Note : Les descriptions sont présentées dans la langue officielle dans laquelle elles ont été soumises.
CA 02298274 2000-02-08
Yaker 13
SPECIFIABLE DELETE TIMES FOR EMAIL MESSAGES
Field of the Invention
The present invention relates to computer networks that support the
transmission of
electronic mail (email) messages between nodes of the network.
Cross-Reference to Related Applications
This is a continuation-in-part of co-pending application serial number
08/900.793. tiled on
7/2/97 as attorney docket no. Yaker 7, the teachings of which are incorporated
herein by
reference.
Description of the Related Art
Typical computer networks allow a user (i.e., an email sender) to send an
email message to
one or more other users (i.e., email recipients), who can then each decide
independently if and when
to read his or her copy of the email message. After an email message is read
by a recipient. the
recipient typically has the option of deleting the message or saving the
message for future use. In
some email systems, although a message has been deleted, it can still be
recovered from an
I 5 electronic "trash bin" containing such deleted messages. Only when the
user explicitly empties the
trash will email messages become irretrievable by the user. Some systems allow
users to select an
option whereby the trash is emptied whenever the user logs out of the email
system, but this option
is typically disabled by default.
One of the drawbacks to conventional email systems is that, unless the
recipient explicitly
deletes a message and then, if necessary. explicitly empties the trash, the
message will be retained
indefinitely in the memory of his or her computer. This can be problematic
when email messages
contains sensitive or confidential material.
Summary Of The Invention
The present invention is directed to an email system that allows a user to
instruct the
system to automatically delete an email message after a specified time or
duration. Depending on
the options provided in a particular implementation of such an email system,
the user may be the
sender of an email message, the recipient. or the system administrator. Again,
depending on the
implementation, this automatic message deletion may apply only to messages
that have been read
CA 02298274 2000-02-08
Yaker 13 2
by the recipient or it may apply to any message whether or not the message has
been read by the
recipient.
In one embodiment of the invention, the present invention is a method and
apparatus for
processing email messages by a computer. An email message is received and
stored into memory,
wherein a user-specified delete time is or has been assigned for the message.
The message is then
automatically deleted from the memory after etpiration of the delete time.
Brief Description Of The Drawings
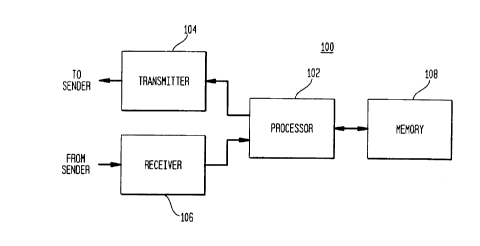
Fig. 1 shows a block diagram of an email messaging system, according to one
embodiment
of the present invention;
Fig. 2 shows a flow diagram of the processing implemented by the system of
Fig. 1 related
. to the preparation and sending of an email message; and
Fig. 3 shows a flow diagram of the processing implemented by the system of
Fig. 1 related
to the receipt and handling of an email message.
Detailed Description
I 5 The present invention addresses a security problem related to email
systems. fn particular,
an email system of the present invention enables a user to specify a time for
deleting an email
message. The user may be the sender of the message, a recipient of the
message, or the system
administrator for the computer network. The delete time may be specified in
terms of a particular
duration of time, e.g., a number of hours. days. or weeks, after transmission
or receipt of the
message. Alternatively, the delete time may be specified in terms of a time
and date by hour. day.
month, and year. In one embodiment, the sender of the email message has the
abiliy to spcci h the
delete time when preparing the message. Alternatively or in addition, each
recipient can specilv a
default delete time for each email message he or she receives or a specific
delete time for each
different email message as the recipient reads that message. The system
administrator may also be
able to specify default delete times. including different delete times for
different network users.
Typically, default delete times, whether set by recipients or system
administrators, would be in
terms of a particular duration of time rather than a time and date.
Fig. 1 shows a block diagram of a node 100 of a computer neUvork supporting
the
preparation and sending of outgoing mail messages to one or more other network
users a, wll ,m
CA 02298274 2000-02-08
Yaker 13 3
the receipt and handling of incoming email messages from other network users,
according to one
embodiment of the present invention. The computer network can be any suitable
ype of computer
network, such as a local area network or intranet or a wide area network or
Internet. Similar, node
100 can be any suitable type of computer such as a desktop personal computer
or a workstation.
