declared
via the
system source code, the system source code can be again analyzed to obtain a
target
permission in the system source code. The target permission here indicates a
use
permission that conforms to a preset condition, the preset condition can be
self-defined,
such self-definition can be determined and obtained according to the levels of
the use
permissions, or determined and obtained according to the meanings of the use
permissions.
[0103] In one embodiment, for instance, levels of the use permissions are
classified as normal
permission and danger permission, the target permission can be a danger
permission,
because it is almost impossible for a normal permission to get in touch with
user privacy
data, for example, a permission to set the time zone is a normal permission.
Of course, if
a user considers time zone data as his privacy data, the "normal permission"
can still get
21
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
in touch with such data. If it is declared in the system source code that it
requires a
"normal permission", such permission will be automatically granted to the
engineering
project to be detected. The danger permission subsumes all privacy data of the
user
possibly got in touch with. For instance, the capability to obtain short
message content
pertains to a danger permission. If it is declared in the system source code
that it requires
a certain danger permission or some certain danger permissions, the
engineering project
to be detected will pop up a window to remind the user during operation,
enquiring
whether the user grants the currently requested permission to the engineering
project to
be detected, and the permission can be used by the application only after the
user clicks
to confirm authorization. The behavior modes of many permissions are different
from
both normal permissions and danger permissions. Some such permissions as
system
floating window permission and permission to modify system setup, etc. also
pertain to
danger permissions, and are also extremely sensitive to the system in which
the
engineering project to be detected resides, so most engineering projects to be
detected
should not use such permissions. If a certain engineering project to be
detected requires
a certain permission therefrom, the permission should be declared in the
system source
code.
[0104] Step 606 ¨ obtaining an analysis keyword to which the target permission
corresponds,
and searching for matching source code content in the system source code
according to
the analysis keyword.
[0105] Step 608 ¨creating a corresponding association relation of the analysis
keyword with the
corresponding source code content.
[0106] The analysis keyword here is used to identify the corresponding target
permission, and
the corresponding target permission can be identified with preset fields.
Specifically, after
the target permission in the system source code has been obtained, the
analysis keyword
to which the target permission corresponds can be obtained, for instance,
22
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
READ CALENDAR, WRITE CALENDAR can both serve as analysis keywords to
which the target permission corresponds. Moreover, searching for matching
source code
content in the system source code according to the analysis keyword can
specifically be
to base on the analysis keyword to search for the corresponding location of
the analysis
keyword in the system source code, then determine the corresponding source
code content
according to the location, and hence create an association relation of the
source code
content with the corresponding analysis keyword. For instance, each row of
codes of the
system source code is traversed to detect whether the analysis keyword appears
in any
row of codes of the system source code, after it has been detected that the
analysis
keyword appears in a certain row of codes, a corresponding association
relation of the
code content to which this row of codes corresponds can be created with the
analysis
keyword.
[0107] In one embodiment, for instance, the target permission is a danger
permission, and all
danger permissions can be set as corresponding analysis keywords, for
instance,
android.Manifest.permission is an application manifest configuration file,
that is to say,
analysis keywords are used in the application manifest configuration file to
identify
corresponding use permissions:
[0108] android.Manifest.permission#READ CALENDAR
[0109] android.Manifest.permission#WRITE CALENDAR
[0110] android.Manifest.permission#CAMERA
[0111] android.Manifest.permission#READ CONTACTS
[0112] android.Manifest.permission#WRITE CONTACTS
[0113] android.Manifest.permission#GET ACCOUNTS
[0114] android.Manifest.permission#ACCESS FINE LOCATION
[0115] android.Manifest.permission#ACCESS COARSE LOCATION
[0116] android.Manifest.permission#RECORD AUDIO
[0117] android.Manifest.permission#READ PHONE STATE
[0118] android.Manifest.permission#CALL PHONE
23
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0119] android.Manifest.permission#READ CALL LOG
[0120] android.Manifest.permission#WRITE CALL LOG
[0121] android.Manifest.permission#ADD VOICEMAIL
[0122] android.Manifest.permission#USE SIP
[0123] android.Manifest.permission#PROCESS OUTGOING CALLS
[0124] android.Manifest.permission#BODY SENSORS
[0125] android.Manifest.permission#SEND SMS
[0126] android.Manifest.permission#RECEIVE SMS
[0127] android.Manifest.permission#READ SMS
[0128] android.Manifest.permission#RECEIVE WAP PUSH
[0129] android.Manifest.permission#RECEIVE MMS
[0130] Subsequently, each row of codes of the system source code is traversed
to detect whether
any analysis keyword appears in any row of codes of the system source code,
after it has
been detected that an analysis keyword appears in a certain row of codes, a
corresponding
association relation of the code content to which this row of codes
corresponds can be
created with the analysis keyword, for instance, the source code content to
which the
analysis keyword READ CALENDAR corresponds is the content of the one-
thousandth
row in the system source code, an association relation of READ CALENDAR is
then
created with the content of the one-thousandth row in the system source code.