The basic block diagram ~f Fig. 1 show s the general functionality supported
by a node of an email
system.
In particular, transmitter 104 of Fig. 1 transmits outgoing email messages
from node 100.
receiver 106 receives incoming email messages, and memory 108 stores incoming
email messages.
Processor 102 coordinates the activities of the other components of node 100,
including the
preparation and transmission of outgoing email messages as well as the
receipt, storage, reading.
and deleting of incoming email messages. Depending on the implementation, an
email system can
be designed to provide some or all of the following options to network users:
o A sender of an email message can select a delete time (e.g., via either a
speciFed date and
time or a specified dwation) for each outgoing message.
I S o The sender can set a default delete time in terms of a specified
duration for each of his ur
her email messages. In addition, the sender can vary the delete time from
message to
message.
o The sender can vary the delete time from recipient to recipient for a single
email message
o The sender has the option of specifying that the message be deleted only
after the mcssa~~e
has been read by the recipient or whether or not the message has been read.
o The sender has the option of specifying that the message be deleted as soon
as it is read by
a recipient, whether or not the specified delete time has expired.
o The recipient or system administrator can set a default delete time (e.g.,
t~picallv a
specified duration) for all incoming messages.
o The recipient has the opUOn of specifying that the message be deleted either
(al only at~nr
the message has been read by the recipient or (b) whether or not the message
has been read.
o The recipient can set a specific delete time as each incoming message is
read by the
recipient.
CA 02298274 2000-02-08
Yaker 13 4
o The recipient can override a delete time specified by the sender.
In any event, assuming that the relevant conditions are met, after the
expiration of a specified delete
time, processor 102 of Fig. 1 will automatically delete the corresponding
email message, where
"delete" may mean "make the message unavailable to the recipient," in which
case, it is equivalent
to sending an email message to a trash bin and then emptying the trash for
conventional email
systems. Depending on the implementation. the term "delete" as understood for
the present
invention may also imply an operation that completely erases the corresponding
region of memory
108, so that even system administrators using special memory reconstruction
routines cannot
recover the message.
Fig. 2 shows a flow diagram of the processing implemented by node 100 of Fig.
1 when the
user is a sender of an outgoing email message, according to one embodiment of
the present
invention. In that case, the user prepares an email message for one or more
recipients (step 202 of
Fig. 2), optionally specifying an automatic delete time for the message (step
204) and whether or
not that automatic delete time applies to unread messages (step 206). The
sender then transmits the
1 S email message to the recipients) (step 208), where the automatic deletion
instructions are
embedded in the email message according to some appropriate specified
protocol.
Fig. 3 shows a flow diagram of the processing implemented by node 100 of Fig.
1 when the
user is a recipient of an incoming email message, according to one embodiment
of the present
invention. Prior to receiving an email message. the recipient optionally
specifies a default
automatic delete time for his or her incoming email messages (step 302 of Fig.
3) and whether ur
not that automatic delete time applies to unread messages (step 304). After
the recipient receiv cs
an incoming email message (step 306) and after expiration of the specified
delete time. assumm~
all other conditions are met (e.g., a flag has been set indicating that the
message has been read if
only read messages are to be deleted). the processor automatically deletes the
message (step 308)
Each incoming email message, with its embedded delete time information, is
assigned a
receipt time by the processor indicating the time of receipt of the email
message by the recipient
When the delete time is specified as a particular date and time, the processor
compares the dvlctc
time with the local time kept by the machine to determine when to delete the
message. V'hcn the
delete time is specified as a particular duration (e.g., in number of days or
hours), the proccs:ur
compares the local time to the sum of the message receipt time and the
specified delete um~ u>
determine when to delete the message.
CA 02298274 2000-02-08
Yaker I3
In addition to applying at the individual computers where email messages are
received. the
present invention can also be applied within computer servers that are
responsible for storing and
distributing email messages to individual recipients.
It will be further understood that various changes in the details, materials.
and
arrangements of the parts which have been described and illustrated in order
to explain the nature
of this invention may be made by those skilled in the art without departing
from the principle and
scope of the invention as expressed in the Following claims.