[0131] In one embodiment, as shown in Fig. 7, the step of obtaining an
analysis keyword to
which the target permission corresponds, and searching for matching source
code content
in the system source code according to the analysis keyword includes:
[0132] Step 702 - traversing each row of source codes of the system source
code;
[0133] Step 704 - obtaining a current row of source codes, and judging whether
the current row
of source codes contains the analysis keyword; and
[0134] Step 706 - determining, when the current row of source codes contains
the analysis
keyword, the current row of source codes as the source code content to which
the analysis
24
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
keyword corresponds.
[0135] The system source code includes at least one row of source codes, each
row of source
codes includes corresponding source code content, and searching for matching
source
code content in the system source code according to the analysis keyword can
specifically
be to traverse each row of source codes of the system source code, and obtain
a current
row of source codes, the current row of source codes indicates source codes
currently
being used for processing, it is possible to randomly determine a row of
source codes
from the system source code to serve as the current row of source codes, and
it is also
possible to sequentially take each row in the system source code to serve as
the current
row of source codes. Moreover, judging whether the current row of source codes
contains
the analysis keyword can specifically be to detect whether the analysis
keyword is present
in the current row of source codes, if the analysis keyword is present in the
current row
of source codes, the current row of source codes is determined as the source
code content
to which the analysis keyword corresponds, otherwise, the next row of source
codes is
obtained, the next row of source codes is taken to serve as the current row of
source codes,
and the step is returned to judge whether the current row of source codes
contains the
analysis keyword, so on and so forth, until the source code contents to which
all analysis
keywords correspond are obtained.
[0136] In one embodiment, for instance, the target permission is a danger
permission, and all
danger permissions can be set as corresponding analysis keywords, for
instance,
android.Manifest.permission is an application manifest configuration file,
that is to say,
analysis keywords are used in the application manifest configuration file to
identify
corresponding use permissions:
[0137] android.Manifest.permission#READ CALENDAR
[0138] android.Manifest.permission#WRITE CALENDAR
[0139] an dro i d.Man i fest.permi s si on#CAMERA
[0140] android.Manifest.permission#READ CONTACTS
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0141] Thereafter, each row of codes of the system source code is again
traversed to detect
whether any analysis keyword appears in any row of codes of the system source
code,
after it has been detected that an analysis keyword appears in a certain row
of codes, a
corresponding association relation of the code content to which this row of
codes
corresponds can be created with the analysis keyword, for instance, the source
code
content to which the analysis keyword READ CALENDAR corresponds is the content
of the one-thousandth row in the system source code, the one-thousandth row of
source
code content is then determined to be the source code content to which the
analysis
keyword READ CALENDAR corresponds.
[0142] In a specific embodiment, there is provided a permission abnormality
detecting method
that specifically comprises the following steps:
[0143] 1. obtaining an original application manifest configuration file to
which an engineering
project to be detected corresponds, wherein the original application manifest
configuration file includes use permission nodes to which the engineering
project to be
detected corresponds;
[0144] 1-1, obtaining a system operation instruction;
[0145] 1-2, obtaining, when the system operation instruction is operative for
the first time, a
system source code to which a system in which the engineering project to be
detected
resides corresponds;
[0146] 1-3, analyzing the system source code, and obtaining a development
environment to
which the system source code corresponds;
[0147] 1-4, obtaining, when the development environment is determined as a
development
environment supported by the system, an original application manifest
configuration file
to which the engineering project to be detected corresponds;
[0148] 2. extracting the use permission nodes from the original application
manifest
configuration file, and obtaining a permission node list file, wherein the
permission node
list includes a first use permission;
26
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0149] 3. deleting permission content to which the use permission nodes
correspond in the
original application manifest configuration file, and obtaining an
intermediate application
manifest configuration file;
[0150] 4. detecting the intermediate application manifest configuration file,
and obtaining a
permission detection result list, wherein the permission detection result
includes a second
use permission;
[0151] 5. determining any abnormal use permission according to the permission
node list file
and the permission detection result list;
[0152] 5-1. obtaining a current use permission;
[0153] 5-2. determining the current use permission as an abnormal use
permission if the current
use permission is only present in the permission node list file or only
present in the
permission detection result list;
[0154] 6. generating a permission abnormality detection report according to
the abnormal use
permission;
[0155] 7. obtaining a system source code to which the system in which the
engineering project
to be detected resides corresponds;
[0156] 8. analyzing the system source code, and obtaining a target permission
in the system
source code;
[0157] 9. obtaining an analysis keyword to which the target permission
corresponds, and
searching for matching source code content in the system source code according
to the
analysis keyword;
[0158] 9-1. traversing each row of source codes of the system source code;
[0159] 9-2. obtaining a current row of source codes, and judging whether the
current row of
source codes contains the analysis keyword;
[0160] 9-3. determining, when the current row of source codes contains the
analysis keyword,
the current row of source codes as the source code content to which the
analysis keyword
corresponds;
[0161] 10. creating a corresponding association relation of the analysis
keyword with the
corresponding source code content;
27
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0162] 11. obtaining a source code to be detected;
[0163] 12. detecting whether the source code to be detected has any matching
target analysis
keyword according to the association relation;
[0164] 13. obtaining, when a matching target analysis keyword is present in
the source code to
be detected, a target permission that corresponds to the target analysis
keyword;
[0165] 14. detecting whether an original application manifest configuration
file has any use
permission node to which the target permission corresponds; and
[0166] 15. determining, when there is no use permission node corresponding to
the target
permission, a permission to which the source code to be detected corresponds
as an
abnormal use permission.
[0167] As should be understood, although the various steps in the
aforementioned flowcharts are
sequentially displayed as indicated by arrows, these steps are not necessarily
executed in
the sequences indicated by arrows. Unless otherwise explicitly noted in this
paper,
execution of these steps is not restricted by any sequence, as these steps can
also be
executed in other sequences (than those indicated in the drawings). Moreover,
at least
partial steps in the flowcharts may include plural sub-steps or multi-phases,
these sub-
steps or phases are not necessarily completed at the same timing, but can be
executed at
different timings, and these sub-steps or phases are also not necessarily
sequentially
performed, but can be performed in turns or alternately with other steps or
with at least
some of sub-steps or phases of other steps.
[0168] In one embodiment, as shown in Fig. 8, there is provided a permission
abnormality
detecting device 800 that comprises a first obtaining module 802, an analysis
keyword
matching module 804, a second obtaining module 806, a permission node
detecting
module 808, and an abnormal use permission determining module 810, of which
[0169] the first obtaining module 802 is employed for obtaining a source code
to be detected;
[0170] the analysis keyword matching module 804 is employed for detecting
whether the source
code to be detected has any matching target analysis keyword according to an
association
28
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
relation;
[0171] the second obtaining module 806 is employed for obtaining, when a
matching target
analysis keyword is present in the source code to be detected, a target
permission that
corresponds to the target analysis keyword;
[0172] the permission node detecting module 808 is employed for detecting
whether an original
application manifest configuration file has any target use permission node
that
corresponds to the target permission; and
[0173] the abnormal use permission determining module 810 is employed for
determining, when
there is no target use permission node corresponding to the target permission,
a
permission to which the source code to be detected corresponds as an abnormal
use
permission.
[0174] In one embodiment, as shown in Fig. 9, the permission abnormality
detecting device 800
further comprises:
[0175] a manifest configuration file obtaining module 902, for obtaining an
original application
manifest configuration file to which an engineering project to be detected
corresponds,
wherein the original application manifest configuration file includes use
permission
nodes to which the engineering project to be detected corresponds;
[0176] a use permission node extracting module 904, for extracting the use
permission nodes
from the original application manifest configuration file, and obtaining a
permission node
list file, wherein the permission node list includes a first use permission;
[0177] a use permission node processing module 906, for deleting permission
content to which
the use permission nodes correspond in the original application manifest
configuration
file, and obtaining an intermediate application manifest configuration file;
[0178] a manifest configuration file detecting module 908, for detecting the
intermediate
application manifest configuration file, and obtaining a permission detection
result list,
wherein the permission detection result includes a second use permission;
[0179] an abnormal use permission determining module 910, for determining any
abnormal use
permission according to the permission node list file and the permission
detection result
29
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
list; and
[0180] a permission abnormality detection report generating module 912, for
generating a
permission abnormality detection report according to the abnormal use
permission.
[0181] In one embodiment, as shown in Fig. 10, the manifest configuration file
obtaining module
902 includes:
[0182] an operation instruction obtaining unit 902a, for obtaining a system
operation instruction;
[0183] an operation instruction detecting unit 902b, for obtaining, when the
system operation
instruction is operative for the first time, a system source code to which a
system in which
the engineering project to be detected resides corresponds;
[0184] a system source code analyzing unit 902c, for analyzing the system
source code, and
obtaining a development environment to which the system source code
corresponds; and
[0185] a development environment detecting unit 902d, for obtaining, when the
development
environment is determined as a development environment supported by the
system, an
original application manifest configuration file to which the engineering
project to be
detected corresponds.
[0186] In one embodiment, the abnormal use permission determining module 910
is further
employed for obtaining a current use permission; and determining the current
use
permission as an abnormal use permission if the current use permission is only
present in
the permission node list file or only present in the permission detection
result list.
[0187] In one embodiment, as shown in Fig. 11, the permission abnormality
detecting device
800 further comprises:
[0188] a system source code obtaining module 1102, for obtaining a system
source code to which
the system in which the engineering project to be detected resides
corresponds;
[0189] a system source code analyzing module 1104, for analyzing the system
source code, and
obtaining a target permission in the system source code;
[0190] a source code content searching module 1106, for obtaining an analysis
keyword to which
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
the target permission corresponds, and searching for matching source code
content in the
system source code according to the analysis keyword; and
[0191] an association relation creating module 1108, for creating a
corresponding association
relation of the analysis keyword with the corresponding source code content.
[0192] In one embodiment, the source code content searching module 1106 is
further employed
for traversing each row of source codes of the system source code; obtaining a
current
row of source codes, and judging whether the current row of source codes
contains the
analysis keyword; and determining, when the current row of source codes
contains the
analysis keyword, the current row of source codes as the source code content
to which
the analysis keyword corresponds.
[0193] Specific definitions relevant to the permission abnormality detecting
device may be
inferred from the aforementioned definitions to the permission abnormality
detecting
method, while no repetition is made in this context. The various modules in
the
aforementioned permission abnormality detecting device can be wholly or partly
realized
via software, hardware, and a combination of software with hardware. The
various
modules can be embedded in the form of hardware in a processor in a computer
equipment or independent of any computer equipment, and can also be stored in
the form
of software in a memory in a computer equipment, so as to facilitate the
processor to
invoke and perform operations corresponding to the aforementioned various
modules.
[0194] Fig. 12 is a view illustrating the internal structure of a computer
equipment in an
embodiment. The computer equipment can specifically be terminal 102 or server
104 in
Fig. 1. As shown in Fig. 12, the computer equipment comprises a processor, a
memory, a
network interface, an input means and a display screen connected to each other
via a
system bus. The memory includes a nonvolatile storage medium and an internal
memory.
The nonvolatile storage medium of the computer equipment stores therein an
operating
system, and can further store therein a computer program that enables a
processor to
31
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
realize a permission abnormality detecting method when it is executed by the
processor.
The internal memory can also store therein a computer program that enables a
processor
to realize a permission abnormality detecting method when it is executed by
the processor.
The display screen of the computer equipment can be a liquid crystal display
screen or an
electronic ink display screen, the input means of the computer equipment can
be a touch
layer covering on the display screen, can also be a press button, a track ball
or a touch
control board disposed on the housing of the computer equipment, and can
further be an
externally connected keyboard, touch control board or mouse, etc.
[0195] As understandable to persons skilled in the art, the structure
illustrated in Fig. 12 is merely
a block diagram of partial structure relevant to the solution of the present
application, and
does not constitute any restriction to the computer equipment on which the
solution of
the present application is applied, as the specific computer equipment may
comprise
component parts that are more than or less than those illustrated in Fig. 12,
or may
combine certain component parts, or may have different layout of component
parts.
[0196] In one embodiment, there is provided a computer equipment that
comprises a memory, a
processor and a computer program stored on the memory and operable on the
processor,
and the following steps are realized when the processor executes the computer
program:
obtaining a source code to be detected; detecting whether the source code to
be detected
has any matching target analysis keyword according to an association relation;
obtaining,
when a matching target analysis keyword is present in the source code to be
detected, a
target permission that corresponds to the target analysis keyword; detecting
whether an
original application manifest configuration file has any target use permission
node that
corresponds to the target permission; and determining, when there is no target
use
permission node corresponding to the target permission, a permission to which
the source
code to be detected corresponds as an abnormal use permission.
[0197] In one embodiment, when the processor executes the computer program,
the following
32
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
steps are further realized: obtaining an original application manifest
configuration file to
which an engineering project to be detected corresponds, wherein the original
application
manifest configuration file includes use permission nodes to which the
engineering
project to be detected corresponds; extracting the use permission nodes from
the original
application manifest configuration file, and obtaining a permission node list
file, wherein
the permission node list includes a first use permission; deleting permission
content to
which the use permission nodes correspond in the original application manifest
configuration file, and obtaining an intermediate application manifest
configuration file;
detecting the intermediate application manifest configuration file, and
obtaining a
permission detection result list, wherein the permission detection result
includes a second
use permission; determining any abnormal use permission according to the
permission
node list file and the permission detection result list; and generating a
permission
abnormality detection report according to the abnormal use permission.
[0198] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: obtaining a system operation instruction;
obtaining, when the
system operation instruction is operative for the first time, a system source
code to which
a system in which the engineering project to be detected resides corresponds;
analyzing
the system source code, and obtaining a development environment to which the
system
source code corresponds; and obtaining, when the development environment is
determined as a development environment supported by the system, an original
application manifest configuration file to which the engineering project to be
detected
corresponds.
[0199] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: obtaining a current use permission; and
determining the current
use permission as an abnormal use permission if the current use permission is
only present
in the permission node list file or only present in the permission detection
result list.
33
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0200] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: obtaining a system source code to which the system
in which
the engineering project to be detected resides corresponds; analyzing the
system source
code, and obtaining a target permission in the system source code; obtaining
an analysis
keyword to which the target permission corresponds, and searching for matching
source
code content in the system source code according to the analysis keyword; and
creating
a corresponding association relation of the analysis keyword with the
corresponding
source code content.
[0201] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: traversing each row of source codes of the system
source code;
obtaining a current row of source codes, and judging whether the current row
of source
codes contains the analysis keyword; and determining, when the current row of
source
codes contains the analysis keyword, the current row of source codes as the
source code
content to which the analysis keyword corresponds.
[0202] In one embodiment, there is provided a computer-readable storage medium
storing
thereon a computer program, and the following steps are realized when the
computer
program is executed by a processor: obtaining a source code to be detected;
detecting
whether the source code to be detected has any matching target analysis
keyword
according to an association relation; obtaining, when a matching target
analysis keyword
is present in the source code to be detected, a target permission that
corresponds to the
target analysis keyword; detecting whether an original application manifest
configuration
file has any target use permission node that corresponds to the target
permission; and
determining, when there is no target use permission node corresponding to the
target
permission, a permission to which the source code to be detected corresponds
as an
abnormal use permission.
[0203] In one embodiment, when the processor executes the computer program,
the following
34
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
steps are further realized: obtaining an original application manifest
configuration file to
which an engineering project to be detected corresponds, wherein the original
application
manifest configuration file includes use permission nodes to which the
engineering
project to be detected corresponds; extracting the use permission nodes from
the original
application manifest configuration file, and obtaining a permission node list
file, wherein
the permission node list includes a first use permission; deleting permission
content to
which the use permission nodes correspond in the original application manifest
configuration file, and obtaining an intermediate application manifest
configuration file;
detecting the intermediate application manifest configuration file, and
obtaining a
permission detection result list, wherein the permission detection result
includes a second
use permission; determining any abnormal use permission according to the
permission
node list file and the permission detection result list; and generating a
permission
abnormality detection report according to the abnormal use permission.
[0204] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: obtaining a system operation instruction;
obtaining, when the
system operation instruction is operative for the first time, a system source
code to which
a system in which the engineering project to be detected resides corresponds;
analyzing
the system source code, and obtaining a development environment to which the
system
source code corresponds; and obtaining, when the development environment is
determined as a development environment supported by the system, an original
application manifest configuration file to which the engineering project to be
detected
corresponds.
[0205] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: obtaining a current use permission; and
determining the current
use permission as an abnormal use permission if the current use permission is
only present
in the permission node list file or only present in the permission detection
result list.
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
[0206] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: obtaining a system source code to which the system
in which
the engineering project to be detected resides corresponds; analyzing the
system source
code, and obtaining a target permission in the system source code; obtaining
an analysis
keyword to which the target permission corresponds, and searching for matching
source
code content in the system source code according to the analysis keyword; and
creating
a corresponding association relation of the analysis keyword with the
corresponding
source code content.
[0207] In one embodiment, when the processor executes the computer program,
the following
steps are further realized: traversing each row of source codes of the system
source code;
obtaining a current row of source codes, and judging whether the current row
of source
codes contains the analysis keyword; and determining, when the current row of
source
codes contains the analysis keyword, the current row of source codes as the
source code
content to which the analysis keyword corresponds.
[0208] As comprehensible to persons ordinarily skilled in the art, the entire
or partial flows in
the methods according to the aforementioned embodiments can be completed via a
computer program instructing relevant hardware, the computer program can be
stored in
a nonvolatile computer-readable storage medium, and the computer program can
include
the flows as embodied in the aforementioned various methods when executed. Any
reference to the memory, storage, database or other media used in the various
embodiments provided by the present application can all include nonvolatile
and/or
volatile memory/memories. The nonvolatile memory can include a read-only
memory
(ROM), a programmable ROM (PROM), an electrically programmable ROM (EPROM),
an electrically erasable and programmable ROM (EEPROM) or a flash memory. The
volatile memory can include a random access memory (RAM) or an external cache
memory. To serve as explanation rather than restriction, the RAM is obtainable
in many
forms, such as static RAM (SRAM), dynamic RAM (DRAM), synchronous DRAM
36
Date Regue/Date Received 2022-07-05
CA 03166981 2022-07-05
(SDRAM), dual data rate SDRAM (DDRSDRAM), enhanced SDRAM (ESDRAM),
synchronous link (Synchlink) DRAM (SLDRAM), memory bus (Rambus) direct RAM
(RDRAM), direct Rambus dynamic RAM (DRDRAM), and Rambus dynamic RAM
(RDRAM), etc.
[0209] Technical features of the aforementioned embodiments are randomly
combinable, while
all possible combinations of the technical features in the aforementioned
embodiments
are not exhausted for the sake of brevity, but all these should be considered
to fall within
the scope recorded in the Description as long as such combinations of the
technical
features are not mutually contradictory.
[0210] The foregoing embodiments are merely directed to several modes of
execution of the
present application, and their descriptions are relatively specific and
detailed, but they
should not be hence misunderstood as restrictions to the inventive patent
scope. As should
be pointed out, persons with ordinary skill in the art may further make
various
modifications and improvements without departing from the conception of the
present
application, and all these should pertain to the protection scope of the
present application.
Accordingly, the patent protection scope of the present application shall be
based on the
attached Claims.
37
Date Regue/Date Received 2022-07-05